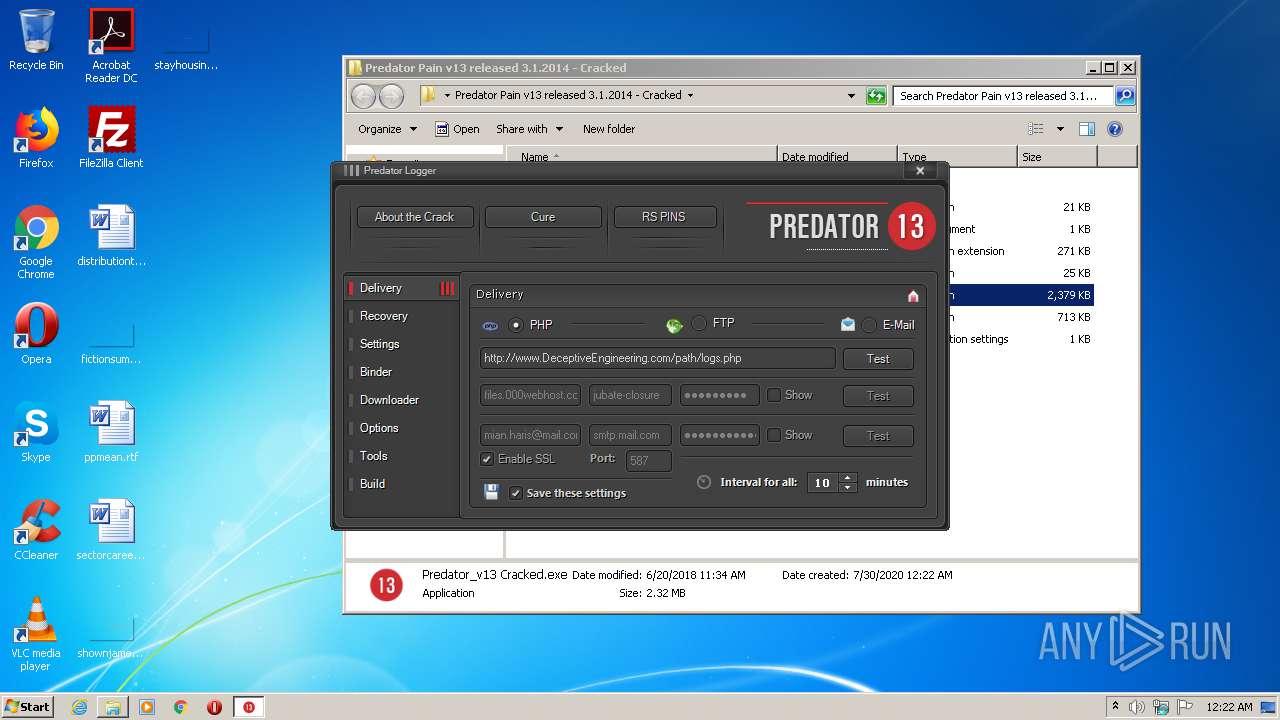
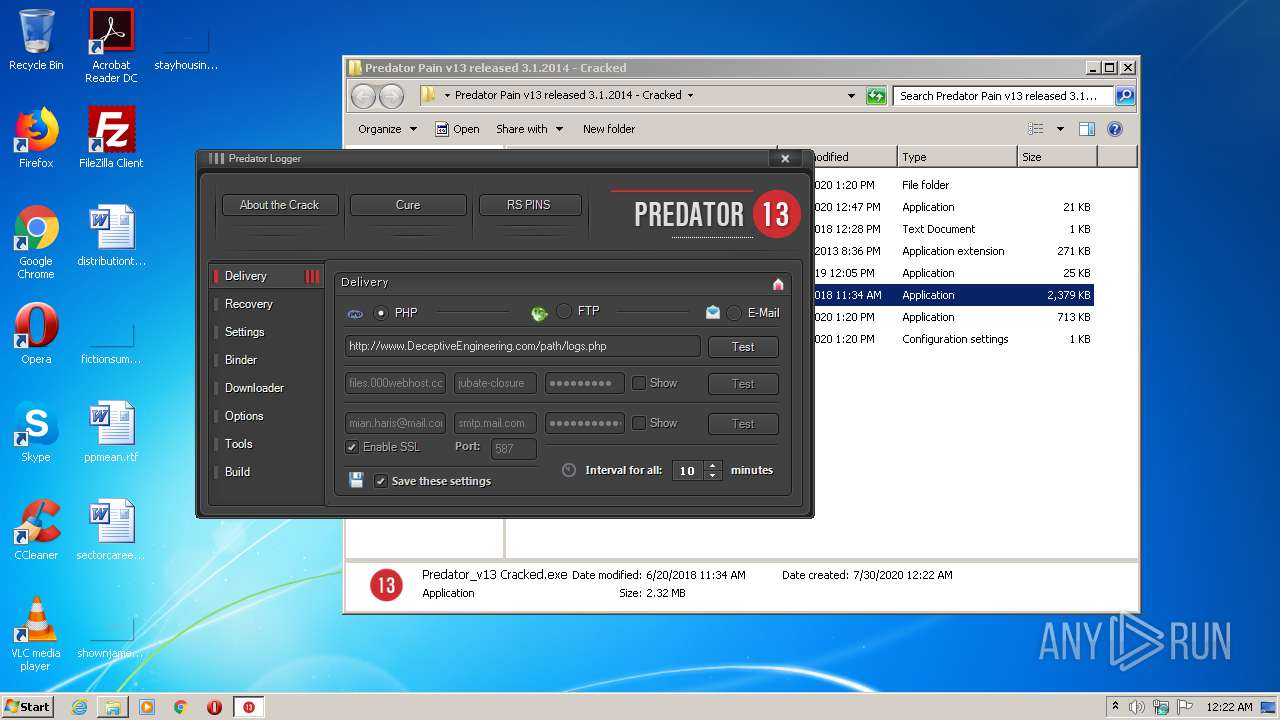
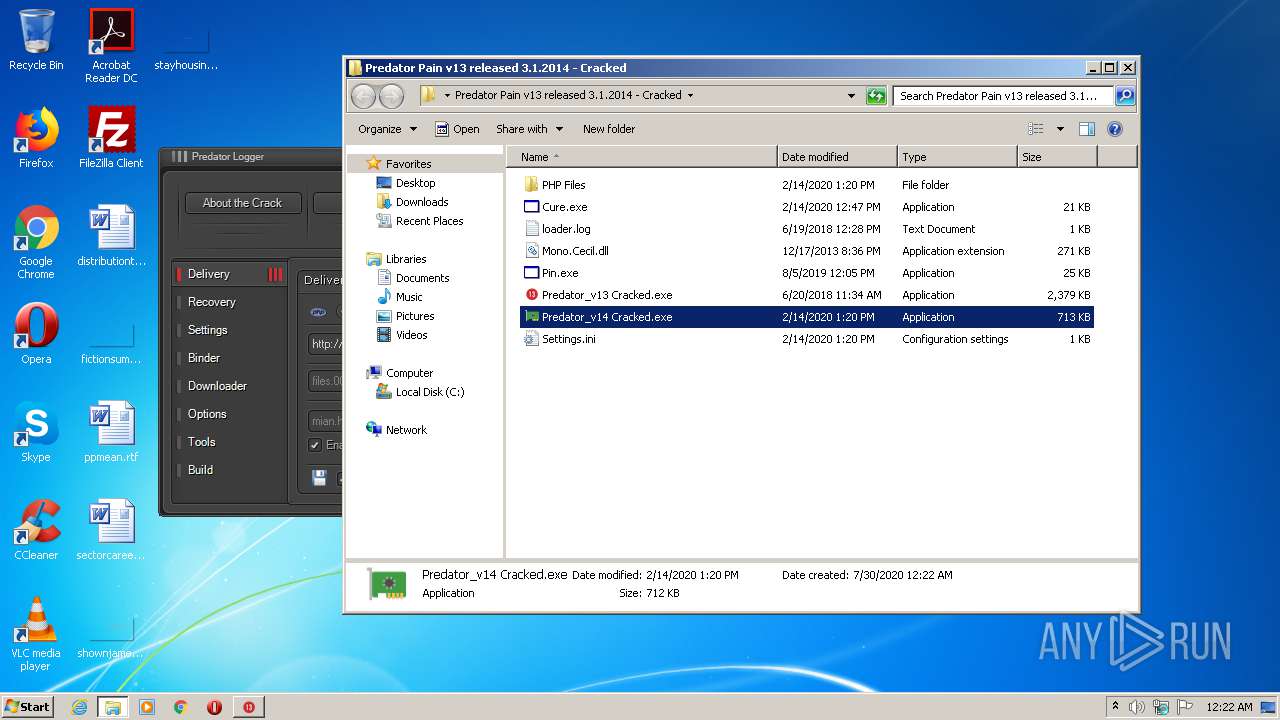
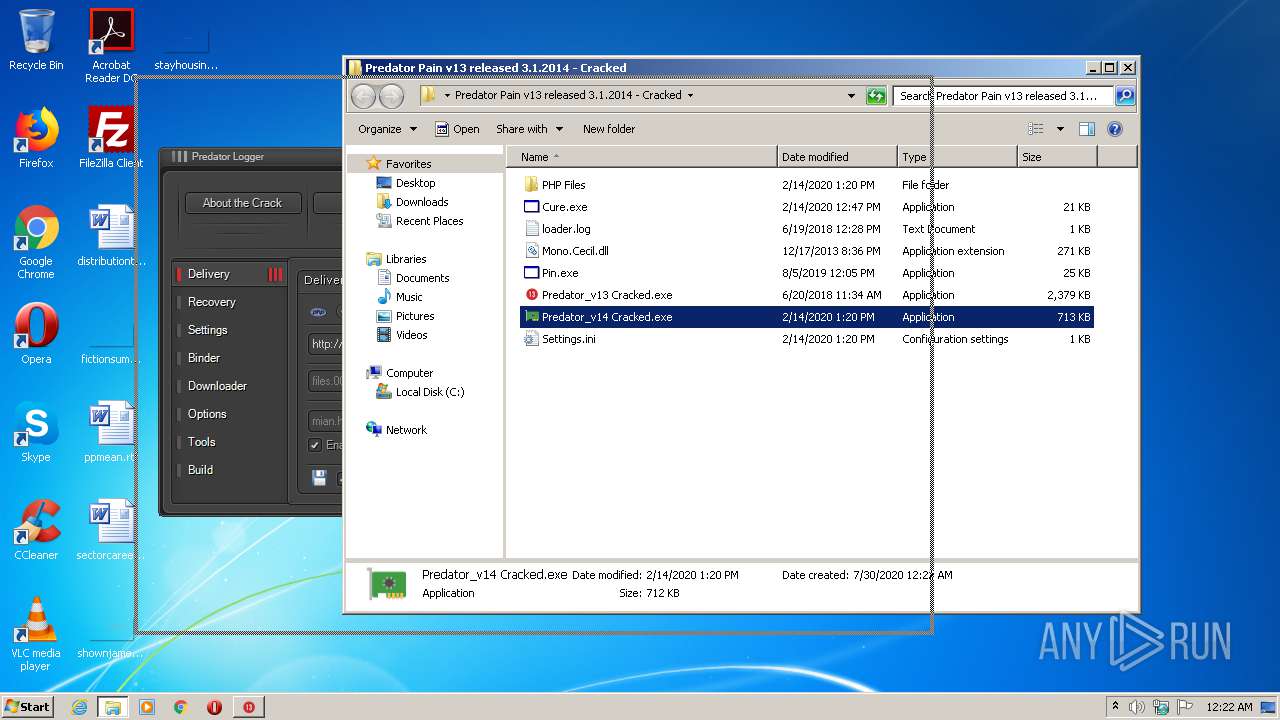
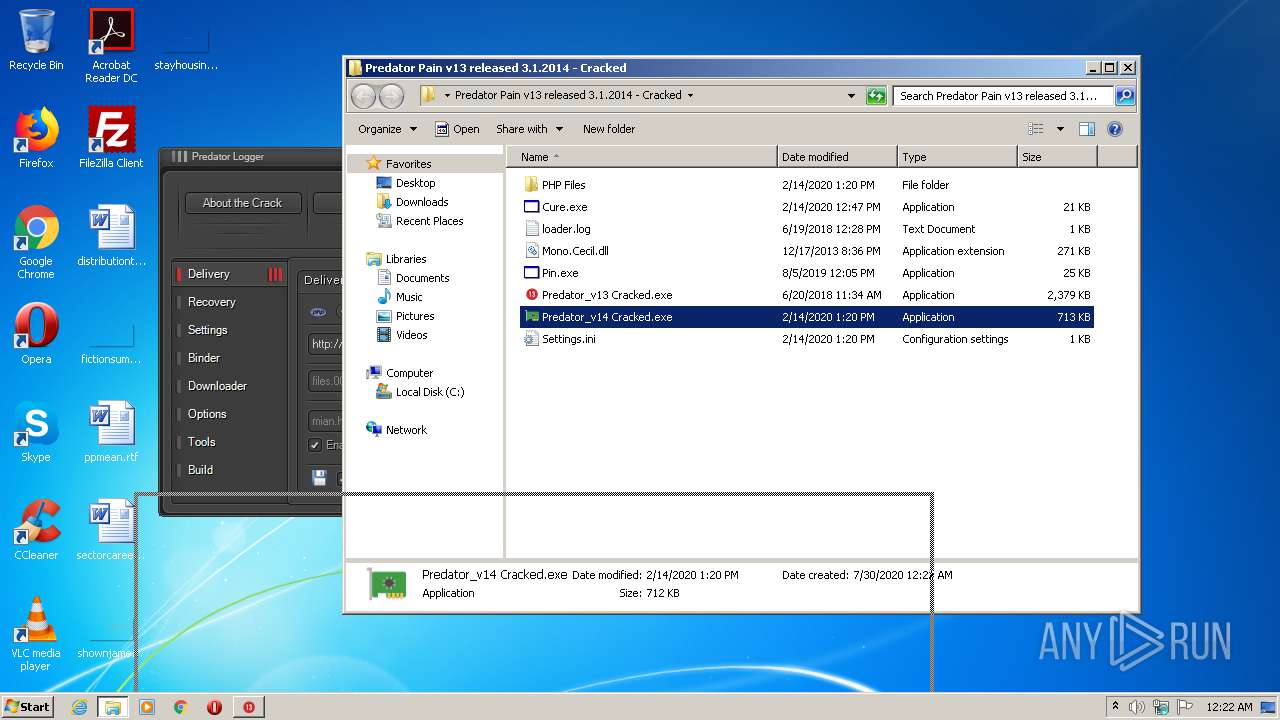
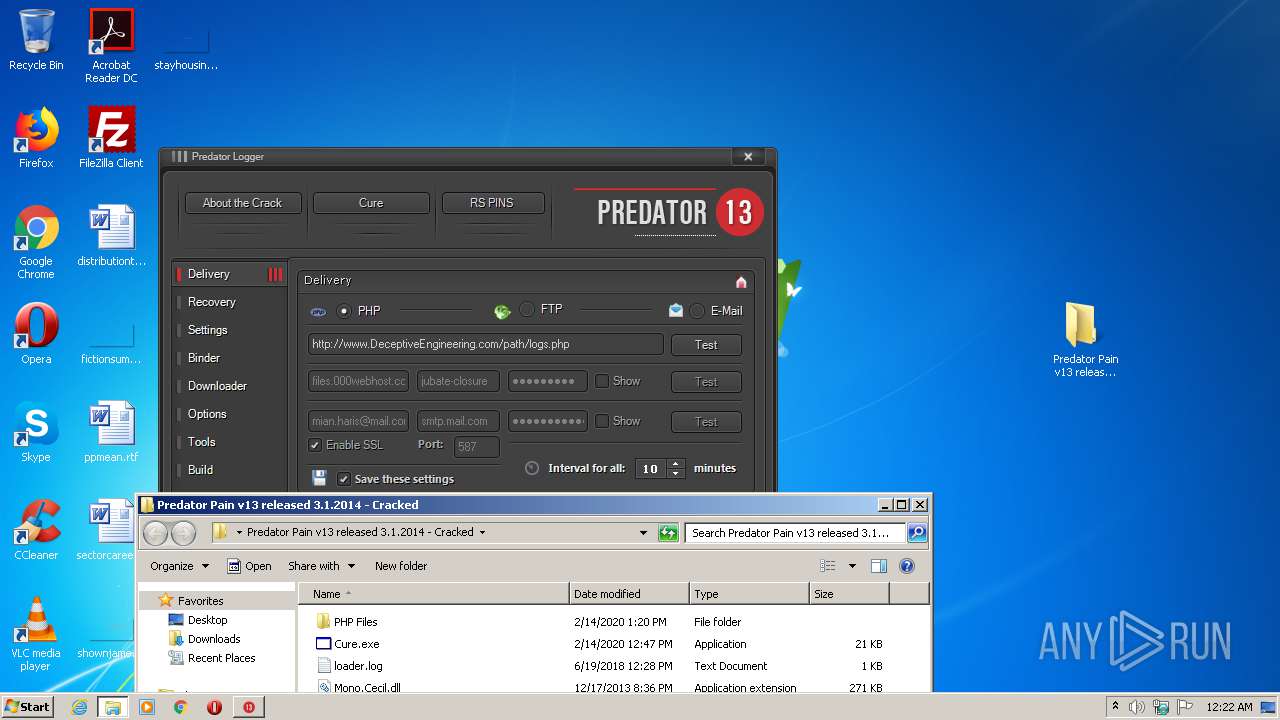
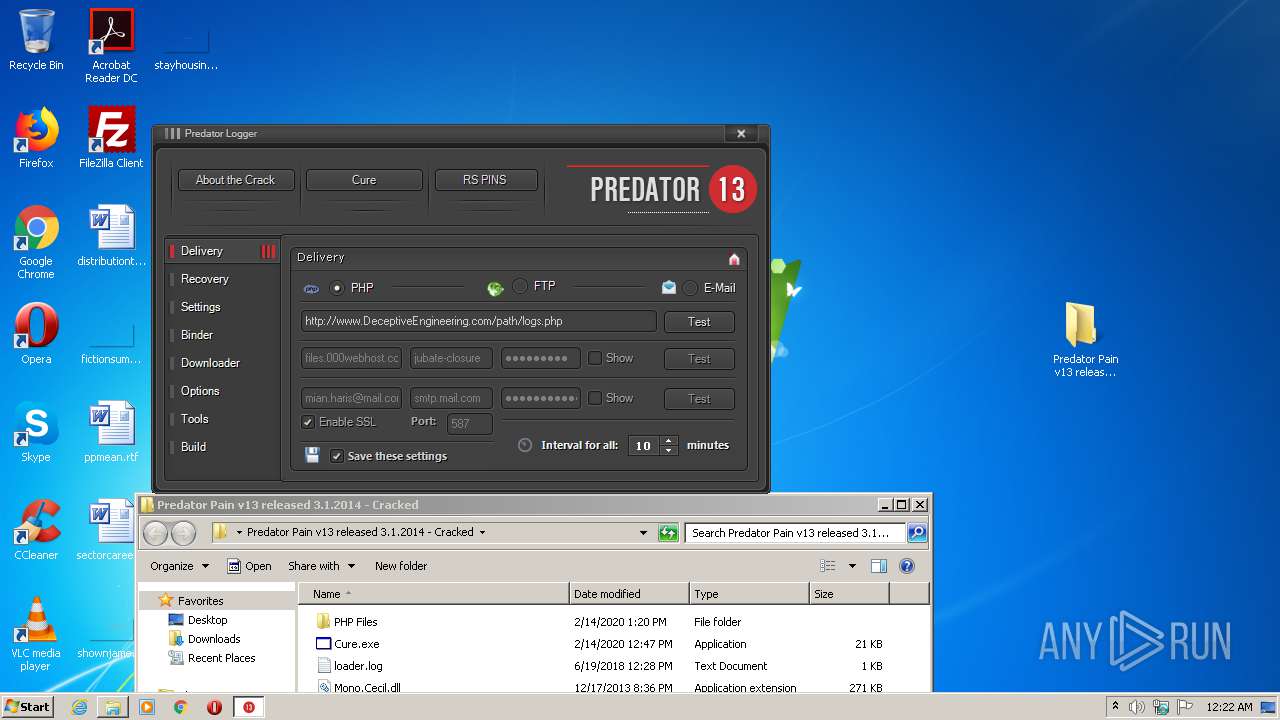
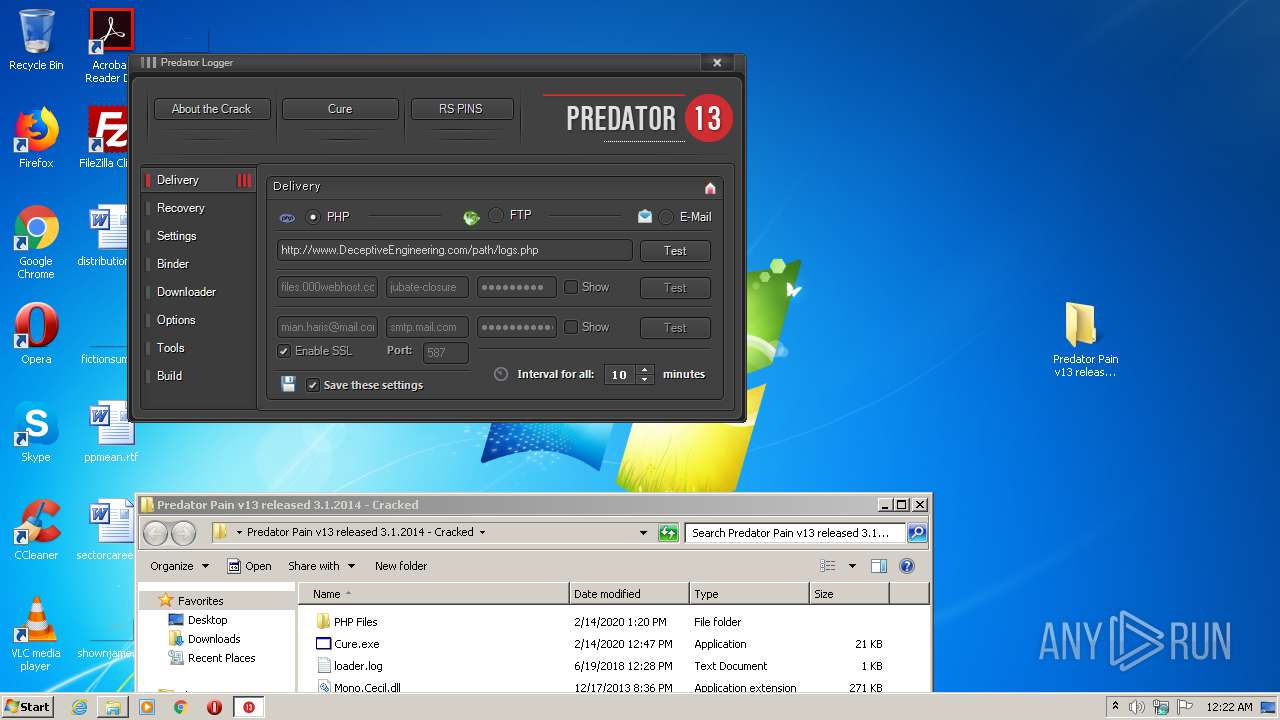
| File name: | Predator Pain v13 released 3.1.2014 - Cracked.rar |
| Full analysis: | https://app.any.run/tasks/59a7ccb7-4803-4997-a31b-8cf409094025 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | July 29, 2020, 23:22:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4C7B97192C4CC26D61773CF7CD9FF6A0 |
| SHA1: | A63CB5C1E88F5078549E71D9804CCF20F9449653 |
| SHA256: | E6BA3386C042F21DACB6B5D0E09D03660620C62FF82874CEDA695150E9B59B57 |
| SSDEEP: | 24576:+CQXE+2T6dOYjCdKlpeWscXqk0+GUzEK95+8whn80+E0OBCxQb:+oZwCdKloWPqkjJEKI0OBCQb |
MALICIOUS
Application was dropped or rewritten from another process
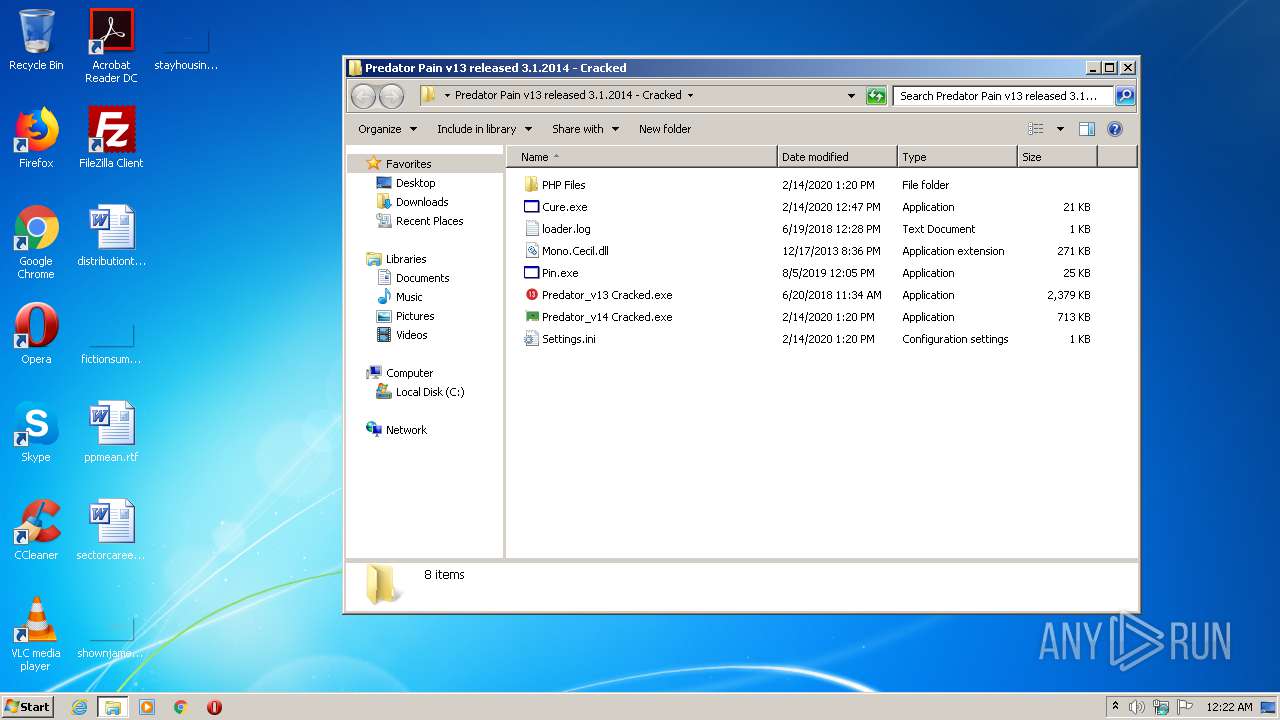
- Predator_v14 Cracked.exe (PID: 928)
- Predator_v13 Cracked.exe (PID: 3912)
- EBFile_1.exe (PID: 3896)
- Chrome32.exe (PID: 3432)
- Predator_v13 Cracked.exe (PID: 2612)
- Predator_v14 Cracked.exe (PID: 3872)
HAWKEYE was detected
- Predator_v14 Cracked.exe (PID: 928)
Changes the autorun value in the registry
- EBFile_1.exe (PID: 3896)
- Chrome32.exe (PID: 3432)
Actions looks like stealing of personal data
- vbc.exe (PID: 324)
- vbc.exe (PID: 3804)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1772)
- Predator_v14 Cracked.exe (PID: 928)
- EBFile_1.exe (PID: 3896)
- Chrome32.exe (PID: 3432)
Creates files in the user directory
- Predator_v14 Cracked.exe (PID: 928)
- EBFile_1.exe (PID: 3896)
Checks for external IP
- Predator_v14 Cracked.exe (PID: 928)
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 1772)
Starts itself from another location
- EBFile_1.exe (PID: 3896)
Executes scripts
- Predator_v14 Cracked.exe (PID: 928)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 3804)
INFO
Manual execution by user
- Predator_v14 Cracked.exe (PID: 928)
- Predator_v13 Cracked.exe (PID: 3912)
- Predator_v14 Cracked.exe (PID: 3872)
- Predator_v13 Cracked.exe (PID: 2612)
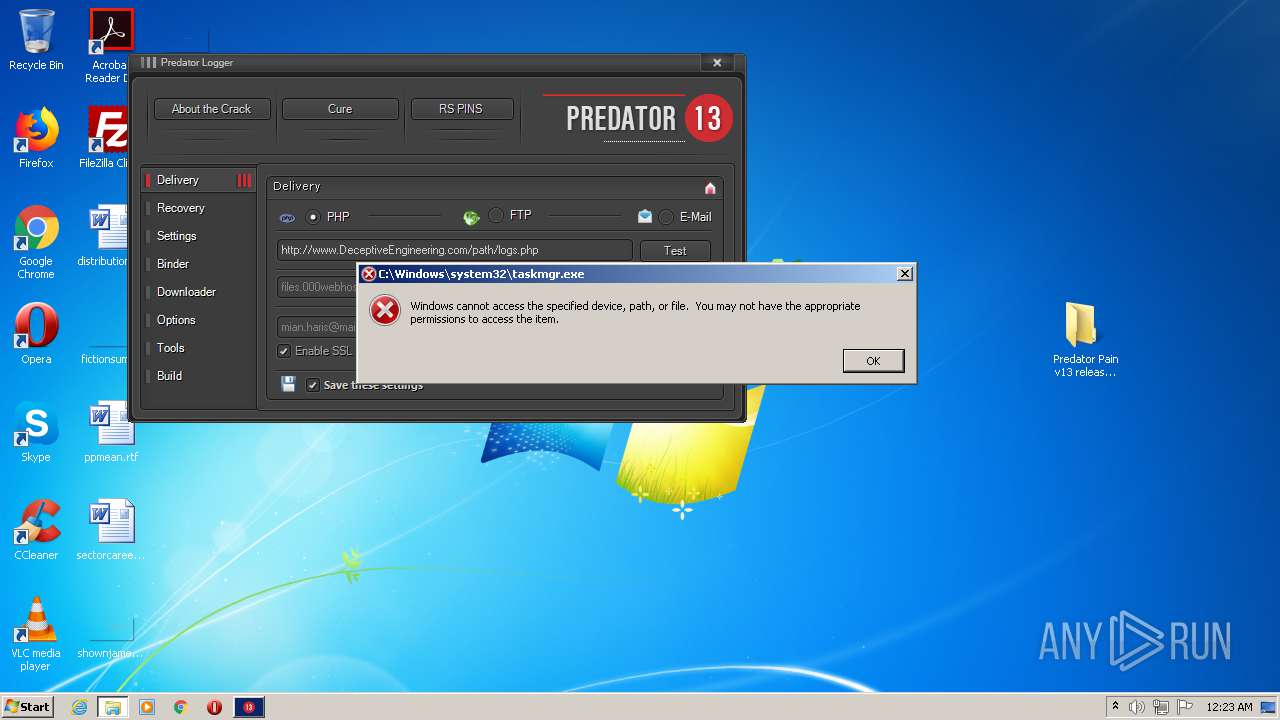
- taskmgr.exe (PID: 2160)
Dropped object may contain Bitcoin addresses
- Predator_v14 Cracked.exe (PID: 928)
- Chrome32.exe (PID: 3432)
- EBFile_1.exe (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
10
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | Predator_v14 Cracked.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 928 | "C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v14 Cracked.exe" | C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v14 Cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Microsoft Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1772 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Predator Pain v13 released 3.1.2014 - Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2160 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2612 | "C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v13 Cracked.exe" | C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v13 Cracked.exe | explorer.exe | ||||||||||||
User: admin Company: Predator Inc. Integrity Level: MEDIUM Description: Predator Logger Exit code: 0 Version: 13.0.0.0 Modules
| |||||||||||||||
| 3432 | "C:\Users\admin\AppData\Local\Google (x86)\Chrome32.exe" C:\Users\admin\AppData\Local\Temp\EBFile_1.exe | C:\Users\admin\AppData\Local\Google (x86)\Chrome32.exe | EBFile_1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Adobe Reader Exit code: 0 Version: 11.0.10.32 Modules
| |||||||||||||||
| 3804 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | Predator_v14 Cracked.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 3872 | "C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v14 Cracked.exe" | C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v14 Cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Microsoft Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3896 | "C:\Users\admin\AppData\Local\Temp\EBFile_1.exe" | C:\Users\admin\AppData\Local\Temp\EBFile_1.exe | Predator_v14 Cracked.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Adobe Reader Exit code: 0 Version: 11.0.10.32 Modules
| |||||||||||||||
| 3912 | "C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v13 Cracked.exe" | C:\Users\admin\Desktop\Predator Pain v13 released 3.1.2014 - Cracked\Predator_v13 Cracked.exe | explorer.exe | ||||||||||||
User: admin Company: Predator Inc. Integrity Level: MEDIUM Description: Predator Logger Exit code: 0 Version: 13.0.0.0 Modules
| |||||||||||||||
Total events
1 362
Read events
1 308
Write events
54
Delete events
0
Modification events
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Predator Pain v13 released 3.1.2014 - Cracked.rar | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
9
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holdermail.txt | — | |
MD5:— | SHA256:— | |||
| 3804 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holderwb.txt | — | |
MD5:— | SHA256:— | |||
| 1772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1772.28043\Predator Pain v13 released 3.1.2014 - Cracked\desktop.ini | ini | |
MD5:— | SHA256:— | |||
| 1772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1772.28043\Predator Pain v13 released 3.1.2014 - Cracked\Cure.exe | executable | |
MD5:1D6CE95B1B5D4D9A7CA8DAFFF0EF9DD1 | SHA256:F004580E2B6A28353D6C7FEFBB7CD5009C68683F2C81C7A005A9A8560A1127B2 | |||
| 1772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1772.28043\Predator Pain v13 released 3.1.2014 - Cracked\Settings.ini | text | |
MD5:— | SHA256:— | |||
| 928 | Predator_v14 Cracked.exe | C:\Users\admin\AppData\Roaming\pidloc.txt | text | |
MD5:— | SHA256:— | |||
| 928 | Predator_v14 Cracked.exe | C:\Users\admin\AppData\Local\Temp\EBFile_1.exe | executable | |
MD5:— | SHA256:— | |||
| 3896 | EBFile_1.exe | C:\Users\admin\AppData\Local\Google (x86)\Chrome32.exe | executable | |
MD5:— | SHA256:— | |||
| 3432 | Chrome32.exe | C:\Users\admin\AppData\Roaming\Adobe (x86)\AcroRd32.exe | executable | |
MD5:— | SHA256:— | |||
| 3896 | EBFile_1.exe | C:\Users\admin\AppData\Roaming\Adobe (x86)\AcroRd32.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
6
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
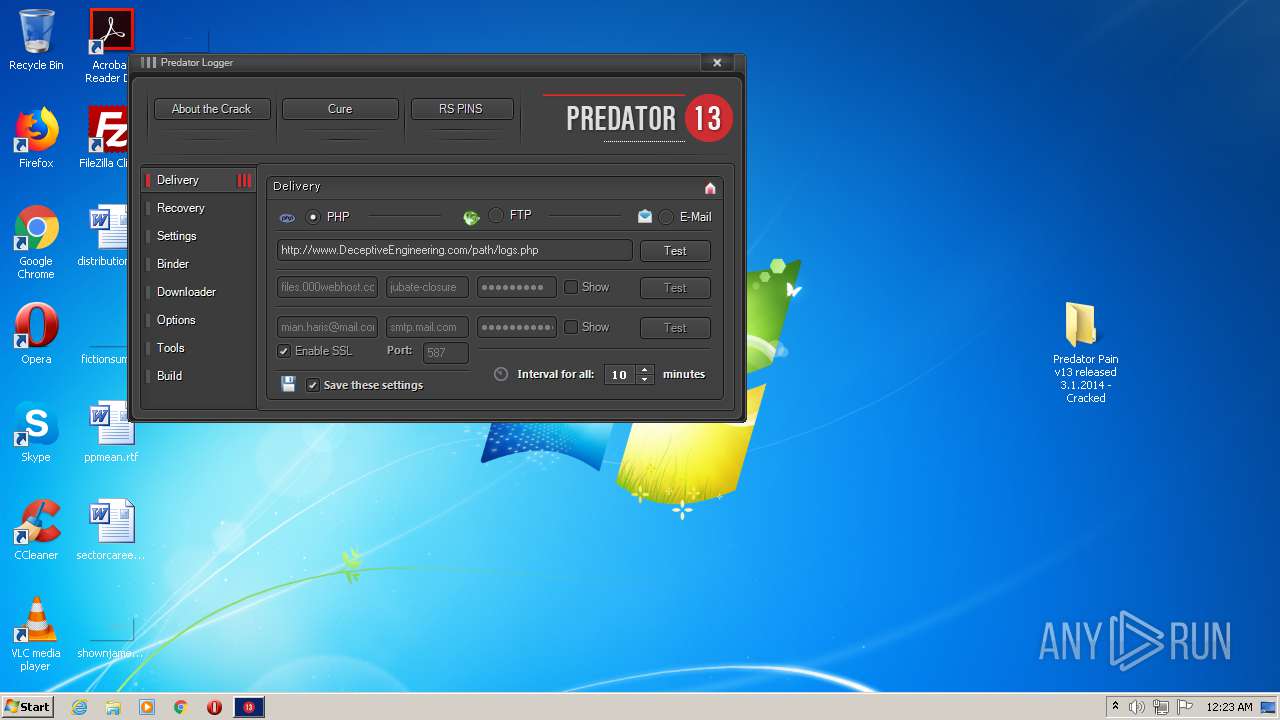
3912 | Predator_v13 Cracked.exe | GET | 200 | 199.59.242.153:80 | http://ww25.deceptiveengineering.com/path/logs.php?fname=PLogger_v13_Test.txt&data=%5BPLogger%20v.13%5D%20Your%20PHP%20has%20been%20verified,%20you%20may%20delete%20this%20file%20now.&subid1=20200730-0923-189e-bcef-3267f48b9346 | US | html | 3.93 Kb | malicious |
928 | Predator_v14 Cracked.exe | GET | 301 | 104.16.154.36:80 | http://whatismyipaddress.com/ | US | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
928 | Predator_v14 Cracked.exe | 104.16.154.36:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
928 | Predator_v14 Cracked.exe | 104.16.154.36:443 | whatismyipaddress.com | Cloudflare Inc | US | shared |
928 | Predator_v14 Cracked.exe | 145.14.144.10:21 | files.000webhost.com | Hostinger International Limited | US | malicious |
3912 | Predator_v13 Cracked.exe | 70.32.1.32:80 | www.deceptiveengineering.com | GigeNET | US | malicious |
3912 | Predator_v13 Cracked.exe | 199.59.242.153:80 | ww25.deceptiveengineering.com | Bodis, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |
files.000webhost.com |
| malicious |
www.deceptiveengineering.com |
| malicious |
ww25.deceptiveengineering.com |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
928 | Predator_v14 Cracked.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
928 | Predator_v14 Cracked.exe | A Network Trojan was detected | SPYWARE [PTsecurity] HawkEye / Predator Pain (IP Chck) |
928 | Predator_v14 Cracked.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
928 | Predator_v14 Cracked.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
928 | Predator_v14 Cracked.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2 ETPRO signatures available at the full report