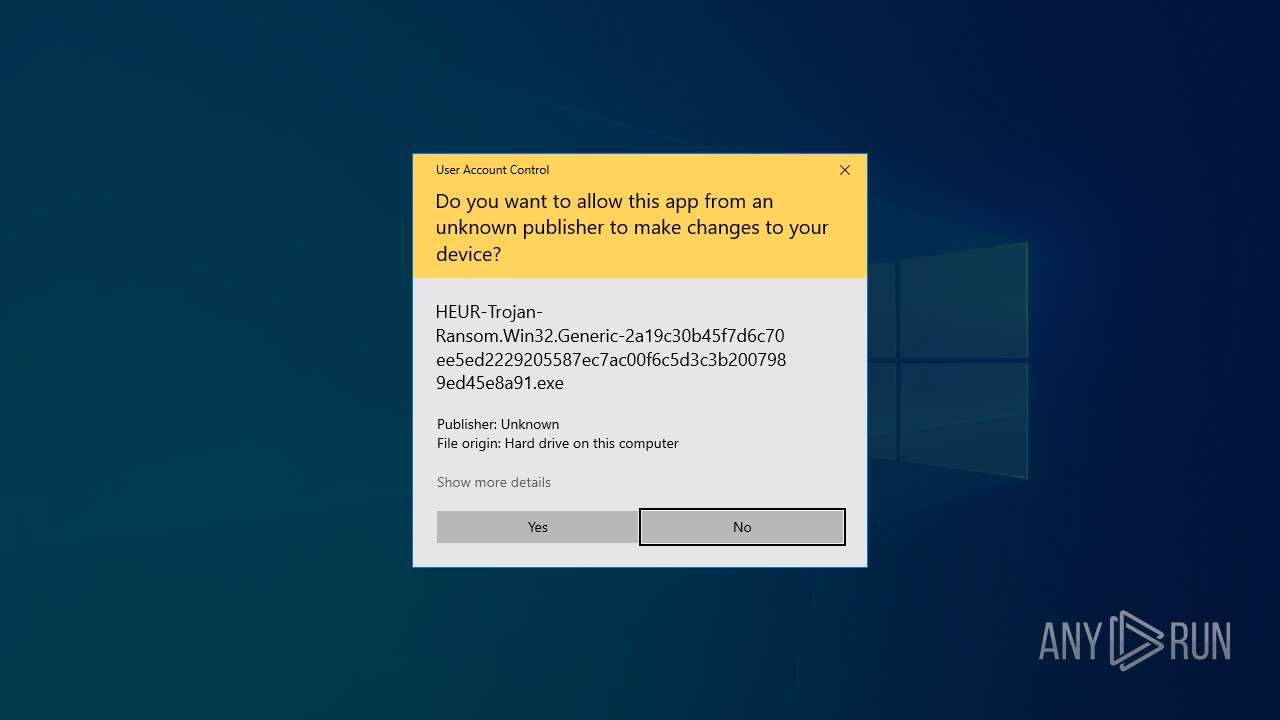
| File name: | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.7z |
| Full analysis: | https://app.any.run/tasks/6674a856-7bf9-4093-8dc0-3f0577b1cdad |
| Verdict: | Malicious activity |
| Threats: | Medusa is a ransomware malware family targeting businesses and institutions. Medusa encrypts crucial data, rendering it inaccessible, and attempts to pressure users to pay to regain control of their information. The group behind this malicious software hosts a TOR website where it shares the list of the organizations whose infrastructure has been compromised. This malware utilizes various tactics, including exploiting vulnerabilities and employs a unique file extension (".MEDUSA") to mark encrypted files. |
| Analysis date: | May 10, 2025, 11:55:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 0D59D6A06F96761D71D0D2CCEC6ABBEC |
| SHA1: | 529D3CB6BE743DC06CEB7688358ABF60D8131405 |
| SHA256: | E855CB6EEEB2B9B17D0F52790DA2FA74D0960FA3735A134482181265E80D7DAC |
| SSDEEP: | 6144:lkZ3Vzq7u6WEs8k4t1nCNZ9x4W2z7AJeQkBq5jO98qIiftsBykZA:l43Vzq7aES4bnCNZ7oAJT7w8qFfCJA |
MALICIOUS
Changes the autorun value in the registry
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
MEDUSALOCKER has been detected (YARA)
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
RANSOMWARE has been detected
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
SUSPICIOUS
Uses WMIC.EXE to obtain shadow copy information
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Write to the desktop.ini file (may be used to cloak folders)
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6964)
Creates file in the systems drive root
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Executable content was dropped or overwritten
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Uses pipe srvsvc via SMB (transferring data)
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Process drops legitimate windows executable
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6800)
Creates files or folders in the user directory
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Reads the machine GUID from the registry
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Checks supported languages
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
- ShellExperienceHost.exe (PID: 6964)
- SearchApp.exe (PID: 7484)
Manual execution by a user
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4024)
Reads the computer name
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
- ShellExperienceHost.exe (PID: 6964)
- SearchApp.exe (PID: 7484)
Drops a (possible) Coronavirus decoy
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with german language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Process checks computer location settings
- SearchApp.exe (PID: 7484)
Aspack has been detected
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with czech language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with french language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with spanish language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with bulgarian language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with english language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with japanese language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with Italian language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with korean language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with polish language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with portuguese language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
The sample compiled with russian language support
- HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe (PID: 3240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:06:28 12:03:02+00:00 |
| ArchivedFileName: | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe |
Total processes
149
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3240 | "C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe" | C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4024 | wmic.exe SHADOWCOPY /nointeractive | C:\Windows\SysWOW64\wbem\WMIC.exe | — | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 44124 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5744 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6244 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6964 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7152 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 058
Read events
39 829
Write events
6 162
Delete events
6 067
Modification events
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.7z | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
109
Suspicious files
1 999
Text files
101
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
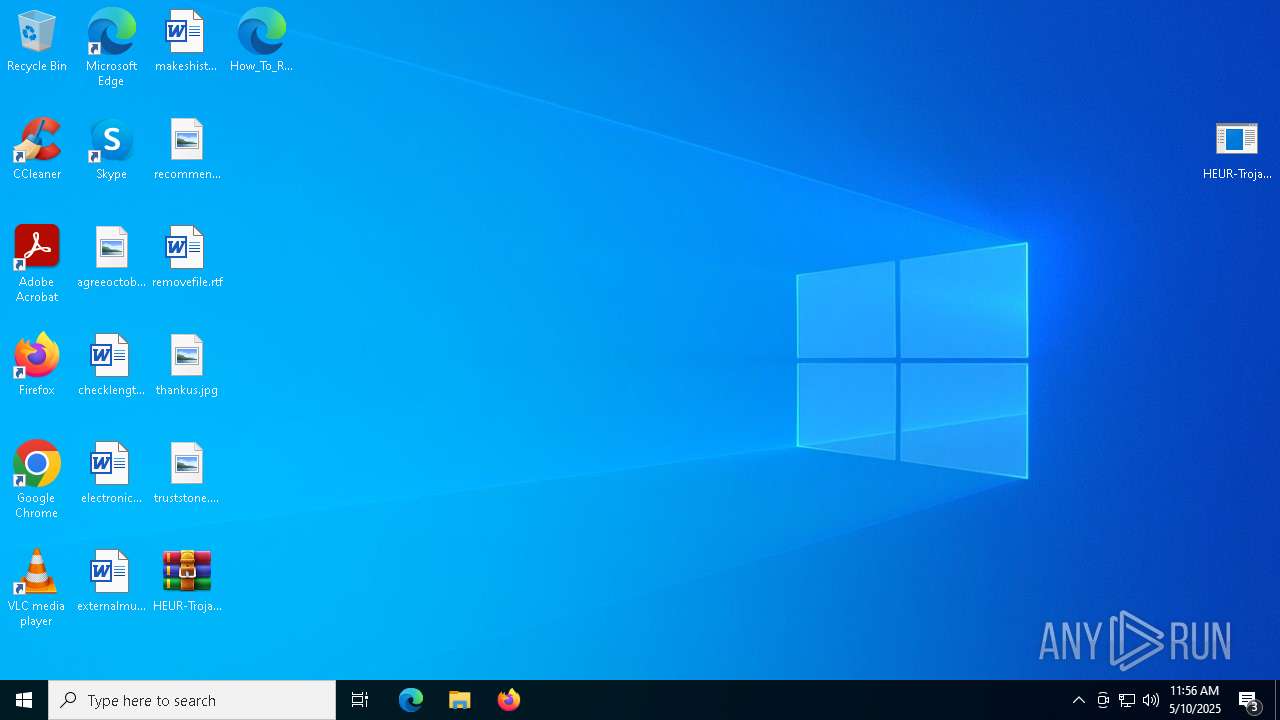
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | C:\Users\Public\Desktop\How_To_Recover.mht | binary | |
MD5:6C62AEF73FBE797CB7328A0F24E8224B | SHA256:CF118F19B398D5452CF66CF1115654B30697918C092E2AF09197EF8DA92A3885 | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | \\?\Volume{eaf65672-68c3-4f99-8d5c-104b5f4d8fff}\$RECYCLE.BIN\S-1-5-21-1693682860-607145093-2874071422-1001\desktop.ini | text | |
MD5:AD0B0B4416F06AF436328A3C12DC491B | SHA256:23521DE51CA1DB2BC7B18E41DE7693542235284667BF85F6C31902547A947416 | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | C:\How_To_Recover.mht | binary | |
MD5:6C62AEF73FBE797CB7328A0F24E8224B | SHA256:CF118F19B398D5452CF66CF1115654B30697918C092E2AF09197EF8DA92A3885 | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | C:\BOOTNXT.inprocess | binary | |
MD5:93B885ADFE0DA089CDF634904FD59F71 | SHA256:6E340B9CFFB37A989CA544E6BB780A2C78901D3FB33738768511A30617AFA01D | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | C:\bootmgr.inprocess | binary | |
MD5:D9364029A39FF14634FF132E2786CB47 | SHA256:C399AF25EAFAF9D89B33C5F0613D00B690BE5C11163DE45AA2F5D5739EFBB05F | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | \\?\Volume{eaf65672-68c3-4f99-8d5c-104b5f4d8fff}\Recovery\WindowsRE\boot.sdi.inprocess | binary | |
MD5:22D9945B4AAE36DD59620A918F2E65F4 | SHA256:CD2C00CE027687CE4A8BDC967F26A8AB82F651C9BECD703658BA282EC49702BD | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | \\?\Volume{2f5c5e73-85a9-11eb-90a8-9a9b76358421}\Recovery\WindowsRE\boot.sdi.inprocess | binary | |
MD5:22D9945B4AAE36DD59620A918F2E65F4 | SHA256:CD2C00CE027687CE4A8BDC967F26A8AB82F651C9BECD703658BA282EC49702BD | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | \\?\Volume{2f5c5e71-85a9-11eb-90a8-9a9b76358421}\NvVars.covid | binary | |
MD5:0DF7408F76827F81F5E767D8C3F98CF3 | SHA256:0598522041626ED493E3CF44C05F2C0EF706D101733D8336BCA7DD72F5845E62 | |||
| 3240 | HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | \\?\Volume{2f5c5e71-85a9-11eb-90a8-9a9b76358421}\$RECYCLE.BIN\desktop.ini | ini | |
MD5:AD0B0B4416F06AF436328A3C12DC491B | SHA256:23521DE51CA1DB2BC7B18E41DE7693542235284667BF85F6C31902547A947416 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6800.46848\HEUR-Trojan-Ransom.Win32.Generic-2a19c30b45f7d6c70ee5ed2229205587ec7ac00f6c5d3c3b2007989ed45e8a91.exe | executable | |
MD5:59A11294CC1496126FCD9AF1A3371D0B | SHA256:2A19C30B45F7D6C70EE5ED2229205587EC7AC00F6C5D3C3B2007989ED45E8A91 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7588 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7588 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7484 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.2:445 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |