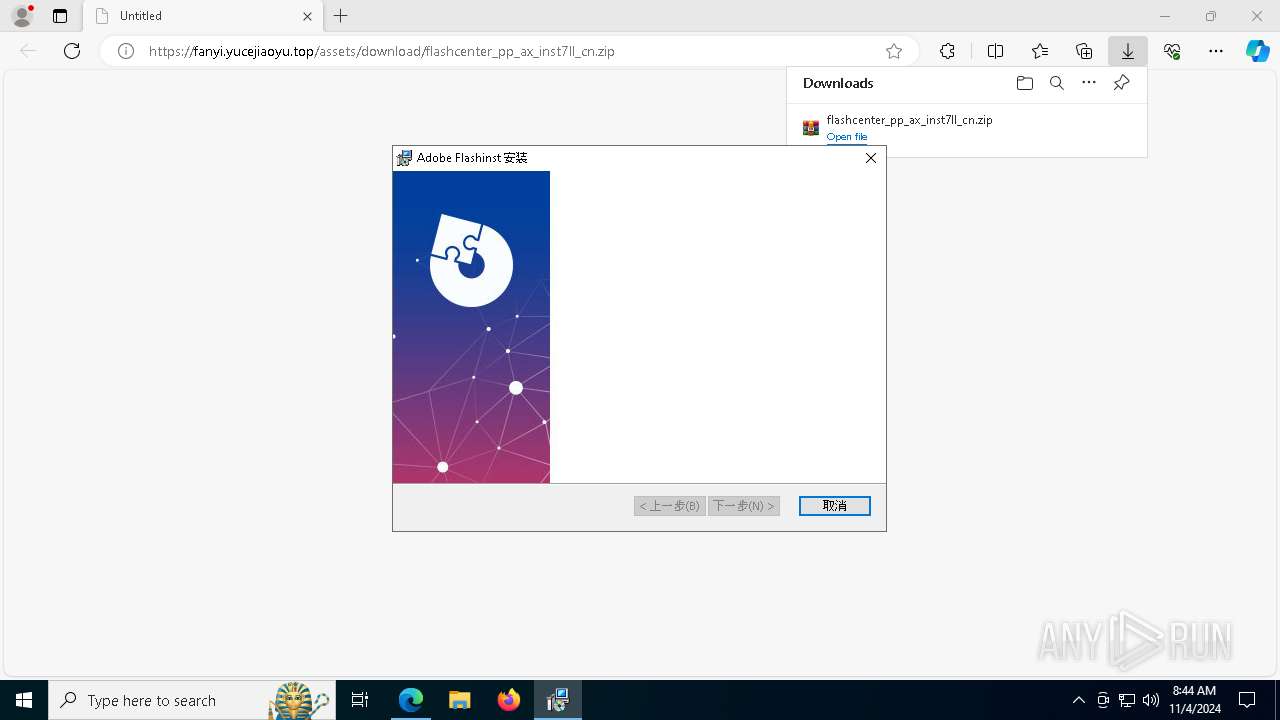
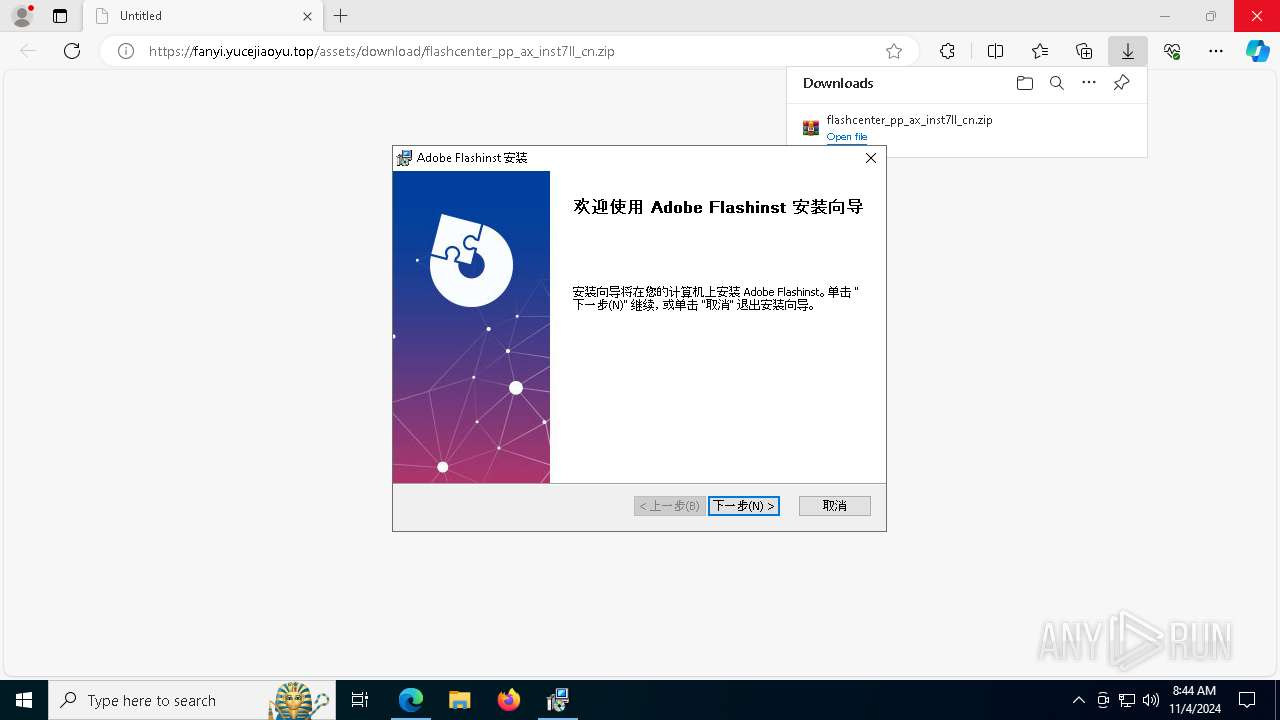
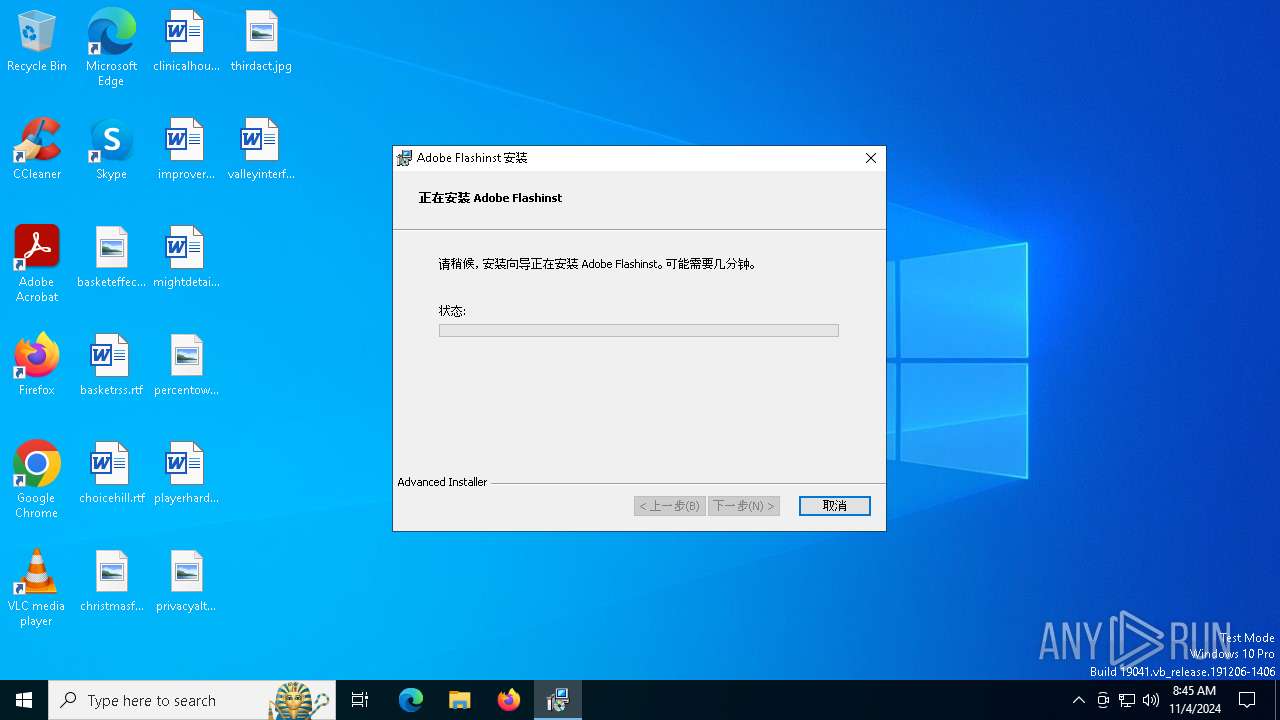
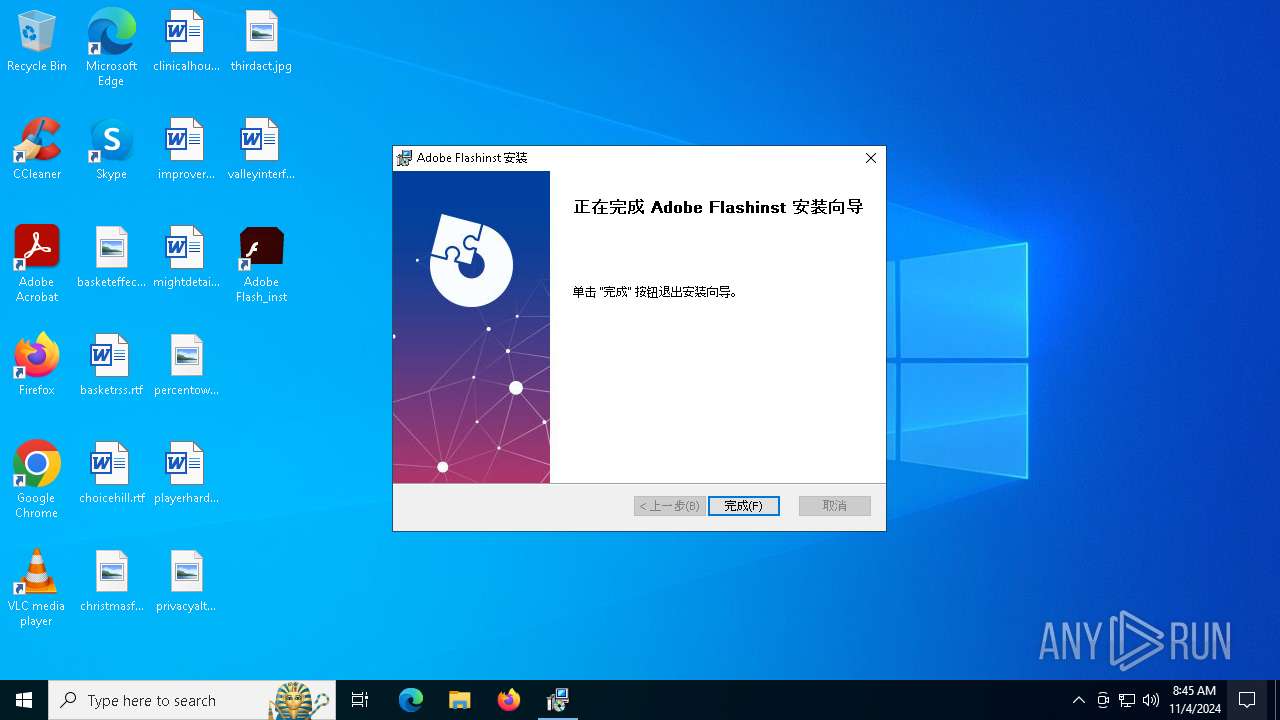
| URL: | https://fanyi.yucejiaoyu.top/assets/download/flashcenter_pp_ax_inst7ll_cn.zip |
| Full analysis: | https://app.any.run/tasks/5862d169-7237-4778-8ed5-37bb6c7bf190 |
| Verdict: | Malicious activity |
| Threats: | Gh0st RAT is a malware with advanced trojan functionality that enables attackers to establish full control over the victim’s system. The spying capabilities of Gh0st RAT made it a go-to tool for numerous criminal groups in high-profile attacks against government and corporate organizations. The most common vector of attack involving this malware begins with spam and phishing emails. |
| Analysis date: | November 04, 2024, 08:43:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 53CE84A2FD2307D99CD5757661A58B86 |
| SHA1: | 23E2CBEE89AF1CC7964B4D1BB1C2C771C96EAB1B |
| SHA256: | E733920241D2581F18D13E029CB6864B3369CF4180274B7BCDB59E81314673E4 |
| SSDEEP: | 3:N8uZBOqBLpAapy4L4:2YB1E |
MALICIOUS
Adds path to the Windows Defender exclusion list
- msiexec.exe (PID: 3900)
- TaskLoad.exe (PID: 7036)
Changes powershell execution policy (Unrestricted)
- TaskLoad.exe (PID: 7036)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 4584)
Process drops legitimate windows executable
- msiexec.exe (PID: 7352)
- TaskLoad.exe (PID: 7036)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 3900)
- TaskLoad.exe (PID: 7036)
Script adds exclusion path to Windows Defender
- msiexec.exe (PID: 3900)
- TaskLoad.exe (PID: 7036)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 5564)
- TaskLoad.exe (PID: 7036)
- TaskLoad.exe (PID: 6708)
- powershell.exe (PID: 5512)
Starts itself from another location
- WsTaskLoad.exe (PID: 7916)
Application launched itself
- TaskLoad.exe (PID: 7036)
The process drops C-runtime libraries
- TaskLoad.exe (PID: 7036)
Executable content was dropped or overwritten
- TaskLoad.exe (PID: 7036)
The process executes via Task Scheduler
- fUsKbQQM.exe (PID: 7364)
- fUsKbQQM.exe (PID: 7288)
INFO
Executable content was dropped or overwritten
- msiexec.exe (PID: 7352)
- msiexec.exe (PID: 7292)
- msiexec.exe (PID: 7868)
- msiexec.exe (PID: 3900)
- msedge.exe (PID: 1248)
Manages system restore points
- SrTasks.exe (PID: 6712)
Application launched itself
- msedge.exe (PID: 7444)
- msedge.exe (PID: 5172)
The process uses the downloaded file
- iexplore.exe (PID: 4076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
241
Monitored processes
95
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\WINDOWS\System32\WindowsPowershell\v1.0\Powershell.exe" -Command Set-ExecutionPolicy Unrestricted | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | TaskLoad.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x29c,0x2a0,0x2a4,0x298,0x28c,0x7ffbc23f5fd8,0x7ffbc23f5fe4,0x7ffbc23f5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4132 --field-trial-handle=2484,i,7187579551381510141,6834774084811408686,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5232 --field-trial-handle=2412,i,8889713318776306060,4367380363853336802,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1236 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4044 --field-trial-handle=2412,i,8889713318776306060,4367380363853336802,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5624 --field-trial-handle=2412,i,8889713318776306060,4367380363853336802,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1396 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5352 --field-trial-handle=2412,i,8889713318776306060,4367380363853336802,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2084 | C:\Windows\syswow64\MsiExec.exe -Embedding 3C42094522B5D1E19057AF28F866748A | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5156 --field-trial-handle=2412,i,8889713318776306060,4367380363853336802,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
Total events
12 559
Read events
12 478
Write events
72
Delete events
9
Modification events
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (5172) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5172) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5172) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5172) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
143
Suspicious files
383
Text files
168
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF8e095.TMP | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF8e150.TMP | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF8e170.TMP | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF8e170.TMP | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF8e150.TMP | — | |
MD5:— | SHA256:— | |||
| 5172 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
88
DNS requests
75
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 184.28.66.24:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6088 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6200 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6128 | SIHClient.exe | GET | 200 | 184.28.66.24:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6128 | SIHClient.exe | GET | 200 | 184.28.66.24:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8100 | svchost.exe | HEAD | 200 | 2.16.164.89:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1730976752&P2=404&P3=2&P4=SU5Ic12xrGqC2%2fHbnAlJnmlyvm2hCwxe9796q7z%2b6%2bCSRTpIqX44XL9hobxevPmgN9E9SZDfo0rJ62l8MZtcHg%3d%3d | unknown | — | — | whitelisted |
8100 | svchost.exe | GET | 206 | 2.16.164.89:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1730976752&P2=404&P3=2&P4=SU5Ic12xrGqC2%2fHbnAlJnmlyvm2hCwxe9796q7z%2b6%2bCSRTpIqX44XL9hobxevPmgN9E9SZDfo0rJ62l8MZtcHg%3d%3d | unknown | — | — | whitelisted |
8100 | svchost.exe | GET | 206 | 2.16.164.89:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1730976752&P2=404&P3=2&P4=SU5Ic12xrGqC2%2fHbnAlJnmlyvm2hCwxe9796q7z%2b6%2bCSRTpIqX44XL9hobxevPmgN9E9SZDfo0rJ62l8MZtcHg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6308 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.183:443 | — | Akamai International B.V. | GB | unknown |
5172 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2692 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2692 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2692 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
fanyi.yucejiaoyu.top |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Gh0stRat |
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Gh0stRat |