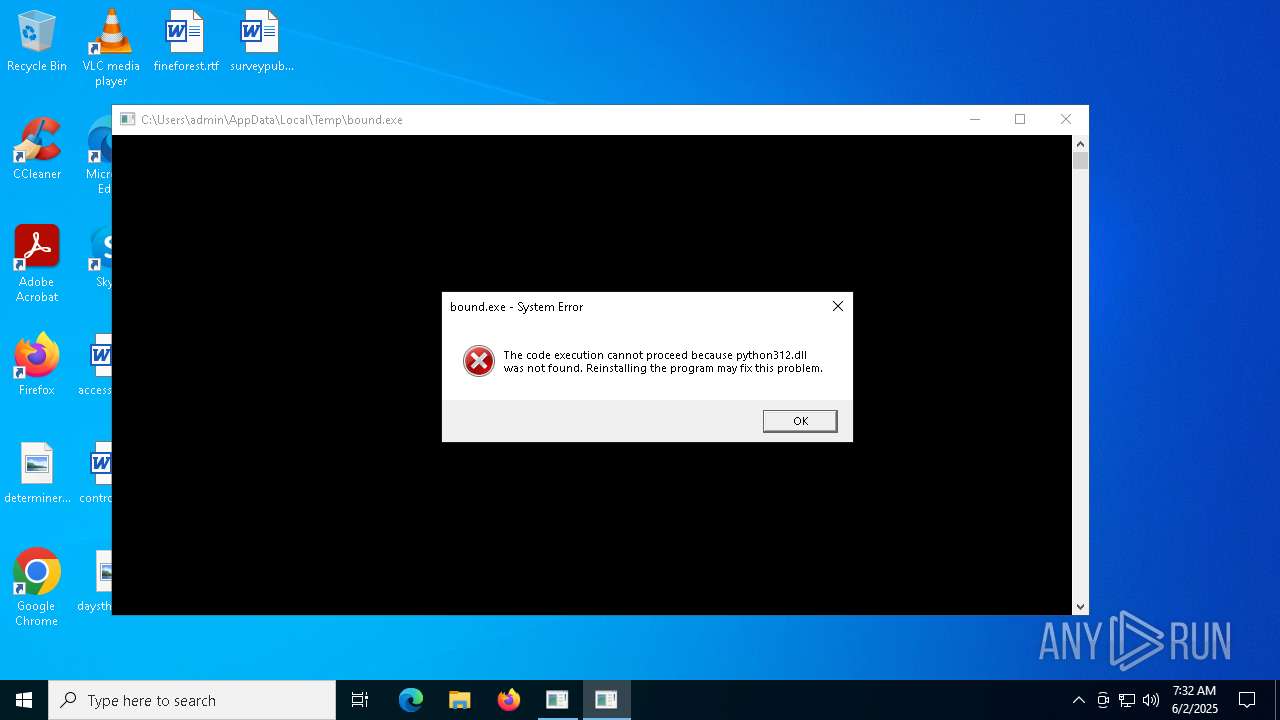
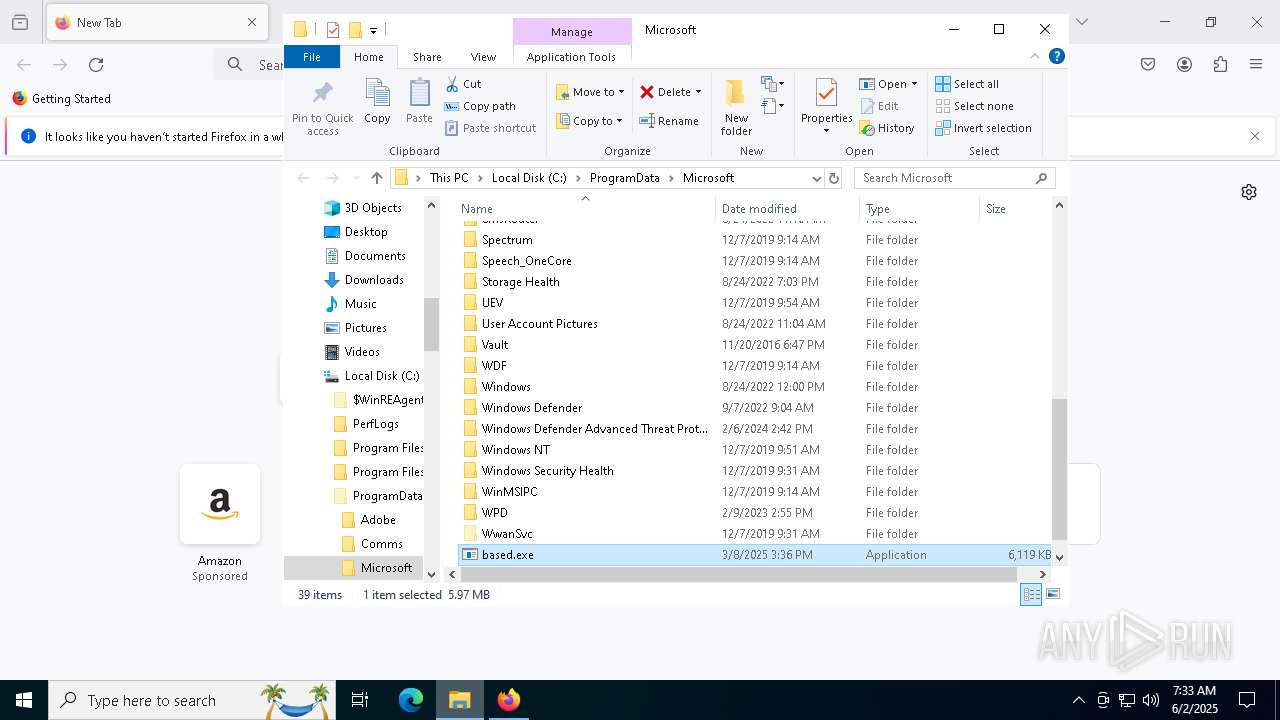
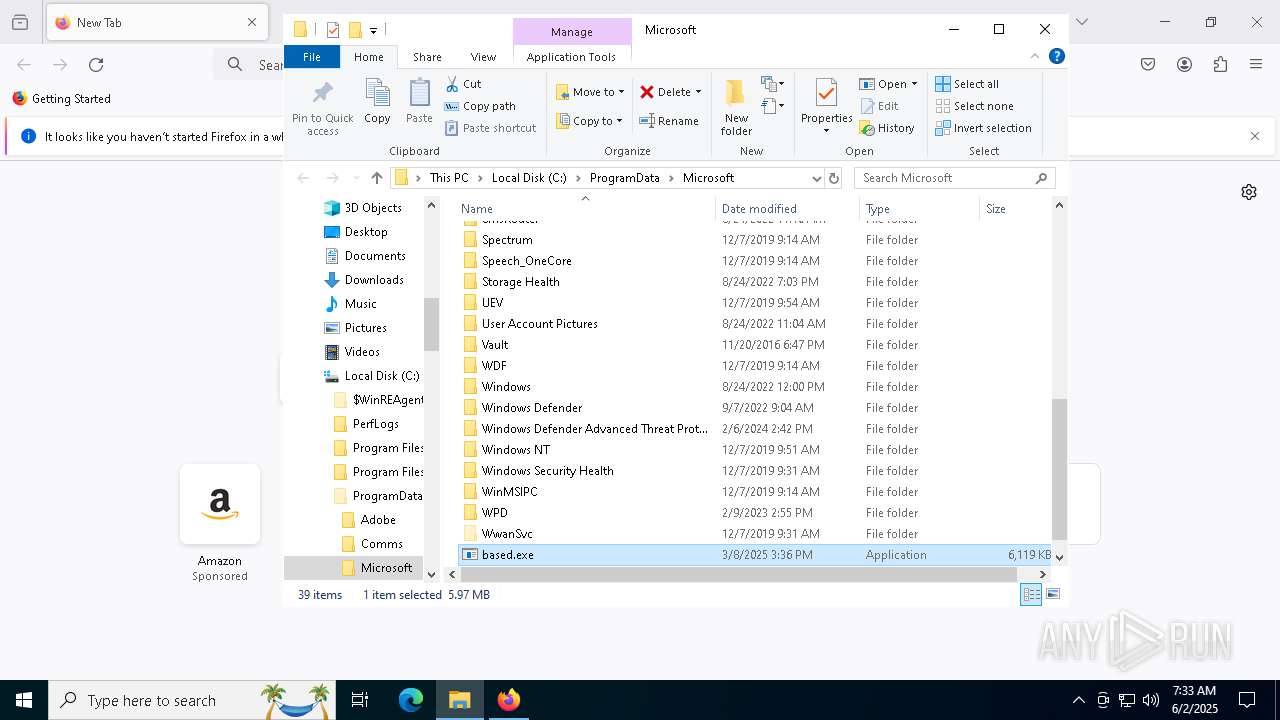
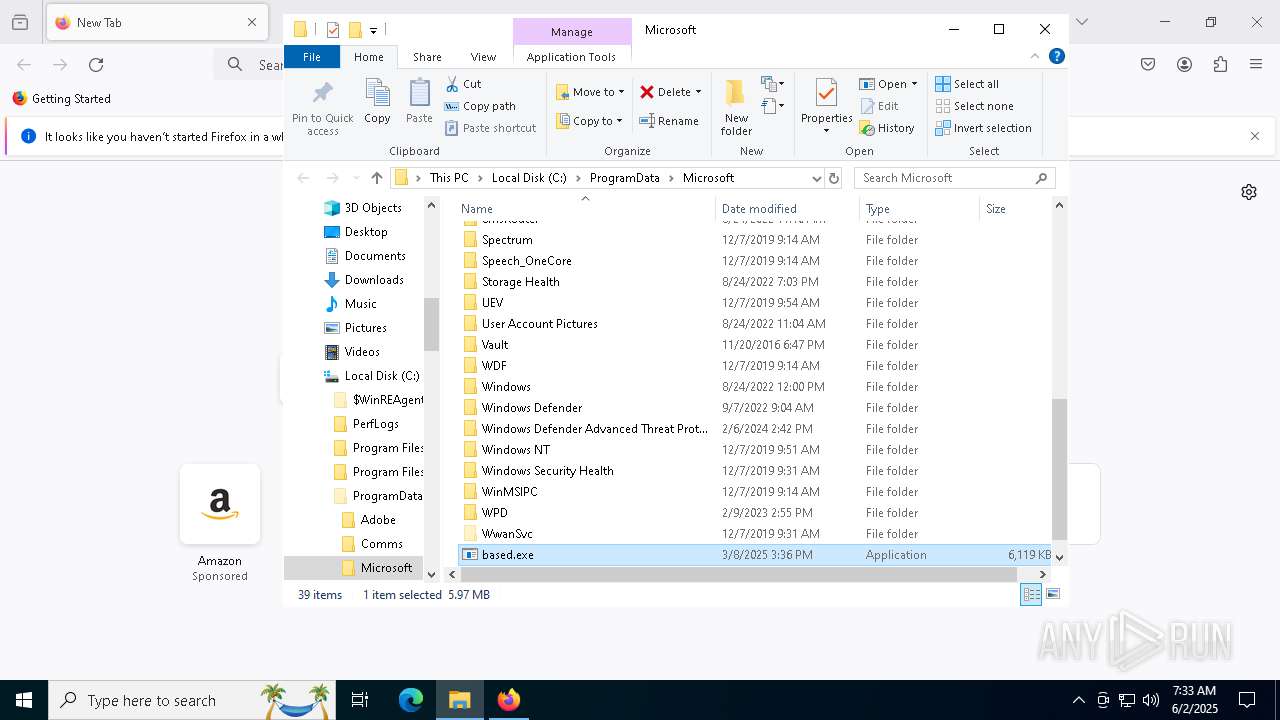
| File name: | crypto-hunter.exe |
| Full analysis: | https://app.any.run/tasks/c1ecae03-ac81-4639-939c-cd5650358ed6 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | June 02, 2025, 07:32:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 88577C82B441B3B34B45C890E563C24E |
| SHA1: | 2EF0A199494AF2E79430DD0A04C34287CF3C3BD0 |
| SHA256: | EBB40D8C4D54109D0589D468D5BC1D6B2AC2AFE44228A72353376E6D2BC61F1A |
| SSDEEP: | 196608:za7d1OCXImjO2fWFM7f0Ediex846CF9MsAhJEFnoVZJ/:ztCYoOeZf0aHv9wJESZp |
MALICIOUS
GENERIC has been found (auto)
- Build.exe (PID: 4652)
- s.exe (PID: 5772)
SFX dropper has been detected
- Build.exe (PID: 4220)
Executing a file with an untrusted certificate
- hacn.exe (PID: 1452)
- based.exe (PID: 4756)
- based.exe (PID: 516)
- hacn.exe (PID: 3100)
- setup.exe (PID: 4652)
- CompPkgSrv.exe (PID: 1852)
- setup.exe (PID: 6620)
- CompPkgSrv.exe (PID: 7344)
Adds path to the Windows Defender exclusion list
- based.exe (PID: 4756)
- cmd.exe (PID: 6252)
- cmd.exe (PID: 4528)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 4272)
Changes Windows Defender settings
- cmd.exe (PID: 6252)
- cmd.exe (PID: 4272)
- cmd.exe (PID: 4528)
- setup.exe (PID: 6620)
Changes settings for real-time protection
- powershell.exe (PID: 7288)
Changes Controlled Folder Access settings
- powershell.exe (PID: 7288)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 7288)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 7288)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 7288)
Actions looks like stealing of personal data
- based.exe (PID: 4756)
Steals credentials from Web Browsers
- based.exe (PID: 4756)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 7288)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 7288)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 4700)
Stealers network behavior
- based.exe (PID: 4756)
BLANKGRABBER has been detected (SURICATA)
- based.exe (PID: 4756)
Adds process to the Windows Defender exclusion list
- setup.exe (PID: 6620)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 7196)
COINMINER has been found (auto)
- setup1.exe (PID: 5548)
Vulnerable driver has been detected
- updater.exe (PID: 7840)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
The process drops C-runtime libraries
- crypto-hunter.exe (PID: 5552)
- based.exe (PID: 516)
- hacn.exe (PID: 1452)
- jB32aoas.exe (PID: 2692)
- CompPkgSrv.exe (PID: 1852)
- setup.exe (PID: 4652)
- svchost.exe (PID: 6192)
Executable content was dropped or overwritten
- crypto-hunter.exe (PID: 5552)
- Build.exe (PID: 4652)
- hacn.exe (PID: 1452)
- based.exe (PID: 516)
- based.exe (PID: 4756)
- jB32aoas.exe (PID: 2692)
- s.exe (PID: 5772)
- CompPkgSrv.exe (PID: 1852)
- svchost.exe (PID: 6192)
- setup.exe (PID: 4652)
- powershell.exe (PID: 6632)
- Dism.exe (PID: 7592)
- Dism.exe (PID: 1812)
- Dism.exe (PID: 7296)
- setup1.exe (PID: 5548)
- setup0.exe (PID: 7980)
- updater.exe (PID: 7840)
- update.exe (PID: 2148)
Process drops python dynamic module
- crypto-hunter.exe (PID: 5552)
- hacn.exe (PID: 1452)
- based.exe (PID: 516)
- jB32aoas.exe (PID: 2692)
- CompPkgSrv.exe (PID: 1852)
- svchost.exe (PID: 6192)
- setup.exe (PID: 4652)
Process drops legitimate windows executable
- crypto-hunter.exe (PID: 5552)
- Build.exe (PID: 4652)
- based.exe (PID: 516)
- hacn.exe (PID: 1452)
- jB32aoas.exe (PID: 2692)
- CompPkgSrv.exe (PID: 1852)
- setup.exe (PID: 4652)
- svchost.exe (PID: 6192)
Application launched itself
- crypto-hunter.exe (PID: 5552)
- Build.exe (PID: 4220)
- based.exe (PID: 516)
- hacn.exe (PID: 1452)
- cmd.exe (PID: 6876)
- jB32aoas.exe (PID: 2692)
- setup.exe (PID: 4652)
- svchost.exe (PID: 6192)
- CompPkgSrv.exe (PID: 1852)
Reads security settings of Internet Explorer
- Build.exe (PID: 4652)
- Build.exe (PID: 4220)
- s.exe (PID: 5772)
Starts CMD.EXE for commands execution
- based.exe (PID: 4756)
- hacn.exe (PID: 3100)
- cmd.exe (PID: 6876)
- svchost.exe (PID: 7892)
- CompPkgSrv.exe (PID: 7344)
Loads Python modules
- hacn.exe (PID: 3100)
- jB32aoas.exe (PID: 6632)
- setup.exe (PID: 6620)
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Found strings related to reading or modifying Windows Defender settings
- based.exe (PID: 4756)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6252)
- cmd.exe (PID: 4528)
- setup.exe (PID: 6620)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6252)
- cmd.exe (PID: 4272)
- cmd.exe (PID: 4528)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 4648)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 1184)
- setup.exe (PID: 6620)
Get information on the list of running processes
- based.exe (PID: 4756)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 6876)
The executable file from the user directory is run by the CMD process
- bound.exe (PID: 3176)
- rar.exe (PID: 5800)
Script disables Windows Defender's IPS
- cmd.exe (PID: 4272)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 4272)
Potential Corporate Privacy Violation
- hacn.exe (PID: 3100)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 3032)
- WMIC.exe (PID: 7752)
- WMIC.exe (PID: 7296)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 8136)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 7960)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7512)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 7520)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 4208)
There is functionality for taking screenshot (YARA)
- hacn.exe (PID: 1452)
- hacn.exe (PID: 3100)
- CompPkgSrv.exe (PID: 1852)
- svchost.exe (PID: 6192)
- setup.exe (PID: 4652)
- setup.exe (PID: 6620)
- CompPkgSrv.exe (PID: 7344)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6640)
- CompPkgSrv.exe (PID: 7344)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7496)
- WMIC.exe (PID: 7636)
Creates file in the systems drive root
- jB32aoas.exe (PID: 6632)
- setup.exe (PID: 6620)
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Checks for external IP
- svchost.exe (PID: 2196)
- based.exe (PID: 4756)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- based.exe (PID: 4756)
- CompPkgSrv.exe (PID: 7344)
The process creates files with name similar to system file names
- s.exe (PID: 5772)
The process checks if current user has admin rights
- setup.exe (PID: 6620)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 236)
Reads the BIOS version
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Reads the date of Windows installation
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 8104)
Script adds exclusion process to Windows Defender
- setup.exe (PID: 6620)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 8036)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 6632)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 4620)
- DismHost.exe (PID: 2124)
- DismHost.exe (PID: 7800)
- DismHost.exe (PID: 7704)
Manipulates environment variables
- powershell.exe (PID: 5452)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 8652)
- powershell.exe (PID: 8472)
Starts SC.EXE for service management
- cmd.exe (PID: 6876)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 8860)
- cmd.exe (PID: 8884)
Stops a currently running service
- sc.exe (PID: 7256)
- sc.exe (PID: 5972)
- sc.exe (PID: 3304)
- sc.exe (PID: 7764)
- sc.exe (PID: 4268)
- sc.exe (PID: 7816)
- sc.exe (PID: 2432)
- sc.exe (PID: 2652)
- sc.exe (PID: 5332)
- sc.exe (PID: 2152)
- sc.exe (PID: 8900)
- sc.exe (PID: 8920)
- sc.exe (PID: 8940)
- sc.exe (PID: 8960)
- sc.exe (PID: 8980)
- sc.exe (PID: 9068)
- sc.exe (PID: 8516)
- sc.exe (PID: 9096)
- sc.exe (PID: 9132)
- sc.exe (PID: 9160)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 5720)
- schtasks.exe (PID: 7512)
The process executes via Task Scheduler
- updater.exe (PID: 7840)
- update.exe (PID: 2148)
Removes files via Powershell
- powershell.exe (PID: 7296)
Possible usage of Discord/Telegram API has been detected (YARA)
- CompPkgSrv.exe (PID: 7344)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 7840)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
INFO
Reads the computer name
- crypto-hunter.exe (PID: 5552)
- Build.exe (PID: 4220)
- Build.exe (PID: 4652)
- based.exe (PID: 516)
- hacn.exe (PID: 1452)
- based.exe (PID: 4756)
- MpCmdRun.exe (PID: 4700)
- hacn.exe (PID: 3100)
- jB32aoas.exe (PID: 2692)
- s.exe (PID: 5772)
- CompPkgSrv.exe (PID: 1852)
- svchost.exe (PID: 6192)
- setup.exe (PID: 4652)
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Checks supported languages
- crypto-hunter.exe (PID: 5552)
- crypto-hunter.exe (PID: 2432)
- hacn.exe (PID: 1452)
- Build.exe (PID: 4220)
- Build.exe (PID: 4652)
- based.exe (PID: 4756)
- based.exe (PID: 516)
- hacn.exe (PID: 3100)
- MpCmdRun.exe (PID: 4700)
- rar.exe (PID: 5800)
- jB32aoas.exe (PID: 2692)
- jB32aoas.exe (PID: 6632)
- s.exe (PID: 5772)
- CompPkgSrv.exe (PID: 1852)
- setup.exe (PID: 4652)
- svchost.exe (PID: 6192)
- setup0.exe (PID: 7980)
- setup1.exe (PID: 5548)
- setup.exe (PID: 6620)
- svchost.exe (PID: 7892)
- CompPkgSrv.exe (PID: 7344)
The sample compiled with english language support
- crypto-hunter.exe (PID: 5552)
- Build.exe (PID: 4652)
- based.exe (PID: 516)
- hacn.exe (PID: 1452)
- based.exe (PID: 4756)
- jB32aoas.exe (PID: 2692)
- CompPkgSrv.exe (PID: 1852)
- svchost.exe (PID: 6192)
- setup.exe (PID: 4652)
- powershell.exe (PID: 6632)
- Dism.exe (PID: 7592)
- Dism.exe (PID: 1812)
- Dism.exe (PID: 7296)
Create files in a temporary directory
- crypto-hunter.exe (PID: 5552)
- based.exe (PID: 516)
- hacn.exe (PID: 1452)
- based.exe (PID: 4756)
- MpCmdRun.exe (PID: 4700)
- rar.exe (PID: 5800)
- jB32aoas.exe (PID: 2692)
- CompPkgSrv.exe (PID: 1852)
- setup.exe (PID: 4652)
- svchost.exe (PID: 6192)
Reads the machine GUID from the registry
- crypto-hunter.exe (PID: 2432)
- based.exe (PID: 4756)
- hacn.exe (PID: 3100)
- rar.exe (PID: 5800)
- jB32aoas.exe (PID: 6632)
- setup.exe (PID: 6620)
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Process checks computer location settings
- Build.exe (PID: 4652)
- Build.exe (PID: 4220)
- s.exe (PID: 5772)
Creates files in the program directory
- Build.exe (PID: 4652)
- hacn.exe (PID: 3100)
- s.exe (PID: 5772)
Checks operating system version
- hacn.exe (PID: 3100)
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6324)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 7268)
- powershell.exe (PID: 8036)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7268)
- powershell.exe (PID: 6324)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 672)
- powershell.exe (PID: 1176)
Checks proxy server information
- hacn.exe (PID: 3100)
- CompPkgSrv.exe (PID: 7344)
PyInstaller has been detected (YARA)
- hacn.exe (PID: 1452)
- based.exe (PID: 516)
- hacn.exe (PID: 3100)
- svchost.exe (PID: 6192)
- CompPkgSrv.exe (PID: 1852)
- setup.exe (PID: 4652)
- setup.exe (PID: 6620)
- CompPkgSrv.exe (PID: 7344)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7520)
- WMIC.exe (PID: 7828)
- WMIC.exe (PID: 3032)
- WMIC.exe (PID: 7496)
- WMIC.exe (PID: 7752)
- WMIC.exe (PID: 7296)
- WMIC.exe (PID: 7636)
Attempting to use instant messaging service
- based.exe (PID: 4756)
- svchost.exe (PID: 2196)
Found Base64 encoded reflection usage via PowerShell (YARA)
- based.exe (PID: 4756)
Reads CPU info
- CompPkgSrv.exe (PID: 7344)
- svchost.exe (PID: 7892)
Changes the registry key values via Powershell
- setup.exe (PID: 6620)
Returns hidden items found within a container (POWERSHELL)
- powershell.exe (PID: 6632)
- powershell.exe (PID: 5452)
- conhost.exe (PID: 8056)
- powershell.exe (PID: 4020)
- conhost.exe (PID: 5248)
- conhost.exe (PID: 7976)
- conhost.exe (PID: 8104)
- conhost.exe (PID: 4892)
- conhost.exe (PID: 4648)
- conhost.exe (PID: 5324)
- conhost.exe (PID: 2124)
- conhost.exe (PID: 7632)
- conhost.exe (PID: 4400)
- conhost.exe (PID: 7888)
- conhost.exe (PID: 4620)
- powershell.exe (PID: 7296)
- conhost.exe (PID: 8660)
- conhost.exe (PID: 8480)
- powershell.exe (PID: 8652)
- conhost.exe (PID: 8868)
- powershell.exe (PID: 8472)
- conhost.exe (PID: 8876)
- conhost.exe (PID: 8620)
- conhost.exe (PID: 6344)
Manual execution by a user
- powershell.exe (PID: 4020)
- powershell.exe (PID: 5452)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 6876)
- schtasks.exe (PID: 3096)
- dialer.exe (PID: 7300)
- schtasks.exe (PID: 7512)
- schtasks.exe (PID: 7260)
- schtasks.exe (PID: 516)
- dialer.exe (PID: 7448)
- schtasks.exe (PID: 5720)
- schtasks.exe (PID: 6640)
- firefox.exe (PID: 7704)
- powershell.exe (PID: 8652)
- cmd.exe (PID: 8860)
- dialer.exe (PID: 9008)
- powershell.exe (PID: 8472)
- dialer.exe (PID: 8480)
- dialer.exe (PID: 8912)
- cmd.exe (PID: 8884)
- schtasks.exe (PID: 8548)
- schtasks.exe (PID: 8660)
- dialer.exe (PID: 8516)
- dialer.exe (PID: 9196)
Returns all items recursively from all subfolders (POWERSHELL)
- powershell.exe (PID: 7296)
Application launched itself
- firefox.exe (PID: 7704)
- firefox.exe (PID: 7268)
The sample compiled with japanese language support
- updater.exe (PID: 7840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:08 15:37:19+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.32 |
| CodeSize: | 165888 |
| InitializedDataSize: | 95232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xafa0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
317
Monitored processes
186
Malicious processes
30
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | powershell -Command "$currentPrincipal = New-Object Security.Principal.WindowsPrincipal([Security.Principal.WindowsIdentity]::GetCurrent()); $currentPrincipal.IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\ProgramData\Microsoft\based.exe" | C:\ProgramData\Microsoft\based.exe | Build.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays NIC MAC information Exit code: 0 Version: 10.0.22621.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | C:\WINDOWS\System32\schtasks.exe /create /f /ru "System" /tn "GoogleUpdateMachineQC" /xml "C:\Users\admin\AppData\Local\Temp\xcogymxilhvf.xml" | C:\Windows\System32\schtasks.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | powershell Get-ItemPropertyValue -Path HKLM:SOFTWARE\Roblox\RobloxStudioBrowser\roblox.com -Name .ROBLOSECURITY | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | powershell Get-ItemPropertyValue -Path HKCU:SOFTWARE\Roblox\RobloxStudioBrowser\roblox.com -Name .ROBLOSECURITY | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | C:\WINDOWS\system32\cmd.exe /c "powershell Get-ItemPropertyValue -Path 'HKLM:System\CurrentControlSet\Control\Session Manager\Environment' -Name PROCESSOR_IDENTIFIER" | C:\Windows\System32\cmd.exe | — | based.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\ProgramData\Microsoft\hacn.exe" | C:\ProgramData\Microsoft\hacn.exe | Build.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2736 -childID 1 -isForBrowser -prefsHandle 2732 -prefMapHandle 2728 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1432 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {bfe8d141-0253-4acc-9eaf-53b9443d60d7} 7268 "\\.\pipe\gecko-crash-server-pipe.7268" 1864a8a2f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | hacn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
123 262
Read events
123 176
Write events
21
Delete events
65
Modification events
| (PID) Process: | (3100) hacn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\GirkinZAvtomatom |
| Operation: | write | Name: | hohols |
Value: True | |||
| (PID) Process: | (5772) s.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (4784) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\PushNotifications |
| Operation: | write | Name: | ToastEnabled |
Value: 0 | |||
| (PID) Process: | (2652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (4620) DismHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Appx\EnterpriseUninstallBlockList |
| Operation: | delete value | Name: | Microsoft.Windows.SecHealthUI_cw5n1h2txyewy |
Value: | |||
| (PID) Process: | (6632) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deprovisioned\Microsoft.Windows.SecHealthUI_cw5n1h2txyewy |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7800) DismHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Appx\EnterpriseUninstallBlockList |
| Operation: | delete value | Name: | Microsoft.Windows.SecHealthUI_cw5n1h2txyewy |
Value: | |||
| (PID) Process: | (7704) DismHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Appx\EnterpriseUninstallBlockList |
| Operation: | delete value | Name: | Microsoft.Windows.SecHealthUI_cw5n1h2txyewy |
Value: | |||
| (PID) Process: | (7300) dialer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\dialerconfig\pid |
| Operation: | write | Name: | svc64 |
Value: 7300 | |||
| (PID) Process: | (7196) ReAgentc.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
611
Suspicious files
188
Text files
178
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5552 | crypto-hunter.exe | C:\Users\admin\AppData\Local\Temp\_MEI55522\libcrypto-1_1.dll | executable | |
MD5:C702B01B9D16F58AD711BF53C0C73203 | SHA256:49363CBA6A25B49A29C6ADD58258E9FEB1C9531460F2716D463AB364D15120E1 | |||
| 5552 | crypto-hunter.exe | C:\Users\admin\AppData\Local\Temp\_MEI55522\_socket.pyd | executable | |
MD5:26A6147D9FFD545FD80C9ED664D66D06 | SHA256:35F18DD2452642CEFB6F883AFC74D560E22AA71BDB6B26E63B076D7EA4246D38 | |||
| 5552 | crypto-hunter.exe | C:\Users\admin\AppData\Local\Temp\_MEI55522\_decimal.pyd | executable | |
MD5:816CBDB21CB715612CA358F0A2688321 | SHA256:45F987F784C7F494C469B5A3938C3A37970AA6BEF4EFAB2D1AC145559CA97508 | |||
| 5552 | crypto-hunter.exe | C:\Users\admin\AppData\Local\Temp\_MEI55522\_hashlib.pyd | executable | |
MD5:47552C83D1890FF91037EECD02B730A2 | SHA256:C3024B95F7F1757D9496C8171EACA5F8B9BB8C7CD7F6077077B5AAA1302B0CA4 | |||
| 4652 | Build.exe | C:\ProgramData\Microsoft\hacn.exe | executable | |
MD5:F07FF81C4C60944A81C97D268DD630A2 | SHA256:C59F20641310E8A1C2A04BEA95458425903A63859C77A8E9C13E2631C6E39800 | |||
| 5552 | crypto-hunter.exe | C:\Users\admin\AppData\Local\Temp\_MEI55522\VCRUNTIME140.dll | executable | |
MD5:870FEA4E961E2FBD00110D3783E529BE | SHA256:76FDB83FDE238226B5BEBAF3392EE562E2CB7CA8D3EF75983BF5F9D6C7119644 | |||
| 5552 | crypto-hunter.exe | C:\Users\admin\AppData\Local\Temp\_MEI55522\_bz2.pyd | executable | |
MD5:13F9AF35BC2CA51E1A0D9F912280832B | SHA256:5CFA3E2D465614A5F7BDBFE8BBBAE012D075BBE83D9561DA3F93F4C19F9B94B3 | |||
| 1452 | hacn.exe | C:\Users\admin\AppData\Local\Temp\_MEI14522\_cffi_backend.cp310-win_amd64.pyd | executable | |
MD5:2BAAA98B744915339AE6C016B17C3763 | SHA256:4F1CE205C2BE986C9D38B951B6BCB6045EB363E06DACC069A41941F80BE9068C | |||
| 1452 | hacn.exe | C:\Users\admin\AppData\Local\Temp\_MEI14522\VCRUNTIME140.dll | executable | |
MD5:F34EB034AA4A9735218686590CBA2E8B | SHA256:9D2B40F0395CC5D1B4D5EA17B84970C29971D448C37104676DB577586D4AD1B1 | |||
| 1452 | hacn.exe | C:\Users\admin\AppData\Local\Temp\_MEI14522\_bz2.pyd | executable | |
MD5:86D1B2A9070CD7D52124126A357FF067 | SHA256:62173A8FADD4BF4DD71AB89EA718754AA31620244372F0C5BBBAE102E641A60E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
82
DNS requests
119
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3100 | hacn.exe | GET | 200 | 142.250.181.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4756 | based.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | whitelisted |
8008 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8008 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7268 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7268 | firefox.exe | POST | 200 | 172.217.18.3:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1088 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4756 | based.exe | 142.250.185.99:443 | gstatic.com | GOOGLE | US | whitelisted |
3100 | hacn.exe | 142.250.181.228:80 | www.google.com | GOOGLE | US | whitelisted |
3100 | hacn.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
github.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3100 | hacn.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
4756 | based.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
4756 | based.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
4756 | based.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
4756 | based.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |