| File name: | NanoCore.exe |
| Full analysis: | https://app.any.run/tasks/6fc56517-6e2a-4e07-a93e-3e040a7c445f |
| Verdict: | Malicious activity |
| Threats: | NanoCore is a Remote Access Trojan or RAT. This malware is highly customizable with plugins which allow attackers to tailor its functionality to their needs. Nanocore is created with the .NET framework and it’s available for purchase for just $25 from its “official” website. |
| Analysis date: | March 09, 2025, 16:07:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 4 sections |
| MD5: | 1728ACC244115CBAFD3B810277D2E321 |
| SHA1: | BE64732F46C8A26A5BBF9D7F69C7F031B2C5180B |
| SHA256: | EC359F50CA15395F273899C0FF7C0CD87AB5C2E23FDCFC6C72FEDC0097161D4B |
| SSDEEP: | 24576:d7dOT1b7eAJzjSTUd+21nm3kEvpqZ0vSxmfexX6shz07DTl/uz5:d7dqVw2+2KkS4PmGX6og7w |
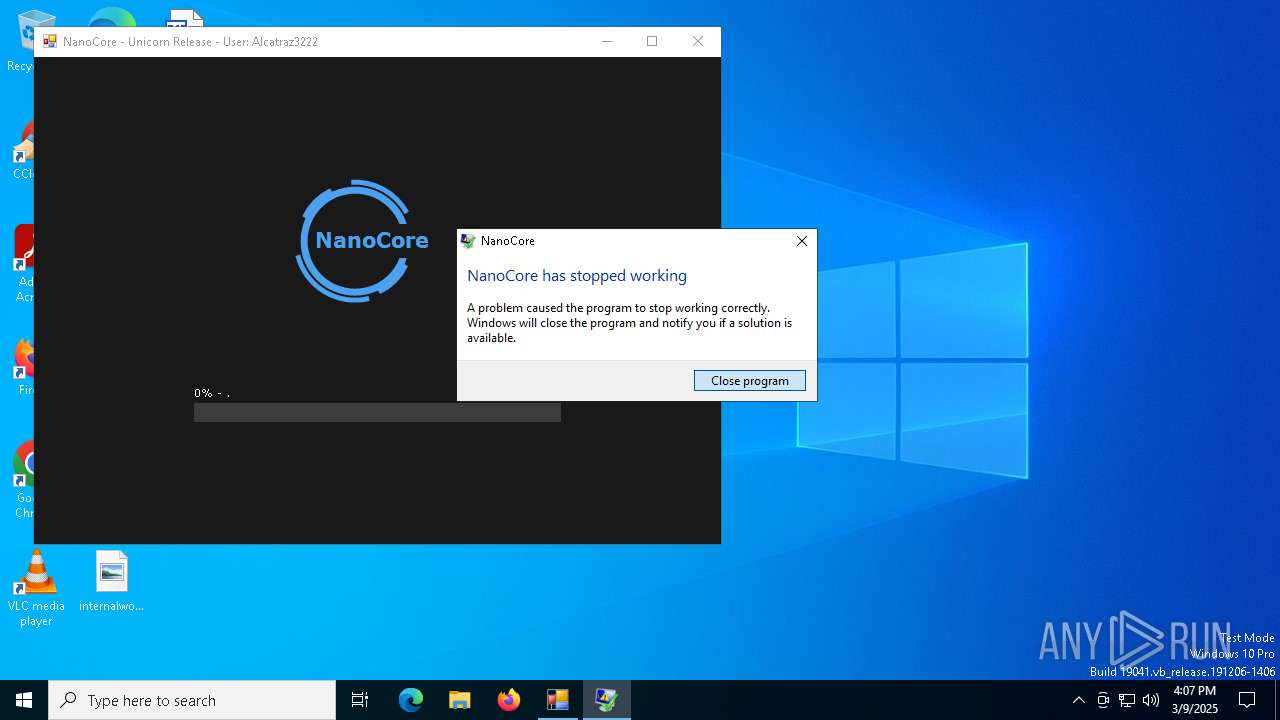
MALICIOUS
NANOCORE mutex has been found
- NanoCore.exe (PID: 2656)
SUSPICIOUS
Reads the date of Windows installation
- dw20.exe (PID: 1628)
INFO
Checks supported languages
- NanoCore.exe (PID: 2656)
- dw20.exe (PID: 1628)
Checks proxy server information
- dw20.exe (PID: 1628)
- BackgroundTransferHost.exe (PID: 7700)
Reads the software policy settings
- dw20.exe (PID: 1628)
- BackgroundTransferHost.exe (PID: 7700)
Reads the computer name
- NanoCore.exe (PID: 2656)
- dw20.exe (PID: 1628)
Creates files or folders in the user directory
- dw20.exe (PID: 1628)
- BackgroundTransferHost.exe (PID: 7700)
Reads the machine GUID from the registry
- dw20.exe (PID: 1628)
- NanoCore.exe (PID: 2656)
Creates files in the program directory
- dw20.exe (PID: 1628)
Reads CPU info
- dw20.exe (PID: 1628)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 7408)
- BackgroundTransferHost.exe (PID: 7892)
- BackgroundTransferHost.exe (PID: 8136)
- BackgroundTransferHost.exe (PID: 7036)
- Taskmgr.exe (PID: 2504)
- BackgroundTransferHost.exe (PID: 7700)
Reads product name
- dw20.exe (PID: 1628)
Process checks computer location settings
- dw20.exe (PID: 1628)
Reads Environment values
- dw20.exe (PID: 1628)
.NET Reactor protector has been detected
- NanoCore.exe (PID: 2656)
Application launched itself
- firefox.exe (PID: 3884)
- firefox.exe (PID: 7952)
Manual execution by a user
- firefox.exe (PID: 7952)
- Taskmgr.exe (PID: 2504)
- Taskmgr.exe (PID: 7144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (45.1) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (19.2) |
| .exe | | | Win64 Executable (generic) (17) |
| .scr | | | Windows screen saver (8) |
| .dll | | | Win32 Dynamic Link Library (generic) (4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:07:01 07:55:53+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1421824 |
| InitializedDataSize: | 19968 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15d0ce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.2.0 |
| ProductVersionNumber: | 1.2.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | NanoCore |
| FileVersion: | 1.2.2.0 |
| InternalName: | NanoCore.exe |
| LegalCopyright: | |
| OriginalFileName: | NanoCore.exe |
| ProductVersion: | 1.2.2.0 |
| AssemblyVersion: | 1.2.2.0 |
Total processes
159
Monitored processes
23
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4924 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 2716 -prefMapHandle 4848 -prefsLen 38053 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b2b30a15-f2f4-437b-947e-638bd73bebb9} 3884 "\\.\pipe\gecko-crash-server-pipe.3884" 1646fef3710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1116 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
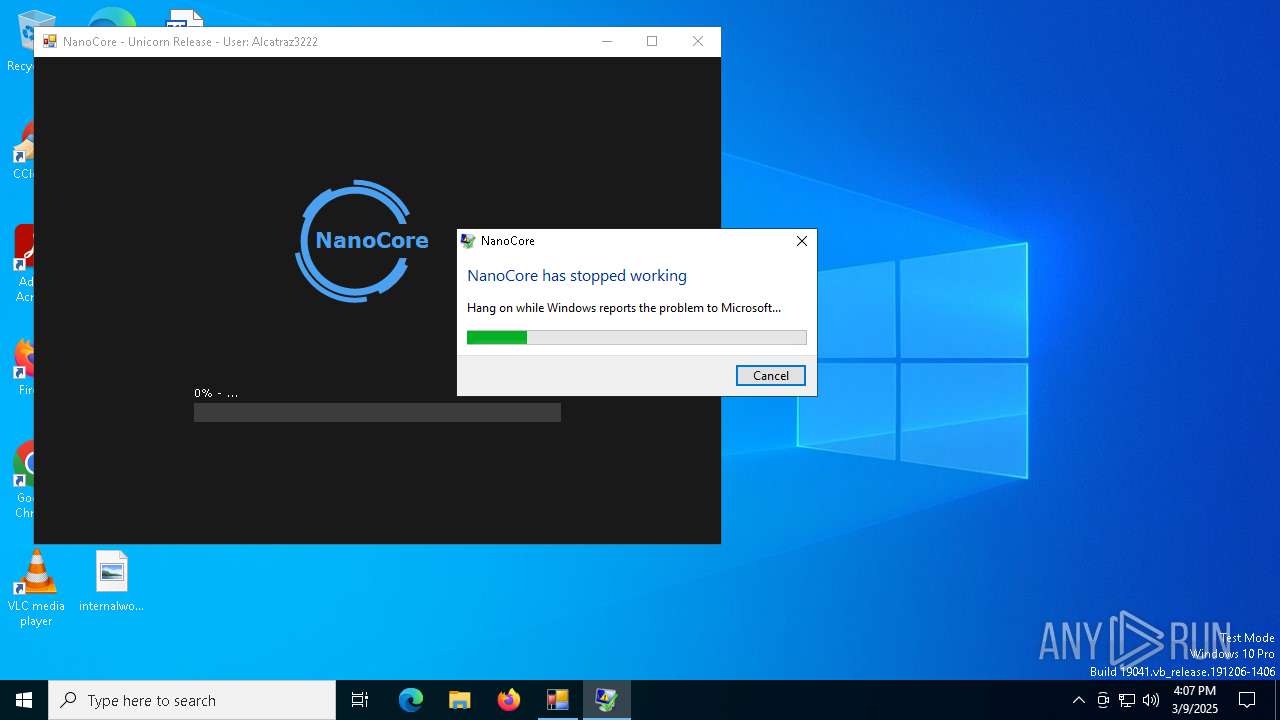
| 1628 | dw20.exe -x -s 1012 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | NanoCore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 2504 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4300 -childID 2 -isForBrowser -prefsHandle 4296 -prefMapHandle 4292 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {2f29360e-5fa1-45ed-acf9-fdf1e802e9c5} 3884 "\\.\pipe\gecko-crash-server-pipe.3884" 1646ef12850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2656 | "C:\Users\admin\AppData\Local\Temp\NanoCore.exe" | C:\Users\admin\AppData\Local\Temp\NanoCore.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: NanoCore Exit code: 3762507597 Version: 1.2.2.0 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5168 -childID 5 -isForBrowser -prefsHandle 5260 -prefMapHandle 5052 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9aaf9ea7-370e-49c2-9988-fb51a68936c8} 3884 "\\.\pipe\gecko-crash-server-pipe.3884" 16470d03150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3884 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5344 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1904 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1836 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {2ac4f004-8668-46ff-8621-87b0ee14ffcd} 3884 "\\.\pipe\gecko-crash-server-pipe.3884" 16467af1510 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
18 685
Read events
18 666
Write events
18
Delete events
1
Modification events
| (PID) Process: | (1628) dw20.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | ClockTimeSeconds |
Value: C0BCCD6700000000 | |||
| (PID) Process: | (1628) dw20.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | TickCount |
Value: C5C2100000000000 | |||
| (PID) Process: | (7408) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7408) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7408) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7700) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7700) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7700) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7892) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7892) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
0
Suspicious files
133
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1628 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_nanocore.exe_d034d261e85a445b68a08d6bca47deaf282fb_00000000_ada6625d-9ed0-4769-bfef-f33ecb8219f2\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7700 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\0a8cb8f0-64c9-4623-8101-55cec910cbb9.down_data | — | |
MD5:— | SHA256:— | |||
| 3884 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 1628 | dw20.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:3B5E0BD6640456A749D9155E6C135727 | SHA256:C362A3D2B661C6066A02FC169FAAA1976C2F6160DA5837C7E68B7E0F67B794ED | |||
| 1628 | dw20.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:680B0331A3CC8FCCE16367586EC7A721 | SHA256:19F1B5D2C7F62663C14D97578411DC610E5F33E6CE4165977314442435F15305 | |||
| 1628 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC074.tmp.xml | xml | |
MD5:5541153F561A09BE6F1AC837FF762128 | SHA256:05158E7B8F595D5E8FBD657AB5407E6364BF38C8023D55A12544D90E43E352CF | |||
| 3884 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7700 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\0a8cb8f0-64c9-4623-8101-55cec910cbb9.3a73a118-fbba-4109-9a0b-4a27cd9231fc.down_meta | binary | |
MD5:6E5B1AEBF9E282267A7C1EDDFB4023ED | SHA256:E27FFB5AA5BB60C84446AFB509E864B587207E6646D22B058DD49EBBE53869E1 | |||
| 7700 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:3F96F3F8DAC035F742D841915BB61943 | SHA256:7CB5D30E65B7747C5FE0AAC40D98AFF146136DD5D35DD8ABBB1AC45491278BB5 | |||
| 3884 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
106
DNS requests
109
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1628 | dw20.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7700 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3884 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
3884 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1052 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
3884 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5800 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3884 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1628 | dw20.exe | 20.189.173.20:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1628 | dw20.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1628 | dw20.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |