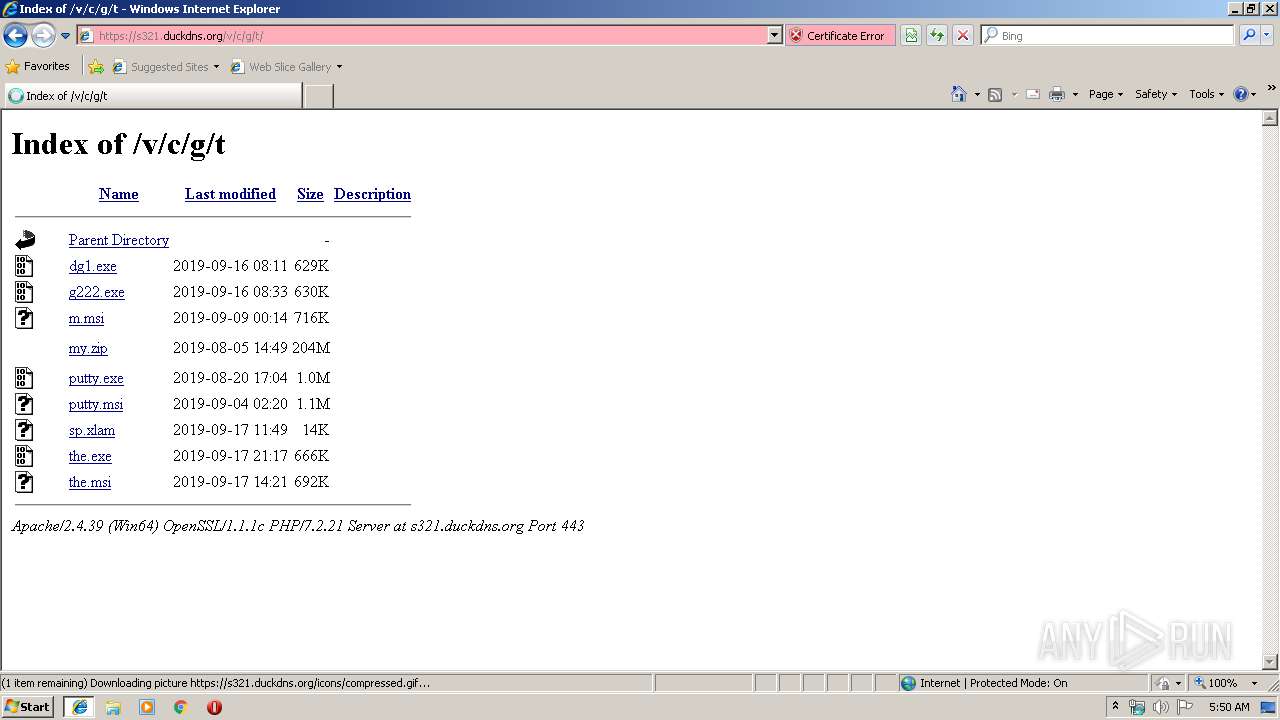
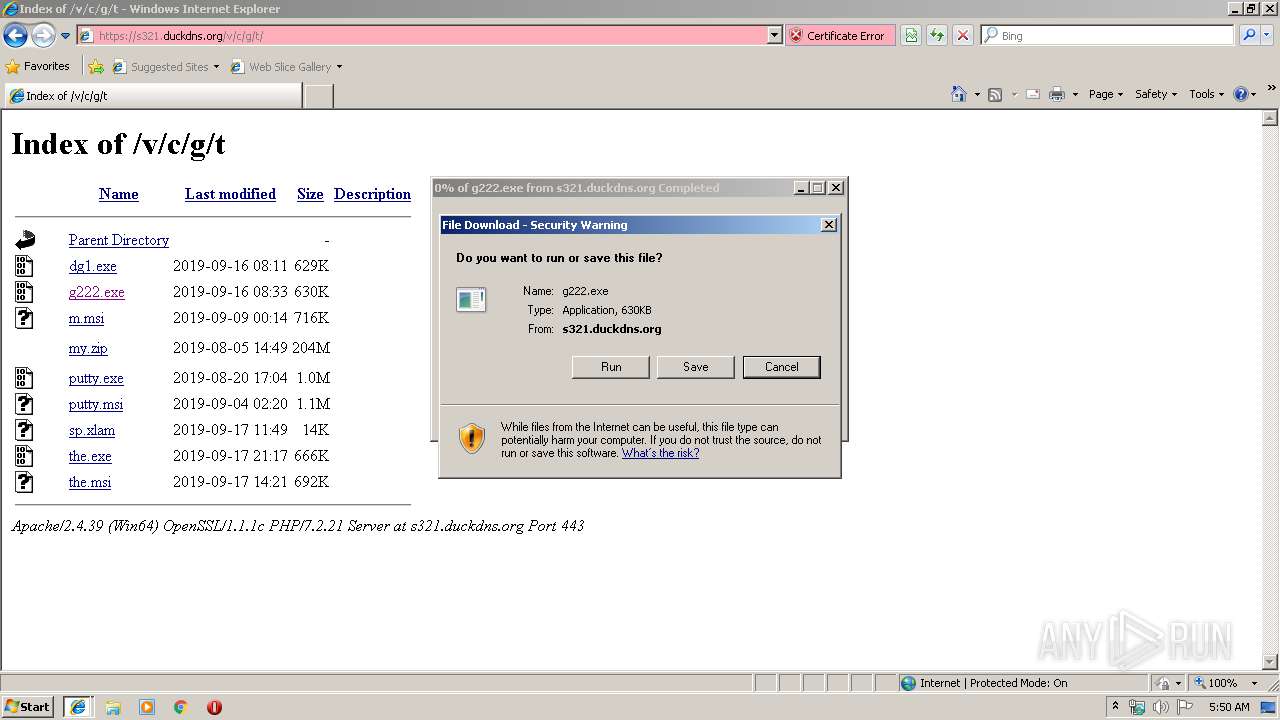
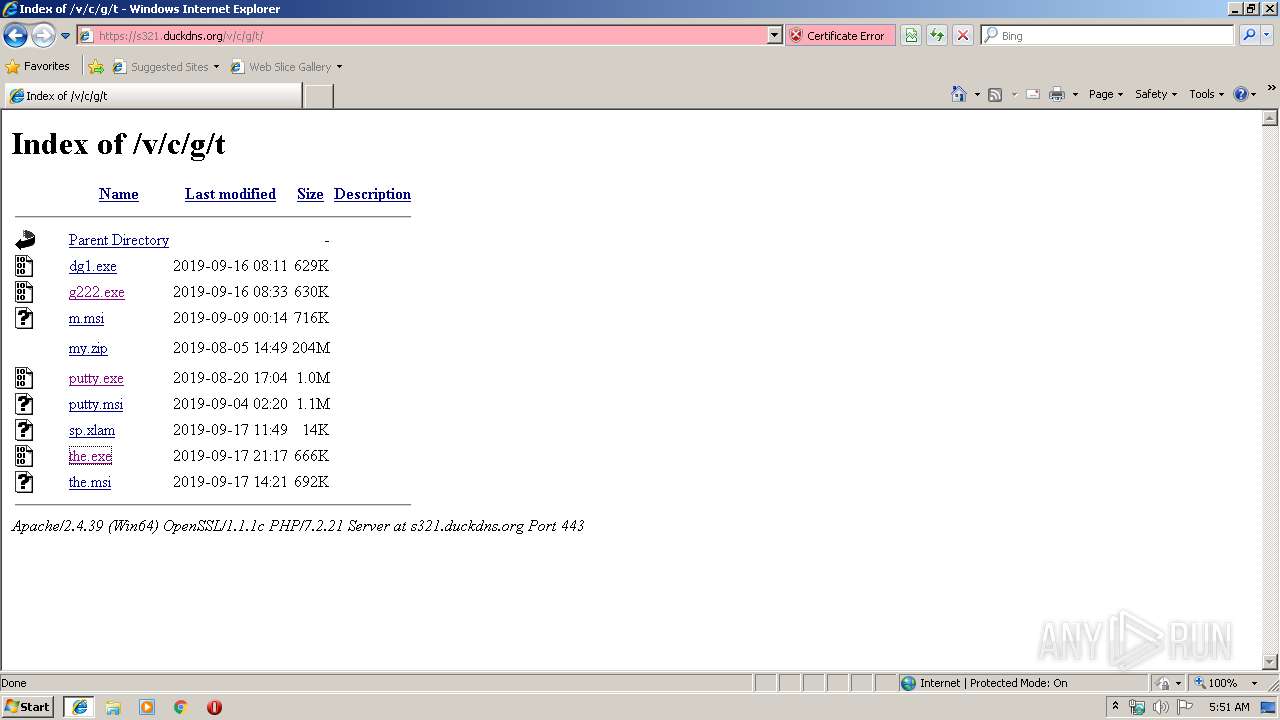
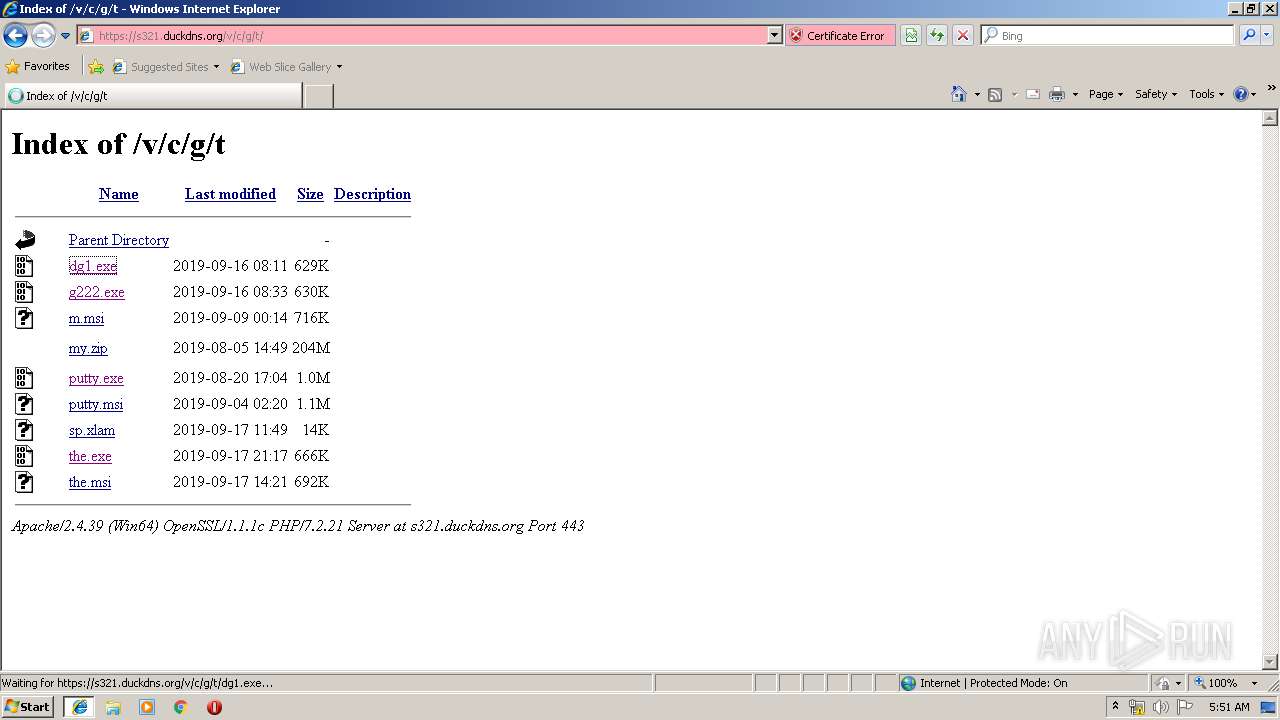
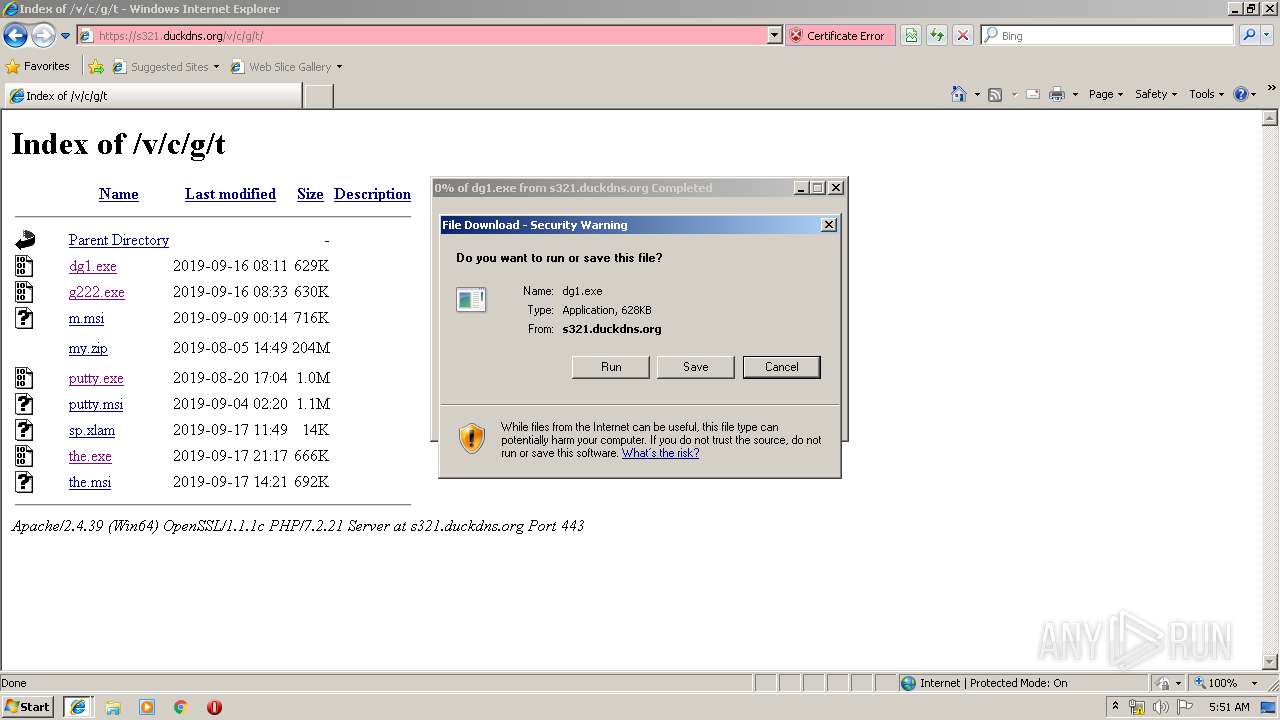
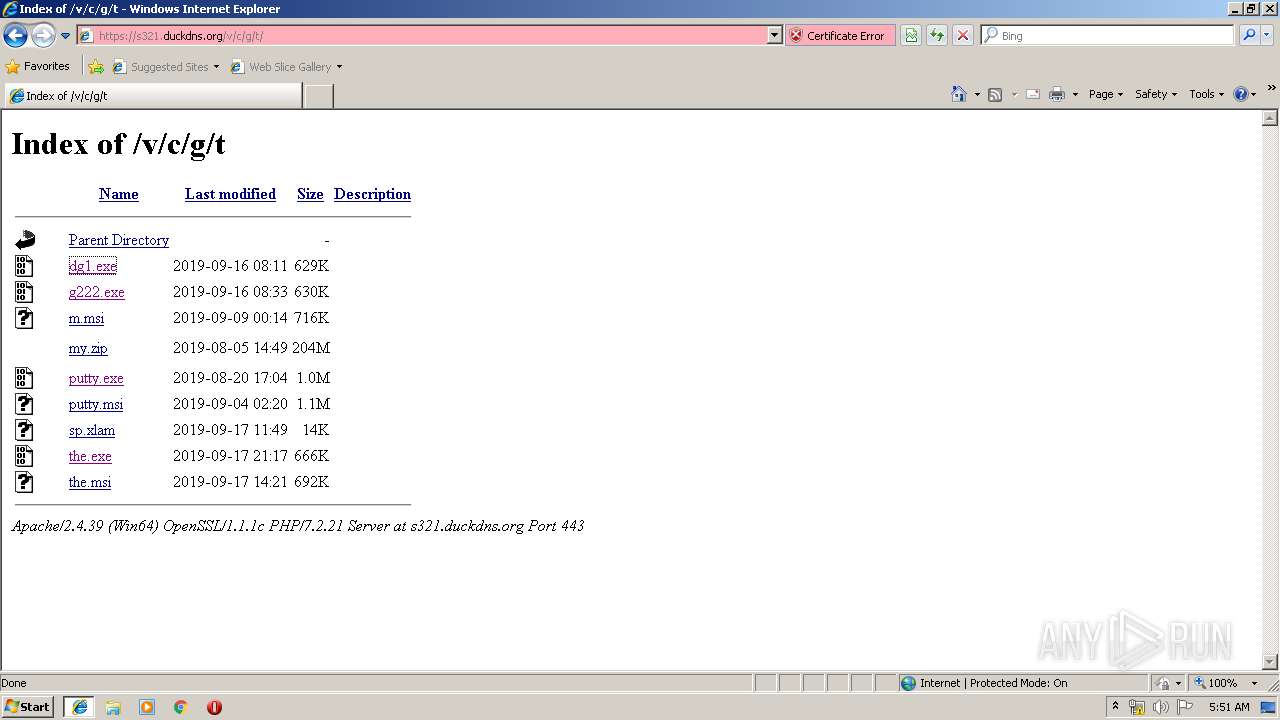
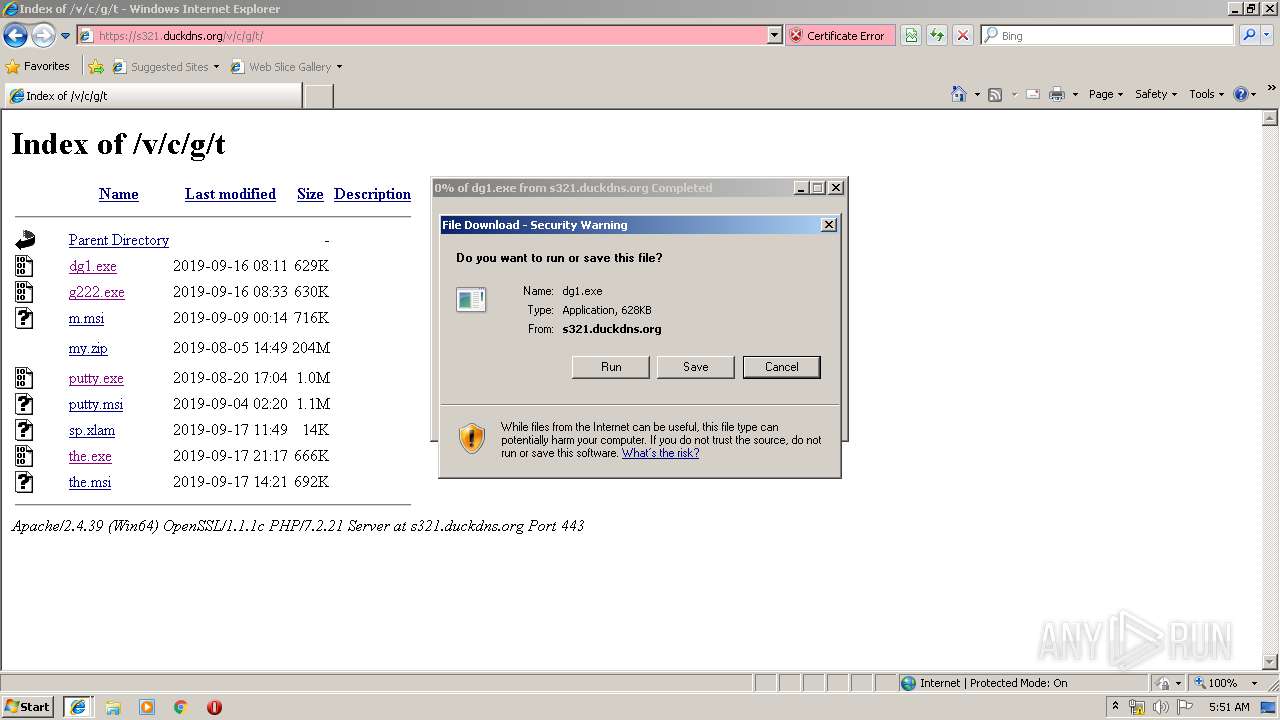
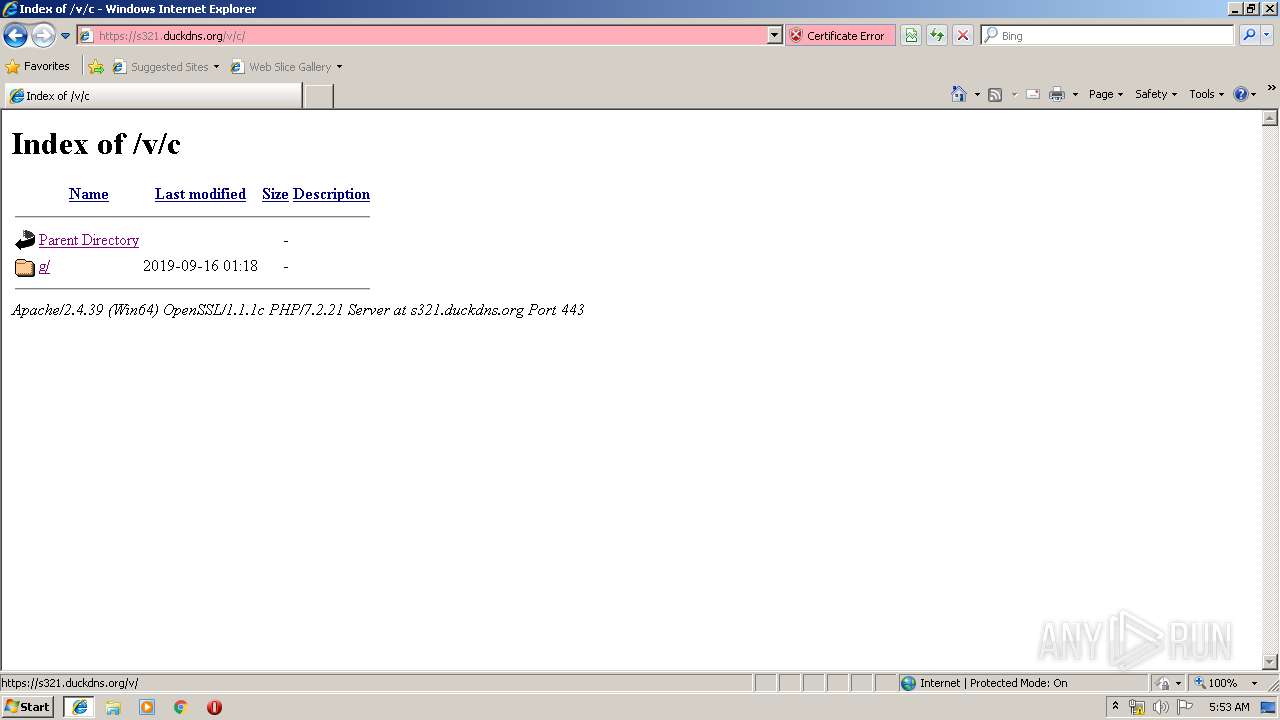
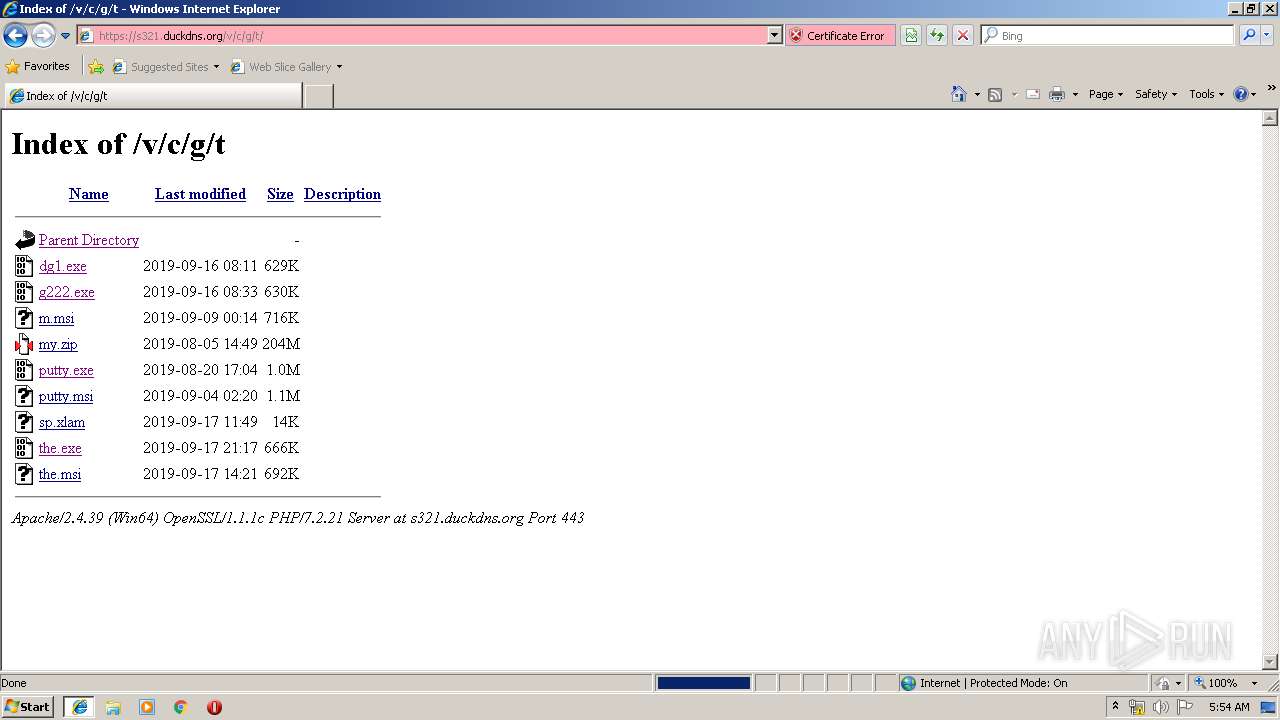
| URL: | https://s321.duckdns.org/v/c/g/t/ |
| Full analysis: | https://app.any.run/tasks/c7d7aa91-742b-4210-8d2a-072edee22485 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | September 19, 2019, 04:50:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D59C5CF9D38F5862795F1EB1D22DB34D |
| SHA1: | B7B73CFF4F1E756282B15FBEBAB7DFA1EF8D522F |
| SHA256: | E78BBE7536E79E2DAEC42AF1600887F361C565DC0EFAE40D6E53C6F990634DB0 |
| SSDEEP: | 3:N8WCLWisi:2WIWli |
MALICIOUS
Application was dropped or rewritten from another process
- putty[1].exe (PID: 2388)
- g222[1].exe (PID: 3824)
- RegAsm.exe (PID: 2484)
- the[1].exe (PID: 2376)
- dg1[1].exe (PID: 2332)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- gtwse.exe (PID: 3644)
- gtwse.exe (PID: 3452)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
- vbc.exe (PID: 3684)
- rxopqjfpxbjhankh.exe (PID: 2752)
- gtwse.exe (PID: 812)
- gtwse.exe (PID: 3240)
- RegAsm.exe (PID: 2972)
AGENTTESLA was detected
- RegAsm.exe (PID: 2484)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Uses Task Scheduler to run other applications
- g222[1].exe (PID: 3824)
- dg1[1].exe (PID: 2332)
- gtwse.exe (PID: 3644)
- gtwse.exe (PID: 3452)
- gtwse.exe (PID: 812)
- gtwse.exe (PID: 3240)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 356)
- schtasks.exe (PID: 3200)
- schtasks.exe (PID: 2288)
- schtasks.exe (PID: 3180)
- schtasks.exe (PID: 3972)
- schtasks.exe (PID: 320)
- schtasks.exe (PID: 3472)
Changes the autorun value in the registry
- RegAsm.exe (PID: 2484)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- msiexec.exe (PID: 2532)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 2484)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- msiexec.exe (PID: 2532)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Connects to CnC server
- explorer.exe (PID: 276)
FORMBOOK was detected
- msiexec.exe (PID: 2532)
- explorer.exe (PID: 276)
- Firefox.exe (PID: 2428)
Stealing of credential data
- msiexec.exe (PID: 2532)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 276)
Executable content was dropped or overwritten
- iexplore.exe (PID: 4064)
- iexplore.exe (PID: 3576)
- RegAsm.exe (PID: 2484)
- dg1[1].exe (PID: 2332)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
- explorer.exe (PID: 276)
- DllHost.exe (PID: 3132)
Creates files in the user directory
- RegAsm.exe (PID: 2484)
- dg1[1].exe (PID: 2332)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- msiexec.exe (PID: 2532)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Reads the cookies of Mozilla Firefox
- RegAsm.exe (PID: 2484)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Reads the cookies of Google Chrome
- RegAsm.exe (PID: 2484)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Reads Internet Cache Settings
- RegAsm.exe (PID: 2484)
Checks for external IP
- RegAsm.exe (PID: 2484)
- RegAsm.exe (PID: 2768)
- RegAsm.exe (PID: 2628)
- RegAsm.exe (PID: 2860)
- RegAsm.exe (PID: 2792)
Executes scripts
- the[1].exe (PID: 2376)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 2532)
Cleans NTFS data-stream (Zone Identifier)
- dg1[1].exe (PID: 2332)
Executed via Task Scheduler
- gtwse.exe (PID: 3644)
- gtwse.exe (PID: 3452)
- gtwse.exe (PID: 812)
- gtwse.exe (PID: 3240)
Loads DLL from Mozilla Firefox
- msiexec.exe (PID: 2532)
Creates files in the program directory
- DllHost.exe (PID: 3132)
Executed via COM
- DllHost.exe (PID: 3132)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 4064)
Reads Internet Cache Settings
- iexplore.exe (PID: 3576)
- iexplore.exe (PID: 4064)
Changes internet zones settings
- iexplore.exe (PID: 3576)
Application launched itself
- iexplore.exe (PID: 3576)
Manual execution by user
- msiexec.exe (PID: 2532)
Reads the hosts file
- msiexec.exe (PID: 2532)
Creates files in the user directory
- Firefox.exe (PID: 2428)
- iexplore.exe (PID: 3576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
31
Malicious processes
14
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 320 | "schtasks.exe" /query | C:\Windows\system32\schtasks.exe | — | gtwse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | "schtasks.exe" /query | C:\Windows\system32\schtasks.exe | — | g222[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 812 | C:\Users\admin\AppData\Roaming\gtwse.exe | C:\Users\admin\AppData\Roaming\gtwse.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2288 | "schtasks.exe" /query | C:\Windows\system32\schtasks.exe | — | dg1[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\dg1[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\dg1[1].exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2376 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\the[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\the[1].exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2388 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\putty[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\putty[1].exe | — | iexplore.exe | |||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet and Rlogin client Exit code: 0 Version: Release 0.72 (with embedded help) Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | msiexec.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2484 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | g222[1].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 4294967295 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
Total events
1 230
Read events
1 067
Write events
161
Delete events
2
Modification events
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {04BFABF7-DA99-11E9-B86F-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070900040013000400320024005503 | |||
Executable files
16
Suspicious files
84
Text files
51
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9EB5.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9EB6.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9EC7.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9EC8.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAC85.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarAC86.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94308059B57B3142E455B38A6EB92015 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
56
DNS requests
22
Threats
67
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
276 | explorer.exe | GET | — | 208.91.197.27:80 | http://www.makemypalns.com/nx/?pPx=ApT8EAiMFA2+XJLCRmgCZm8rhvVcwq/I/QK9sQO578BDe9Iv1LXHeXrScLYaCIMT5AmOkA==&pB=jliTiHT8W&sql=1 | US | — | — | malicious |
2628 | RegAsm.exe | GET | 200 | 18.214.132.216:80 | http://checkip.amazonaws.com/ | US | text | 13 b | malicious |
276 | explorer.exe | GET | 302 | 54.208.77.124:80 | http://www.worldsbestfathers.com/nx/?pPx=UaeCgaZsVdNoQTzSynKueu2VBZ3WVeazCAxAYjUxIFyArxvRwJX57GVEGlvLNXIYuzpSvQ==&pB=jliTiHT8W&sql=1 | US | html | 309 b | malicious |
276 | explorer.exe | POST | — | 54.208.77.124:80 | http://www.worldsbestfathers.com/nx/ | US | — | — | malicious |
276 | explorer.exe | POST | — | 54.208.77.124:80 | http://www.worldsbestfathers.com/nx/ | US | — | — | malicious |
276 | explorer.exe | POST | — | 217.160.0.29:80 | http://www.forstfex.com/nx/ | DE | — | — | malicious |
276 | explorer.exe | GET | 301 | 104.221.216.171:80 | http://www.jingyimx.com/nx/?pPx=zkugRN2tzGJEhPxBzYlLh0OQ41H1Tm05zd4OlCBLsrvrfIsOaBhkOu+axv+FxM87aN2bUw==&pB=jliTiHT8W | US | html | 158 b | malicious |
276 | explorer.exe | POST | — | 208.91.197.27:80 | http://www.makemypalns.com/nx/ | US | — | — | malicious |
276 | explorer.exe | POST | — | 54.208.77.124:80 | http://www.worldsbestfathers.com/nx/ | US | — | — | malicious |
276 | explorer.exe | POST | — | 217.160.0.29:80 | http://www.forstfex.com/nx/ | DE | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3576 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4064 | iexplore.exe | 23.249.163.172:443 | s321.duckdns.org | ColoCrossing | US | malicious |
4064 | iexplore.exe | 8.248.101.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
2484 | RegAsm.exe | 18.205.71.63:80 | checkip.amazonaws.com | — | US | shared |
2768 | RegAsm.exe | 18.214.132.216:80 | checkip.amazonaws.com | — | US | shared |
2628 | RegAsm.exe | 18.214.132.216:80 | checkip.amazonaws.com | — | US | shared |
276 | explorer.exe | 54.208.77.124:80 | www.worldsbestfathers.com | Amazon.com, Inc. | US | malicious |
276 | explorer.exe | 104.221.216.171:80 | www.jingyimx.com | eSited Solutions | US | malicious |
2860 | RegAsm.exe | 18.205.71.63:80 | checkip.amazonaws.com | — | US | shared |
276 | explorer.exe | 217.160.0.29:80 | www.forstfex.com | 1&1 Internet SE | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s321.duckdns.org |
| malicious |
www.bing.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
checkip.amazonaws.com |
| malicious |
www.thatcraftychick.com |
| unknown |
www.jingyimx.com |
| malicious |
www.www719234.com |
| unknown |
www.worldsbestfathers.com |
| malicious |
www.forstfex.com |
| malicious |
www.873dwo.info |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2484 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
2768 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
2628 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
30 ETPRO signatures available at the full report