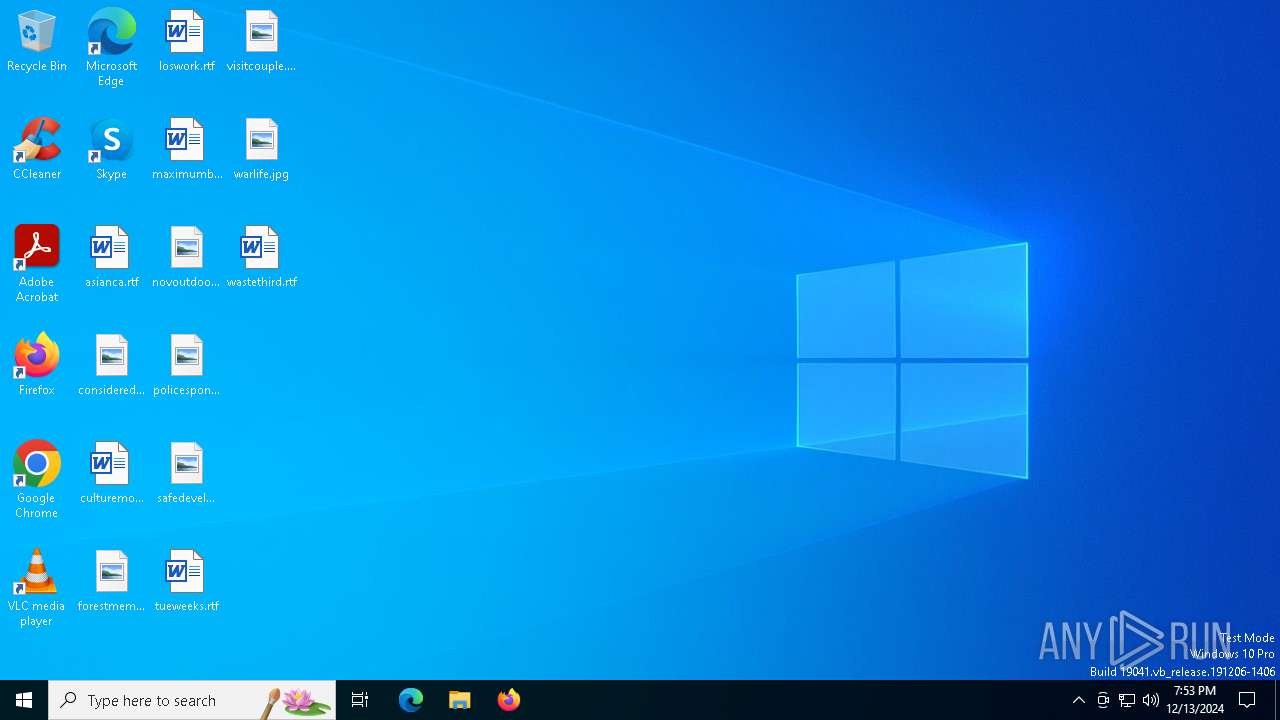
| File name: | file |
| Full analysis: | https://app.any.run/tasks/047304e7-3a78-44f8-9cde-af35f92214fd |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 13, 2024, 19:53:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 3B7F8EA6D98D68EDD65A49C922671468 |
| SHA1: | E5D999ECC81A188BFA758AF9980ECF55038527B3 |
| SHA256: | EADBAD94A4EF1B106F1309FDDE748C49D606FC04589FC079853292B0C4EE136F |
| SSDEEP: | 98304:bHkYbAXoiPpqcw6YSC6sunTrGSjlzkkIyG1r9ehbxXq63q+lbzN/ZgVE3WrHCI4+:b1 |
MALICIOUS
AMADEY has been detected (SURICATA)
- skotes.exe (PID: 6564)
Connects to the CnC server
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- svchost.exe (PID: 2192)
Steals credentials from Web Browsers
- 90813d843f.exe (PID: 7108)
- eddf699b5c.exe (PID: 3808)
LUMMA mutex has been found
- 90813d843f.exe (PID: 7108)
- 6cad2dbca3.exe (PID: 8660)
Actions looks like stealing of personal data
- 90813d843f.exe (PID: 7108)
- eddf699b5c.exe (PID: 3808)
- 755bfa09c6.exe (PID: 8452)
- 6cad2dbca3.exe (PID: 8660)
Changes the autorun value in the registry
- skotes.exe (PID: 6564)
AMADEY has been detected (YARA)
- skotes.exe (PID: 6564)
Possible tool for stealing has been detected
- 7c6a1d738f.exe (PID: 6252)
- firefox.exe (PID: 6420)
StealC has been detected
- eddf699b5c.exe (PID: 3808)
STEALC has been detected (SURICATA)
- eddf699b5c.exe (PID: 3808)
VIDAR mutex has been found
- 755bfa09c6.exe (PID: 8452)
LUMMA has been found (auto)
- skotes.exe (PID: 6564)
GCLEANER has been detected (SURICATA)
- 6f0f67af9a.exe (PID: 4468)
STEALC has been detected (YARA)
- eddf699b5c.exe (PID: 3808)
LUMMA has been detected (SURICATA)
- 6cad2dbca3.exe (PID: 8660)
- svchost.exe (PID: 2192)
SUSPICIOUS
Reads the BIOS version
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- skotes.exe (PID: 7820)
- c64e6a4deb.exe (PID: 8044)
- ECFCBFBGDB.exe (PID: 8976)
- skotes.exe (PID: 540)
Starts itself from another location
- file.exe (PID: 6332)
Executable content was dropped or overwritten
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- 6f0f67af9a.exe (PID: 4468)
Reads security settings of Internet Explorer
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- 755bfa09c6.exe (PID: 8452)
- 6f0f67af9a.exe (PID: 4468)
Contacting a server suspected of hosting an CnC
- skotes.exe (PID: 6564)
- svchost.exe (PID: 2192)
- 6cad2dbca3.exe (PID: 8660)
- eddf699b5c.exe (PID: 3808)
Potential Corporate Privacy Violation
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- 6f0f67af9a.exe (PID: 4468)
Process requests binary or script from the Internet
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
Application launched itself
- 90813d843f.exe (PID: 7020)
Connects to the server without a host name
- skotes.exe (PID: 6564)
- 6f0f67af9a.exe (PID: 4468)
- eddf699b5c.exe (PID: 3808)
Uses TASKKILL.EXE to kill Browsers
- 7c6a1d738f.exe (PID: 6252)
Uses TASKKILL.EXE to kill process
- 7c6a1d738f.exe (PID: 6252)
Windows Defender mutex has been found
- eddf699b5c.exe (PID: 3808)
Searches for installed software
- eddf699b5c.exe (PID: 3808)
The process executes via Task Scheduler
- skotes.exe (PID: 7820)
- skotes.exe (PID: 540)
Checks Windows Trust Settings
- 755bfa09c6.exe (PID: 8452)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- 755bfa09c6.exe (PID: 8452)
The process drops Mozilla's DLL files
- eddf699b5c.exe (PID: 3808)
Starts CMD.EXE for commands execution
- eddf699b5c.exe (PID: 3808)
- 755bfa09c6.exe (PID: 8452)
The process drops C-runtime libraries
- eddf699b5c.exe (PID: 3808)
Process drops legitimate windows executable
- eddf699b5c.exe (PID: 3808)
The executable file from the user directory is run by the CMD process
- ECFCBFBGDB.exe (PID: 8976)
Executes application which crashes
- 755bfa09c6.exe (PID: 8452)
- 6f0f67af9a.exe (PID: 4468)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8048)
INFO
Checks supported languages
- file.exe (PID: 6332)
- 90813d843f.exe (PID: 7020)
- skotes.exe (PID: 6564)
- 90813d843f.exe (PID: 7108)
- 7c6a1d738f.exe (PID: 6252)
- eddf699b5c.exe (PID: 3808)
- skotes.exe (PID: 7820)
- c64e6a4deb.exe (PID: 8044)
- 755bfa09c6.exe (PID: 8452)
- ECFCBFBGDB.exe (PID: 8976)
Reads the computer name
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
- 90813d843f.exe (PID: 7108)
- 7c6a1d738f.exe (PID: 6252)
- eddf699b5c.exe (PID: 3808)
- 755bfa09c6.exe (PID: 8452)
- 6f0f67af9a.exe (PID: 4468)
Sends debugging messages
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- skotes.exe (PID: 7820)
- c64e6a4deb.exe (PID: 8044)
- 6f0f67af9a.exe (PID: 4468)
- ECFCBFBGDB.exe (PID: 8976)
- skotes.exe (PID: 540)
The process uses the downloaded file
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
Process checks computer location settings
- file.exe (PID: 6332)
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
Checks proxy server information
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- 755bfa09c6.exe (PID: 8452)
- 6f0f67af9a.exe (PID: 4468)
- WerFault.exe (PID: 9172)
- WerFault.exe (PID: 1144)
Create files in a temporary directory
- skotes.exe (PID: 6564)
Reads the software policy settings
- 90813d843f.exe (PID: 7108)
- 6cad2dbca3.exe (PID: 8660)
- WerFault.exe (PID: 1144)
- WerFault.exe (PID: 9172)
The sample compiled with english language support
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
Reads mouse settings
- 7c6a1d738f.exe (PID: 6252)
Themida protector has been detected
- skotes.exe (PID: 6564)
- eddf699b5c.exe (PID: 3808)
- 6f0f67af9a.exe (PID: 4468)
Application launched itself
- firefox.exe (PID: 6420)
- firefox.exe (PID: 6440)
- chrome.exe (PID: 7492)
- msedge.exe (PID: 8684)
- chrome.exe (PID: 9152)
- msedge.exe (PID: 1544)
Reads product name
- eddf699b5c.exe (PID: 3808)
Reads CPU info
- eddf699b5c.exe (PID: 3808)
Creates files or folders in the user directory
- skotes.exe (PID: 6564)
- 755bfa09c6.exe (PID: 8452)
- 6f0f67af9a.exe (PID: 4468)
- eddf699b5c.exe (PID: 3808)
- WerFault.exe (PID: 9172)
Reads the machine GUID from the registry
- 755bfa09c6.exe (PID: 8452)
Attempting to use instant messaging service
- 755bfa09c6.exe (PID: 8452)
Creates files in the program directory
- eddf699b5c.exe (PID: 3808)
- 755bfa09c6.exe (PID: 8452)
The sample compiled with czech language support
- skotes.exe (PID: 6564)
Executable content was dropped or overwritten
- firefox.exe (PID: 6440)
Reads Environment values
- eddf699b5c.exe (PID: 3808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(6564) skotes.exe
C2185.215.113.43
URLhttp://185.215.113.43/Zu7JuNko/index.php
Version4.42
Options
Drop directoryabc3bc1985
Drop nameskotes.exe
Strings (120)2016
cmd /C RMDIR /s/q
Comodo
st=s
=
skotes.exe
\App
Norton
e1
AVG
" && timeout 1 && del
exe
2019
--
wb
DefaultSettings.YResolution
ProgramData\
:::
VideoID
Rem
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
http://
<d>
2022
Sophos
Programs
lv:
&unit=
------
POST
%-lu
<c>
Content-Type: application/x-www-form-urlencoded
185.215.113.43
Doctor Web
\
id:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
360TotalSecurity
Startup
clip.dll
"
Content-Type: application/octet-stream
Content-Type: multipart/form-data; boundary=----
cred.dll|clip.dll|
S-%lu-
rb
rundll32.exe
0123456789
GetNativeSystemInfo
abc3bc1985
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
" && ren
d1
ESET
vs:
"
------
sd:
WinDefender
dll
e0
%USERPROFILE%
Panda Security
SOFTWARE\Microsoft\Windows NT\CurrentVersion
zip
cmd
-unicode-
cred.dll
shell32.dll
ProductName
&&
shutdown -s -t 0
|
/Plugins/
Bitdefender
\0000
Content-Disposition: form-data; name="data"; filename="
/Zu7JuNko/index.php
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
av:
4.42
-%lu
Avira
GET
e2
/quiet
Kaspersky Lab
#
ps1
-executionpolicy remotesigned -File "
DefaultSettings.XResolution
Powershell.exe
bi:
msi
https://
random
pc:
un:
abcdefghijklmnopqrstuvwxyz0123456789-_
ar:
Main
"taskkill /f /im "
ComputerName
2025
AVAST Software
SYSTEM\ControlSet001\Services\BasicDisplay\Video
r=
.jpg
CurrentBuild
og:
dm:
?scr=1
kernel32.dll
/k
&& Exit"
+++
rundll32
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:22 17:40:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 322048 |
| InitializedDataSize: | 104960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x31f000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
213
Monitored processes
78
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\AppData\Local\Temp\abc3bc1985\skotes.exe" | C:\Users\admin\AppData\Local\Temp\abc3bc1985\skotes.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4508 --field-trial-handle=1976,i,8448535505114482516,7798073850907406260,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1144 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8452 -s 3016 | C:\Windows\SysWOW64\WerFault.exe | 755bfa09c6.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --remote-debugging-port=9223 --profile-directory="Default" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | 755bfa09c6.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1852 -parentBuildID 20240213221259 -prefsHandle 1780 -prefMapHandle 1768 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {476f70bd-503d-4fa4-b55d-8cee1643ad33} 6440 "\\.\pipe\gecko-crash-server-pipe.6440" 1ce7f0f0a10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | taskkill /F /IM opera.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | 7c6a1d738f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | taskkill /F /IM chrome.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | 7c6a1d738f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 365
Read events
36 323
Write events
42
Delete events
0
Modification events
| (PID) Process: | (6564) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6564) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6564) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6564) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 7c6a1d738f.exe |
Value: C:\Users\admin\AppData\Local\Temp\1014911001\7c6a1d738f.exe | |||
| (PID) Process: | (3808) eddf699b5c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3808) eddf699b5c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3808) eddf699b5c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6440) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6564) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | eddf699b5c.exe |
Value: C:\Users\admin\AppData\Local\Temp\1014912001\eddf699b5c.exe | |||
| (PID) Process: | (7492) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
53
Suspicious files
418
Text files
186
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6440 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6564 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\random[1].exe | executable | |
MD5:28E568616A7B792CAC1726DEB77D9039 | SHA256:9597798F7789ADC29FBE97707B1BD8CA913C4D5861B0AD4FDD6B913AF7C7A8E2 | |||
| 6332 | file.exe | C:\Users\admin\AppData\Local\Temp\abc3bc1985\skotes.exe | executable | |
MD5:3B7F8EA6D98D68EDD65A49C922671468 | SHA256:EADBAD94A4EF1B106F1309FDDE748C49D606FC04589FC079853292B0C4EE136F | |||
| 6332 | file.exe | C:\Windows\Tasks\skotes.job | binary | |
MD5:6B3F95A43C3DAD0C2CF2389D38139323 | SHA256:19660AB9FA9AF33DF84959435F7D053863C6B916C7CCAFCA2580315F3ED425EE | |||
| 6564 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\random[1].exe | executable | |
MD5:2C4DECB4A0DD610843D56D6C8A7F3474 | SHA256:065B99CB2637E4516BA4784DCB269D59CAE9651A29CA0B8BD12AB429B2D73B07 | |||
| 6440 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 6440 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6564 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[1].exe | executable | |
MD5:7F74BD86D679D7FA0C3F344959EAFBCB | SHA256:35BB0A40CC2B7D579A049ABE5D901F4FD12A1FF27F68DDCACD2CA1A5D52F0191 | |||
| 6440 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6564 | skotes.exe | C:\Users\admin\AppData\Local\Temp\1014911001\7c6a1d738f.exe | executable | |
MD5:2C4DECB4A0DD610843D56D6C8A7F3474 | SHA256:065B99CB2637E4516BA4784DCB269D59CAE9651A29CA0B8BD12AB429B2D73B07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
105
TCP/UDP connections
224
DNS requests
198
Threats
89
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3808 | eddf699b5c.exe | POST | 200 | 185.215.113.206:80 | http://185.215.113.206/c4becf79229cb002.php | unknown | — | — | malicious |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6564 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
6564 | skotes.exe | GET | 200 | 31.41.244.11:80 | http://31.41.244.11/files/fate/random.exe | unknown | — | — | unknown |
6564 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
6564 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
6564 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
6440 | firefox.exe | POST | — | 142.250.186.67:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
3808 | eddf699b5c.exe | GET | — | 185.215.113.206:80 | http://185.215.113.206/68b591d6548ec281/sqlite3.dll | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.19.80.88:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5856 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2396 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
drive-connect.cyou |
| malicious |
youtube.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6564 | skotes.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6564 | skotes.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
6564 | skotes.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 2 |
6564 | skotes.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6564 | skotes.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6564 | skotes.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6564 | skotes.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6564 | skotes.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6564 | skotes.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6564 | skotes.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
file.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
eddf699b5c.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
c64e6a4deb.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
6f0f67af9a.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
ECFCBFBGDB.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|