| File name: | 64764096-B173-1905-B039-AA3FEBD1A8B4.eml.zip |
| Full analysis: | https://app.any.run/tasks/bec95e65-2ee8-4317-bef4-f9ae9b301523 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | October 20, 2020, 11:18:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 572E2667DAA27A5234EDD9399BA4A4DF |
| SHA1: | 04924FACAF7D7CF57B87D379EE63EB2CA7DCA80F |
| SHA256: | EC4B0728C3699C4B2A1E15025B88EFB377EA66045A66D9ECD3CB4213D6FBAD03 |
| SSDEEP: | 24576:k0TeK0vX/eQM9IYPQX56GpdtpUgjIO1rlLhRCOnnLt:heLP/Y9Iqy5npUArlrPnR |
MALICIOUS
Application was dropped or rewritten from another process
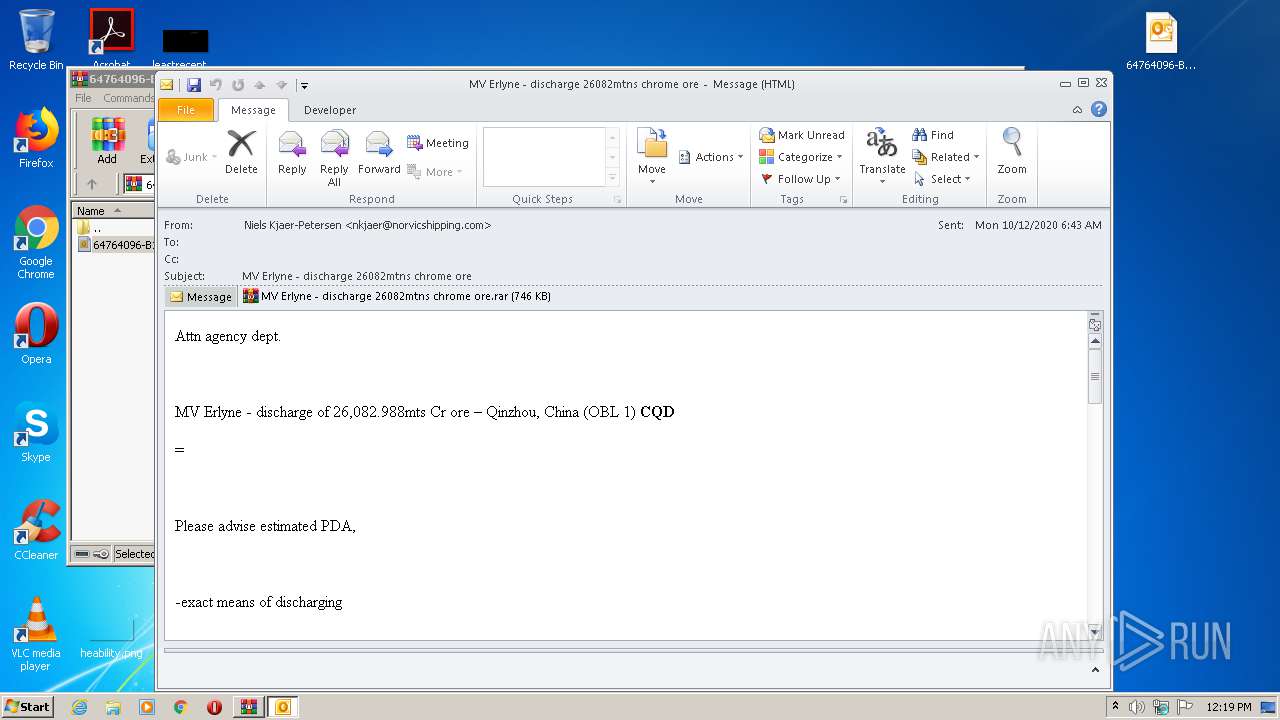
- MV Erlyne - discharge 26082mtns chrome ore.exe (PID: 2572)
- MV Erlyne - discharge 26082mtns chrome ore.exe (PID: 2888)
AGENTTESLA was detected
- MV Erlyne - discharge 26082mtns chrome ore.exe (PID: 2888)
Actions looks like stealing of personal data
- MV Erlyne - discharge 26082mtns chrome ore.exe (PID: 2888)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2916)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2916)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2528)
Application launched itself
- MV Erlyne - discharge 26082mtns chrome ore.exe (PID: 2572)
INFO
Manual execution by user
- OUTLOOK.EXE (PID: 2916)
- WinRAR.exe (PID: 2528)
- MV Erlyne - discharge 26082mtns chrome ore.exe (PID: 2572)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2832)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:10:12 09:32:26 |
| ZipCRC: | 0x7d12c471 |
| ZipCompressedSize: | 826317 |
| ZipUncompressedSize: | 1074013 |
| ZipFileName: | 64764096-B173-1905-B039-AA3FEBD1A8B4.eml |
Total processes
45
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2528 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\MV Erlyne - discharge 26082mtns chrome ore.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\Desktop\MV Erlyne - discharge 26082mtns chrome ore.exe" | C:\Users\admin\Desktop\MV Erlyne - discharge 26082mtns chrome ore.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Toblerone Exit code: 0 Version: 15.0.0.0 Modules
| |||||||||||||||
| 2832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\64764096-B173-1905-B039-AA3FEBD1A8B4.eml.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2888 | "{path}" | C:\Users\admin\Desktop\MV Erlyne - discharge 26082mtns chrome ore.exe | MV Erlyne - discharge 26082mtns chrome ore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Toblerone Exit code: 0 Version: 15.0.0.0 Modules
| |||||||||||||||
| 2916 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\64764096-B173-1905-B039-AA3FEBD1A8B4.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
2 012
Read events
1 469
Write events
524
Delete events
19
Modification events
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\64764096-B173-1905-B039-AA3FEBD1A8B4.eml.zip | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2916) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
Executable files
1
Suspicious files
2
Text files
29
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF428.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpF63D.tmp | — | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\IGR5GZO2\MV Erlyne - discharge 26082mtns chrome ore (2).rar\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2832.7103\64764096-B173-1905-B039-AA3FEBD1A8B4.eml | eml | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D3C070C5.dat | image | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_8FAC361743CD384294F34D986F0B6ED4.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{7B33DBCC-E03D-4D80-9C7B-4C8E3779B089}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_408ACDCFD048444592830BB30DB21E58.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2916 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2916 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2888 | MV Erlyne - discharge 26082mtns chrome ore.exe | 136.243.28.2:587 | mail.provil.gr | Hetzner Online GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
mail.provil.gr |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2888 | MV Erlyne - discharge 26082mtns chrome ore.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |