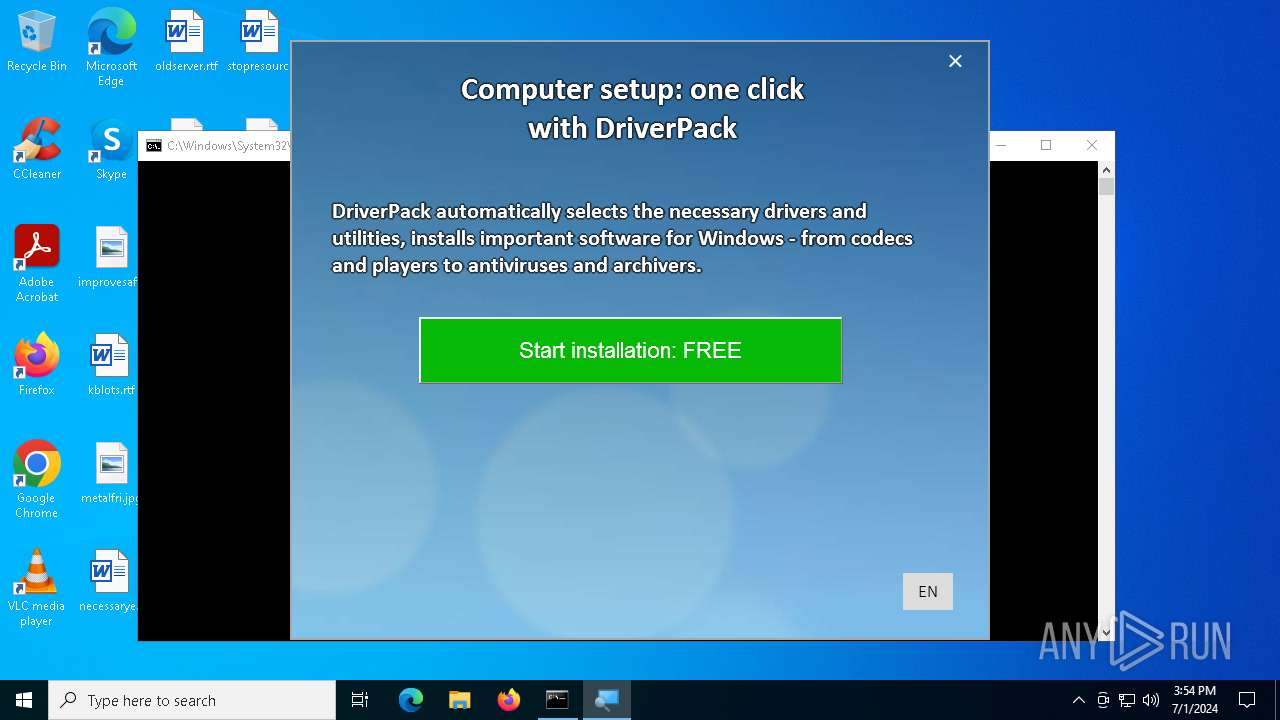
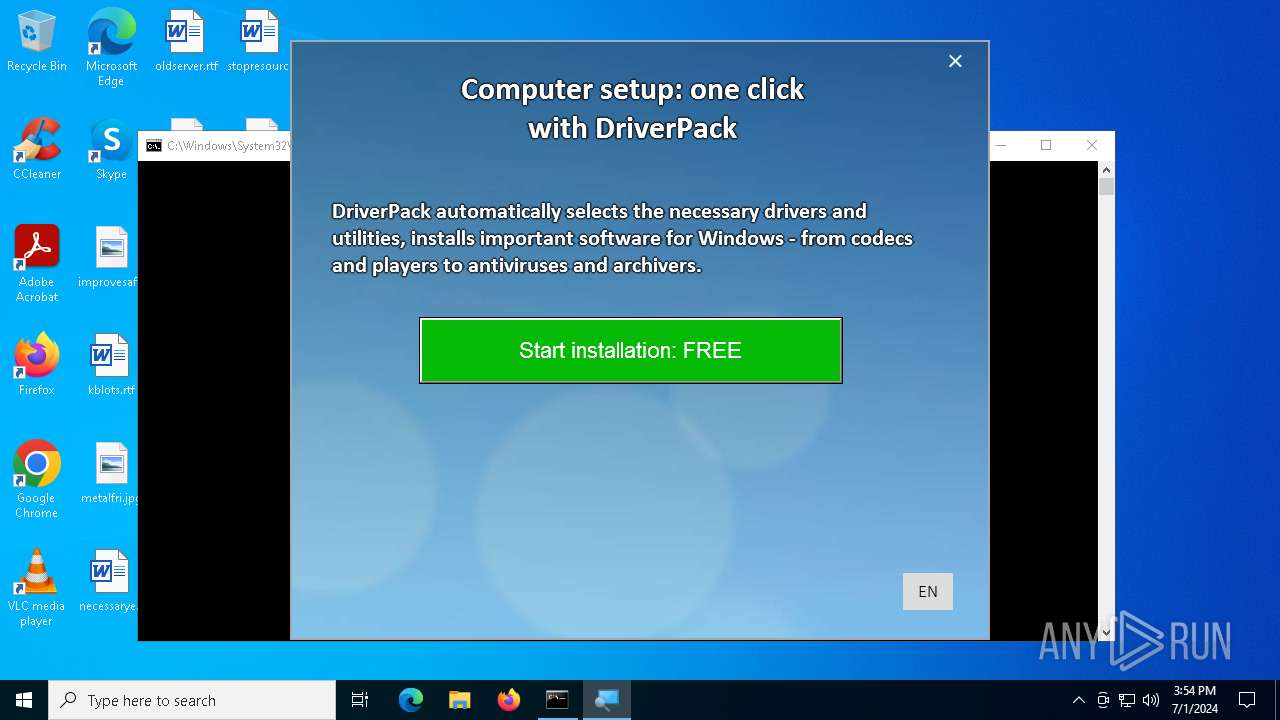
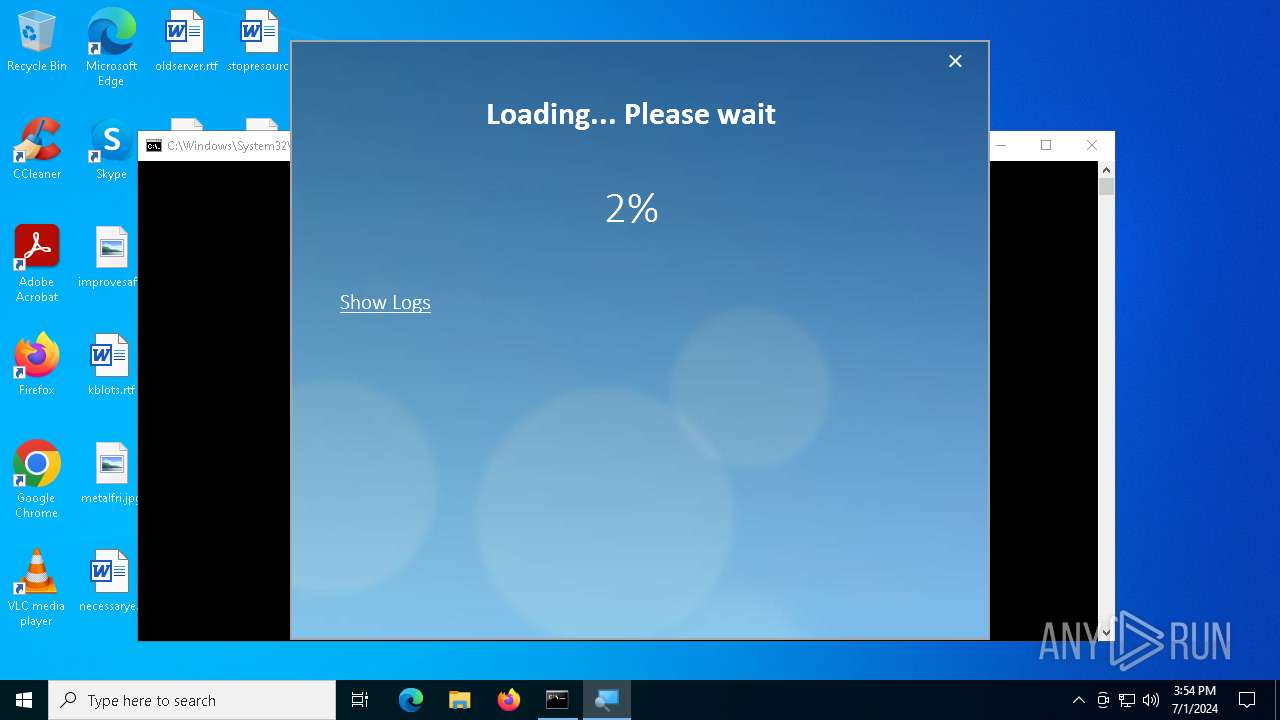
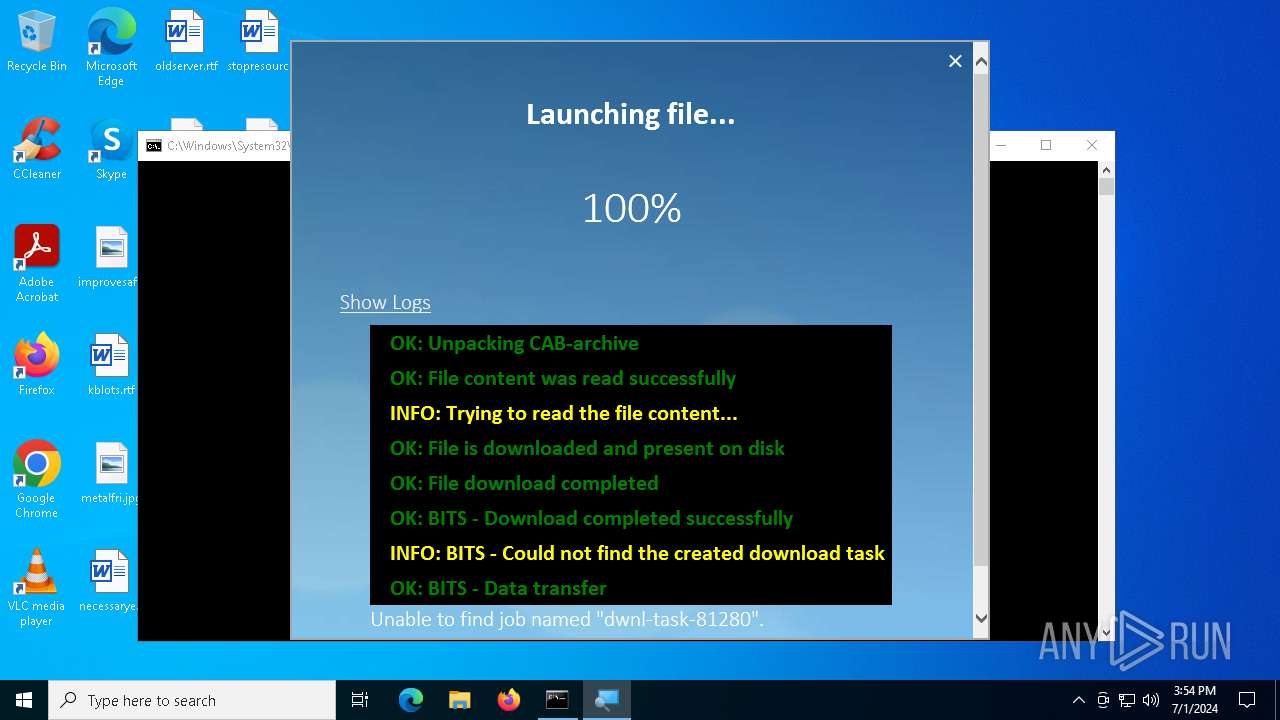
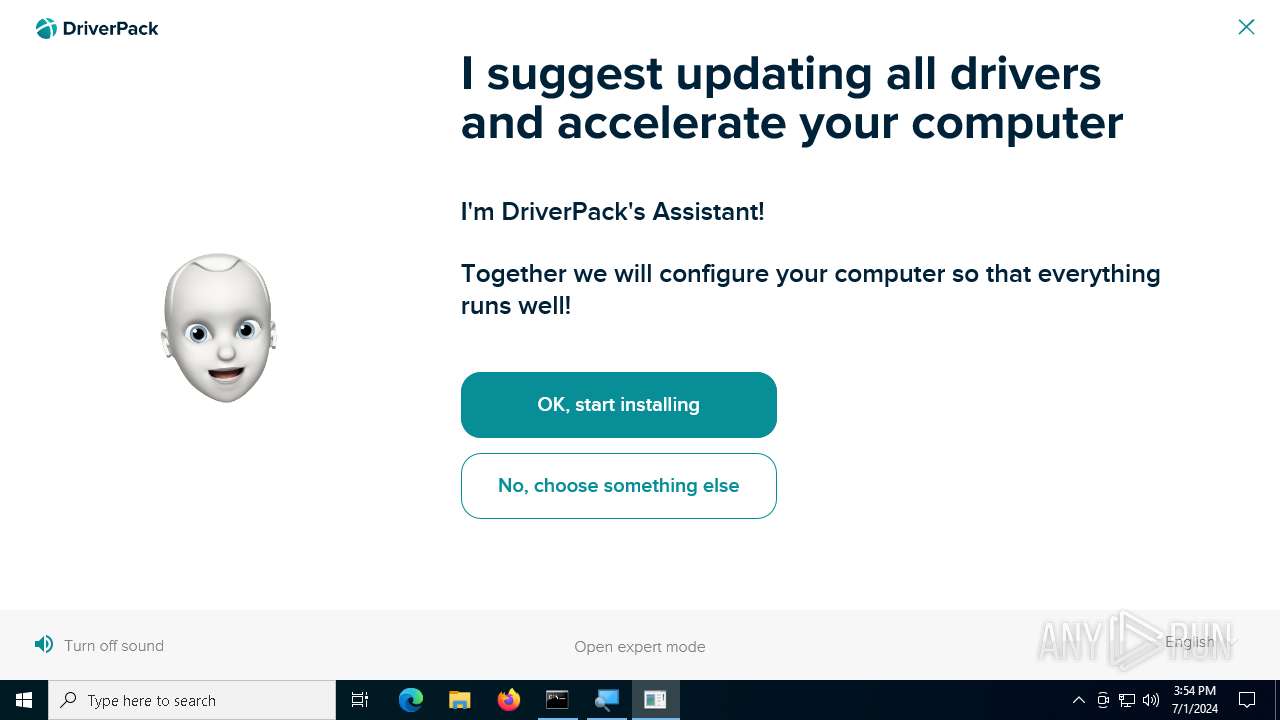
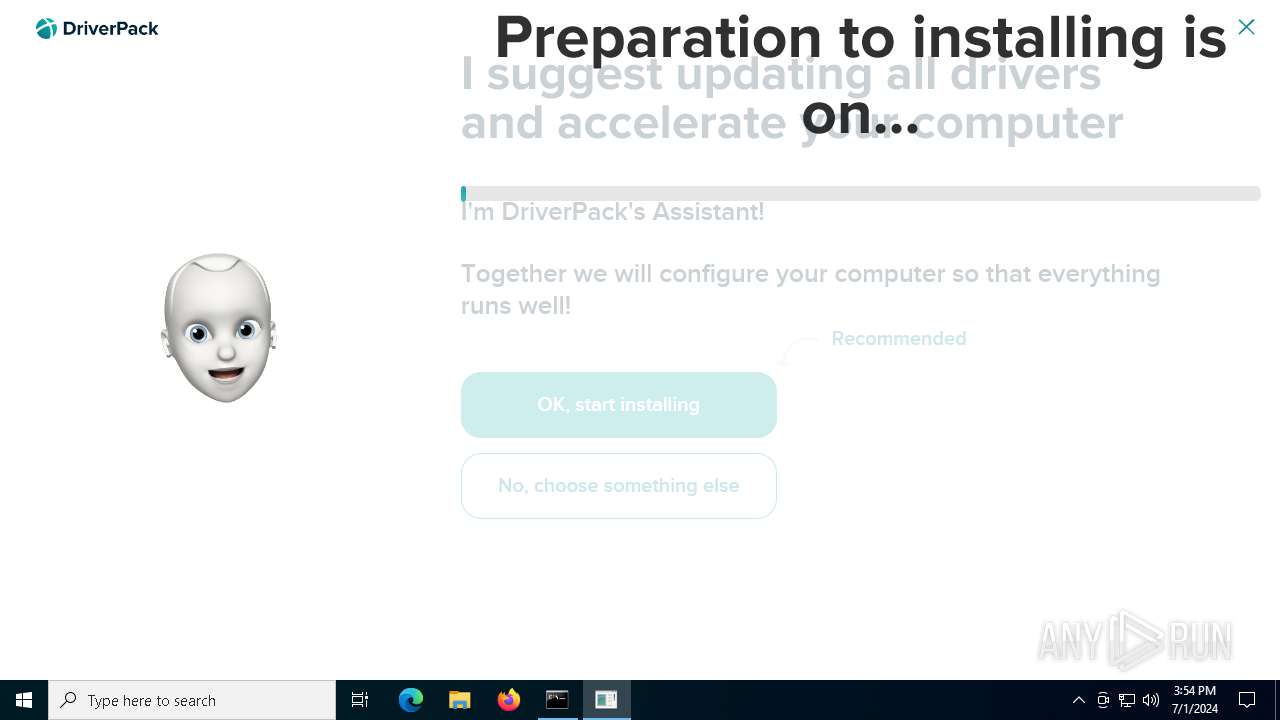
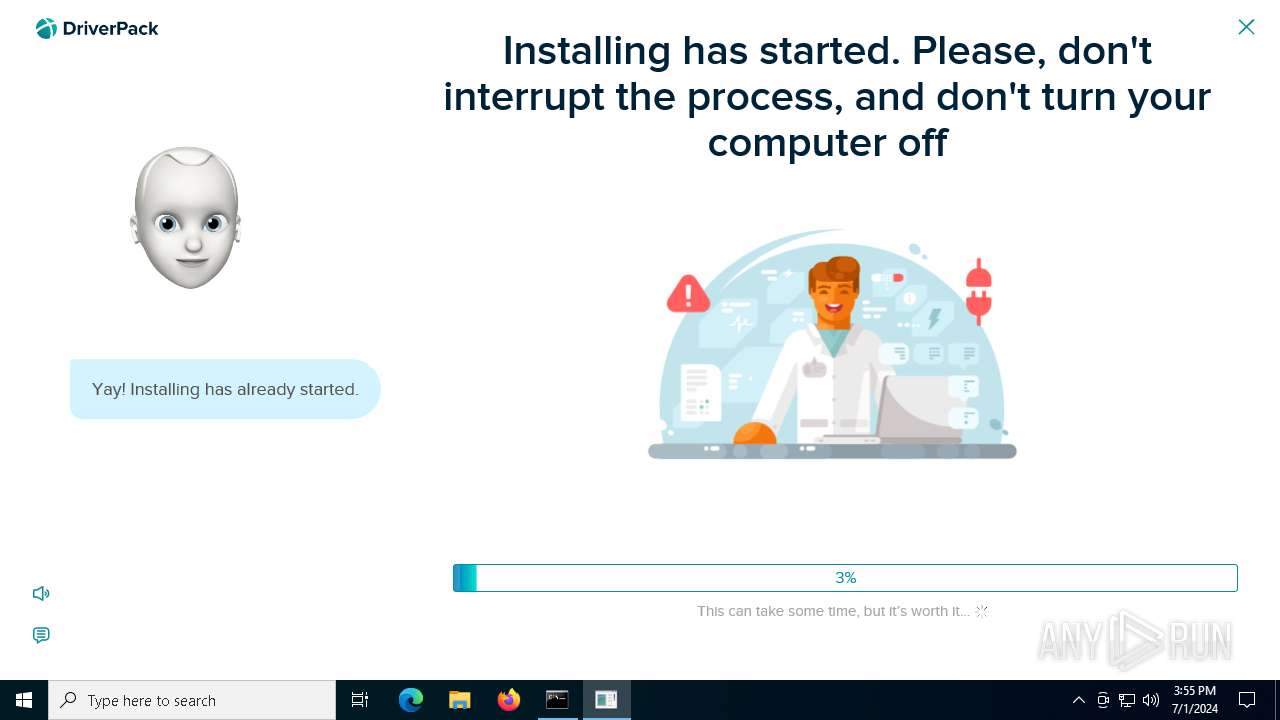
| File name: | PROD_Start_DriverPack.hta |
| Full analysis: | https://app.any.run/tasks/ab3e7775-1bee-4c6b-9fdc-f1d8b4eb2281 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | July 01, 2024, 15:54:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 (with BOM) text, with CRLF line terminators |
| MD5: | DDA846A4704EFC2A03E1F8392E6F1FFC |
| SHA1: | 387171A06EEE5A76AAEDC3664385BB89703CF6DF |
| SHA256: | E9DC9648D8FB7D943431459F49A7D9926197C2D60B3C2B6A58294FD75B672B25 |
| SSDEEP: | 48:uzK1vpKljUYpuqgs1pxXzOSRByHCpmF50bxxdW6kI:qiIT3BjNOSOGmF50tKA |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 776)
- mshta.exe (PID: 6836)
- mshta.exe (PID: 6772)
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 5504)
Drops the executable file immediately after the start
- expand.exe (PID: 6488)
- 7za.exe (PID: 6260)
- csc.exe (PID: 1120)
- aria2c.exe (PID: 3688)
Bypass execution policy to execute commands
- powershell.exe (PID: 7164)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6448)
Starts Visual C# compiler
- powershell.exe (PID: 7164)
SUSPICIOUS
Found strings related to reading or modifying Windows Defender settings
- mshta.exe (PID: 776)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6244)
- cmd.exe (PID: 6448)
Query Microsoft Defender status
- mshta.exe (PID: 776)
- cmd.exe (PID: 6244)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5504)
- cmd.exe (PID: 6440)
- cmd.exe (PID: 6616)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 6932)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 6528)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 6488)
- cmd.exe (PID: 7024)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 6680)
- cmd.exe (PID: 6984)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 6464)
- cmd.exe (PID: 6716)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 6456)
- cmd.exe (PID: 6508)
- cmd.exe (PID: 6844)
Cmdlet gets the status of antimalware software installed on the computer
- cmd.exe (PID: 6244)
The process verifies whether the antivirus software is installed
- mshta.exe (PID: 776)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 776)
- cmd.exe (PID: 6152)
- mshta.exe (PID: 6836)
Executable content was dropped or overwritten
- expand.exe (PID: 6488)
- 7za.exe (PID: 6260)
- csc.exe (PID: 1120)
- aria2c.exe (PID: 3688)
Drops 7-zip archiver for unpacking
- expand.exe (PID: 6488)
- 7za.exe (PID: 6260)
The executable file from the user directory is run by the CMD process
- 7za.exe (PID: 6260)
- driverpack-wget.exe (PID: 6816)
- driverpack-wget.exe (PID: 7104)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 6444)
- driverpack-wget.exe (PID: 3680)
- driverpack-wget.exe (PID: 376)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 6872)
- driverpack-wget.exe (PID: 6440)
- driverpack-wget.exe (PID: 7036)
- driverpack-wget.exe (PID: 4104)
- driverpack-wget.exe (PID: 1968)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 5792)
- driverpack-wget.exe (PID: 4020)
- driverpack-wget.exe (PID: 2140)
- driverpack-wget.exe (PID: 6540)
- driverpack-wget.exe (PID: 6444)
- driverpack-wget.exe (PID: 6624)
- driverpack-wget.exe (PID: 2492)
- aria2c.exe (PID: 6420)
- aria2c.exe (PID: 2932)
- driverpack-wget.exe (PID: 376)
- driverpack-wget.exe (PID: 7716)
- driverpack-wget.exe (PID: 7264)
- aria2c.exe (PID: 3688)
- driverpack-wget.exe (PID: 7192)
- driverpack-wget.exe (PID: 7280)
- driverpack-wget.exe (PID: 7876)
- driverpack-wget.exe (PID: 7760)
- driverpack-wget.exe (PID: 7776)
- driverpack-wget.exe (PID: 7896)
- driverpack-wget.exe (PID: 7268)
- aria2c.exe (PID: 6948)
- aria2c.exe (PID: 2488)
Application launched itself
- cmd.exe (PID: 6152)
- mshta.exe (PID: 776)
Process drops legitimate windows executable
- 7za.exe (PID: 6260)
Unpacks CAB file
- expand.exe (PID: 6488)
Executing commands from a ".bat" file
- mshta.exe (PID: 776)
- cmd.exe (PID: 6152)
Executing commands from ".cmd" file
- mshta.exe (PID: 6836)
Changes internet zones settings
- mshta.exe (PID: 6836)
The process hide an interactive prompt from the user
- cmd.exe (PID: 6448)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6448)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 6448)
Get information on the list of running processes
- cmd.exe (PID: 6448)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6752)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6448)
Uses .NET C# to load dll
- powershell.exe (PID: 7164)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 6952)
Starts application with an unusual extension
- cmd.exe (PID: 6592)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6592)
INFO
Reads Internet Explorer settings
- mshta.exe (PID: 776)
- mshta.exe (PID: 6836)
- mshta.exe (PID: 6772)
Checks proxy server information
- mshta.exe (PID: 776)
- mshta.exe (PID: 6836)
- mshta.exe (PID: 6772)
Uses BITSADMIN.EXE
- cmd.exe (PID: 6616)
- cmd.exe (PID: 6440)
- cmd.exe (PID: 6932)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 6528)
- cmd.exe (PID: 7024)
- cmd.exe (PID: 6488)
- cmd.exe (PID: 6680)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 6984)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 6456)
- cmd.exe (PID: 6464)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 6716)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 6508)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 6844)
Checks supported languages
- expand.exe (PID: 6488)
- 7za.exe (PID: 6260)
- csc.exe (PID: 1120)
- cvtres.exe (PID: 6064)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 6816)
- driverpack-wget.exe (PID: 6444)
- driverpack-wget.exe (PID: 7104)
- driverpack-wget.exe (PID: 3680)
- driverpack-wget.exe (PID: 376)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 1968)
- driverpack-wget.exe (PID: 6872)
- driverpack-wget.exe (PID: 4104)
- driverpack-wget.exe (PID: 6440)
- driverpack-wget.exe (PID: 7036)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 4020)
- driverpack-wget.exe (PID: 5792)
- driverpack-wget.exe (PID: 2140)
Reads the machine GUID from the registry
- expand.exe (PID: 6488)
- csc.exe (PID: 1120)
Create files in a temporary directory
- expand.exe (PID: 6488)
- 7za.exe (PID: 6260)
- csc.exe (PID: 1120)
- cvtres.exe (PID: 6064)
- driverpack-wget.exe (PID: 6816)
- driverpack-wget.exe (PID: 7104)
- driverpack-wget.exe (PID: 6444)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 3680)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 4104)
- driverpack-wget.exe (PID: 6872)
- driverpack-wget.exe (PID: 7036)
- driverpack-wget.exe (PID: 1968)
- driverpack-wget.exe (PID: 6440)
- driverpack-wget.exe (PID: 376)
- driverpack-wget.exe (PID: 2140)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 5792)
- driverpack-wget.exe (PID: 4020)
Reads the computer name
- 7za.exe (PID: 6260)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 6816)
- driverpack-wget.exe (PID: 7104)
- driverpack-wget.exe (PID: 3680)
- driverpack-wget.exe (PID: 376)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 6444)
- driverpack-wget.exe (PID: 6872)
- driverpack-wget.exe (PID: 4104)
- driverpack-wget.exe (PID: 6440)
- driverpack-wget.exe (PID: 7036)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 1968)
- driverpack-wget.exe (PID: 4020)
- driverpack-wget.exe (PID: 5792)
- driverpack-wget.exe (PID: 2140)
Creates files or folders in the user directory
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 6816)
- driverpack-wget.exe (PID: 7104)
- driverpack-wget.exe (PID: 6444)
- driverpack-wget.exe (PID: 3680)
- driverpack-wget.exe (PID: 376)
- driverpack-wget.exe (PID: 2176)
- driverpack-wget.exe (PID: 6440)
- driverpack-wget.exe (PID: 4104)
- driverpack-wget.exe (PID: 1968)
- driverpack-wget.exe (PID: 6872)
- driverpack-wget.exe (PID: 7036)
- driverpack-wget.exe (PID: 3020)
- driverpack-wget.exe (PID: 5792)
- driverpack-wget.exe (PID: 4020)
- driverpack-wget.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
EXIF
HTML
| Title: | Starting... |
|---|---|
| HTTPEquivXUACompatible: | IE=7 |
Total processes
405
Monitored processes
262
Malicious processes
9
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | "tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/EXPERT-DRIVERS-2.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_21286.log" | C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\Tools\driverpack-wget.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 376 | "tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/EXPERT-PROGRAMS_CHECKBOX_USED-1.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_63398.log" | C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\Tools\driverpack-wget.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 776 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\PROD_Start_DriverPack.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/EXPERT-PROGRAMS_CHECKBOX_USED-1.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_63398.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_63398.txt"" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1120 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\aay5h20j\aay5h20j.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/EXPERT-PROTECT-3.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_54182.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_54182.txt"" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1164 | rundll32 kernel32,Sleep | C:\Windows\SysWOW64\rundll32.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1740 | "C:\Windows\System32\cmd.exe" /c ""tools\aria2c.exe" "http://dl.driverpack.io/soft/OperaBlink64.exe.torrent" --dir="C:\Users\admin\AppData\Roaming\DRPSu\PROGRAMS" --quiet --continue --min-split-size=1M --follow-torrent=true --check-integrity --seed-time=0 --bt-stop-timeout=120 || echo Done & call echo Done %^errorLevel% > "C:\Users\admin\AppData\Roaming\DRPSu\temp\run_command_7872.txt"" | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1968 | "tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/CONTINUOUS-1.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_25119.log" | C:\Users\admin\AppData\Local\Temp\beetle-cab\DriverPack\Tools\driverpack-wget.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
48 220
Read events
47 985
Write events
235
Delete events
0
Modification events
| (PID) Process: | (3532) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | htafile_.hta |
Value: 0 | |||
| (PID) Process: | (3532) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.hta\OpenWithProgids |
| Operation: | write | Name: | htafile |
Value: | |||
| (PID) Process: | (3532) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3532) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3532) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3532) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (776) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
13
Suspicious files
125
Text files
642
Unknown types
77
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\style[1].css | text | |
MD5:CE40483E494B033AA4A204080ABB54DA | SHA256:1FC4501622BAFC4560C28442D01F708579F26AFBB88229328B2CE7E83A2D36A8 | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\missing-scripts-detector[1].js | txt | |
MD5:5BB70933199563BD95A85E9D58D0920B | SHA256:915A03DDD5D887CE43185A21FD9927FFCFC6E8F373D80D6FB0BFE96E65C029CD | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\client_ip[1].js | text | |
MD5:789A523148EA70896D2629BF15D3D55C | SHA256:6C07D5D12B457393F5ED69D3BDB0F9580365CABAE2C1B329A8D9B68FC9539714 | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\1[1].js | txt | |
MD5:B2AEEF062DB55284085A863B0FCF48A5 | SHA256:C79C9F0F44CA9EF9E84346BB88C12187C3F0DDE18F6C8FA83A54D1D89CBB0CB7 | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\4[1].js | txt | |
MD5:B21247B2428E6D9F72405EB1A2F5F75C | SHA256:9DDF298484BD63F71CFF04DD81E00913266FA8D71793E2C26F3B7B215067812C | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\3[1].js | txt | |
MD5:CC9E168614A8D567352E24F970CA21E0 | SHA256:578820B83CD0244FFC068665C531A8C7D633F890A927A682A1708B84B7A08702 | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\step1_av[1].htm | html | |
MD5:1FAE5694001ACA3836F123E1A89AFD3D | SHA256:2240EF798569427F1B37E16BF630D7BD5E415F5835CA9FDF730E1F063721291B | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\2[1].js | txt | |
MD5:22D3D08CBEC1245327396FAA5B60725A | SHA256:923CBFF9E47CA64E292A8932A13ED11F9E4A488DC20775181B010231F15E3E26 | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\statistics[1].js | txt | |
MD5:0701E8CE6920DA0050B219769314E144 | SHA256:5D53ECD246441E19CD7B305749C822132476170938E5B7A673856B1FD29708BF | |||
| 776 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\5[1].js | txt | |
MD5:50B3202ACF32B140238D284FD2F9CE17 | SHA256:F173F32E6CE3B40E56CC2B41EA8F6B15555F2B38D069A39F561C40EBC4F51EDA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
360
TCP/UDP connections
114
DNS requests
49
Threats
241
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/step1_av.html | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/style.css | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/missing-scripts-detector.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/client_ip.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/1.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/2.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/3.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/4.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/variables/5.js | unknown | — | — | unknown |
776 | mshta.exe | GET | 200 | 54.220.192.176:80 | http://dwrapper-prod.herokuapp.com/bin/src/statistics.js | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2476 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3188 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1452 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
776 | mshta.exe | 54.220.192.176:80 | dwrapper-prod.herokuapp.com | AMAZON-02 | IE | unknown |
776 | mshta.exe | 3.126.133.169:80 | exampledd.matomo.cloud | AMAZON-02 | DE | unknown |
4656 | SearchApp.exe | 92.123.104.6:443 | — | Akamai International B.V. | DE | unknown |
1544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dwrapper-prod.herokuapp.com |
| unknown |
exampledd.matomo.cloud |
| unknown |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dwrapper-dev.herokuapp.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
776 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
776 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
776 | mshta.exe | Potentially Bad Traffic | ET HUNTING PowerShell DownloadFile Command Common In Powershell Stagers |
2168 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
2168 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
6836 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
6836 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2168 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
2168 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
6836 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
7 ETPRO signatures available at the full report