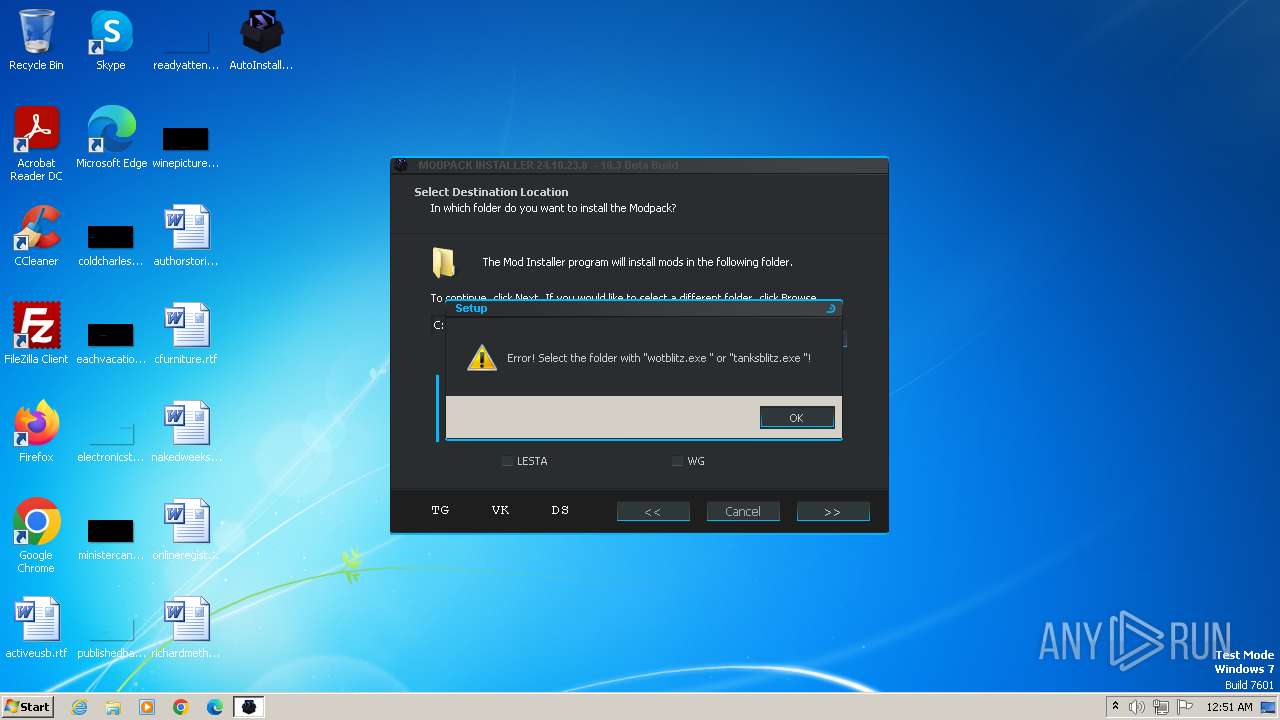
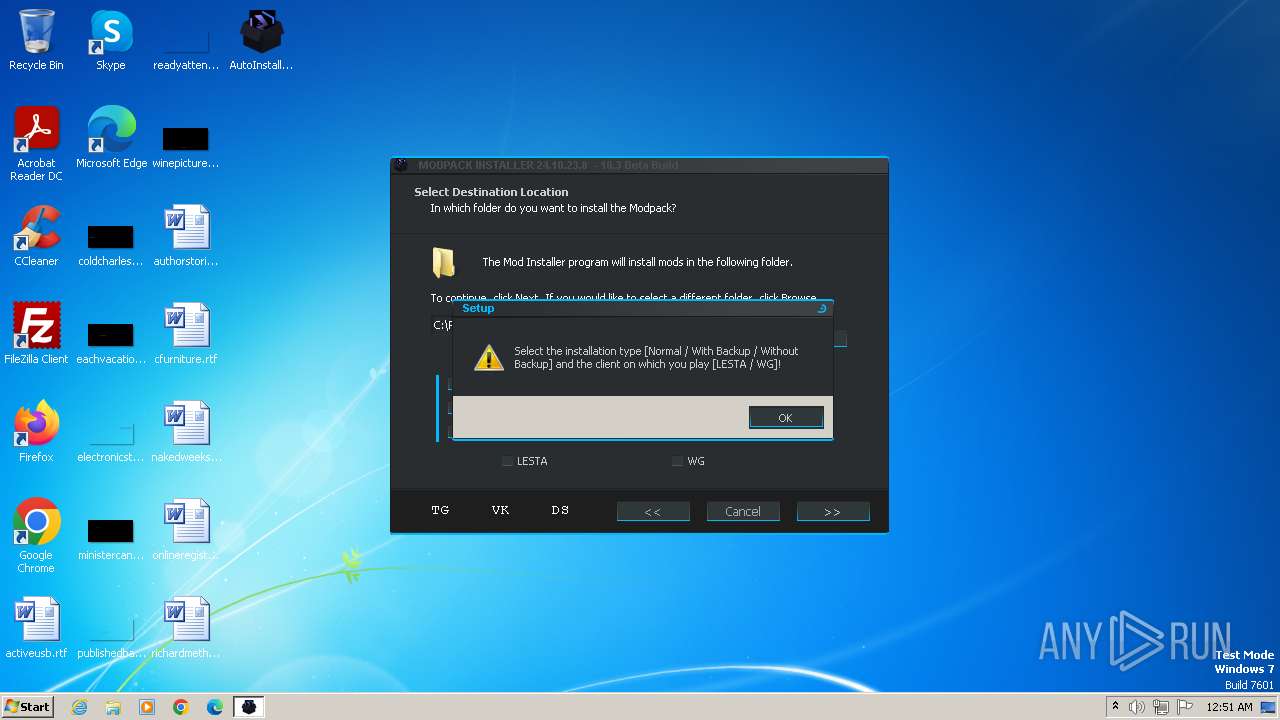
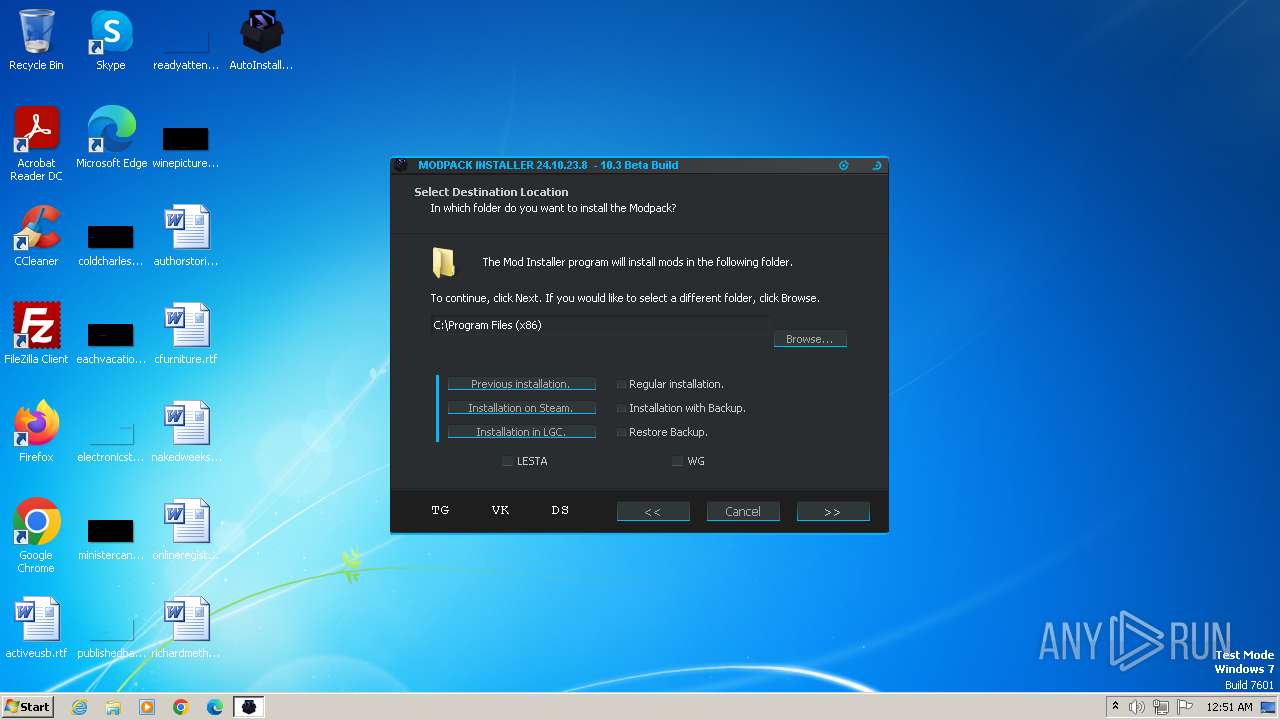
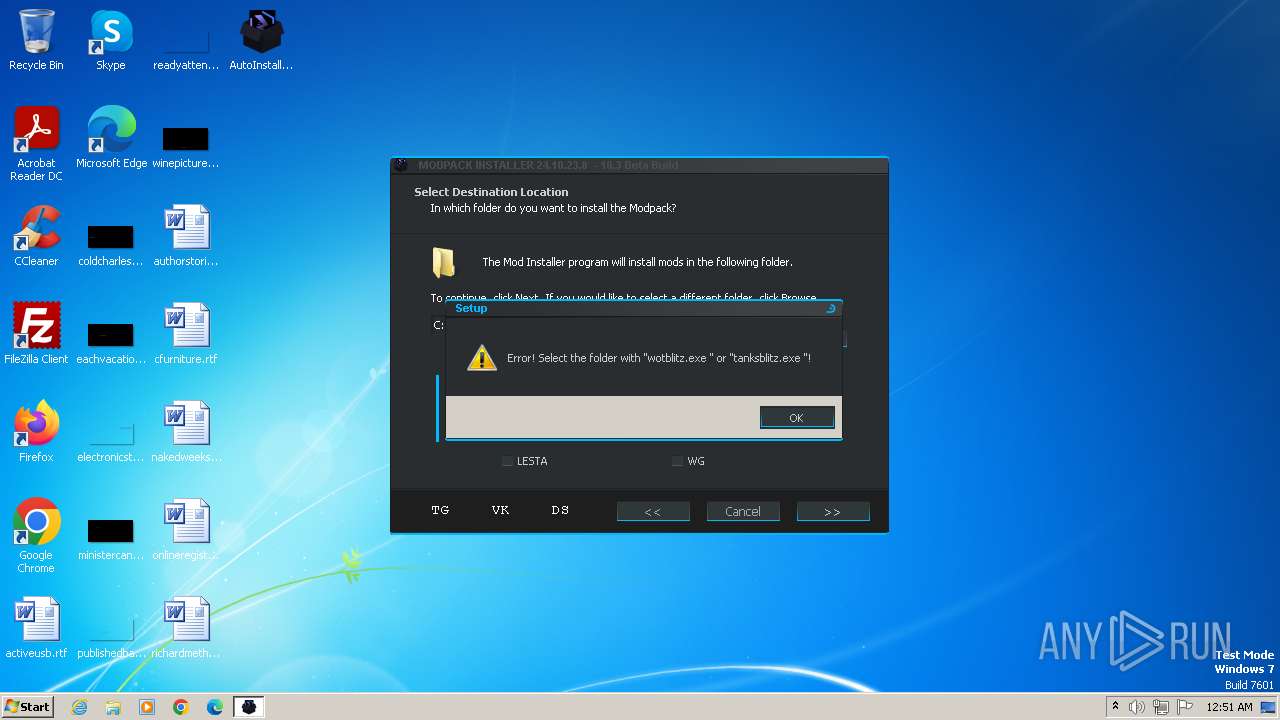
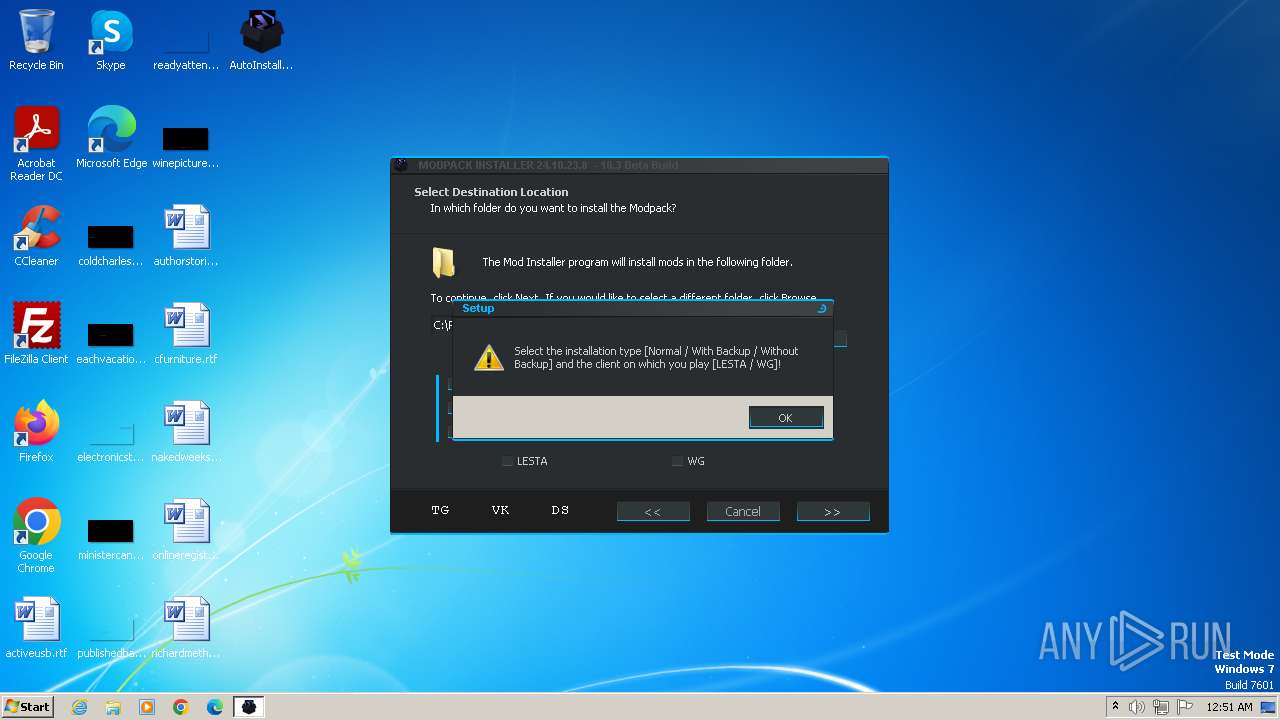
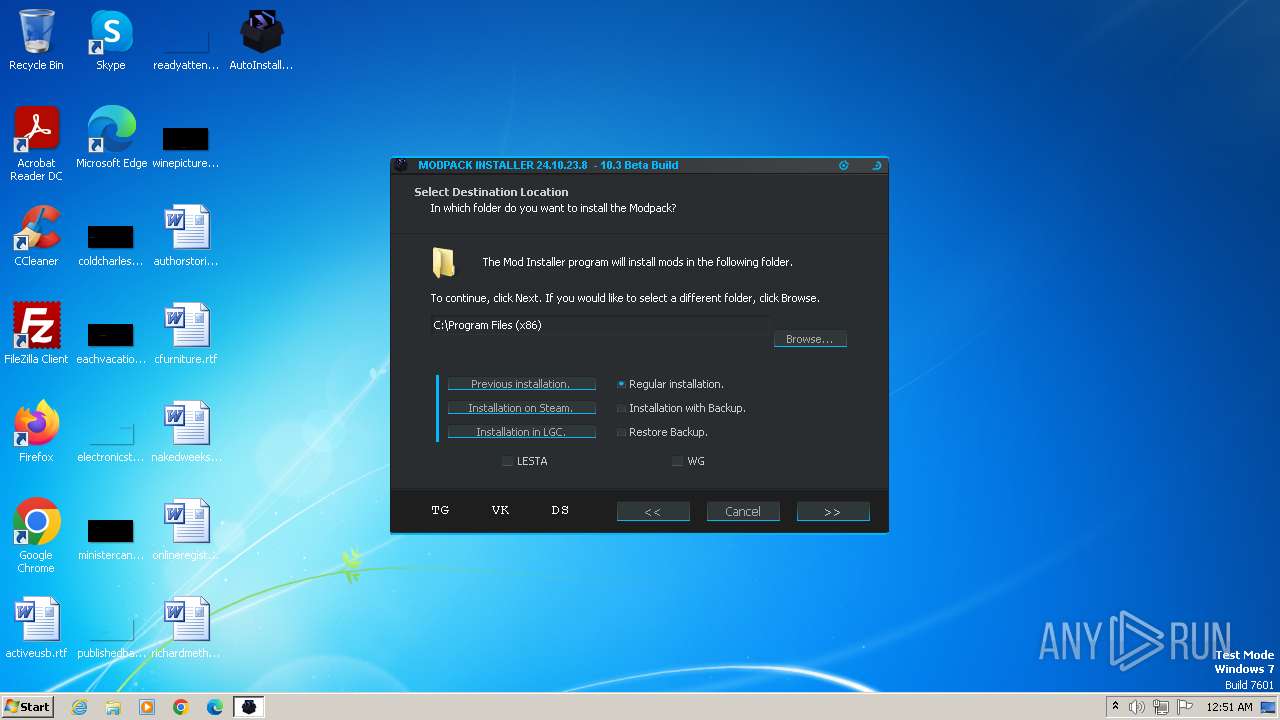
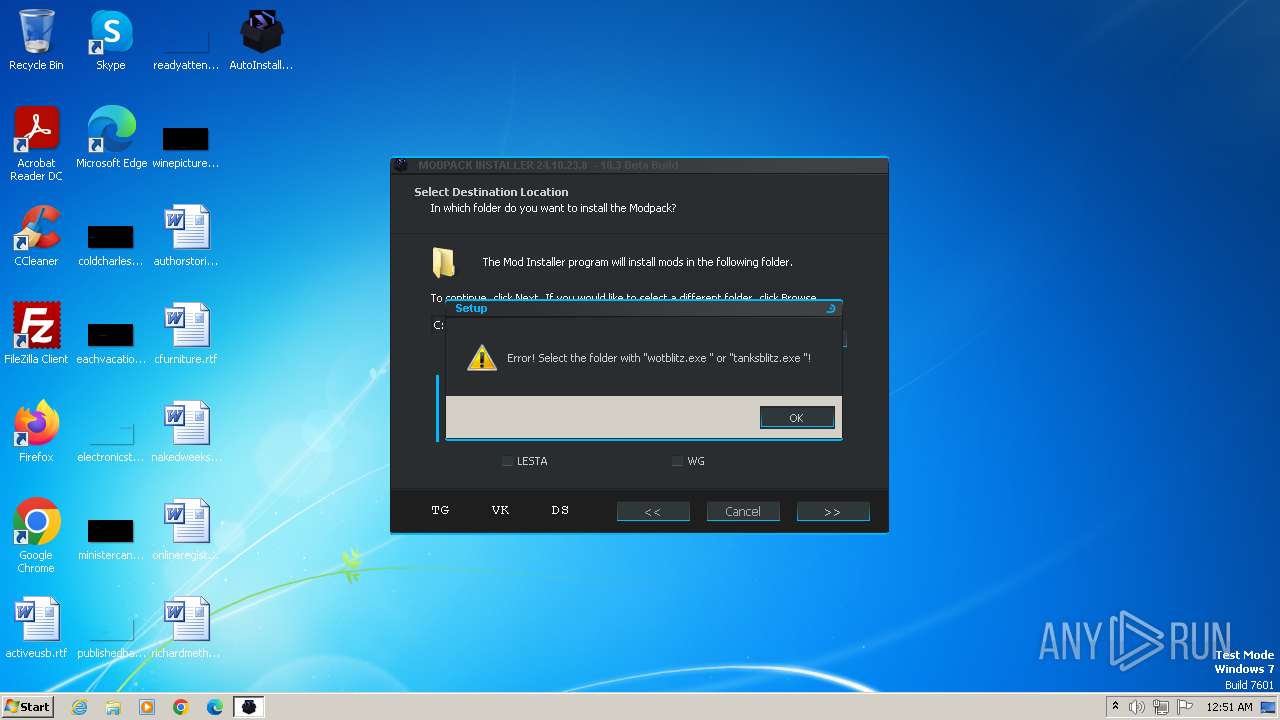
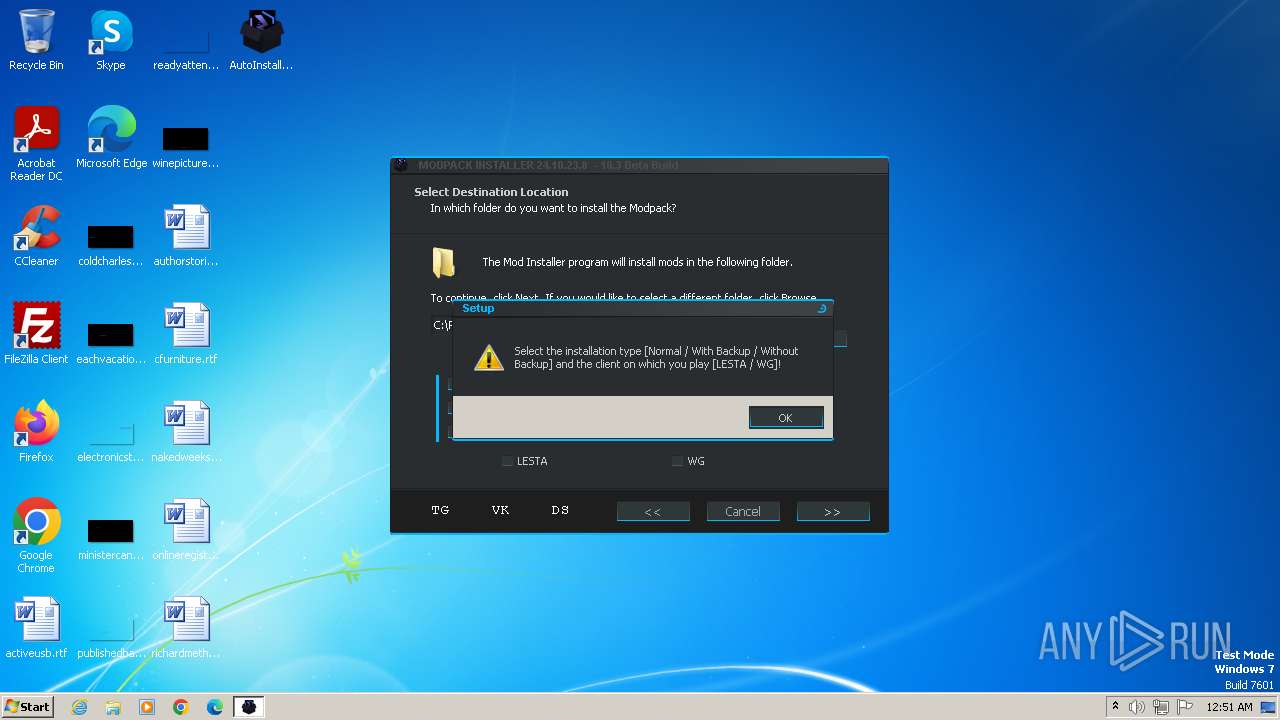
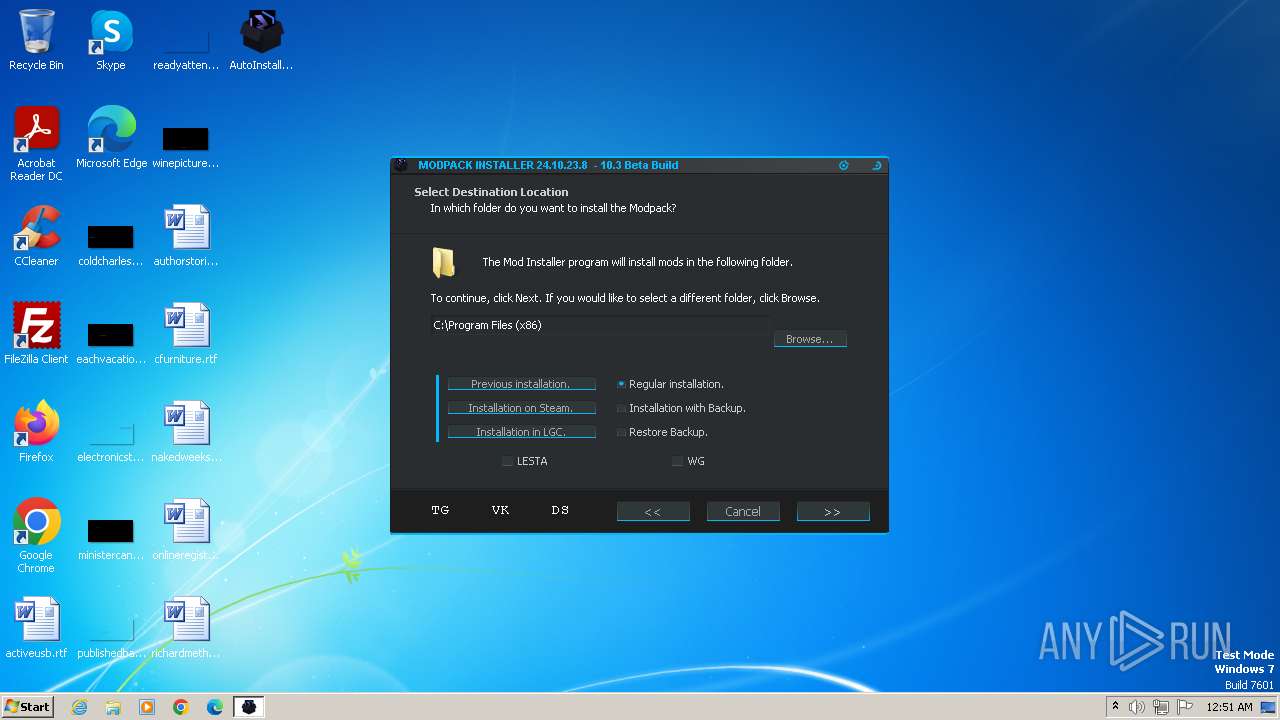
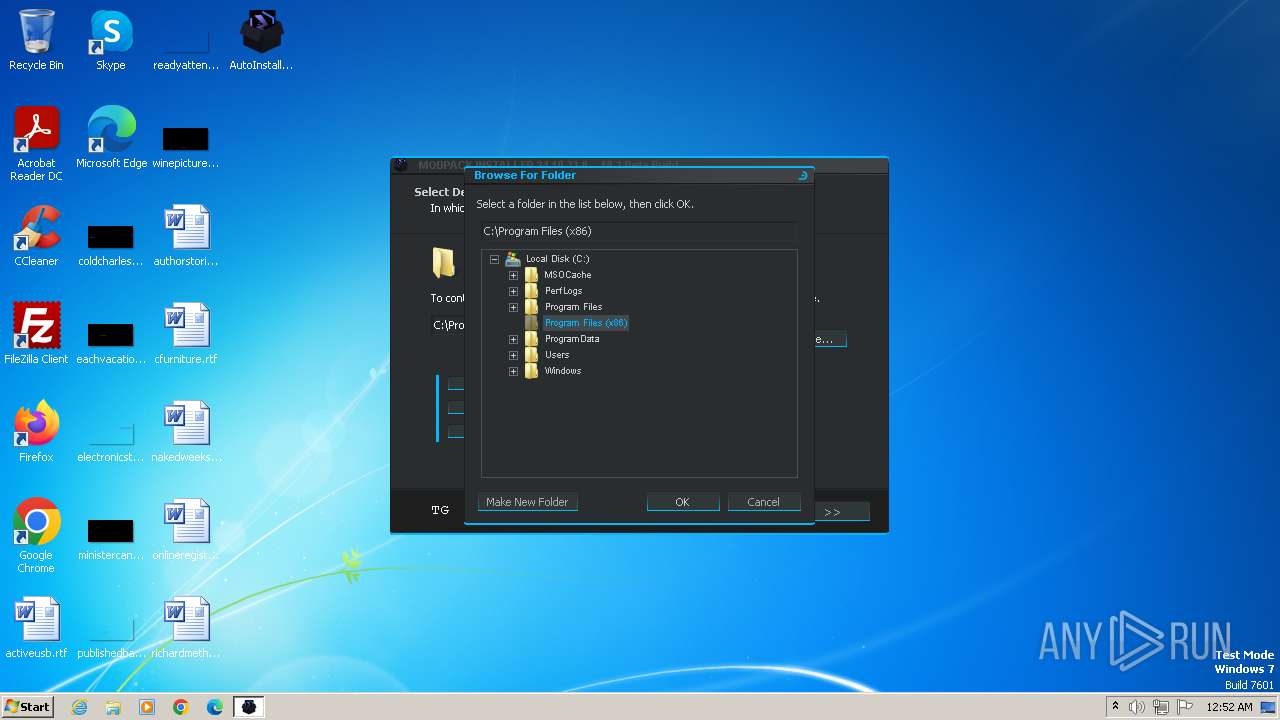
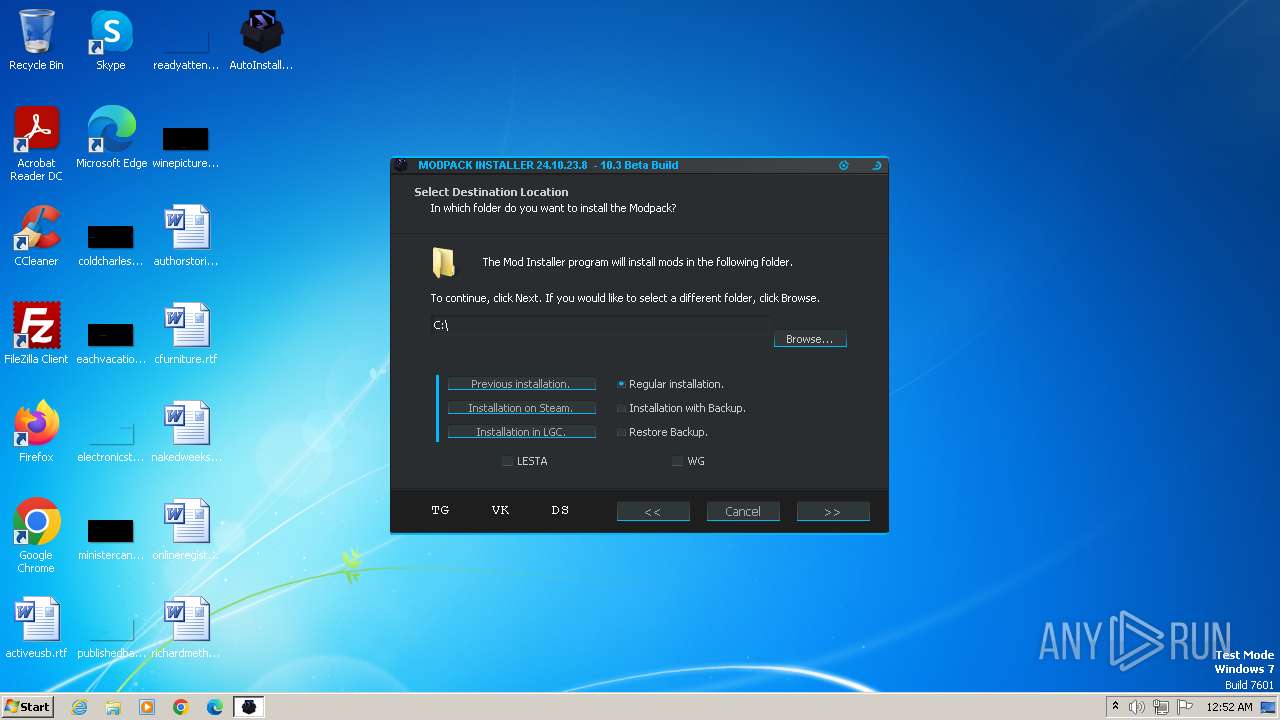
| File name: | AutoInstaller.exe |
| Full analysis: | https://app.any.run/tasks/33011c55-4f58-4b2d-a4a9-9175e6cee8b1 |
| Verdict: | Malicious activity |
| Threats: | SystemBC is a Remote Access Trojan (RAT) that can hide communication with the Command and Control server, and deposit other malware strains. |
| Analysis date: | October 24, 2023, 23:50:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8F797543072BEB845A51F33EA12278AF |
| SHA1: | 177981EF0454885F372EB53FA672A62702196E65 |
| SHA256: | E8187F81F39C861D5BEF4E0A0905AB1AB257B05EEEF8AE5AE5C8E7A4ACEF71B0 |
| SSDEEP: | 49152:r7HecD4dnbibBl2kG7DC51AeTTJ34bZtV0o+kGJfzhLN24LLKJ8JN+UAb7EMZsga:X+cD4dnJ25ueTTd4tt2jzh84vTJNknEN |
MALICIOUS
Drops the executable file immediately after the start
- AutoInstaller.exe (PID: 3016)
- AutoInstaller.exe (PID: 3416)
- AutoInstaller.tmp (PID: 1240)
- Mod_Installer.exe (PID: 3648)
- Mod_Installer.tmp (PID: 2252)
- AutoInstaller.exe (PID: 3136)
Application was dropped or rewritten from another process
- Mod_Installer.exe (PID: 3648)
Loads dropped or rewritten executable
- Mod_Installer.tmp (PID: 2252)
SYSTEMBC has been detected (YARA)
- Mod_Installer.tmp (PID: 2252)
SUSPICIOUS
Reads the Windows owner or organization settings
- AutoInstaller.tmp (PID: 1412)
- Mod_Installer.tmp (PID: 2252)
- AutoInstaller.tmp (PID: 1240)
Reads the Internet Settings
- AutoInstaller.tmp (PID: 1412)
- AutoInstaller.tmp (PID: 1240)
Reads settings of System Certificates
- AutoInstaller.tmp (PID: 1240)
Process drops legitimate windows executable
- Mod_Installer.tmp (PID: 2252)
INFO
Create files in a temporary directory
- AutoInstaller.exe (PID: 3416)
- AutoInstaller.exe (PID: 3016)
- AutoInstaller.exe (PID: 3136)
- AutoInstaller.tmp (PID: 1240)
- Mod_Installer.exe (PID: 3648)
- Mod_Installer.tmp (PID: 2252)
Reads the computer name
- AutoInstaller.tmp (PID: 2120)
- AutoInstaller.tmp (PID: 1412)
- Mod_Installer.tmp (PID: 2252)
- AutoInstaller.tmp (PID: 1240)
Checks supported languages
- AutoInstaller.tmp (PID: 2120)
- AutoInstaller.exe (PID: 3416)
- AutoInstaller.exe (PID: 3016)
- AutoInstaller.tmp (PID: 1412)
- Mod_Installer.exe (PID: 3648)
- Mod_Installer.tmp (PID: 2252)
- AutoInstaller.exe (PID: 3136)
- AutoInstaller.tmp (PID: 1240)
Reads the machine GUID from the registry
- AutoInstaller.tmp (PID: 1240)
Application was dropped or rewritten from another process
- AutoInstaller.tmp (PID: 1412)
- AutoInstaller.tmp (PID: 2120)
- AutoInstaller.tmp (PID: 1240)
- Mod_Installer.tmp (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 68096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
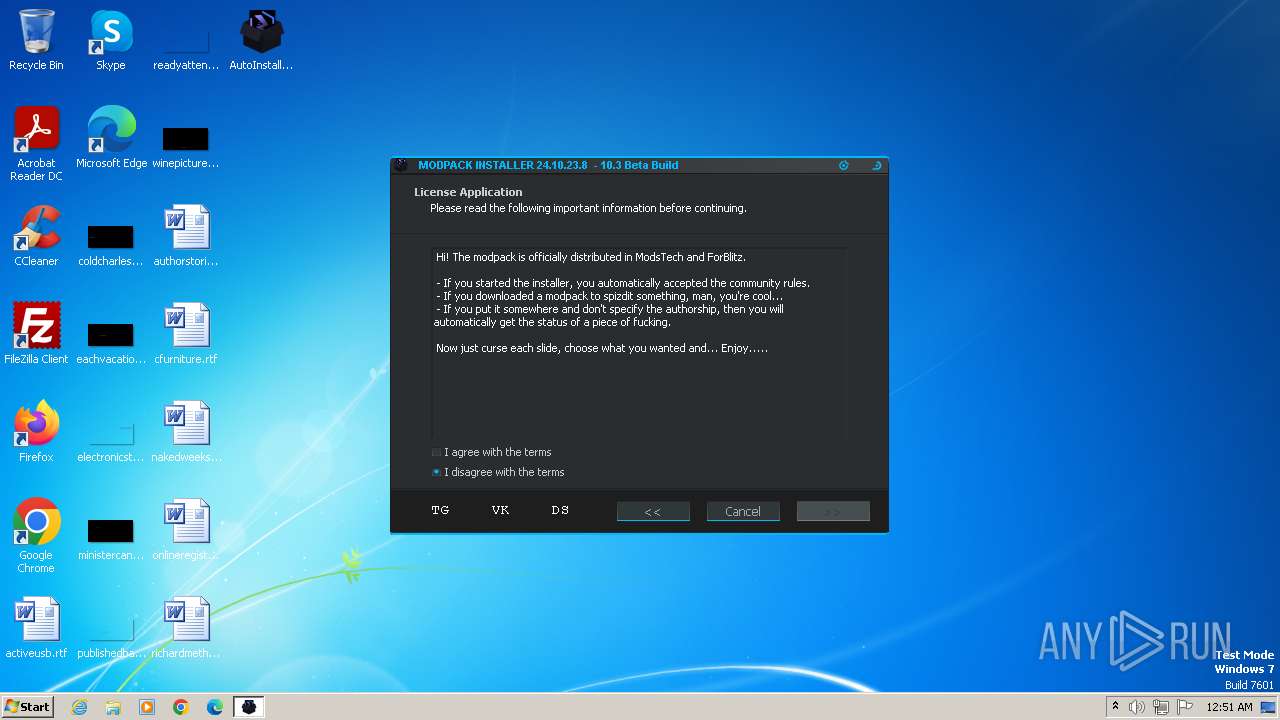
| CompanyName: | ModsTech |
| FileDescription: | Mod installer from the ModsTech community. |
| FileVersion: | 1.0.0.0 |
| LegalCopyright: | Copyright © 2020-2023 ModsTech. |
| OriginalFileName: | |
| ProductName: | AutoInstaller 1.0.0.0 |
| ProductVersion: | 1.0.0.0 |
Total processes
50
Monitored processes
8
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
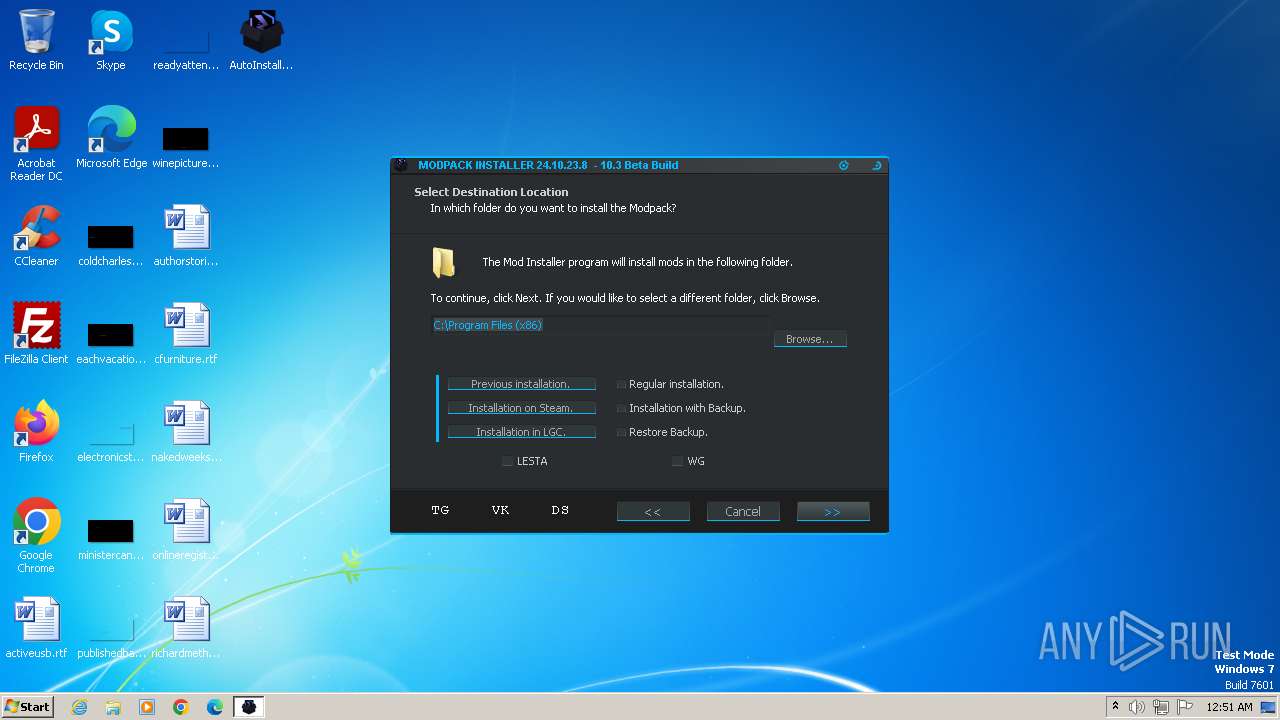
| 1240 | "C:\Users\admin\AppData\Local\Temp\is-7FBFN.tmp\AutoInstaller.tmp" /SL5="$60300,811008,811008,C:\Users\admin\Desktop\AutoInstaller.exe" /VERYSILENT | C:\Users\admin\AppData\Local\Temp\is-7FBFN.tmp\AutoInstaller.tmp | AutoInstaller.exe | ||||||||||||
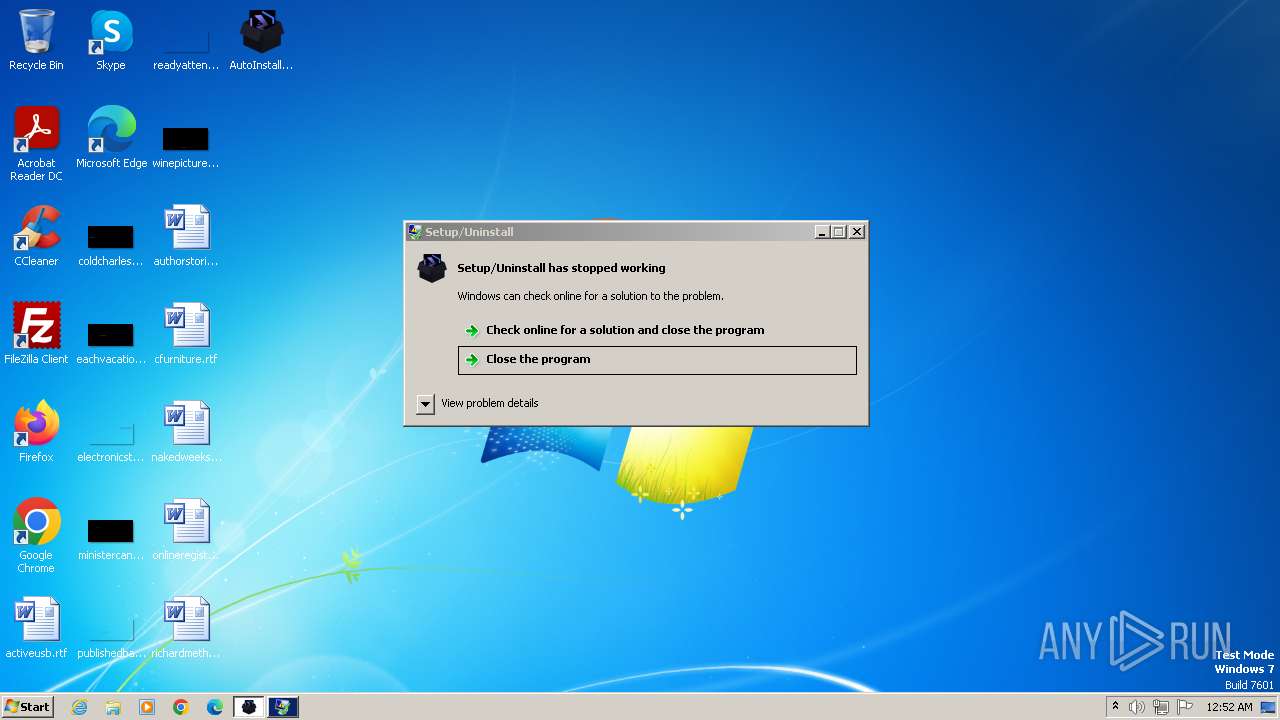
User: admin Company: ModsTech Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\AppData\Local\Temp\is-7SODI.tmp\AutoInstaller.tmp" /SL5="$30302,811008,811008,C:\Users\admin\Desktop\AutoInstaller.exe" /SPAWNWND=$140216 /NOTIFYWND=$50300 | C:\Users\admin\AppData\Local\Temp\is-7SODI.tmp\AutoInstaller.tmp | — | AutoInstaller.exe | |||||||||||
User: admin Company: ModsTech Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\is-23S4I.tmp\AutoInstaller.tmp" /SL5="$50300,811008,811008,C:\Users\admin\Desktop\AutoInstaller.exe" | C:\Users\admin\AppData\Local\Temp\is-23S4I.tmp\AutoInstaller.tmp | — | AutoInstaller.exe | |||||||||||
User: admin Company: ModsTech Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\AppData\Local\Temp\is-69CH9.tmp\Mod_Installer.tmp" /SL5="$70300,2160366,171008,C:\Users\admin\AppData\Local\Temp\Mod_Installer.exe" | C:\Users\admin\AppData\Local\Temp\is-69CH9.tmp\Mod_Installer.tmp | Mod_Installer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\Desktop\AutoInstaller.exe" /SPAWNWND=$140216 /NOTIFYWND=$50300 | C:\Users\admin\Desktop\AutoInstaller.exe | AutoInstaller.tmp | ||||||||||||
User: admin Company: ModsTech Integrity Level: HIGH Description: Mod installer from the ModsTech community. Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3136 | "C:\Users\admin\Desktop\AutoInstaller.exe" /VERYSILENT | C:\Users\admin\Desktop\AutoInstaller.exe | — | AutoInstaller.tmp | |||||||||||
User: admin Company: ModsTech Integrity Level: HIGH Description: Mod installer from the ModsTech community. Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3416 | "C:\Users\admin\Desktop\AutoInstaller.exe" | C:\Users\admin\Desktop\AutoInstaller.exe | — | explorer.exe | |||||||||||
User: admin Company: ModsTech Integrity Level: MEDIUM Description: Mod installer from the ModsTech community. Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3648 | "C:\Users\admin\AppData\Local\Temp\Mod_Installer.exe" | C:\Users\admin\AppData\Local\Temp\Mod_Installer.exe | — | AutoInstaller.tmp | |||||||||||
User: admin Company: ModsTech Integrity Level: HIGH Description: Mod installer from the ModsTech community. Exit code: 0 Version: 24.10.23.8 Modules
| |||||||||||||||
Total events
4 253
Read events
4 221
Write events
20
Delete events
12
Modification events
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 3C9B5239D2379B012CAE31442BCBBCB7A41AAAED8CBCA9F318B07ACE2E740BE4 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 840500004C1FCBE9D406DA01 | |||
| (PID) Process: | (1412) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1240) AutoInstaller.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1240) AutoInstaller.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
Executable files
16
Suspicious files
0
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1240 | AutoInstaller.tmp | C:\Users\admin\AppData\Local\Temp\is-IJNFM.tmp\is-DPAA2.tmp | executable | |
MD5:AE08008756A1B19065182C2710A3961E | SHA256:2D70D84CD7B135E0903FF195EE9DCC526038573170C49510C2208F08DC5350A9 | |||
| 2252 | Mod_Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-IE4QF.tmp\1_03-Interface-v2.bk | text | |
MD5:369E267443A95160687AAFA9CB9E390D | SHA256:86F823618CBF2A3700265F1E5FD791F5D3C0922B1A8977F83530ACD43B3E39E0 | |||
| 2252 | Mod_Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-IE4QF.tmp\isskinu.dll | executable | |
MD5:7D9087C4E2F9AB2DB78A46AB52A7F360 | SHA256:FF1374ABD93690F5E6E591BAE23B49AACC8BBE8B7B05B539EC8AEE755070A0E3 | |||
| 2252 | Mod_Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-IE4QF.tmp\1_51-Flags-v1.bk | text | |
MD5:B44095800E0F835536FD77CC2042F463 | SHA256:2A951D5205E1CAF588CD5444BBBE6888C0D6EEA666A459289D2B1239B8B1C32A | |||
| 2252 | Mod_Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-IE4QF.tmp\1_52-Flags-v2.bk | text | |
MD5:B44095800E0F835536FD77CC2042F463 | SHA256:2A951D5205E1CAF588CD5444BBBE6888C0D6EEA666A459289D2B1239B8B1C32A | |||
| 2252 | Mod_Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-IE4QF.tmp\2_06-Exhaust-v1.bk | text | |
MD5:B4FD4DFF3EC4898217AD49629AA55DDE | SHA256:55D3BCAF0F59231C18D85DDD442A9D280E1953CAF7F5670D527FA724340E518D | |||
| 2252 | Mod_Installer.tmp | C:\Users\admin\AppData\Local\Temp\is-IE4QF.tmp\1_02-Interface-v1.bk | text | |
MD5:369E267443A95160687AAFA9CB9E390D | SHA256:86F823618CBF2A3700265F1E5FD791F5D3C0922B1A8977F83530ACD43B3E39E0 | |||
| 3648 | Mod_Installer.exe | C:\Users\admin\AppData\Local\Temp\is-69CH9.tmp\Mod_Installer.tmp | executable | |
MD5:6F2357869B62A65609506FCE9A782C0D | SHA256:58302EE01FD9D1DF285555D5DE8F477FC16EC329483D704F4FCB2D64E63BA0F1 | |||
| 1240 | AutoInstaller.tmp | C:\Users\admin\AppData\Local\Temp\Mod_Installer.exe | executable | |
MD5:AE08008756A1B19065182C2710A3961E | SHA256:2D70D84CD7B135E0903FF195EE9DCC526038573170C49510C2208F08DC5350A9 | |||
| 3136 | AutoInstaller.exe | C:\Users\admin\AppData\Local\Temp\is-7FBFN.tmp\AutoInstaller.tmp | executable | |
MD5:27BE9CD516395BBE00C9DE447F243B5B | SHA256:DA00D3BA399333B5627EC8D8E5B2197108B3809856F1A7FDAA1AD4BBCE669E77 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1240 | AutoInstaller.tmp | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |