analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| File name: | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264 |
| Full analysis: | https://app.any.run/tasks/f9b3380f-cfa4-42c5-bd40-ab070595d173 |
| Verdict: | Malicious activity |
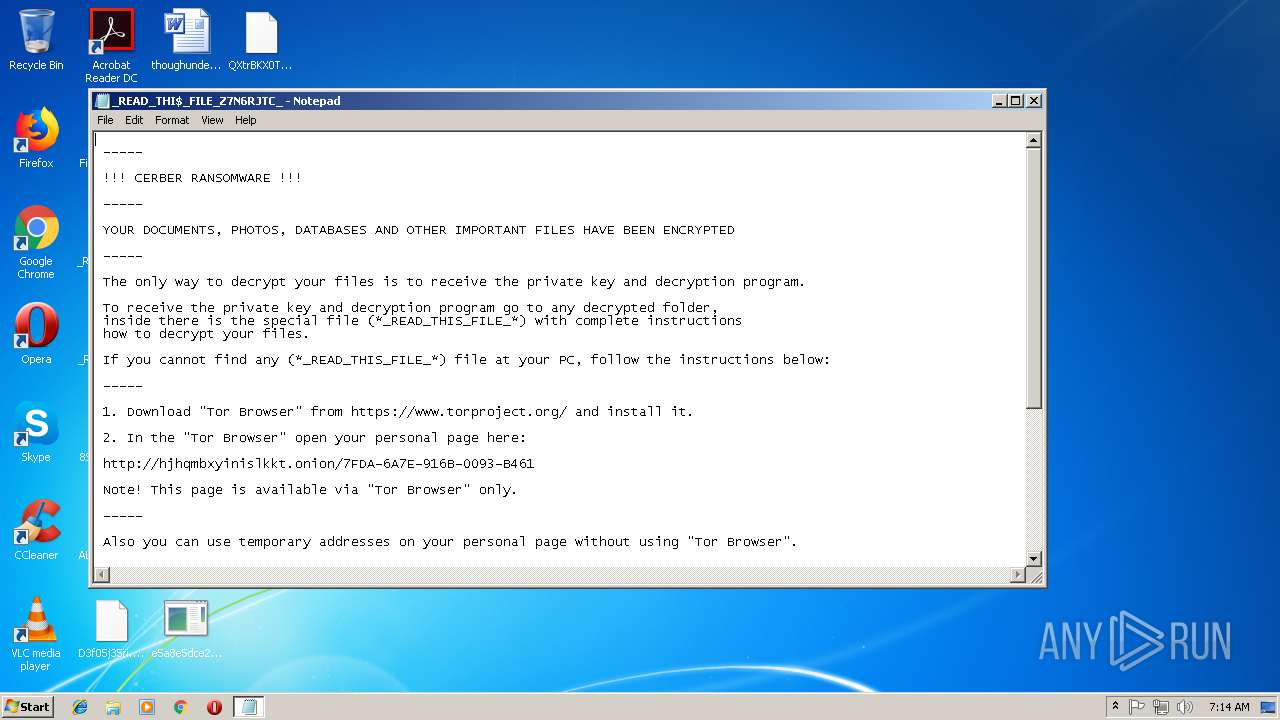
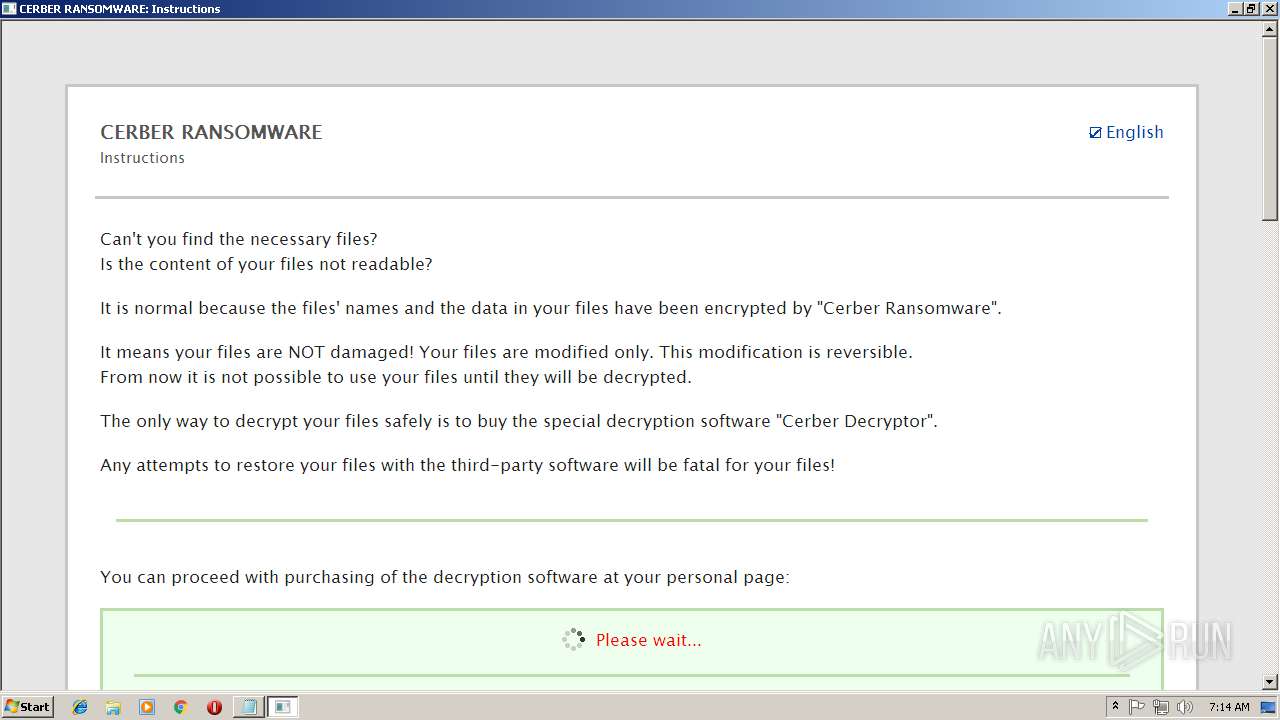
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | February 19, 2019, 07:13:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3393D55CC4782315F7F58DDB5095CBB6 |
| SHA1: | EE9CFBDB29546A2FAE8A0D73C72EAC5D1663C956 |
| SHA256: | E5A8E5DCE2E126E1A24E1253B67DADBBC4BDC4BA2F9B1332D09B8C5241881264 |
| SSDEEP: | 6144:8UrYZcL8lpmTNB6YkThb8Hnfby8dHlEL8DNd8:WZcA/mTPHWhQHnfW8fEL8Ji |
MALICIOUS
CERBER was detected
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Connects to CnC server
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Actions looks like stealing of personal data
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2352)
Runs app for hidden code execution
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Dropped file may contain instructions of ransomware
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
SUSPICIOUS
Uses NETSH.EXE for network configuration
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Creates files in the user directory
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Starts MSHTA.EXE for opening HTA or HTMLS files
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Starts CMD.EXE for commands execution
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2352)
INFO
Dropped object may contain Bitcoin addresses
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
- mshta.exe (PID: 2272)
Dropped object may contain URL to Tor Browser
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Dropped object may contain TOR URL's
- e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe (PID: 2940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | 5.1 |
| OSVersion: | 5.1 |
| EntryPoint: | 0x8836 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 9216 |
| CodeSize: | 257024 |
| LinkerVersion: | 10 |
| PEType: | PE32 |
| TimeStamp: | 2021:01:27 12:31:12+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Jan-2021 11:31:12 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000C0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 27-Jan-2021 11:31:12 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0003EB90 | 0x0003EC00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.83995 |
.data1 | 0x00040000 | 0x00000100 | 0x00000000 | IMAGE_SCN_MEM_WRITE | 0 |
.data | 0x00041000 | 0x00000B6E | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.9178 |
.rsrc | 0x00042000 | 0x000016D5 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.69973 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.9864 | 341 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.5 | 1024 | UNKNOWN | English - United States | IT |
3 | 3.5 | 1024 | UNKNOWN | English - United States | IT |
4 | 3.5 | 1024 | UNKNOWN | English - United States | IT |
Imports
dsprop.dll |
kernel32.dll |
odbctrac.dll |
shell32.dll |
shlwapi.dll |
Total processes
46
Monitored processes
10
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2940 | "C:\Users\admin\Desktop\e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe" | C:\Users\admin\Desktop\e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | explorer.exe | |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
| 3064 | C:\Windows\system32\netsh.exe advfirewall set allprofiles state on | C:\Windows\system32\netsh.exe | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3880 | C:\Windows\system32\netsh.exe advfirewall reset | C:\Windows\system32\netsh.exe | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3372 | C:\Windows\system32\netsh.exe advfirewall firewall add rule name="mQgMn7LCWG" dir=out action=block program="C:\Program Files\Windows Defender\MpCmdRun.exe" | C:\Windows\system32\netsh.exe | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3904 | C:\Windows\system32\netsh.exe advfirewall firewall add rule name="YWvVhA5dL5" dir=out action=block program="C:\Program Files\Windows Defender\MSASCui.exe" | C:\Windows\system32\netsh.exe | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2272 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\Desktop\_READ_THI$_FILE_ND34S_.hta" | C:\Windows\System32\mshta.exe | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft (R) HTML Application host Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 2520 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\_READ_THI$_FILE_Z7N6RJTC_.txt | C:\Windows\system32\NOTEPAD.EXE | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2352 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 3324 | taskkill /f /im "e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3528 | ping -n 1 127.0.0.1 | C:\Windows\system32\PING.EXE | — | cmd.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
327
Read events
146
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
3
Text files
22
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\appdata\roaming\microsoft\onenote\14.0\preferences.dat | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\appdata\roaming\microsoft\outlook\outlook.srs | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\constructionlet.rtf | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\onenote notebooks\personal\unfiled notes.one | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\outlook files\[email protected] | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\outlook files\outlook data file - test.pst | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\outlook files\outlook data file - nomail.pst | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\outlook files\outlook.pst | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\users\admin\documents\onenote notebooks\personal\general.one | — | |
MD5:— | SHA256:— | |||
| 2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | C:\Users\admin\AppData\Local\Temp\90059c37\41a4.tmp | text | |
MD5:7FDA6A7E916BE2AD32087C308A9902D9 | SHA256:7B284E45B3CBD8428912AAF9914F59BC0264E00F51537606DD4305F91DBD1133 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
2 170
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2272 | mshta.exe | GET | 200 | 52.2.101.52:80 | http://api.blockcypher.com/v1/btc/main/txs/1016d7ceff188e9fe32e68e9761bd811f354cfb31d7d106ec3c4f3ebce7f7a50?_=1550560453770 | US | text | 1.11 Kb | whitelisted |
2272 | mshta.exe | GET | 200 | 52.2.101.52:80 | http://api.blockcypher.com/v1/btc/main/addrs/1HTDy9SkfhwaNCXFA8wFCvN53f3iGpm8kb?_=1550560450239 | US | text | 15.7 Kb | whitelisted |
2272 | mshta.exe | GET | 404 | 104.199.222.174:80 | http://hjhqmbxyinislkkt.1j9r76.top/7FDA-6A7E-916B-0093-B461?iframe&_=1550560453942 | US | html | 1.35 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 94.21.172.8:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | 94.21.172.0:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | malicious |
— | — | 94.21.172.6:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.4:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.10:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.2:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.3:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.5:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.7:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | unknown |
— | — | 94.21.172.1:6893 | — | DIGI Tavkozlesi es Szolgaltato Kft. | HU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.blockcypher.com |
| whitelisted |
hjhqmbxyinislkkt.1j9r76.top |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2940 | e5a8e5dce2e126e1a24e1253b67dadbbc4bdc4ba2f9b1332d09b8c5241881264.exe | A Network Trojan was detected | ET TROJAN Ransomware/Cerber Checkin M3 (8) |
2272 | mshta.exe | A Network Trojan was detected | MALWARE [PTsecurity] Possible Cerber bitcoin activity |
2272 | mshta.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
2272 | mshta.exe | A Network Trojan was detected | MALWARE [PTsecurity] Possible Cerber bitcoin activity |
2272 | mshta.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
— | — | A Network Trojan was detected | ET TROJAN ABUSE.CH Ransomware/Cerber Onion Domain Lookup |
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2272 | mshta.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2272 | mshta.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
1 ETPRO signatures available at the full report