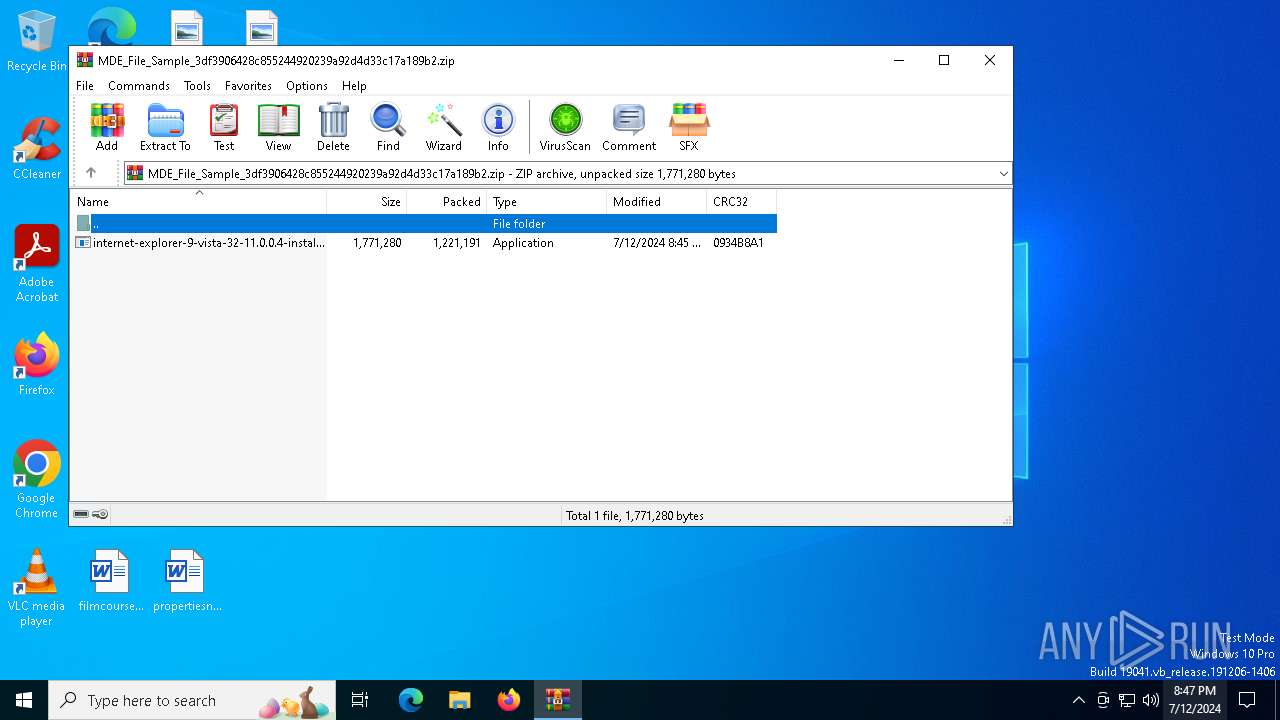
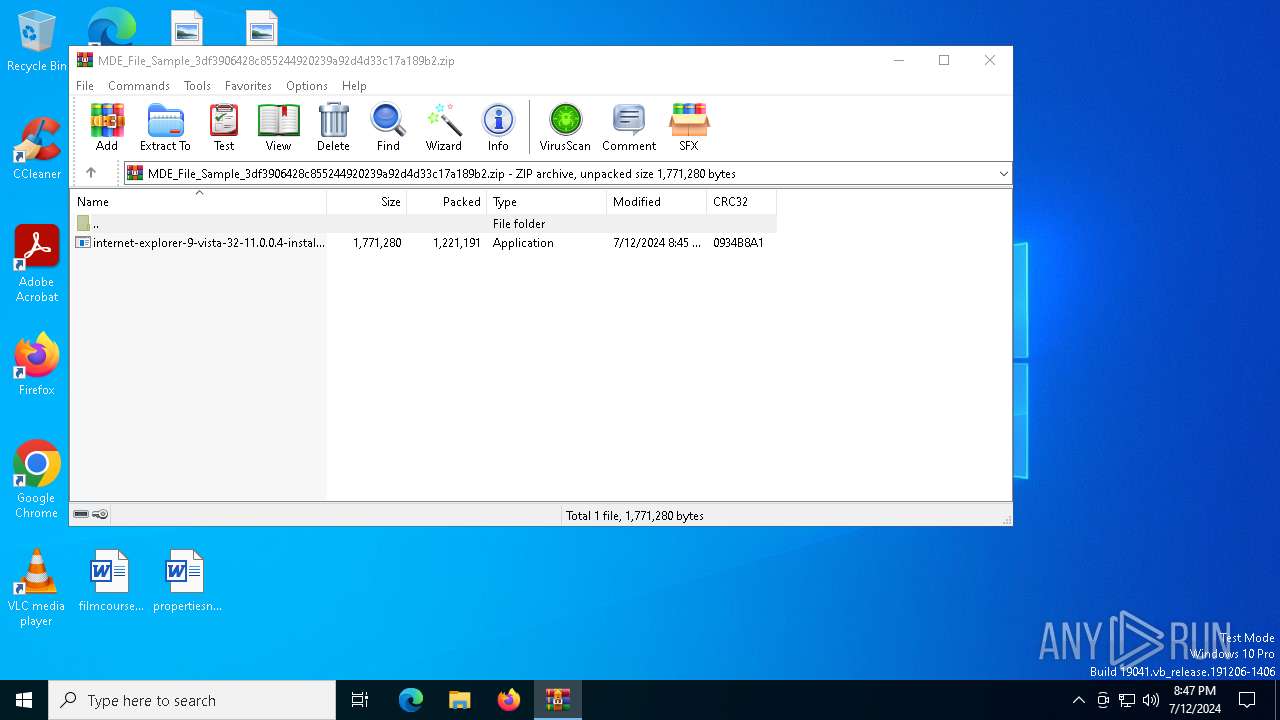
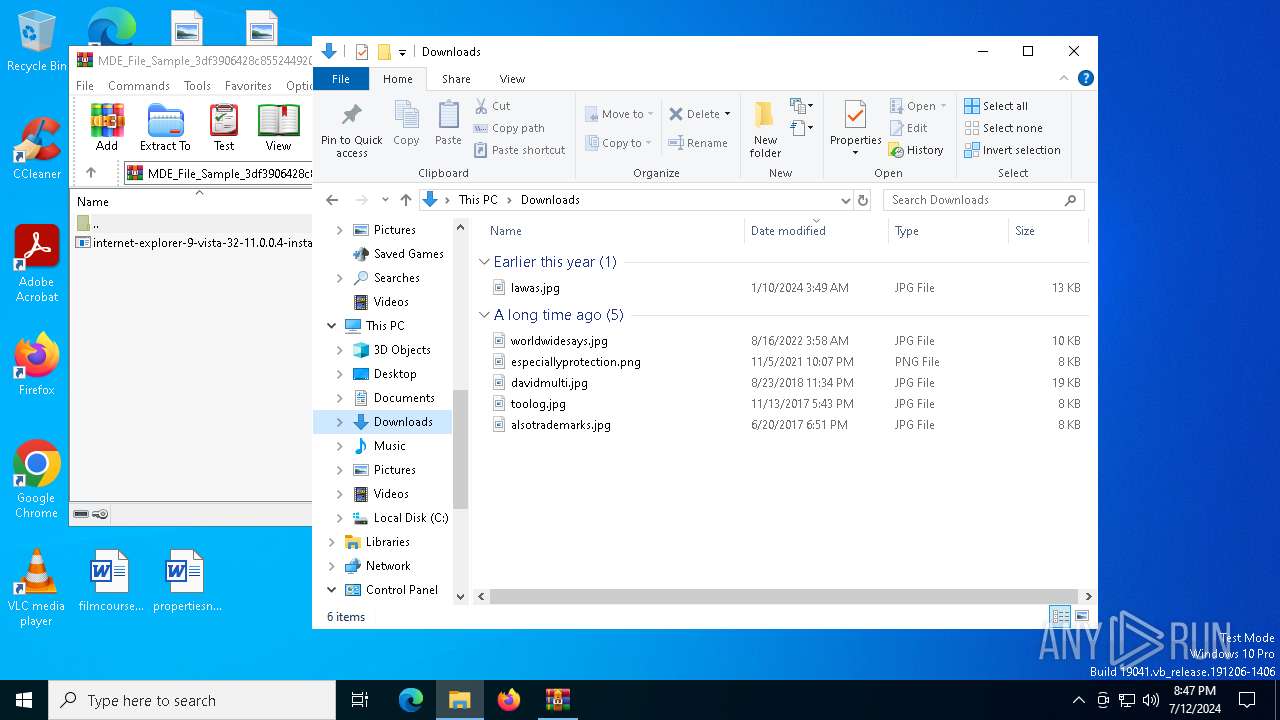
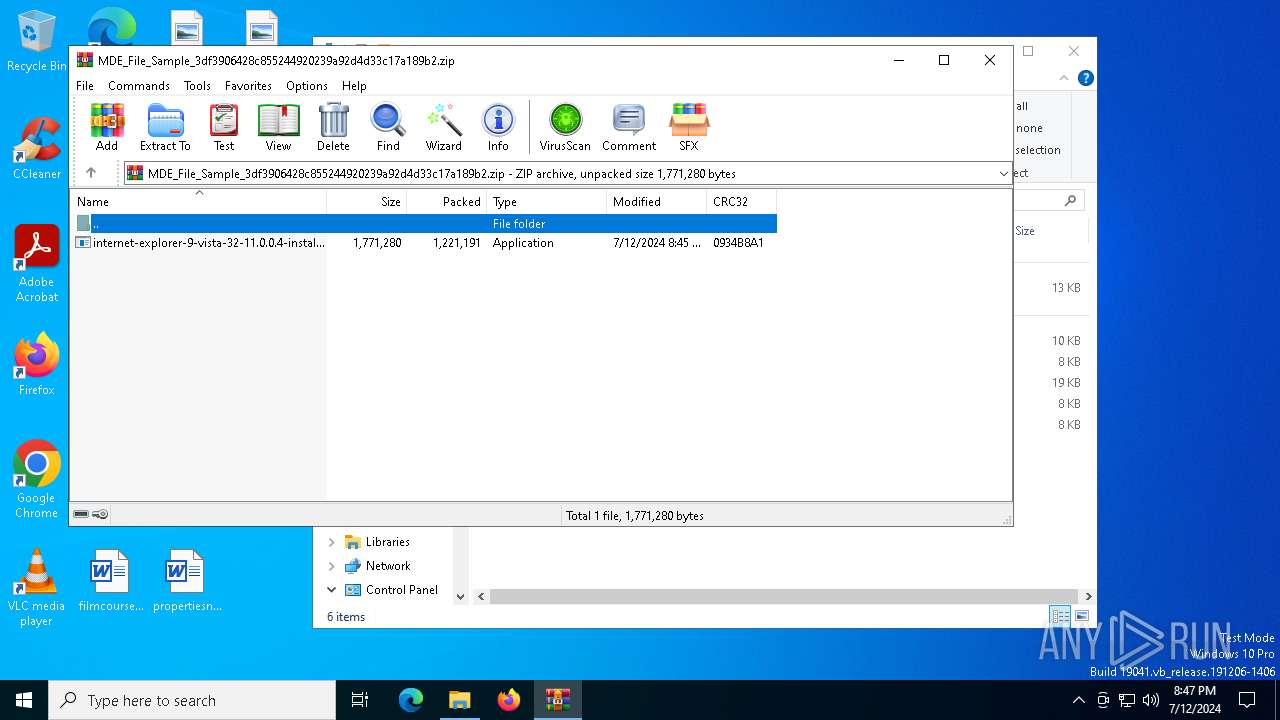
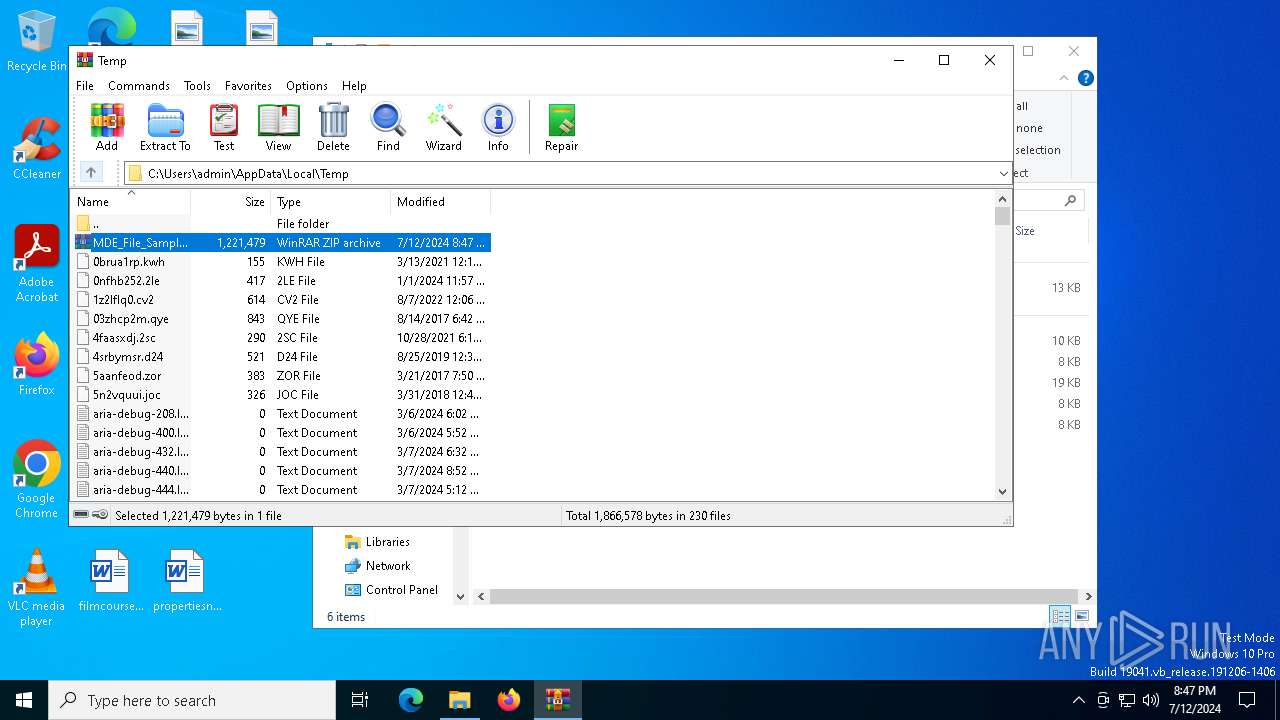
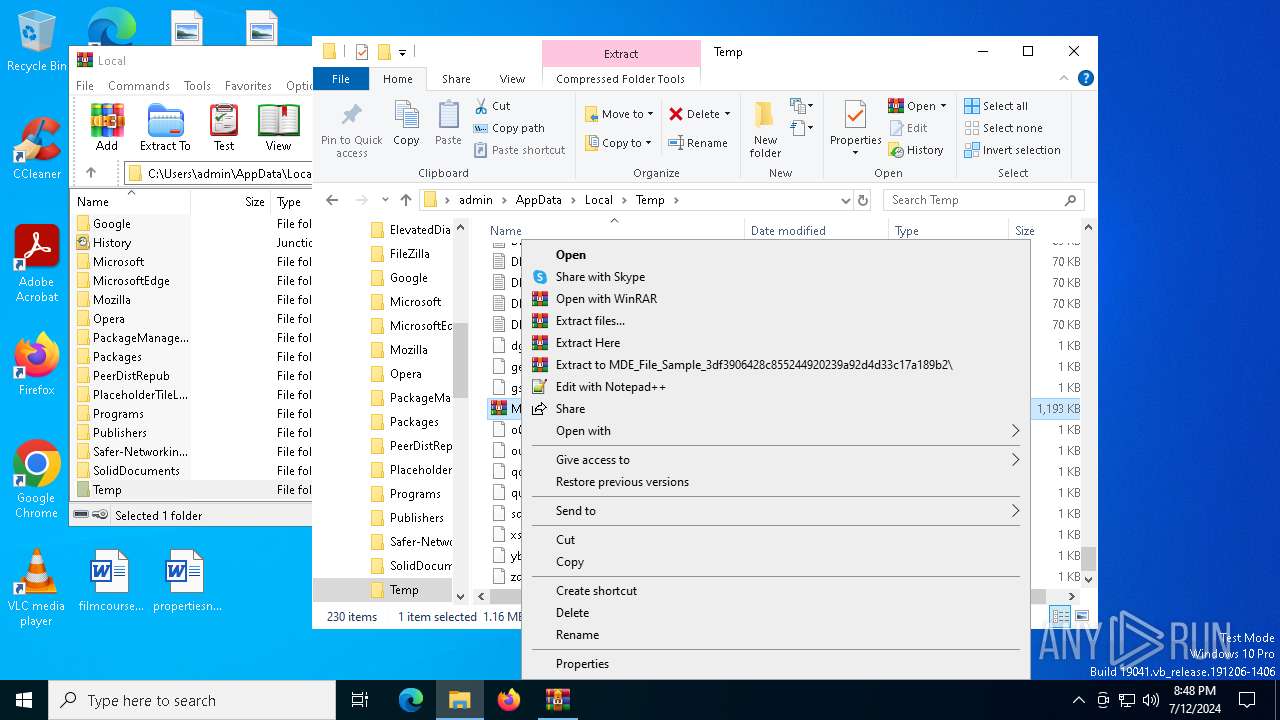
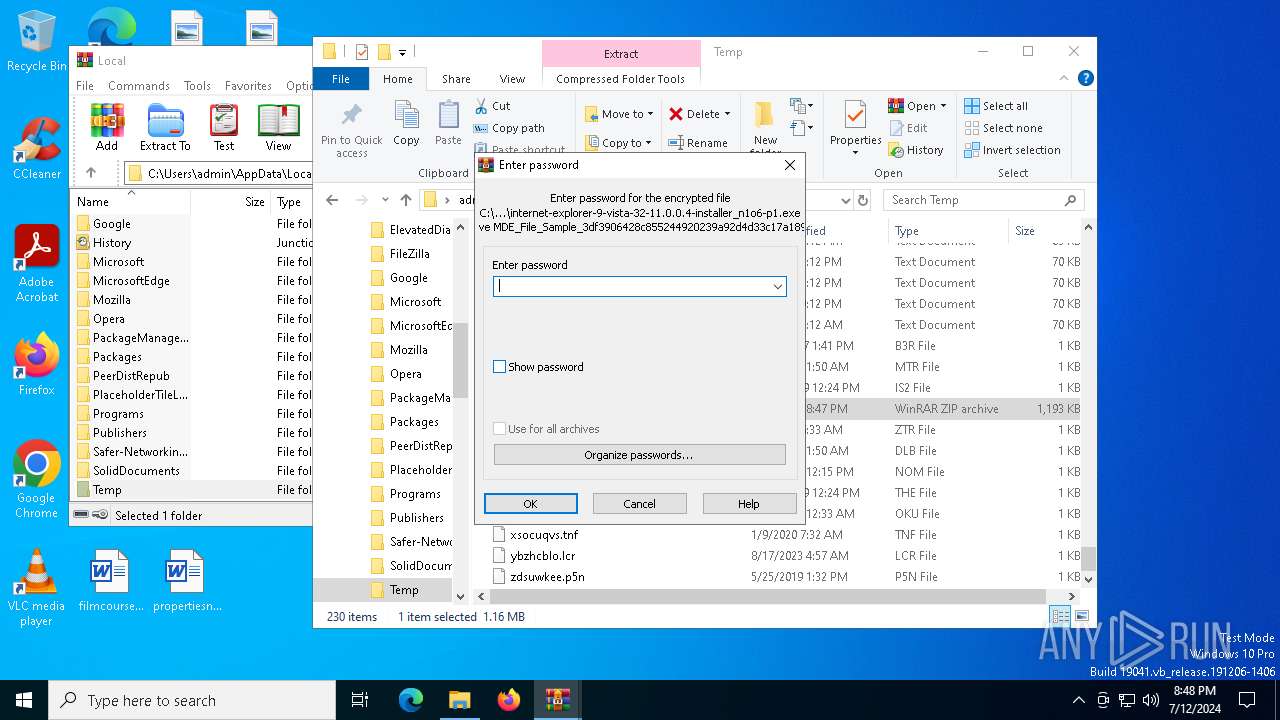
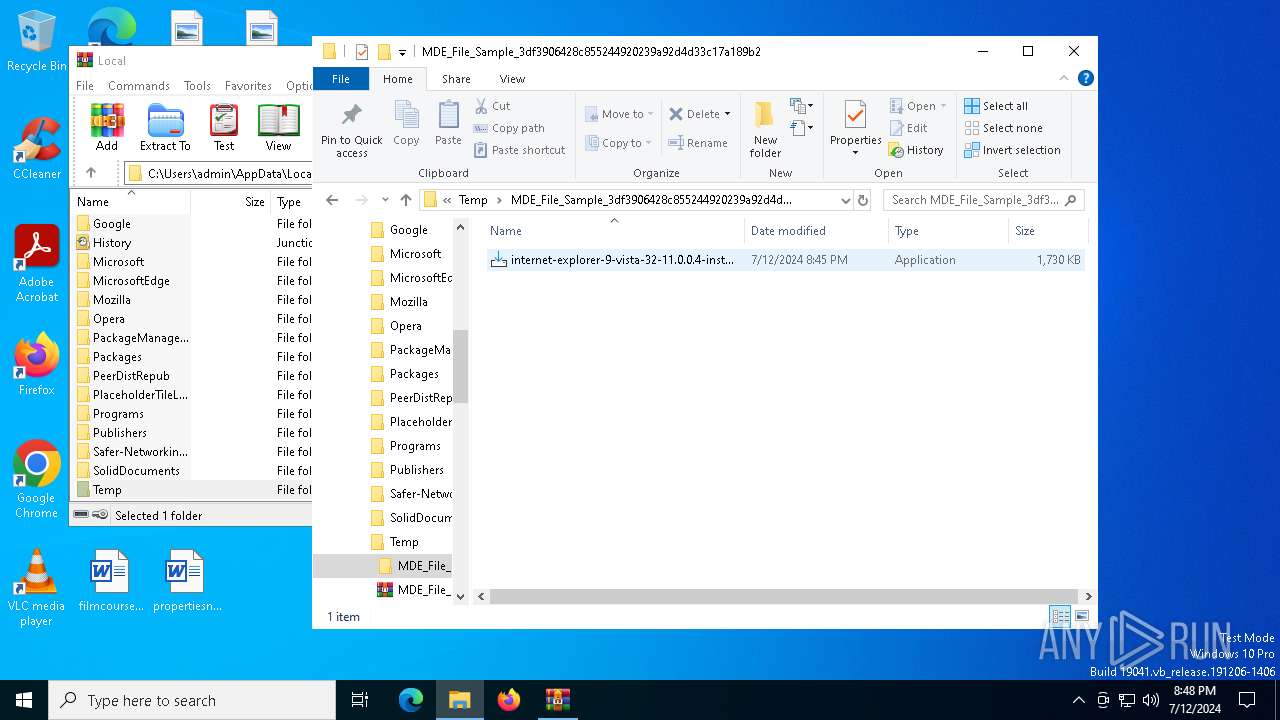
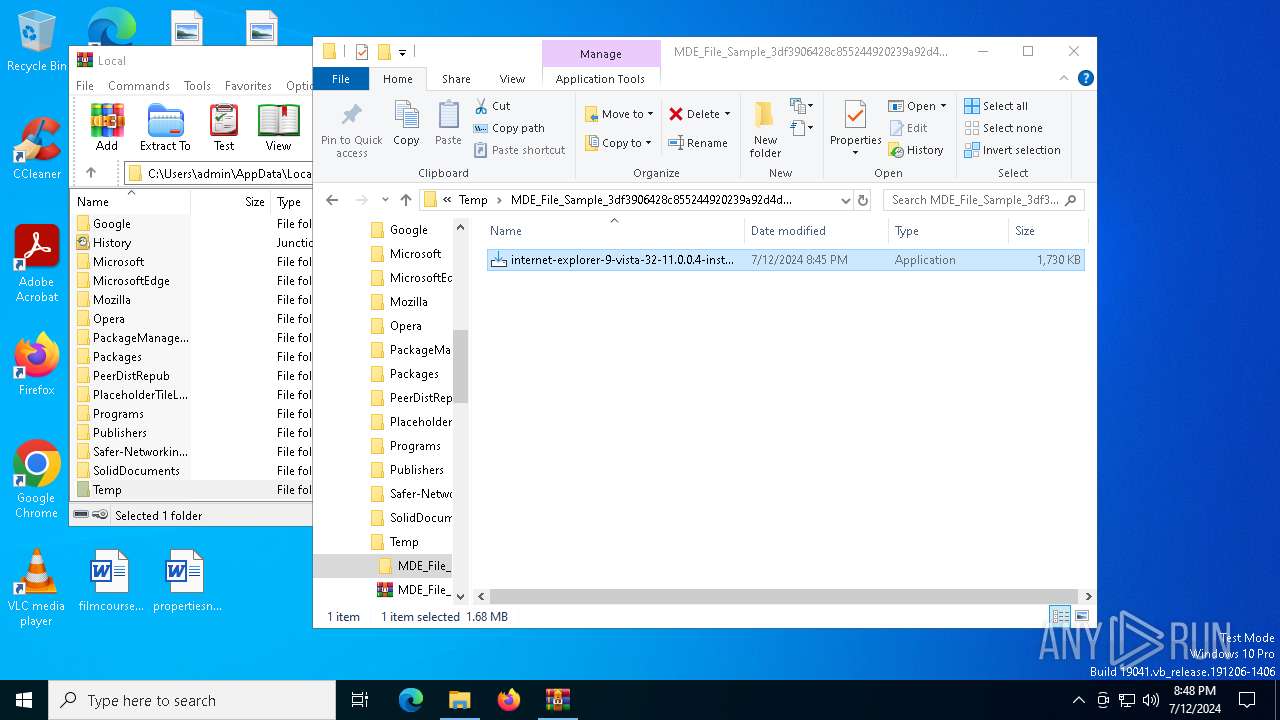
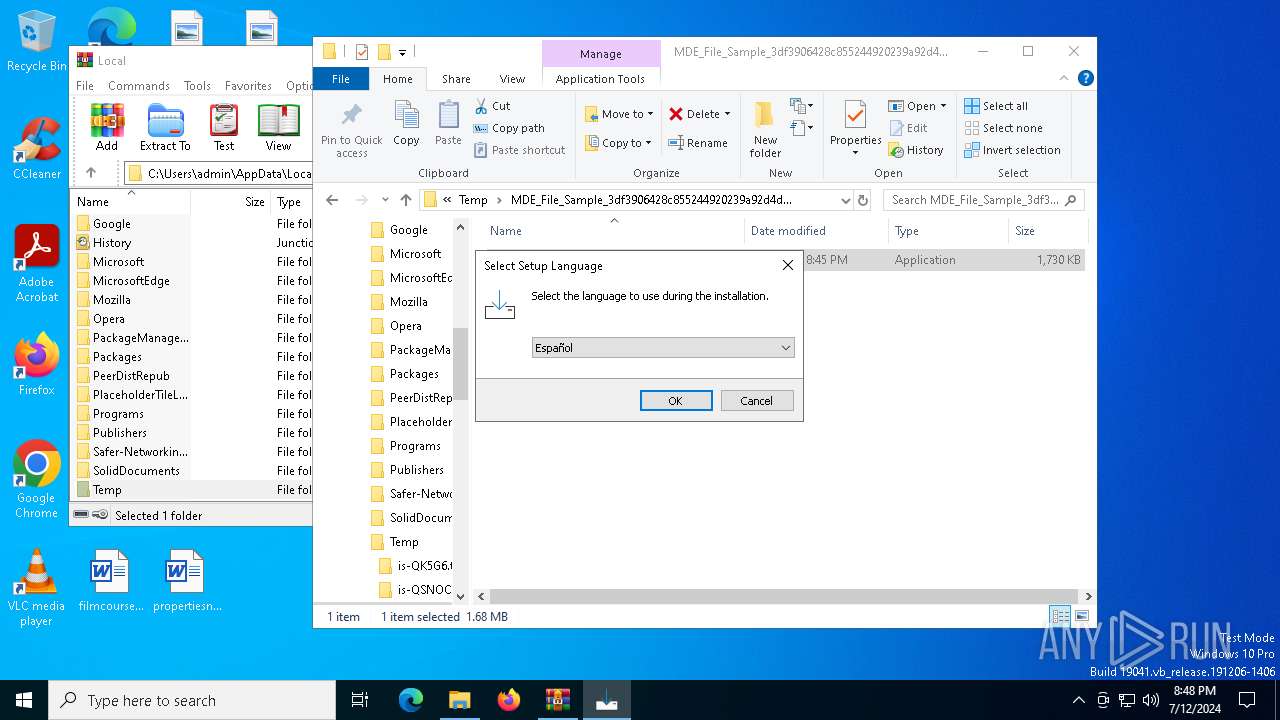
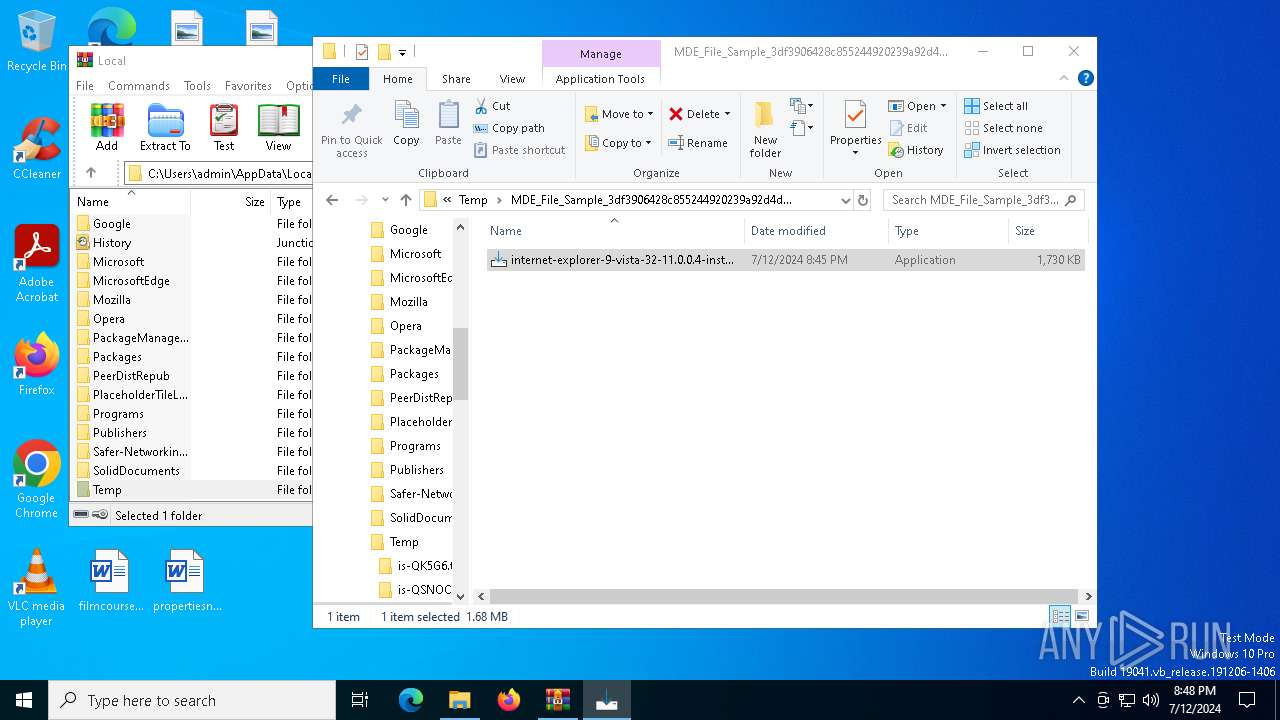
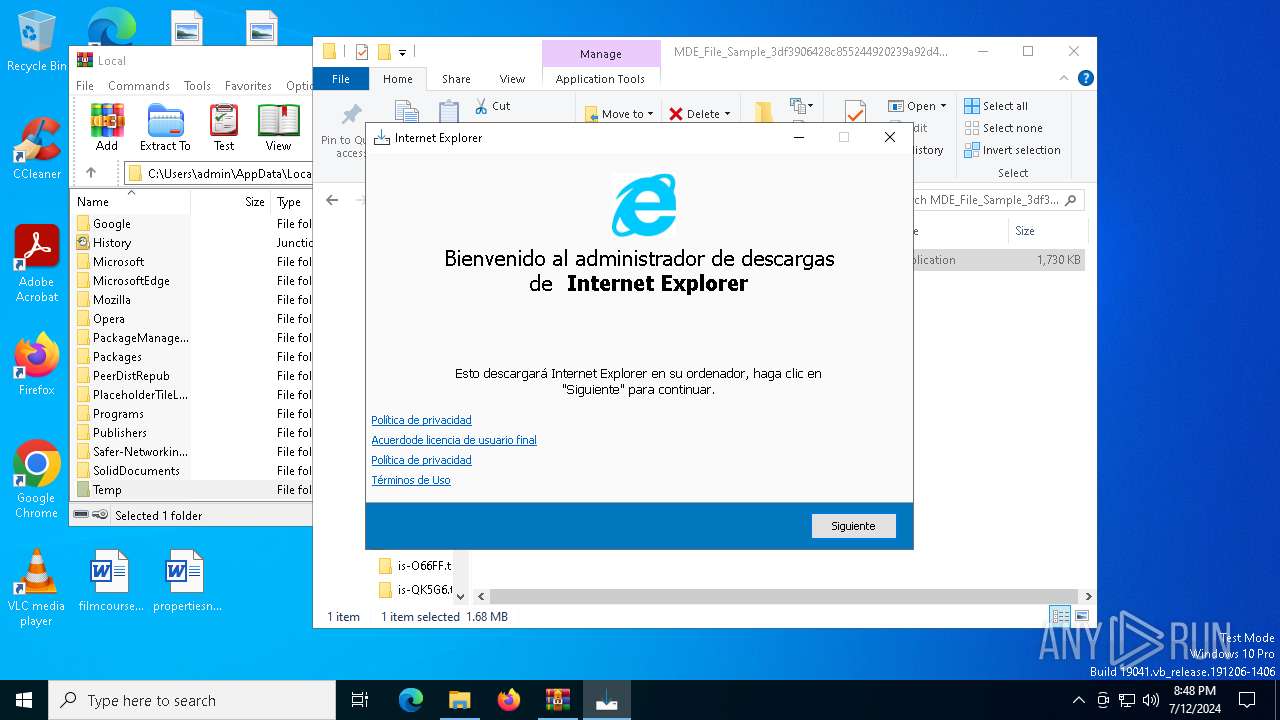
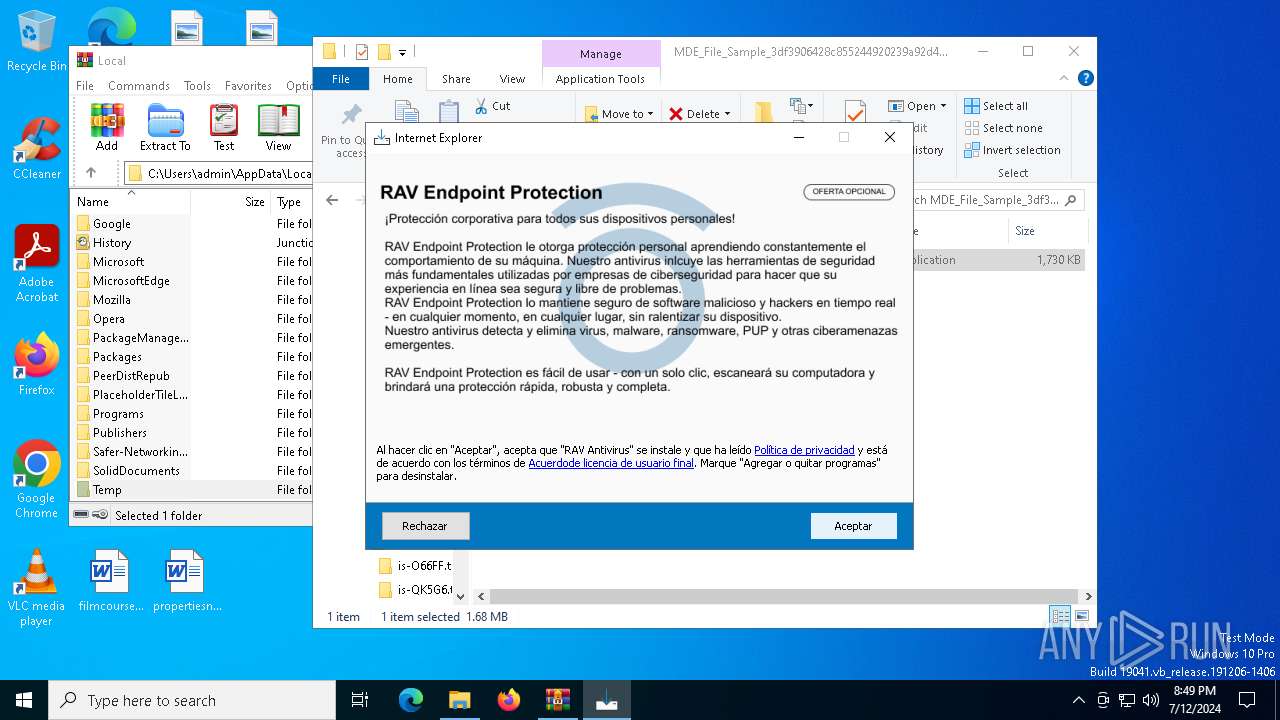
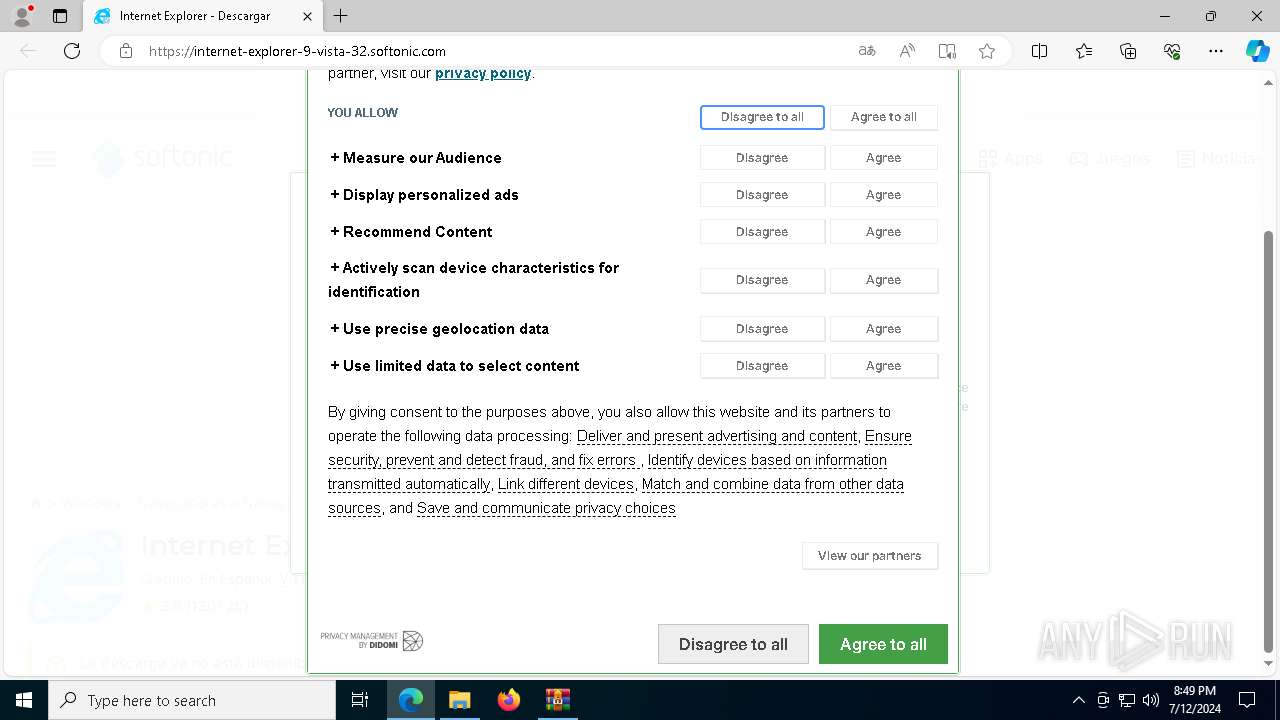
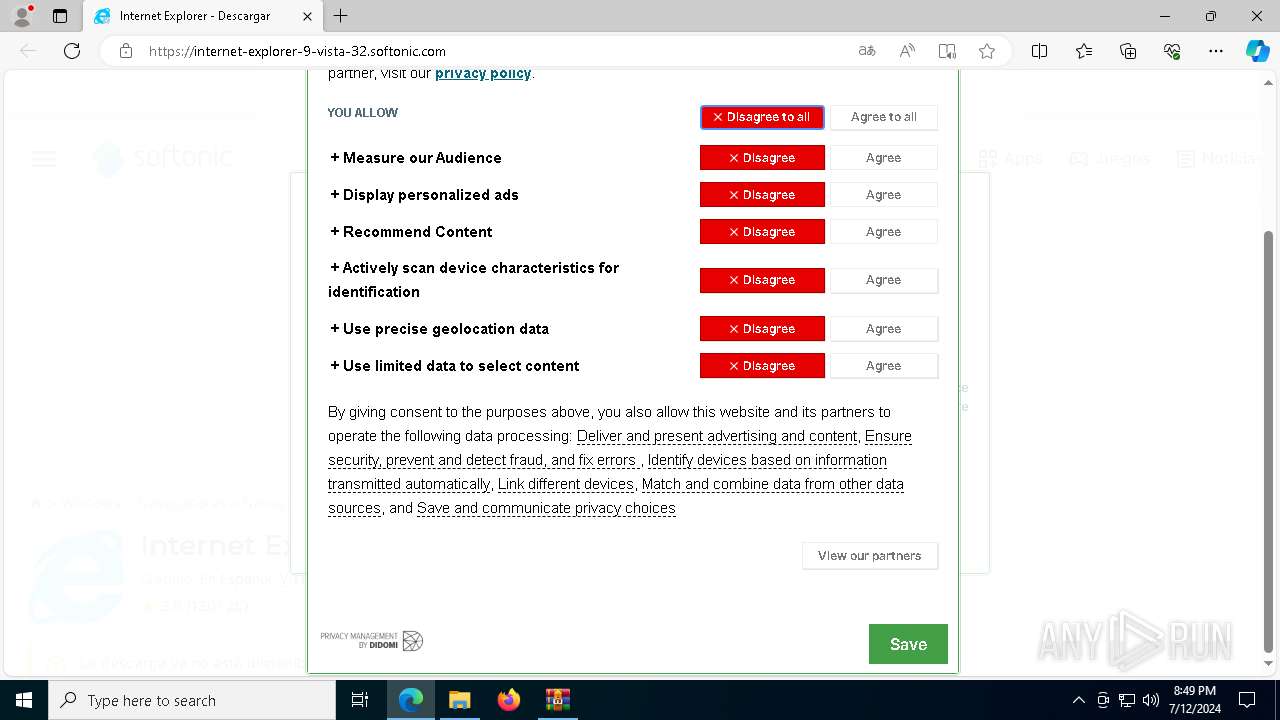
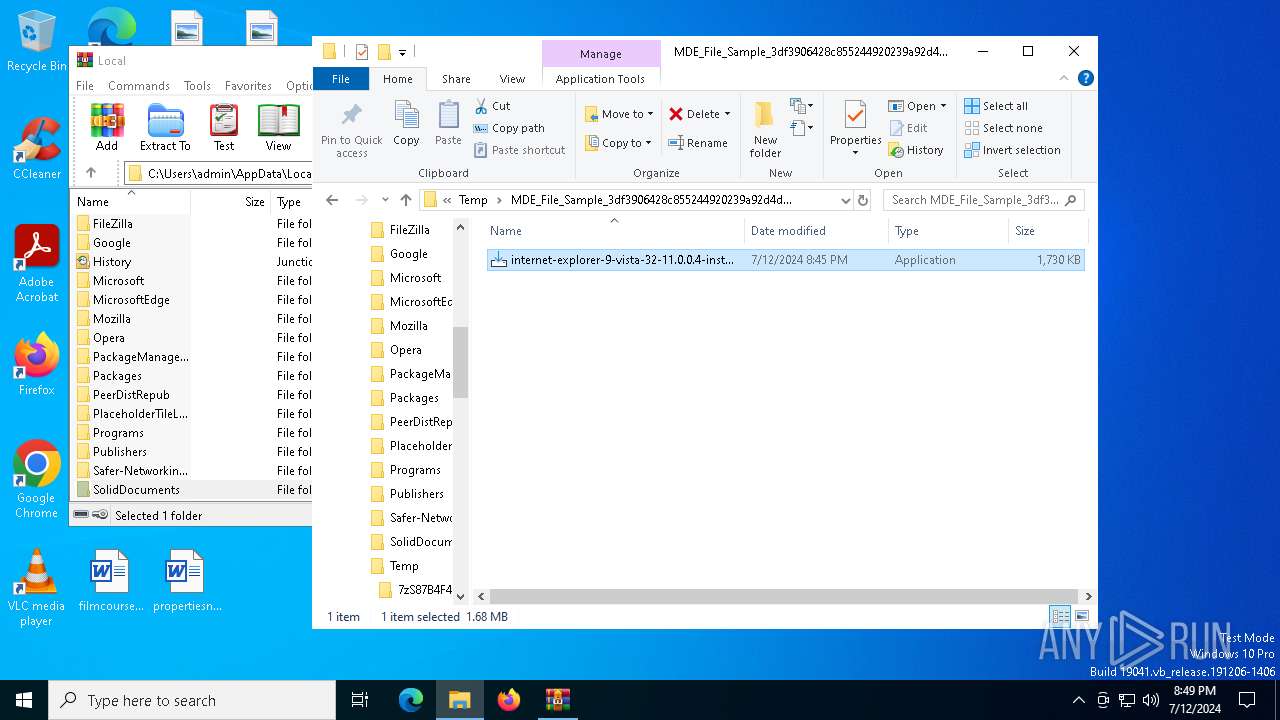
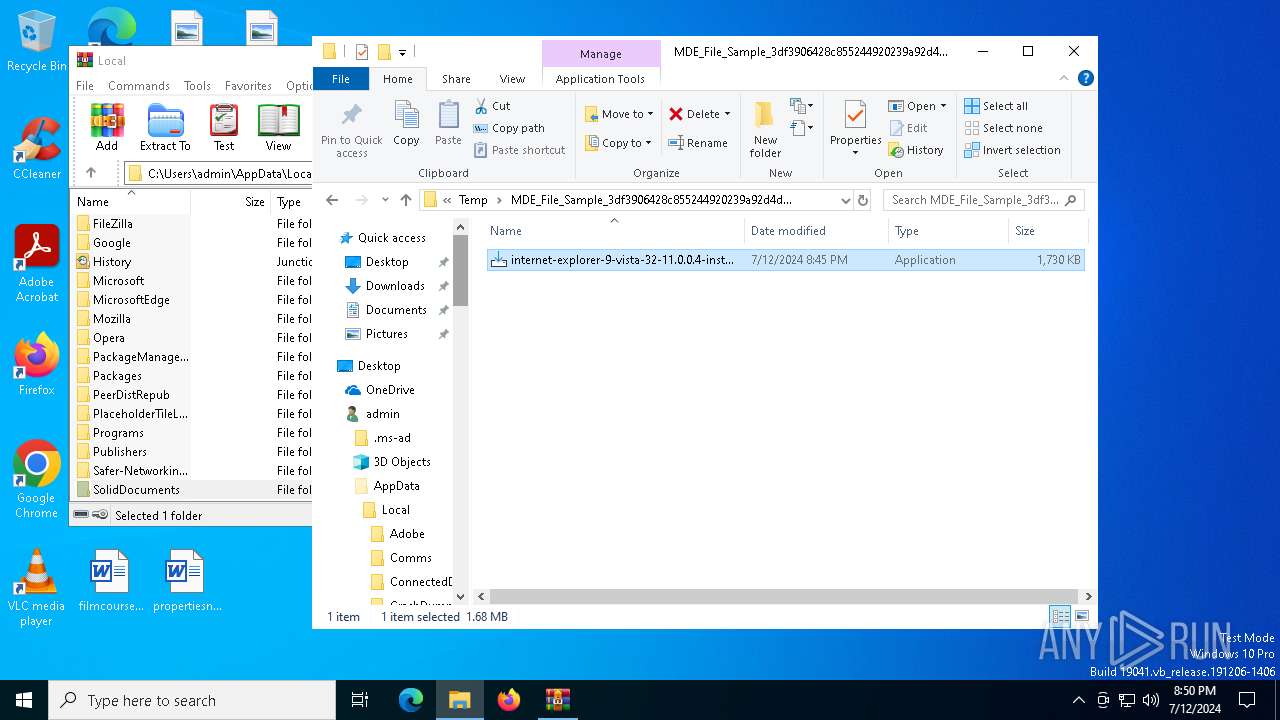
| File name: | MDE_File_Sample_3df3906428c855244920239a92d4d33c17a189b2.zip |
| Full analysis: | https://app.any.run/tasks/87e0153b-d471-475f-81f9-eb9fbd63d82a |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 12, 2024, 20:46:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 58CD365F148628E2605CF349157521FA |
| SHA1: | 06297C8A4191A662764026A030DA120E474AA68D |
| SHA256: | E93956CF656FFC3B14352ED1B43D928F0DF686F431DD505F44332C04998A4CD6 |
| SSDEEP: | 49152:NgHRvG+rK3vZrNfqia2TQg0YgikS39LXPCIc6Ggw0poDYW6ci04lnTmBegww/vCK:NgHdGEK3viiXUCmy9TPCIYgHp66304lS |
MALICIOUS
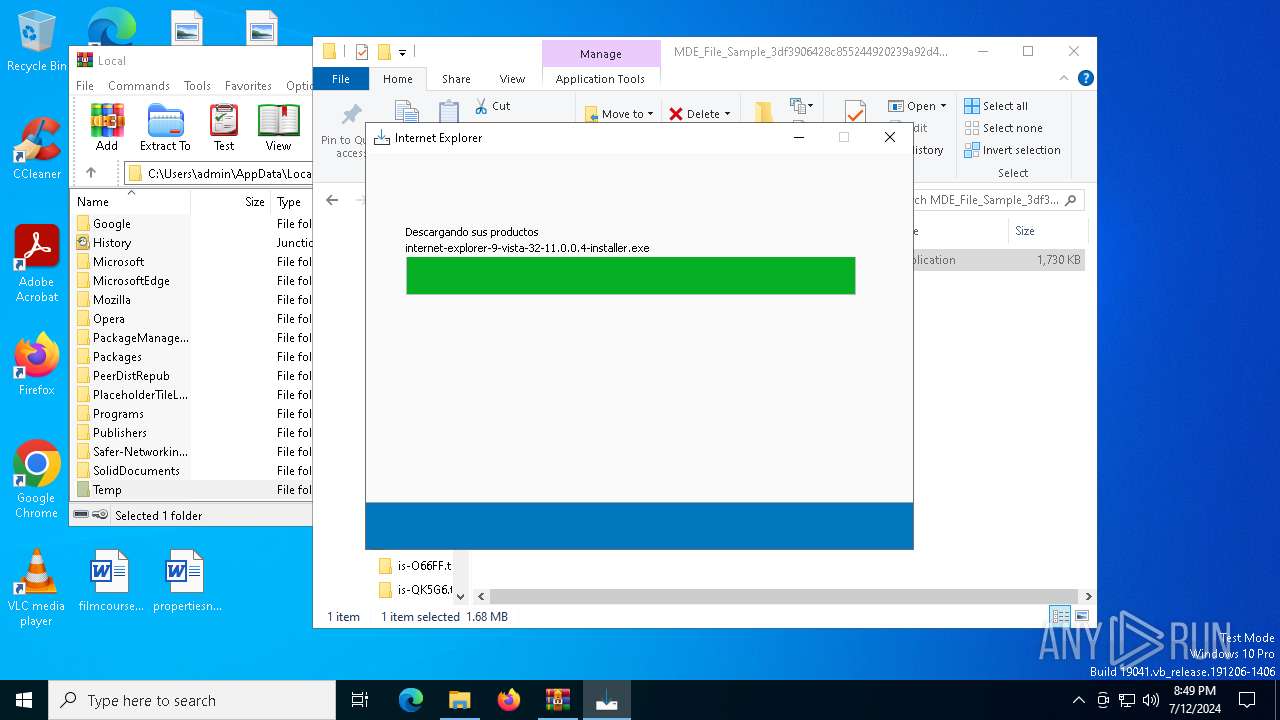
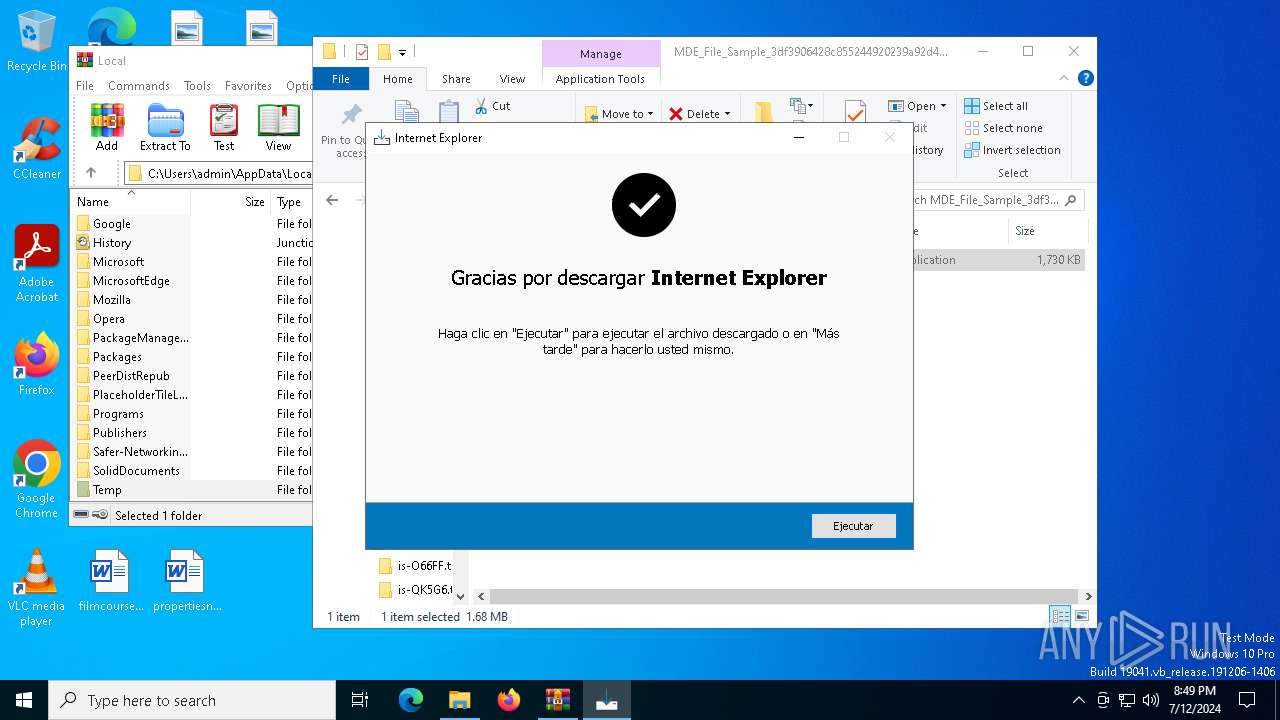
Drops the executable file immediately after the start
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6728)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6888)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- 3vyedffx.exe (PID: 7032)
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 3972)
- rsEngineSvc.exe (PID: 1772)
Creates a writable file in the system directory
- UnifiedStub-installer.exe (PID: 3972)
- rsEDRSvc.exe (PID: 5220)
Changes the autorun value in the registry
- rundll32.exe (PID: 5456)
CYBERGATE has been detected (YARA)
- rsEngineSvc.exe (PID: 1772)
