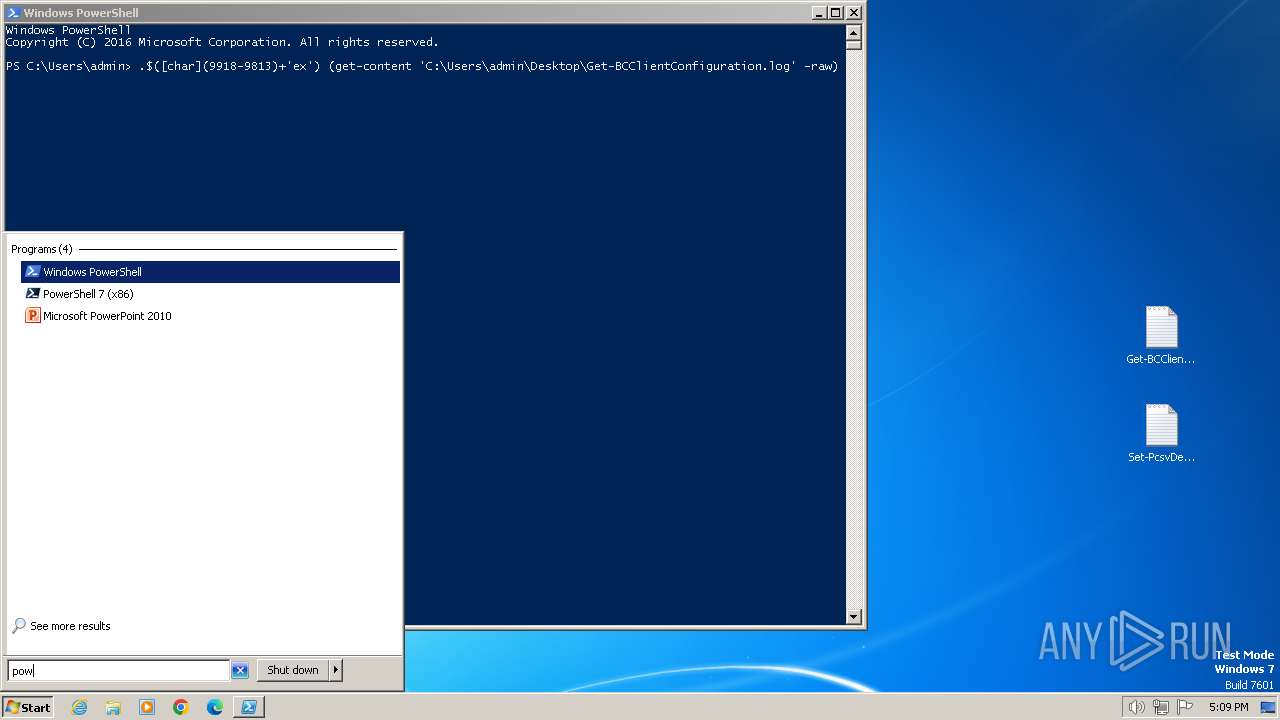
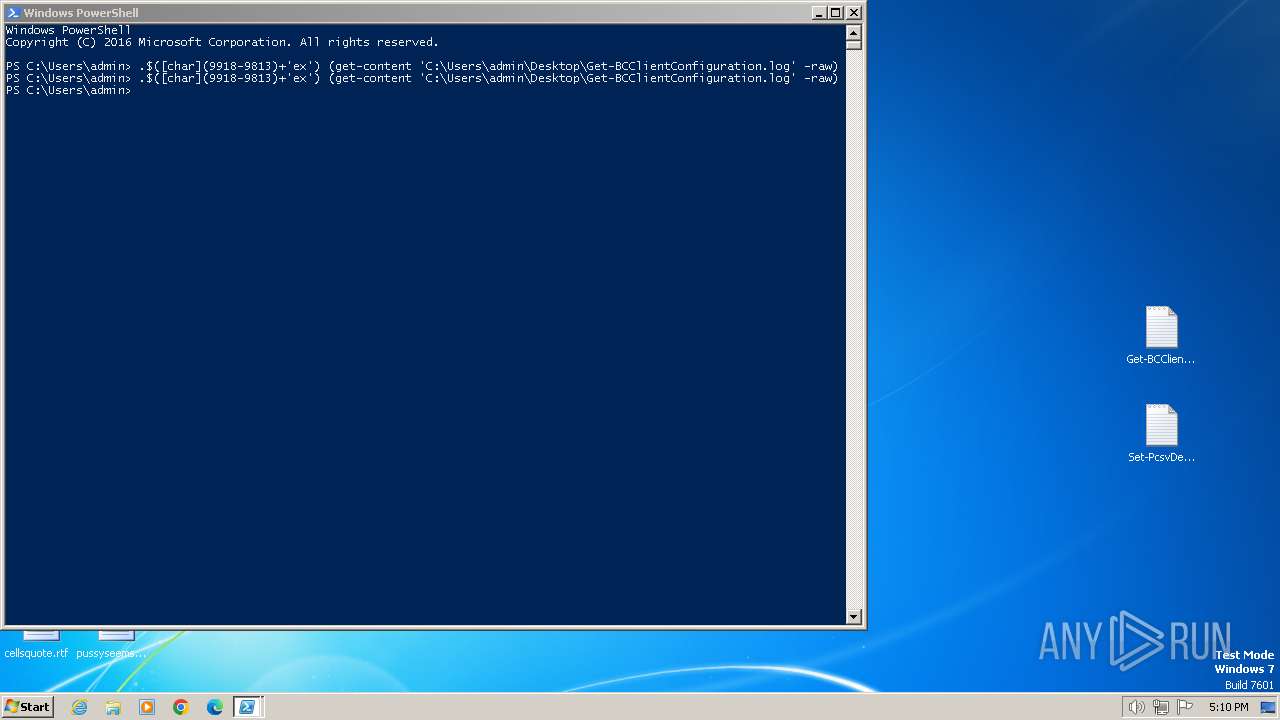
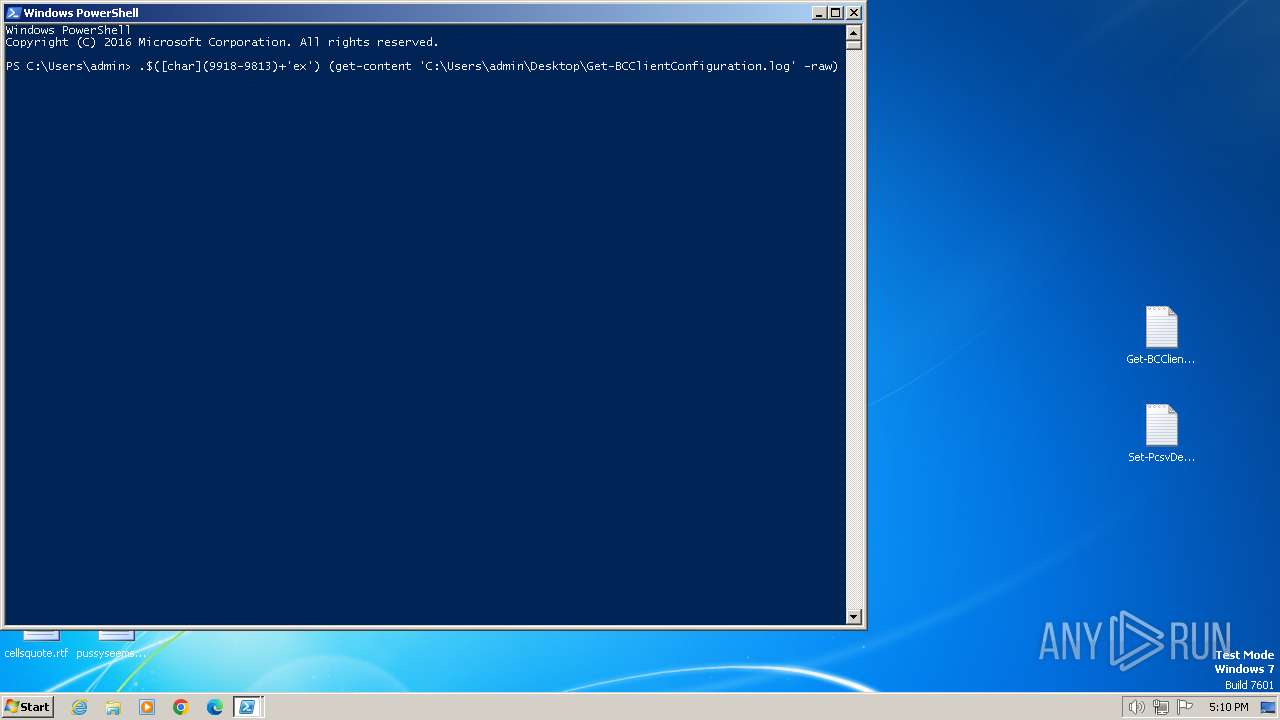
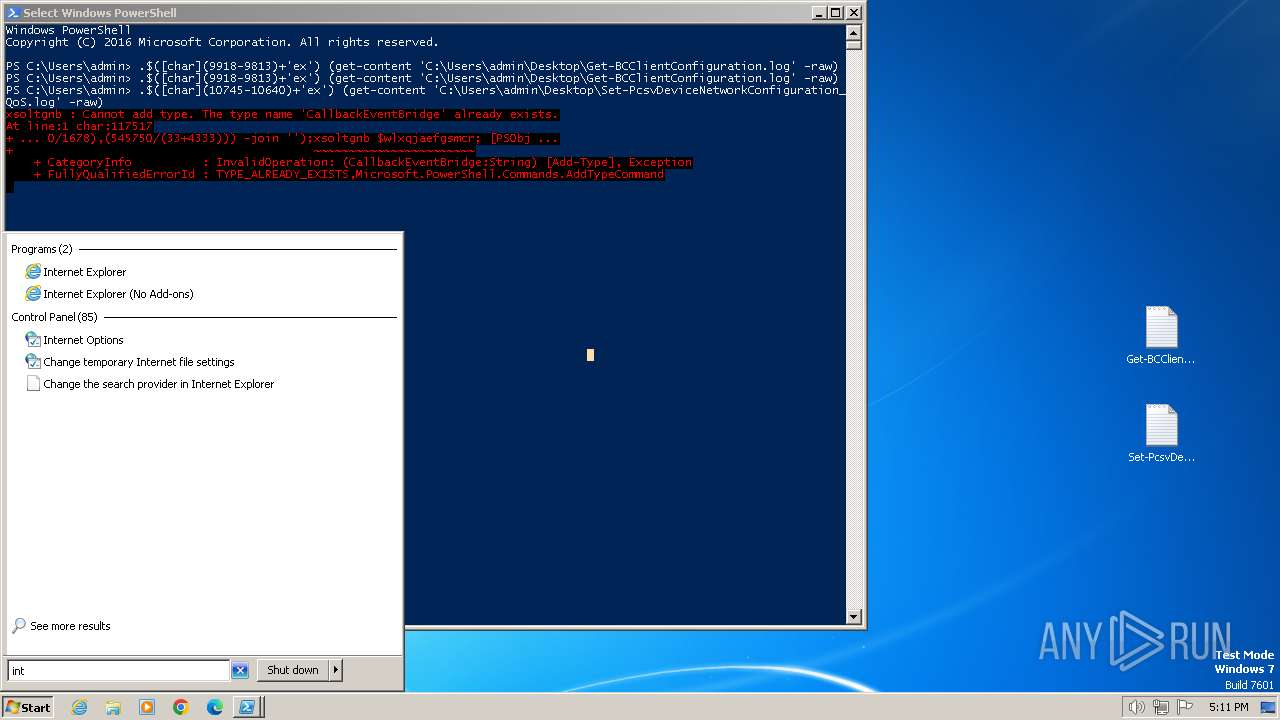
| File name: | Get-BCClientConfiguration.log |
| Full analysis: | https://app.any.run/tasks/357c7dde-bda6-4f30-a8fd-911e79bc178e |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 18, 2024, 17:08:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (32767), with no line terminators |
| MD5: | 30DF6E4CA7144550ABF923C3D2C1680A |
| SHA1: | 81A3372AC9E44176FE8EF688B9534EE640AFD66C |
| SHA256: | EA8156B5E8FF96429DF4E30A42D9C38B283F667B7FFBBED2D8BEB3D10F9EEEA3 |
| SSDEEP: | 12288:rOYebPif0tYcAOpw6VWAbfmWP9VtiI8c3jUWUEoOWZ9Wk85zSZhXLISL761wYm+g:rOgMtYT6XfNqIf3mvy4PXBIwYmoqbS+ |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 2340)
- powershell.exe (PID: 3164)
Drops the executable file immediately after the start
- csc.exe (PID: 3392)
- csc.exe (PID: 240)
- csc.exe (PID: 880)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 3164)
Steals credentials from Web Browsers
- powershell.exe (PID: 3164)
Actions looks like stealing of personal data
- powershell.exe (PID: 3164)
SUSPICIOUS
Uses .NET C# to load dll
- powershell.exe (PID: 2340)
- powershell.exe (PID: 3164)
Executable content was dropped or overwritten
- csc.exe (PID: 240)
- csc.exe (PID: 880)
- csc.exe (PID: 3392)
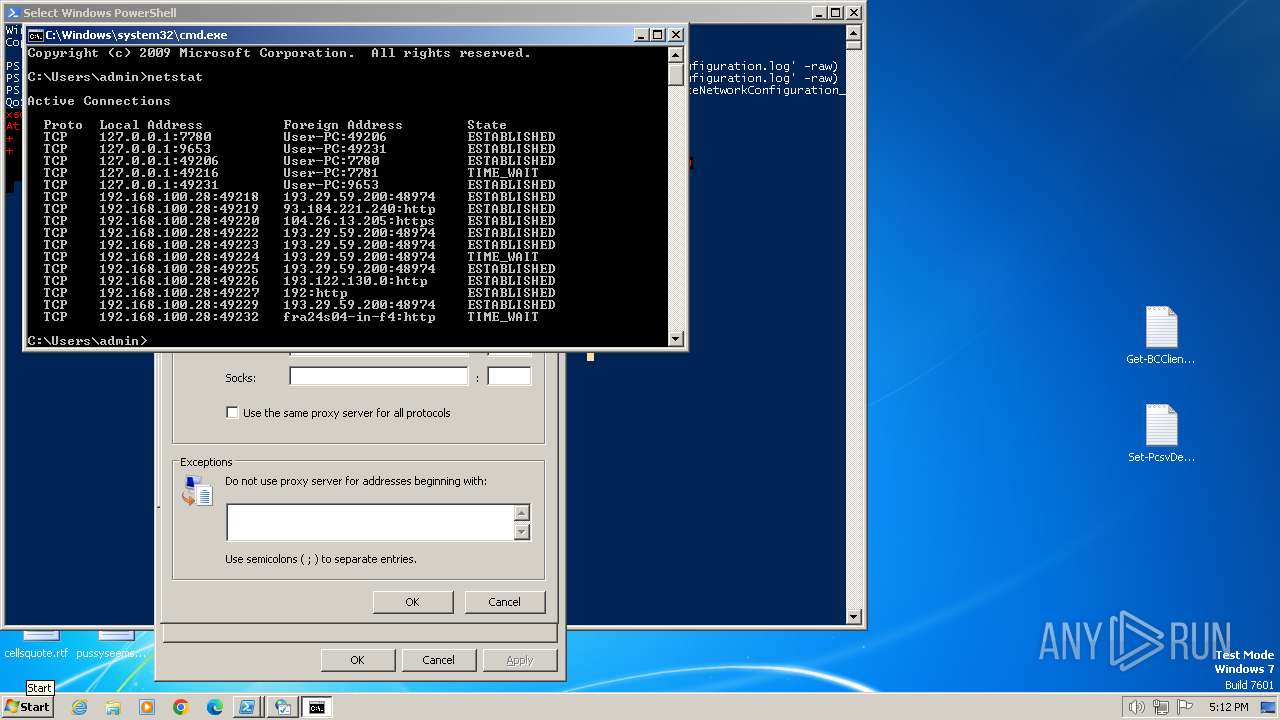
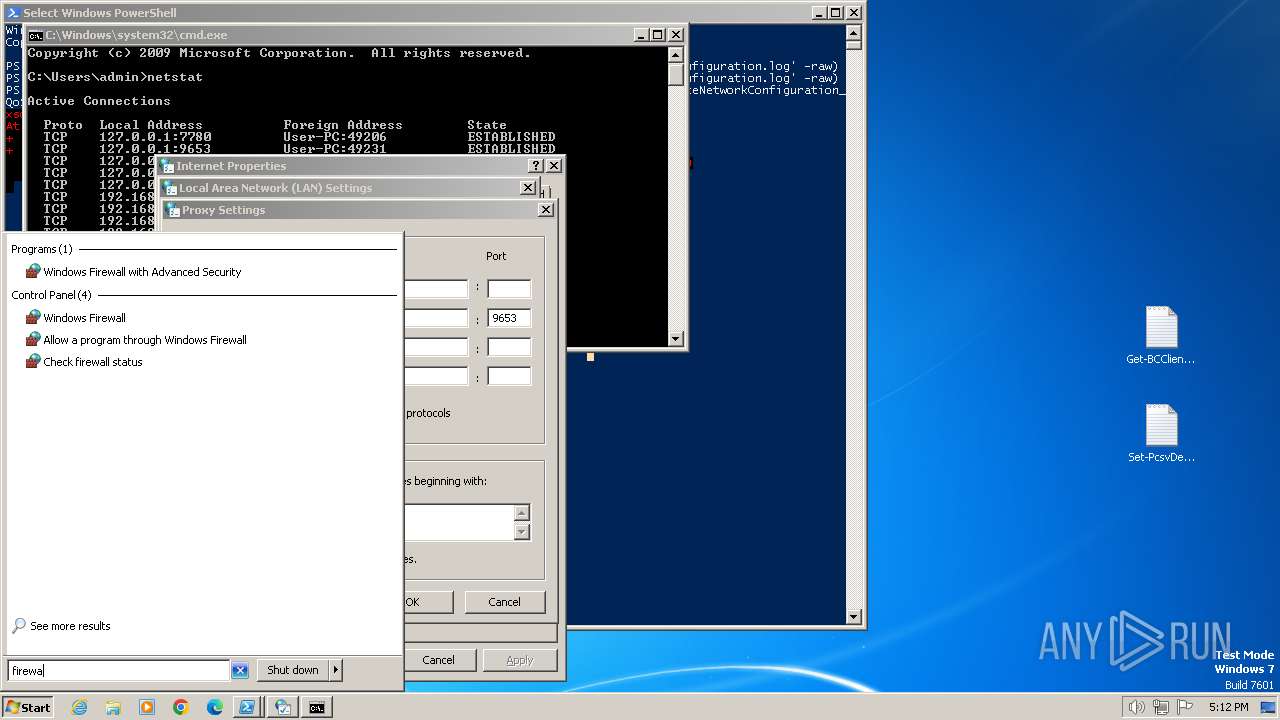
Connects to unusual port
- powershell.exe (PID: 3164)
Checks for external IP
- powershell.exe (PID: 3164)
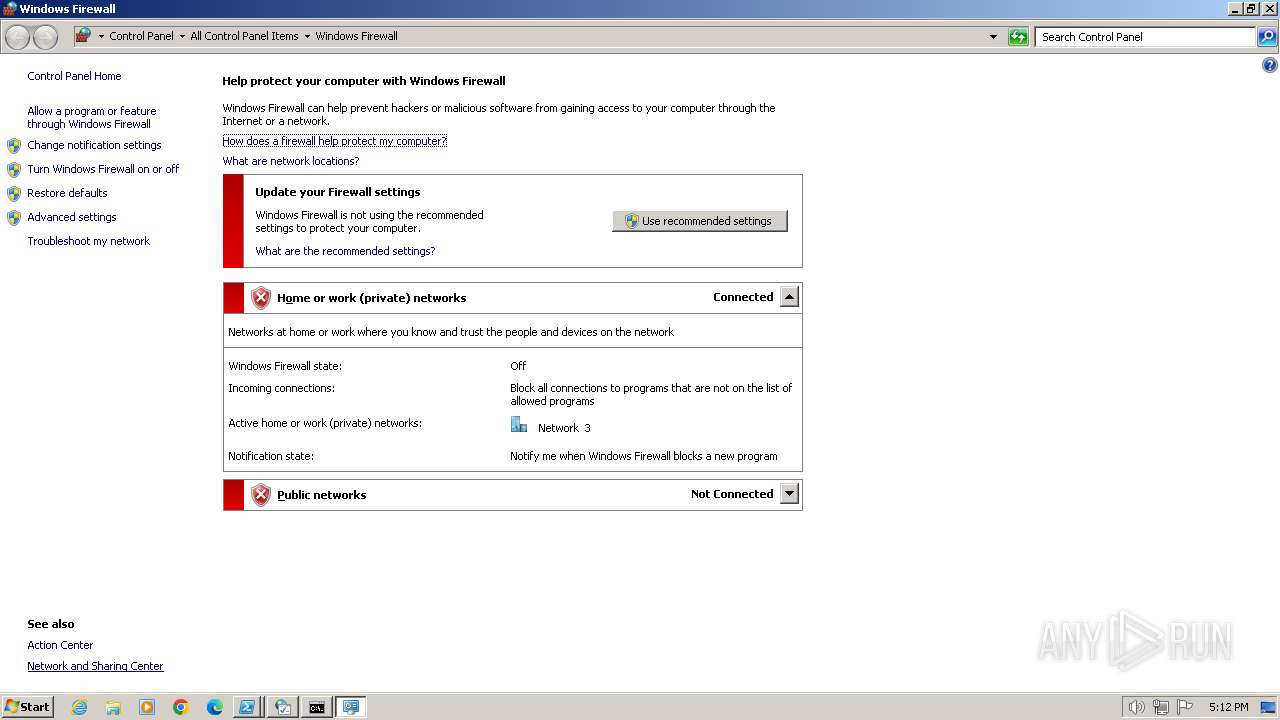
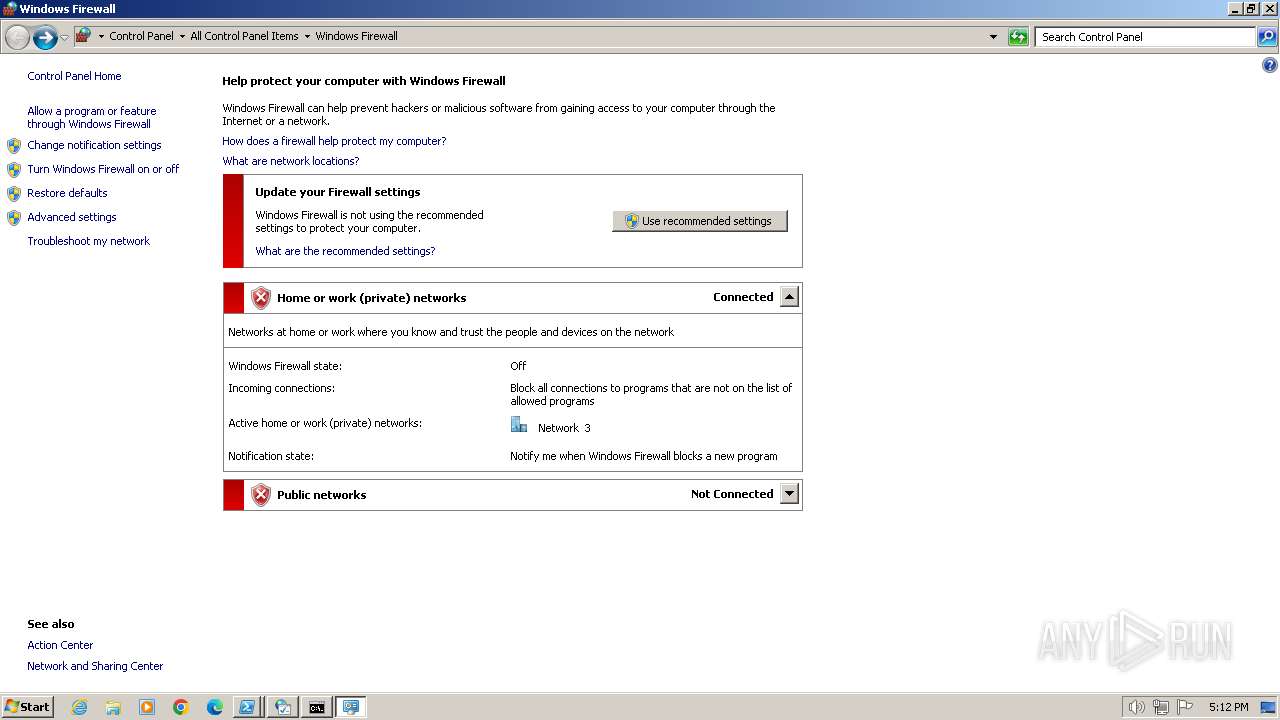
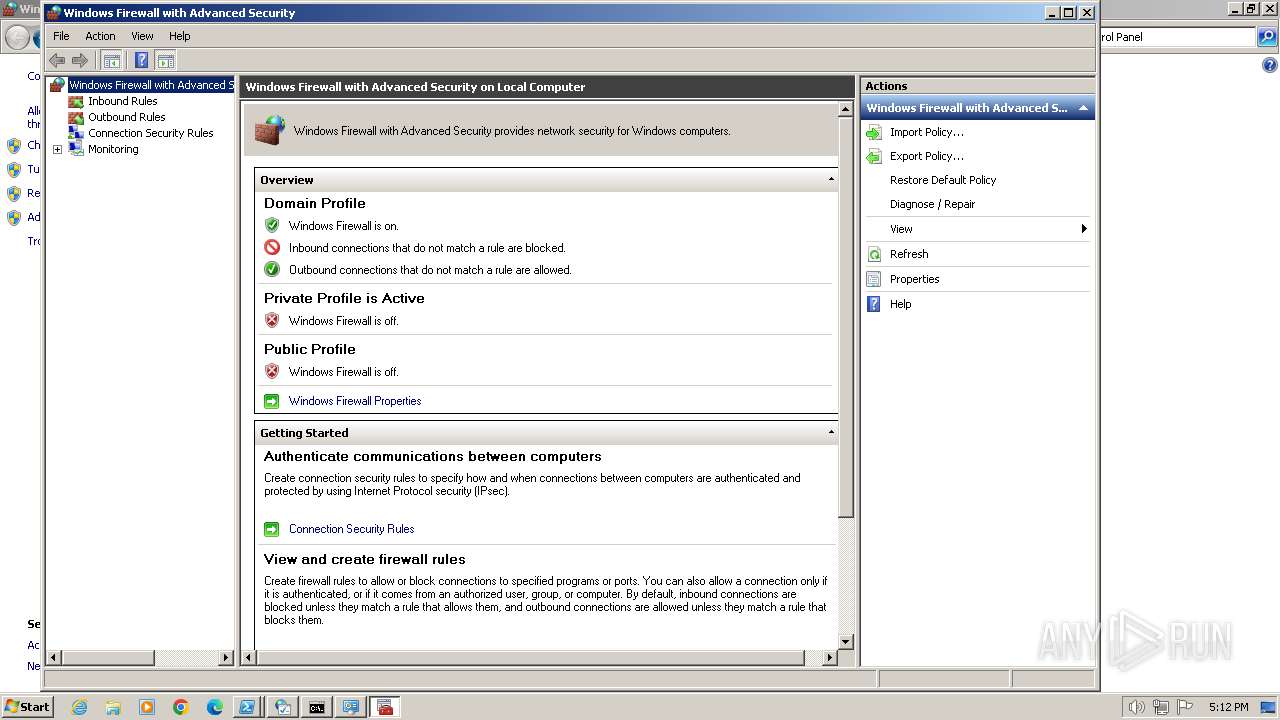
Uses NETSH.EXE to add a firewall rule or allowed programs
- powershell.exe (PID: 3164)
Reads browser cookies
- powershell.exe (PID: 3164)
The process verifies whether the antivirus software is installed
- powershell.exe (PID: 3164)
The Powershell connects to the Internet
- powershell.exe (PID: 3164)
Unusual connection from system programs
- powershell.exe (PID: 3164)
Loads DLL from Mozilla Firefox
- powershell.exe (PID: 3164)
Reads the Internet Settings
- powershell.exe (PID: 3164)
- rundll32.exe (PID: 3252)
Reads Microsoft Outlook installation path
- rundll32.exe (PID: 3252)
Accesses Microsoft Outlook profiles
- powershell.exe (PID: 3164)
INFO
Reads the machine GUID from the registry
- csc.exe (PID: 3392)
- cvtres.exe (PID: 3996)
- cvtres.exe (PID: 3912)
- csc.exe (PID: 880)
- csc.exe (PID: 240)
- cvtres.exe (PID: 1556)
Manual execution by a user
- powershell.exe (PID: 2340)
- powershell.exe (PID: 3164)
- rundll32.exe (PID: 3252)
- cmd.exe (PID: 2416)
Checks supported languages
- csc.exe (PID: 3392)
- cvtres.exe (PID: 3996)
- csc.exe (PID: 240)
- csc.exe (PID: 880)
- cvtres.exe (PID: 3912)
- cvtres.exe (PID: 1556)
Create files in a temporary directory
- cvtres.exe (PID: 3996)
- csc.exe (PID: 3392)
- csc.exe (PID: 880)
- csc.exe (PID: 240)
- cvtres.exe (PID: 3912)
- cvtres.exe (PID: 1556)
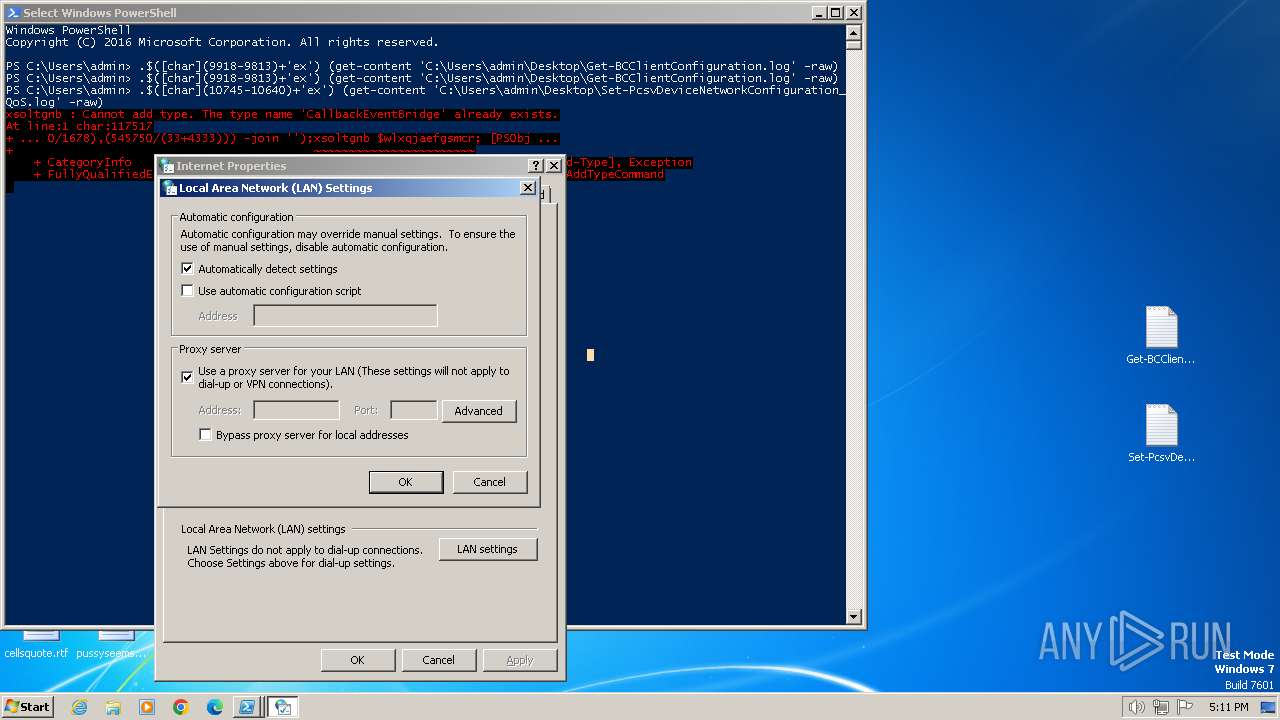
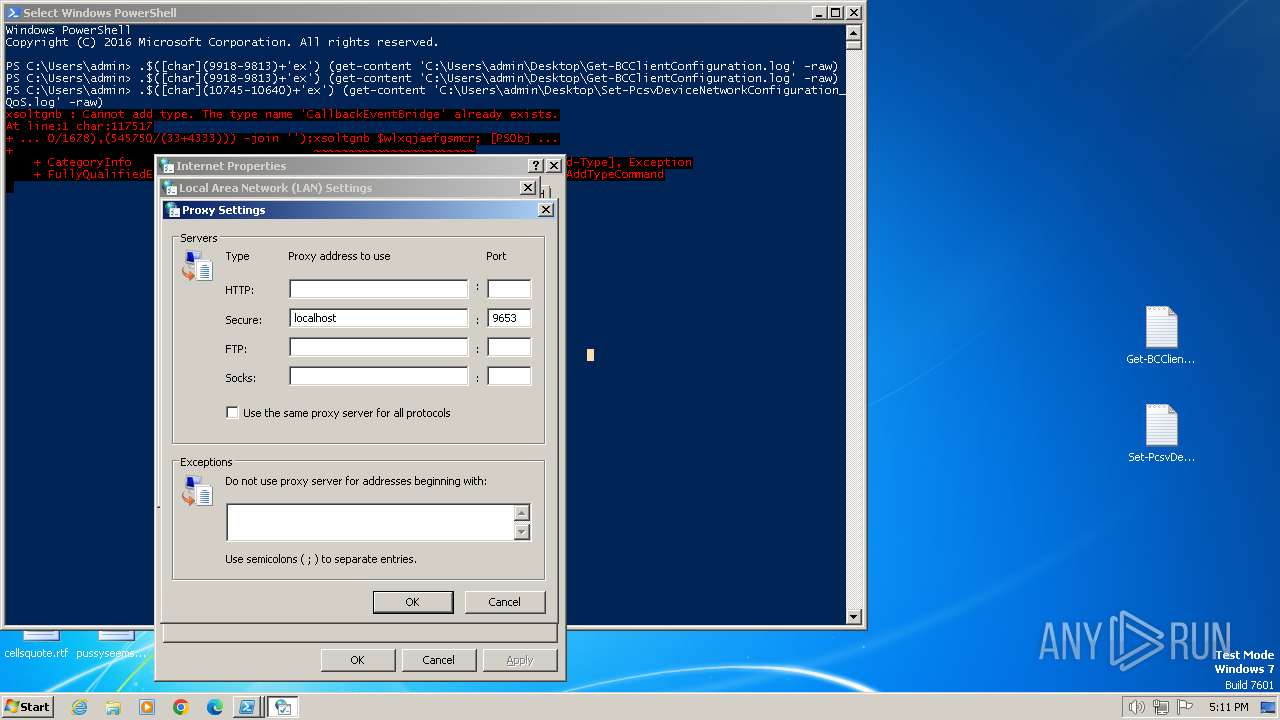
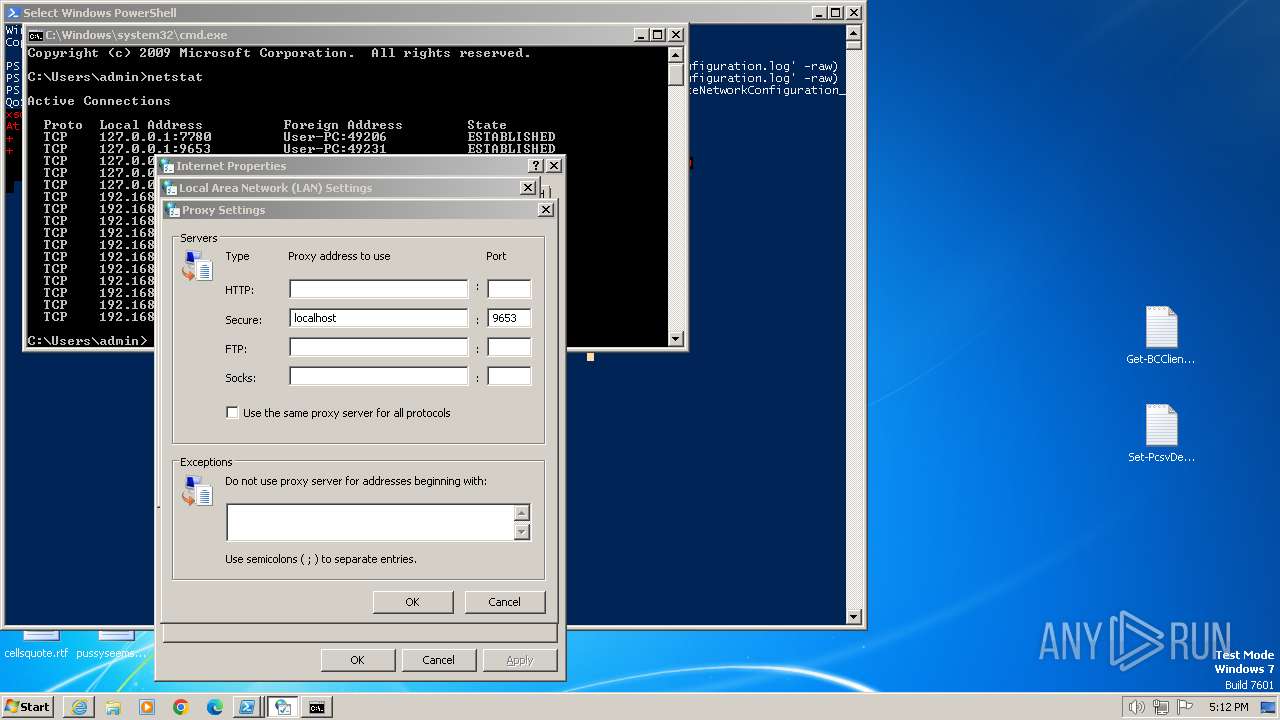
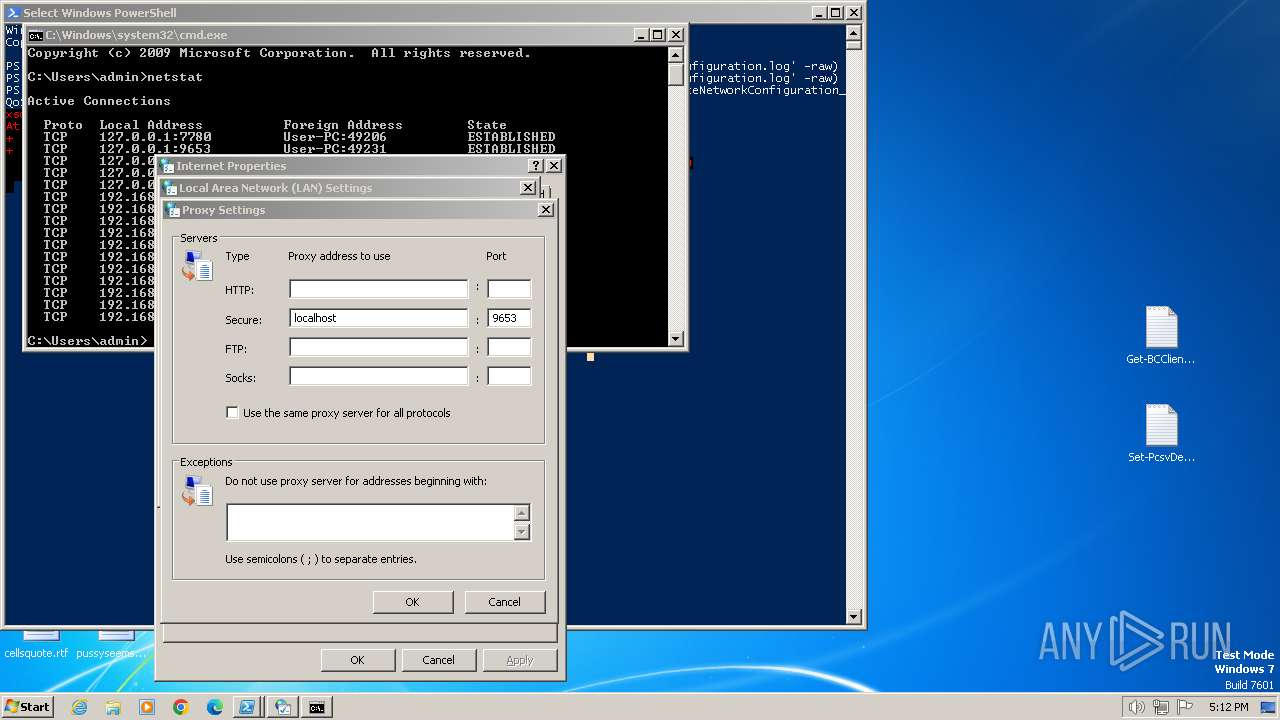
Checks proxy server information
- rundll32.exe (PID: 3252)
- powershell.exe (PID: 3164)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3252)
- dllhost.exe (PID: 2356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
62
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\axow3xac.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 296 | "netsh.exe" firewall add allowedprogram C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe SystemUpdate ENABLE | C:\Windows\System32\netsh.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\axotgmjb.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1556 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES513E.tmp" "c:\Users\admin\AppData\Local\Temp\CSC4513DE09B8D9400097D779B6D24CDC9.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 2340 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2356 | C:\Windows\system32\DllHost.exe /Processid:{A4B07E49-6567-4FB8-8D39-01920E3B2357} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3164 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3252 | "C:\Windows\System32\rundll32.exe" C:\Windows\System32\shell32.dll,Control_RunDLL C:\Windows\System32\inetcpl.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3392 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\d2xt3jmb.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
21 788
Read events
21 031
Write events
751
Delete events
6
Modification events
| (PID) Process: | (2340) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3164) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-1 |
Value: IPsec Relying Party | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-2 |
Value: Provides IPsec based enforcement for Network Access Protection | |||
| (PID) Process: | (296) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-4 |
Value: 1.0 | |||
Executable files
3
Suspicious files
19
Text files
11
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2340 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bvtjdamd.jvm.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Local\Temp\d2xt3jmb.cmdline | text | |
MD5:83CD32018F8553F998985F86629E7962 | SHA256:0D52199DC798F5E90197609889AC761E6208ACEA0D995A59C453324FF111D7D0 | |||
| 3392 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC1A1A8A27E17E41B295FFD1C1F9C33B78.TMP | binary | |
MD5:6339A8E8C686FE63DE4D73251F04213A | SHA256:70BF707BE1D57C1310A79DB01D50A6B6C2A9E626A4D0D3AEE195B263A4554861 | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z6KNB3K1QBF71OJOPYEJ.temp | binary | |
MD5:67BC9011476C87B42100EDEB9660C156 | SHA256:1332A0F6F56E228FD1BF8D1756BBA448C457E74C26A8E2DDA9F0BA80BE65F1BC | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jc5a2zp5.4zc.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:67BC9011476C87B42100EDEB9660C156 | SHA256:1332A0F6F56E228FD1BF8D1756BBA448C457E74C26A8E2DDA9F0BA80BE65F1BC | |||
| 3392 | csc.exe | C:\Users\admin\AppData\Local\Temp\d2xt3jmb.out | text | |
MD5:DA9D3A8A7BE2CF831AF4D8B2A3292B79 | SHA256:B1393DAE441BA86BC3D0FF8F62EB046B8475A70C06021284190D146912F7B6D4 | |||
| 3392 | csc.exe | C:\Users\admin\AppData\Local\Temp\d2xt3jmb.dll | executable | |
MD5:B7DBF14D645777475F8F7E16668CCF55 | SHA256:392C29E15DA764CAB3863726F11433758CE1648DF6824B9B3D269CF3633CF2FB | |||
| 3164 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF18e75d.TMP | binary | |
MD5:67BC9011476C87B42100EDEB9660C156 | SHA256:1332A0F6F56E228FD1BF8D1756BBA448C457E74C26A8E2DDA9F0BA80BE65F1BC | |||
| 3164 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:67BC9011476C87B42100EDEB9660C156 | SHA256:1332A0F6F56E228FD1BF8D1756BBA448C457E74C26A8E2DDA9F0BA80BE65F1BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
15
DNS requests
52
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3164 | powershell.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bc345c6dc22f287a | unknown | compressed | 65.2 Kb | unknown |
3164 | powershell.exe | GET | 200 | 34.117.186.192:80 | http://ipinfo.io/84.17.48.231/city | unknown | text | 18 b | unknown |
3164 | powershell.exe | GET | 200 | 34.117.186.192:80 | http://ipinfo.io/84.17.48.231/region | unknown | text | 6 b | unknown |
3164 | powershell.exe | GET | 200 | 34.117.186.192:80 | http://ipinfo.io/84.17.48.231/country | unknown | text | 3 b | unknown |
3164 | powershell.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | html | 104 b | unknown |
3164 | powershell.exe | GET | 200 | 142.250.186.36:80 | http://www.google.com/robots.txt | unknown | text | 8.28 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3164 | powershell.exe | 193.29.59.200:48974 | mw1qqfw3domqtl4.top | IP-Projects GmbH & Co. KG | DE | unknown |
3164 | powershell.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3164 | powershell.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
3164 | powershell.exe | 193.122.130.0:80 | checkip.dyndns.org | ORACLE-BMC-31898 | US | unknown |
3164 | powershell.exe | 34.117.186.192:80 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
3164 | powershell.exe | 142.250.186.36:80 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
5hf7vjymsa8ubll.top |
| unknown |
5hf7vjymsa8ubll.fun |
| unknown |
5hf7vjymsa8ubll.com |
| unknown |
5hf7vjymsa8ubll.cn |
| unknown |
duz797wnbs3bb7o.top |
| unknown |
duz797wnbs3bb7o.fun |
| unknown |
duz797wnbs3bb7o.com |
| unknown |
duz797wnbs3bb7o.cn |
| unknown |
16rxmbr783v6m69.top |
| unknown |
16rxmbr783v6m69.fun |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3164 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
3164 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
3164 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
1080 | svchost.exe | Misc activity | AV INFO Query to checkip.dyndns. Domain |
3164 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
3164 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - checkip.dyndns.org |
2 ETPRO signatures available at the full report