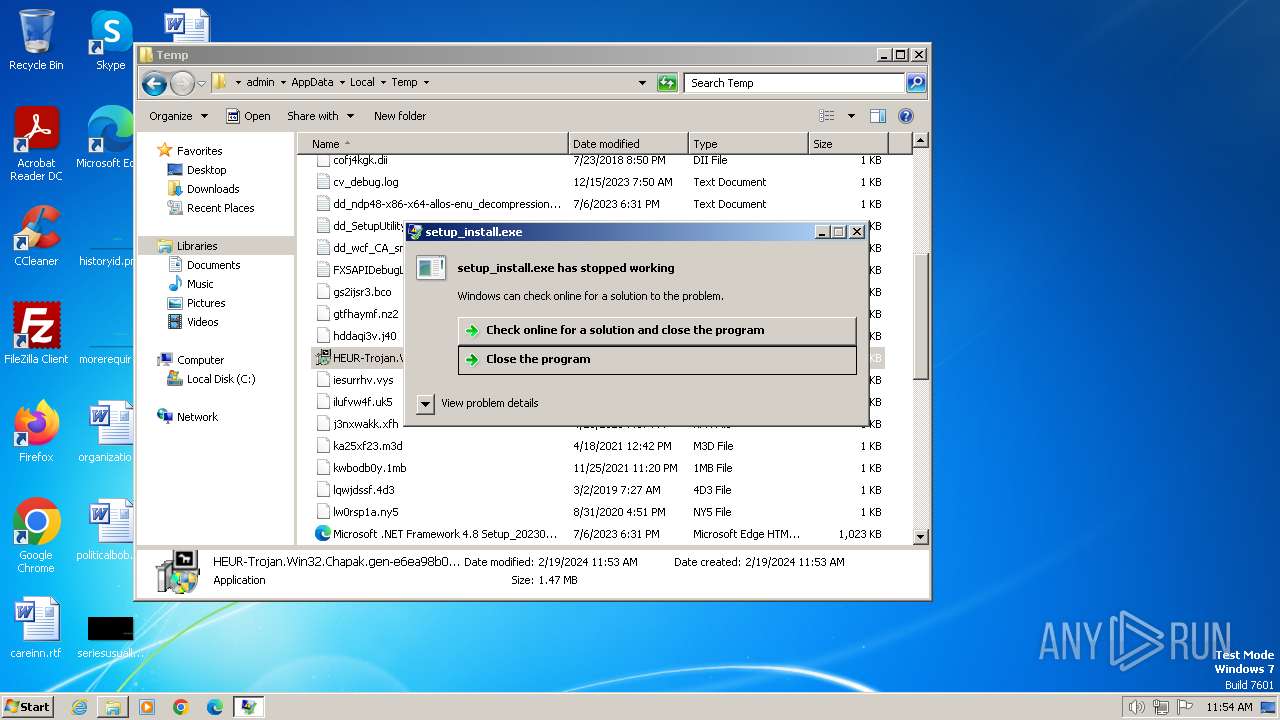
| File name: | HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe |
| Full analysis: | https://app.any.run/tasks/c53db868-4ac8-4ef7-9062-42944edb4b2b |
| Verdict: | Malicious activity |
| Threats: | PrivateLoader is a malware family that is specifically created to infect computer systems and drop additional malicious programs. It operates using a pay-per-install business model, which means that the individuals behind it are paid for each instance of successful deployment of different types of harmful programs, including trojans, stealers, and other ransomware. |
| Analysis date: | February 19, 2024, 11:53:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 269D7E74E4B21A2FC0E66907C77FC0BC |
| SHA1: | FC09525A2F93BF089D0B02C5220E7EE452E64747 |
| SHA256: | E6EA98B046B11A35EFA0AC1243F6190FF4D4247A35784E65A9FEAAF4918AE779 |
| SSDEEP: | 49152:bsM2FT2gKUQyBStGWDAj/nhVSo5/+XdbfZgEh+STw7ZOjaw9ZCRMX8MkXw8hZHMc:bYFT2hRyBkGCK/h4o5WXdTOEh+6w7rRN |
MALICIOUS
Drops the executable file immediately after the start
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
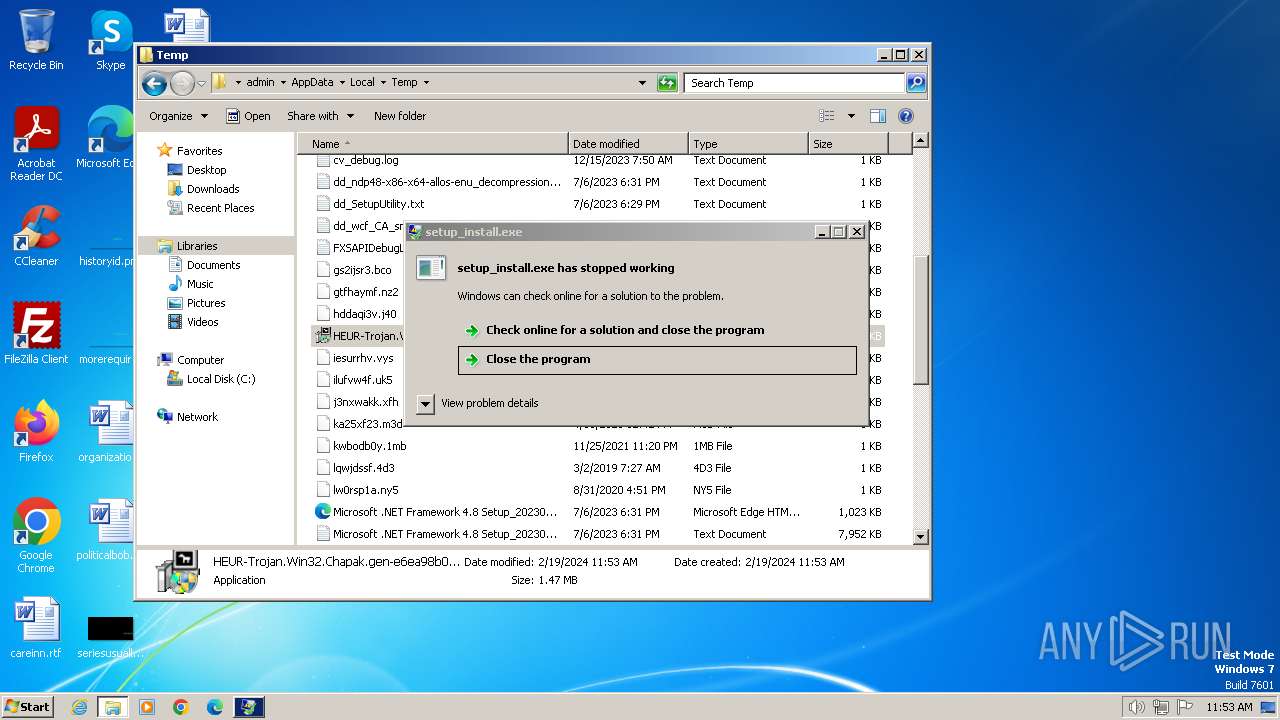
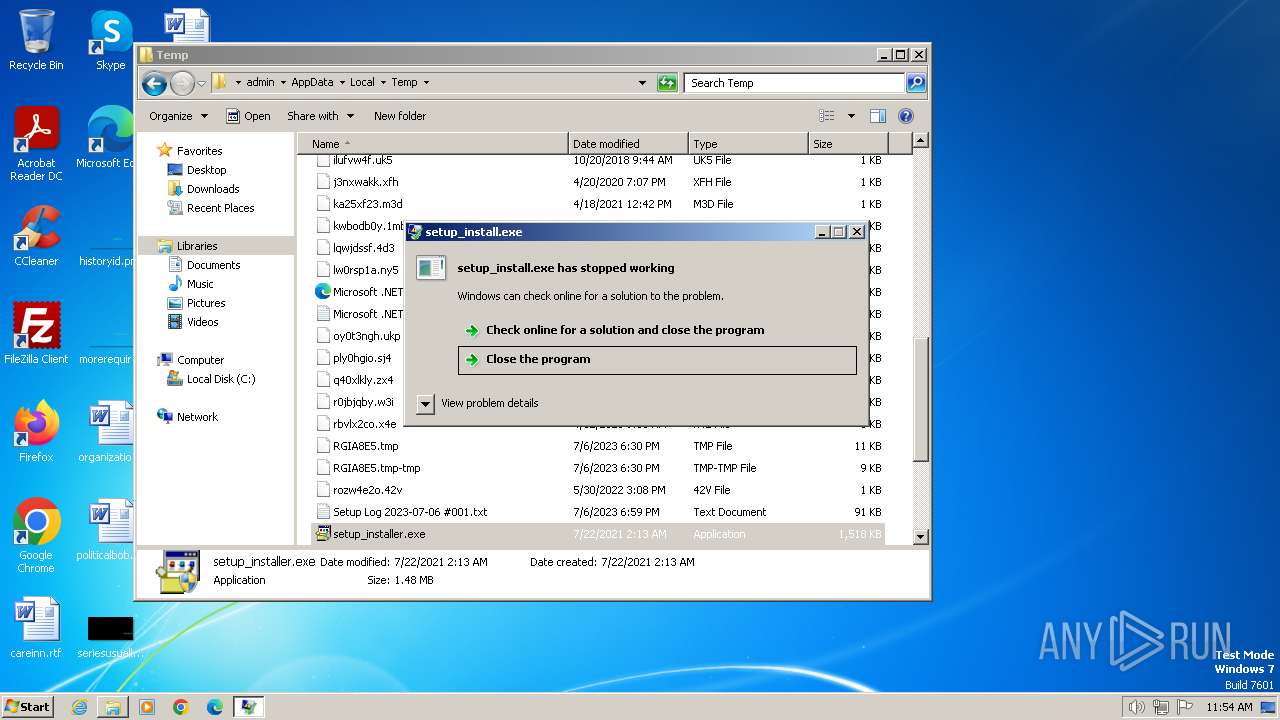
- setup_installer.exe (PID: 2848)
- setup_install.exe (PID: 3464)
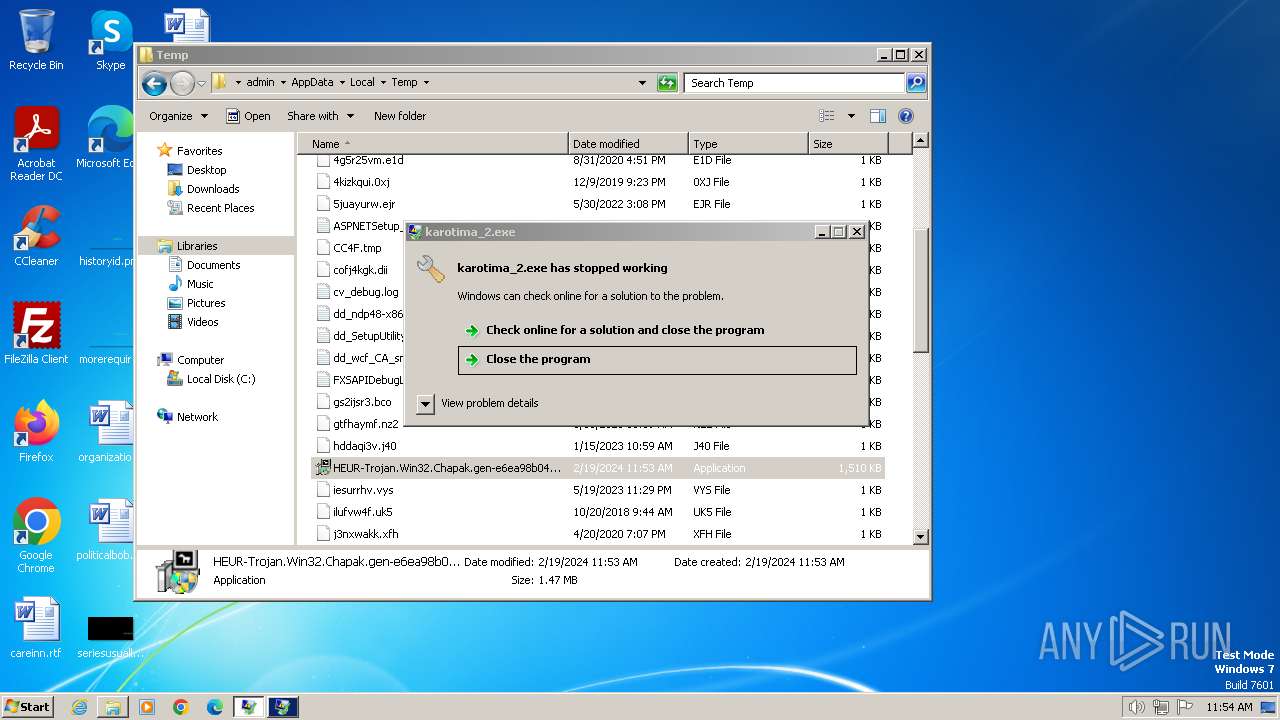
- karotima_2.exe (PID: 3212)
- setup_installer.exe (PID: 3088)
- setup_install.exe (PID: 1792)
- karotima_2.exe (PID: 3556)
- setup_installer.exe (PID: 920)
- setup_install.exe (PID: 3260)
- setup_installer.exe (PID: 3248)
- setup_install.exe (PID: 1288)
- karotima_2.exe (PID: 3016)
- setup_installer.exe (PID: 4052)
- setup_install.exe (PID: 3460)
- setup_installer.exe (PID: 3068)
- setup_install.exe (PID: 2100)
- karotima_2.exe (PID: 3276)
- karotima_2.exe (PID: 880)
- setup_install.exe (PID: 2584)
- setup_installer.exe (PID: 2396)
- karotima_2.exe (PID: 3192)
PRIVATELOADER has been detected (YARA)
- karotima_1.exe (PID: 2624)
- karotima_1.exe (PID: 480)
- karotima_1.exe (PID: 3272)
- karotima_1.exe (PID: 1692)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
Reads security settings of Internet Explorer
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
- setup_installer.exe (PID: 2848)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 712)
- setup_installer.exe (PID: 3088)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2516)
- setup_installer.exe (PID: 920)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2268)
- setup_installer.exe (PID: 3248)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3652)
- setup_installer.exe (PID: 4052)
- setup_installer.exe (PID: 3068)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 1584)
- setup_installer.exe (PID: 2396)
Executable content was dropped or overwritten
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
- setup_installer.exe (PID: 2848)
- setup_install.exe (PID: 3464)
- karotima_2.exe (PID: 3212)
- setup_installer.exe (PID: 3088)
- setup_install.exe (PID: 1792)
- karotima_2.exe (PID: 3556)
- setup_installer.exe (PID: 920)
- setup_install.exe (PID: 3260)
- setup_installer.exe (PID: 3248)
- setup_install.exe (PID: 1288)
- setup_installer.exe (PID: 4052)
- karotima_2.exe (PID: 3016)
- setup_install.exe (PID: 3460)
- karotima_2.exe (PID: 3276)
- setup_installer.exe (PID: 3068)
- setup_install.exe (PID: 2100)
- karotima_2.exe (PID: 880)
- setup_install.exe (PID: 2584)
- setup_installer.exe (PID: 2396)
- karotima_2.exe (PID: 3192)
Reads the Internet Settings
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
- setup_installer.exe (PID: 2848)
- karotima_1.exe (PID: 2624)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 712)
- setup_installer.exe (PID: 3088)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2516)
- setup_installer.exe (PID: 920)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2268)
- setup_installer.exe (PID: 3248)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3652)
- setup_installer.exe (PID: 4052)
- setup_installer.exe (PID: 3068)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 1584)
- setup_installer.exe (PID: 2396)
Starts CMD.EXE for commands execution
- setup_install.exe (PID: 3464)
- setup_install.exe (PID: 1792)
- setup_install.exe (PID: 3260)
- setup_install.exe (PID: 1288)
- setup_install.exe (PID: 3460)
- setup_install.exe (PID: 2100)
- setup_install.exe (PID: 2584)
The executable file from the user directory is run by the CMD process
- karotima_1.exe (PID: 2624)
- karotima_2.exe (PID: 3212)
- karotima_2.exe (PID: 3556)
- karotima_1.exe (PID: 480)
- karotima_1.exe (PID: 3272)
- karotima_2.exe (PID: 3140)
- karotima_1.exe (PID: 3024)
- karotima_2.exe (PID: 3016)
- karotima_2.exe (PID: 3276)
- karotima_1.exe (PID: 1692)
- karotima_2.exe (PID: 880)
- karotima_1.exe (PID: 1340)
- karotima_2.exe (PID: 3192)
- karotima_1.exe (PID: 2936)
Reads settings of System Certificates
- karotima_1.exe (PID: 2624)
- karotima_1.exe (PID: 480)
- karotima_1.exe (PID: 3272)
- karotima_1.exe (PID: 3024)
- karotima_1.exe (PID: 1692)
- karotima_1.exe (PID: 1340)
- karotima_1.exe (PID: 2936)
Adds/modifies Windows certificates
- karotima_1.exe (PID: 2624)
Checks for external IP
- karotima_1.exe (PID: 2624)
- karotima_1.exe (PID: 480)
- karotima_1.exe (PID: 3272)
- karotima_1.exe (PID: 3024)
- karotima_1.exe (PID: 1692)
- karotima_1.exe (PID: 1340)
- karotima_1.exe (PID: 2936)
Process drops legitimate windows executable
- karotima_2.exe (PID: 3212)
- karotima_2.exe (PID: 3556)
- karotima_2.exe (PID: 3016)
- karotima_2.exe (PID: 3276)
- karotima_2.exe (PID: 880)
- karotima_2.exe (PID: 3192)
INFO
Checks supported languages
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
- setup_installer.exe (PID: 2848)
- setup_install.exe (PID: 3464)
- karotima_2.exe (PID: 3212)
- karotima_1.exe (PID: 2624)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 712)
- setup_installer.exe (PID: 3088)
- setup_install.exe (PID: 1792)
- karotima_2.exe (PID: 3556)
- karotima_1.exe (PID: 480)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2516)
- setup_installer.exe (PID: 920)
- setup_install.exe (PID: 3260)
- karotima_2.exe (PID: 3140)
- karotima_1.exe (PID: 3272)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2268)
- setup_installer.exe (PID: 3248)
- setup_install.exe (PID: 1288)
- karotima_1.exe (PID: 3024)
- karotima_2.exe (PID: 3016)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3652)
- setup_installer.exe (PID: 4052)
- setup_install.exe (PID: 3460)
- karotima_2.exe (PID: 3276)
- karotima_1.exe (PID: 1692)
- setup_installer.exe (PID: 3068)
- setup_install.exe (PID: 2100)
- karotima_1.exe (PID: 1340)
- karotima_2.exe (PID: 880)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 1584)
- setup_installer.exe (PID: 2396)
- setup_install.exe (PID: 2584)
- karotima_2.exe (PID: 3192)
- karotima_1.exe (PID: 2936)
Reads the computer name
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
- setup_installer.exe (PID: 2848)
- setup_install.exe (PID: 3464)
- karotima_1.exe (PID: 2624)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 712)
- setup_installer.exe (PID: 3088)
- setup_install.exe (PID: 1792)
- karotima_1.exe (PID: 480)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2516)
- setup_installer.exe (PID: 920)
- setup_install.exe (PID: 3260)
- karotima_1.exe (PID: 3272)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2268)
- setup_installer.exe (PID: 3248)
- setup_install.exe (PID: 1288)
- karotima_1.exe (PID: 3024)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3652)
- setup_installer.exe (PID: 4052)
- setup_install.exe (PID: 3460)
- karotima_1.exe (PID: 1692)
- setup_installer.exe (PID: 3068)
- setup_install.exe (PID: 2100)
- karotima_1.exe (PID: 1340)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 1584)
- setup_installer.exe (PID: 2396)
- setup_install.exe (PID: 2584)
- karotima_1.exe (PID: 2936)
Create files in a temporary directory
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3216)
- setup_installer.exe (PID: 2848)
- karotima_2.exe (PID: 3212)
- karotima_1.exe (PID: 2624)
- setup_installer.exe (PID: 3088)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 712)
- karotima_2.exe (PID: 3556)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2516)
- setup_installer.exe (PID: 920)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2268)
- setup_installer.exe (PID: 3248)
- karotima_2.exe (PID: 3016)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3652)
- setup_installer.exe (PID: 4052)
- karotima_2.exe (PID: 3276)
- setup_installer.exe (PID: 3068)
- karotima_2.exe (PID: 880)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 1584)
- setup_installer.exe (PID: 2396)
- karotima_2.exe (PID: 3192)
Reads the software policy settings
- karotima_1.exe (PID: 2624)
- karotima_1.exe (PID: 480)
- karotima_1.exe (PID: 3272)
- karotima_1.exe (PID: 3024)
- karotima_1.exe (PID: 1692)
- karotima_1.exe (PID: 1340)
- karotima_1.exe (PID: 2936)
Manual execution by a user
- explorer.exe (PID: 1348)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 712)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2516)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 984)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 2268)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 3652)
- setup_installer.exe (PID: 3068)
- HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe (PID: 1584)
Reads the machine GUID from the registry
- karotima_1.exe (PID: 2624)
- karotima_1.exe (PID: 480)
- karotima_1.exe (PID: 3272)
- karotima_1.exe (PID: 3024)
- karotima_1.exe (PID: 1692)
- karotima_1.exe (PID: 1340)
- karotima_1.exe (PID: 2936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
PrivateLoader
(PID) Process(2624) karotima_1.exe
C2 (2)http://wfsdragon.ru/api/setStats.php
37.0.11.41
Attributes
Payload (2)http://37.0.8.235/proxies.txt
http://136.144.41.201/server.txt
Strings (288)CryptAcquireContextA
Advapi32.dll
Crypto++ RNG
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
http://37.0.8.235/proxies.txt
:1080
http://136.144.41.201/server.txt
HOST:
http://wfsdragon.ru/api/setStats.php
37.0.11.41
links
extensions
wininet.dll
https://
SetIncrement|ColdWallet
SetIncrement|BrowserWallet
SetIncrement|CryptoWallet
GetCryptoSleeping
SetIncrement|NoCryptoWallet
net_country_code
os_country_code
browsers
Chrome:
Edge:
ip_country
AddExtensionStat|
AddLoggerStat|
SetIncrement|ww_starts
false
iplis.ru/1S3fd7.mp3
iplis.ru/1G8Fx7.mp3
iplis.ru/1pRXr7.txt
iplis.ru/1BV4j7.mp4
yobit.net
yobit.io
zb.com
binance.com
huobi.com
hitbtc.com
bitfinex.com
kraken.com
bitstamp.net
bittrex.com
gate.io
exmo.com
bitflyer.com
poloniex.com
kucoin.com
coinone.co.kr
livecoin.net
mercatox.com
localbitcoins.com
korbit.co.kr
bitmex.com
cryptobridge.freshdesk.com
volabit.com
tradeogre.com
blockchain.com
bitkub.com
uphold.com
wallet.uphold.com
login.blockchain.com
tidex.com
coinbase.com
coinome.com
bitso.com
coinpayments.net
luno.com
coinexchange.io
bitmax.io
btc-alpha.com
bitbank.cc
independentreserve.com
bitmart.com
cex.io
cryptopia.co.nz
cryptonator.com
advcash.com
my.dogechain.info
spectrocoin.com
exir.io
exir.tech
coinbene.com
bitforex.com
gopax.co.kr
catex.io
vindax.com
coineal.com
maicoin.com
finexbox.com
etherflyer.com
bx.in.th
bitopro.com
lbank.info
citex.co.kr
coinzo.com
atomars.com
coinfinit.com
bitker.com
btc-trade.com.ua
dobitrade.com
btcexa.com
satowallet.com
cpdax.com
trade.io
btcnext.io
exmarkets.com
localtrade.cc
btc-exchange.com
chaoex.com
jex.com
therocktrading.com
gdac.com
southxchange.com
tokens.net
fexpro.net
btcbox.co.jp
coinmex.com
cryptology.com
kuna.io
cointiger.com
cashierest.com
liquid.com
coinbit.co.kr
mxc.com
bilaxy.com
coinall.com
coindeal.com
omgfin.com
stex.com
oceanex.pro
bithumb.com
ftx.com
shortex.net
coin.z.com
fcoin.com
fatbtc.com
tokenize.exchange
simex.global
instantbitex.com
btcmarkets.net
SOFTWARE\Google\Chrome\PreferenceMACs
\Google\Chrome\User Data\
\Login Data
SOFTWARE\Microsoft\Edge\PreferenceMACs
\Microsoft\Edge\User Data\
SOFTWARE\BraveSoftware\Brave-Browser\PreferenceMACs
\BraveSoftware\Brave-Browser\User Data\
SOFTWARE\CryptoTab Browser\PreferenceMACs
\CryptoTab Browser\User Data\
\Roaming
\Opera Software\Opera Stable
\atomic
\Atomic Wallet
\com.liberty.jaxx
\Electrum
\Exodus
\MultiDoge
\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
\Microsoft\Edge\Application
(x86)\Microsoft\Edge\Application
SOFTWARE\Microsoft\Edge\BLBeacon
version
\Secure Preferences
filter_browsers
browser
use_open_browser
settings
install_time
\Extensions\
\u003C
protection
extensions.settings.
super_mac
msedge.exe
\extensions.settings
SOFTWARE\Microsoft\Edge\PreferenceMACs\
\msedge.exe
\Google\Chrome\Application
(x86)\Google\Chrome\Application
SOFTWARE\Google\Chrome\BLBeacon
\resources.pak
chrome
chrome.exe
SOFTWARE\Google\Chrome\PreferenceMACs\
\chrome.exe
Guest Profile
System Profile
Error!
ext_url
cfg_url
data=
/base/api/getData.php
Windows Server 2016
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008 R2
Windows Server 2008
Windows Server
Windows 10
Windows 8.1
Windows 8
Windows 7
Windows Vista
Windows XP
SOFTWARE\Policies\Microsoft\Windows Defender
DisableAntiSpyware
DisableRoutinelyTakingAction
SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
DisableBehaviorMonitoring
DisableOnAccessProtection
DisableScanOnRealtimeEnable
DisableRealtimeMonitoring
DisableIOAVProtection
DisableRawWriteNotification
GetComputerNameA
VerSetConditionMask
VerifyVersionInfoW
GetGeoInfoA
GetCurrentProcess
GetVersionExA
MultiByteToWideChar
WideCharToMultiByte
User32.dll
CharToOemA
IsWow64Process
GetModuleHandleA
LoadLibraryA
SetPriorityClass
Sleep
GetTempPathA
CreateProcessA
GetFileAttributesA
CreateDirectoryA
CreateThread
CloseHandle
VirtualAlloc
VirtualFree
OpenProcess
TerminateProcess
GetUserGeoID
ntdll.dll
NtQuerySystemInformation
RtlGetVersion
Shell32.dll
ShellExecuteA
SHGetFolderPathA
RegOpenKeyExA
RegSetValueExA
RegCloseKey
RegCreateKeyExA
RegDeleteKeyA
RegDeleteValueA
RegQueryValueExA
RegEnumKeyExA
ConvertSidToStringSidA
LookupAccountNameA
WINHTTP.dll
http://
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
(PID) Process(480) karotima_1.exe
C2 (2)http://wfsdragon.ru/api/setStats.php
37.0.11.41
Attributes
Payload (2)http://37.0.8.235/proxies.txt
http://136.144.41.201/server.txt
Strings (288)CryptAcquireContextA
Advapi32.dll
Crypto++ RNG
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
http://37.0.8.235/proxies.txt
:1080
http://136.144.41.201/server.txt
HOST:
http://wfsdragon.ru/api/setStats.php
37.0.11.41
links
extensions
wininet.dll
https://
SetIncrement|ColdWallet
SetIncrement|BrowserWallet
SetIncrement|CryptoWallet
GetCryptoSleeping
SetIncrement|NoCryptoWallet
net_country_code
os_country_code
browsers
Chrome:
Edge:
ip_country
AddExtensionStat|
AddLoggerStat|
SetIncrement|ww_starts
false
iplis.ru/1S3fd7.mp3
iplis.ru/1G8Fx7.mp3
iplis.ru/1pRXr7.txt
iplis.ru/1BV4j7.mp4
yobit.net
yobit.io
zb.com
binance.com
huobi.com
hitbtc.com
bitfinex.com
kraken.com
bitstamp.net
bittrex.com
gate.io
exmo.com
bitflyer.com
poloniex.com
kucoin.com
coinone.co.kr
livecoin.net
mercatox.com
localbitcoins.com
korbit.co.kr
bitmex.com
cryptobridge.freshdesk.com
volabit.com
tradeogre.com
blockchain.com
bitkub.com
uphold.com
wallet.uphold.com
login.blockchain.com
tidex.com
coinbase.com
coinome.com
bitso.com
coinpayments.net
luno.com
coinexchange.io
bitmax.io
btc-alpha.com
bitbank.cc
independentreserve.com
bitmart.com
cex.io
cryptopia.co.nz
cryptonator.com
advcash.com
my.dogechain.info
spectrocoin.com
exir.io
exir.tech
coinbene.com
bitforex.com
gopax.co.kr
catex.io
vindax.com
coineal.com
maicoin.com
finexbox.com
etherflyer.com
bx.in.th
bitopro.com
lbank.info
citex.co.kr
coinzo.com
atomars.com
coinfinit.com
bitker.com
btc-trade.com.ua
dobitrade.com
btcexa.com
satowallet.com
cpdax.com
trade.io
btcnext.io
exmarkets.com
localtrade.cc
btc-exchange.com
chaoex.com
jex.com
therocktrading.com
gdac.com
southxchange.com
tokens.net
fexpro.net
btcbox.co.jp
coinmex.com
cryptology.com
kuna.io
cointiger.com
cashierest.com
liquid.com
coinbit.co.kr
mxc.com
bilaxy.com
coinall.com
coindeal.com
omgfin.com
stex.com
oceanex.pro
bithumb.com
ftx.com
shortex.net
coin.z.com
fcoin.com
fatbtc.com
tokenize.exchange
simex.global
instantbitex.com
btcmarkets.net
SOFTWARE\Google\Chrome\PreferenceMACs
\Google\Chrome\User Data\
\Login Data
SOFTWARE\Microsoft\Edge\PreferenceMACs
\Microsoft\Edge\User Data\
SOFTWARE\BraveSoftware\Brave-Browser\PreferenceMACs
\BraveSoftware\Brave-Browser\User Data\
SOFTWARE\CryptoTab Browser\PreferenceMACs
\CryptoTab Browser\User Data\
\Roaming
\Opera Software\Opera Stable
\atomic
\Atomic Wallet
\com.liberty.jaxx
\Electrum
\Exodus
\MultiDoge
\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
\Microsoft\Edge\Application
(x86)\Microsoft\Edge\Application
SOFTWARE\Microsoft\Edge\BLBeacon
version
\Secure Preferences
filter_browsers
browser
use_open_browser
settings
install_time
\Extensions\
\u003C
protection
extensions.settings.
super_mac
msedge.exe
\extensions.settings
SOFTWARE\Microsoft\Edge\PreferenceMACs\
\msedge.exe
\Google\Chrome\Application
(x86)\Google\Chrome\Application
SOFTWARE\Google\Chrome\BLBeacon
\resources.pak
chrome
chrome.exe
SOFTWARE\Google\Chrome\PreferenceMACs\
\chrome.exe
Guest Profile
System Profile
Error!
ext_url
cfg_url
data=
/base/api/getData.php
Windows Server 2016
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008 R2
Windows Server 2008
Windows Server
Windows 10
Windows 8.1
Windows 8
Windows 7
Windows Vista
Windows XP
SOFTWARE\Policies\Microsoft\Windows Defender
DisableAntiSpyware
DisableRoutinelyTakingAction
SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
DisableBehaviorMonitoring
DisableOnAccessProtection
DisableScanOnRealtimeEnable
DisableRealtimeMonitoring
DisableIOAVProtection
DisableRawWriteNotification
GetComputerNameA
VerSetConditionMask
VerifyVersionInfoW
GetGeoInfoA
GetCurrentProcess
GetVersionExA
MultiByteToWideChar
WideCharToMultiByte
User32.dll
CharToOemA
IsWow64Process
GetModuleHandleA
LoadLibraryA
SetPriorityClass
Sleep
GetTempPathA
CreateProcessA
GetFileAttributesA
CreateDirectoryA
CreateThread
CloseHandle
VirtualAlloc
VirtualFree
OpenProcess
TerminateProcess
GetUserGeoID
ntdll.dll
NtQuerySystemInformation
RtlGetVersion
Shell32.dll
ShellExecuteA
SHGetFolderPathA
RegOpenKeyExA
RegSetValueExA
RegCloseKey
RegCreateKeyExA
RegDeleteKeyA
RegDeleteValueA
RegQueryValueExA
RegEnumKeyExA
ConvertSidToStringSidA
LookupAccountNameA
WINHTTP.dll
http://
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
(PID) Process(3272) karotima_1.exe
C2 (2)http://wfsdragon.ru/api/setStats.php
37.0.11.41
Attributes
Payload (2)http://37.0.8.235/proxies.txt
http://136.144.41.201/server.txt
Strings (288)CryptAcquireContextA
Advapi32.dll
Crypto++ RNG
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
http://37.0.8.235/proxies.txt
:1080
http://136.144.41.201/server.txt
HOST:
http://wfsdragon.ru/api/setStats.php
37.0.11.41
links
extensions
wininet.dll
https://
SetIncrement|ColdWallet
SetIncrement|BrowserWallet
SetIncrement|CryptoWallet
GetCryptoSleeping
SetIncrement|NoCryptoWallet
net_country_code
os_country_code
browsers
Chrome:
Edge:
ip_country
AddExtensionStat|
AddLoggerStat|
SetIncrement|ww_starts
false
iplis.ru/1S3fd7.mp3
iplis.ru/1G8Fx7.mp3
iplis.ru/1pRXr7.txt
iplis.ru/1BV4j7.mp4
yobit.net
yobit.io
zb.com
binance.com
huobi.com
hitbtc.com
bitfinex.com
kraken.com
bitstamp.net
bittrex.com
gate.io
exmo.com
bitflyer.com
poloniex.com
kucoin.com
coinone.co.kr
livecoin.net
mercatox.com
localbitcoins.com
korbit.co.kr
bitmex.com
cryptobridge.freshdesk.com
volabit.com
tradeogre.com
blockchain.com
bitkub.com
uphold.com
wallet.uphold.com
login.blockchain.com
tidex.com
coinbase.com
coinome.com
bitso.com
coinpayments.net
luno.com
coinexchange.io
bitmax.io
btc-alpha.com
bitbank.cc
independentreserve.com
bitmart.com
cex.io
cryptopia.co.nz
cryptonator.com
advcash.com
my.dogechain.info
spectrocoin.com
exir.io
exir.tech
coinbene.com
bitforex.com
gopax.co.kr
catex.io
vindax.com
coineal.com
maicoin.com
finexbox.com
etherflyer.com
bx.in.th
bitopro.com
lbank.info
citex.co.kr
coinzo.com
atomars.com
coinfinit.com
bitker.com
btc-trade.com.ua
dobitrade.com
btcexa.com
satowallet.com
cpdax.com
trade.io
btcnext.io
exmarkets.com
localtrade.cc
btc-exchange.com
chaoex.com
jex.com
therocktrading.com
gdac.com
southxchange.com
tokens.net
fexpro.net
btcbox.co.jp
coinmex.com
cryptology.com
kuna.io
cointiger.com
cashierest.com
liquid.com
coinbit.co.kr
mxc.com
bilaxy.com
coinall.com
coindeal.com
omgfin.com
stex.com
oceanex.pro
bithumb.com
ftx.com
shortex.net
coin.z.com
fcoin.com
fatbtc.com
tokenize.exchange
simex.global
instantbitex.com
btcmarkets.net
SOFTWARE\Google\Chrome\PreferenceMACs
\Google\Chrome\User Data\
\Login Data
SOFTWARE\Microsoft\Edge\PreferenceMACs
\Microsoft\Edge\User Data\
SOFTWARE\BraveSoftware\Brave-Browser\PreferenceMACs
\BraveSoftware\Brave-Browser\User Data\
SOFTWARE\CryptoTab Browser\PreferenceMACs
\CryptoTab Browser\User Data\
\Roaming
\Opera Software\Opera Stable
\atomic
\Atomic Wallet
\com.liberty.jaxx
\Electrum
\Exodus
\MultiDoge
\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
\Microsoft\Edge\Application
(x86)\Microsoft\Edge\Application
SOFTWARE\Microsoft\Edge\BLBeacon
version
\Secure Preferences
filter_browsers
browser
use_open_browser
settings
install_time
\Extensions\
\u003C
protection
extensions.settings.
super_mac
msedge.exe
\extensions.settings
SOFTWARE\Microsoft\Edge\PreferenceMACs\
\msedge.exe
\Google\Chrome\Application
(x86)\Google\Chrome\Application
SOFTWARE\Google\Chrome\BLBeacon
\resources.pak
chrome
chrome.exe
SOFTWARE\Google\Chrome\PreferenceMACs\
\chrome.exe
Guest Profile
System Profile
Error!
ext_url
cfg_url
data=
/base/api/getData.php
Windows Server 2016
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008 R2
Windows Server 2008
Windows Server
Windows 10
Windows 8.1
Windows 8
Windows 7
Windows Vista
Windows XP
SOFTWARE\Policies\Microsoft\Windows Defender
DisableAntiSpyware
DisableRoutinelyTakingAction
SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
DisableBehaviorMonitoring
DisableOnAccessProtection
DisableScanOnRealtimeEnable
DisableRealtimeMonitoring
DisableIOAVProtection
DisableRawWriteNotification
GetComputerNameA
VerSetConditionMask
VerifyVersionInfoW
GetGeoInfoA
GetCurrentProcess
GetVersionExA
MultiByteToWideChar
WideCharToMultiByte
User32.dll
CharToOemA
IsWow64Process
GetModuleHandleA
LoadLibraryA
SetPriorityClass
Sleep
GetTempPathA
CreateProcessA
GetFileAttributesA
CreateDirectoryA
CreateThread
CloseHandle
VirtualAlloc
VirtualFree
OpenProcess
TerminateProcess
GetUserGeoID
ntdll.dll
NtQuerySystemInformation
RtlGetVersion
Shell32.dll
ShellExecuteA
SHGetFolderPathA
RegOpenKeyExA
RegSetValueExA
RegCloseKey
RegCreateKeyExA
RegDeleteKeyA
RegDeleteValueA
RegQueryValueExA
RegEnumKeyExA
ConvertSidToStringSidA
LookupAccountNameA
WINHTTP.dll
http://
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
(PID) Process(1692) karotima_1.exe
C2 (2)http://wfsdragon.ru/api/setStats.php
37.0.11.41
Attributes
Payload (2)http://37.0.8.235/proxies.txt
http://136.144.41.201/server.txt
Strings (288)CryptAcquireContextA
Advapi32.dll
Crypto++ RNG
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
http://37.0.8.235/proxies.txt
:1080
http://136.144.41.201/server.txt
HOST:
http://wfsdragon.ru/api/setStats.php
37.0.11.41
links
extensions
wininet.dll
https://
SetIncrement|ColdWallet
SetIncrement|BrowserWallet
SetIncrement|CryptoWallet
GetCryptoSleeping
SetIncrement|NoCryptoWallet
net_country_code
os_country_code
browsers
Chrome:
Edge:
ip_country
AddExtensionStat|
AddLoggerStat|
SetIncrement|ww_starts
false
iplis.ru/1S3fd7.mp3
iplis.ru/1G8Fx7.mp3
iplis.ru/1pRXr7.txt
iplis.ru/1BV4j7.mp4
yobit.net
yobit.io
zb.com
binance.com
huobi.com
hitbtc.com
bitfinex.com
kraken.com
bitstamp.net
bittrex.com
gate.io
exmo.com
bitflyer.com
poloniex.com
kucoin.com
coinone.co.kr
livecoin.net
mercatox.com
localbitcoins.com
korbit.co.kr
bitmex.com
cryptobridge.freshdesk.com
volabit.com
tradeogre.com
blockchain.com
bitkub.com
uphold.com
wallet.uphold.com
login.blockchain.com
tidex.com
coinbase.com
coinome.com
bitso.com
coinpayments.net
luno.com
coinexchange.io
bitmax.io
btc-alpha.com
bitbank.cc
independentreserve.com
bitmart.com
cex.io
cryptopia.co.nz
cryptonator.com
advcash.com
my.dogechain.info
spectrocoin.com
exir.io
exir.tech
coinbene.com
bitforex.com
gopax.co.kr
catex.io
vindax.com
coineal.com
maicoin.com
finexbox.com
etherflyer.com
bx.in.th
bitopro.com
lbank.info
citex.co.kr
coinzo.com
atomars.com
coinfinit.com
bitker.com
btc-trade.com.ua
dobitrade.com
btcexa.com
satowallet.com
cpdax.com
trade.io
btcnext.io
exmarkets.com
localtrade.cc
btc-exchange.com
chaoex.com
jex.com
therocktrading.com
gdac.com
southxchange.com
tokens.net
fexpro.net
btcbox.co.jp
coinmex.com
cryptology.com
kuna.io
cointiger.com
cashierest.com
liquid.com
coinbit.co.kr
mxc.com
bilaxy.com
coinall.com
coindeal.com
omgfin.com
stex.com
oceanex.pro
bithumb.com
ftx.com
shortex.net
coin.z.com
fcoin.com
fatbtc.com
tokenize.exchange
simex.global
instantbitex.com
btcmarkets.net
SOFTWARE\Google\Chrome\PreferenceMACs
\Google\Chrome\User Data\
\Login Data
SOFTWARE\Microsoft\Edge\PreferenceMACs
\Microsoft\Edge\User Data\
SOFTWARE\BraveSoftware\Brave-Browser\PreferenceMACs
\BraveSoftware\Brave-Browser\User Data\
SOFTWARE\CryptoTab Browser\PreferenceMACs
\CryptoTab Browser\User Data\
\Roaming
\Opera Software\Opera Stable
\atomic
\Atomic Wallet
\com.liberty.jaxx
\Electrum
\Exodus
\MultiDoge
\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
\Microsoft\Edge\Application
(x86)\Microsoft\Edge\Application
SOFTWARE\Microsoft\Edge\BLBeacon
version
\Secure Preferences
filter_browsers
browser
use_open_browser
settings
install_time
\Extensions\
\u003C
protection
extensions.settings.
super_mac
msedge.exe
\extensions.settings
SOFTWARE\Microsoft\Edge\PreferenceMACs\
\msedge.exe
\Google\Chrome\Application
(x86)\Google\Chrome\Application
SOFTWARE\Google\Chrome\BLBeacon
\resources.pak
chrome
chrome.exe
SOFTWARE\Google\Chrome\PreferenceMACs\
\chrome.exe
Guest Profile
System Profile
Error!
ext_url
cfg_url
data=
/base/api/getData.php
Windows Server 2016
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008 R2
Windows Server 2008
Windows Server
Windows 10
Windows 8.1
Windows 8
Windows 7
Windows Vista
Windows XP
SOFTWARE\Policies\Microsoft\Windows Defender
DisableAntiSpyware
DisableRoutinelyTakingAction
SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
DisableBehaviorMonitoring
DisableOnAccessProtection
DisableScanOnRealtimeEnable
DisableRealtimeMonitoring
DisableIOAVProtection
DisableRawWriteNotification
GetComputerNameA
VerSetConditionMask
VerifyVersionInfoW
GetGeoInfoA
GetCurrentProcess
GetVersionExA
MultiByteToWideChar
WideCharToMultiByte
User32.dll
CharToOemA
IsWow64Process
GetModuleHandleA
LoadLibraryA
SetPriorityClass
Sleep
GetTempPathA
CreateProcessA
GetFileAttributesA
CreateDirectoryA
CreateThread
CloseHandle
VirtualAlloc
VirtualFree
OpenProcess
TerminateProcess
GetUserGeoID
ntdll.dll
NtQuerySystemInformation
RtlGetVersion
Shell32.dll
ShellExecuteA
SHGetFolderPathA
RegOpenKeyExA
RegSetValueExA
RegCloseKey
RegCreateKeyExA
RegDeleteKeyA
RegDeleteValueA
RegQueryValueExA
RegEnumKeyExA
ConvertSidToStringSidA
LookupAccountNameA
WINHTTP.dll
http://
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:01 02:44:18+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x35d8 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
129
Monitored processes
51
Malicious processes
31
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | karotima_1.exe | C:\Users\admin\AppData\Local\Temp\7zS01C55F68\karotima_1.exe | cmd.exe | ||||||||||||
User: admin Company: SoftWare Portal Integrity Level: HIGH Description: SoftWare Portal Exit code: 0 Version: 2.0.1.3 Modules
PrivateLoader(PID) Process(480) karotima_1.exe C2 (2)http://wfsdragon.ru/api/setStats.php 37.0.11.41 Attributes Payload (2)http://37.0.8.235/proxies.txt http://136.144.41.201/server.txt Strings (288)CryptAcquireContextA Advapi32.dll Crypto++ RNG ipinfo.io/widget country db-ip.com data-api-key=" /self countryCode www.maxmind.com/geoip/v2.1/city/me iso_code GetIP api.ipgeolocation.io/ipgeo?include=hostname&ip= country_code2 http://37.0.8.235/proxies.txt :1080 http://136.144.41.201/server.txt HOST: http://wfsdragon.ru/api/setStats.php 37.0.11.41 links extensions wininet.dll https:// SetIncrement|ColdWallet SetIncrement|BrowserWallet SetIncrement|CryptoWallet GetCryptoSleeping SetIncrement|NoCryptoWallet net_country_code os_country_code browsers Chrome: Edge: ip_country AddExtensionStat| AddLoggerStat| SetIncrement|ww_starts false iplis.ru/1S3fd7.mp3 iplis.ru/1G8Fx7.mp3 iplis.ru/1pRXr7.txt iplis.ru/1BV4j7.mp4 yobit.net yobit.io zb.com binance.com huobi.com hitbtc.com bitfinex.com kraken.com bitstamp.net bittrex.com gate.io exmo.com bitflyer.com poloniex.com kucoin.com coinone.co.kr livecoin.net mercatox.com localbitcoins.com korbit.co.kr bitmex.com cryptobridge.freshdesk.com volabit.com tradeogre.com blockchain.com bitkub.com uphold.com wallet.uphold.com login.blockchain.com tidex.com coinbase.com coinome.com bitso.com coinpayments.net luno.com coinexchange.io bitmax.io btc-alpha.com bitbank.cc independentreserve.com bitmart.com cex.io cryptopia.co.nz cryptonator.com advcash.com my.dogechain.info spectrocoin.com exir.io exir.tech coinbene.com bitforex.com gopax.co.kr catex.io vindax.com coineal.com maicoin.com finexbox.com etherflyer.com bx.in.th bitopro.com lbank.info citex.co.kr coinzo.com atomars.com coinfinit.com bitker.com btc-trade.com.ua dobitrade.com btcexa.com satowallet.com cpdax.com trade.io btcnext.io exmarkets.com localtrade.cc btc-exchange.com chaoex.com jex.com therocktrading.com gdac.com southxchange.com tokens.net fexpro.net btcbox.co.jp coinmex.com cryptology.com kuna.io cointiger.com cashierest.com liquid.com coinbit.co.kr mxc.com bilaxy.com coinall.com coindeal.com omgfin.com stex.com oceanex.pro bithumb.com ftx.com shortex.net coin.z.com fcoin.com fatbtc.com tokenize.exchange simex.global instantbitex.com btcmarkets.net SOFTWARE\Google\Chrome\PreferenceMACs \Google\Chrome\User Data\ \Login Data SOFTWARE\Microsoft\Edge\PreferenceMACs \Microsoft\Edge\User Data\ SOFTWARE\BraveSoftware\Brave-Browser\PreferenceMACs \BraveSoftware\Brave-Browser\User Data\ SOFTWARE\CryptoTab Browser\PreferenceMACs \CryptoTab Browser\User Data\ \Roaming \Opera Software\Opera Stable \atomic \Atomic Wallet \com.liberty.jaxx \Electrum \Exodus \MultiDoge \Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn \Microsoft\Edge\Application (x86)\Microsoft\Edge\Application SOFTWARE\Microsoft\Edge\BLBeacon version \Secure Preferences filter_browsers browser use_open_browser settings install_time \Extensions\ \u003C protection extensions.settings. super_mac msedge.exe \extensions.settings SOFTWARE\Microsoft\Edge\PreferenceMACs\ \msedge.exe \Google\Chrome\Application (x86)\Google\Chrome\Application SOFTWARE\Google\Chrome\BLBeacon \resources.pak chrome chrome.exe SOFTWARE\Google\Chrome\PreferenceMACs\ \chrome.exe Guest Profile System Profile Error! ext_url cfg_url data= /base/api/getData.php Windows Server 2016 Windows Server 2012 R2 Windows Server 2012 Windows Server 2008 R2 Windows Server 2008 Windows Server Windows 10 Windows 8.1 Windows 8 Windows 7 Windows Vista Windows XP SOFTWARE\Policies\Microsoft\Windows Defender DisableAntiSpyware DisableRoutinelyTakingAction SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection DisableBehaviorMonitoring DisableOnAccessProtection DisableScanOnRealtimeEnable DisableRealtimeMonitoring DisableIOAVProtection DisableRawWriteNotification GetComputerNameA VerSetConditionMask VerifyVersionInfoW GetGeoInfoA GetCurrentProcess GetVersionExA MultiByteToWideChar WideCharToMultiByte User32.dll CharToOemA IsWow64Process GetModuleHandleA LoadLibraryA SetPriorityClass Sleep GetTempPathA CreateProcessA GetFileAttributesA CreateDirectoryA CreateThread CloseHandle VirtualAlloc VirtualFree OpenProcess TerminateProcess GetUserGeoID ntdll.dll NtQuerySystemInformation RtlGetVersion Shell32.dll ShellExecuteA SHGetFolderPathA RegOpenKeyExA RegSetValueExA RegCloseKey RegCreateKeyExA RegDeleteKeyA RegDeleteValueA RegQueryValueExA RegEnumKeyExA ConvertSidToStringSidA LookupAccountNameA WINHTTP.dll http:// WinHttpConnect WinHttpQueryHeaders WinHttpOpen WinHttpOpenRequest WinHttpQueryDataAvailable WinHttpSendRequest WinHttpReceiveResponse WinHttpReadData WinHttpCloseHandle InternetOpenA InternetSetOptionA HttpOpenRequestA InternetConnectA InternetOpenUrlA HttpQueryInfoA InternetQueryOptionA HttpSendRequestA InternetReadFile InternetCloseHandle | |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe" | C:\Users\admin\AppData\Local\Temp\HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 784 | C:\Windows\system32\cmd.exe /c karotima_2.exe | C:\Windows\System32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225477 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 880 | karotima_2.exe | C:\Users\admin\AppData\Local\Temp\7zSCFBAE888\karotima_2.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\AppData\Local\Temp\setup_installer.exe" | C:\Users\admin\AppData\Local\Temp\setup_installer.exe | HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
| 984 | "C:\Users\admin\AppData\Local\Temp\HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe" | C:\Users\admin\AppData\Local\Temp\HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1020 | C:\Windows\system32\cmd.exe /c karotima_1.exe | C:\Windows\System32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1124 | C:\Windows\system32\cmd.exe /c karotima_2.exe | C:\Windows\System32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225477 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1288 | "C:\Users\admin\AppData\Local\Temp\7zS0BC37758\setup_install.exe" | C:\Users\admin\AppData\Local\Temp\7zS0BC37758\setup_install.exe | setup_installer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Modules
| |||||||||||||||
| 1340 | karotima_1.exe | C:\Users\admin\AppData\Local\Temp\7zSCFBAE888\karotima_1.exe | cmd.exe | ||||||||||||
User: admin Company: SoftWare Portal Integrity Level: HIGH Description: SoftWare Portal Exit code: 0 Version: 2.0.1.3 Modules
| |||||||||||||||
Total events
59 161
Read events
58 949
Write events
207
Delete events
5
Modification events
| (PID) Process: | (3216) HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3216) HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3216) HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3216) HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2848) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2624) karotima_1.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2624) karotima_1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates |
| Operation: | delete value | Name: | 9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
Value: | |||
Executable files
77
Suspicious files
8
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2624 | karotima_1.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:DD97FC666DF4292FEEC108F150DED1B4 | SHA256:6D7A7B5B0FE2D80A09212CAA0DE0C41C2B587B5E01FEE63A3E643AAC3BD17942 | |||
| 3216 | HEUR-Trojan.Win32.Chapak.gen-e6ea98b046b11a35.exe | C:\Users\admin\AppData\Local\Temp\setup_installer.exe | executable | |
MD5:78418BFB23C7ADF70828F675E990DE49 | SHA256:B14218CB639C6AFA35A66CF418035CE10475B53F5386896A44327FD48D8447C8 | |||
| 2848 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS02B5ADD7\libgcc_s_dw2-1.dll | executable | |
MD5:9AEC524B616618B0D3D00B27B6F51DA1 | SHA256:59A466F77584438FC3ABC0F43EDC0FC99D41851726827A008841F05CFE12DA7E | |||
| 2624 | karotima_1.exe | C:\Users\admin\AppData\Local\Temp\CabF6C4.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2848 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS02B5ADD7\libcurlpp.dll | executable | |
MD5:E6E578373C2E416289A8DA55F1DC5E8E | SHA256:43E86D650A68F1F91FA2F4375AFF2720E934AA78FA3D33E06363122BF5A9535F | |||
| 2848 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS02B5ADD7\setup_install.exe | executable | |
MD5:118F130D93DB3BE4452AD8A0751509DF | SHA256:F7DEC887C3345567CE86CE60CC8841A6A54EDA35049811049DEBD1C5451656F4 | |||
| 3464 | setup_install.exe | C:\Users\admin\AppData\Local\Temp\7zS02B5ADD7\karotima_1.exe | executable | |
MD5:9108AD5775C76CCCBB4EADF02DE24F5D | SHA256:C9D5525B2F2B76087121039EE1C23ED35508E60F653479722EC64EA3A064878E | |||
| 2624 | karotima_1.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2624 | karotima_1.exe | C:\Users\admin\AppData\Local\Temp\TarF6C5.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3212 | karotima_2.exe | C:\Users\admin\AppData\Local\Temp\CC4F.tmp | executable | |
MD5:EBB2B4FD62087283D9448F7F8796727D | SHA256:9C9EA64C0D56BF17D388C58B36AB7A79CA6AA74446B6DD2F614F5CBF9D828529 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
28
DNS requests
8
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2624 | karotima_1.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5ea8adc661810059 | unknown | compressed | 65.2 Kb | unknown |
3272 | karotima_1.exe | GET | 403 | 104.18.146.235:80 | http://www.maxmind.com/geoip/v2.1/city/me | unknown | html | 4.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2624 | karotima_1.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2624 | karotima_1.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2624 | karotima_1.exe | 37.0.8.235:80 | — | — | NL | unknown |
480 | karotima_1.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
480 | karotima_1.exe | 37.0.8.235:80 | — | — | NL | unknown |
3272 | karotima_1.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
3024 | karotima_1.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wxkeww.xyz |
| unknown |
ipinfo.io |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
dns.msftncsi.com |
| shared |
db-ip.com |
| whitelisted |
api.db-ip.com |
| shared |
www.maxmind.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2624 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2624 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
480 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
480 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
3272 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3272 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
3024 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3024 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
1692 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
1692 | karotima_1.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |