| URL: | http://mail-bigfile.hiworks.biz/service/download/dbe8d94bd81ed9de846a3746bc06328fb8446d046f6f1f32827bb2442e1e8c38 |
| Full analysis: | https://app.any.run/tasks/387536c5-6bdb-467c-823b-bb6cb8dae389 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | December 19, 2023, 05:48:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6BA4BD9239EBC0880ED03061810D0627 |
| SHA1: | 1C7362E8C006A09804AEEFE88EB950E6DC480C17 |
| SHA256: | E5B451F801775ADBE0CBD65FA57C09D448A817E7246196C9FD5C26DE1835FFA1 |
| SSDEEP: | 3:N1KTDCx5AOMHxZK4mKBgH465SRLCTWNDBXdyEn:CB0uBgHr50DBt |
MALICIOUS
Drops the executable file immediately after the start
- powershell.exe (PID: 2168)
GULOADER has been detected (SURICATA)
- wab.exe (PID: 1384)
Steals credentials from Web Browsers
- wab.exe (PID: 952)
Actions looks like stealing of personal data
- wab.exe (PID: 2876)
- wab.exe (PID: 2880)
- wab.exe (PID: 952)
REMCOS has been detected (SURICATA)
- wab.exe (PID: 1384)
Steals credentials
- wab.exe (PID: 952)
- wab.exe (PID: 2880)
Uses NirSoft utilities to collect credentials
- wab.exe (PID: 952)
- wab.exe (PID: 2880)
SUSPICIOUS
Reads the Internet Settings
- ORDER#79956500027_20231219.com (PID: 1784)
- wab.exe (PID: 1384)
Starts POWERSHELL.EXE for commands execution
- ORDER#79956500027_20231219.com (PID: 1784)
Connects to the server without a host name
- wab.exe (PID: 1384)
Connects to unusual port
- wab.exe (PID: 1384)
Application launched itself
- wab.exe (PID: 1384)
Loads DLL from Mozilla Firefox
- wab.exe (PID: 2876)
Accesses Microsoft Outlook profiles
- wab.exe (PID: 2880)
INFO
Reads the computer name
- ORDER#79956500027_20231219.com (PID: 1784)
- wab.exe (PID: 1384)
- wab.exe (PID: 2876)
- wab.exe (PID: 2880)
- wab.exe (PID: 952)
The process uses the downloaded file
- WinRAR.exe (PID: 1864)
- iexplore.exe (PID: 2036)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1864)
Checks supported languages
- ORDER#79956500027_20231219.com (PID: 1784)
- wab.exe (PID: 1384)
- wab.exe (PID: 2880)
- wab.exe (PID: 952)
- wab.exe (PID: 2876)
Manual execution by a user
- ORDER#79956500027_20231219.com (PID: 1784)
- WINWORD.EXE (PID: 1992)
- chrome.exe (PID: 3040)
Application launched itself
- iexplore.exe (PID: 2036)
- chrome.exe (PID: 3040)
Creates files in the program directory
- ORDER#79956500027_20231219.com (PID: 1784)
Create files in a temporary directory
- ORDER#79956500027_20231219.com (PID: 1784)
- wab.exe (PID: 952)
- wab.exe (PID: 2876)
- wab.exe (PID: 2880)
Creates files or folders in the user directory
- ORDER#79956500027_20231219.com (PID: 1784)
- wab.exe (PID: 1384)
Checks proxy server information
- wab.exe (PID: 1384)
Reads the machine GUID from the registry
- wab.exe (PID: 1384)
- wab.exe (PID: 2876)
- wab.exe (PID: 952)
Reads product name
- wab.exe (PID: 1384)
Reads Environment values
- wab.exe (PID: 1384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
30
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --mojo-platform-channel-handle=2180 --field-trial-handle=1156,i,3523692383700943705,13714538708510562724,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Program Files\windows mail\wab.exe" /stext "C:\Users\admin\AppData\Local\Temp\fuzkefqfkhztmegvobtzjvzteh" | C:\Program Files\windows mail\wab.exe | wab.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1380 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3944 --field-trial-handle=1156,i,3523692383700943705,13714538708510562724,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\windows mail\wab.exe" | C:\Program Files\windows mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=4012 --field-trial-handle=1156,i,3523692383700943705,13714538708510562724,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1784 | "C:\Users\admin\Desktop\ORDER#79956500027_20231219.com" | C:\Users\admin\Desktop\ORDER#79956500027_20231219.com | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\사본(11) - ORDER#79956500027_20231219.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
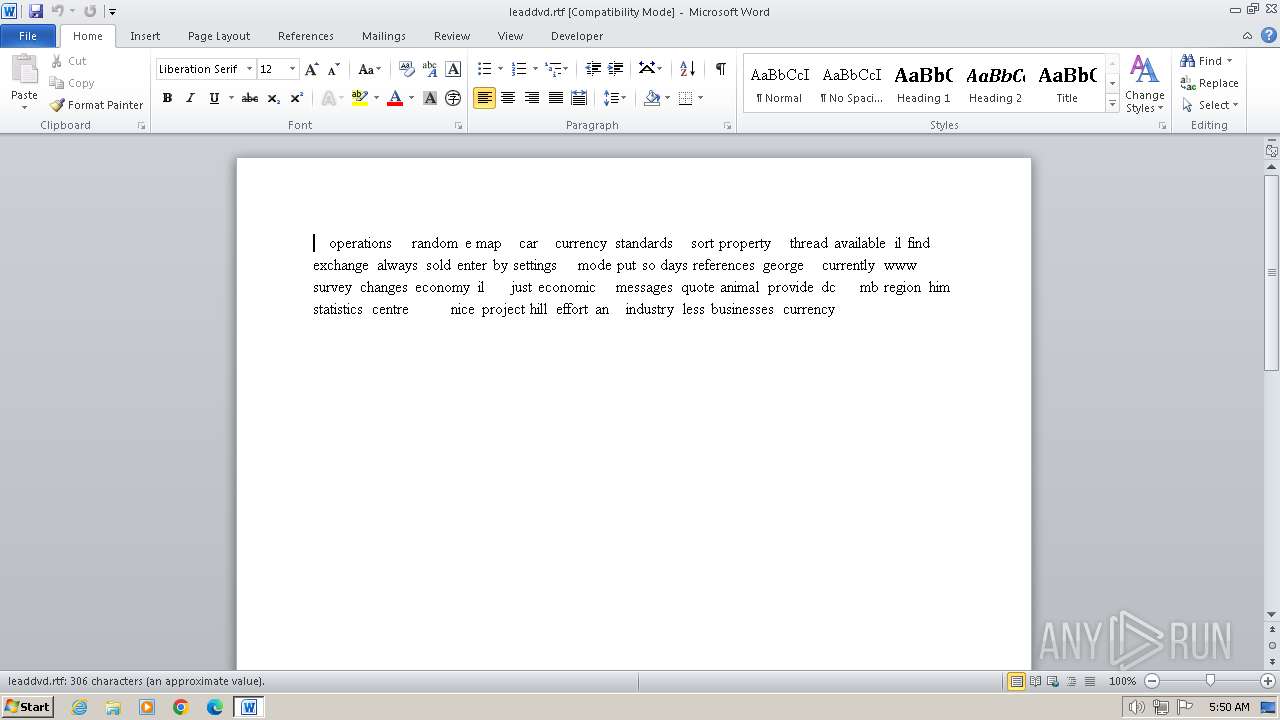
| 1992 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\leaddvd.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=2340 --field-trial-handle=1156,i,3523692383700943705,13714538708510562724,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://mail-bigfile.hiworks.biz/service/download/dbe8d94bd81ed9de846a3746bc06328fb8446d046f6f1f32827bb2442e1e8c38" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 382
Read events
17 048
Write events
186
Delete events
148
Modification events
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
3
Suspicious files
104
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFDCF45B46816E3CF.TMP | binary | |
MD5:69DD447F9DB915633C7D68F83A6A26BB | SHA256:210A0B990FCCBA10885ABD81EF636BC8FF1C4891965FBCC8007DB11F858AFECD | |||
| 2068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\사본(11)%20-%20ORDER#79956500027_20231219[1].zip | compressed | |
MD5:3464B4B924ADBDA3740363DECC9C89A3 | SHA256:2C03693377ECEDE4379F190859050D27D99879988E1E6B7FD737E5DFBE5223EE | |||
| 2036 | iexplore.exe | C:\Users\admin\Downloads\사본(11) - ORDER#79956500027_20231219.zip.yofcgvy.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.41443\ORDER#79956500027_20231219.com | executable | |
MD5:A61991F7B4B4DC37317D0EF860C9B70C | SHA256:5C30D414283FECBDD093B0231344C012A9A34F419DC02879D0A03ABA15D7E56B | |||
| 1784 | ORDER#79956500027_20231219.com | C:\Users\admin\AppData\Local\Temp\rubious\Paagribelsernes92\dagtures\Orddelingerne.Ari | binary | |
MD5:73E3AB6D5213AF174BDE45DEB2CE1DBB | SHA256:853A680980F537E138AE2E81BD471D9C699E2A667A7C33DEDF0691213B171885 | |||
| 2068 | iexplore.exe | C:\Users\admin\Downloads\사본(11) - ORDER#79956500027_20231219.zip.yofcgvy.partial | compressed | |
MD5:C1955D712A87EE33D91EEE11E7A2981C | SHA256:424D477B24663F6E2CDD68F4B7FC91A9F58056BB3D759F43C5B4F5A830D6087A | |||
| 2036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{432B0DB7-9E32-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:48BE9C225F9A799077F2B07B09C4185B | SHA256:093C256042FECDD1D788967AE9A39DB0EFC009898AC99B0A272D2585F521F7B0 | |||
| 1992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR95CE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2168 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1lqjf3fm.y50.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2168 | powershell.exe | C:\Users\admin\AppData\Local\Temp\l4nlti4h.pzx.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
36
DNS requests
30
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2068 | iexplore.exe | GET | 200 | 45.120.70.56:80 | http://mail-bigfile.hiworks.biz/service/download/dbe8d94bd81ed9de846a3746bc06328fb8446d046f6f1f32827bb2442e1e8c38 | unknown | compressed | 286 Kb | unknown |
2036 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ca04fd3518ca5bb7 | unknown | compressed | 4.66 Kb | unknown |
2036 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?914f352674d8023c | unknown | compressed | 4.66 Kb | unknown |
2036 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?22dec979149153ff | unknown | compressed | 4.66 Kb | unknown |
2036 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a414549a770d7263 | unknown | — | — | unknown |
1384 | wab.exe | GET | — | 146.70.79.70:80 | http://146.70.79.70/doditAmnAdSOdqGlRTzkqvo161.bin | unknown | — | — | unknown |
1384 | wab.exe | GET | 200 | 146.70.79.70:80 | http://146.70.79.70/doditAmnAdSOdqGlRTzkqvo161.bin | unknown | binary | 483 Kb | unknown |
1384 | wab.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | binary | 950 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2068 | iexplore.exe | 45.120.70.56:80 | mail-bigfile.hiworks.biz | LG DACOM Corporation | KR | unknown |
2036 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2036 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2036 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1384 | wab.exe | 146.70.79.70:80 | — | M247 Ltd | HK | unknown |
1384 | wab.exe | 146.70.79.70:27000 | — | M247 Ltd | HK | unknown |
1384 | wab.exe | 178.237.33.50:80 | geoplugin.net | Schuberg Philis B.V. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mail-bigfile.hiworks.biz |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
geoplugin.net |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1384 | wab.exe | A Network Trojan was detected | LOADER [ANY.RUN] GuLoader |
1384 | wab.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
1384 | wab.exe | A Network Trojan was detected | LOADER [ANY.RUN] GuLoader |
1384 | wab.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
1384 | wab.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x TLS Connection |
1384 | wab.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS JA3 Hash |
1384 | wab.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x TLS Connection |
1384 | wab.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS JA3 Hash |
3 ETPRO signatures available at the full report