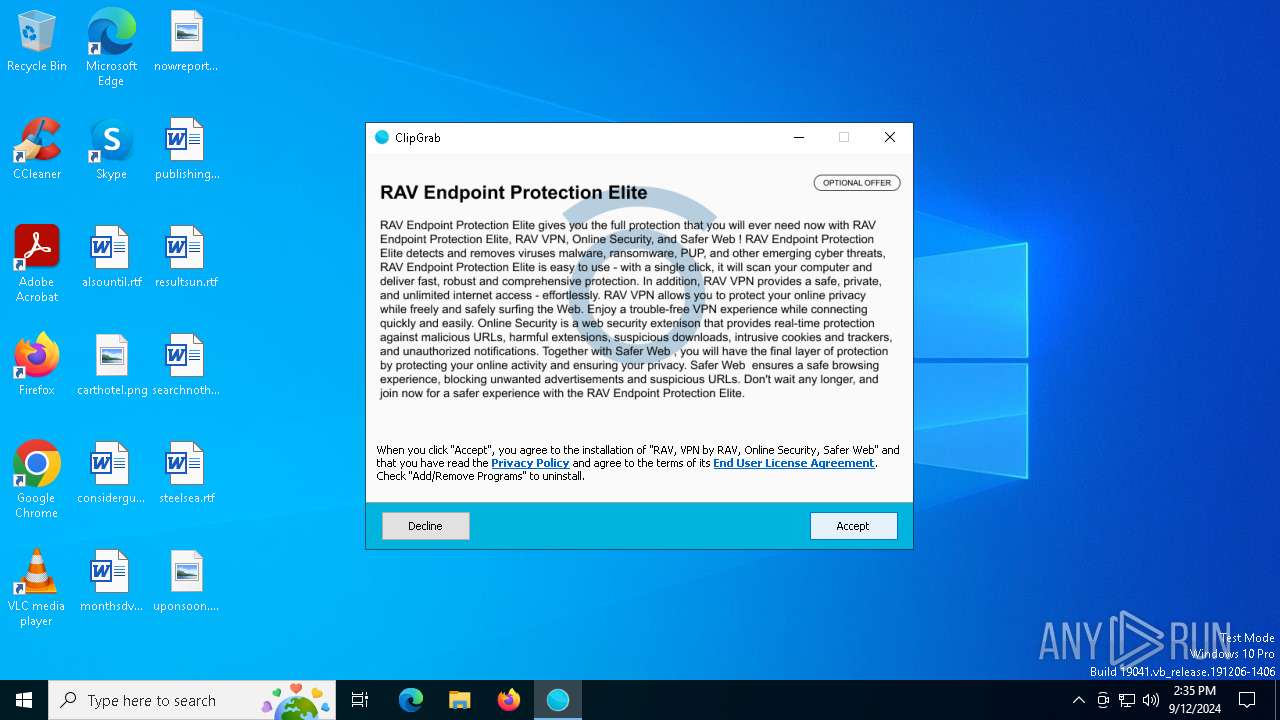
| File name: | clipgrab-3.9.10-dotinstaller.exe |
| Full analysis: | https://app.any.run/tasks/c9d40c3e-3d10-454d-b486-d9038e6ea5a5 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | September 12, 2024, 14:34:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D5351A9AFA0356B886F609FF7F53603D |
| SHA1: | 7368DE3DB110E4398BE3EDD3AFDD6BC48F7BB9FD |
| SHA256: | E92C5CF7509DD9792FAC8202FB08295DFC9E5F18663DB81BF07990DE1BC85893 |
| SSDEEP: | 98304:d+cD4dnQIRP3sBI6IauBPDZONh4DkLmDYfuXqGQoHbHL7WdaRCJ7HIf+UJfxlbqK:NA2NE |
MALICIOUS
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 5400)
- rsEngineSvc.exe (PID: 6948)
Changes the autorun value in the registry
- rundll32.exe (PID: 2460)
SUSPICIOUS
Executable content was dropped or overwritten
- clipgrab-3.9.10-dotinstaller.exe (PID: 6492)
- clipgrab-3.9.10-dotinstaller.exe (PID: 780)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- clipgrab-3.9.10-portable.exe (PID: 6840)
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- vc_redist.x86.exe (PID: 4668)
- vc_redist.x86.exe (PID: 4440)
- prod0.exe (PID: 1920)
- 2pzfvsa0.exe (PID: 6520)
- UnifiedStub-installer.exe (PID: 5400)
Reads security settings of Internet Explorer
- clipgrab-3.9.10-dotinstaller.tmp (PID: 6764)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- prod0.exe (PID: 1920)
- ShellExperienceHost.exe (PID: 4444)
- UnifiedStub-installer.exe (PID: 5400)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- rsEDRSvc.exe (PID: 6200)
- rsEngineSvc.exe (PID: 6948)
Reads the Windows owner or organization settings
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- clipgrab-3.9.10-portable.tmp (PID: 5712)
Process drops legitimate windows executable
- vc_redist.x86.exe (PID: 4440)
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- 2pzfvsa0.exe (PID: 6520)
- UnifiedStub-installer.exe (PID: 5400)
The process drops C-runtime libraries
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- UnifiedStub-installer.exe (PID: 5400)
Starts a Microsoft application from unusual location
- vc_redist.x86.exe (PID: 4440)
- vc_redist.x86.exe (PID: 4668)
Searches for installed software
- vc_redist.x86.exe (PID: 4668)
- UnifiedStub-installer.exe (PID: 5400)
Reads the date of Windows installation
- prod0.exe (PID: 1920)
- rsEDRSvc.exe (PID: 5772)
- rsEngineSvc.exe (PID: 6948)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 5400)
Executes application which crashes
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
Executes as Windows Service
- rsSyncSvc.exe (PID: 6176)
- rsWSC.exe (PID: 1568)
- rsClientSvc.exe (PID: 6800)
- rsEngineSvc.exe (PID: 6948)
- rsEDRSvc.exe (PID: 5772)
- WmiApSrv.exe (PID: 7580)
Loads Python modules
- python.exe (PID: 3208)
- python.exe (PID: 6836)
- python.exe (PID: 1060)
- python.exe (PID: 6056)
- python.exe (PID: 5220)
- python.exe (PID: 5712)
- python.exe (PID: 4316)
- python.exe (PID: 6996)
- python.exe (PID: 3684)
- python.exe (PID: 1124)
- python.exe (PID: 4060)
- python.exe (PID: 1636)
- python.exe (PID: 4160)
- python.exe (PID: 6908)
- python.exe (PID: 5172)
- python.exe (PID: 6004)
- python.exe (PID: 4024)
- python.exe (PID: 2572)
- python.exe (PID: 300)
- python.exe (PID: 3184)
- python.exe (PID: 1280)
- python.exe (PID: 6320)
- python.exe (PID: 568)
- python.exe (PID: 508)
- python.exe (PID: 2524)
Process drops python dynamic module
- clipgrab-3.9.10-portable.tmp (PID: 5712)
The process creates files with name similar to system file names
- UnifiedStub-installer.exe (PID: 5400)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 5400)
- rundll32.exe (PID: 2460)
Checks Windows Trust Settings
- UnifiedStub-installer.exe (PID: 5400)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- rsWSC.exe (PID: 1568)
- rsEDRSvc.exe (PID: 6200)
- rsEDRSvc.exe (PID: 5772)
- rsEngineSvc.exe (PID: 6948)
Adds/modifies Windows certificates
- UnifiedStub-installer.exe (PID: 5400)
- rsWSC.exe (PID: 4544)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 5400)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 5400)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 5400)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 5400)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 5400)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 5772)
Reads the BIOS version
- rsEDRSvc.exe (PID: 5772)
- rsEngineSvc.exe (PID: 6948)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 6948)
Application launched itself
- rsAppUI.exe (PID: 3352)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 6948)
INFO
Create files in a temporary directory
- clipgrab-3.9.10-dotinstaller.exe (PID: 6492)
- clipgrab-3.9.10-dotinstaller.exe (PID: 780)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- vc_redist.x86.exe (PID: 4668)
- prod0.exe (PID: 1920)
- 2pzfvsa0.exe (PID: 6520)
- clipgrab-3.9.10-portable.exe (PID: 6840)
- UnifiedStub-installer.exe (PID: 5400)
- rsAppUI.exe (PID: 3352)
Checks supported languages
- clipgrab-3.9.10-dotinstaller.tmp (PID: 6764)
- clipgrab-3.9.10-dotinstaller.exe (PID: 6492)
- clipgrab-3.9.10-dotinstaller.exe (PID: 780)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- vc_redist.x86.exe (PID: 4440)
- vc_redist.x86.exe (PID: 4668)
- prod0.exe (PID: 1920)
- 2pzfvsa0.exe (PID: 6520)
- UnifiedStub-installer.exe (PID: 5400)
- rsSyncSvc.exe (PID: 6372)
- clipgrab.exe (PID: 5644)
- ffmpeg.exe (PID: 5172)
- ffmpeg.exe (PID: 2360)
- rsSyncSvc.exe (PID: 6176)
- python.exe (PID: 1060)
- python.exe (PID: 6056)
- python.exe (PID: 6836)
- python.exe (PID: 5220)
- clipgrab-3.9.10-portable.exe (PID: 6840)
- python.exe (PID: 3208)
- python.exe (PID: 5712)
- python.exe (PID: 4316)
- python.exe (PID: 6996)
- python.exe (PID: 3684)
- python.exe (PID: 1124)
- python.exe (PID: 4060)
- python.exe (PID: 5172)
- python.exe (PID: 1636)
- python.exe (PID: 6908)
- QtWebEngineProcess.exe (PID: 5984)
- python.exe (PID: 4160)
- python.exe (PID: 300)
- QtWebEngineProcess.exe (PID: 1748)
- python.exe (PID: 6004)
- python.exe (PID: 4024)
- python.exe (PID: 2572)
- QtWebEngineProcess.exe (PID: 2456)
- python.exe (PID: 3184)
- ffmpeg.exe (PID: 6016)
- ShellExperienceHost.exe (PID: 4444)
- rsClientSvc.exe (PID: 1496)
- rsWSC.exe (PID: 1568)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- clipgrab.exe (PID: 608)
- rsEngineSvc.exe (PID: 6948)
- rsClientSvc.exe (PID: 6800)
- ffmpeg.exe (PID: 1780)
- python.exe (PID: 1280)
- python.exe (PID: 6320)
- python.exe (PID: 508)
- ffmpeg.exe (PID: 5772)
- python.exe (PID: 568)
- python.exe (PID: 2524)
- QtWebEngineProcess.exe (PID: 892)
- rsEDRSvc.exe (PID: 6200)
- rsEDRSvc.exe (PID: 5772)
- EPP.exe (PID: 1280)
- rsHelper.exe (PID: 1752)
- rsAppUI.exe (PID: 3352)
- rsAppUI.exe (PID: 7376)
- rsAppUI.exe (PID: 3104)
- rsAppUI.exe (PID: 6732)
- rsAppUI.exe (PID: 7176)
- rsLitmus.A.exe (PID: 7636)
Process checks computer location settings
- clipgrab-3.9.10-dotinstaller.tmp (PID: 6764)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- prod0.exe (PID: 1920)
- rsAppUI.exe (PID: 3352)
- rsAppUI.exe (PID: 7176)
- rsAppUI.exe (PID: 7376)
Reads the computer name
- clipgrab-3.9.10-dotinstaller.tmp (PID: 6764)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- vc_redist.x86.exe (PID: 4668)
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- rsSyncSvc.exe (PID: 6372)
- rsSyncSvc.exe (PID: 6176)
- clipgrab.exe (PID: 5644)
- python.exe (PID: 4024)
- python.exe (PID: 3184)
- ShellExperienceHost.exe (PID: 4444)
- rsWSC.exe (PID: 1568)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- rsEngineSvc.exe (PID: 6948)
- rsClientSvc.exe (PID: 1496)
- rsClientSvc.exe (PID: 6800)
- clipgrab.exe (PID: 608)
- python.exe (PID: 6320)
- rsEDRSvc.exe (PID: 6200)
- rsEDRSvc.exe (PID: 5772)
- rsHelper.exe (PID: 1752)
- rsAppUI.exe (PID: 3352)
- rsAppUI.exe (PID: 3104)
- rsAppUI.exe (PID: 6732)
Creates a software uninstall entry
- clipgrab-3.9.10-portable.tmp (PID: 5712)
Creates files in the program directory
- clipgrab-3.9.10-portable.tmp (PID: 5712)
- UnifiedStub-installer.exe (PID: 5400)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- rsEngineSvc.exe (PID: 6948)
- rsEDRSvc.exe (PID: 6200)
- rsEDRSvc.exe (PID: 5772)
The process uses the downloaded file
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- runonce.exe (PID: 6316)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- rsEDRSvc.exe (PID: 6200)
- rsEngineSvc.exe (PID: 6948)
Reads the machine GUID from the registry
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- ffmpeg.exe (PID: 5172)
- clipgrab.exe (PID: 5644)
- ffmpeg.exe (PID: 2360)
- python.exe (PID: 3208)
- python.exe (PID: 1060)
- python.exe (PID: 6056)
- python.exe (PID: 6836)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- python.exe (PID: 5220)
- python.exe (PID: 5712)
- python.exe (PID: 4316)
- python.exe (PID: 6996)
- python.exe (PID: 1124)
- python.exe (PID: 4060)
- python.exe (PID: 5172)
- python.exe (PID: 1636)
- python.exe (PID: 4160)
- python.exe (PID: 6908)
- python.exe (PID: 6004)
- python.exe (PID: 4024)
- python.exe (PID: 300)
- ffmpeg.exe (PID: 6016)
- python.exe (PID: 3184)
- rsWSC.exe (PID: 1568)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- python.exe (PID: 6320)
- rsEngineSvc.exe (PID: 6948)
- python.exe (PID: 508)
- ffmpeg.exe (PID: 5772)
- ffmpeg.exe (PID: 1780)
- clipgrab.exe (PID: 608)
- python.exe (PID: 1280)
- python.exe (PID: 568)
- rsEDRSvc.exe (PID: 5772)
- rsHelper.exe (PID: 1752)
- rsEDRSvc.exe (PID: 6200)
- rsAppUI.exe (PID: 3352)
Reads Environment values
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- rsEngineSvc.exe (PID: 6948)
- rsEDRSvc.exe (PID: 5772)
- rsAppUI.exe (PID: 3352)
Reads the software policy settings
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- WerFault.exe (PID: 3184)
- WerFault.exe (PID: 1076)
- slui.exe (PID: 6868)
- clipgrab.exe (PID: 5644)
- rsWSC.exe (PID: 4544)
- rsEngineSvc.exe (PID: 5720)
- rsEngineSvc.exe (PID: 6948)
- clipgrab.exe (PID: 608)
- rsWSC.exe (PID: 1568)
- rsEDRSvc.exe (PID: 6200)
- rsEDRSvc.exe (PID: 5772)
- slui.exe (PID: 4692)
Checks proxy server information
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- clipgrab-3.9.10-dotinstaller.tmp (PID: 488)
- WerFault.exe (PID: 3184)
- WerFault.exe (PID: 1076)
- python.exe (PID: 4024)
- python.exe (PID: 3184)
- rsWSC.exe (PID: 4544)
- python.exe (PID: 6320)
- rsAppUI.exe (PID: 3352)
- slui.exe (PID: 4692)
Disables trace logs
- prod0.exe (PID: 1920)
- UnifiedStub-installer.exe (PID: 5400)
- rsEngineSvc.exe (PID: 6948)
- rsEDRSvc.exe (PID: 5772)
Sends debugging messages
- clipgrab.exe (PID: 5644)
- ShellExperienceHost.exe (PID: 4444)
- clipgrab.exe (PID: 608)
- rsEngineSvc.exe (PID: 6948)
- rsEDRSvc.exe (PID: 5772)
Creates files or folders in the user directory
- WerFault.exe (PID: 3184)
- WerFault.exe (PID: 1076)
- clipgrab.exe (PID: 5644)
- UnifiedStub-installer.exe (PID: 5400)
- rsWSC.exe (PID: 4544)
- rsAppUI.exe (PID: 3352)
- rsAppUI.exe (PID: 6732)
- rsEngineSvc.exe (PID: 6948)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 5400)
Reads the time zone
- runonce.exe (PID: 6316)
- rsEDRSvc.exe (PID: 5772)
- rsEngineSvc.exe (PID: 6948)
Reads security settings of Internet Explorer
- runonce.exe (PID: 6316)
Manual execution by a user
- clipgrab.exe (PID: 608)
Reads product name
- rsEDRSvc.exe (PID: 5772)
- rsAppUI.exe (PID: 3352)
- rsEngineSvc.exe (PID: 6948)
Reads CPU info
- rsEDRSvc.exe (PID: 5772)
- rsEngineSvc.exe (PID: 6948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 369152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.9.10.0 |
| ProductVersionNumber: | 3.9.10.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | ClipGrab Installer |
| FileVersion: | 3.9.10 |
| LegalCopyright: | © ClipGrab |
| OriginalFileName: | |
| ProductName: | ClipGrab |
| ProductVersion: | 3.9.10 |
Total processes
252
Monitored processes
113
Malicious processes
10
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files (x86)\ClipGrab\python\python.exe" C:/Users/admin/AppData/Roaming/ClipGrab/ClipGrab/yt-dlp --version | C:\Program Files (x86)\ClipGrab\python\python.exe | — | clipgrab.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Exit code: 0 Version: 3.8.9 Modules
| |||||||||||||||
| 488 | "C:\Users\admin\AppData\Local\Temp\is-JDLO7.tmp\clipgrab-3.9.10-dotinstaller.tmp" /SL5="$150050,1870827,1112064,C:\Users\admin\AppData\Local\Temp\clipgrab-3.9.10-dotinstaller.exe" /SPAWNWND=$604DA /NOTIFYWND=$E02E0 | C:\Users\admin\AppData\Local\Temp\is-JDLO7.tmp\clipgrab-3.9.10-dotinstaller.tmp | clipgrab-3.9.10-dotinstaller.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 3221226525 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 508 | "C:\Program Files (x86)\ClipGrab\python\python.exe" C:/Users/admin/AppData/Roaming/ClipGrab/ClipGrab/yt-dlp --version | C:\Program Files (x86)\ClipGrab\python\python.exe | — | clipgrab.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.8.9 Modules
| |||||||||||||||
| 568 | "C:\Program Files (x86)\ClipGrab\python\python.exe" C:/Users/admin/AppData/Roaming/ClipGrab/ClipGrab/yt-dlp --version | C:\Program Files (x86)\ClipGrab\python\python.exe | — | clipgrab.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.8.9 Modules
| |||||||||||||||
| 608 | "C:\Program Files (x86)\ClipGrab\clipgrab.exe" | C:\Program Files (x86)\ClipGrab\clipgrab.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 780 | "C:\Users\admin\AppData\Local\Temp\clipgrab-3.9.10-dotinstaller.exe" /SPAWNWND=$604DA /NOTIFYWND=$E02E0 | C:\Users\admin\AppData\Local\Temp\clipgrab-3.9.10-dotinstaller.exe | clipgrab-3.9.10-dotinstaller.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: ClipGrab Installer Exit code: 3221226525 Version: 3.9.10 Modules
| |||||||||||||||
| 892 | "C:\Program Files (x86)\ClipGrab\QtWebEngineProcess.exe" --type=renderer --no-sandbox --disable-gpu-memory-buffer-video-frames --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations --disable-features=MojoVideoCapture,SurfaceSynchronization,UseModernMediaControls,UseVideoCaptureApiForDevToolsSnapshots --disable-databases --disable-gpu-compositing --service-pipe-token=7720244379084028290 --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7720244379084028290 --renderer-client-id=2 --mojo-platform-channel-handle=2644 /prefetch:1 | C:\Program Files (x86)\ClipGrab\QtWebEngineProcess.exe | — | clipgrab.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: MEDIUM Description: Qt Qtwebengineprocess Exit code: 0 Version: 5.12.6.0 Modules
| |||||||||||||||
| 1060 | "C:\Program Files (x86)\ClipGrab\python\python.exe" "" --version | C:\Program Files (x86)\ClipGrab\python\python.exe | — | clipgrab.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Exit code: 1 Version: 3.8.9 Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 488 -s 1008 | C:\Windows\SysWOW64\WerFault.exe | clipgrab-3.9.10-dotinstaller.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1124 | "C:\Program Files (x86)\ClipGrab\python\python.exe" "" --version | C:\Program Files (x86)\ClipGrab\python\python.exe | — | clipgrab.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Exit code: 1 Version: 3.8.9 Modules
| |||||||||||||||
Total events
72 504
Read events
72 199
Write events
230
Delete events
75
Modification events
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: 50160000EFC8AD192105DB01 | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: 85268E212C1DFB7F7A7E5129873732C0D64F645F89DD142DB7B1186525F0E713 | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Temp\is-PDHJ0.tmp\vc_redist.x86.exe | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFilesHash |
Value: FB775D2F1566FF0A59A32BED54F41D2CD88CA64450A0B87607F01ED849BF3419 | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{8A1033B0-EF33-4FB5-97A1-C47A7DCDD7E6}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.5 (u) | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{8A1033B0-EF33-4FB5-97A1-C47A7DCDD7E6}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\ClipGrab | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{8A1033B0-EF33-4FB5-97A1-C47A7DCDD7E6}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\ClipGrab\ | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{8A1033B0-EF33-4FB5-97A1-C47A7DCDD7E6}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: ClipGrab | |||
| (PID) Process: | (5712) clipgrab-3.9.10-portable.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{8A1033B0-EF33-4FB5-97A1-C47A7DCDD7E6}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
649
Suspicious files
177
Text files
85
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\is-JECM5.tmp | — | |
MD5:— | SHA256:— | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\clipgrab-3.9.10-portable.exe | — | |
MD5:— | SHA256:— | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\zbShieldUtils.dll | executable | |
MD5:B83F5833E96C2EB13F14DCCA805D51A1 | SHA256:00E667B838A4125C8CF847936168BB77BB54580BC05669330CB32C0377C4A401 | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\is-1TBJE.tmp | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\loader.gif | image | |
MD5:F23A523B82AD9103A9AC1DCC33ECA72F | SHA256:59853C413B0813DED6F1E557959768D6662F010F49884D36B62C13038FAC739C | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\RAV_Cross.png | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\finish.png | image | |
MD5:251D2D4FE20ED5D109C1164B4E296634 | SHA256:3F01866E78099BADDAB8CB9E0606664880BD459296760B63F0F98C4F6909FE00 | |||
| 488 | clipgrab-3.9.10-dotinstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-9BN5U.tmp\is-B70VU.tmp | executable | |
MD5:57A6D0F40EBA38813FB7211949E35F45 | SHA256:43ECD4597B2DFE169F3696C72E6AC5665391FD44B21D9B4222A72030427E09D4 | |||
| 6840 | clipgrab-3.9.10-portable.exe | C:\Users\admin\AppData\Local\Temp\is-Q9TE7.tmp\clipgrab-3.9.10-portable.tmp | executable | |
MD5:8DCFBB299A19324BF353D70D7076BCBE | SHA256:1D71E2022FA2ABAE4C1E63DC7DF8D65D0C1193516BCA28C5EAF3817284182E30 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
121
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6320 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3784 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3708 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3784 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3184 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5400 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRBq81UG1MnDOVNKqff0SSEz6JuZwQU6IPEM9fcnwycdpoKptTfh6ZeWO4CEzMAAWTujc16eayoCZIAAAABZO4%3D | unknown | — | — | whitelisted |
5400 | UnifiedStub-installer.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ID%20Verified%20CS%20AOC%20CA%2001.crl | unknown | — | — | whitelisted |
5400 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
5400 | UnifiedStub-installer.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Public%20RSA%20Timestamping%20CA%202020.crl | unknown | — | — | whitelisted |
5400 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAHN4xbodlbjNQAAAAAAAc%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1148 | RUXIMICS.exe | 52.167.17.97:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2120 | MoUsoCoreWorker.exe | 52.167.17.97:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6320 | svchost.exe | 52.167.17.97:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6320 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6320 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
488 | clipgrab-3.9.10-dotinstaller.tmp | 65.9.94.230:443 | d1g2dvgwts5bro.cloudfront.net | AMAZON-02 | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3708 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
d1g2dvgwts5bro.cloudfront.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
shield.reasonsecurity.com |
| unknown |
Threats
Process | Message |
|---|---|
clipgrab.exe | QObject::connect: signal not found in QTreeView
|
clipgrab.exe | "C:\\Program Files (x86)\\ClipGrab\\python\\python.exe: can't find '__main__' module in ''\r\n"
|
clipgrab.exe | Could not reach update server.
|
clipgrab.exe | "WARNING: [youtube:tab] Incomplete data received. Retrying (1/3)...\nWARNING: [youtube:tab] Incomplete data received. Retrying (2/3)...\nWARNING: [youtube:tab] Incomplete data received. Retrying (3/3)...\nWARNING: [youtube:tab] Incomplete data received. Giving up after 3 retries\n"
|
clipgrab.exe | ""
|
clipgrab.exe | Discovered video: "Coffee Run - Blender Open Movie"
|
clipgrab.exe | QObject::connect: signal not found in QTreeView
|
rsEngineSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EPP\x64\SQLite.Interop.dll"...
|
clipgrab.exe | Could not reach update server.
|
clipgrab.exe | Found youtube-dlp "2024.08.06\r"
|