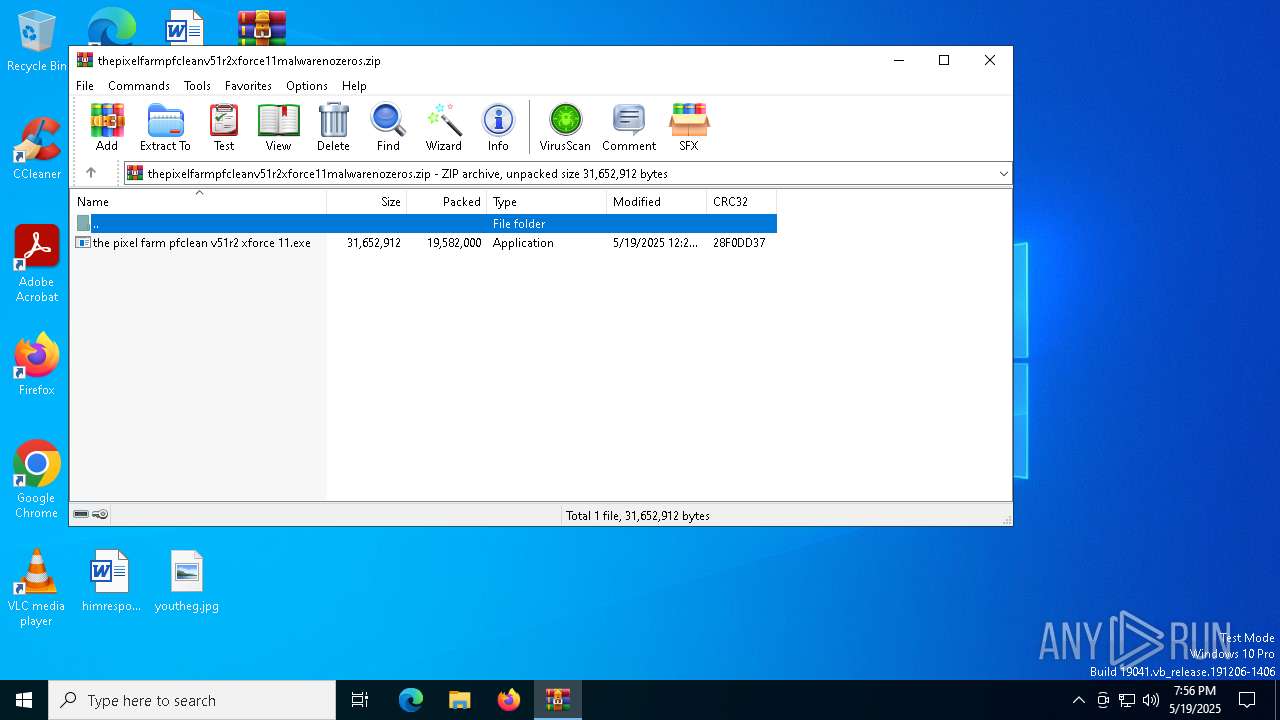
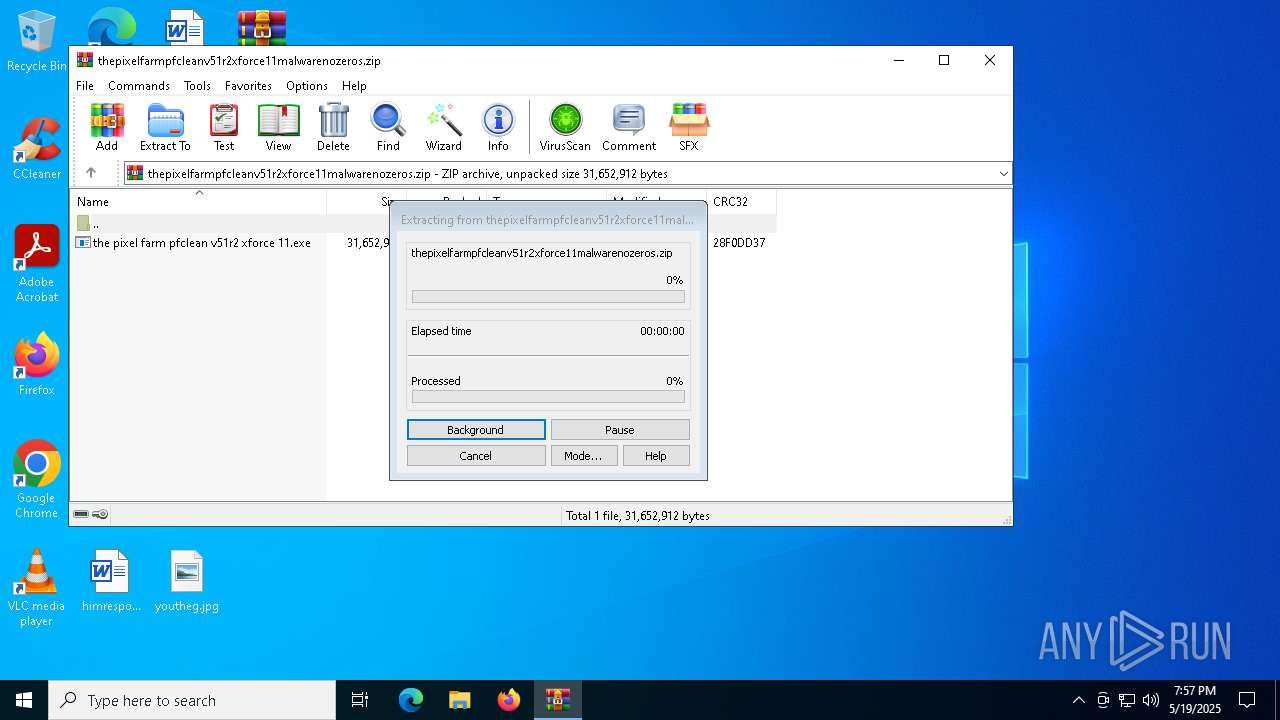
| File name: | thepixelfarmpfcleanv51r2xforce11malwarenozeros.zip |
| Full analysis: | https://app.any.run/tasks/195881c7-761a-45b7-845b-edcc8765cb5e |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 19, 2025, 19:55:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | EB6146FB0FFD2CB9CCEC1E41B735CFAB |
| SHA1: | 77B014CB9BF8B583AF6EA2AD1A812EDAB04A08DD |
| SHA256: | EC689732317E063910E3A7D5E8C1594CBC3A412EBE46B02DDED18FEDAA4C4B7C |
| SSDEEP: | 98304:gkyDorkBV1SkhkpIXgjU/3/DC4gCMsHQKqB053o/jOVs4Bk8+O8XaytohR3FxlTK:SWMO9xS3gTTR/8v9dO1qnq7Rhi85f84L |
MALICIOUS
AutoIt loader has been detected (YARA)
- Marble.com (PID: 2616)
Actions looks like stealing of personal data
- Marble.com (PID: 2616)
Steals credentials from Web Browsers
- Marble.com (PID: 2616)
LUMMA mutex has been found
- Marble.com (PID: 2616)
SUSPICIOUS
Reads security settings of Internet Explorer
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
- WinRAR.exe (PID: 6816)
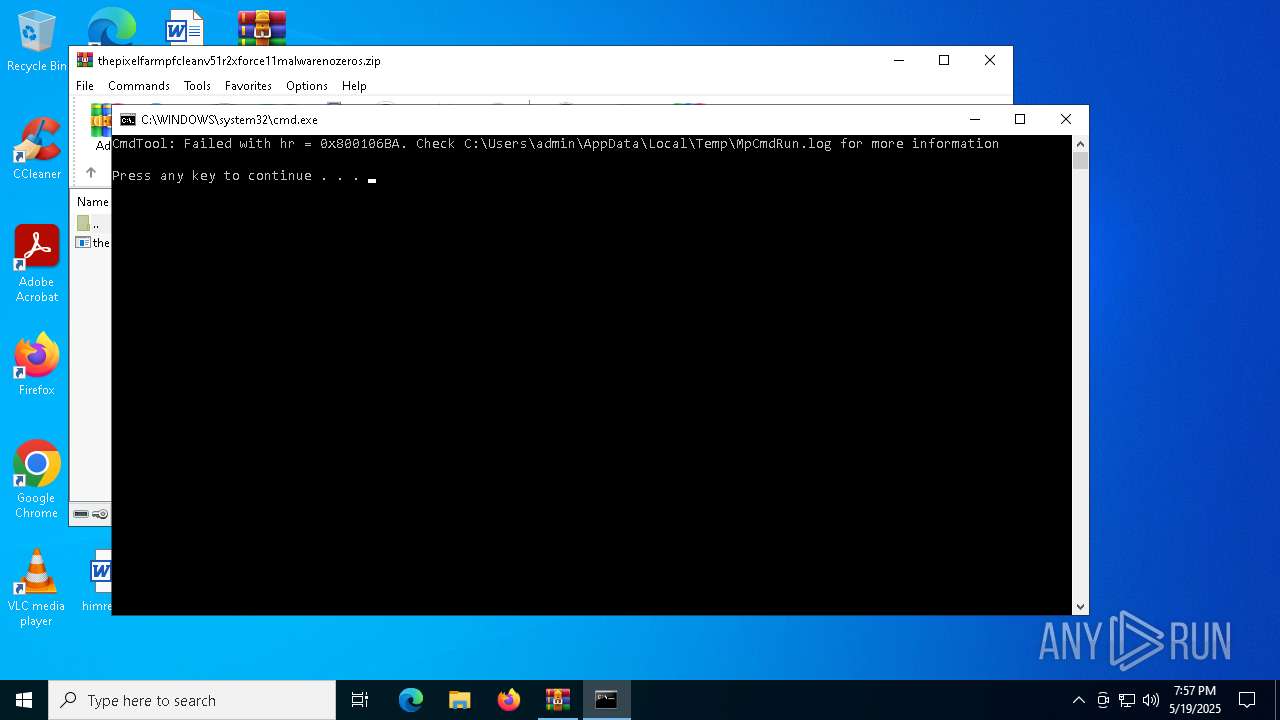
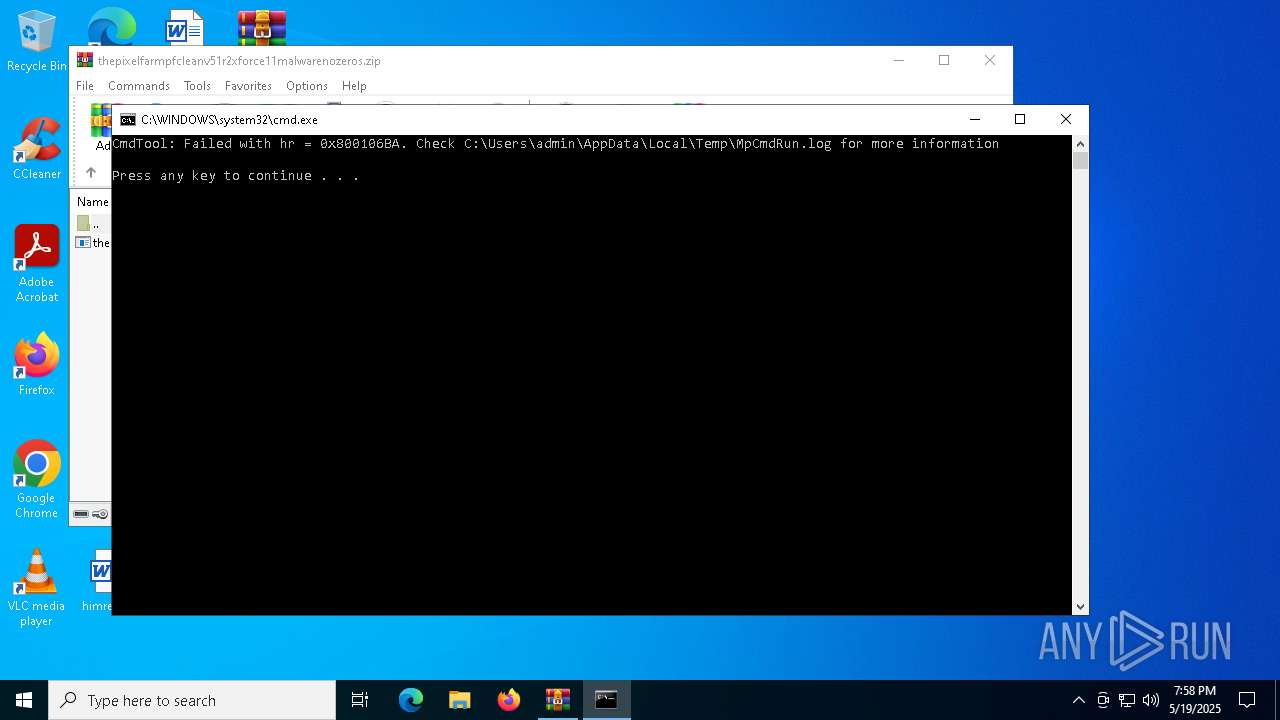
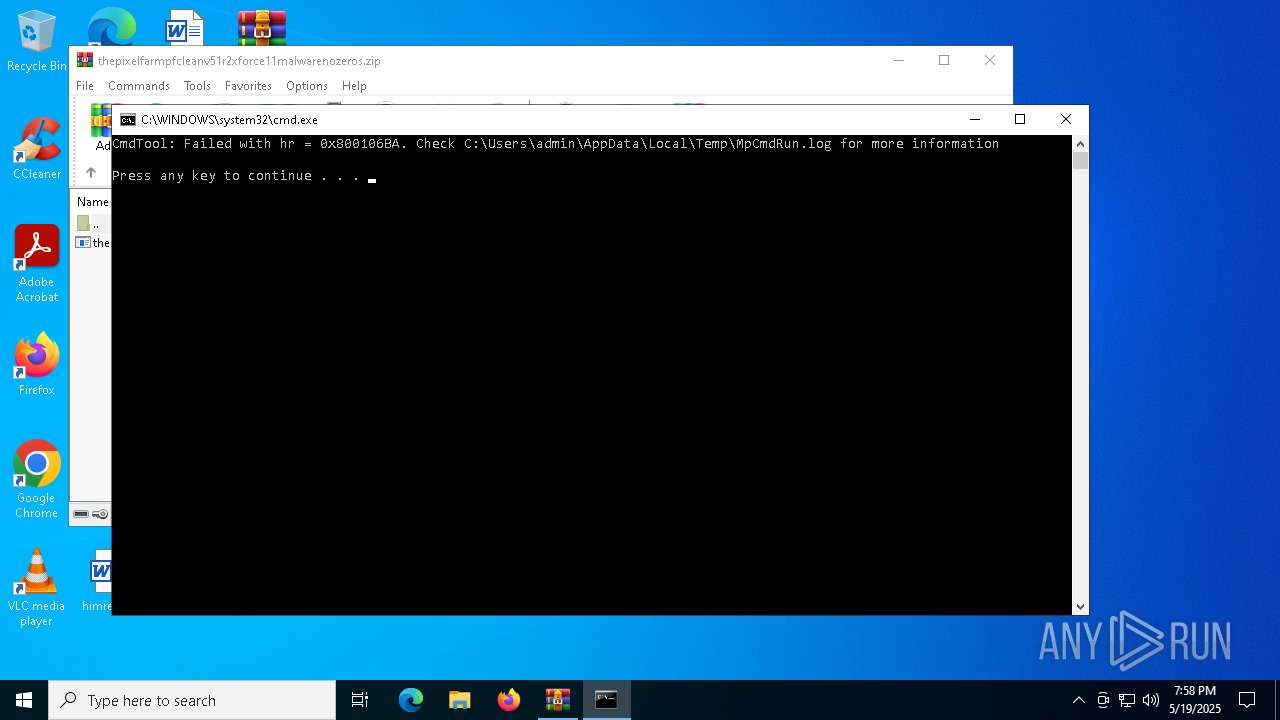
Starts CMD.EXE for commands execution
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
- cmd.exe (PID: 1128)
- WinRAR.exe (PID: 6816)
Executing commands from a ".bat" file
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
- WinRAR.exe (PID: 6816)
Get information on the list of running processes
- cmd.exe (PID: 1128)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1128)
Application launched itself
- cmd.exe (PID: 1128)
Starts application with an unusual extension
- cmd.exe (PID: 1128)
Starts the AutoIt3 executable file
- cmd.exe (PID: 1128)
The executable file from the user directory is run by the CMD process
- Marble.com (PID: 2616)
There is functionality for taking screenshot (YARA)
- Marble.com (PID: 2616)
Searches for installed software
- Marble.com (PID: 2616)
INFO
Checks supported languages
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
- extrac32.exe (PID: 1116)
- Marble.com (PID: 2616)
- MpCmdRun.exe (PID: 2432)
Reads the computer name
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
- extrac32.exe (PID: 1116)
- Marble.com (PID: 2616)
- MpCmdRun.exe (PID: 2432)
Manual execution by a user
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
Process checks computer location settings
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
Create files in a temporary directory
- the pixel farm pfclean v51r2 xforce 11.exe (PID: 2852)
- extrac32.exe (PID: 1116)
- MpCmdRun.exe (PID: 2432)
Creates a new folder
- cmd.exe (PID: 3332)
Reads mouse settings
- Marble.com (PID: 2616)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6816)
Checks proxy server information
- slui.exe (PID: 4452)
Reads the software policy settings
- slui.exe (PID: 4452)
- Marble.com (PID: 2616)
Reads the machine GUID from the registry
- Marble.com (PID: 2616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:19 15:20:34 |
| ZipCRC: | 0x28f0dd37 |
| ZipCompressedSize: | 19582000 |
| ZipUncompressedSize: | 31652912 |
| ZipFileName: | the pixel farm pfclean v51r2 xforce 11.exe |
Total processes
142
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | extrac32 /Y /E Album.xlam | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\WINDOWS\System32\CMd.exe" /c copy Southeast.xlam Southeast.xlam.bat & Southeast.xlam.bat | C:\Windows\SysWOW64\cmd.exe | — | the pixel farm pfclean v51r2 xforce 11.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | findstr /V "childrens" Header | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | findstr "bdservicehost SophosHealth AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
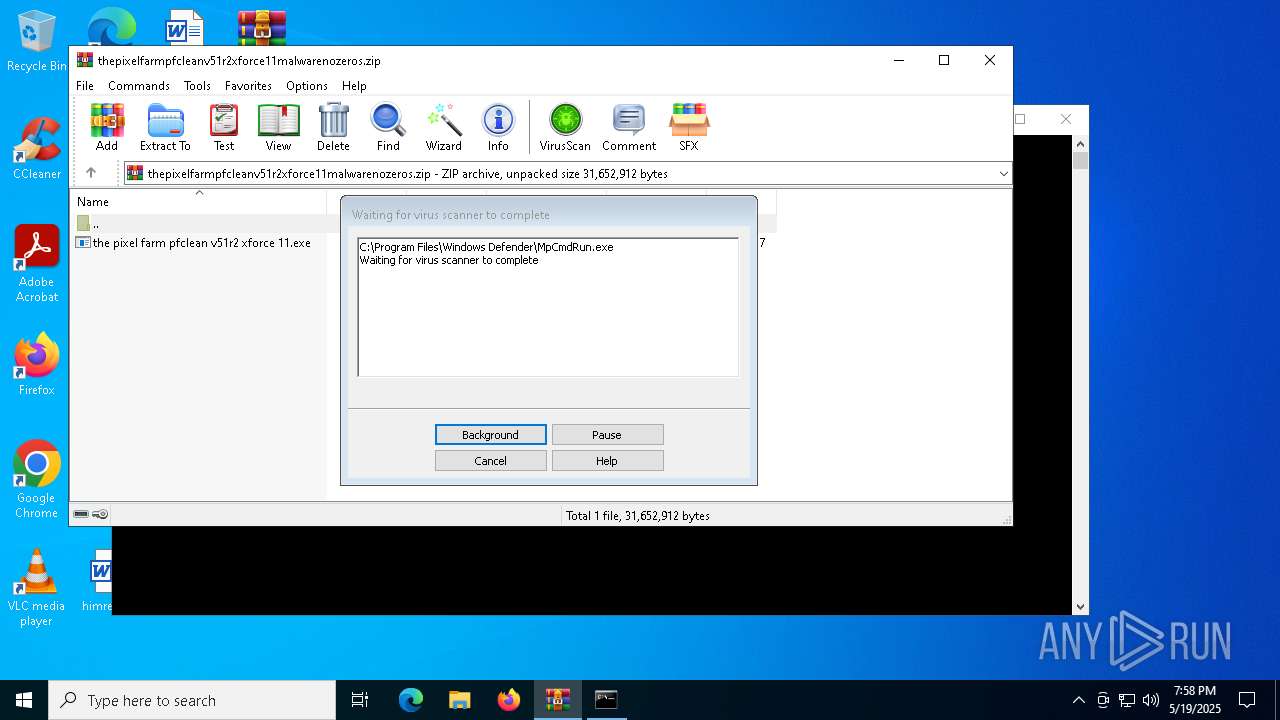
| 2432 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6816.46997" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | Marble.com h | C:\Users\admin\AppData\Local\Temp\565204\Marble.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 2644 | cmd /c copy /b ..\Lopez.xlam + ..\Lookup.xlam + ..\Knowledge.xlam + ..\Newton.xlam + ..\Electric.xlam + ..\Construction.xlam + ..\Ballot.xlam h | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\the pixel farm pfclean v51r2 xforce 11.exe" | C:\Users\admin\Desktop\the pixel farm pfclean v51r2 xforce 11.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3332 | cmd /c md 565204 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4220 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 835
Read events
8 826
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\thepixelfarmpfcleanv51r2xforce11malwarenozeros.zip | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
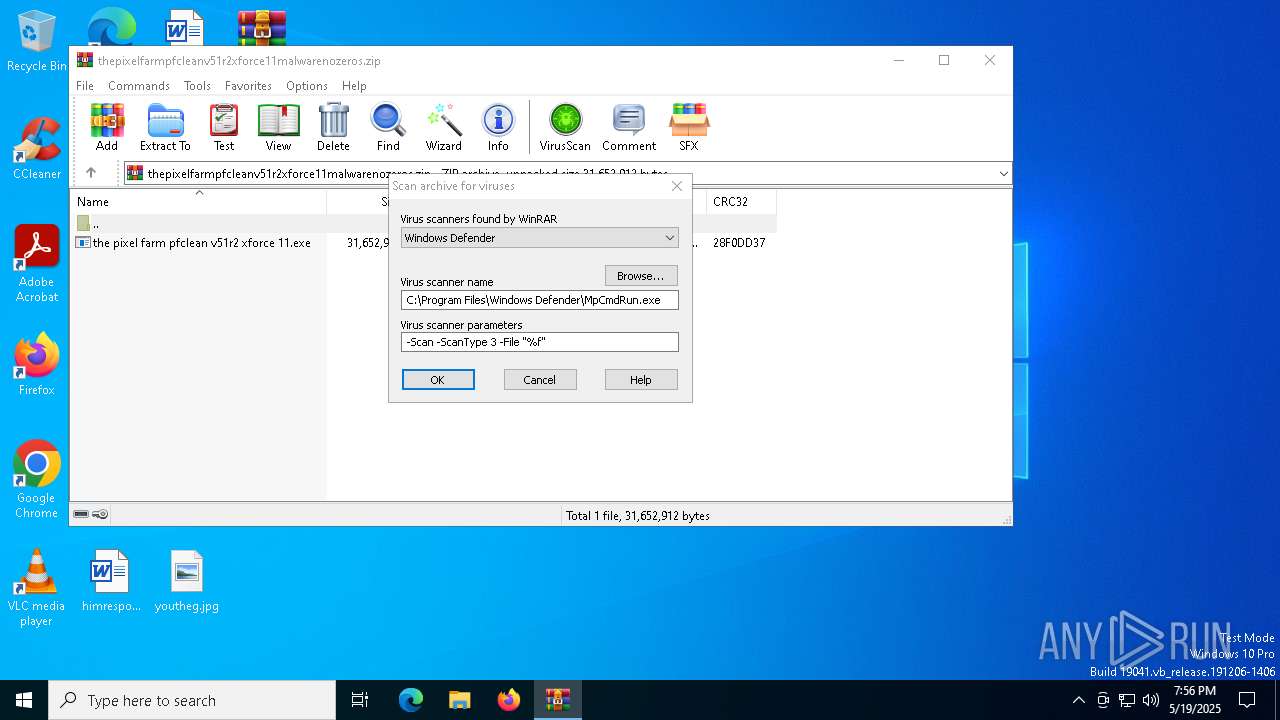
| (PID) Process: | (6816) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
1
Suspicious files
20
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Census | binary | |
MD5:4858BCB014DC33BB307C376BC1E13988 | SHA256:0BB9DB87ADD7781409D9E6D9D79992270155C05148CF86AB4E5DBA93F015ADB6 | |||
| 2852 | the pixel farm pfclean v51r2 xforce 11.exe | C:\Users\admin\AppData\Local\Temp\Southeast.xlam | text | |
MD5:65D49D511F33091EA6B2EEBF02D930A0 | SHA256:DB592310308C45E9E658B823923A4D21B8E5ADB825480B3682560FDEC53DEB85 | |||
| 2852 | the pixel farm pfclean v51r2 xforce 11.exe | C:\Users\admin\AppData\Local\Temp\Lookup.xlam | binary | |
MD5:9551BA3663FE456808D9ECA3A665DD86 | SHA256:AF65453F571968DD36CD9F6FAEA7161212C2A25B69F8C564AB397CC42B08E18F | |||
| 1116 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Crowd | binary | |
MD5:E7A9793F2E312F449F0B12798A2BCD05 | SHA256:3EDBCD1B6A70C74A157B96071DEE3BB32E199139C660427DE8909D8BA9E0934A | |||
| 2852 | the pixel farm pfclean v51r2 xforce 11.exe | C:\Users\admin\AppData\Local\Temp\Newton.xlam | binary | |
MD5:AF59C96AF7C6A54E399FDF6FC972FB4A | SHA256:C8621CE407829C92AA4424BF70E33DAF854613B981F465369DE92FC94F76A817 | |||
| 1116 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Hospitals | binary | |
MD5:4AF14645BB9ED2139DAFDCB8F994E0B4 | SHA256:C9ED9AC971BFC7D8F03F57867B68B9E1E3155EEF23D283491330B8B6ED6EA099 | |||
| 1116 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Pty | binary | |
MD5:3D2B950D19E273F22A795B3EAB400A0C | SHA256:50D55786CFA8DC92E19139A9A7D40ECBF87F186D90D7FAFDF95492B3B67D2E0D | |||
| 2852 | the pixel farm pfclean v51r2 xforce 11.exe | C:\Users\admin\AppData\Local\Temp\Lopez.xlam | binary | |
MD5:538989B3D21D9B57A951C288D77E95FF | SHA256:3CCC96439D019635F2BF89EF5EA1BA0A0A1F8AF8EE6D0276D3D151AE493D3EA2 | |||
| 1116 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Colleague | binary | |
MD5:EB4759D215832ACD87F492F428FF9B8F | SHA256:087B765E17B3DFE7742956A58EE4145CBA8319DAF699083696FE8C2802C92466 | |||
| 1116 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Thing | binary | |
MD5:1BF294CAE0A717DB75A7A3D2C11A3306 | SHA256:21CFADE5FCB029965E3CB799CCFFA17BFEB87F14AE79A58D30927D04F0EF23F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
41
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
616 | SIHClient.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
616 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
616 | SIHClient.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
616 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
616 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
mwiqoVQmMLqTYRxCcviaXKWDykqQy.mwiqoVQmMLqTYRxCcviaXKWDykqQy |
| unknown |