| File name: | ebb7fec4ddd5764b944028ca32c453346d00503fffc5f09d60e40d31e8de80a3 |
| Full analysis: | https://app.any.run/tasks/e4350931-c432-441a-a7ba-780bea857037 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | April 29, 2025, 04:33:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 37B14C53735862A063E6A82CCACA42E3 |
| SHA1: | 9C09EC38963FDFC093A1E4DCFA02A3B1D73EBD16 |
| SHA256: | EBB7FEC4DDD5764B944028CA32C453346D00503FFFC5F09D60E40D31E8DE80A3 |
| SSDEEP: | 49152:CNX9/6v83gJgyMZ15es9R0K41pahEEHy/KLku8IB5ez5r72vmmo5DhzGkSR+5FJF:6XEv83lyMPjR0Kcpahku8aY+W557+6rF |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5680)
PURECRYPTER has been detected (YARA)
- Order V548780.exe (PID: 6872)
Create files in the Startup directory
- Order V548780.exe (PID: 6872)
AGENTTESLA has been detected (YARA)
- InstallUtil.exe (PID: 812)
Actions looks like stealing of personal data
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
SUSPICIOUS
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 2136)
- cmd.exe (PID: 6584)
Starts CMD.EXE for commands execution
- Order V548780.exe (PID: 6872)
- WinRAR.exe (PID: 5680)
- main.exe (PID: 6136)
Reads security settings of Internet Explorer
- Order V548780.exe (PID: 6872)
- WinRAR.exe (PID: 5680)
- main.exe (PID: 6136)
Base64-obfuscated command line is found
- Order V548780.exe (PID: 6872)
Starts POWERSHELL.EXE for commands execution
- Order V548780.exe (PID: 6872)
BASE64 encoded PowerShell command has been detected
- Order V548780.exe (PID: 6872)
Executable content was dropped or overwritten
- Order V548780.exe (PID: 6872)
Potential Corporate Privacy Violation
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
Process uses IPCONFIG to renew DHCP configuration
- cmd.exe (PID: 6744)
- cmd.exe (PID: 6676)
Checks for external IP
- InstallUtil.exe (PID: 812)
- svchost.exe (PID: 2196)
- InstallUtil.exe (PID: 6576)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2644)
Connects to SMTP port
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5680)
INFO
Reads the computer name
- Order V548780.exe (PID: 6872)
- InstallUtil.exe (PID: 812)
- main.exe (PID: 6136)
- MpCmdRun.exe (PID: 208)
- InstallUtil.exe (PID: 6576)
Manual execution by a user
- Order V548780.exe (PID: 6872)
- InstallUtil.exe (PID: 812)
- wscript.exe (PID: 2644)
- InstallUtil.exe (PID: 6576)
Checks supported languages
- Order V548780.exe (PID: 6872)
- InstallUtil.exe (PID: 812)
- main.exe (PID: 6136)
- MpCmdRun.exe (PID: 208)
- InstallUtil.exe (PID: 6576)
Reads the machine GUID from the registry
- Order V548780.exe (PID: 6872)
- InstallUtil.exe (PID: 812)
- main.exe (PID: 6136)
- InstallUtil.exe (PID: 6576)
Process checks computer location settings
- Order V548780.exe (PID: 6872)
- main.exe (PID: 6136)
.NET Reactor protector has been detected
- Order V548780.exe (PID: 6872)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5324)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5324)
Creates files or folders in the user directory
- Order V548780.exe (PID: 6872)
Auto-launch of the file from Startup directory
- Order V548780.exe (PID: 6872)
Disables trace logs
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
Checks proxy server information
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
- slui.exe (PID: 5072)
Reads the software policy settings
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
- slui.exe (PID: 5072)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5680)
Create files in a temporary directory
- MpCmdRun.exe (PID: 208)
ULTRAVNC has been detected
- InstallUtil.exe (PID: 812)
- InstallUtil.exe (PID: 6576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(812) InstallUtil.exe
Protocolsmtp
Hostmail.iaa-airferight.com
Port25
Usernamemail@iaa-airferight.com
PasswordAsaprocky11
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:29 08:24:02 |
| ZipCRC: | 0x60649e59 |
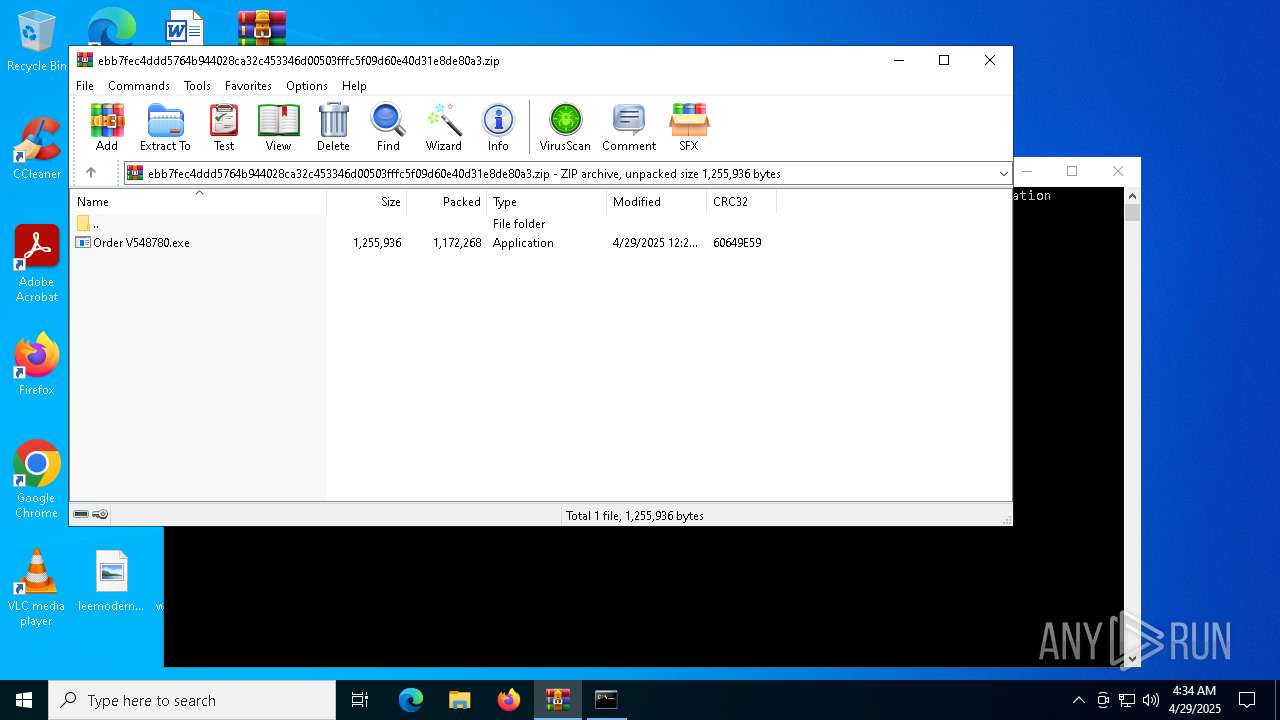
| ZipCompressedSize: | 1172268 |
| ZipUncompressedSize: | 1255936 |
| ZipFileName: | Order V548780.exe |
Total processes
148
Monitored processes
25
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR5680.8177" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
AgentTesla(PID) Process(812) InstallUtil.exe Protocolsmtp Hostmail.iaa-airferight.com Port25 Usernamemail@iaa-airferight.com PasswordAsaprocky11 | |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5680.8177\Rar$Scan58203.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | ipconfig /release | C:\Windows\SysWOW64\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Windows\System32\cmd.exe" /c ipconfig /release | C:\Windows\SysWOW64\cmd.exe | — | Order V548780.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2644 | wscript "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\main.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
20 521
Read events
20 490
Write events
31
Delete events
0
Modification events
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ebb7fec4ddd5764b944028ca32c453346d00503fffc5f09d60e40d31e8de80a3.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6872) Order V548780.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6872) Order V548780.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tmfix1qn.toa.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kagkumtn.vv1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1csrqnhs.w45.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5680.8177\Rar$Scan58203.bat | text | |
MD5:736744647BE3D6D559B3F0E4EB320646 | SHA256:842530B95383BE2D7DDA6CC8FF2FEF49FEB5734F8FE8D8BA7B65C31DBEA36B65 | |||
| 6872 | Order V548780.exe | C:\Users\admin\AppData\Roaming\main.exe | executable | |
MD5:912C123891A7D463E1EA75B86E54F947 | SHA256:51EB3B1C63AEC8D2DFD4A8D3B1032567D81FF493B2DFE5166C35A50E05EBCB06 | |||
| 208 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:3DCE268ACE375AA641ABE20956FD0C78 | SHA256:F499326831954C76559CD2BCF8B99C5AD62D3C53D81CCC6376F6336A14362717 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5680.8177\ebb7fec4ddd5764b944028ca32c453346d00503fffc5f09d60e40d31e8de80a3.zip\Order V548780.exe | executable | |
MD5:912C123891A7D463E1EA75B86E54F947 | SHA256:51EB3B1C63AEC8D2DFD4A8D3B1032567D81FF493B2DFE5166C35A50E05EBCB06 | |||
| 5324 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:44735E0648830E139F526594EF5343D7 | SHA256:C2C362784066CB138CB6772BFEDC20C3C66F991F6EA1D4612916EB2592A49205 | |||
| 5324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pvz0pgpl.1kq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6872 | Order V548780.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\main.vbs | text | |
MD5:712510D093BA2A822DE52C8020555089 | SHA256:51B8A04FC1C9B67BEFEA5C840EE8956EC411F9E8945505C75D18B32585955E49 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
28
DNS requests
7
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6404 | RUXIMICS.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6404 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 172.67.74.152:443 | https://api.ipify.org/ | unknown | text | 12 b | malicious |
— | — | GET | 200 | 104.26.12.205:443 | https://api.ipify.org/ | unknown | text | 12 b | malicious |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6404 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6404 | RUXIMICS.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6404 | RUXIMICS.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
812 | InstallUtil.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
812 | InstallUtil.exe | 46.175.148.58:25 | mail.iaa-airferight.com | Serverius Holding B.V. | NL | malicious |
4920 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6576 | InstallUtil.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
mail.iaa-airferight.com |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
812 | InstallUtil.exe | Potential Corporate Privacy Violation | ET INFO Possible IP Check api.ipify.org |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
812 | InstallUtil.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
6576 | InstallUtil.exe | Potential Corporate Privacy Violation | ET INFO Possible IP Check api.ipify.org |
6576 | InstallUtil.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |