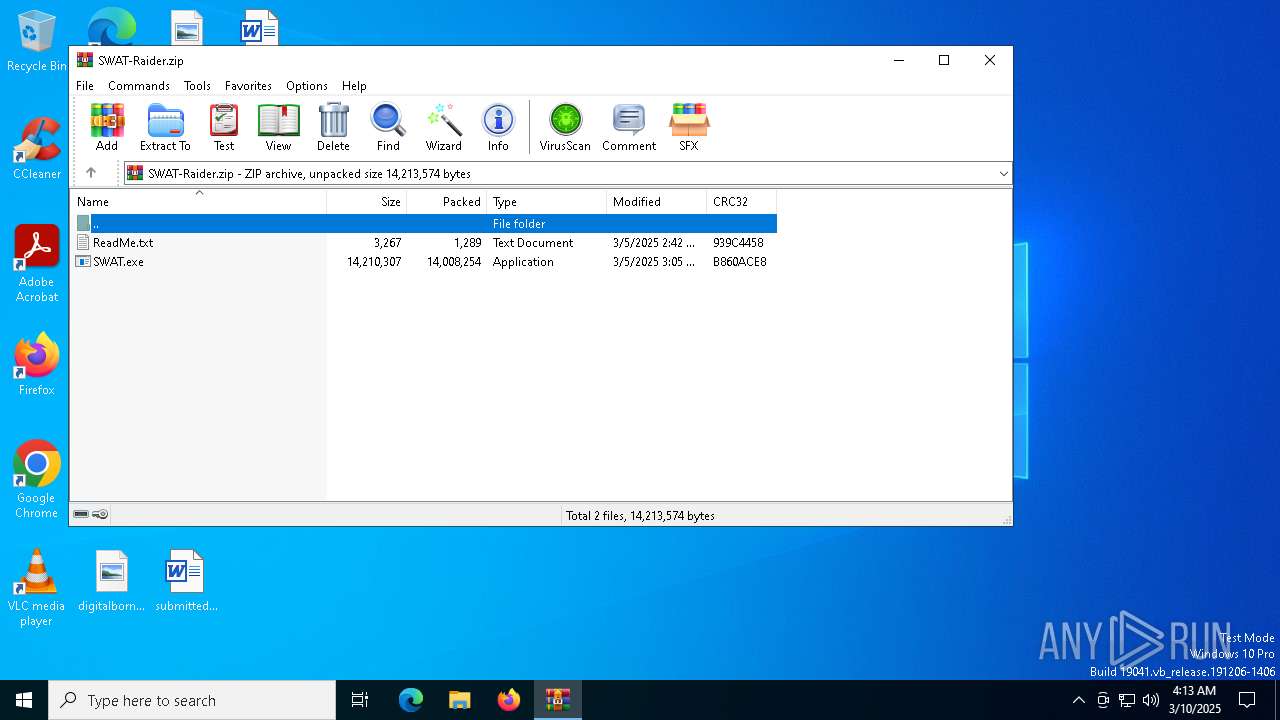
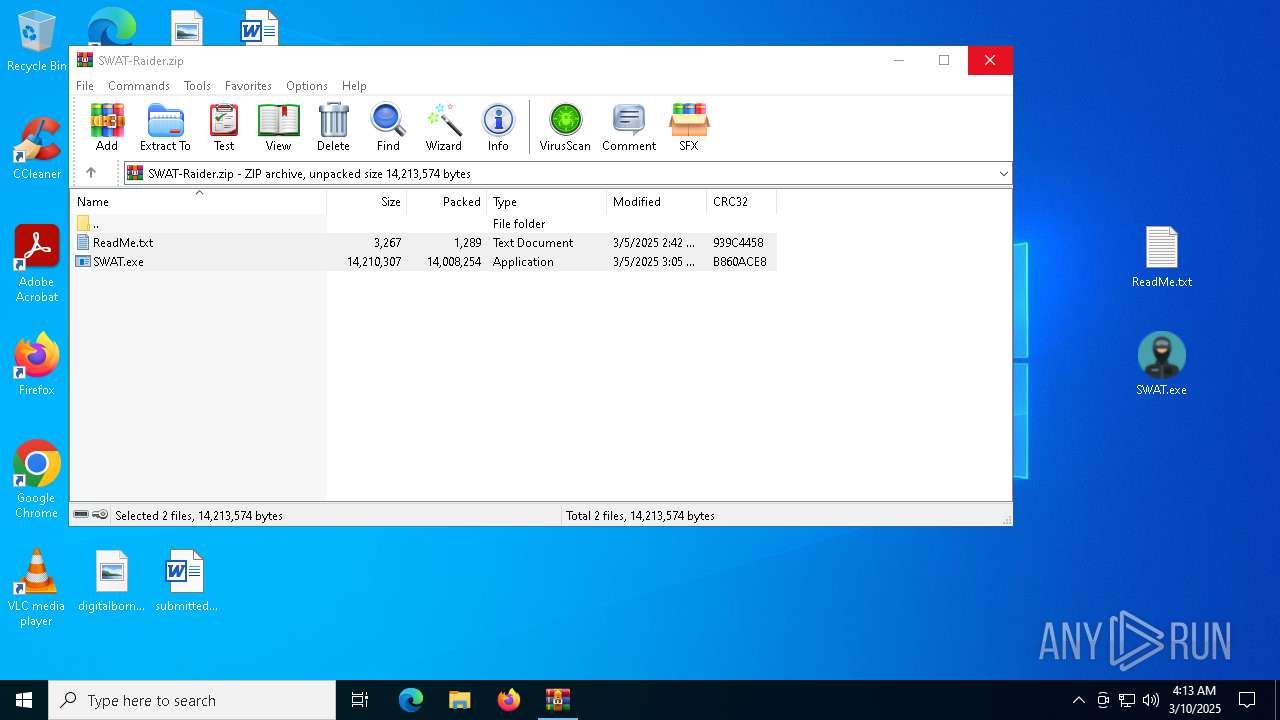
| File name: | SWAT-Raider.zip |
| Full analysis: | https://app.any.run/tasks/b44152f7-aa3a-4304-a3a7-74cd3d0c1323 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | March 10, 2025, 04:13:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 479ADD3BE7E9737A382FD3A4896B4C5A |
| SHA1: | E96C9F34A09C29DC37BC1FA9E56E90CD08DCEF40 |
| SHA256: | E7EF39B259C49829BA5C285E8DD1BBD7E8A04905C42ECCEEE2CCC2741DD5345E |
| SSDEEP: | 98304:X2kNNNWYPZ4aIIoHvIufNwI/G6E3nRFXYZ+7hAxa0Gc9LwlIm1IYZbvDO/hOQNLg:HGti3gIOZOv1OOz+83 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4208)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4208)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 6108)
- BackgroundTransferHost.exe (PID: 668)
- BackgroundTransferHost.exe (PID: 2564)
- BackgroundTransferHost.exe (PID: 7644)
- BackgroundTransferHost.exe (PID: 2152)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 668)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 668)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 668)
Manual execution by a user
- firefox.exe (PID: 5544)
Application launched itself
- firefox.exe (PID: 5544)
- firefox.exe (PID: 5048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:05 04:05:30 |
| ZipCRC: | 0xb860ace8 |
| ZipCompressedSize: | 14008254 |
| ZipUncompressedSize: | 14210307 |
| ZipFileName: | SWAT.exe |
Total processes
151
Monitored processes
21
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7896 -childID 8 -isForBrowser -prefsHandle 7288 -prefMapHandle 6036 -prefsLen 32011 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {58eb8fb1-8218-4ebe-8324-dc314b4384c5} 5048 "\\.\pipe\gecko-crash-server-pipe.5048" 23d4c379a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2084 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\SWAT-Raider.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5048 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5380 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1912 -parentBuildID 20240213221259 -prefsHandle 1816 -prefMapHandle 1776 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {0aef220b-d396-4419-b34b-17ee10d40dbb} 5048 "\\.\pipe\gecko-crash-server-pipe.5048" 23d47aeee10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5544 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
21 610
Read events
21 538
Write events
71
Delete events
1
Modification events
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\SWAT-Raider.zip | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4208) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6108) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6108) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
1
Suspicious files
164
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 668 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f8912ff7-fa13-4bbb-9b63-a674e7a57e49.down_data | — | |
MD5:— | SHA256:— | |||
| 5048 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 668 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\38773b63-3214-478a-a004-d7eab3abcc37.1c5b9693-d741-4105-9448-a86e3f302a86.down_meta | binary | |
MD5:901C5713A94541EF45665ADCBD80040C | SHA256:58A1706CD99F624ED9275F636FD6AE0E4AF8E0A2B051ACDCCB72CE5F0EE75A96 | |||
| 4208 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4208.33770\ReadMe.txt | text | |
MD5:8048A776ECD1AC0ECBF63CBEF2D47D0E | SHA256:8072583CB9C35EFFAAA62E249972FD6F544680E6B3976D8ABD7B53AF9E4CF17F | |||
| 4208 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4208.33770\SWAT.exe | executable | |
MD5:96EE42A2E614609841880141FC3B1B3B | SHA256:8F91CB9E705BEBE84CEEFA2EA5D38D96AC2931D53E0B26B2FEC13277A6D8E9BC | |||
| 668 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\38773b63-3214-478a-a004-d7eab3abcc37.up_meta_secure | binary | |
MD5:F762D299BF777ACAB31F169DEF608B9B | SHA256:F5A257CB0751B9B80B46135F464BD36053EAEB95804E0C745BFE99C2E4CD39D6 | |||
| 668 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f8912ff7-fa13-4bbb-9b63-a674e7a57e49.1c5b9693-d741-4105-9448-a86e3f302a86.down_meta | binary | |
MD5:901C5713A94541EF45665ADCBD80040C | SHA256:58A1706CD99F624ED9275F636FD6AE0E4AF8E0A2B051ACDCCB72CE5F0EE75A96 | |||
| 668 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:FE72DB6B00D357476C3431C87AD9BCED | SHA256:320AC519D5AD872BD8423B71DDF5A960A49174155857A59A68034F30F63122EA | |||
| 5048 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 668 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:AD65BBA990E9A146C8789184B44B3332 | SHA256:C57BBFD31CE81C873E766C5DEEE854B02BFF08020DF9BE1A3B4562BD67CC932D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
138
DNS requests
183
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5048 | firefox.exe | POST | — | 142.250.184.227:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
5048 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
920 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
668 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5048 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5048 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5048 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
5048 | firefox.exe | POST | 200 | 2.19.120.133:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5048 | firefox.exe | POST | 200 | 2.19.120.133:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
920 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
920 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
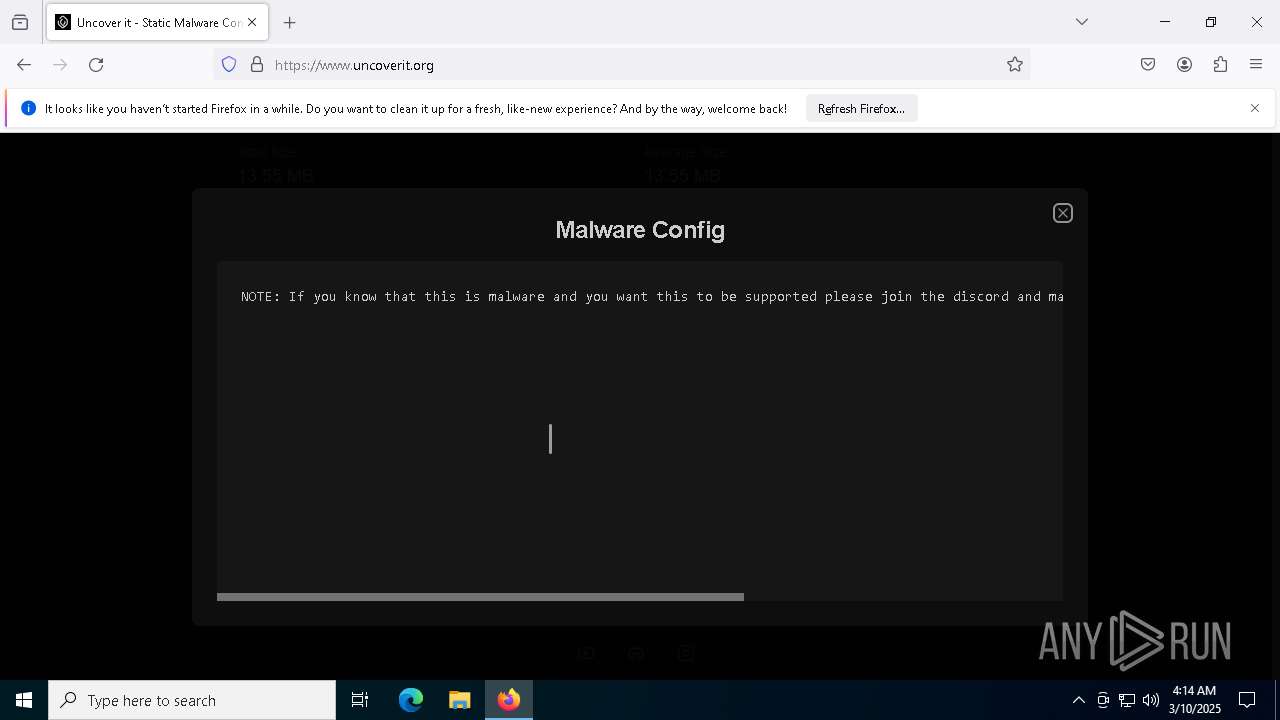
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |