| File name: | file |
| Full analysis: | https://app.any.run/tasks/f2d0d82e-6102-4eda-bee4-56b89e0d4f67 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 06, 2022, 00:09:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InnoSetup self-extracting archive |
| MD5: | 0D075C0A31D92DE7F67FD3CC10526E89 |
| SHA1: | 261D82DECD3192CDD675E2E027C5D4436572A5F1 |
| SHA256: | EC3190BEE8B37B12A46AEB60C273F3D1397D2E739FAB71AA2A24D03FFA3EFBAC |
| SSDEEP: | 98304:wOa+3ngx1WUVTgKbOTMIkSvnnWl/nNmGRdcwb/sgoN2c4FrNppy2LcY/f:NaEngv1f4MQnn+/4GMwD3oNx4pNLcY/f |
MALICIOUS
Drops the executable file immediately after the start
- is-CD75O.tmp (PID: 468)
- Ddyol.exe (PID: 3680)
- PrintFolders.exe (PID: 3004)
- gntuud.exe (PID: 2716)
G-cleaner network activity is detected
- PrintFolders.exe (PID: 3004)
Application was dropped or rewritten from another process
- Ddyol.exe (PID: 3680)
- vOEdAhiYZXN.exe (PID: 2852)
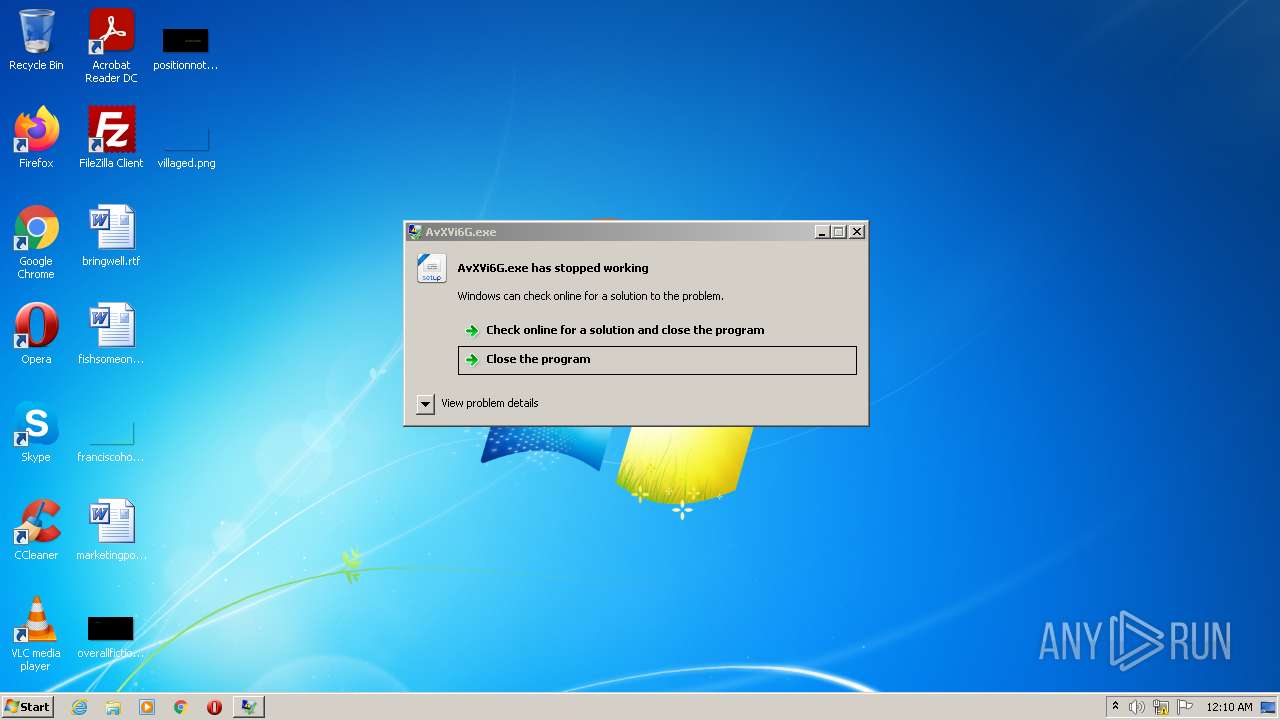
- AvXVi6G.exe (PID: 2984)
- Dsr7Js4o.exe (PID: 664)
- gntuud.exe (PID: 2716)
- gntuud.exe (PID: 2056)
- gntuud.exe (PID: 2148)
Steals credentials from Web Browsers
- Ddyol.exe (PID: 3680)
VIDAR was detected
- Ddyol.exe (PID: 3680)
Loads dropped or rewritten executable
- Ddyol.exe (PID: 3680)
- rundll32.exe (PID: 3656)
Uses Task Scheduler to run other applications
- gntuud.exe (PID: 2716)
Changes the autorun value in the registry
- gntuud.exe (PID: 2716)
Changes the Startup folder
- gntuud.exe (PID: 2716)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2920)
AMADEY was detected
- gntuud.exe (PID: 2716)
Connects to the CnC server
- rundll32.exe (PID: 3656)
SUSPICIOUS
Executable content was dropped or overwritten
- is-CD75O.tmp (PID: 468)
- Ddyol.exe (PID: 3680)
- gntuud.exe (PID: 2716)
- PrintFolders.exe (PID: 3004)
Drops a file with too old compile date
- is-CD75O.tmp (PID: 468)
- gntuud.exe (PID: 2716)
Creates a directory in Program Files
- is-CD75O.tmp (PID: 468)
Reads Microsoft Outlook installation path
- PrintFolders.exe (PID: 3004)
Reads the Internet Settings
- PrintFolders.exe (PID: 3004)
- Ddyol.exe (PID: 3680)
- Dsr7Js4o.exe (PID: 664)
- gntuud.exe (PID: 2716)
Reads the Windows owner or organization settings
- is-CD75O.tmp (PID: 468)
Checks Windows Trust Settings
- Ddyol.exe (PID: 3680)
Reads settings of System Certificates
- Ddyol.exe (PID: 3680)
Connects to the server without a host name
- PrintFolders.exe (PID: 3004)
- Ddyol.exe (PID: 3680)
- gntuud.exe (PID: 2716)
- rundll32.exe (PID: 3656)
Reads browser cookies
- Ddyol.exe (PID: 3680)
Reads security settings of Internet Explorer
- Ddyol.exe (PID: 3680)
Starts CMD.EXE for commands execution
- Ddyol.exe (PID: 3680)
- PrintFolders.exe (PID: 3004)
Starts itself from another location
- Dsr7Js4o.exe (PID: 664)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3996)
Uses TASKKILL.EXE to terminate process
- cmd.exe (PID: 3996)
Executes via Task Scheduler
- gntuud.exe (PID: 2056)
- gntuud.exe (PID: 2148)
Uses RUNDLL32.EXE to load library
- gntuud.exe (PID: 2716)
Process requests binary or script from the Internet
- gntuud.exe (PID: 2716)
Searches for installed software
- Ddyol.exe (PID: 3680)
Starts CMD.EXE for self-deleting
- Ddyol.exe (PID: 3680)
INFO
Checks supported languages
- file.exe (PID: 3544)
- is-CD75O.tmp (PID: 468)
- PrintFolders.exe (PID: 3004)
- Ddyol.exe (PID: 3680)
- vOEdAhiYZXN.exe (PID: 2852)
- AvXVi6G.exe (PID: 2984)
- Dsr7Js4o.exe (PID: 664)
- gntuud.exe (PID: 2716)
- gntuud.exe (PID: 2056)
- gntuud.exe (PID: 2148)
Creates a file in a temporary directory
- file.exe (PID: 3544)
- is-CD75O.tmp (PID: 468)
- Dsr7Js4o.exe (PID: 664)
- gntuud.exe (PID: 2716)
Creates a software uninstall entry
- is-CD75O.tmp (PID: 468)
Application was dropped or rewritten from another process
- is-CD75O.tmp (PID: 468)
Reads the computer name
- PrintFolders.exe (PID: 3004)
- is-CD75O.tmp (PID: 468)
- Ddyol.exe (PID: 3680)
- Dsr7Js4o.exe (PID: 664)
- gntuud.exe (PID: 2716)
Creates files in the program directory
- is-CD75O.tmp (PID: 468)
- Ddyol.exe (PID: 3680)
Loads dropped or rewritten executable
- is-CD75O.tmp (PID: 468)
Checks proxy server information
- PrintFolders.exe (PID: 3004)
- Ddyol.exe (PID: 3680)
- gntuud.exe (PID: 2716)
Drops a file that was compiled in debug mode
- is-CD75O.tmp (PID: 468)
- Ddyol.exe (PID: 3680)
- PrintFolders.exe (PID: 3004)
Reads Environment values
- Ddyol.exe (PID: 3680)
Reads product name
- Ddyol.exe (PID: 3680)
Reads CPU info
- Ddyol.exe (PID: 3680)
Reads the CPU's name
- Ddyol.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (82.8) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.7) |
| .exe | | | Win32 Executable (generic) (3.4) |
| .exe | | | Generic Win/DOS Executable (1.5) |
| .exe | | | DOS Executable Generic (1.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 1992-Jun-19 22:22:17 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup: http://www.innosetup.com |
| CompanyName: | - |
| FileDescription: | PrintFolders Setup |
| FileVersion: | - |
| InternalName: | - |
| OriginalFilename: | - |
| ProductName: | - |
| ProductVersion: | - |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 8 |
| TimeDateStamp: | 1992-Jun-19 22:22:17 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 4096 | 36352 | 36352 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60044 |
DATA | 40960 | 584 | 1024 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.72043 |
BSS | 45056 | 3684 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 49152 | 2248 | 2560 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.2508 |
.tls | 53248 | 8 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 57344 | 24 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.199108 |
.reloc | 61440 | 2156 | 0 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | |
.rsrc | 65536 | 167124 | 167424 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 5.27927 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.39383 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
2 | 5.94971 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.5357 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.48577 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.25469 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.46372 | 21640 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 5.3545 | 38056 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 4.90318 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
4089 | 3.21823 | 754 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4090 | 3.31515 | 780 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
advapi32.dll (#2) |
comctl32.dll |
kernel32.dll |
kernel32.dll (#2) |
oleaut32.dll |
user32.dll |
user32.dll (#2) |
Total processes
62
Monitored processes
17
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | "C:\Users\admin\AppData\Local\Temp\is-OOKJL.tmp\is-CD75O.tmp" /SL4 $30138 "C:\Users\admin\AppData\Local\Temp\file.exe" 3759280 208896 | C:\Users\admin\AppData\Local\Temp\is-OOKJL.tmp\is-CD75O.tmp | file.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.42.0.0 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Roaming\hjFSUTgu\Dsr7Js4o.exe" | C:\Users\admin\AppData\Roaming\hjFSUTgu\Dsr7Js4o.exe | — | PrintFolders.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1236 | taskkill /im "PrintFolders.exe" /f | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe | C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2064 | timeout /t 6 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe | C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2716 | "C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe" | C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe | Dsr7Js4o.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2852 | C:\Users\admin\AppData\Roaming\{e29ac6c0-7037-11de-816d-806e6f6e6963}\vOEdAhiYZXN.exe | — | PrintFolders.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2920 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 1 /TN gntuud.exe /TR "C:\Users\admin\AppData\Local\Temp\ecaac49691\gntuud.exe" /F | C:\Windows\System32\schtasks.exe | — | gntuud.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2984 | "C:\Users\admin\AppData\Roaming\d0gMfzJK94\AvXVi6G.exe" | C:\Users\admin\AppData\Roaming\d0gMfzJK94\AvXVi6G.exe | PrintFolders.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 085
Read events
8 972
Write events
111
Delete events
2
Modification events
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_CURRENT_USER\Software\Atzpoint Software\PrintFolders |
| Operation: | write | Name: | Language |
Value: eng | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.1.2-beta | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\PrintFolders | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\PrintFolders\ | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: PrintFolders | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | DisplayName |
Value: PrintFolders 3.100 | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\PrintFolders\PrintFolders.exe | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\PrintFolders\unins000.exe" | |||
| (PID) Process: | (468) is-CD75O.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{C2483D7A-78F2-476F-86FF-6B2EA9310854}}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\PrintFolders\unins000.exe" /SILENT | |||
Executable files
25
Suspicious files
10
Text files
7
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 468 | is-CD75O.tmp | C:\Program Files\PrintFolders\is-AAI4B.tmp | — | |
MD5:— | SHA256:— | |||
| 468 | is-CD75O.tmp | C:\Program Files\PrintFolders\PrintFolders.exe | — | |
MD5:— | SHA256:— | |||
| 3004 | PrintFolders.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\fuckingdllENCR[1].dll | binary | |
MD5:— | SHA256:— | |||
| 468 | is-CD75O.tmp | C:\Program Files\PrintFolders\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 3004 | PrintFolders.exe | C:\Users\admin\AppData\Roaming\3dsmBNRu\Ddyol.exe | executable | |
MD5:— | SHA256:— | |||
| 468 | is-CD75O.tmp | C:\Program Files\PrintFolders\unins000.dat | dat | |
MD5:— | SHA256:— | |||
| 3544 | file.exe | C:\Users\admin\AppData\Local\Temp\is-OOKJL.tmp\is-CD75O.tmp | executable | |
MD5:— | SHA256:— | |||
| 468 | is-CD75O.tmp | C:\Program Files\PrintFolders\is-Q3PCM.tmp | executable | |
MD5:— | SHA256:— | |||
| 3004 | PrintFolders.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ping[1].htm | text | |
MD5:— | SHA256:— | |||
| 3004 | PrintFolders.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MIXTWO[1].file | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
12
DNS requests
3
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3004 | PrintFolders.exe | GET | 200 | 107.182.129.235:80 | http://107.182.129.235/storage/extension.php | US | binary | 92.0 Kb | malicious |
3004 | PrintFolders.exe | GET | 200 | 171.22.30.106:80 | http://171.22.30.106/library.php | GB | executable | 386 Kb | malicious |
3680 | Ddyol.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
3004 | PrintFolders.exe | GET | 200 | 171.22.30.106:80 | http://171.22.30.106/library.php | GB | executable | 3.78 Mb | malicious |
3004 | PrintFolders.exe | GET | 200 | 107.182.129.235:80 | http://107.182.129.235/storage/ping.php | US | text | 17 b | malicious |
3680 | Ddyol.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
3680 | Ddyol.exe | GET | 200 | 195.201.250.87:80 | http://195.201.250.87/update.zip | DE | compressed | 3.47 Mb | malicious |
3004 | PrintFolders.exe | GET | 200 | 171.22.30.106:80 | http://171.22.30.106/library.php | GB | executable | 615 Kb | malicious |
3680 | Ddyol.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQCxJlJbiuuimg%3D%3D | US | der | 1.74 Kb | whitelisted |
3680 | Ddyol.exe | GET | 200 | 195.201.250.87:80 | http://195.201.250.87/1787 | DE | text | 110 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3004 | PrintFolders.exe | 45.139.105.171:80 | — | Xdeer Limited | BG | malicious |
3680 | Ddyol.exe | 195.201.250.87:80 | — | Hetzner Online GmbH | DE | malicious |
2716 | gntuud.exe | 77.73.133.72:80 | — | Partner LLC | KZ | malicious |
3656 | rundll32.exe | 77.73.133.72:80 | — | Partner LLC | KZ | malicious |
3680 | Ddyol.exe | 8.241.9.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
3680 | Ddyol.exe | 192.124.249.24:80 | ocsp.godaddy.com | SUCURI-SEC | US | suspicious |
3004 | PrintFolders.exe | 107.182.129.235:80 | — | Delis LLC | US | malicious |
3004 | PrintFolders.exe | 171.22.30.106:80 | — | Delis LLC | US | malicious |
3680 | Ddyol.exe | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t.me |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3004 | PrintFolders.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3004 | PrintFolders.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
3004 | PrintFolders.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3680 | Ddyol.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host ZIP Request |
3004 | PrintFolders.exe | Misc activity | ET INFO Packed Executable Download |
3004 | PrintFolders.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
3004 | PrintFolders.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3680 | Ddyol.exe | A Network Trojan was detected | ET TROJAN Arkei/Vidar/Mars Stealer Variant |
3004 | PrintFolders.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3004 | PrintFolders.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
2 ETPRO signatures available at the full report