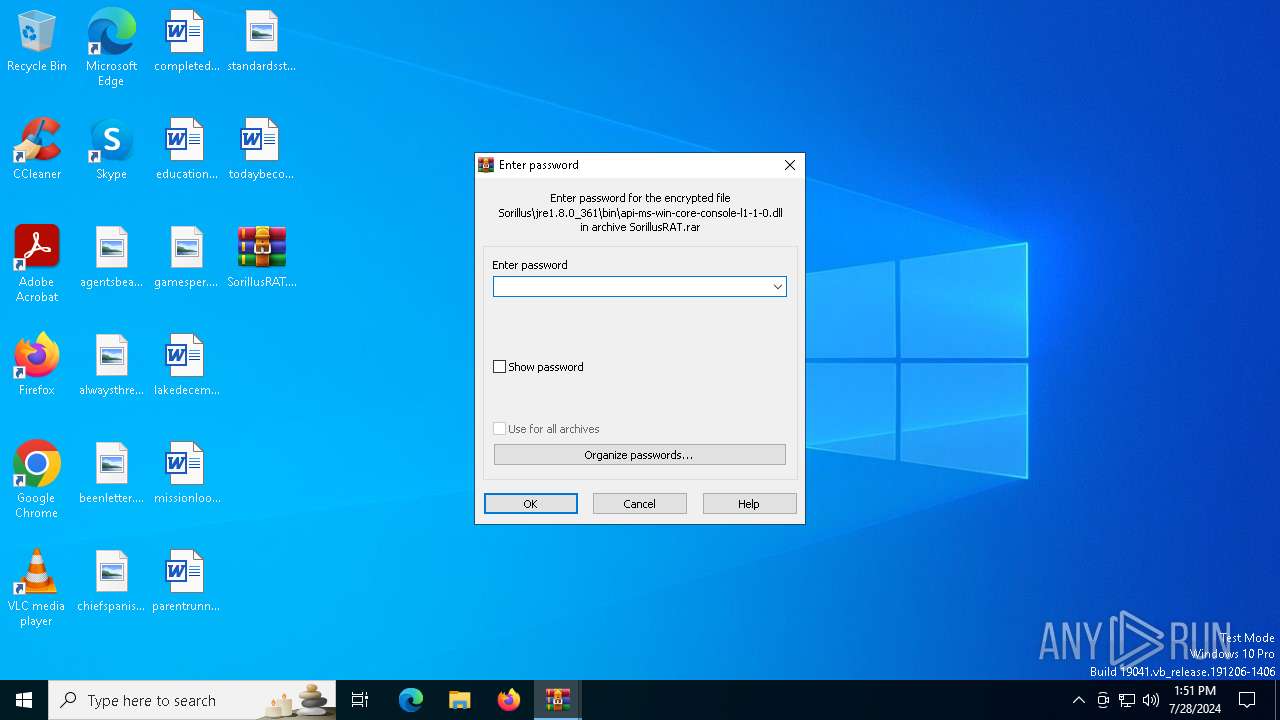
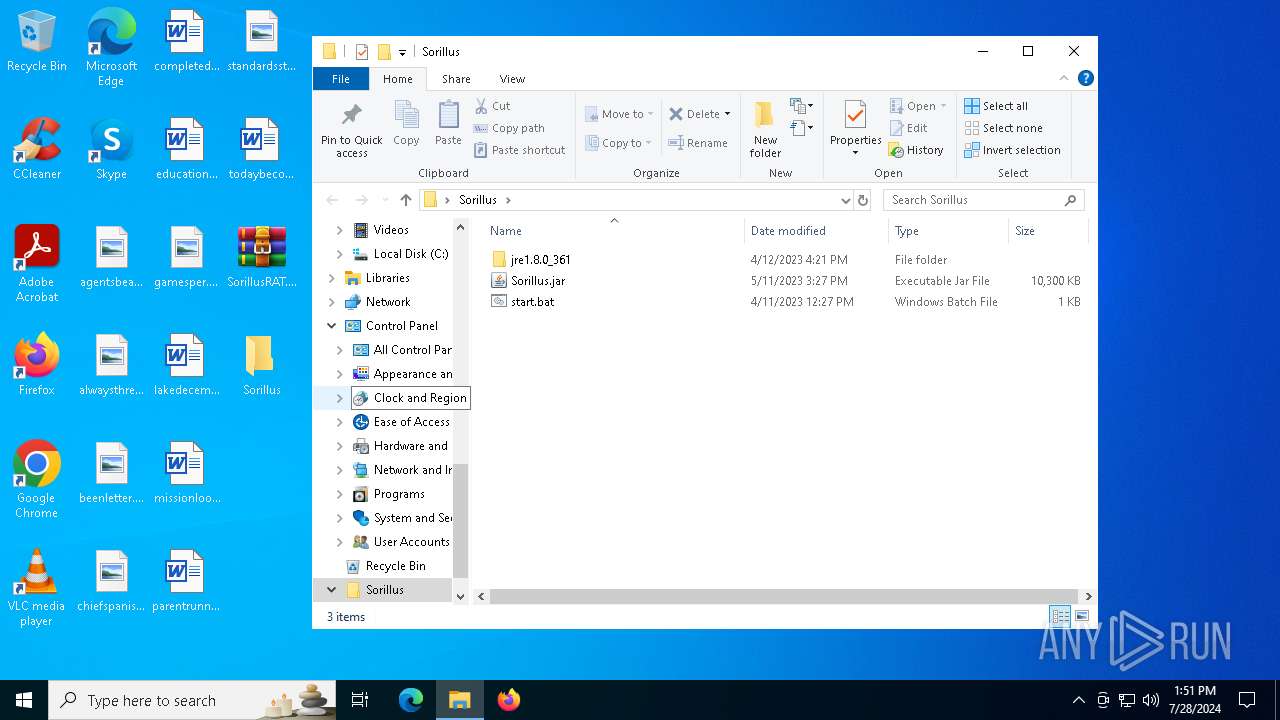
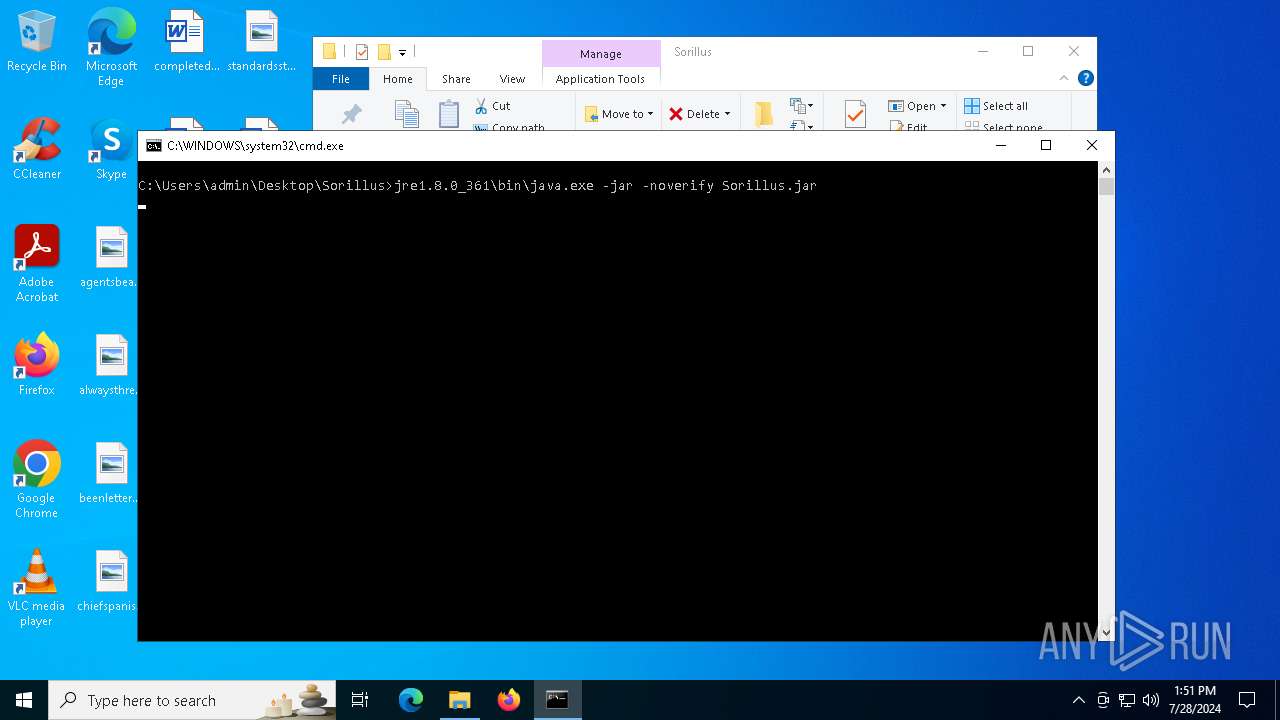
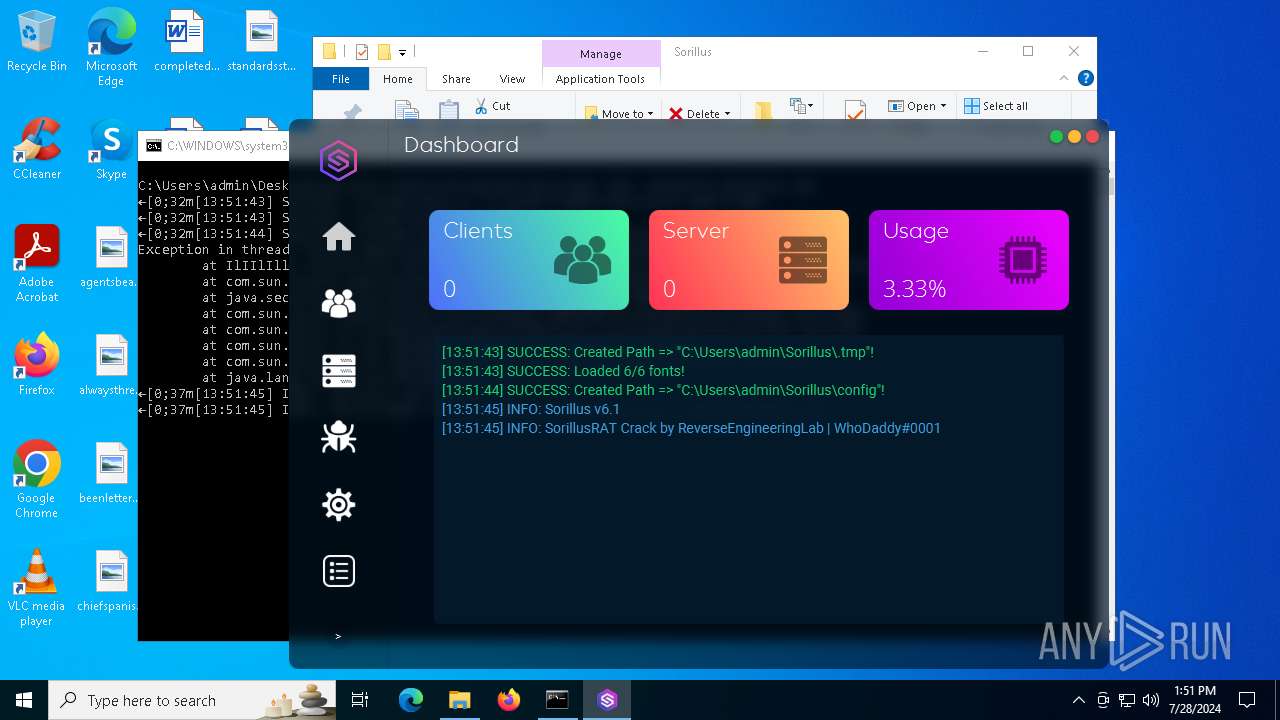
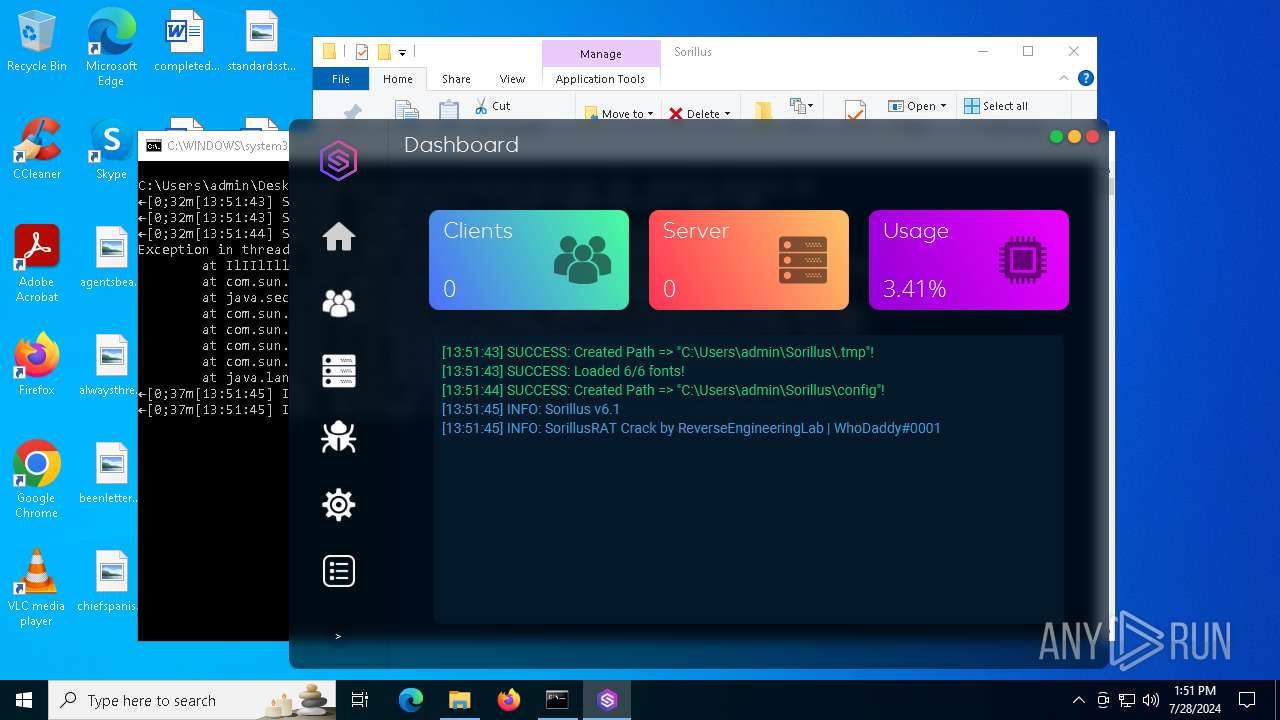
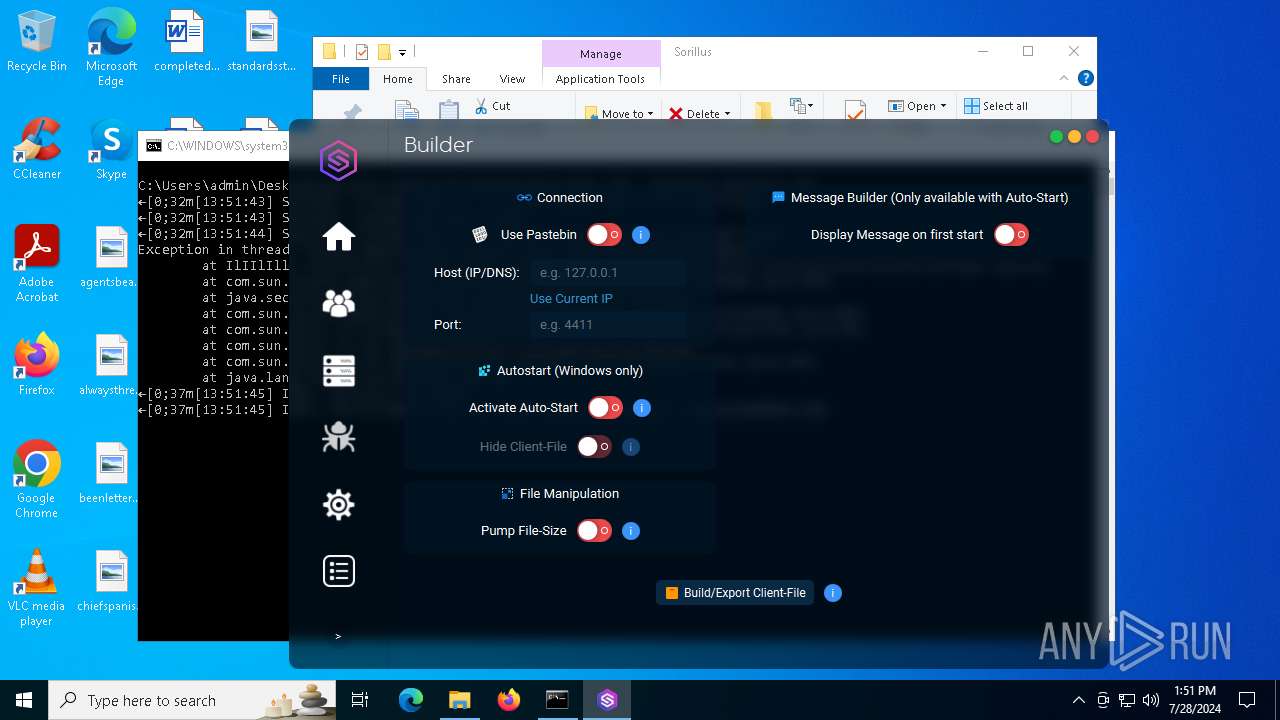
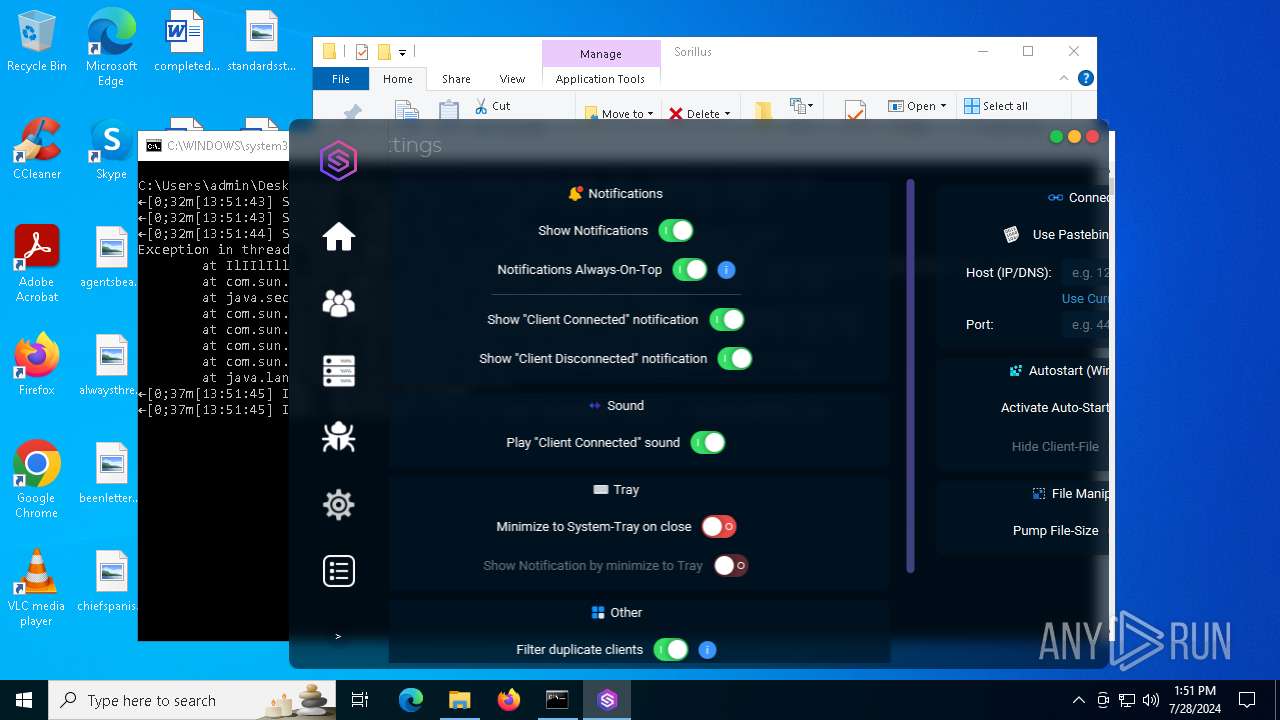
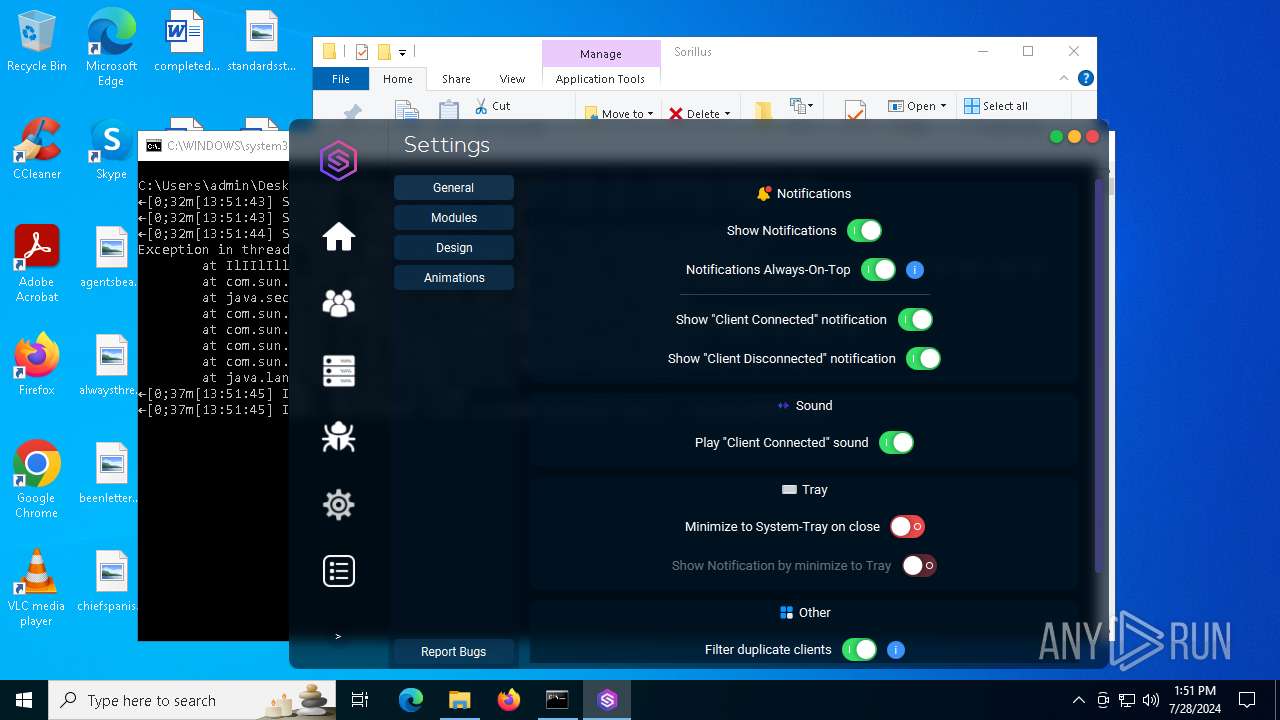
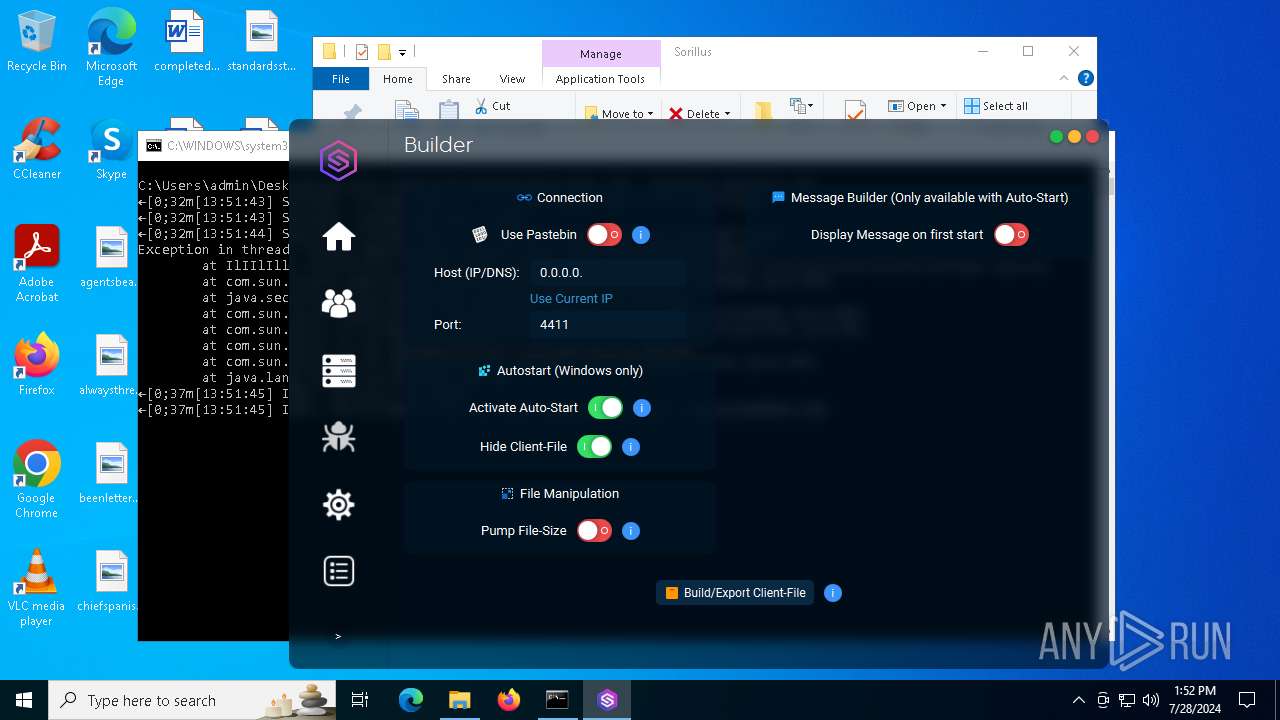
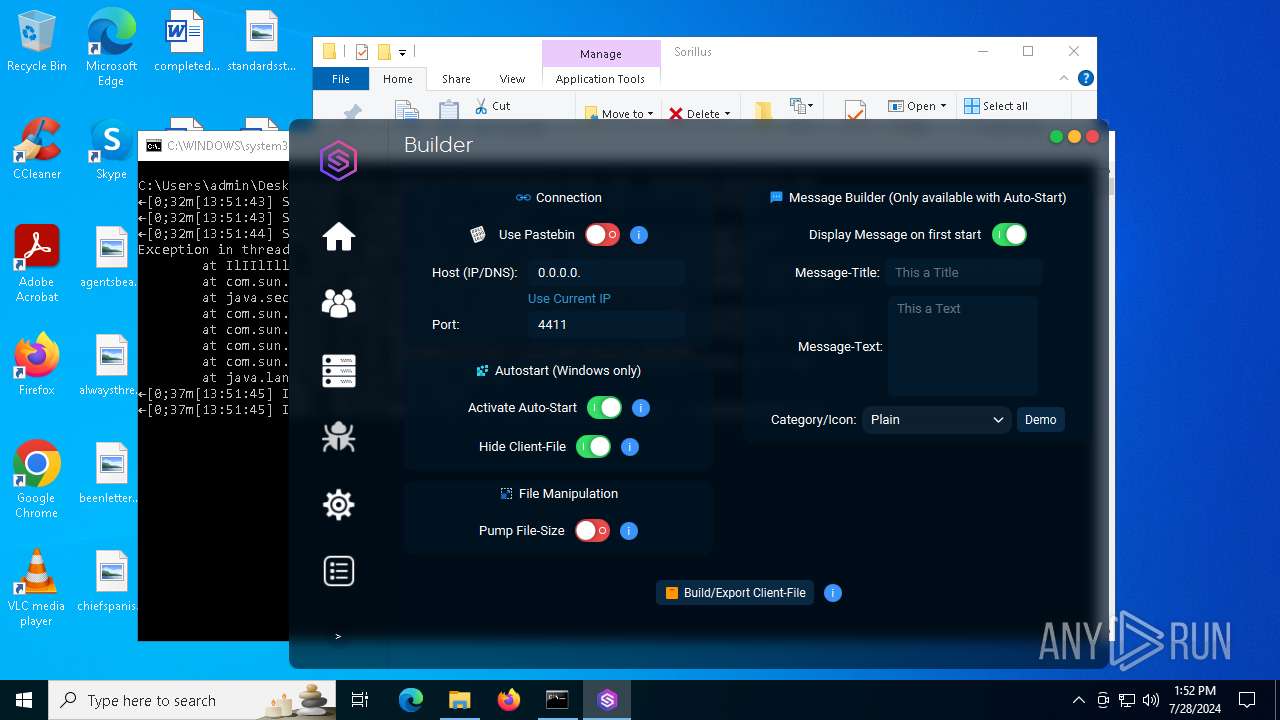
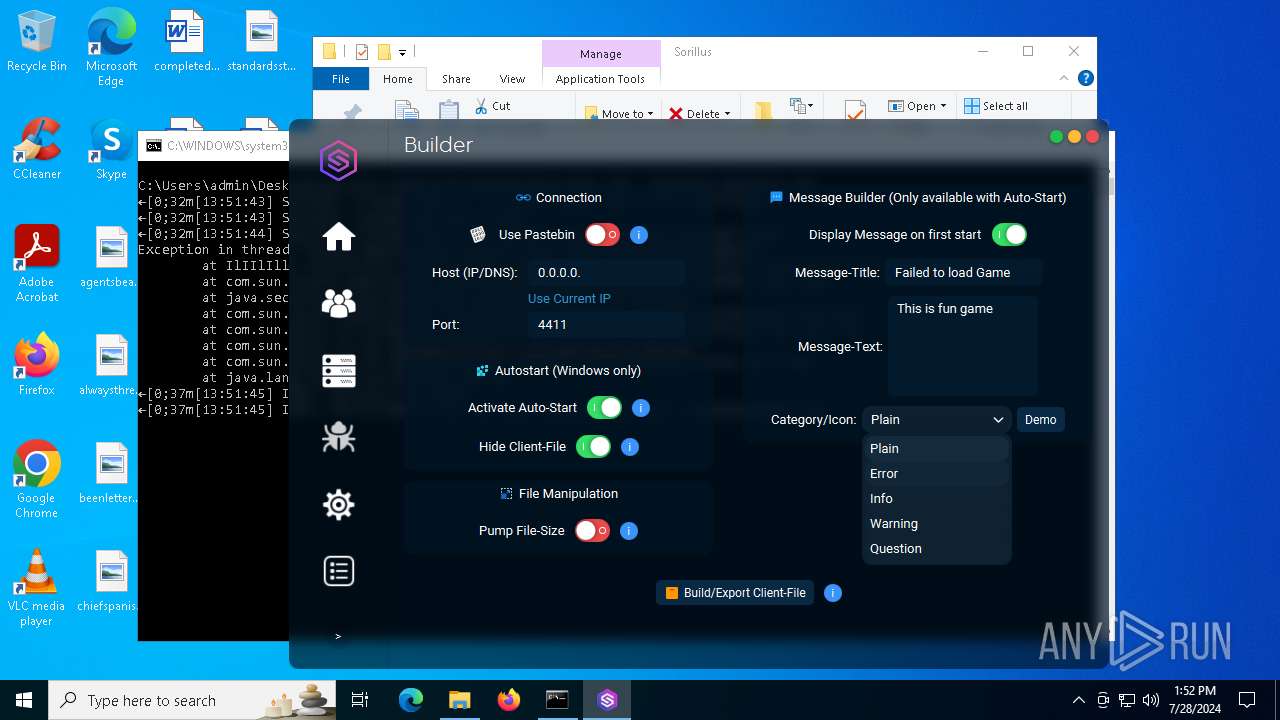
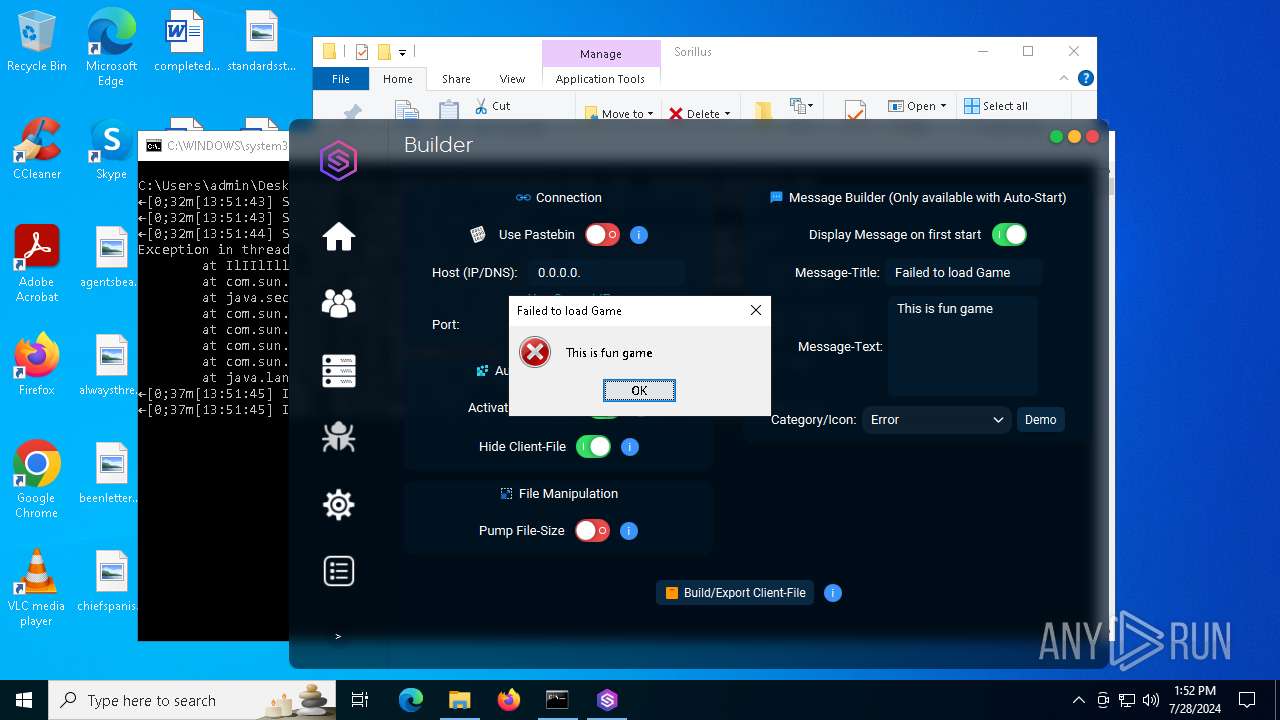
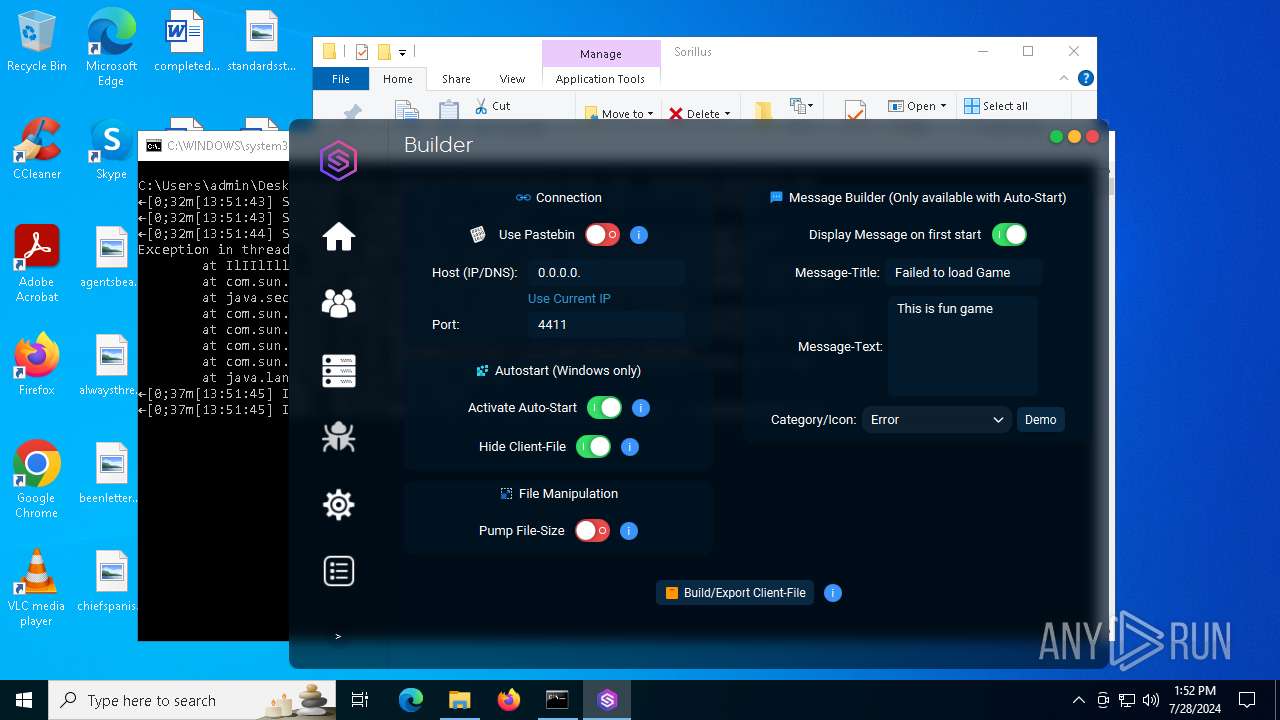
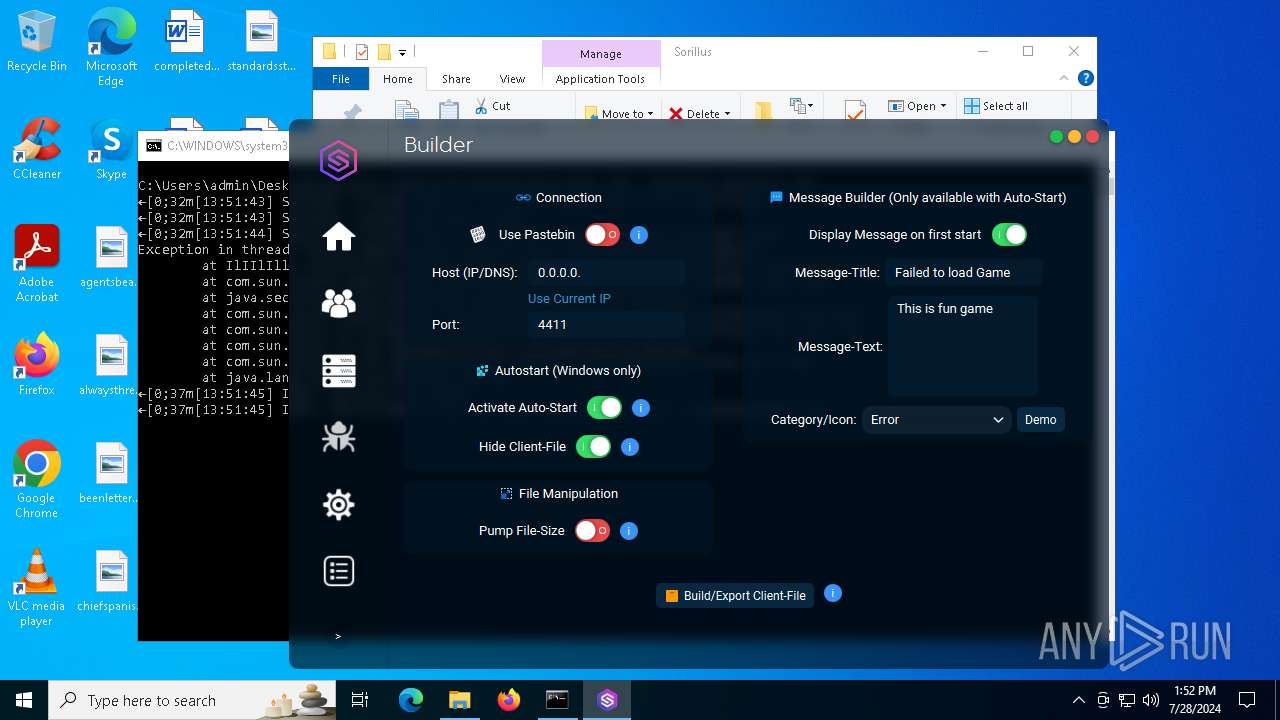
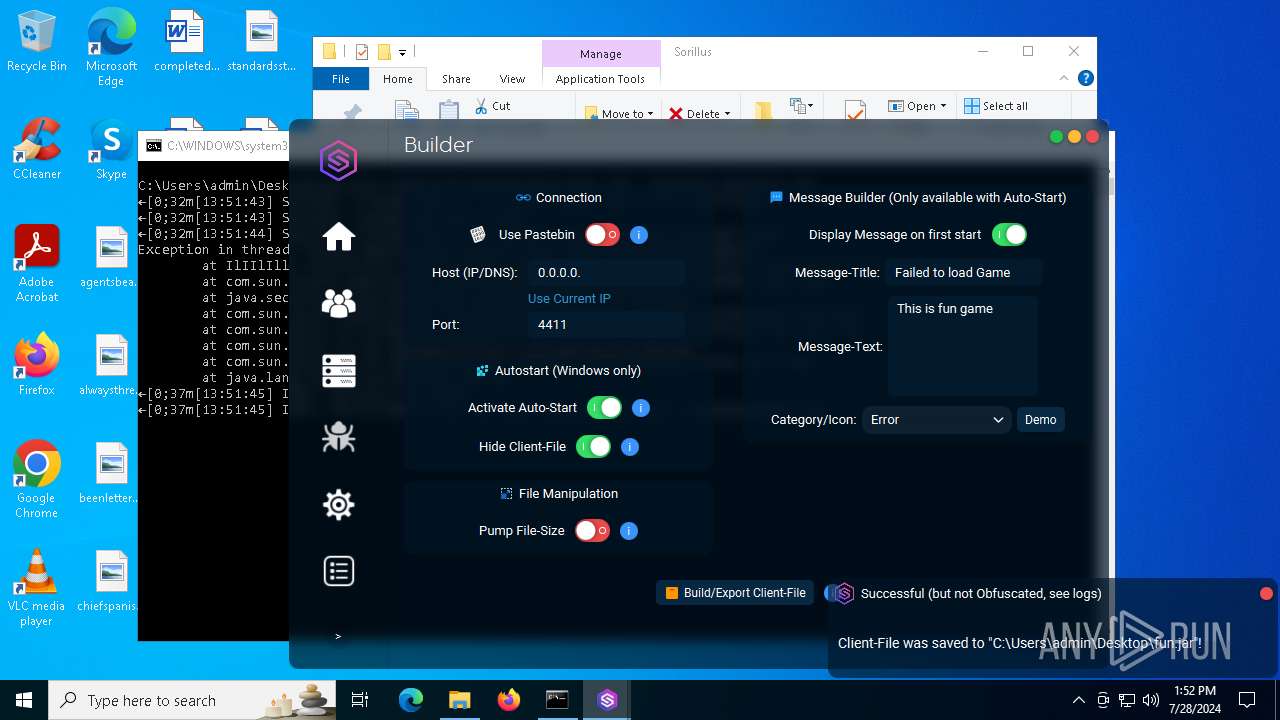
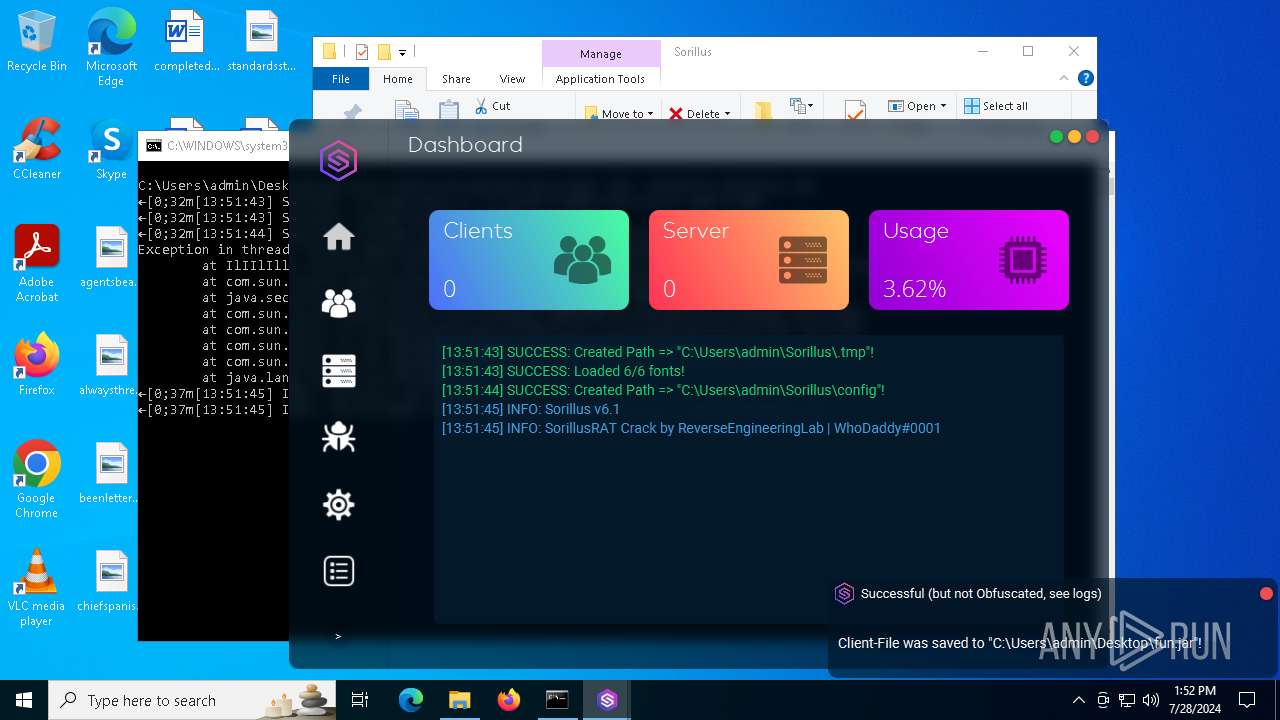
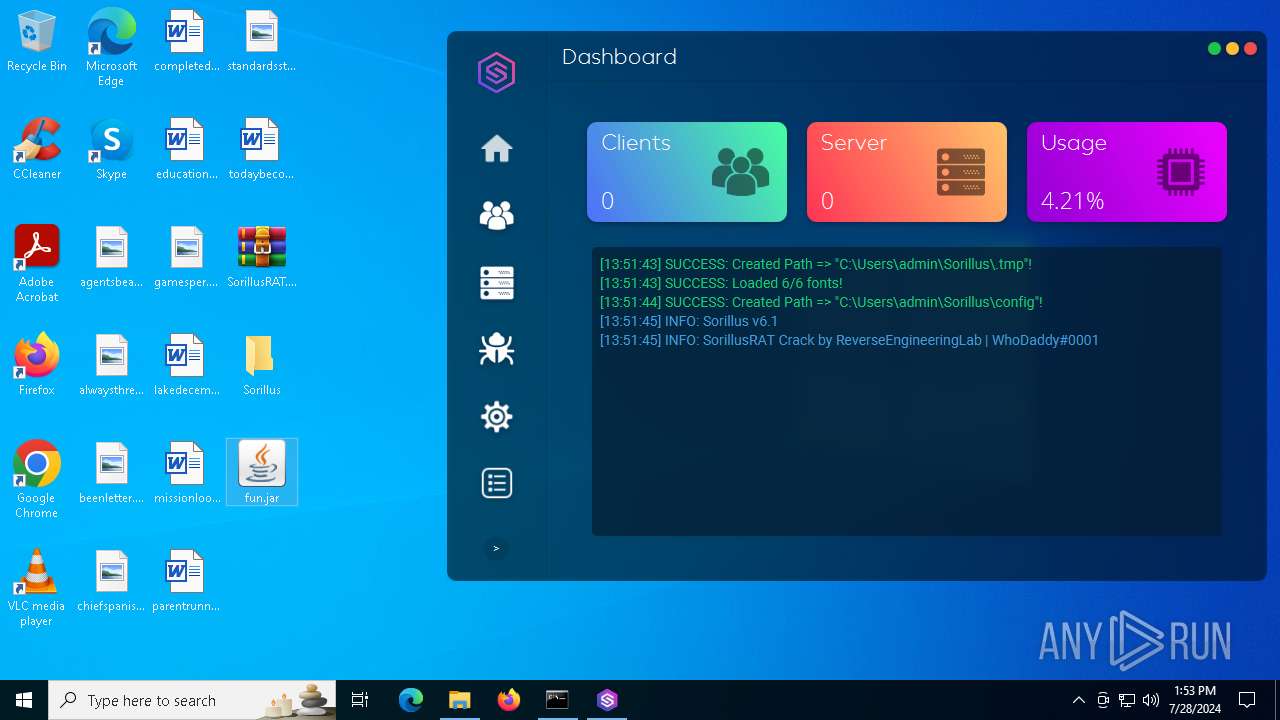
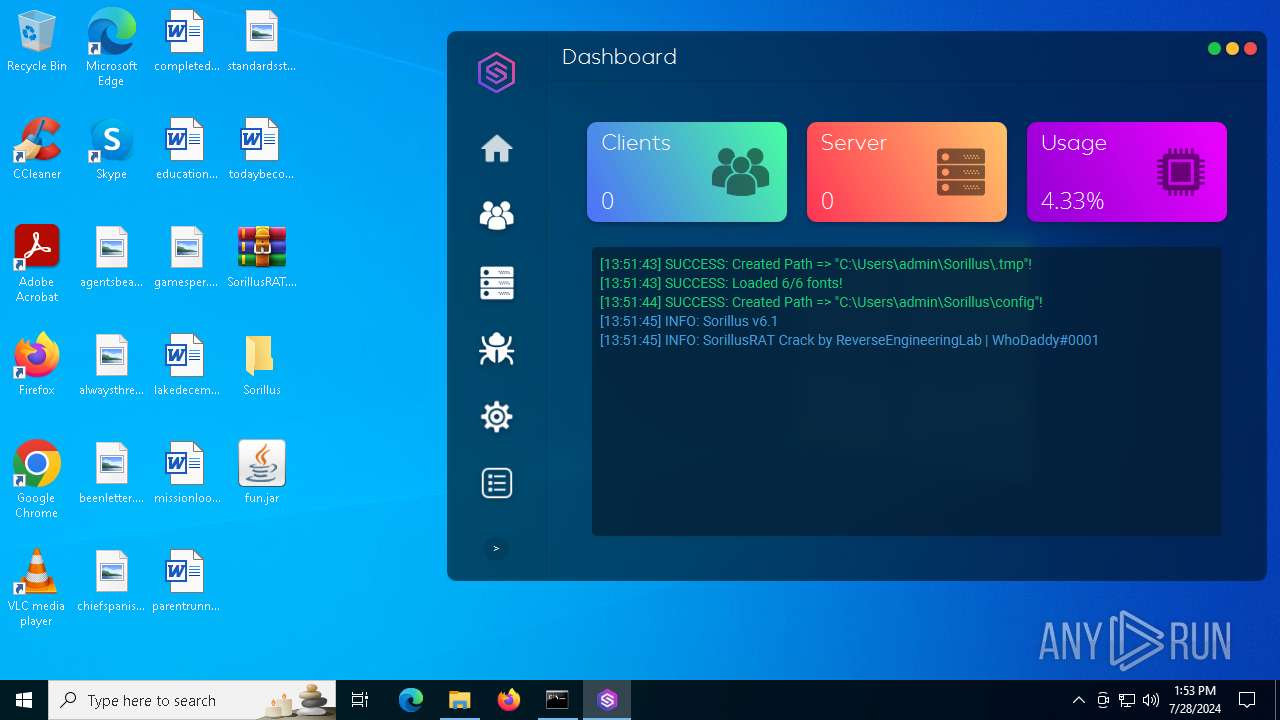
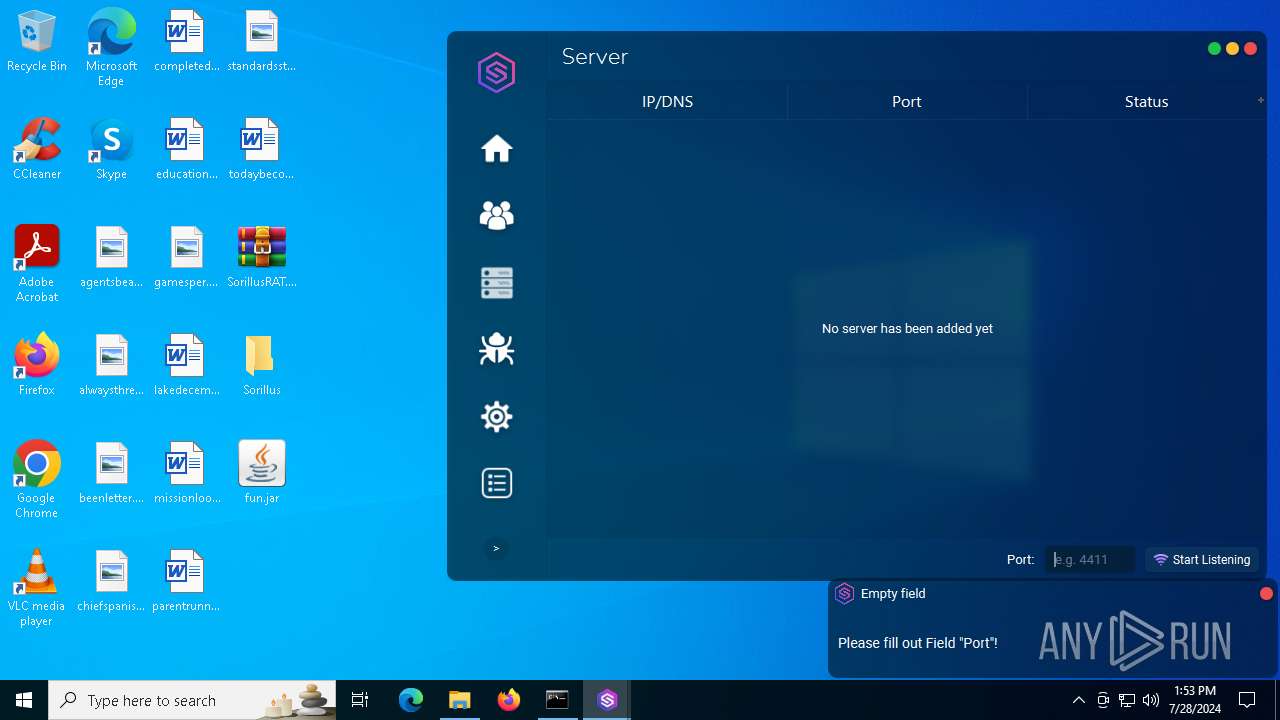
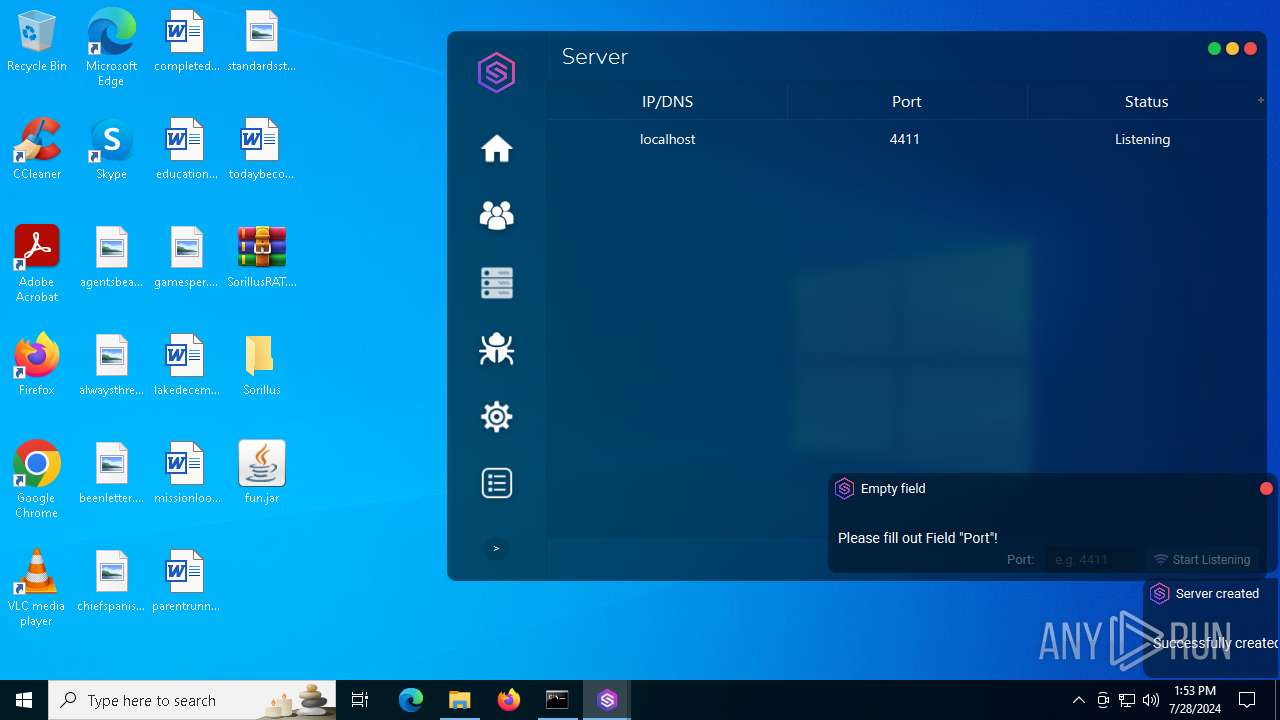
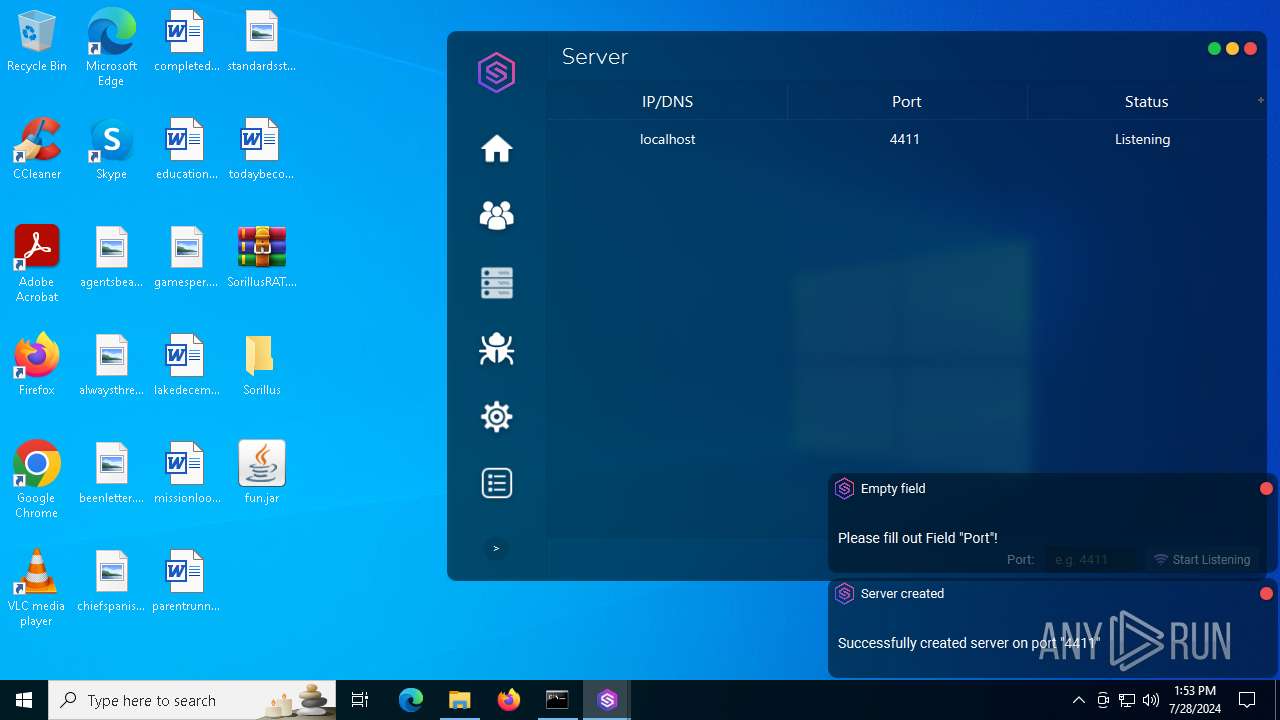
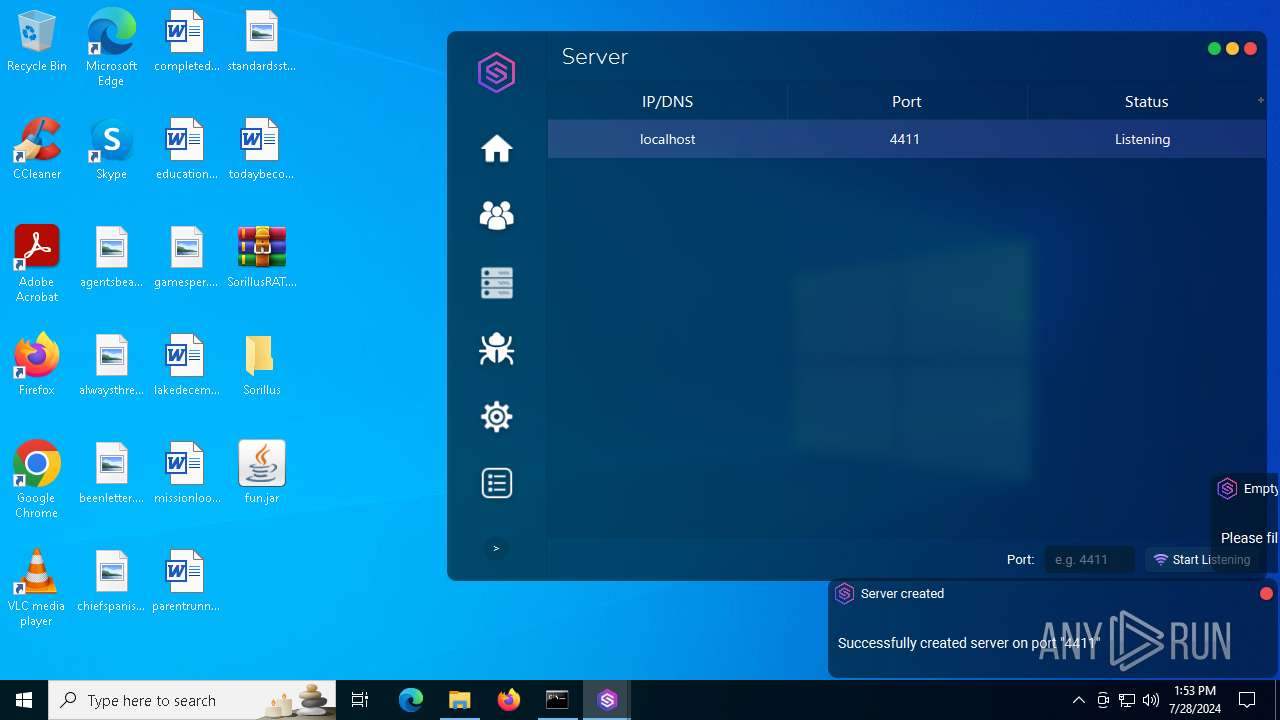
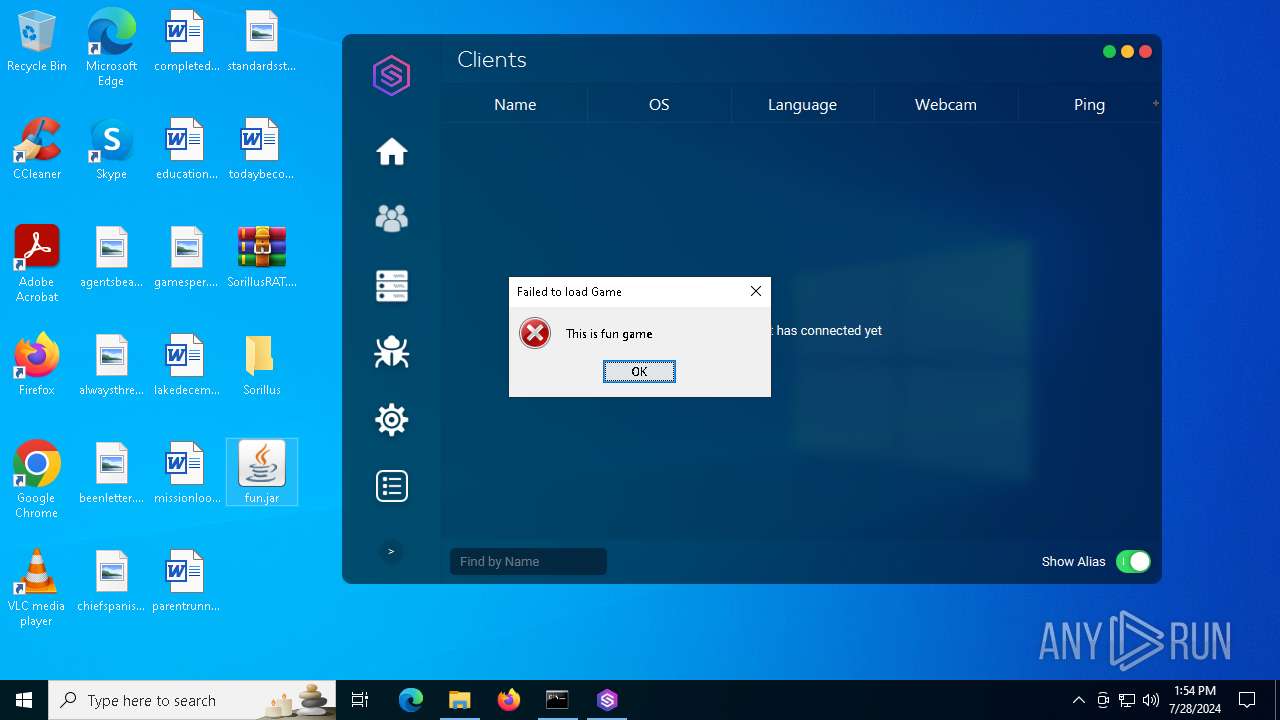
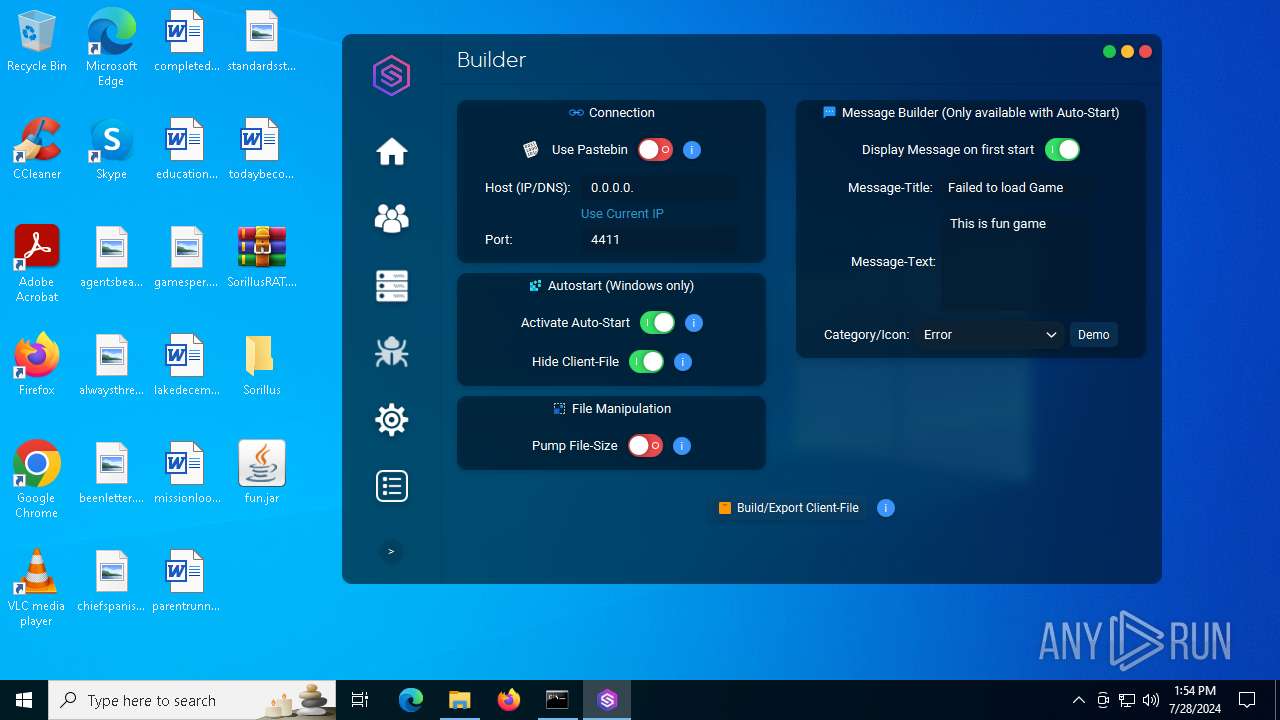
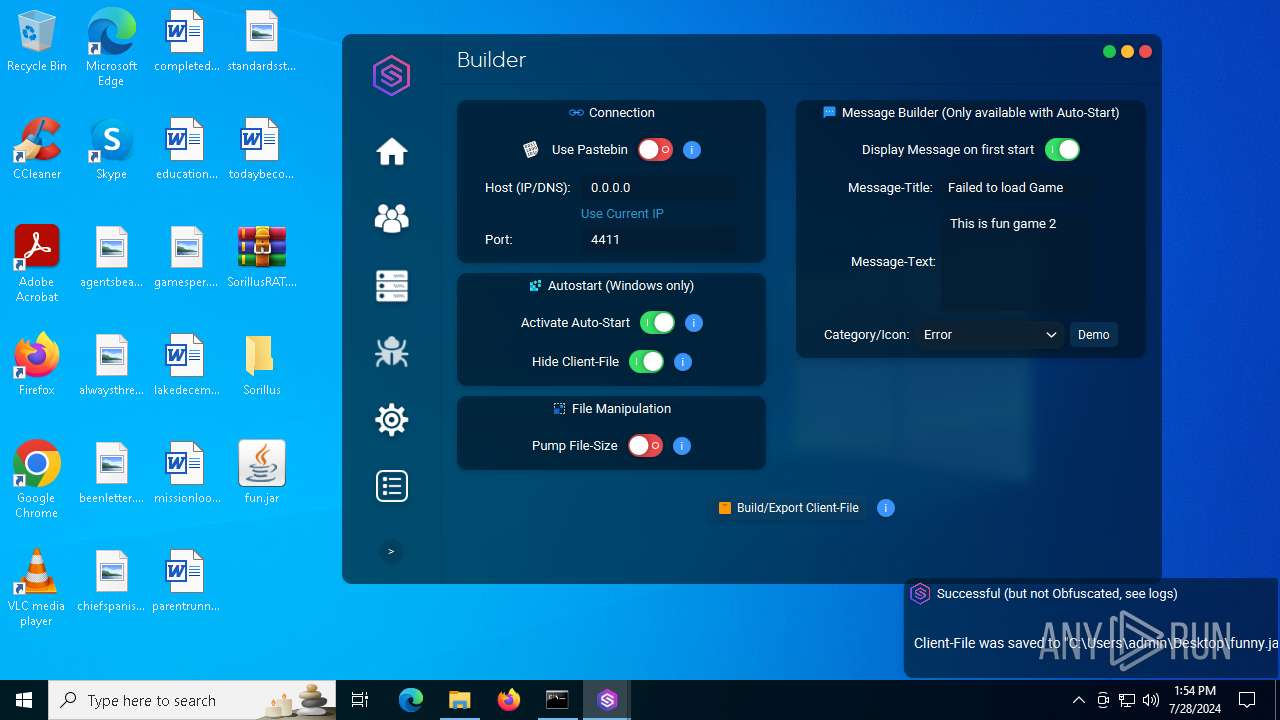
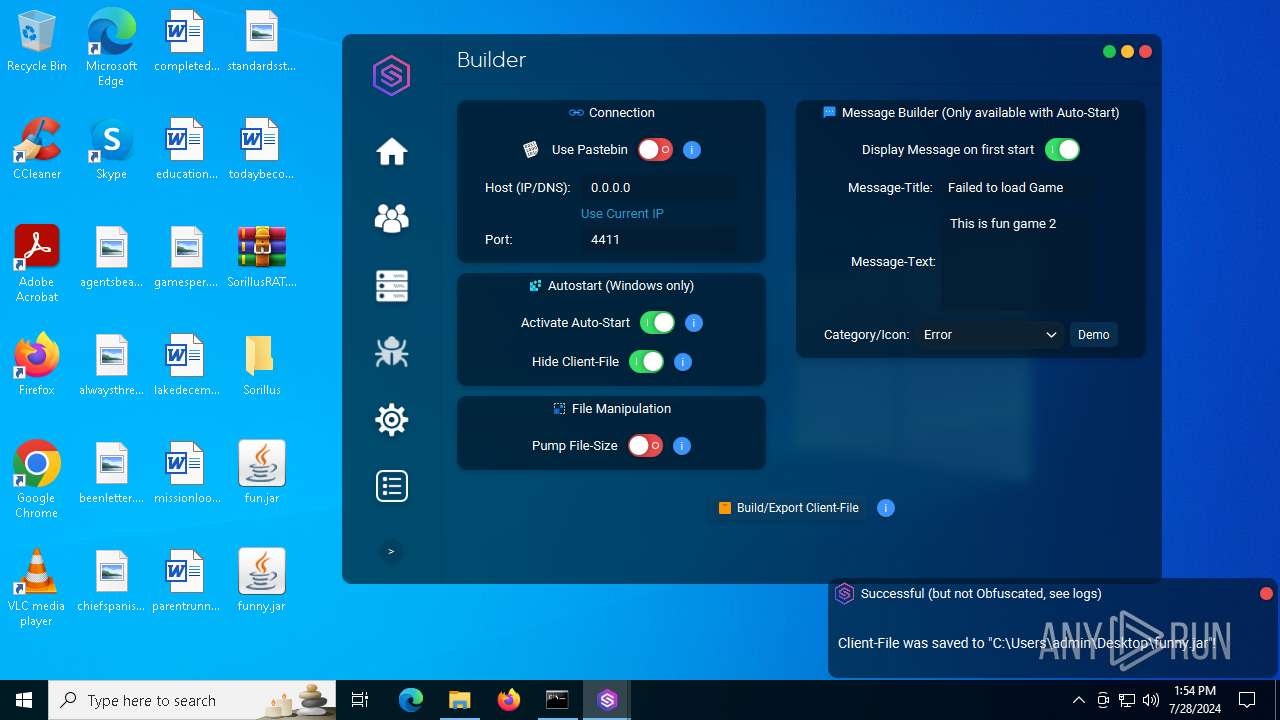
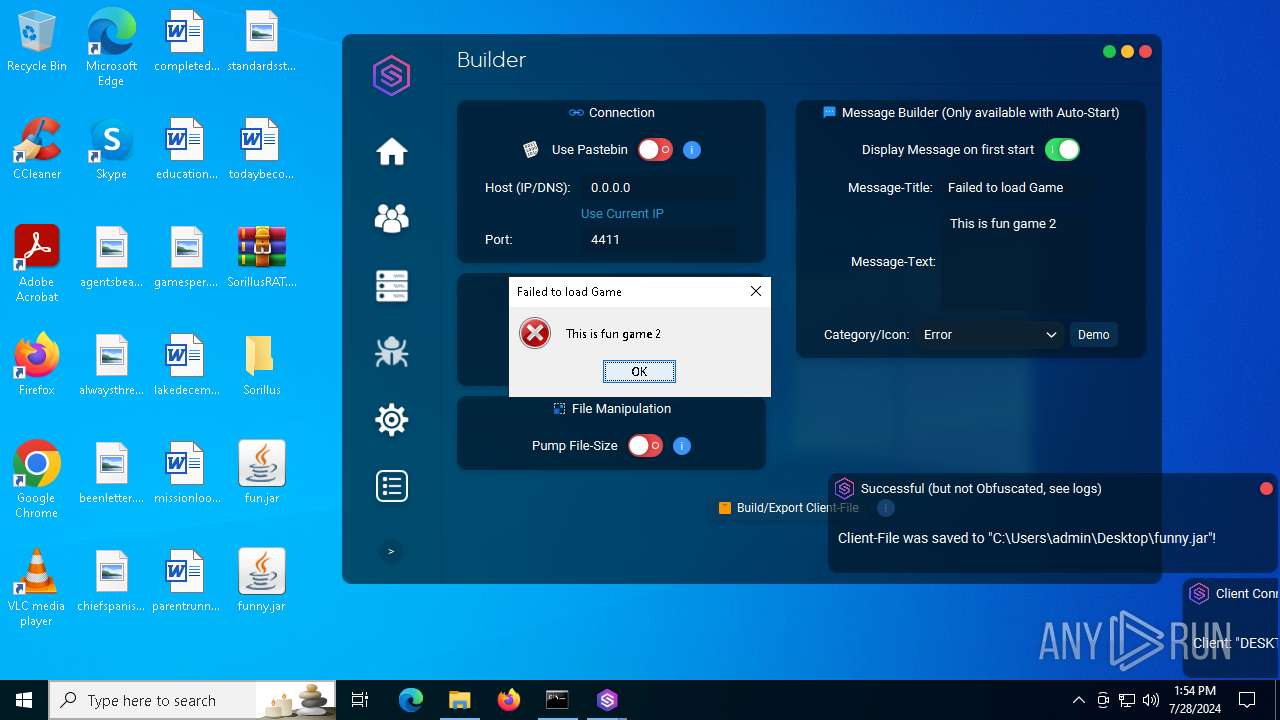
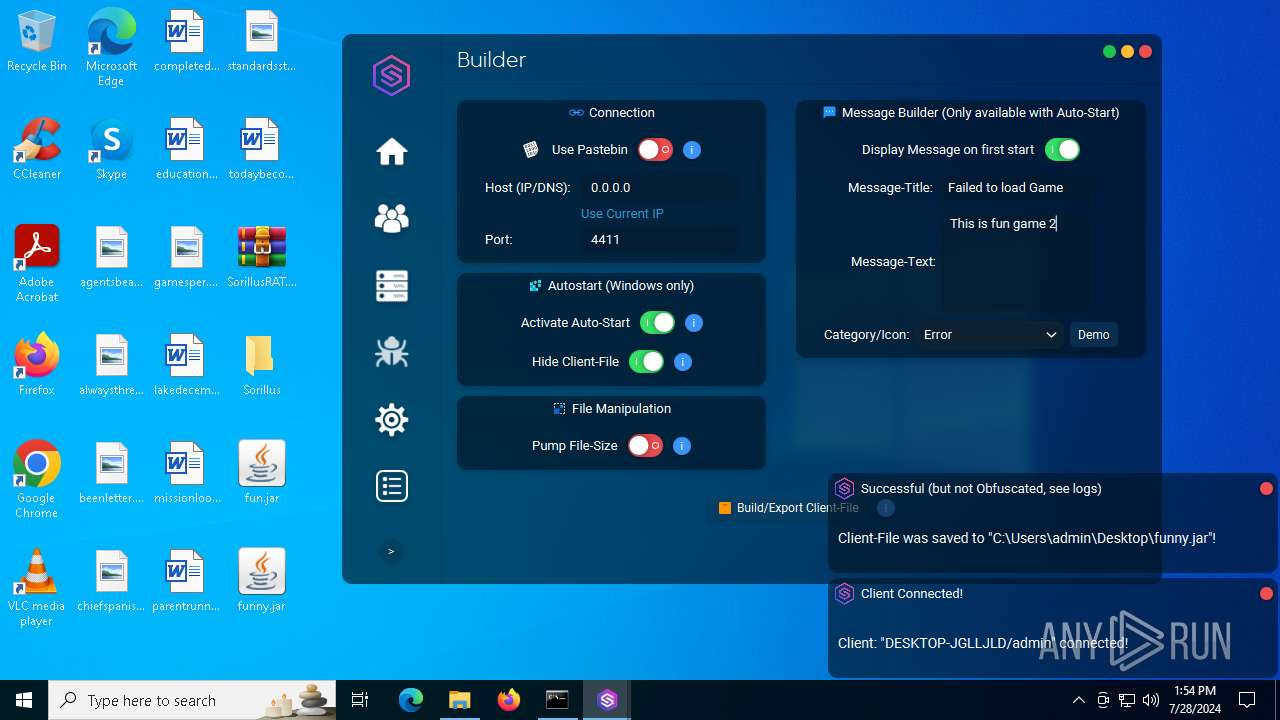
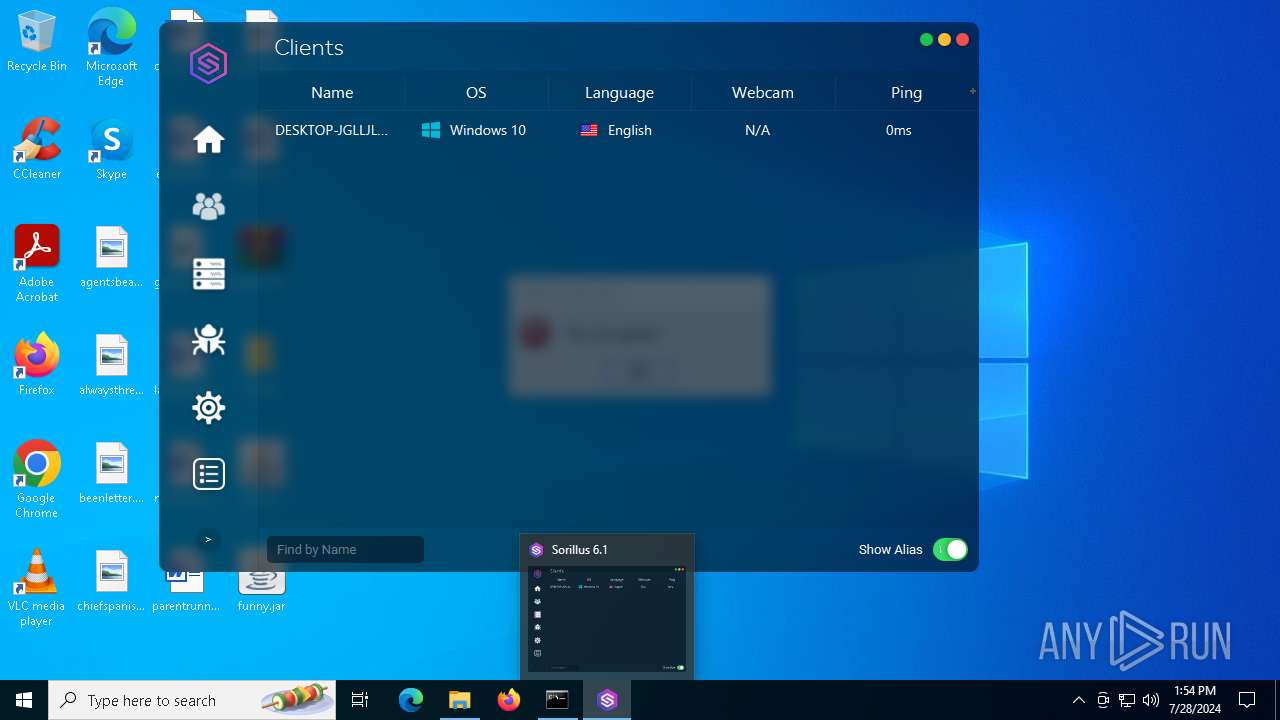
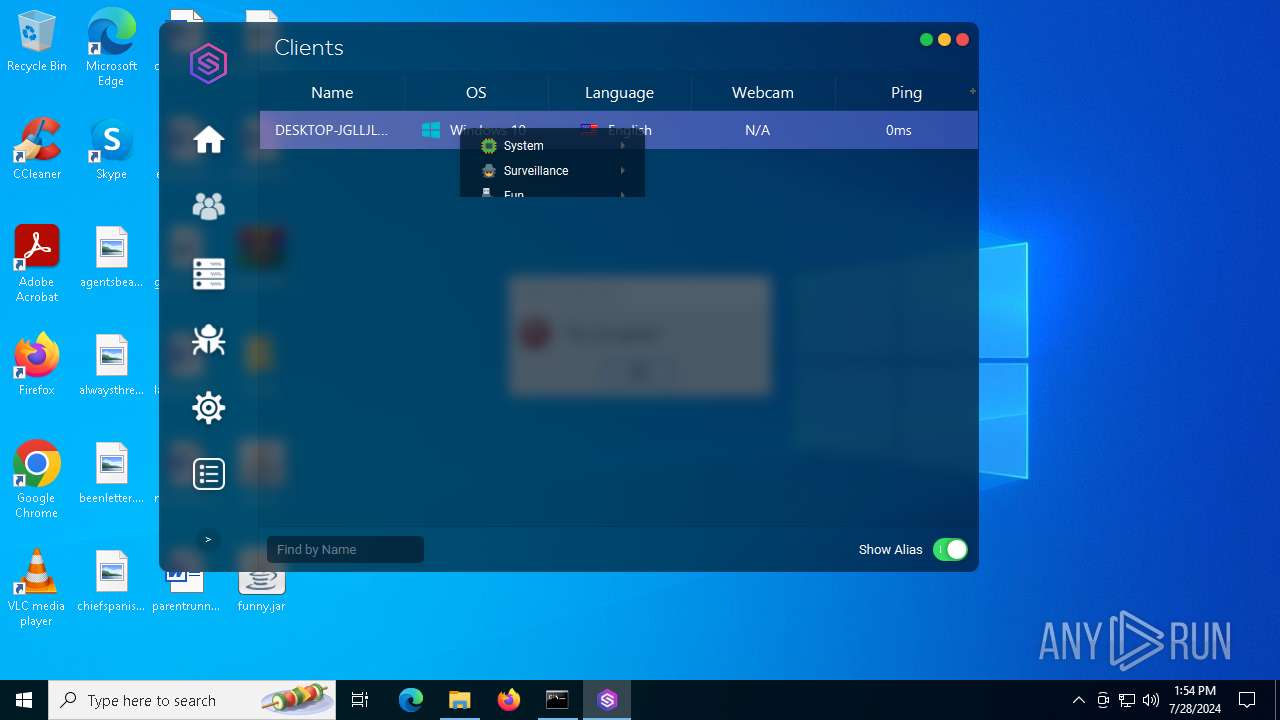
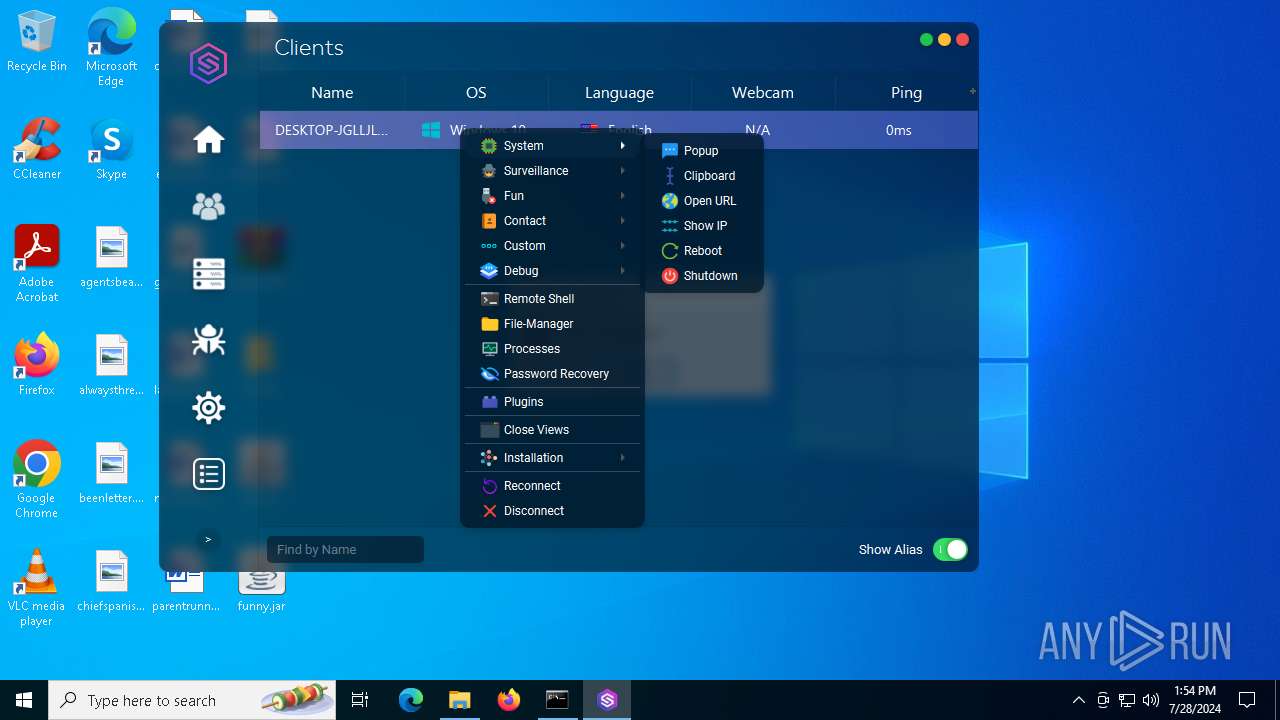
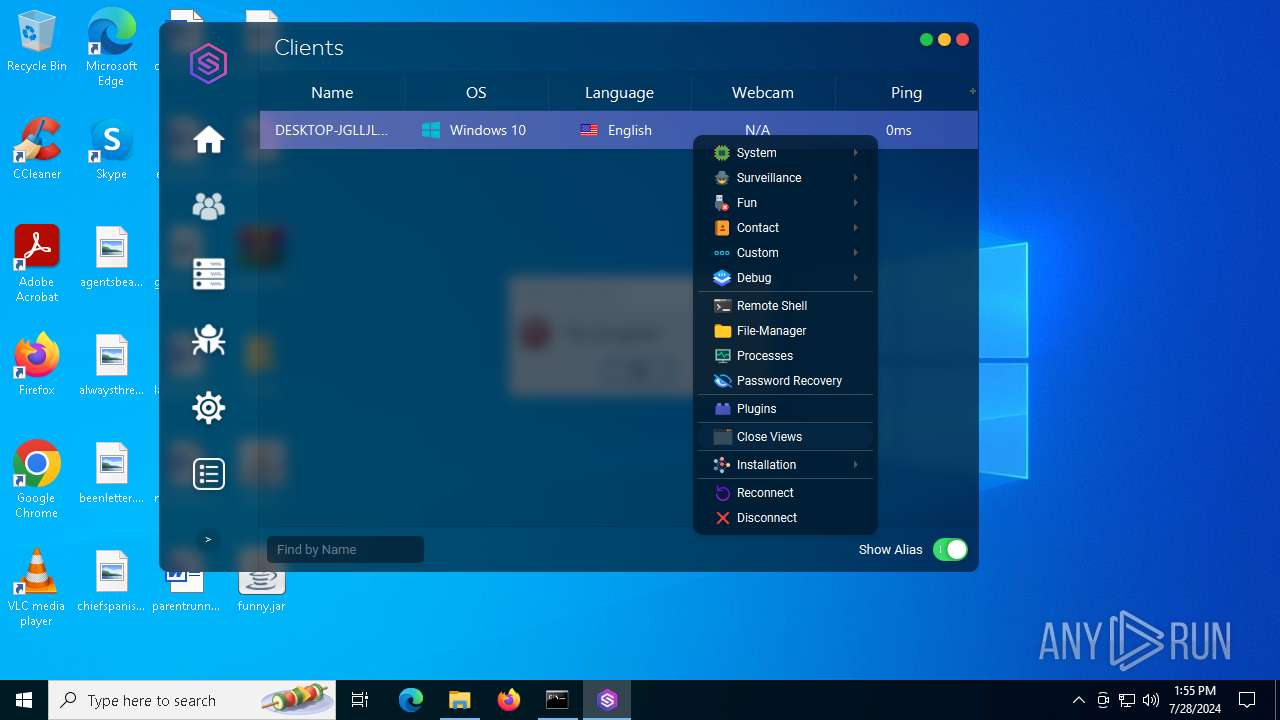
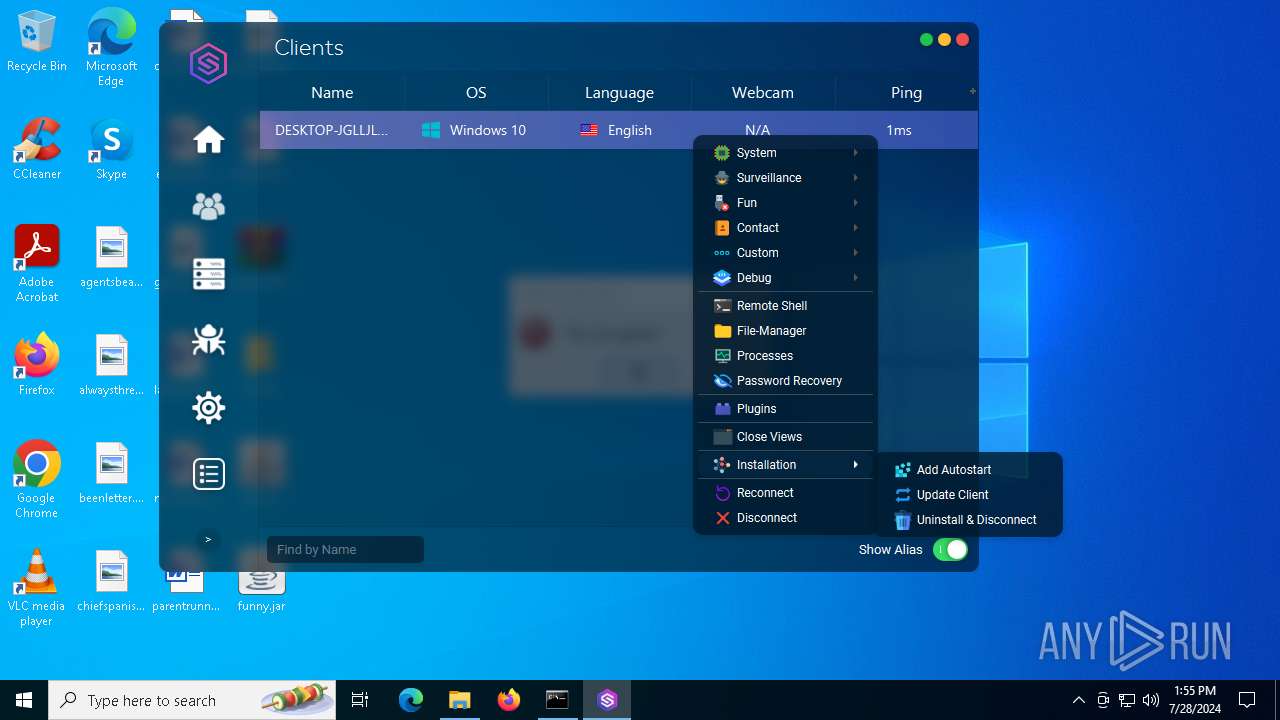
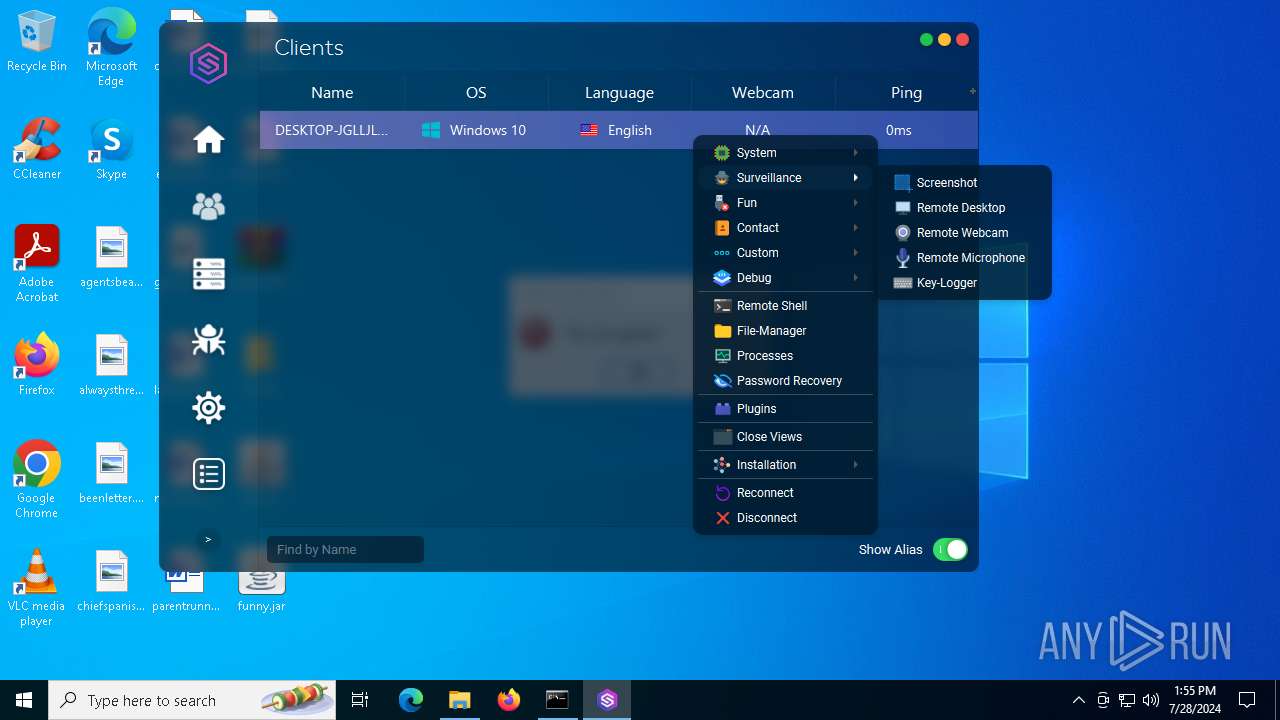
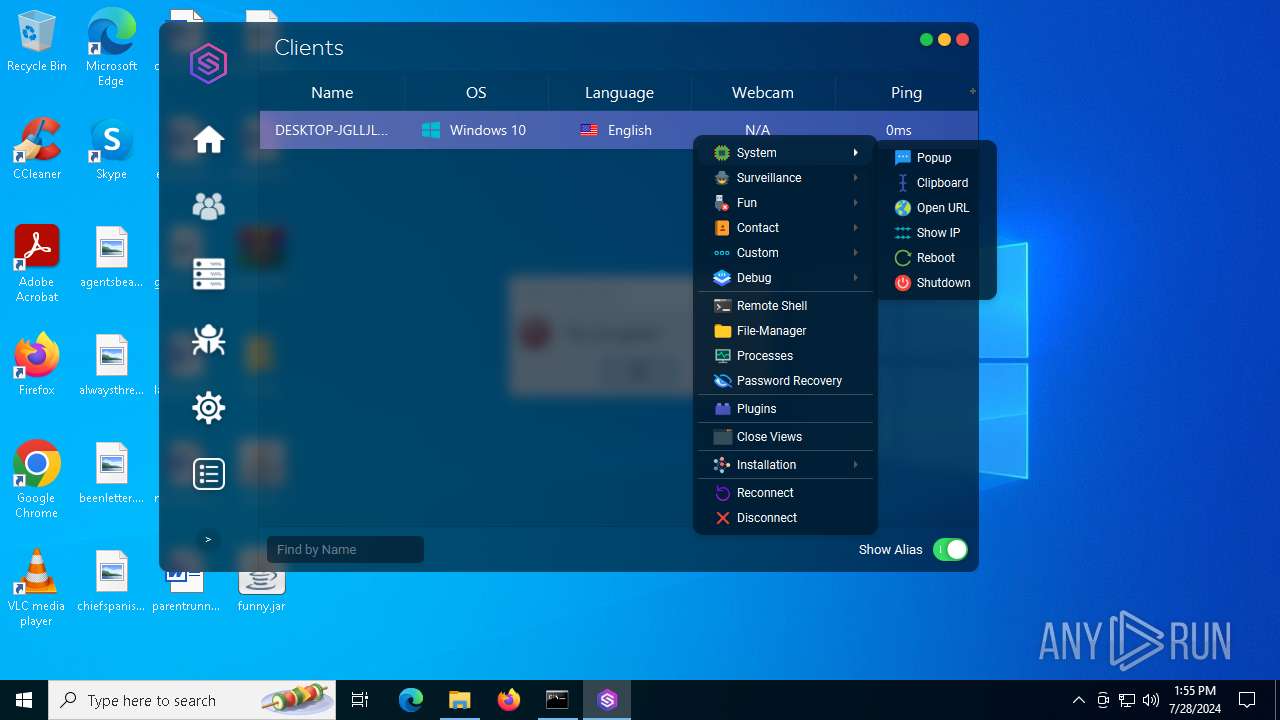
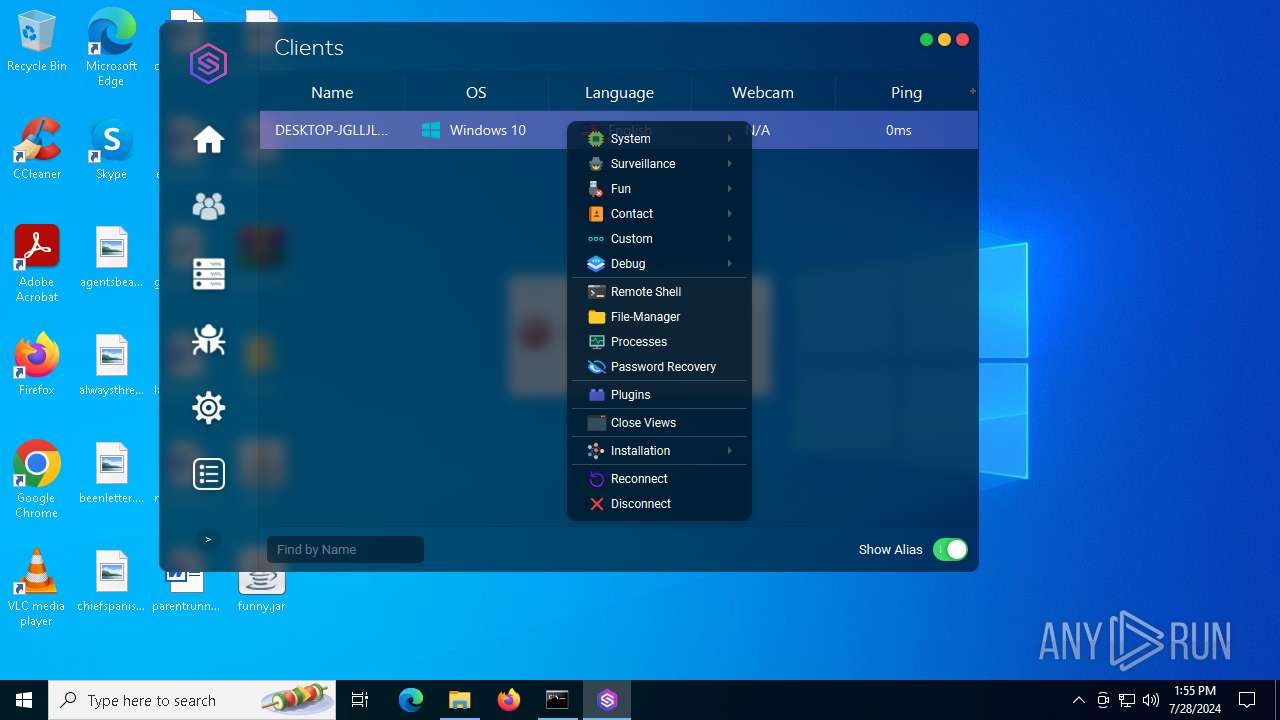
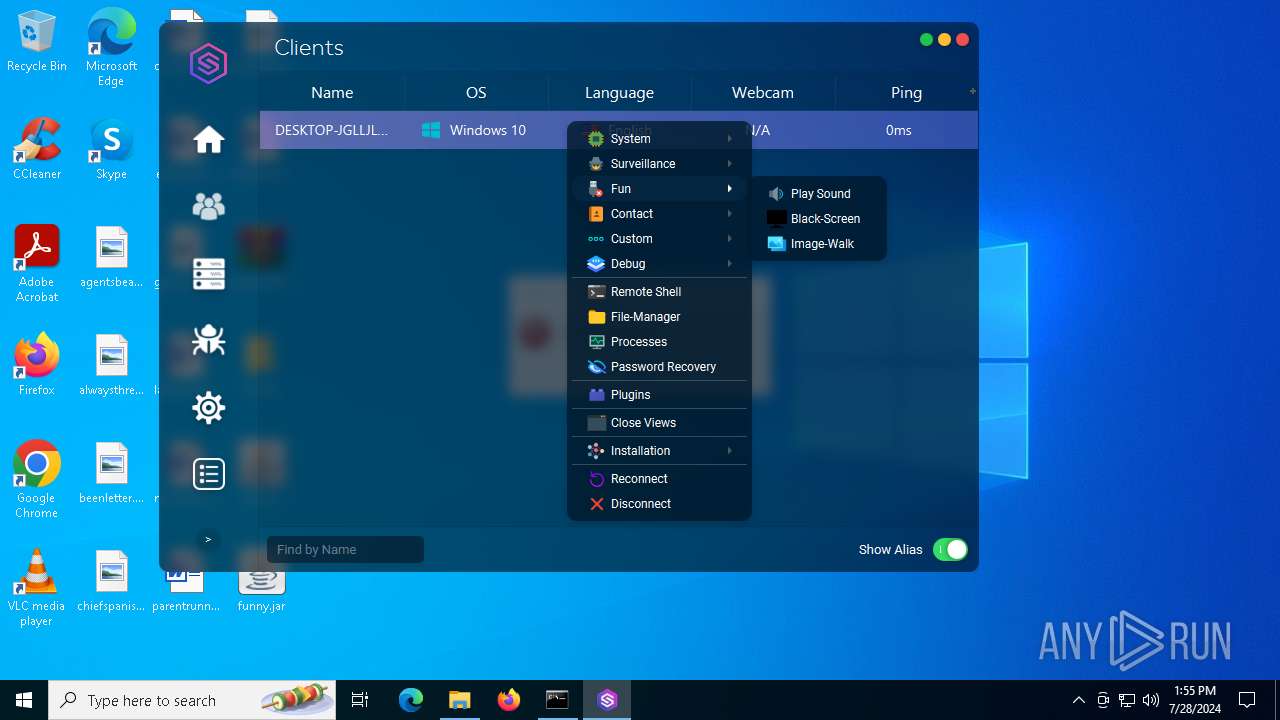
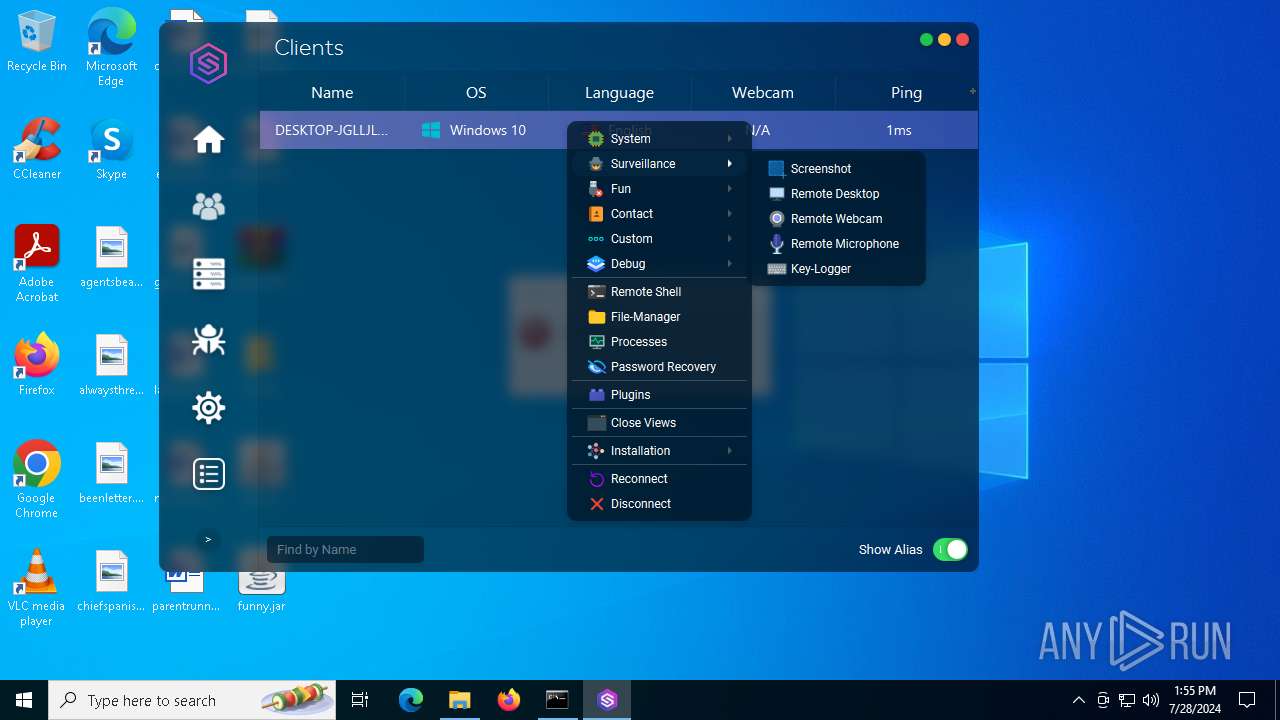
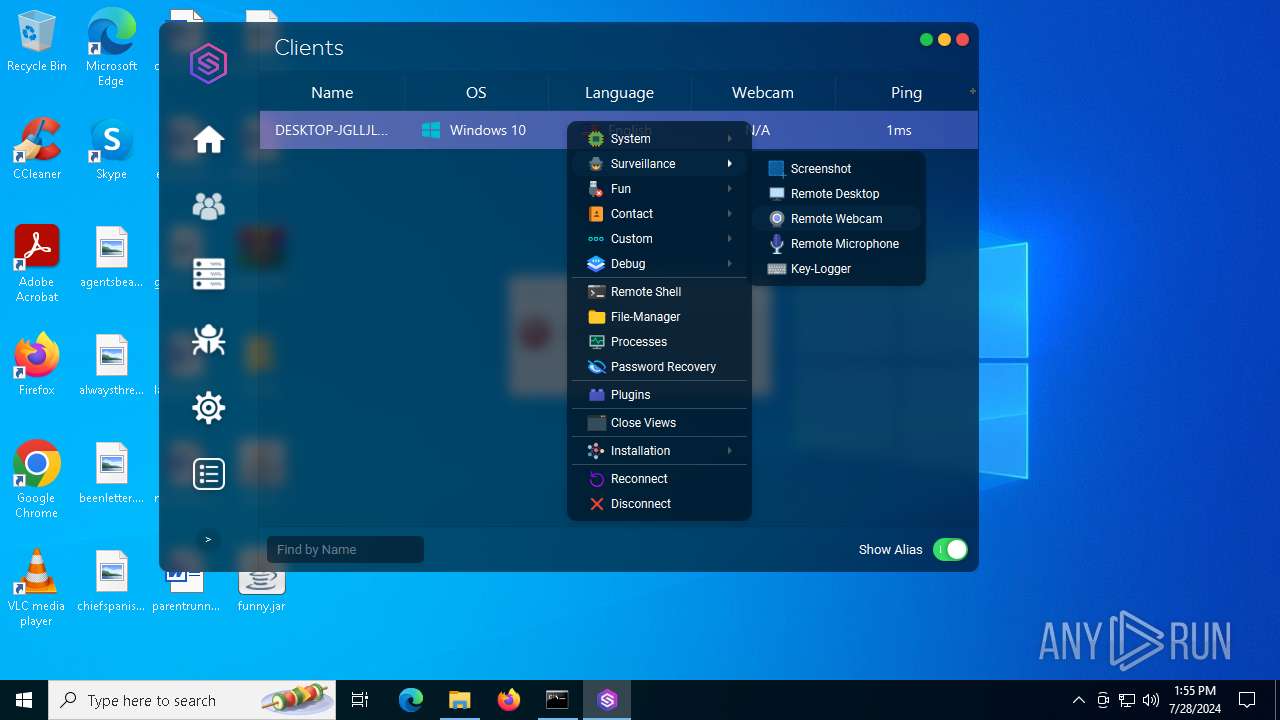
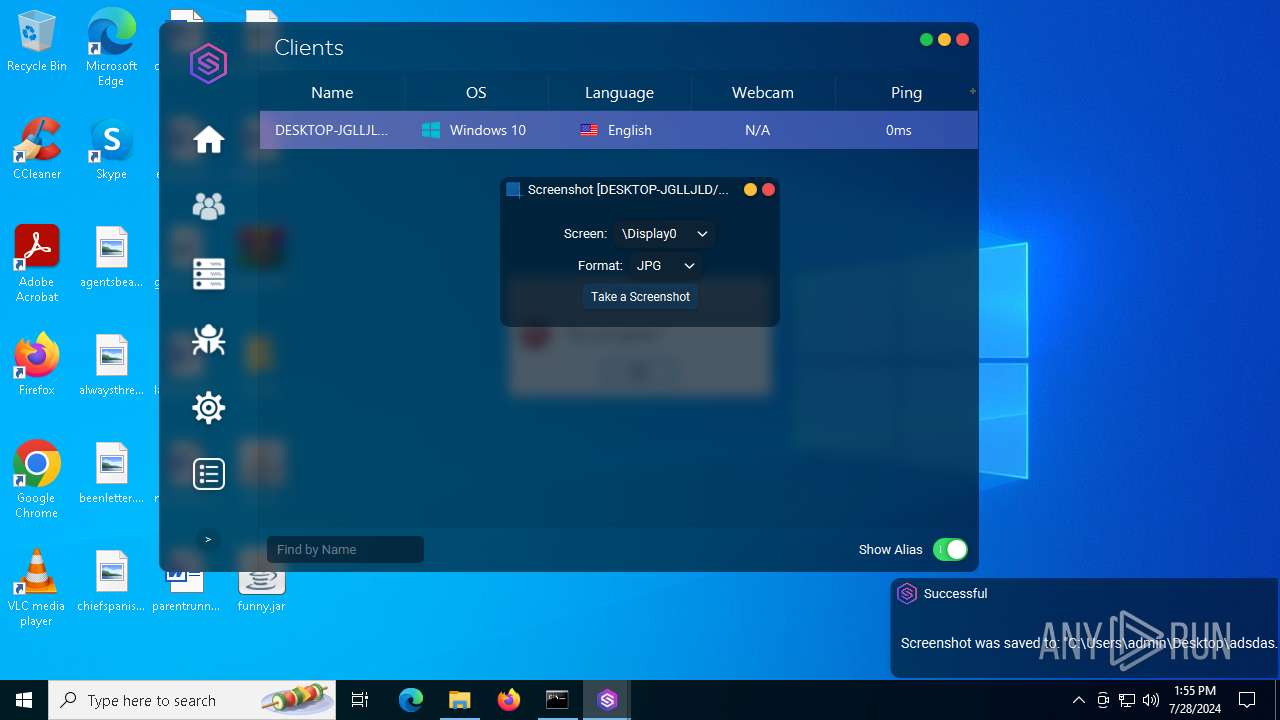
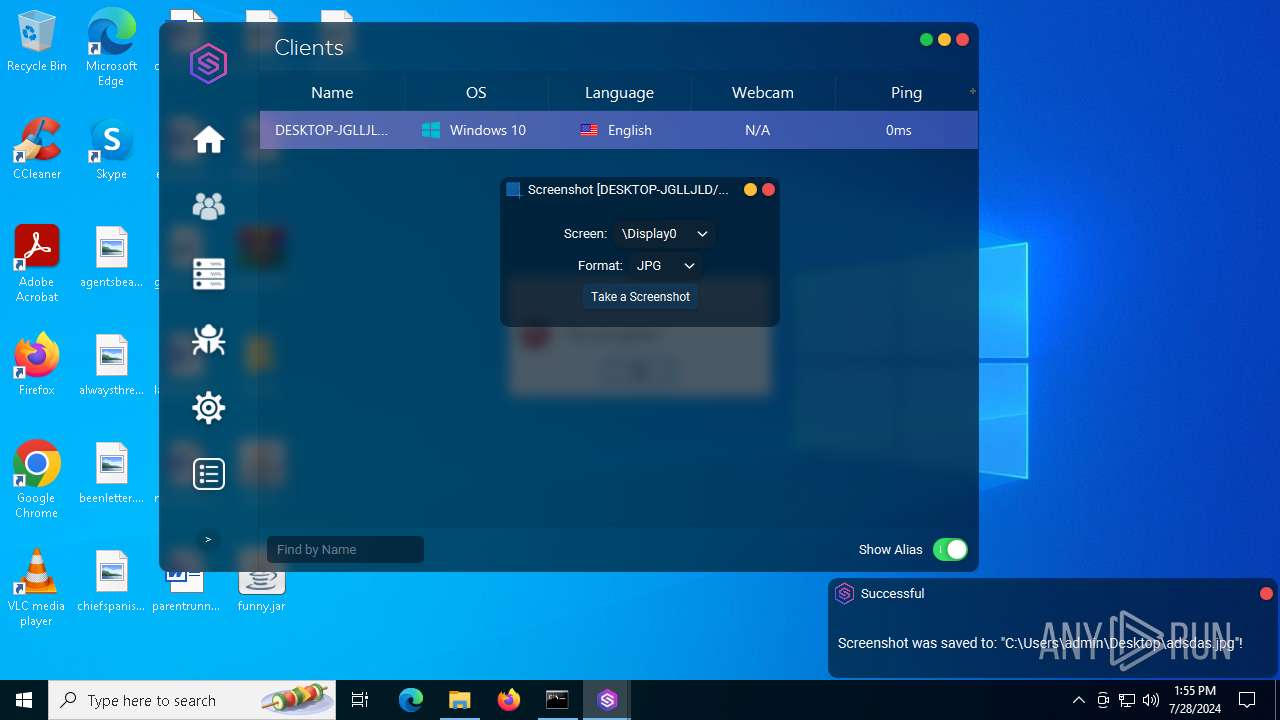
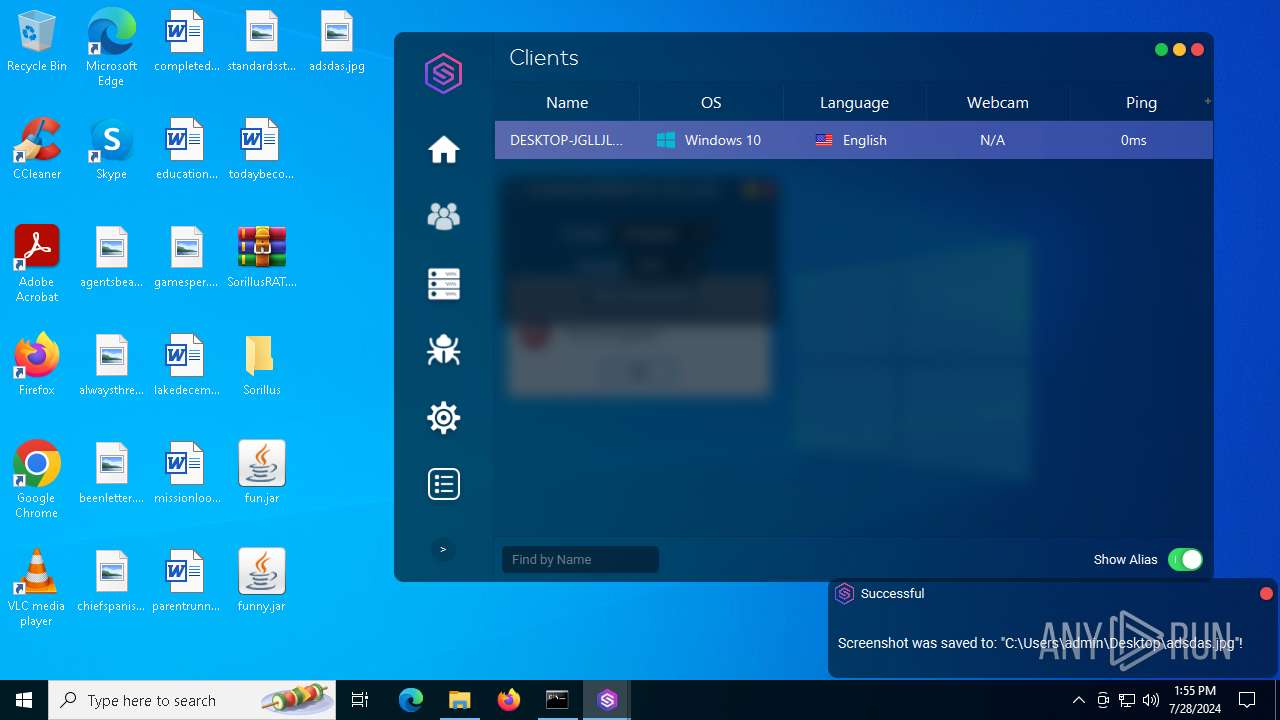
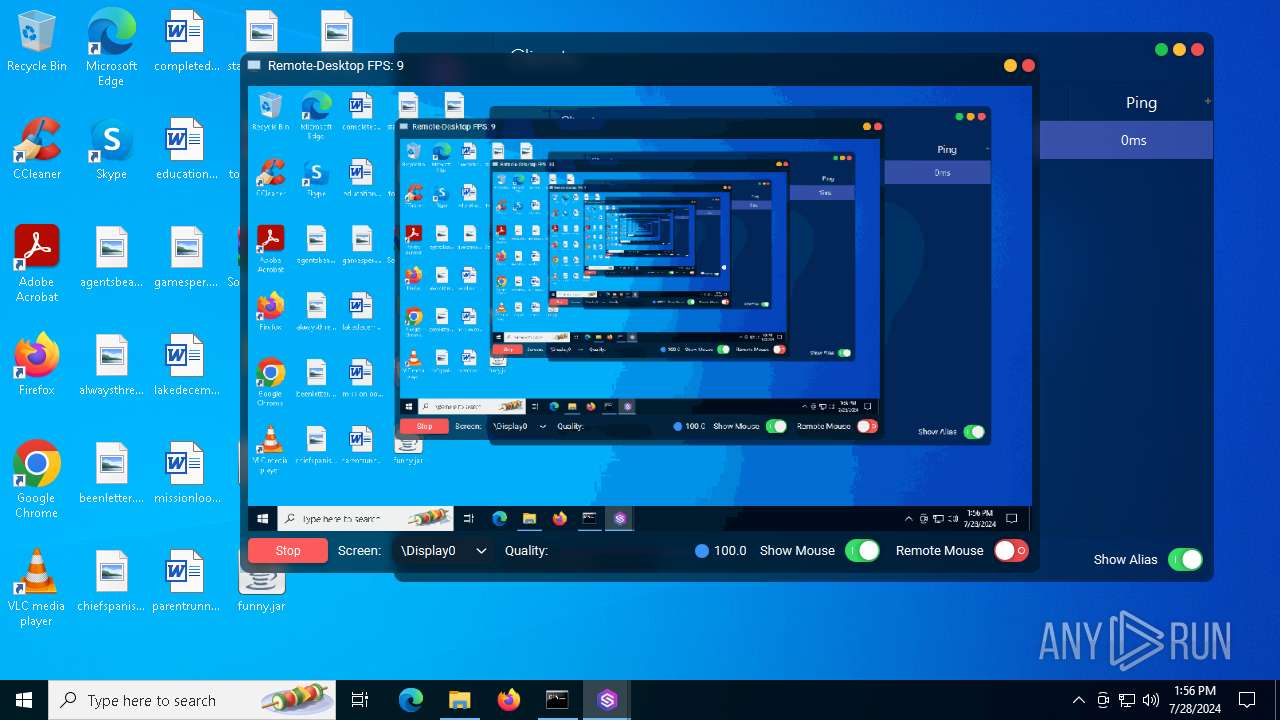
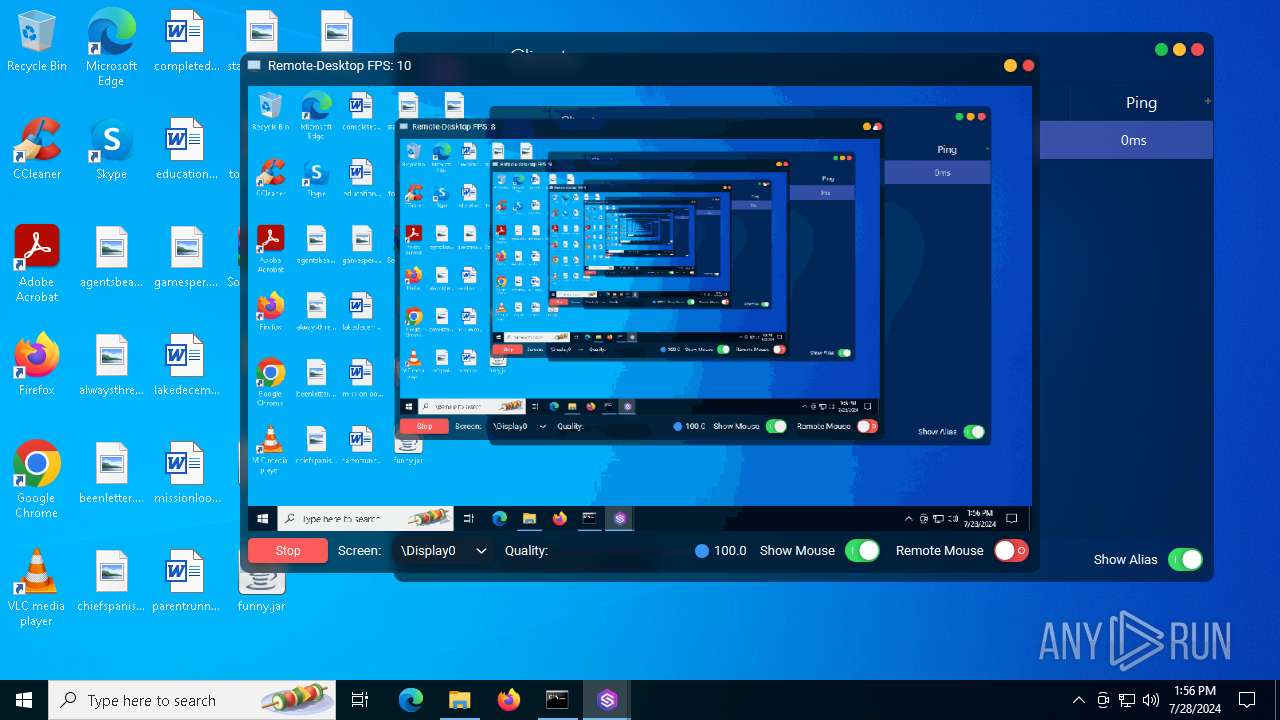
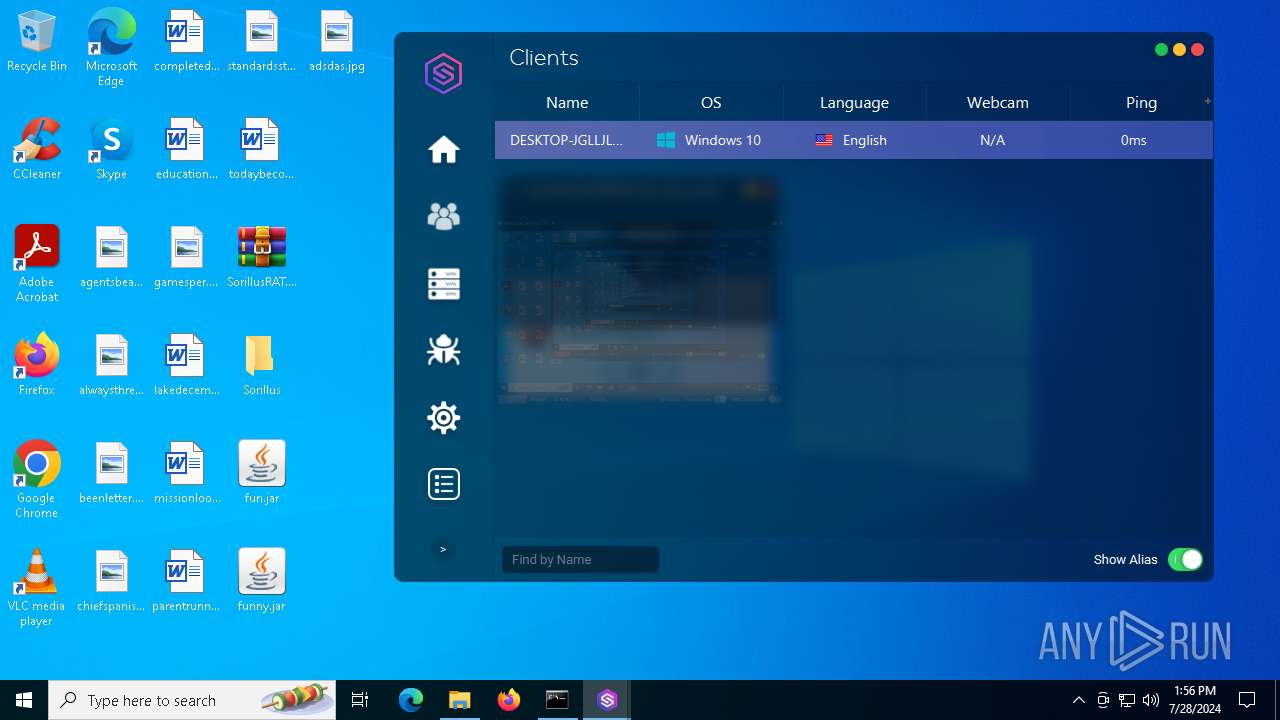
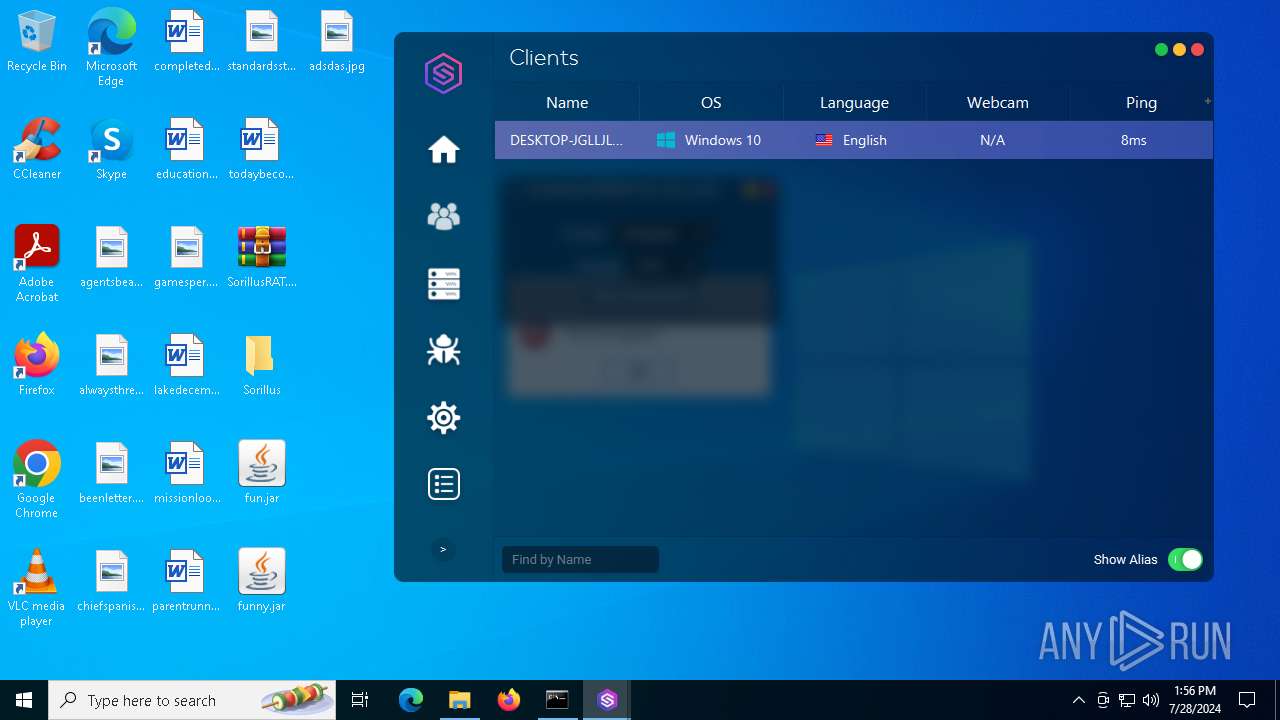
| File name: | SorillusRAT.rar |
| Full analysis: | https://app.any.run/tasks/42101f99-7f66-4969-b3d6-b0e1d0ec5951 |
| Verdict: | Malicious activity |
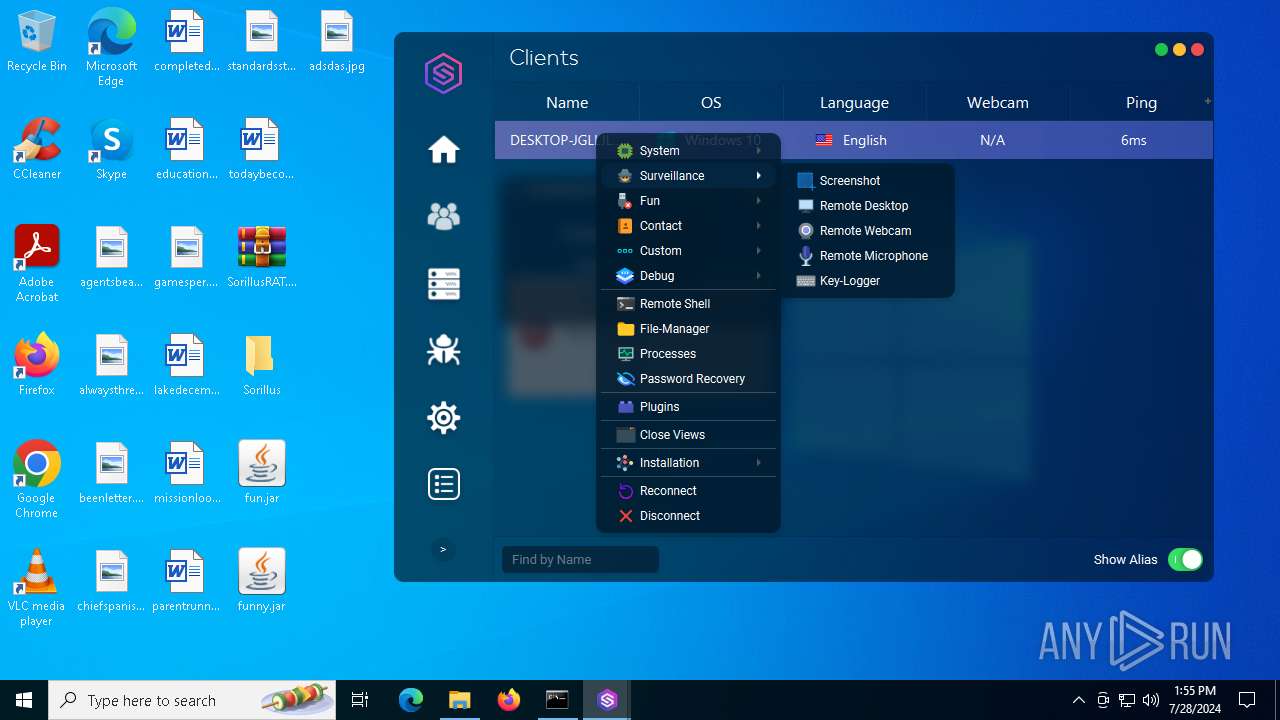
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | July 28, 2024, 13:50:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6B59FC4285E7842E36F3EC5A72935B44 |
| SHA1: | C1F3A89AC73F57C68C78BC9A1EC4C1FAC687B9AF |
| SHA256: | E7AAB6ECC96BE090AB8E04384E4685ED3E92466F5C776AA155A7FD5F05A098E6 |
| SSDEEP: | 786432:SgTpulP9RMRYuLx1EefJn/mhE9+5PCghok/uLyWE7yRtl:SgTpcP9R/sx15ea9+5PFekGLyWE7yRv |
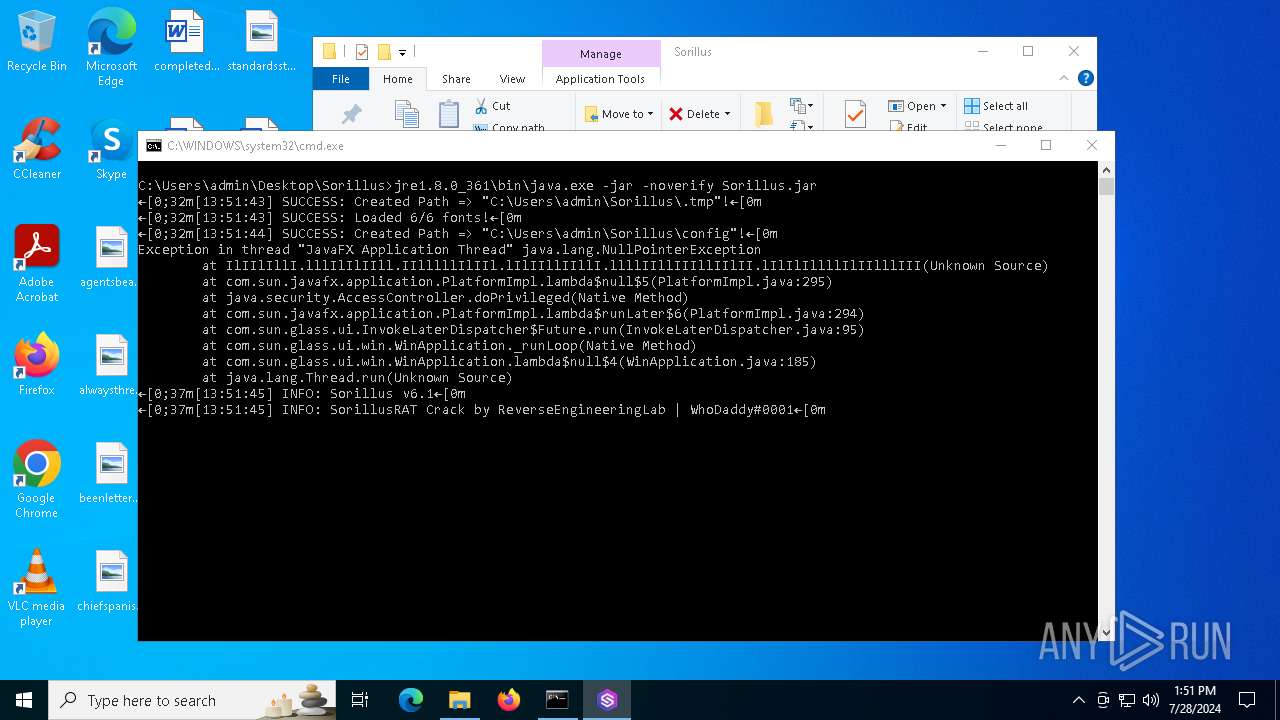
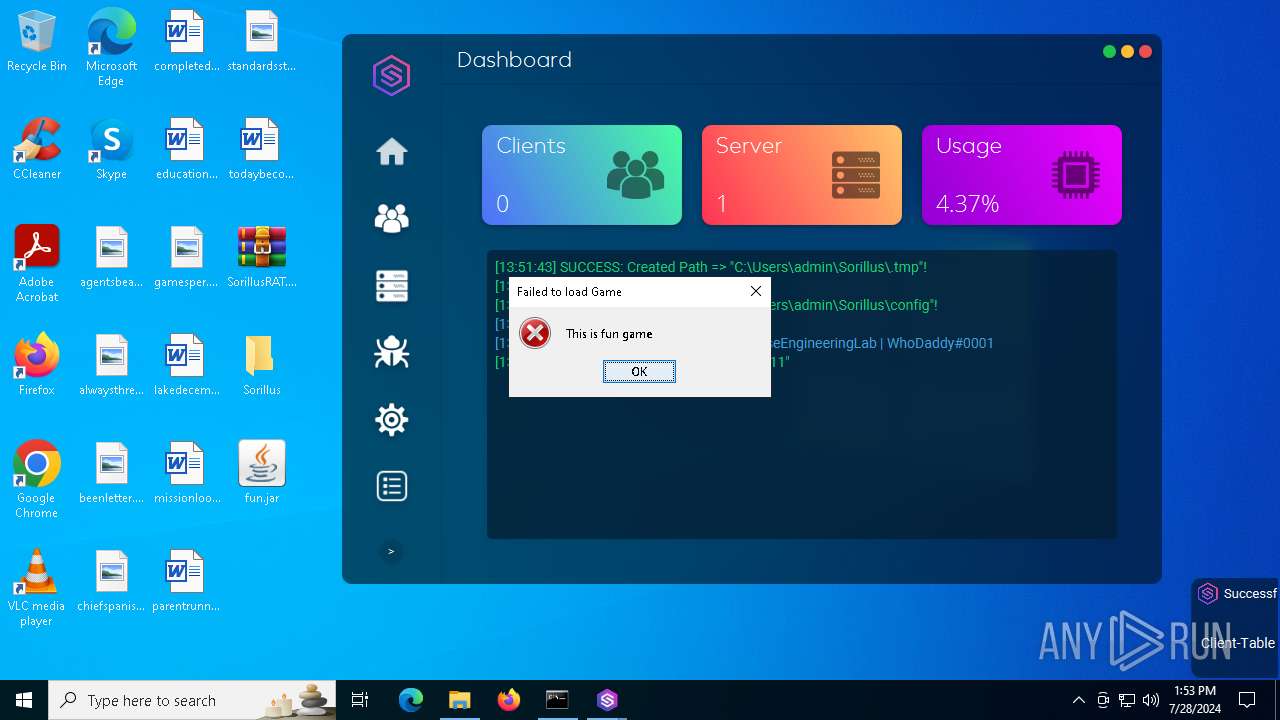
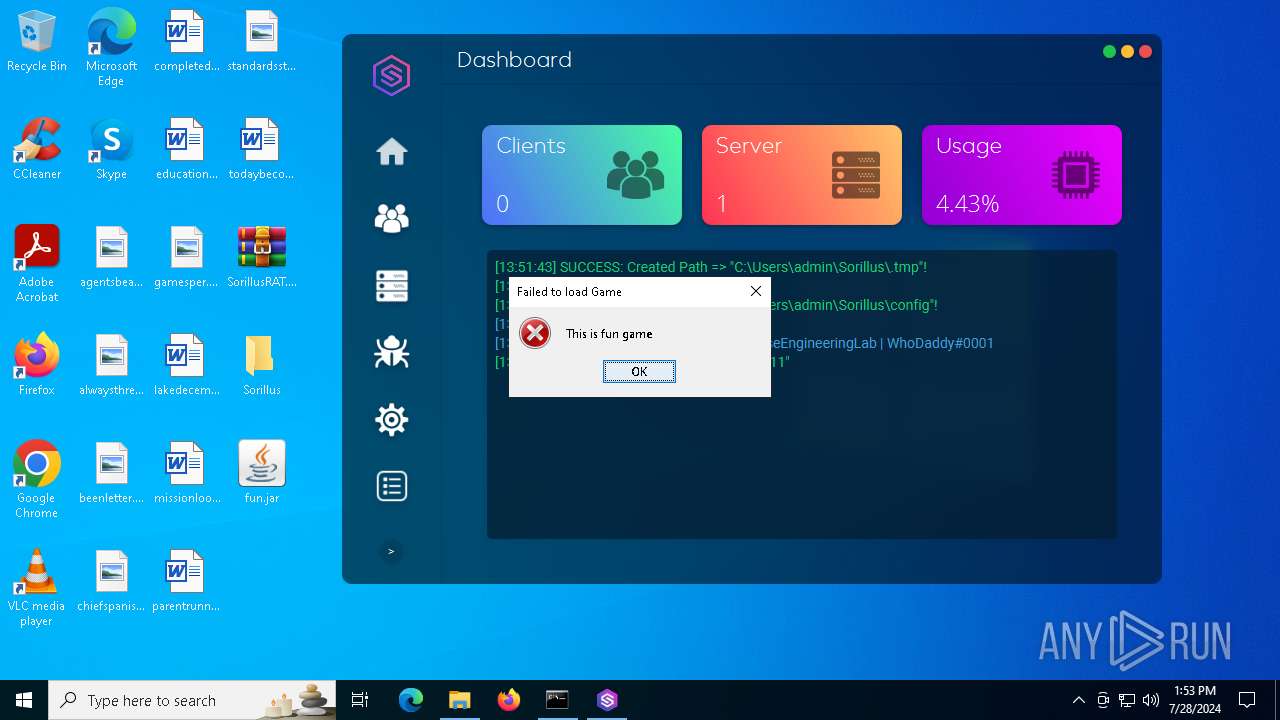
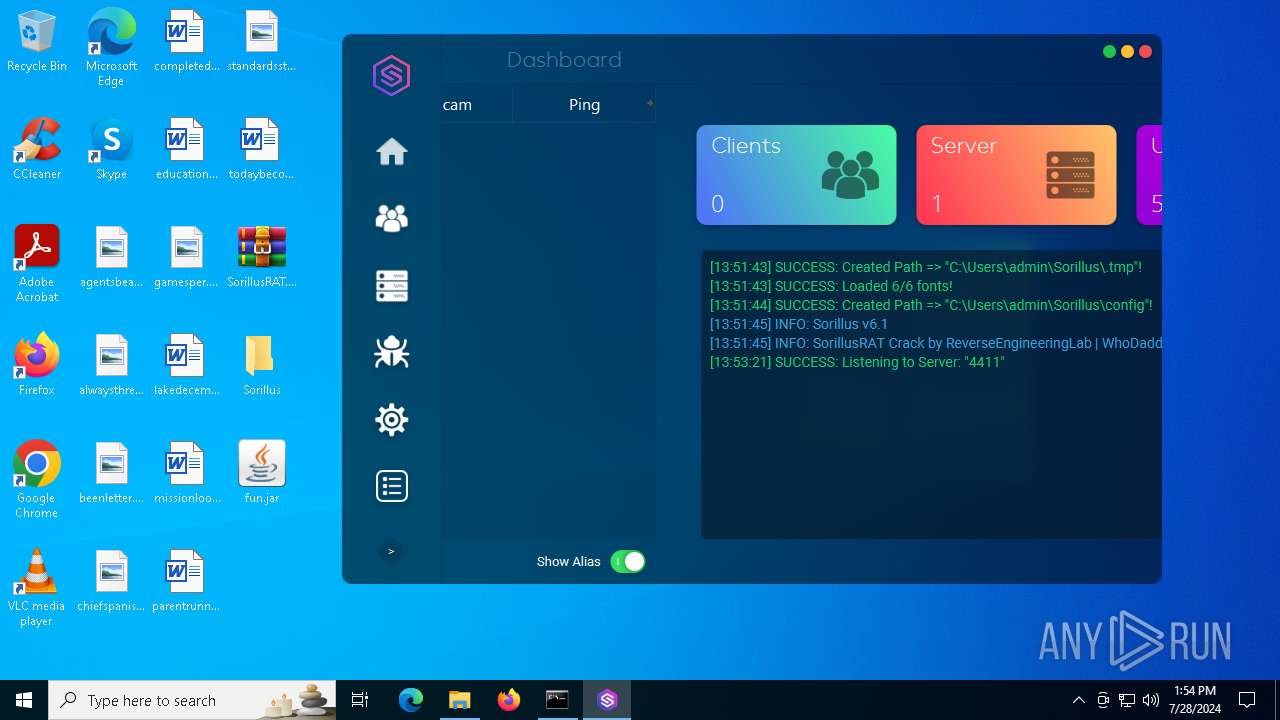
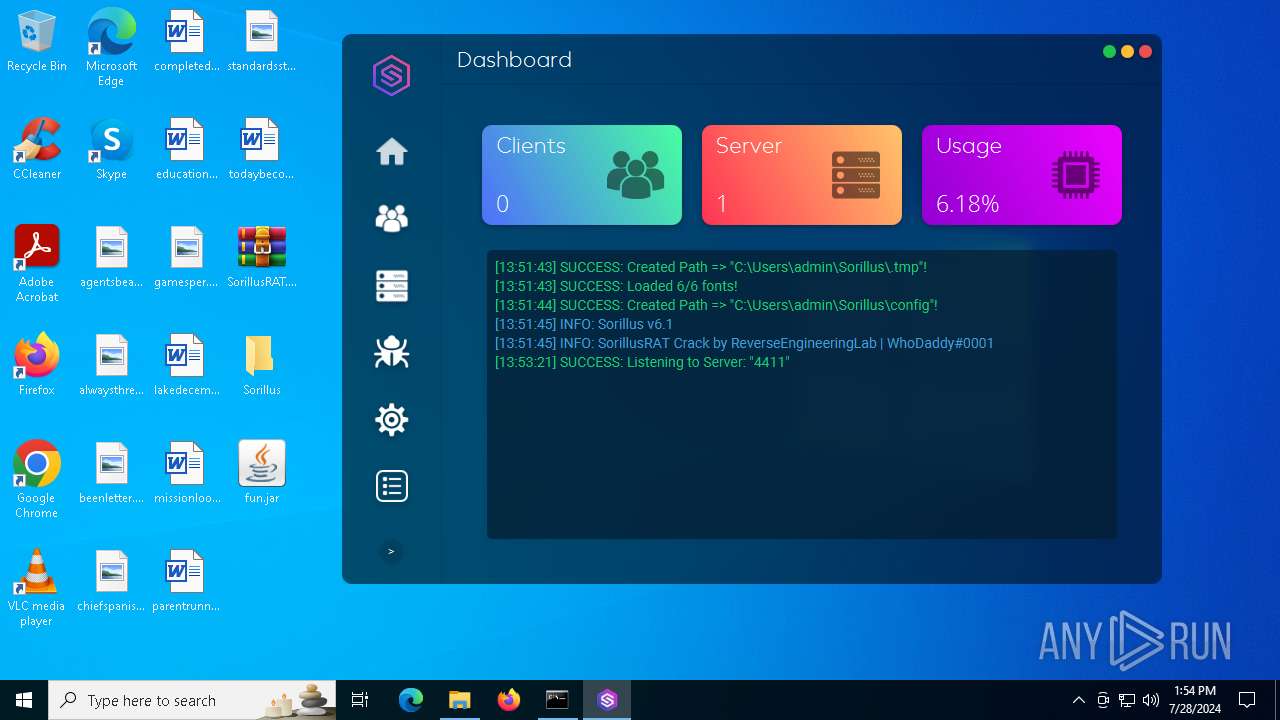
MALICIOUS
Drops the executable file immediately after the start
- java.exe (PID: 6512)
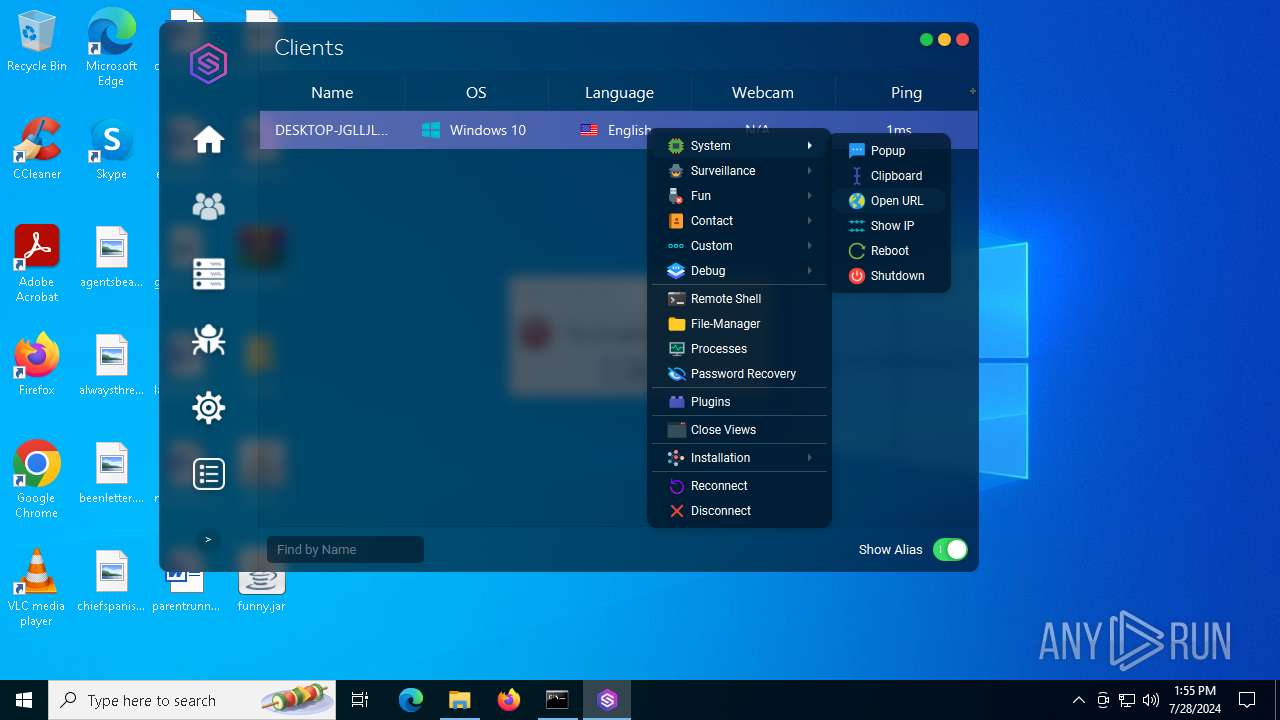
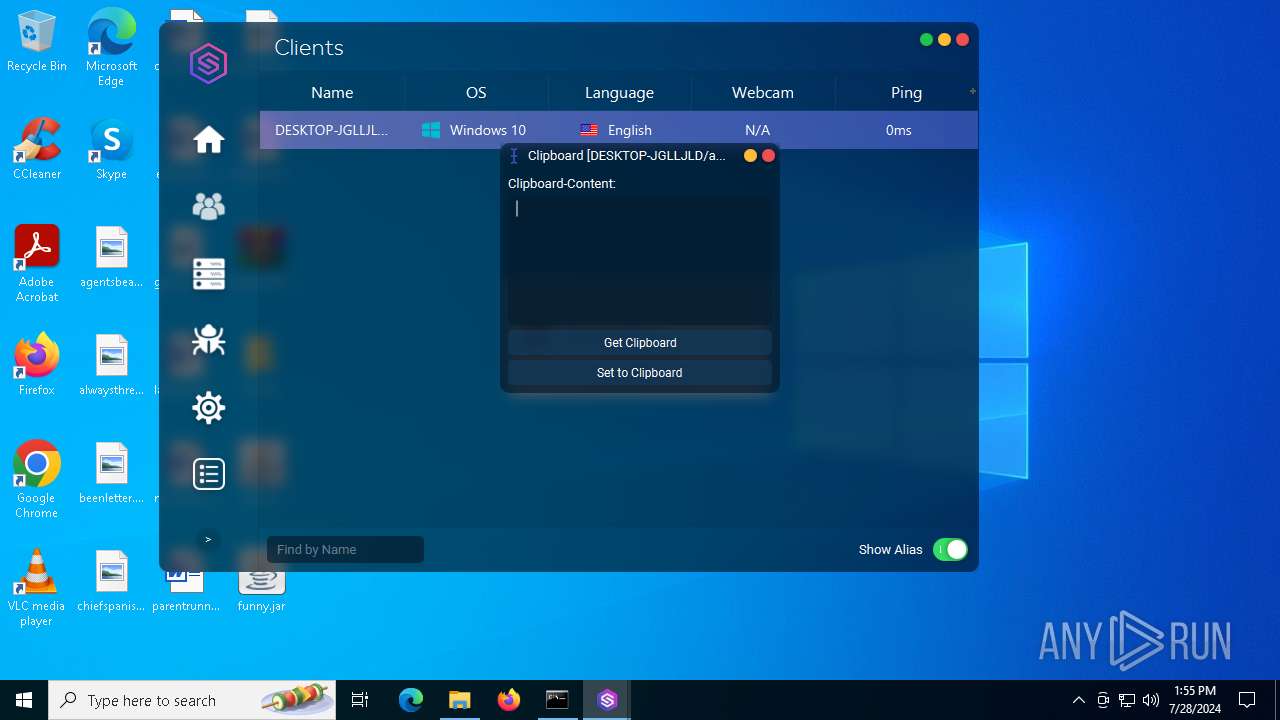
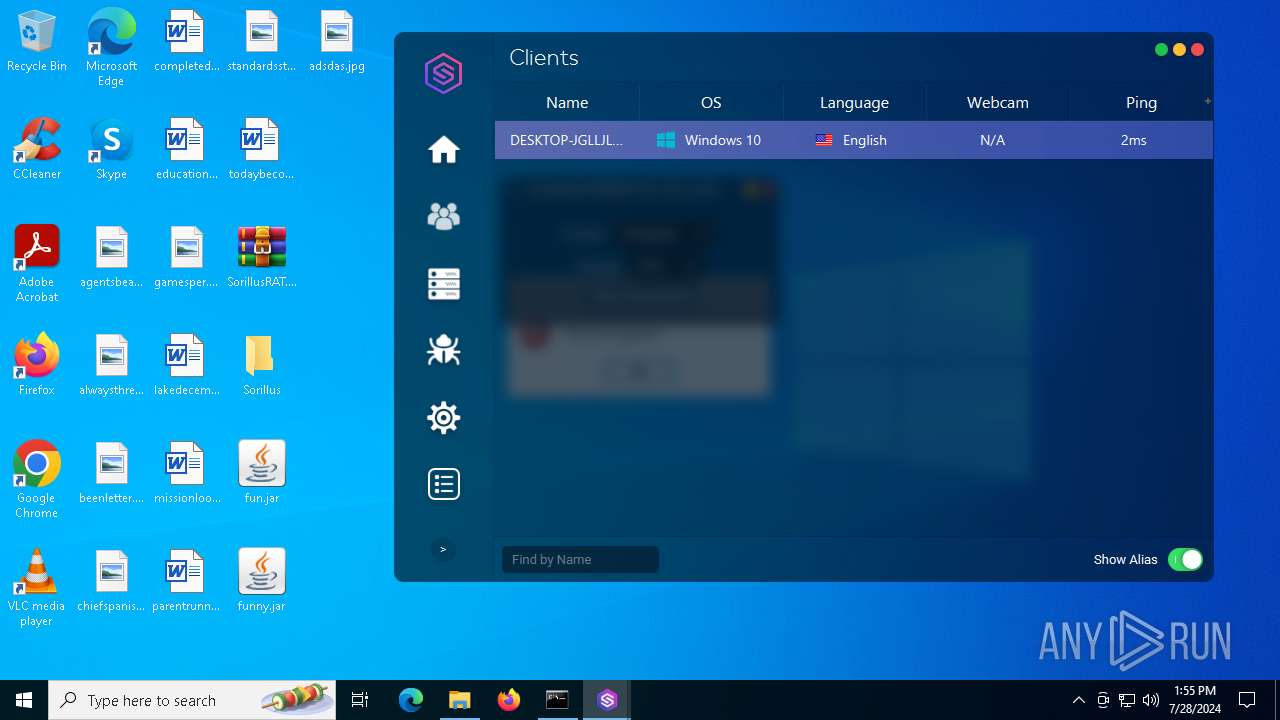
ADWIND has been detected
- java.exe (PID: 6512)
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
Changes the autorun value in the registry
- reg.exe (PID: 5716)
- reg.exe (PID: 3788)
- reg.exe (PID: 5632)
- reg.exe (PID: 6564)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4364)
Executable content was dropped or overwritten
- java.exe (PID: 6512)
Reads security settings of Internet Explorer
- java.exe (PID: 6512)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2668)
- cmd.exe (PID: 6544)
- cmd.exe (PID: 4324)
- cmd.exe (PID: 6140)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 4052)
- javaw.exe (PID: 6760)
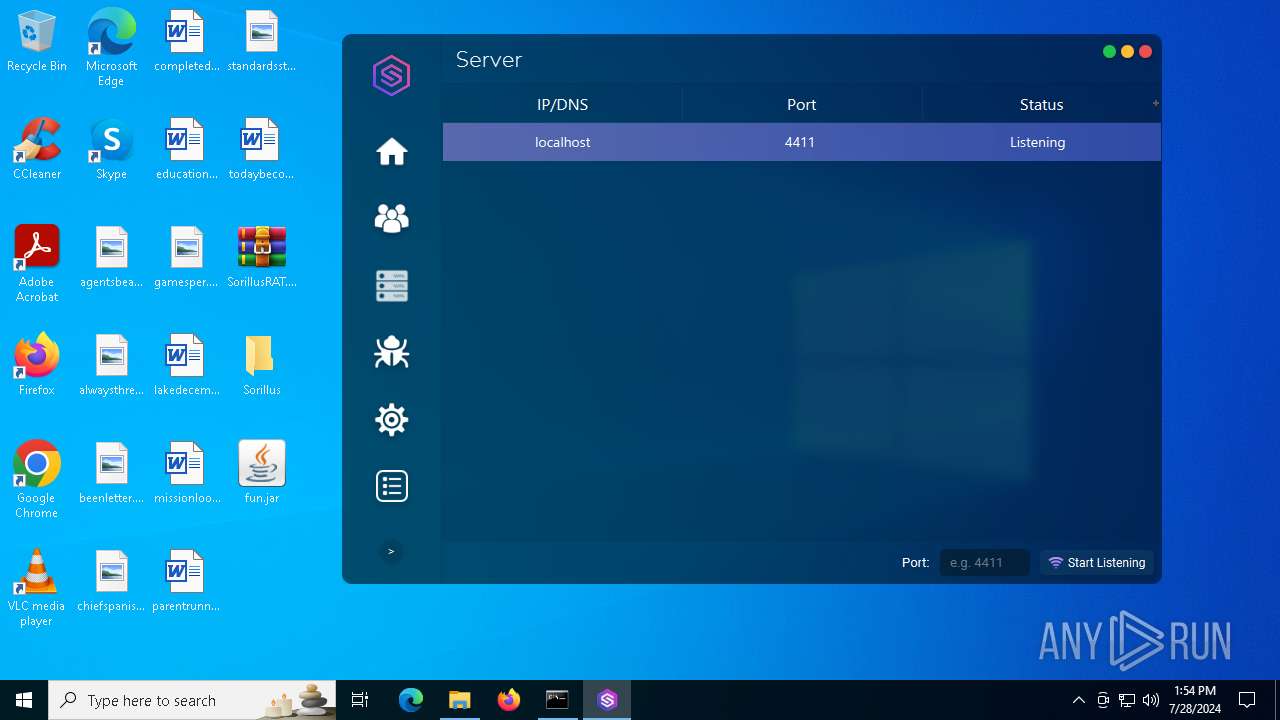
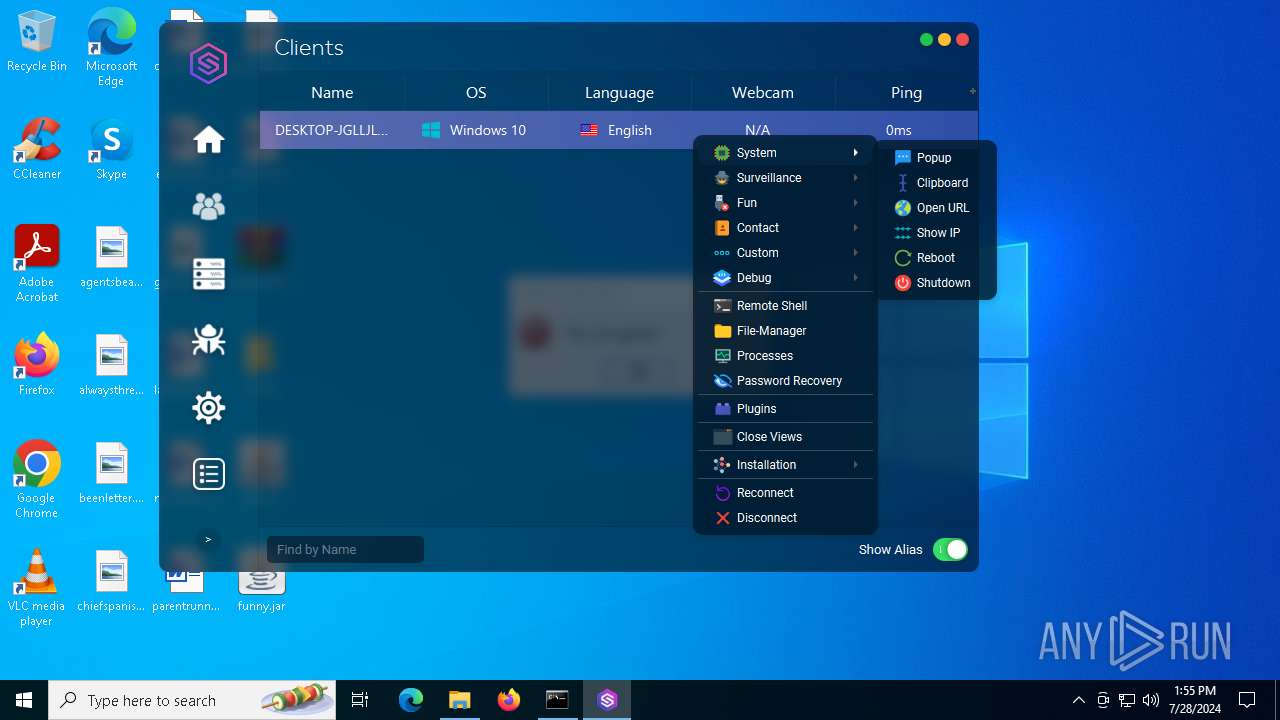
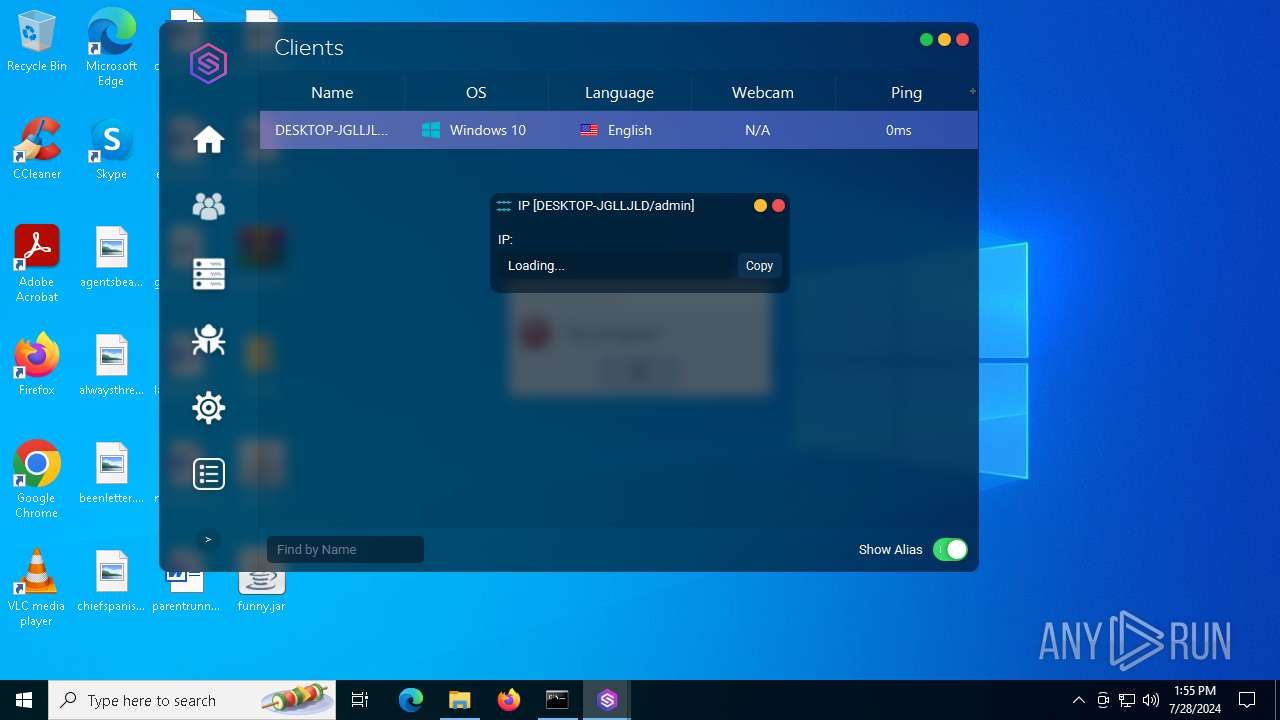
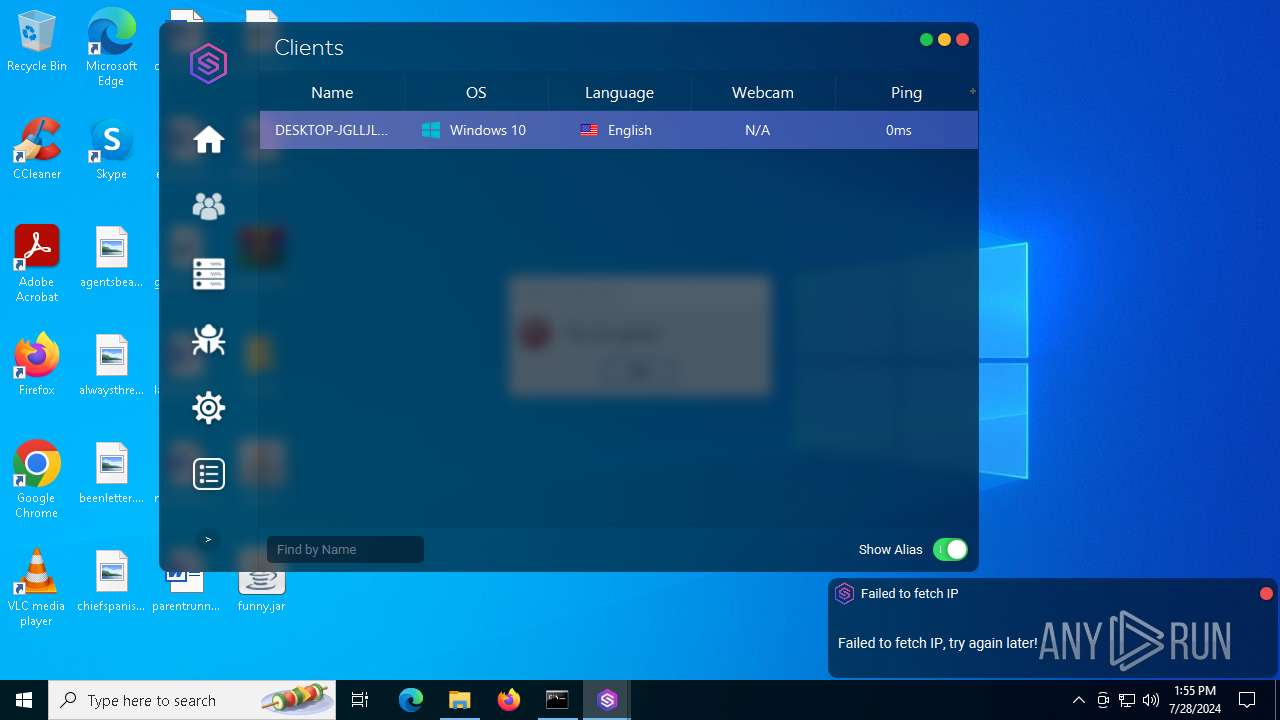
Checks for external IP
- svchost.exe (PID: 2284)
- javaw.exe (PID: 4052)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4364)
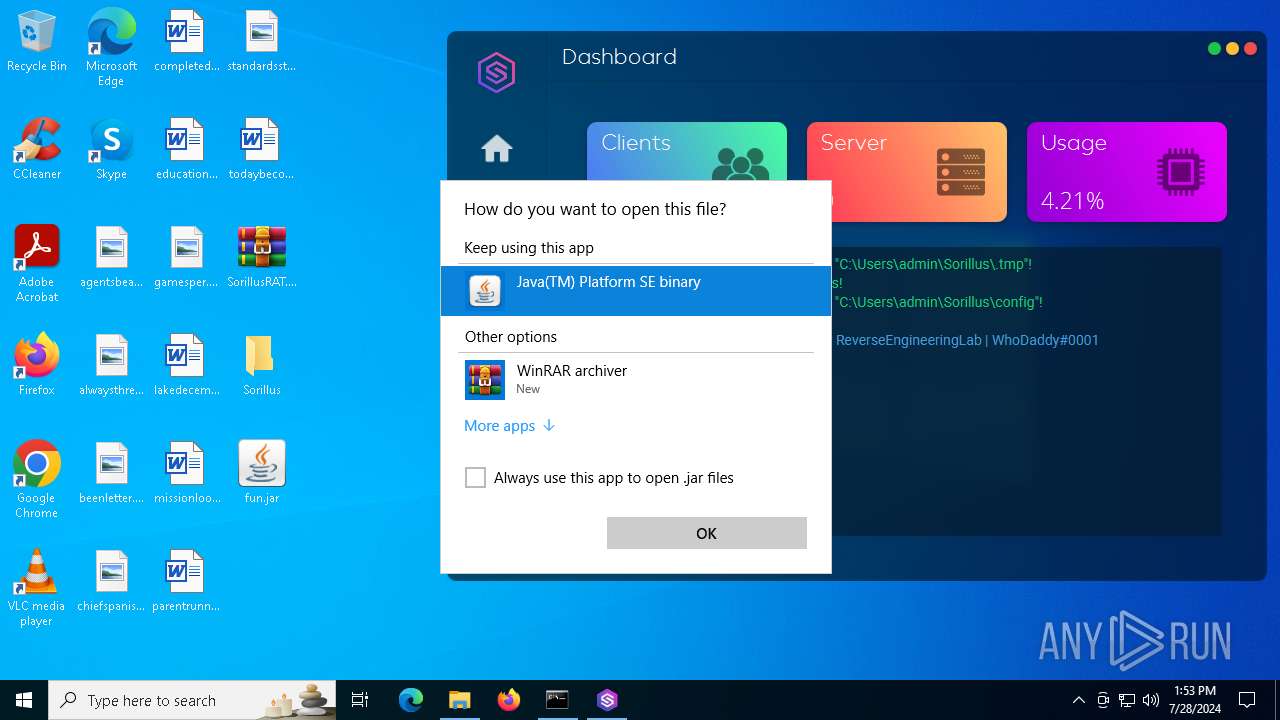
Manual execution by a user
- WinRAR.exe (PID: 4364)
- cmd.exe (PID: 6328)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
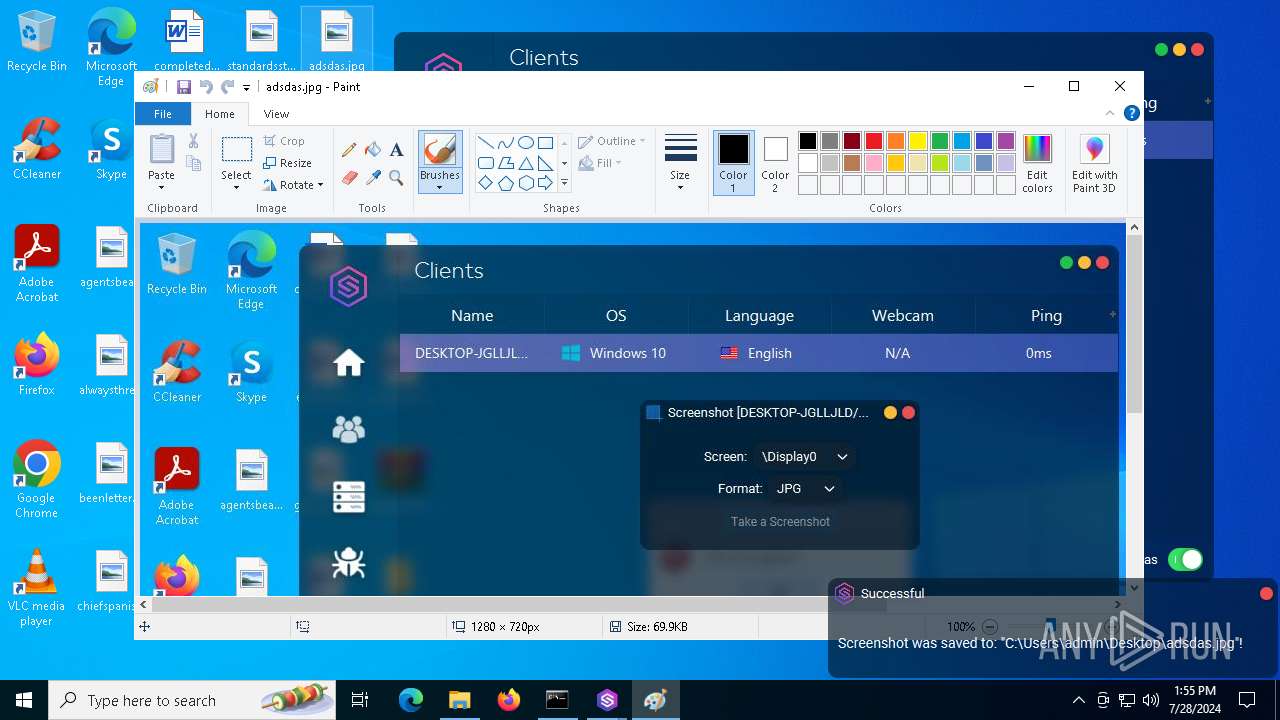
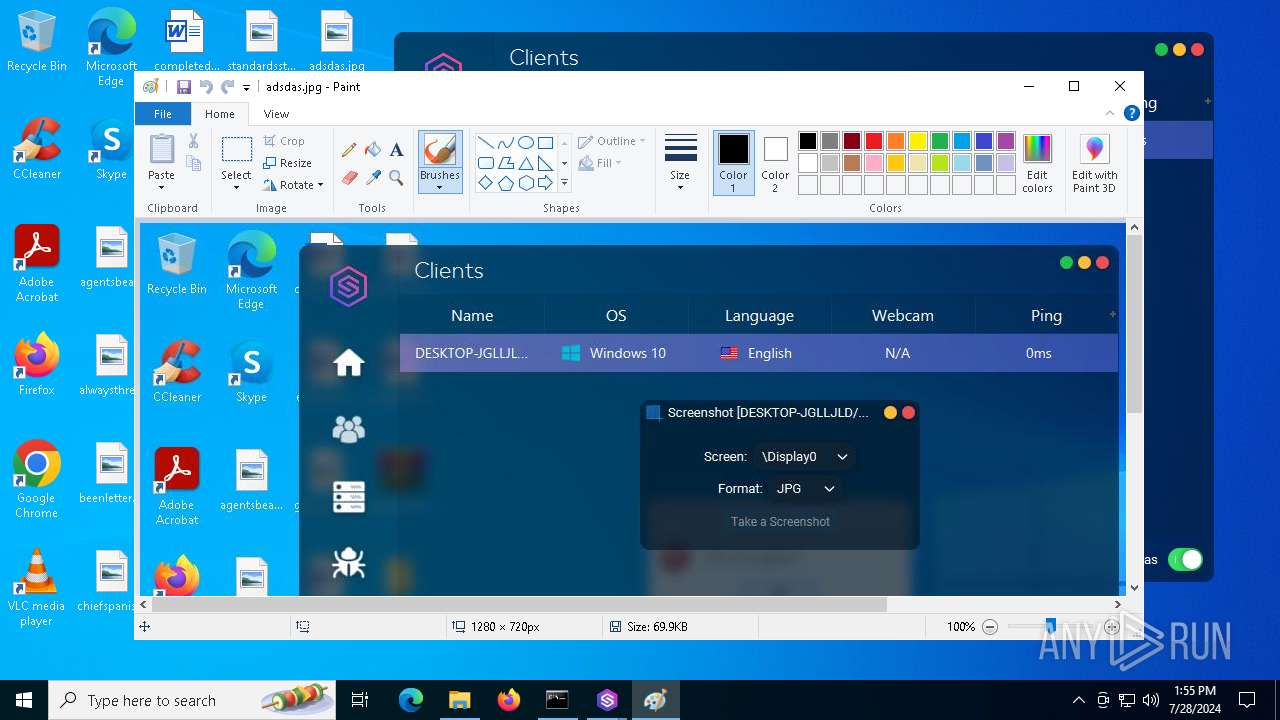
- mspaint.exe (PID: 4852)
Checks supported languages
- java.exe (PID: 6512)
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
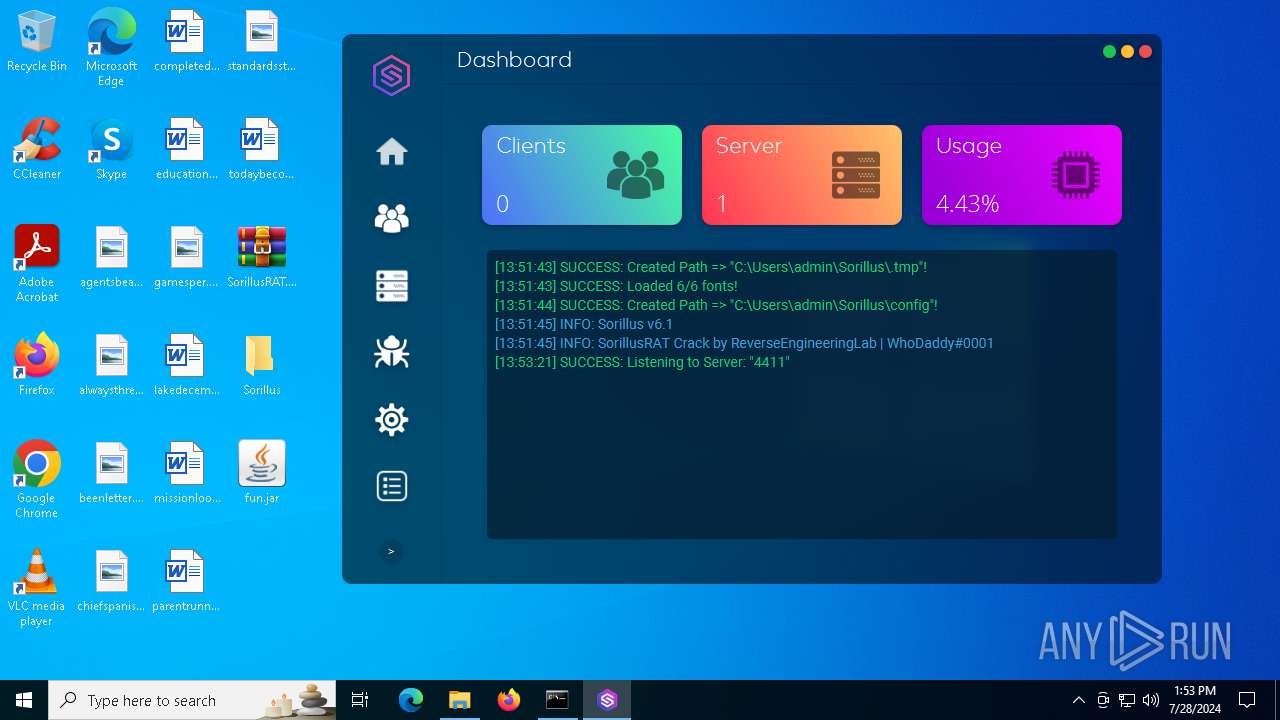
Create files in a temporary directory
- java.exe (PID: 6512)
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
Creates files in the program directory
- java.exe (PID: 6512)
- javaw.exe (PID: 3804)
Reads the machine GUID from the registry
- java.exe (PID: 6512)
- javaw.exe (PID: 4052)
Reads the computer name
- java.exe (PID: 6512)
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
Creates files or folders in the user directory
- java.exe (PID: 6512)
- javaw.exe (PID: 3804)
- javaw.exe (PID: 6744)
- javaw.exe (PID: 6760)
- javaw.exe (PID: 4052)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 256)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 256)
Reads the software policy settings
- slui.exe (PID: 2112)
Checks proxy server information
- slui.exe (PID: 2112)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
169
Monitored processes
35
Malicious processes
6
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | attrib +H C:\Users\admin\AppData\Roaming\Microsoft\.tmp\1722174847071.tmp | C:\Windows\System32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 256 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | attrib +H C:\Users\admin\AppData\Roaming\Microsoft\.tmp\1722174788078.tmp | C:\Windows\System32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | attrib.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | attrib.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | attrib.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 449
Read events
45 185
Write events
245
Delete events
19
Modification events
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SorillusRAT.rar | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
154
Suspicious files
38
Text files
157
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:919E653868A3D9F0C9865941573025DF | SHA256:2AFBFA1D77969D0F4CEE4547870355498D5C1DA81D241E09556D0BD1D6230F8C | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:94788729C9E7B9C888F4E323A27AB548 | SHA256:ACCDD7455FB6D02FE298B987AD412E00D0B8E6F5FB10B52826367E7358AE1187 | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:AC51E3459E8FCE2A646A6AD4A2E220B9 | SHA256:77577F35D3A61217EA70F21398E178F8749455689DB52A2B35A85F9B54C79638 | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:BBAFA10627AF6DFAE5ED6E4AEAE57B2A | SHA256:C78A1217F8DCB157D1A66B80348DA48EBDBBEDCEA1D487FC393191C05AAD476D | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:3BF4406DE02AA148F460E5D709F4F67D | SHA256:349A79FA1572E3538DFBB942610D8C47D03E8A41B98897BC02EC7E897D05237E | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:3A4B6B36470BAD66621542F6D0D153AB | SHA256:2E981EE04F35C0E0B7C58282B70DCC9FC0318F20F900607DAE7A0D40B36E80AF | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:35BC1F1C6FBCCEC7EB8819178EF67664 | SHA256:7A3C5167731238CF262F749AA46AB3BFB2AE1B22191B76E28E1D7499D28C24B7 | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:A038716D7BBD490378B26642C0C18E94 | SHA256:B02324C49DD039FA889B4647331AA9AC65E5ADC0CC06B26F9F086E2654FF9F08 | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-console-l1-2-0.dll | executable | |
MD5:7676560D0E9BC1EE9502D2F920D2892F | SHA256:00942431C2D3193061C7F4DC340E8446BFDBF792A7489F60349299DFF689C2F9 | |||
| 4364 | WinRAR.exe | C:\Users\admin\Desktop\Sorillus\jre1.8.0_361\bin\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:B0E0678DDC403EFFC7CDC69AE6D641FB | SHA256:45E48320ABE6E3C6079F3F6B84636920A367989A88F9BA6847F88C210D972CF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
51
DNS requests
50
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.100.146.10:443 | https://th.bing.com/th?id=ODSWG.a63c4ede-672e-4b0b-b035-e0f9aa973fce&c=1&rs=1&p=0 | unknown | — | — | unknown |
— | — | GET | 200 | 95.100.146.25:443 | https://www.bing.com/th?id=ODSWG.337890f2-f5b9-4e65-8611-af96ccc12251&pid=dsb | unknown | image | 24.0 Kb | unknown |
— | — | POST | 200 | 52.182.143.209:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 95.100.146.40:443 | https://r.bing.com/rb/16/jnc,nj/8is6HLWQOmmjdhp0hh0w6MjZScI.js?bu=DygxcoQBiQGMAYEBe36_AcIBMbIBMcUB&or=w | unknown | s | 21.4 Kb | unknown |
— | — | GET | 200 | 95.100.146.10:443 | https://th.bing.com/th?id=OPN.RTNews_-cPzCNaPObnwOltMQJOoTg&w=140&h=96&c=1&rs=1&p=0 | unknown | image | 3.63 Kb | unknown |
— | — | GET | 200 | 95.100.146.32:443 | https://th.bing.com/th?id=OPN.RTNews_Hb3wXFH2bY7l-cfbm9OF8g&w=140&h=96&c=1&rs=1&p=0 | unknown | image | 3.31 Kb | unknown |
— | — | GET | 200 | 95.100.146.17:443 | https://th.bing.com/th?id=OPN.RTNews_Xi90gGfSvtR3KLjxn9Cb-g&w=140&h=96&c=1&rs=1&p=0 | unknown | image | 4.97 Kb | unknown |
— | — | GET | 200 | 95.100.146.40:443 | https://th.bing.com/th?id=OPN.RTNews_FF7Y6WPKL-DaOAL9sShAyQ&w=140&h=96&c=1&rs=1&p=0 | unknown | image | 3.71 Kb | unknown |
— | — | POST | 200 | 52.168.117.168:443 | https://browser.pipe.aria.microsoft.com/Collector/3.0/?qsp=true&content-type=application%2Fbond-compact-binary&client-id=NO_AUTH&sdk-version=AWT-Web-CJS-1.2.0&x-apikey=33d70a864599496b982a39f036f71122-2064703e-3a9d-4d90-8362-eec08dffe8e8-7176 | unknown | — | — | unknown |
— | — | GET | 200 | 95.100.146.32:443 | https://th.bing.com/th?id=OSGI.3AE3C25FFBF5754A9EB4EEBC7D407CF5&w=86&h=86&c=1&rs=1&p=0 | unknown | image | 3.51 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 95.100.146.17:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
2988 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
0.0.0.0 |
| unknown |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4052 | javaw.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain (checkip .amazonaws .com) in TLS SNI |
2284 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (checkip .amazonaws .com) |
1 ETPRO signatures available at the full report