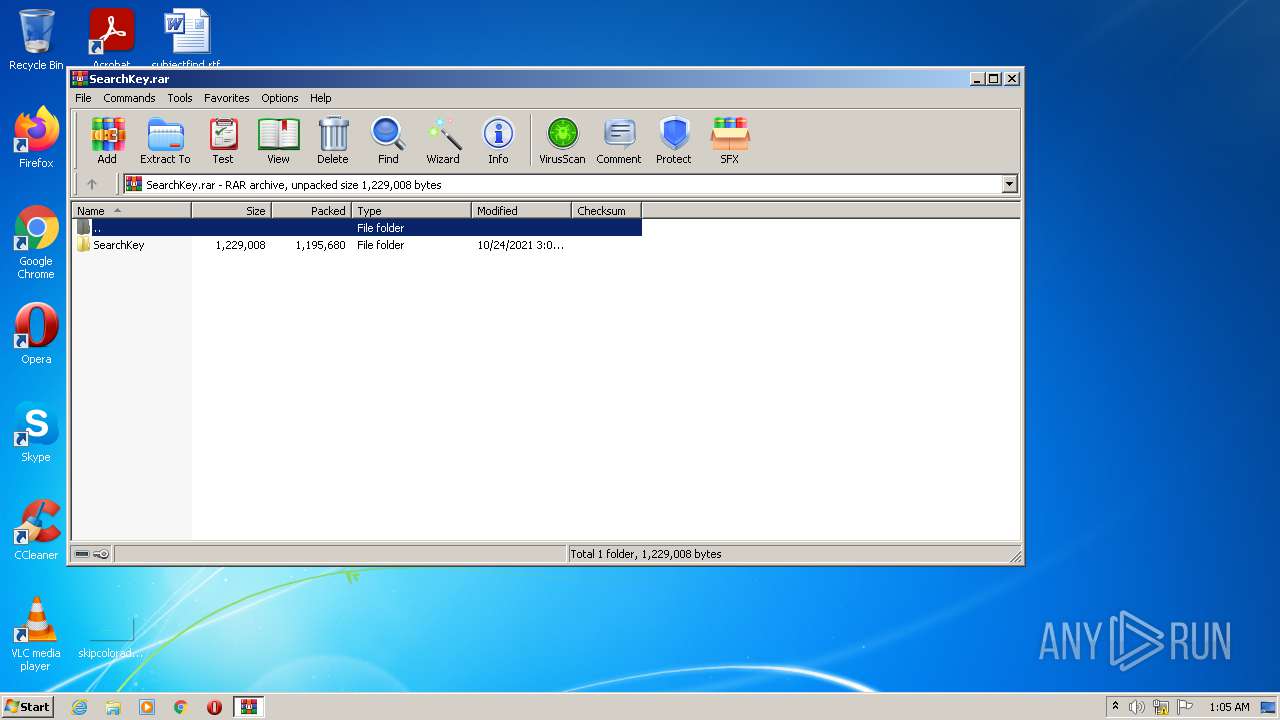
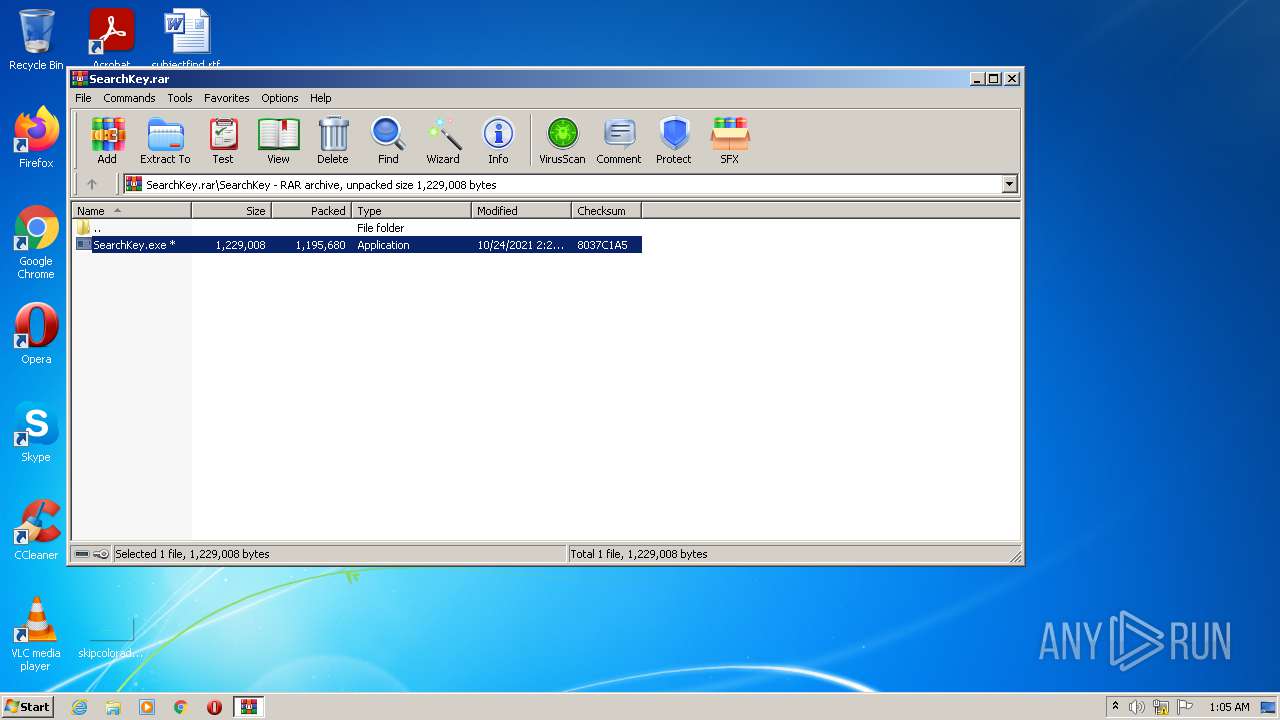
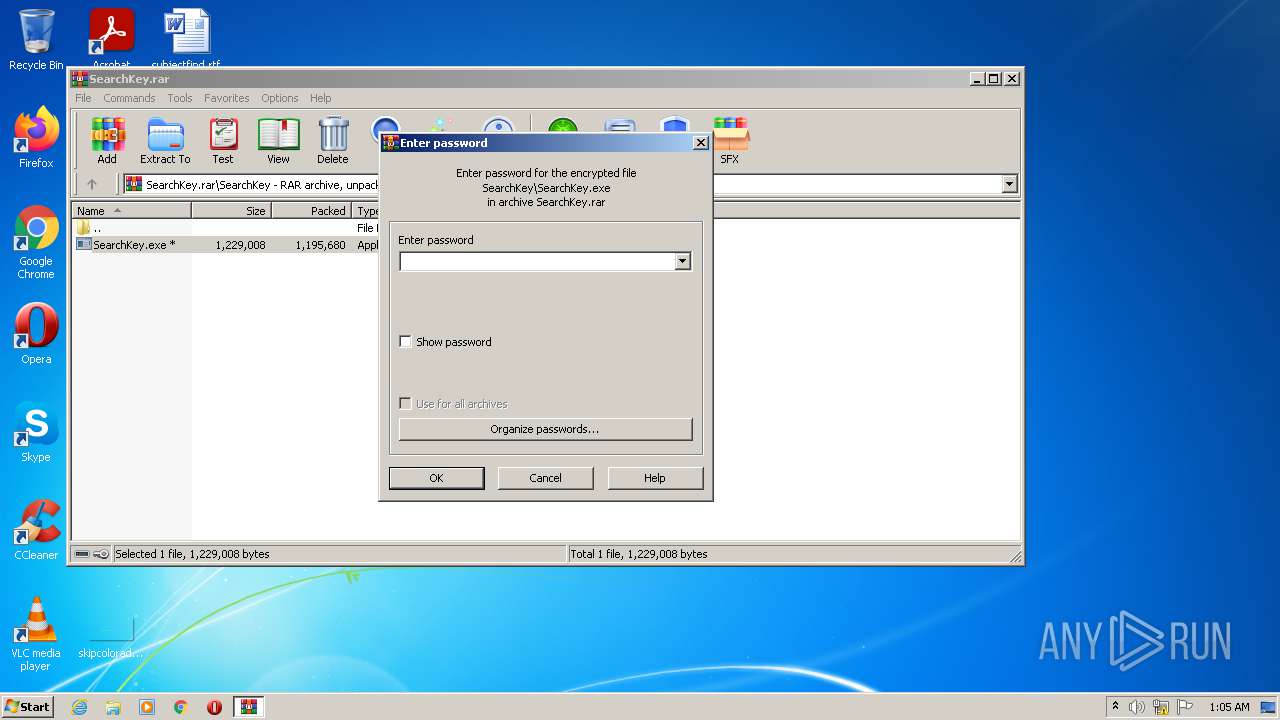
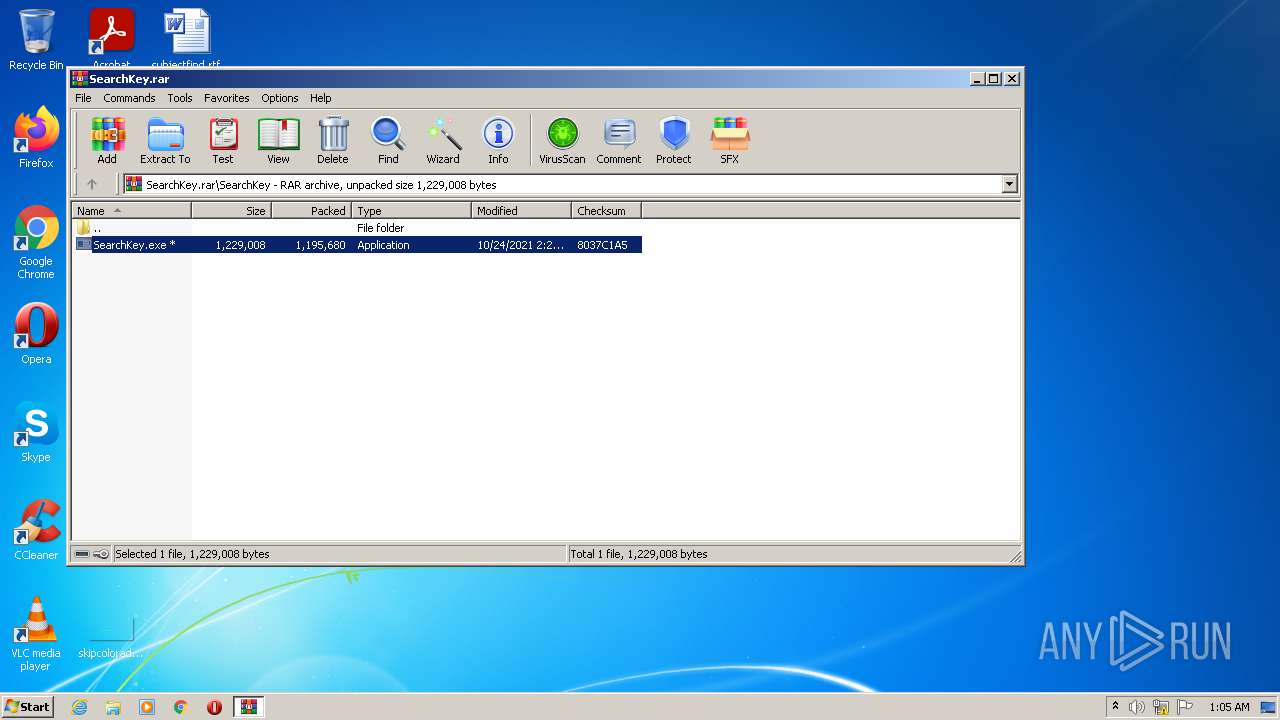
| File name: | SearchKey.rar |
| Full analysis: | https://app.any.run/tasks/4cdd3966-a385-41f0-aa7e-5278c4806624 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | October 25, 2021, 00:05:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B7AEAE0BBF761B45711EA3A0D71E2B7B |
| SHA1: | 716A88F53AED18E2F476CAC1E4367D7D54C37A72 |
| SHA256: | E66F04CDA8667F223CFDC809CF5C253A199A97150DB344CE1F6B827D4E1C624D |
| SSDEEP: | 24576:ymKIa5wgJt2aIIRN7NT5RlsMP1RBPk6u+6C2cOFOuA9pXHkWDOR76SQ3C:ahJtBIiT5sM/r68KODnXHPOB6SSC |
MALICIOUS
Connects to CnC server
- SearchKey.exe (PID: 276)
- rnyuf.exe (PID: 1168)
Application was dropped or rewritten from another process
- SearchKey.exe (PID: 276)
- vms.exe (PID: 3960)
- rnyuf.exe (PID: 1168)
Steals credentials from Web Browsers
- SearchKey.exe (PID: 276)
Drops executable file immediately after starts
- vms.exe (PID: 3960)
Actions looks like stealing of personal data
- SearchKey.exe (PID: 276)
Uses Task Scheduler to run other applications
- rnyuf.exe (PID: 1168)
Changes the Startup folder
- reg.exe (PID: 2696)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3692)
AMADEY was detected
- rnyuf.exe (PID: 1168)
REDLINE was detected
- SearchKey.exe (PID: 276)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3036)
- vms.exe (PID: 3960)
- cmd.exe (PID: 3468)
- rnyuf.exe (PID: 1168)
- SearchKey.exe (PID: 276)
Reads the computer name
- SearchKey.exe (PID: 276)
- WinRAR.exe (PID: 3036)
- vms.exe (PID: 3960)
- rnyuf.exe (PID: 1168)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3036)
- SearchKey.exe (PID: 276)
- vms.exe (PID: 3960)
Starts itself from another location
- vms.exe (PID: 3960)
Searches for installed software
- SearchKey.exe (PID: 276)
Starts CMD.EXE for commands execution
- rnyuf.exe (PID: 1168)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3468)
Drops a file with a compile date too recent
- SearchKey.exe (PID: 276)
Reads the cookies of Google Chrome
- SearchKey.exe (PID: 276)
Reads the cookies of Mozilla Firefox
- SearchKey.exe (PID: 276)
Drops a file with too old compile date
- WinRAR.exe (PID: 3036)
Reads Environment values
- SearchKey.exe (PID: 276)
INFO
Reads settings of System Certificates
- SearchKey.exe (PID: 276)
Checks supported languages
- reg.exe (PID: 2696)
- schtasks.exe (PID: 3692)
Reads the computer name
- schtasks.exe (PID: 3692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3036.038\SearchKey\SearchKey.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3036.038\SearchKey\SearchKey.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\AppData\Local\Temp\5c436eadc6\rnyuf.exe" | C:\Users\admin\AppData\Local\Temp\5c436eadc6\rnyuf.exe | vms.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2696 | REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /f /v Startup /t REG_SZ /d C:\Users\admin\AppData\Local\Temp\5c436eadc6\ | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3036 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SearchKey.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3468 | "C:\Windows\System32\cmd.exe" /C REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /f /v Startup /t REG_SZ /d C:\Users\admin\AppData\Local\Temp\5c436eadc6\ | C:\Windows\System32\cmd.exe | — | rnyuf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3692 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 1 /TN rnyuf.exe /TR "C:\Users\admin\AppData\Local\Temp\5c436eadc6\rnyuf.exe" /F | C:\Windows\System32\schtasks.exe | — | rnyuf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3960 | "C:\Users\admin\AppData\Local\Temp\vms.exe" | C:\Users\admin\AppData\Local\Temp\vms.exe | SearchKey.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
7 098
Read events
6 994
Write events
104
Delete events
0
Modification events
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\171\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SearchKey.rar | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3960 | vms.exe | C:\Users\admin\AppData\Local\Temp\15211302019708150072 | — | |
MD5:— | SHA256:— | |||
| 276 | SearchKey.exe | C:\Users\admin\AppData\Local\Temp\WMlADAP.exe | executable | |
MD5:— | SHA256:— | |||
| 3036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3036.038\SearchKey\SearchKey.exe | executable | |
MD5:B8731F924034BDD7098547944BD6ECC4 | SHA256:D9D58D04E684BDE2237B785D78EB9B7B8F1581DDDCB796D31C523B63A0F5CB94 | |||
| 276 | SearchKey.exe | C:\Users\admin\AppData\Local\Temp\vms.exe | executable | |
MD5:42BA46496EF72FC3BD4E5DA798A57889 | SHA256:9F9140922DD951C9F2B19550B37F9B2A9E9F0E91EAE944D450985477D5215097 | |||
| 1168 | rnyuf.exe | C:\Users\admin\AppData\Local\Temp\152113020197 | image | |
MD5:— | SHA256:— | |||
| 3960 | vms.exe | C:\Users\admin\AppData\Local\Temp\5c436eadc6\rnyuf.exe | executable | |
MD5:42BA46496EF72FC3BD4E5DA798A57889 | SHA256:9F9140922DD951C9F2B19550B37F9B2A9E9F0E91EAE944D450985477D5215097 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
3
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1168 | rnyuf.exe | POST | 200 | 178.208.83.45:80 | http://depressionk1d.ug/k8FppT/index.php | RU | text | 6 b | malicious |
1168 | rnyuf.exe | POST | 200 | 178.208.83.45:80 | http://depressionk1d.ug/k8FppT/index.php?scr=1 | RU | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1168 | rnyuf.exe | 178.208.83.45:80 | depressionk1d.ug | Webzilla B.V. | RU | malicious |
276 | SearchKey.exe | 162.159.134.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
276 | SearchKey.exe | 185.244.217.139:59111 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
depressionk1d.ug |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1168 | rnyuf.exe | A Network Trojan was detected | ET TROJAN Amadey CnC Check-In |
1168 | rnyuf.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
1 ETPRO signatures available at the full report