SUSPICIOUS
Executable content was dropped or overwritten
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6728)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6888)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- 3vyedffx.exe (PID: 7032)
- UnifiedStub-installer.exe (PID: 3972)
- component0.exe (PID: 5940)
Reads security settings of Internet Explorer
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 6768)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
- cookie_exporter.exe (PID: 1928)
- rsWSC.exe (PID: 6596)
- rsEngineSvc.exe (PID: 6560)
- rsEDRSvc.exe (PID: 6460)
- rsEngineSvc.exe (PID: 1772)
Reads the date of Windows installation
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 6768)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- rsEDRSvc.exe (PID: 5220)
- rsEngineSvc.exe (PID: 1772)
Reads the Windows owner or organization settings
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 3972)
Process drops legitimate windows executable
- 3vyedffx.exe (PID: 7032)
- UnifiedStub-installer.exe (PID: 3972)
Searches for installed software
- UnifiedStub-installer.exe (PID: 3972)
Executes as Windows Service
- rsSyncSvc.exe (PID: 244)
- rsWSC.exe (PID: 5148)
- rsEngineSvc.exe (PID: 1772)
- rsClientSvc.exe (PID: 6684)
- rsEDRSvc.exe (PID: 5220)
- WmiApSrv.exe (PID: 7588)
Executes application which crashes
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 3972)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 3972)
- rundll32.exe (PID: 5456)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 3972)
The process creates files with name similar to system file names
- UnifiedStub-installer.exe (PID: 3972)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 3972)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 3972)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 3972)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 3972)
Checks Windows Trust Settings
- rsWSC.exe (PID: 6596)
- rsEngineSvc.exe (PID: 6560)
- rsEDRSvc.exe (PID: 6460)
- rsEDRSvc.exe (PID: 5220)
- rsWSC.exe (PID: 5148)
- rsEngineSvc.exe (PID: 1772)
Adds/modifies Windows certificates
- rsEngineSvc.exe (PID: 6560)
- rsEDRSvc.exe (PID: 5220)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 1772)
Reads the BIOS version
- rsEDRSvc.exe (PID: 5220)
- rsEngineSvc.exe (PID: 1772)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 5220)
Application launched itself
- rsAppUI.exe (PID: 1004)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 1772)
There is functionality for taking screenshot (YARA)
- rsEngineSvc.exe (PID: 1772)
INFO
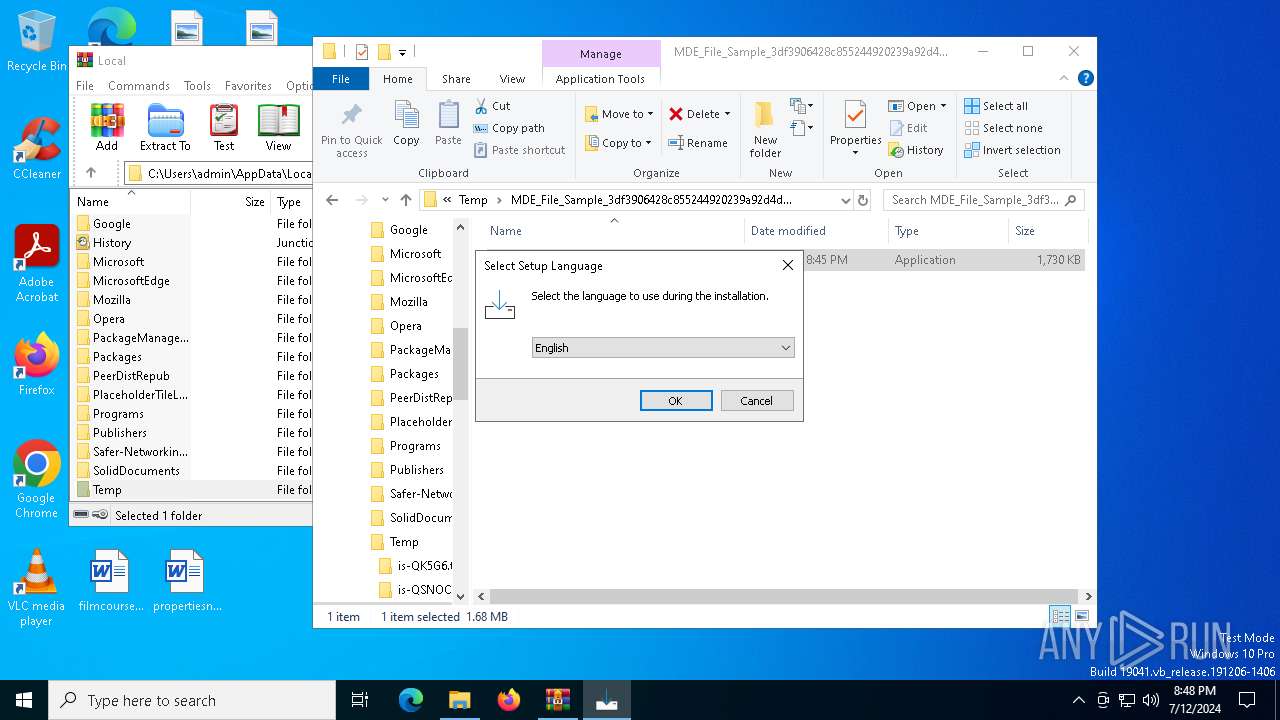
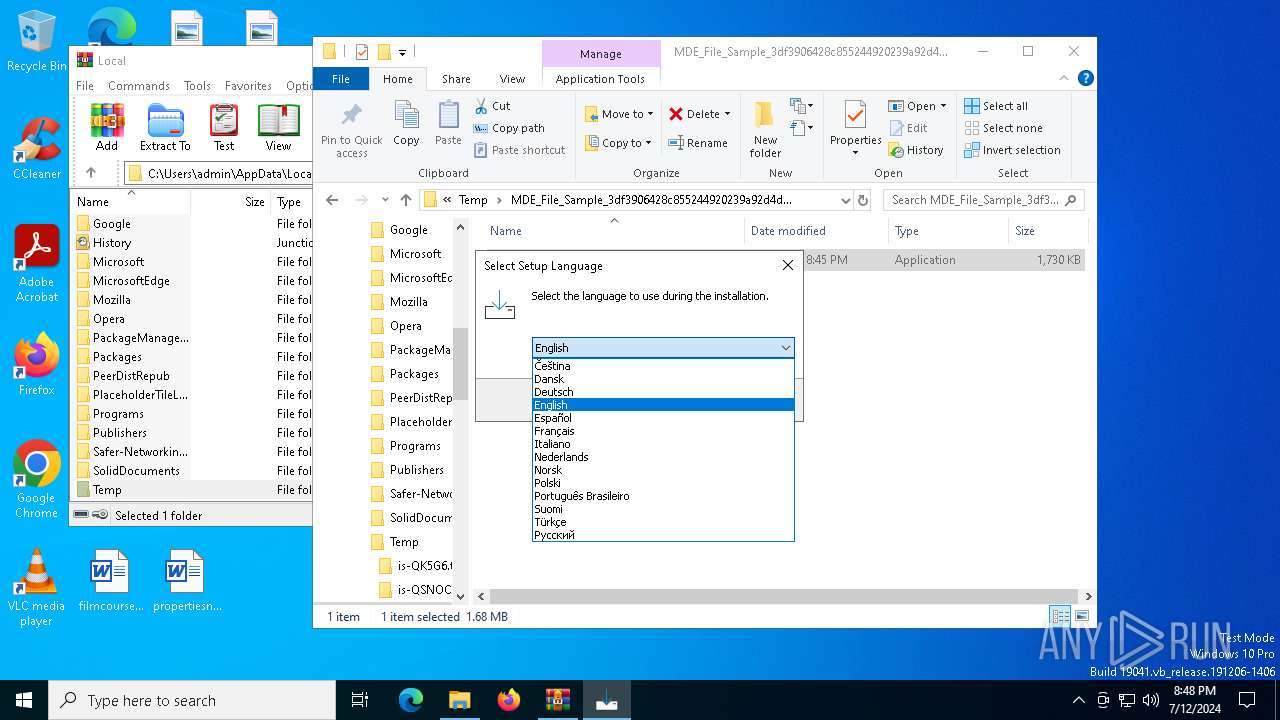
Manual execution by a user
- WinRAR.exe (PID: 6704)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6728)
- msedge.exe (PID: 5332)
- iexplore.exe (PID: 2456)
Create files in a temporary directory
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6728)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6888)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- 3vyedffx.exe (PID: 7032)
- UnifiedStub-installer.exe (PID: 3972)
- rsAppUI.exe (PID: 1004)
Checks supported languages
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 6768)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6728)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe (PID: 6888)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- 3vyedffx.exe (PID: 7032)
- UnifiedStub-installer.exe (PID: 3972)
- rsSyncSvc.exe (PID: 1276)
- rsSyncSvc.exe (PID: 244)
- identity_helper.exe (PID: 6424)
- identity_helper.exe (PID: 6220)
- cookie_exporter.exe (PID: 1928)
- rsWSC.exe (PID: 6596)
- rsWSC.exe (PID: 5148)
- rsClientSvc.exe (PID: 2628)
- rsClientSvc.exe (PID: 6684)
- rsEngineSvc.exe (PID: 6560)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 6460)
- rsEDRSvc.exe (PID: 5220)
- EPP.exe (PID: 3948)
- rsHelper.exe (PID: 1112)
- rsAppUI.exe (PID: 1004)
- rsAppUI.exe (PID: 7244)
- rsAppUI.exe (PID: 7340)
- rsAppUI.exe (PID: 7552)
- rsLitmus.A.exe (PID: 7876)
- rsAppUI.exe (PID: 7276)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6704)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6704)
Reads the computer name
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 6768)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
- rsSyncSvc.exe (PID: 1276)
- rsSyncSvc.exe (PID: 244)
- identity_helper.exe (PID: 6220)
- identity_helper.exe (PID: 6424)
- rsWSC.exe (PID: 6596)
- cookie_exporter.exe (PID: 1928)
- rsWSC.exe (PID: 5148)
- rsClientSvc.exe (PID: 6684)
- rsEngineSvc.exe (PID: 6560)
- rsClientSvc.exe (PID: 2628)
- rsEDRSvc.exe (PID: 6460)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 5220)
- rsHelper.exe (PID: 1112)
- rsAppUI.exe (PID: 1004)
- rsAppUI.exe (PID: 7244)
- rsAppUI.exe (PID: 7276)
Process checks computer location settings
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 6768)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- rsAppUI.exe (PID: 1004)
- rsAppUI.exe (PID: 7340)
- rsAppUI.exe (PID: 7552)
Checks proxy server information
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
- WerFault.exe (PID: 4148)
- WerFault.exe (PID: 6504)
- cookie_exporter.exe (PID: 1928)
- rsWSC.exe (PID: 6596)
- rsEngineSvc.exe (PID: 6560)
- rsAppUI.exe (PID: 1004)
Reads the software policy settings
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
- WerFault.exe (PID: 4148)
- WerFault.exe (PID: 6504)
- rsWSC.exe (PID: 6596)
- rsEngineSvc.exe (PID: 6560)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 6460)
- rsEDRSvc.exe (PID: 5220)
- rsWSC.exe (PID: 5148)
Reads the machine GUID from the registry
- component0.exe (PID: 5940)
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- UnifiedStub-installer.exe (PID: 3972)
- rsWSC.exe (PID: 6596)
- rsWSC.exe (PID: 5148)
- rsEngineSvc.exe (PID: 6560)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 6460)
- rsEDRSvc.exe (PID: 5220)
- rsHelper.exe (PID: 1112)
- rsAppUI.exe (PID: 1004)
Disables trace logs
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 5220)
Reads Environment values
- component0.exe (PID: 5940)
- UnifiedStub-installer.exe (PID: 3972)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 5220)
- rsAppUI.exe (PID: 1004)
Creates files in the program directory
- UnifiedStub-installer.exe (PID: 3972)
- rsWSC.exe (PID: 6596)
- rsEngineSvc.exe (PID: 6560)
- rsEDRSvc.exe (PID: 6460)
- rsEngineSvc.exe (PID: 1772)
- rsEDRSvc.exe (PID: 5220)
Reads Microsoft Office registry keys
- internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp (PID: 4308)
- msedge.exe (PID: 1348)
- msedge.exe (PID: 5332)
- msedge.exe (PID: 3660)
Application launched itself
- msedge.exe (PID: 1348)
- msedge.exe (PID: 5332)
- msedge.exe (PID: 3660)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 3972)
- rsWSC.exe (PID: 5148)
- rsEngineSvc.exe (PID: 1772)
Creates files or folders in the user directory
- WerFault.exe (PID: 6504)
- WerFault.exe (PID: 4148)
- rsWSC.exe (PID: 6596)
- rsEngineSvc.exe (PID: 6560)
- rsAppUI.exe (PID: 1004)
- rsEngineSvc.exe (PID: 1772)
- rsAppUI.exe (PID: 7276)
Reads the time zone
- runonce.exe (PID: 5832)
- rsEDRSvc.exe (PID: 5220)
- rsEngineSvc.exe (PID: 1772)
Reads security settings of Internet Explorer
- runonce.exe (PID: 5832)
Reads product name
- rsEDRSvc.exe (PID: 5220)
- rsAppUI.exe (PID: 1004)
- rsEngineSvc.exe (PID: 1772)
Reads CPU info
- rsEDRSvc.exe (PID: 5220)
- rsEngineSvc.exe (PID: 1772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:12 20:45:52 |
| ZipCRC: | 0x0934b8a1 |
| ZipCompressedSize: | 1221191 |
| ZipUncompressedSize: | 1771280 |
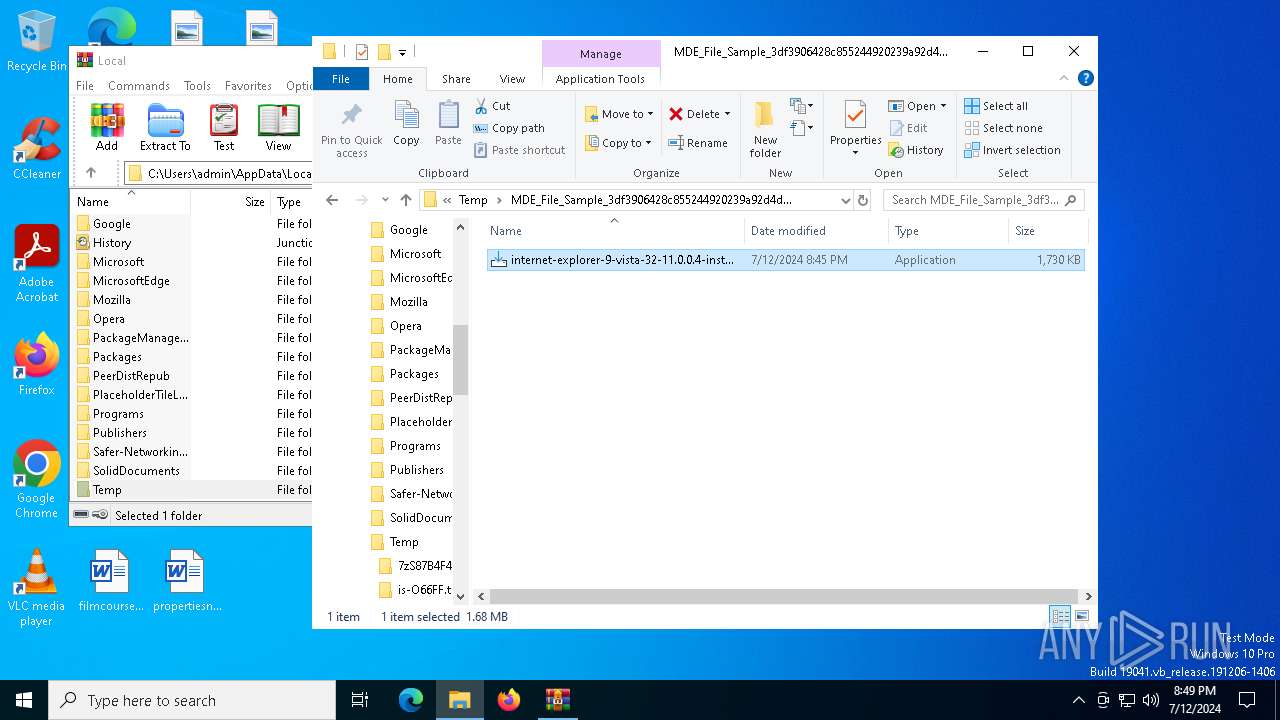
| ZipFileName: | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe |
Total processes
266
Monitored processes
120
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe" -pn:EPP -lpn:rav_antivirus -url:https://update.reasonsecurity.com/v2/live -bn:ReasonLabs -dt:10 | C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: Reason Security Synchronize Service Version: 1.7.2.0 Modules
| |||||||||||||||
| 376 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2432 --field-trial-handle=2436,i,16555730277311780741,13949191236788257730,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=5272 --field-trial-handle=2284,i,7035649379648600775,555174702554230950,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=5016 --field-trial-handle=2436,i,16555730277311780741,13949191236788257730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 916 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5700 --field-trial-handle=2436,i,16555730277311780741,13949191236788257730,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1004 | "C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe" "c:\program files\reasonlabs\EPP\ui\app.asar" --engine-path="c:\program files\reasonlabs\EPP" --minimized --first-run | C:\Program Files\ReasonLabs\Common\Client\v1.4.2\rsAppUI.exe | — | EPP.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: MEDIUM Description: ReasonLabs Application Version: 1.4.2 Modules
| |||||||||||||||
| 1048 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6196 --field-trial-handle=2284,i,7035649379648600775,555174702554230950,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2384 --field-trial-handle=2412,i,8247996684415344757,13789281135522855784,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1112 | "c:\program files\reasonlabs\epp\rsHelper.exe" | C:\Program Files\ReasonLabs\EPP\rsHelper.exe | — | rsEngineSvc.exe | |||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: MEDIUM Description: rsHelper Version: 3.2.0.0 Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x260,0x264,0x268,0x25c,0x27c,0x7ffd963c5fd8,0x7ffd963c5fe4,0x7ffd963c5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
101 239
Read events
100 693
Write events
467
Delete events
79
Modification events
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_3df3906428c855244920239a92d4d33c17a189b2.zip | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
508
Suspicious files
501
Text files
202
Unknown types
46
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6728 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe | C:\Users\admin\AppData\Local\Temp\is-QSNOC.tmp\internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | executable | |
MD5:E07653C6B6CC1B324F03B7976033F39B | SHA256:4F5D4EBA4FFD73C78906116CE2C2A065FECEBB4EAAC31DA58B71D4810BFCA95D | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\is-MF5K4.tmp | executable | |
MD5:E2A03F23A3B964537DD9F2171915F48F | SHA256:2A6BAA2AF689BFC61BB326C54D1693A293EF9357B126A337BBED997E928B92A8 | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\x.png | image | |
MD5:0BD639D161C88F6B8C31EB55478841F9 | SHA256:CA825FAB9A9746DAC2AC63EF48722154A1A56A457DA6AB7D80D34FCACF0B010E | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\Downloads\internet-explorer-9-vista-32-11.0.0.4-installer.exe | html | |
MD5:6CB825EA43F9776B10112384CEADACFD | SHA256:592E7C6586264287E8BCC9AAC891A14F217B4822BB90E6D1E0B66AE40E152EFA | |||
| 6704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_3df3906428c855244920239a92d4d33c17a189b2\internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.exe | executable | |
MD5:3F6DFFF099A9E1AB628BEE91B15E219D | SHA256:5C46BF70E787E3EAEA8206838DC46392EECE561F9834E4D96CA90DA2279C52EA | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\is-RR1SC.tmp | image | |
MD5:1AA6F1A27C3C2E2CD0FB2F150F12B3C8 | SHA256:585F90989F147CB9AD19F38837EEA2822A0B614BA1C352FCD8A6696B0A000753 | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\RAV_Cross.png | image | |
MD5:1AA6F1A27C3C2E2CD0FB2F150F12B3C8 | SHA256:585F90989F147CB9AD19F38837EEA2822A0B614BA1C352FCD8A6696B0A000753 | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\is-41DR0.tmp | image | |
MD5:59517175811CBE3D29661469B5C8F05C | SHA256:355A9A67233E6C0BB173DCB05D84A588D9FCED6CFA2264684AA1F1DD09E1F0A5 | |||
| 4308 | internet-explorer-9-vista-32-11.0.0.4-installer_n1o6-p1.tmp | C:\Users\admin\AppData\Local\Temp\is-O66FF.tmp\v.png | image | |
MD5:901CCEF6859BF21318516EC882854058 | SHA256:00873784B2C875FEFB4FFC71163A3DE9991809C865F750D77990C279D4EBC579 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
232
DNS requests
193
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6504 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6596 | rsWSC.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQCeArDpSs6yEJyh6YNr4MLb | unknown | — | — | whitelisted |
7048 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6504 | WerFault.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6560 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6560 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAGShr6zwVhanQAAAAAAAY%3D | unknown | — | — | whitelisted |
6560 | rsEngineSvc.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQQ9RoB7druAplRfZIM2Szg4IoTvQQUdpw2dBPRkH1hX7MC64D0mUulPoUCEzMAAHpquZwYI%2FKdN8YAAAAAemo%3D | unknown | — | — | whitelisted |
6596 | rsWSC.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQRz3ETyLz2DaZTxGOH%2BA%2BjK7MkGAQUJGWTmAgB6E7U1kzqZFXhwPr7z7MCEAeSK29bdU5YKBXAnjHx1BY%3D | unknown | — | — | whitelisted |
6560 | rsEngineSvc.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ID%20Verified%20CS%20EOC%20CA%2001.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
376 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2848 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1828 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1828 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4656 | SearchApp.exe | 92.123.104.38:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |