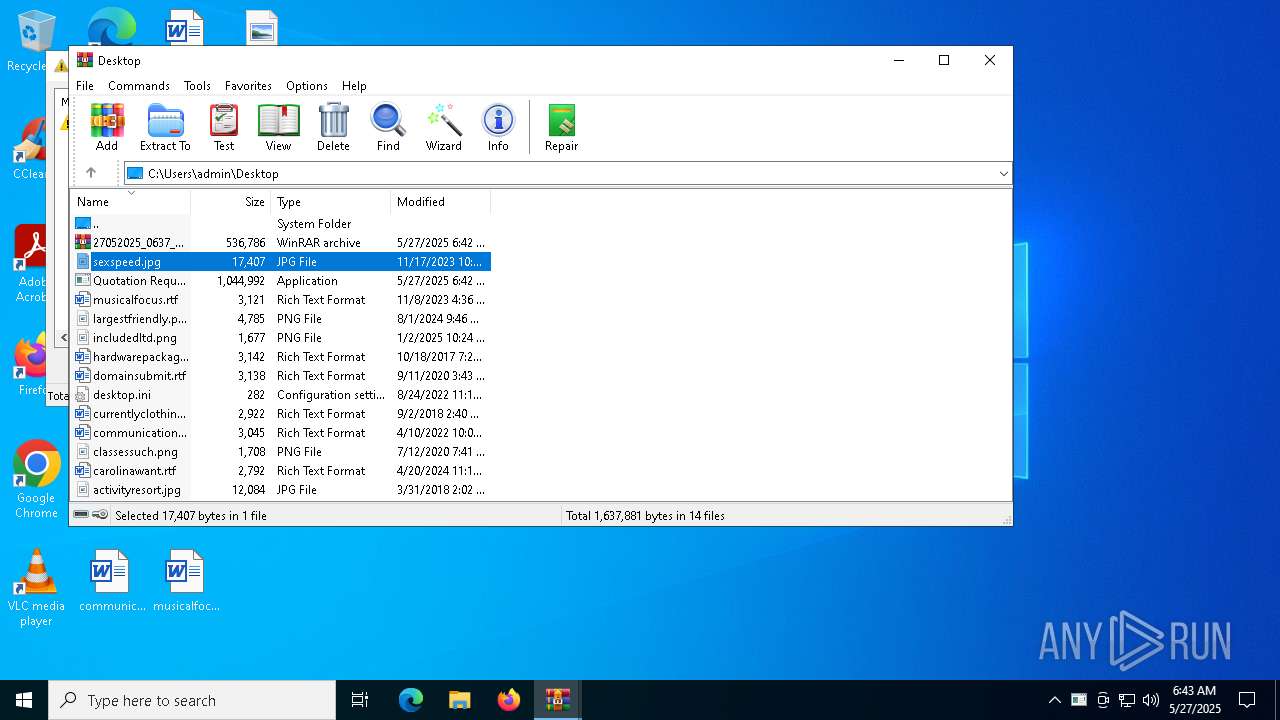
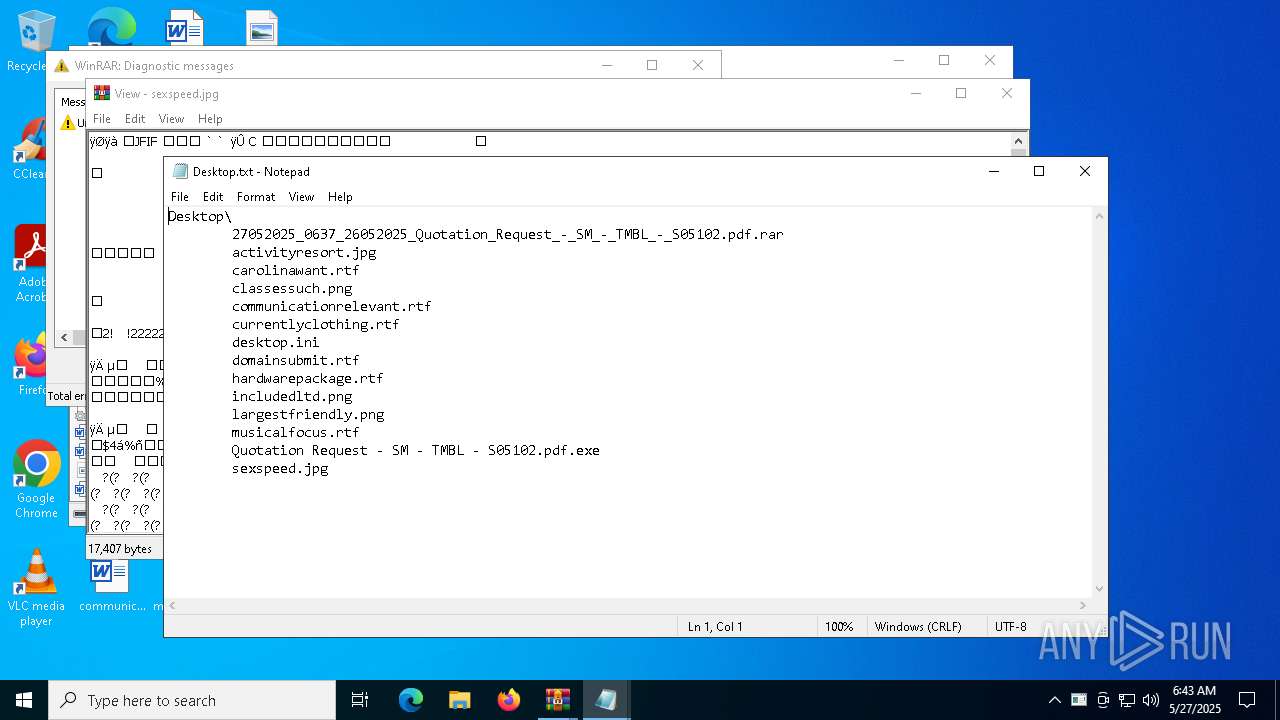
| File name: | 27052025_0637_26052025_Quotation_Request_-_SM_-_TMBL_-_S05102.pdf.rar |
| Full analysis: | https://app.any.run/tasks/bbbe6e3d-17be-408d-88ac-5c6af3a00ed0 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 27, 2025, 06:42:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D0309D17522953C9E890B4A14D26C314 |
| SHA1: | 91FF528B7C84869EC05203640C3535E0A550F209 |
| SHA256: | ECB7E6CCA4706566C9F7233FA4CE7AFD676EBA459888E0BA05CAA3897225A811 |
| SSDEEP: | 24576:SS29/19pDMgoaZYIGCKMdMZnG1NWG/tUhsI/wrT0m+:SS29/TpggoaZYIGCKMdMZnG1NWG/tMsW |
MALICIOUS
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 7828)
STORMKITTY has been detected (YARA)
- RegSvcs.exe (PID: 7828)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 7828)
ASYNCRAT has been detected (MUTEX)
- RegSvcs.exe (PID: 7828)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- RegSvcs.exe (PID: 7828)
Starts application with an unusual extension
- cmd.exe (PID: 2268)
- cmd.exe (PID: 8096)
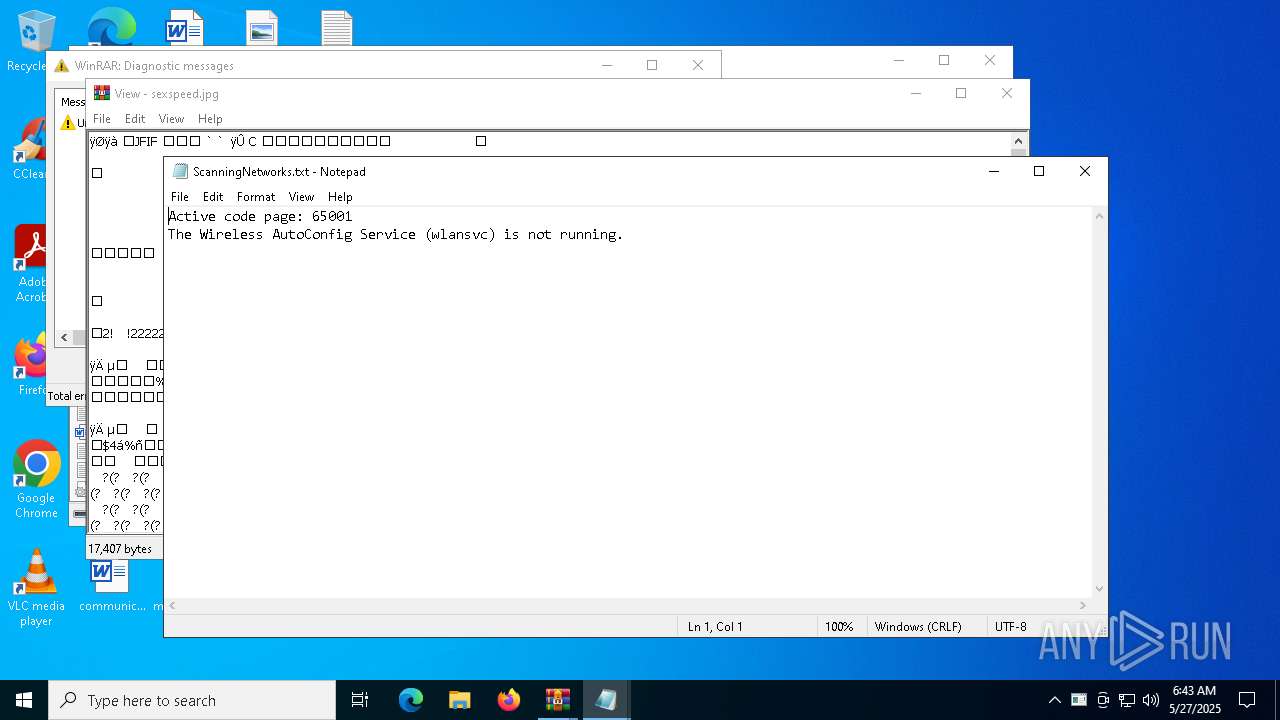
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 2268)
- cmd.exe (PID: 8096)
Checks for external IP
- svchost.exe (PID: 2196)
- RegSvcs.exe (PID: 7828)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8096)
Starts CMD.EXE for commands execution
- RegSvcs.exe (PID: 7828)
Possible usage of Discord/Telegram API has been detected (YARA)
- RegSvcs.exe (PID: 7828)
Potential Corporate Privacy Violation
- RegSvcs.exe (PID: 7828)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegSvcs.exe (PID: 7828)
INFO
Manual execution by a user
- Quotation Request - SM - TMBL - S05102.pdf.exe (PID: 7800)
- notepad.exe (PID: 7272)
- notepad.exe (PID: 4700)
- notepad.exe (PID: 6760)
- notepad.exe (PID: 1020)
- notepad.exe (PID: 6416)
- notepad.exe (PID: 5416)
- notepad.exe (PID: 7320)
- WINWORD.EXE (PID: 5344)
- notepad.exe (PID: 6132)
Reads mouse settings
- Quotation Request - SM - TMBL - S05102.pdf.exe (PID: 7800)
Checks supported languages
- RegSvcs.exe (PID: 7828)
- Quotation Request - SM - TMBL - S05102.pdf.exe (PID: 7800)
- chcp.com (PID: 7220)
- chcp.com (PID: 8148)
Reads the computer name
- RegSvcs.exe (PID: 7828)
Create files in a temporary directory
- Quotation Request - SM - TMBL - S05102.pdf.exe (PID: 7800)
- RegSvcs.exe (PID: 7828)
The sample compiled with english language support
- WinRAR.exe (PID: 7488)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 7828)
Creates files or folders in the user directory
- RegSvcs.exe (PID: 7828)
Changes the display of characters in the console
- cmd.exe (PID: 2268)
- cmd.exe (PID: 8096)
Reads CPU info
- RegSvcs.exe (PID: 7828)
Disables trace logs
- RegSvcs.exe (PID: 7828)
Checks proxy server information
- RegSvcs.exe (PID: 7828)
- slui.exe (PID: 4628)
Reads the software policy settings
- RegSvcs.exe (PID: 7828)
- slui.exe (PID: 4628)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7320)
- notepad.exe (PID: 7272)
- notepad.exe (PID: 6760)
- notepad.exe (PID: 4700)
- notepad.exe (PID: 6416)
- notepad.exe (PID: 1020)
- notepad.exe (PID: 5416)
- notepad.exe (PID: 6132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 536563 |
| UncompressedSize: | 1044992 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Quotation Request - SM - TMBL - S05102.pdf.exe |
Total processes
153
Monitored processes
24
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\ScanningNetworks.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | "cmd.exe" /C chcp 65001 && netsh wlan show networks mode=bssid | C:\Windows\SysWOW64\cmd.exe | — | RegSvcs.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4700 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Desktop.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5024 | netsh wlan show networks mode=bssid | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5344 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\currentlyclothing.rtf /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5416 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\OneDrive.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Videos.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 463
Read events
27 078
Write events
364
Delete events
21
Modification events
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\27052025_0637_26052025_Quotation_Request_-_SM_-_TMBL_-_S05102.pdf.rar | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
0
Suspicious files
116
Text files
89
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7800 | Quotation Request - SM - TMBL - S05102.pdf.exe | C:\Users\admin\AppData\Local\Temp\recomplete | binary | |
MD5:1D192C751429739DB8CDD0DF4468087C | SHA256:95ABB878C9D272A061EAFBE61653B932514EA9B0FE05C3C362595ECFED18383E | |||
| 7800 | Quotation Request - SM - TMBL - S05102.pdf.exe | C:\Users\admin\AppData\Local\Temp\enterogenous | text | |
MD5:18265F602A50BFD6E104B3793AAEBADD | SHA256:4A75C3797D213F7835C95E4A969A933D577EC359FD6C105907F5EA5DC1ECA255 | |||
| 7800 | Quotation Request - SM - TMBL - S05102.pdf.exe | C:\Users\admin\AppData\Local\Temp\autF7EF.tmp | binary | |
MD5:3FAB405CC807B1978787100C5E21A742 | SHA256:FEE998984BDB2DD645BBEA0E44A6E3D35BC4FA992C03C4EAC0F875AB30800421 | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\desktop.ini | text | |
MD5:3A37312509712D4E12D27240137FF377 | SHA256:B029393EA7B7CF644FB1C9F984F57C1980077562EE2E15D0FFD049C4C48098D3 | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\currentlyclothing.rtf | text | |
MD5:EBCA1B2FC8170E098EE61ED240FA8FC5 | SHA256:585B6C5EB019A7934C2CD7E39C0325E5FC1E5EDCFBC256629299FD4EE52F12C1 | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\baycompleted.rtf | text | |
MD5:9C3872ADC20D6CE540BBBE3EA719E1A8 | SHA256:3CCD781E5125B761941CD5849E6E692B95960B4E367D487D698A90E38909F67A | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\humanship.jpg | image | |
MD5:011C4C514A636EBB2DD108CC2646ED86 | SHA256:2DBBE8D5D30BE33F9D876E437D98B60ACC969780B95619952B8A8AAD28790FB6 | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\desktop.ini | text | |
MD5:ECF88F261853FE08D58E2E903220DA14 | SHA256:CAFEC240D998E4B6E92AD1329CD417E8E9CBD73157488889FD93A542DE4A4844 | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\carolinawant.rtf | text | |
MD5:EA8C80ADACE92EC560A75D71084C3DEE | SHA256:CBCE4675AC61878625BDFF75533EC2EA4EE56958F37ACE6E3FC991FC5E3920D8 | |||
| 7828 | RegSvcs.exe | C:\Users\admin\AppData\Local\eb6ac490e04191317f0bea9d91713320\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\Saved Pictures\desktop.ini | text | |
MD5:87A524A2F34307C674DBA10708585A5E | SHA256:D01A7EF6233EF4AB3EA7210C0F2837931D334A20AE4D2A05ED03291E59E576C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
80
TCP/UDP connections
90
DNS requests
19
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5796 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 52.168.112.66:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.111.229.20:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=0&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B11CBA5AD-6481-4359-897B-F31D01E5AF8D%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofjhlwlmoc1pz531%22%7D | unknown | text | 542 b | whitelisted |
— | — | GET | 200 | 184.24.77.4:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp01840907.cab | unknown | compressed | 42.6 Kb | whitelisted |
— | — | POST | 200 | 52.168.112.66:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | whitelisted |
— | — | GET | 200 | 23.53.43.59:443 | https://metadata.templates.cdn.office.net/client/templates/gallery?lcid=1033&syslcid=1033&uilcid=1033&app=0&ver=16&tl=2&build=16.0.16026>ype=0%2C1%2C2%2C5%2C | unknown | xml | 10.7 Kb | whitelisted |
5776 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5776 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.67.196.114:443 | https://api.mylnikov.org/geolocation/wifi?v=1.1&bssid=d4:da:6d:56:32:50 | unknown | binary | 88 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5776 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5776 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5796 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5776 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
7828 | RegSvcs.exe | 104.16.185.241:80 | icanhazip.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
icanhazip.com |
| whitelisted |
api.mylnikov.org |
| unknown |
api.telegram.org |
| whitelisted |
pastebin.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7828 | RegSvcs.exe | Potential Corporate Privacy Violation | ET INFO Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
7828 | RegSvcs.exe | Attempted Information Leak | ET INFO IP Check Domain (icanhazip. com in HTTP Host) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
— | — | Potential Corporate Privacy Violation | ET INFO Wifi Geolocation Lookup Attempt |
— | — | Potentially Bad Traffic | ET INFO BSSID Location Lookup via api .mylnikov .org |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7828 | RegSvcs.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
7828 | RegSvcs.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |