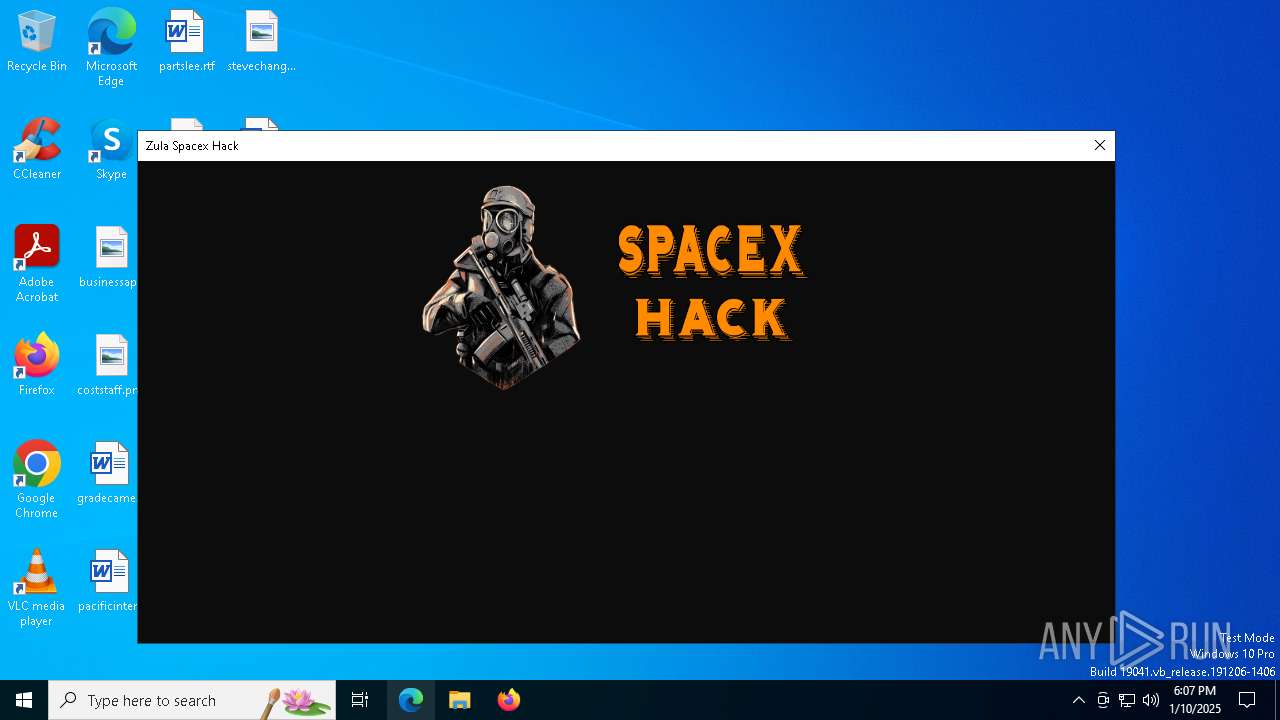
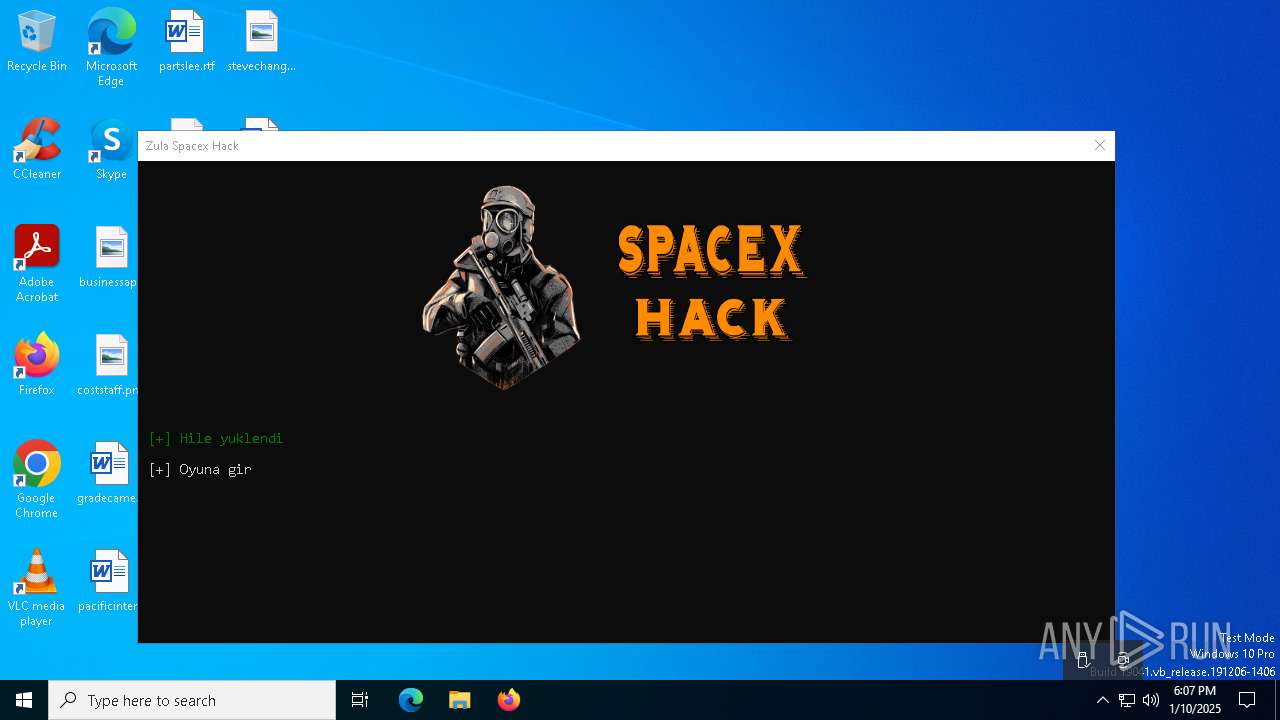
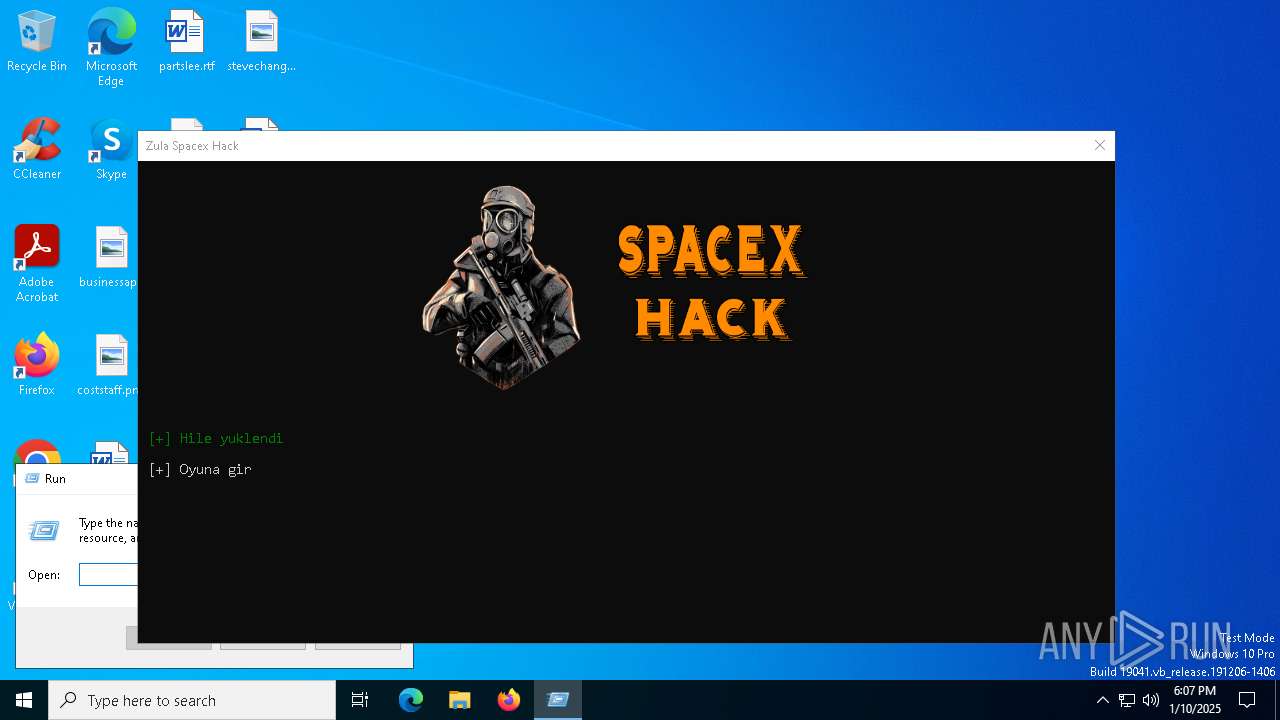
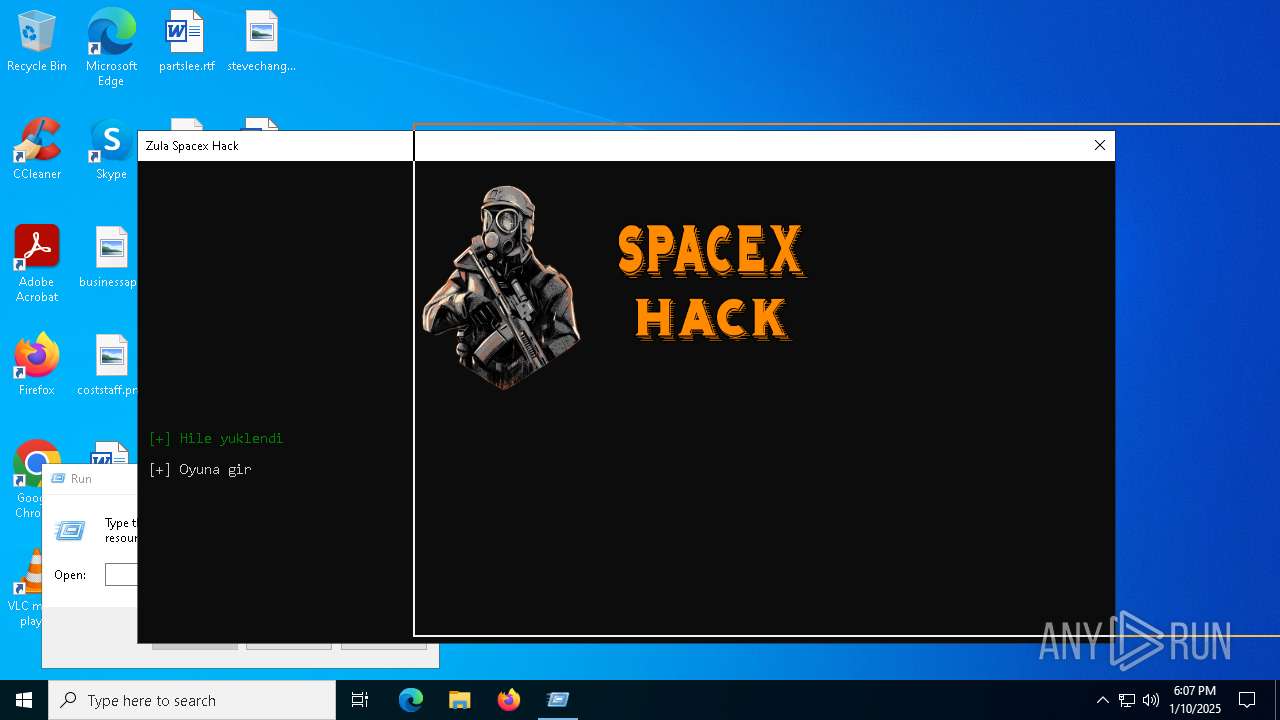
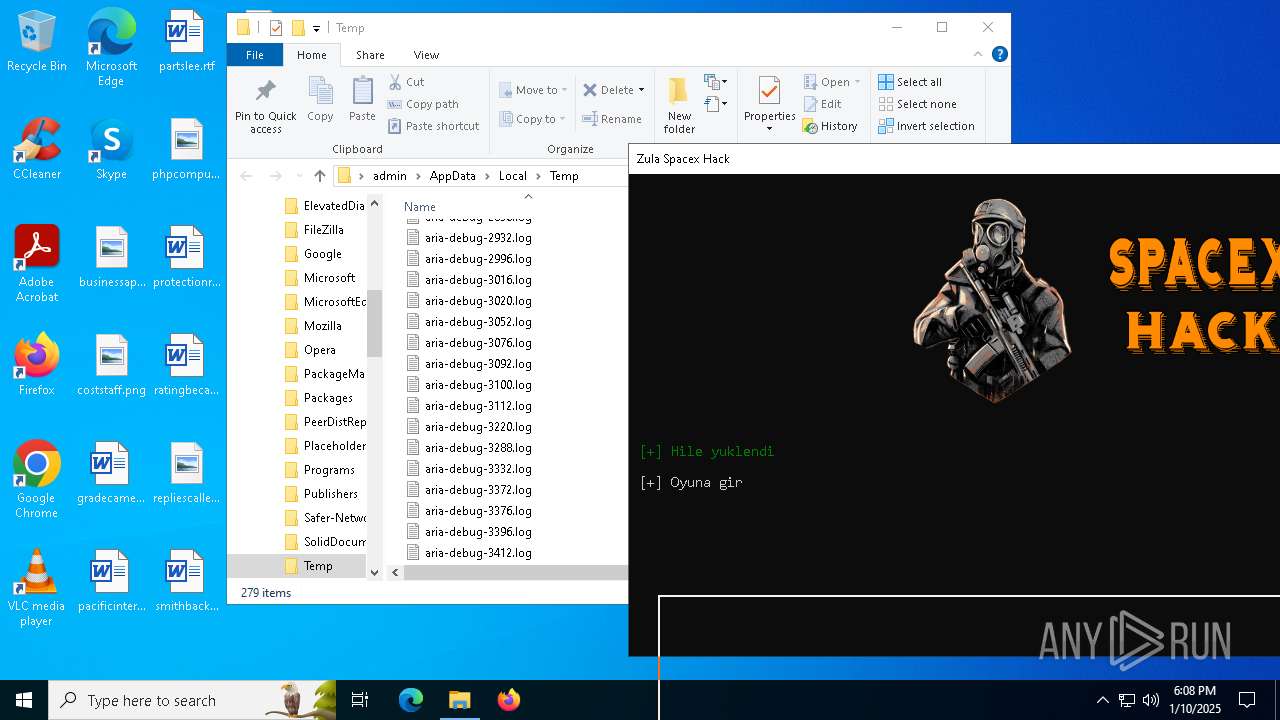
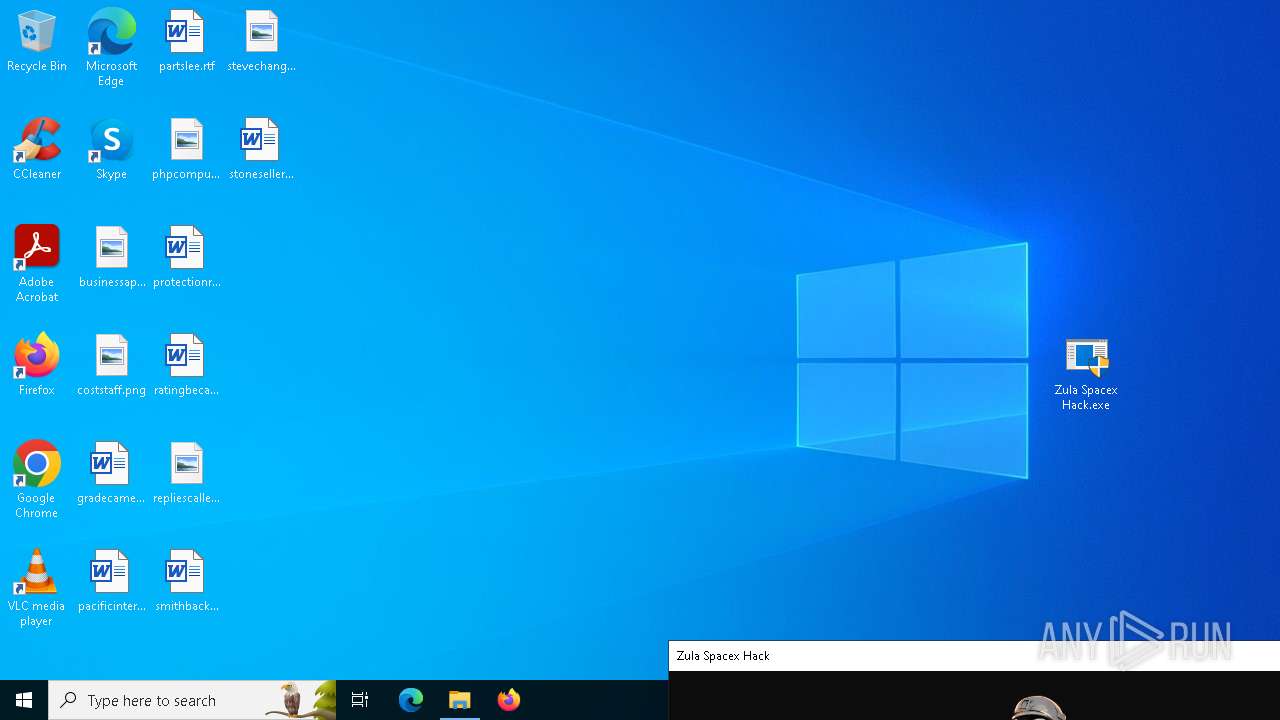
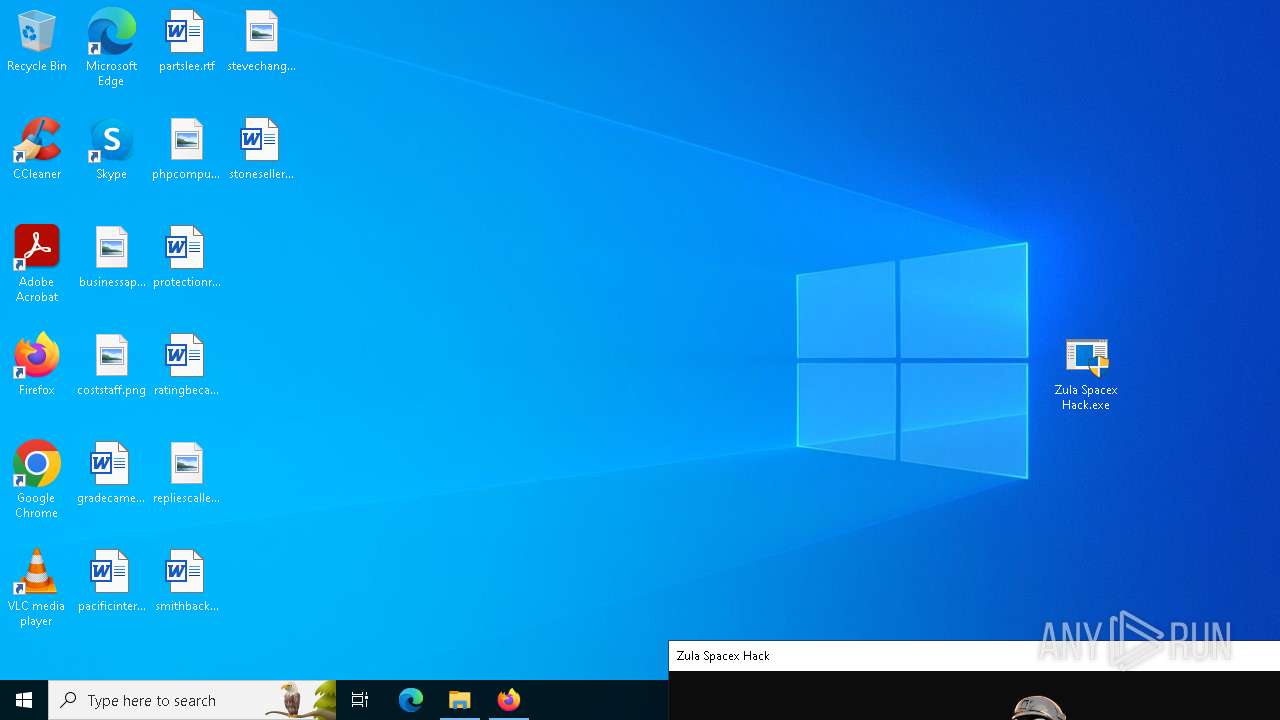
| File name: | Zula Spacex Hack.exe |
| Full analysis: | https://app.any.run/tasks/ecf6828f-9879-4e86-9cf7-bb035f202582 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | January 10, 2025, 18:06:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 9EA8A4AE340433B891D28439C307C3F1 |
| SHA1: | F8BB6E9961CCF4C6F0D340A715EC418D777A20B4 |
| SHA256: | EB8AC22CB3171099CE9F453185E1C66484A4BDDBF612D463365C4BC7C66D73C5 |
| SSDEEP: | 98304:aSyWHQCGILj9fdCdygwiofX7oaAb4cur4kuaCy+L1nERw1nhM78ULK7SCUaZ+2yX:ZAFW |
MALICIOUS
Uses Task Scheduler to autorun other applications
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
QUASAR has been detected (YARA)
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6948)
SUSPICIOUS
The process creates files with name similar to system file names
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
Executable content was dropped or overwritten
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
Process drops legitimate windows executable
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
Reads security settings of Internet Explorer
- Zula Spacex Hack.exe (PID: 6304)
Starts itself from another location
- svchost.exe (PID: 6504)
INFO
Reads the computer name
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
Creates files or folders in the user directory
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
The sample compiled with english language support
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
Checks supported languages
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
Reads the machine GUID from the registry
- Zula Spacex Hack.exe (PID: 6304)
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
Reads Environment values
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
The process uses the downloaded file
- svchost.exe (PID: 6504)
- svchost.exe (PID: 6948)
Manual execution by a user
- firefox.exe (PID: 4576)
Executable content was dropped or overwritten
- firefox.exe (PID: 5304)
Application launched itself
- firefox.exe (PID: 4576)
- firefox.exe (PID: 5304)
Process checks computer location settings
- Zula Spacex Hack.exe (PID: 6304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(6948) svchost.exe
Version1.4.1
C2 (2)darkerzm.duckdns.org:443
Sub_DirWindows
Install_Namesvchost.exe
Mutex9d0cae87-20bd-4a2e-b07e-e89f7d6ed7d3
StartupUpdate
TagSpacex
LogDirLogs
SignatureX/pb635X3WV4wgjuG83gWD0D3Uo8rG401s5A//zYshteNnbPNs/Czg7rpyrXAw03pa8cC91qYZsC0x6ruLFisE2eV5A5yOF3CRLngMZc2InDpM0d8DiQn9YcovJcC3DARyhh4NTapHwvGafzgwqnWxicRVwL5xg262ggAxhPg2jK0l626QJ/oOHYnjHEFVq198Z4MjfaGqblA6eOvfHgJbvH9bu6tS3SlZRbjjOZXYX4n0jtvyYU+LvXN4zN+xpcoq4/MS91Ly4PzJQvnHqmGqQ7EGcAvxcFOtlfnMwbOMOX...
CertificateMIIE9DCCAtygAwIBAgIQAJ8Cpgzf3uRZa2bMdRGamzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDcyOTE0MzEzM1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEArE4nts5MisKdJY3t8ZQo1USMJTgeNjabNJlxO00z11f0VMdfzYSDpE1f3PvhtinY4LKn0eNH...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:31 17:40:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 3162624 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x306172 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
155
Monitored processes
25
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2152 -parentBuildID 20240213221259 -prefsHandle 2128 -prefMapHandle 2116 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {73090e95-02c4-4261-9701-7a1185acbb9d} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a78482d10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1152 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5132 -childID 3 -isForBrowser -prefsHandle 4548 -prefMapHandle 4288 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1448 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7196cdae-9f1e-49e7-82c5-29efe5bd5eb7} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a0bf6d690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4376 -childID 7 -isForBrowser -prefsHandle 2444 -prefMapHandle 2280 -prefsLen 32011 -prefMapSize 244583 -jsInitHandle 1448 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e30d371f-dff8-4ac7-a247-c75702ed2932} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a10670850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1544 | "C:\Users\admin\AppData\Local\Temp\Zula Spacex Hack.exe" | C:\Users\admin\AppData\Local\Temp\Zula Spacex Hack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5820 -childID 6 -isForBrowser -prefsHandle 5348 -prefMapHandle 5472 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1448 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b6a81f53-db93-437d-9664-5ed4c5f04f3d} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a0d7e8d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1668 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2464 -childID 9 -isForBrowser -prefsHandle 6332 -prefMapHandle 5744 -prefsLen 32011 -prefMapSize 244583 -jsInitHandle 1448 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {2585f367-a9b1-4cdb-af2f-5fad24249fac} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a0f4ba4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5888 -childID 8 -isForBrowser -prefsHandle 5228 -prefMapHandle 4464 -prefsLen 32011 -prefMapSize 244583 -jsInitHandle 1448 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7a9eaec4-09d4-4818-b0cd-348f956de9d9} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a11403bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2780 -childID 1 -isForBrowser -prefsHandle 2708 -prefMapHandle 2716 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1448 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {a04f7f55-2a7e-4f29-bd71-de0b34d4f1de} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 22a0a1a9bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2996 | "schtasks" /create /tn "Update" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\Windows\svchost.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 761
Read events
22 721
Write events
39
Delete events
1
Modification events
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E0000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 105 | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 9C62816700000000 | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | 2 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C64176003200005630002A5ADB9020005A554C4153507E312E45584500005A0009000400EFBE2A5ADB902A5A09912E0000007B2600000000140000000000000000000000000000009092FF005A0075006C006100200053007000610063006500780020004800610063006B002E0065007800650000001C000000 | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (5304) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 8 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C64176003200005630002A5ADB9020005A554C4153507E312E45584500005A0009000400EFBE2A5ADB902A5A09912E0000007B2600000000140000000000000000000000000000009092FF005A0075006C006100200053007000610063006500780020004800610063006B002E0065007800650000001C000000 | |||
Executable files
4
Suspicious files
187
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5304 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6304 | Zula Spacex Hack.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | executable | |
MD5:E7E1387343960784B9026FB567F5D0AC | SHA256:43CE2EF57CEFBAE98D64239F8D8010C30F8AE65FE74308711BB2480C1558FA2A | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6504 | svchost.exe | C:\Users\admin\AppData\Roaming\Windows\svchost.exe | executable | |
MD5:E7E1387343960784B9026FB567F5D0AC | SHA256:43CE2EF57CEFBAE98D64239F8D8010C30F8AE65FE74308711BB2480C1558FA2A | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:7D80FB0F34534D16AAA6D53BB6634BDF | SHA256:4D447E913B03E9265D620579F7B6DE4D6836BF46CF8DB37B3E3F176F590885AE | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5304 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:D30F5B10F3D4B3992E4D666F622163F4 | SHA256:2585819A7401A308DA879FA416278E473CEA5F6D0D24C59F514C5A698C61D03A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
151
DNS requests
181
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1468 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1468 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6680 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5304 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5304 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5304 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.227.215:443 | r.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1468 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1468 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | r.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
3040 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
darkerzm.duckdns.org |
| malicious |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
5304 | firefox.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.tc domain |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |