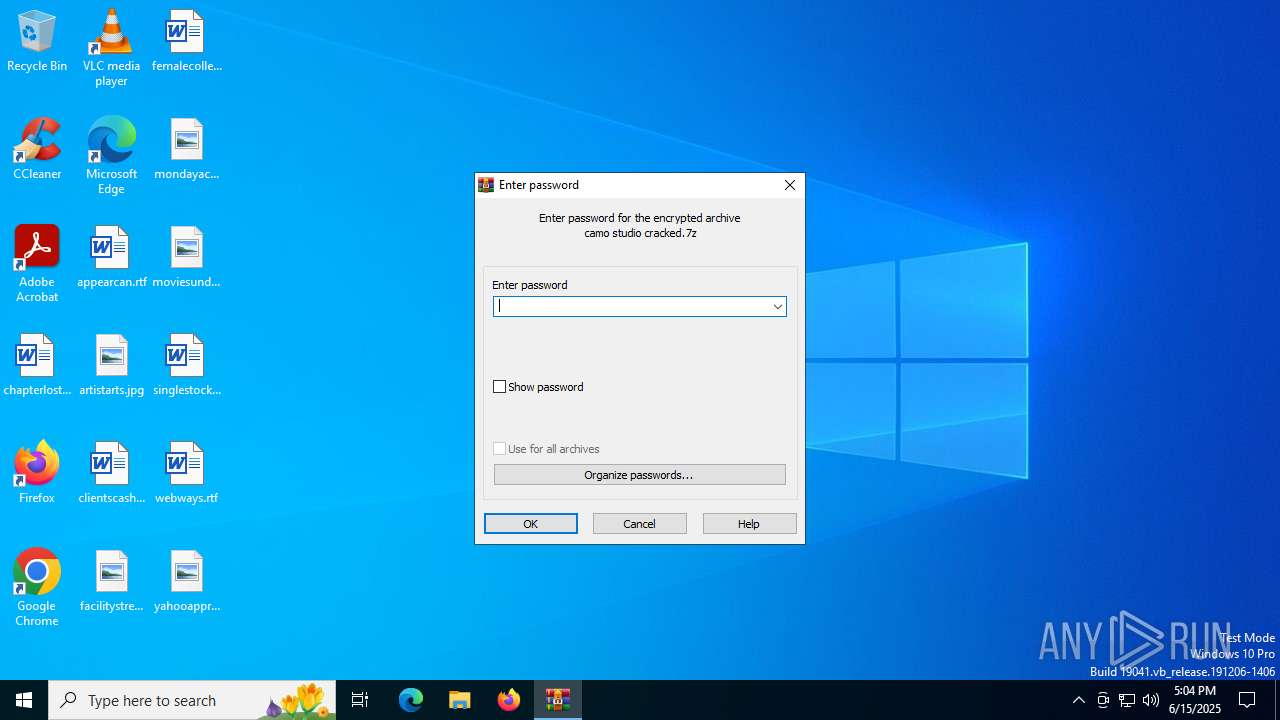
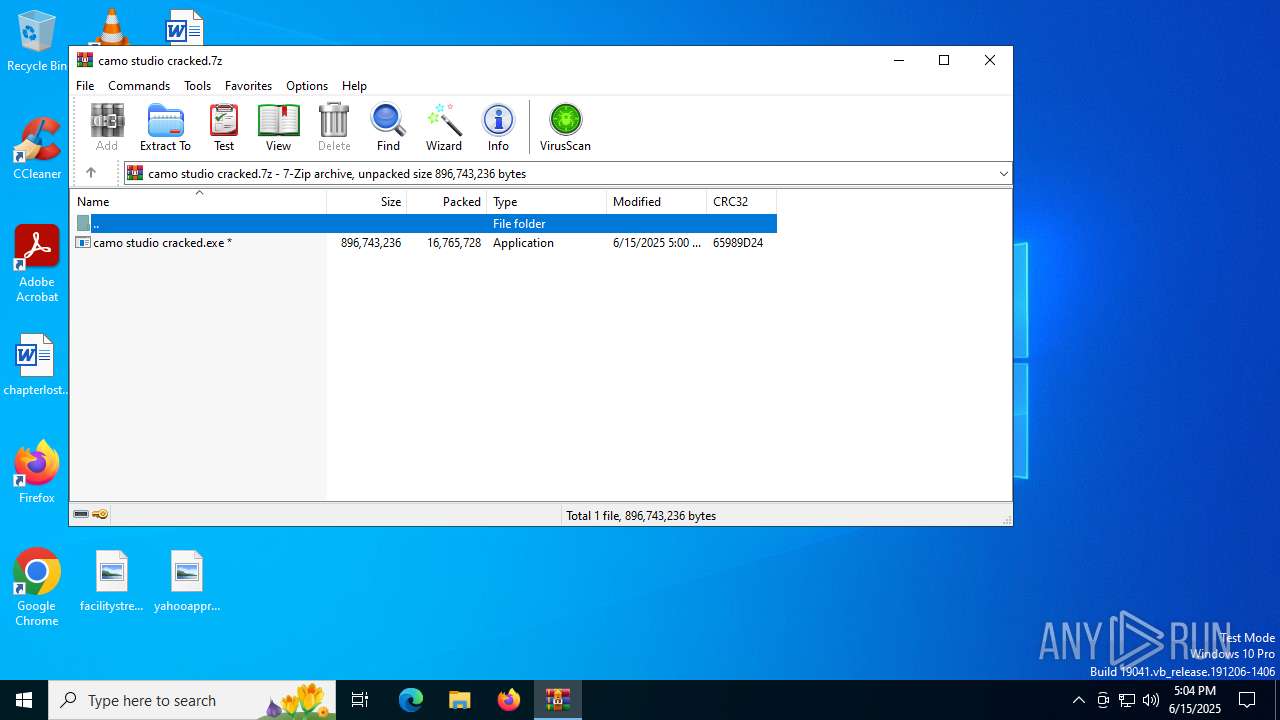
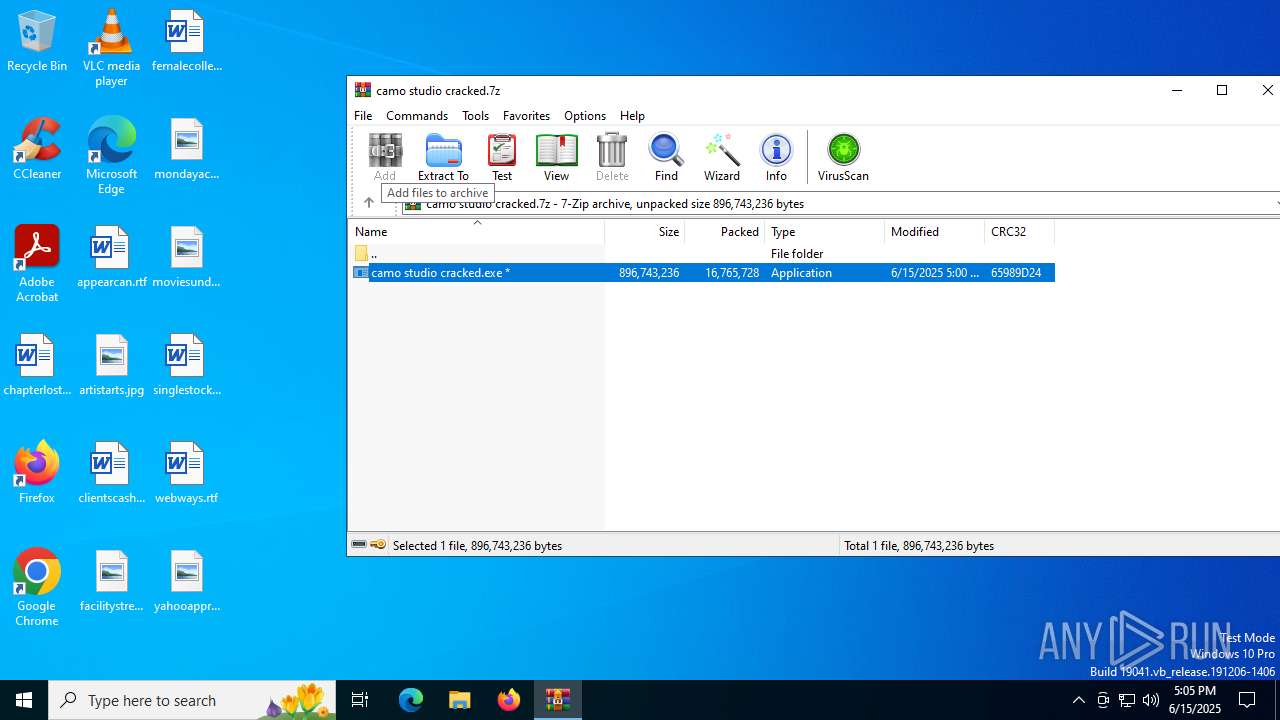
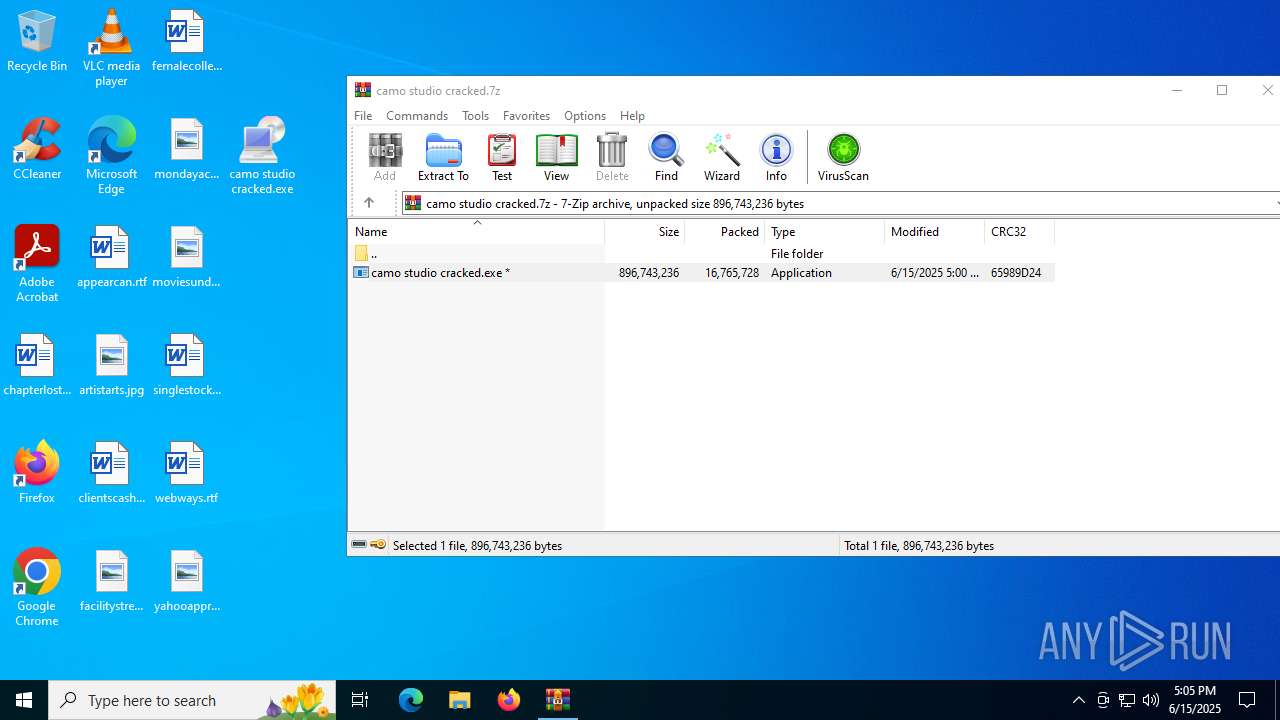
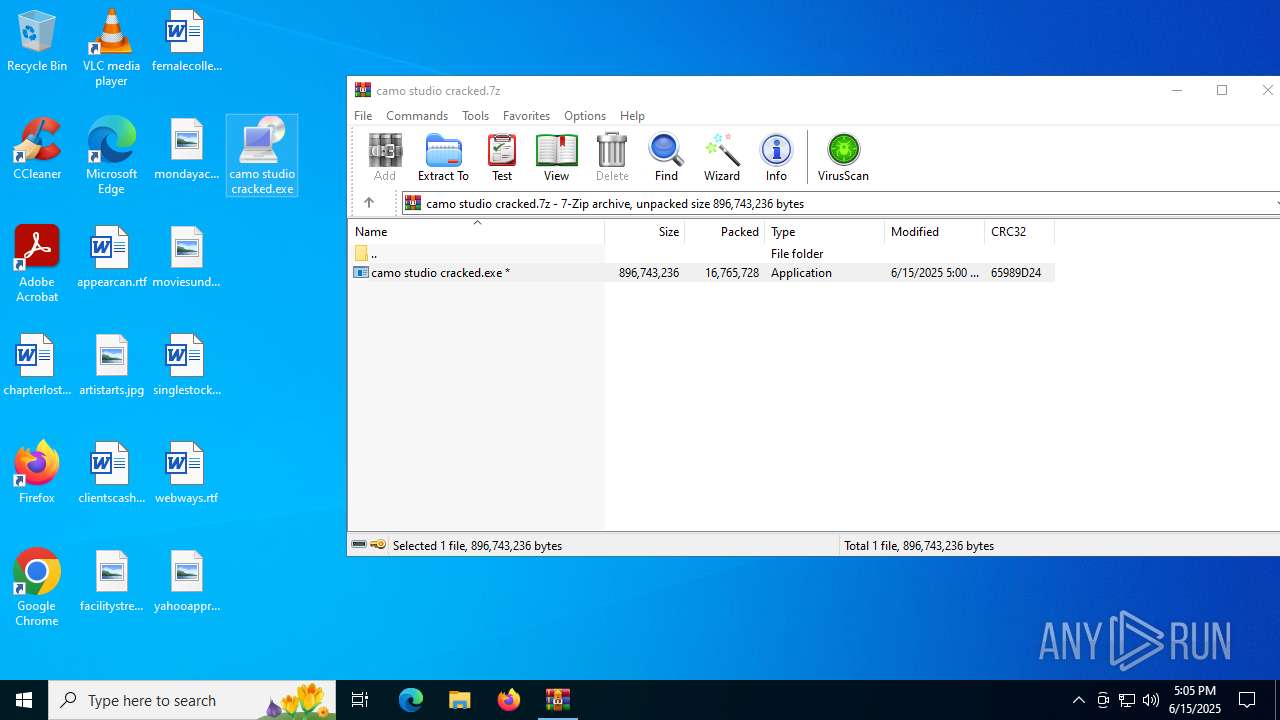
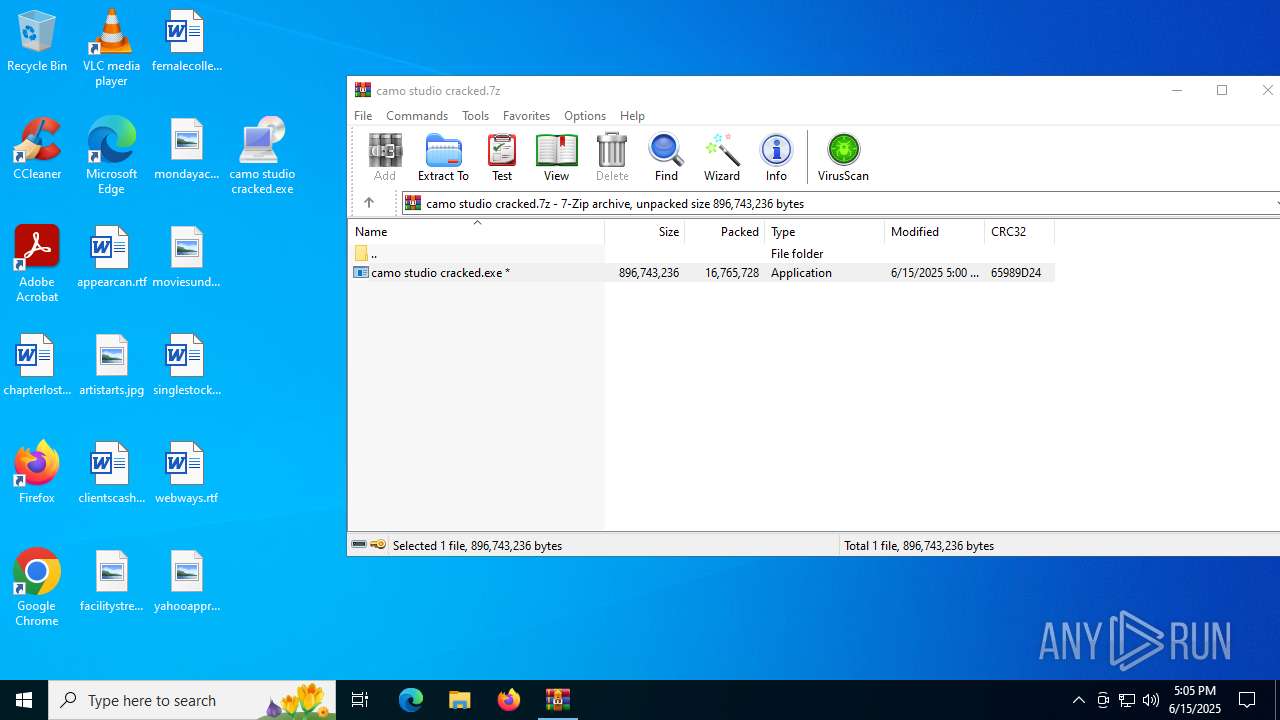
| File name: | camo studio cracked.7z |
| Full analysis: | https://app.any.run/tasks/aa5b7461-413d-46ac-876d-9c007f6334b9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 15, 2025, 17:04:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 957F81EAEC3816BDB52D76355C914C11 |
| SHA1: | 77CFE5F957997CF22D94A221D0F67F0230D77AA7 |
| SHA256: | E586964EC752140D430D8AC7520AA8F262EF66F94229BC8B1FB3C2CB59371243 |
| SSDEEP: | 196608:4jZszrrywcJlbJpHGodA/D2YZsvqSuFbR:umzrrWVG/AvqSkl |
MALICIOUS
AutoIt loader has been detected (YARA)
- Dam.com (PID: 2272)
LUMMA has been detected (YARA)
- Dam.com (PID: 2272)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 516)
- camo studio cracked.exe (PID: 4372)
Executing commands from a ".bat" file
- camo studio cracked.exe (PID: 4372)
- camo studio cracked.exe (PID: 4960)
- camo studio cracked.exe (PID: 2864)
- camo studio cracked.exe (PID: 7100)
- camo studio cracked.exe (PID: 4808)
- camo studio cracked.exe (PID: 2524)
Starts CMD.EXE for commands execution
- camo studio cracked.exe (PID: 4372)
- camo studio cracked.exe (PID: 4960)
- camo studio cracked.exe (PID: 2864)
- camo studio cracked.exe (PID: 7100)
- camo studio cracked.exe (PID: 4808)
- camo studio cracked.exe (PID: 2524)
Get information on the list of running processes
- cmd.exe (PID: 7108)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 2320)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7108)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 2320)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7108)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 2320)
Starts application with an unusual extension
- cmd.exe (PID: 7108)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 2320)
The executable file from the user directory is run by the CMD process
- Dam.com (PID: 4920)
- Dam.com (PID: 2272)
- Dam.com (PID: 2804)
- Dam.com (PID: 4984)
- Dam.com (PID: 7000)
- Dam.com (PID: 3780)
There is functionality for taking screenshot (YARA)
- camo studio cracked.exe (PID: 4372)
- camo studio cracked.exe (PID: 4960)
- Dam.com (PID: 2272)
- camo studio cracked.exe (PID: 2864)
INFO
Create files in a temporary directory
- camo studio cracked.exe (PID: 4372)
- extrac32.exe (PID: 5904)
Reads the computer name
- camo studio cracked.exe (PID: 4372)
- extrac32.exe (PID: 5904)
- Dam.com (PID: 4920)
Checks supported languages
- camo studio cracked.exe (PID: 4372)
- extrac32.exe (PID: 5904)
- Dam.com (PID: 4920)
Process checks computer location settings
- camo studio cracked.exe (PID: 4372)
Reads mouse settings
- Dam.com (PID: 4920)
Manual execution by a user
- camo studio cracked.exe (PID: 2864)
- camo studio cracked.exe (PID: 4960)
- camo studio cracked.exe (PID: 7100)
- camo studio cracked.exe (PID: 4808)
- camo studio cracked.exe (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
202
Monitored processes
65
Malicious processes
5
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\camo studio cracked.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1028 | findstr "bdservicehost SophosHealth AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | findstr "bdservicehost SophosHealth AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | findstr "bdservicehost SophosHealth AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2272 | Dam.com s | C:\Users\admin\AppData\Local\Temp\528171\Dam.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 2296 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\WINDOWS\system32\cmd.exe" /c copy Useful.wav Useful.wav.bat & Useful.wav.bat | C:\Windows\SysWOW64\cmd.exe | — | camo studio cracked.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 144
Read events
8 135
Write events
9
Delete events
0
Modification events
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\camo studio cracked.7z | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
24
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb516.39259\camo studio cracked.exe | — | |
MD5:— | SHA256:— | |||
| 4372 | camo studio cracked.exe | C:\Users\admin\AppData\Local\Temp\Quoted.wav | binary | |
MD5:F8F34F8AF1470DD2946F40A4557BC500 | SHA256:44988EDFF430DBA33835302B5B2DAA6BB8BDE8149B1FCEB460F27D0AB06C97D3 | |||
| 4372 | camo studio cracked.exe | C:\Users\admin\AppData\Local\Temp\Azerbaijan.wav | compressed | |
MD5:EF6031560EE1035E6476D0678E645FAD | SHA256:E23950C205022DBE497732A8A99AE4FB81D5B7D22A18FE363678C97DC3E408EE | |||
| 4372 | camo studio cracked.exe | C:\Users\admin\AppData\Local\Temp\Understanding.wav | binary | |
MD5:0B7E858D3A35890D57130331B5DE6E0D | SHA256:FABE74E4139AD2F0D574C711030DB4D03F818DC4958F0077D74AAB274B8EA079 | |||
| 516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb516.41345\camo studio cracked.exe | — | |
MD5:— | SHA256:— | |||
| 4372 | camo studio cracked.exe | C:\Users\admin\AppData\Local\Temp\Useful.wav | text | |
MD5:6D29AEC55426101D552468296853D471 | SHA256:C9B8D5355F2F7ABD49C3E8513F88B733CB62DAE3933CD8CAE904499CC8219A5B | |||
| 4372 | camo studio cracked.exe | C:\Users\admin\AppData\Local\Temp\Sunset.wav | binary | |
MD5:C4F5BDF1BE29008F0835C1DB4167AB56 | SHA256:9ACCCDD1327A1BBA4DB8215FF5F11CFF518128BD405585D52F6CEC66117826C3 | |||
| 4372 | camo studio cracked.exe | C:\Users\admin\AppData\Local\Temp\Puts.wav | binary | |
MD5:9E4498ECA5076451684ABD546629D17C | SHA256:B2E285EFA63A5AA77D9AD04A8E6A5CDC75253AFA6CED04C9D9B3672B9E73F851 | |||
| 5904 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Visit | binary | |
MD5:D5F5FA75BCBB0E9AFD00A1D4F2638073 | SHA256:7F2C9B1F66C04473596A18BB74F92C2A75ECB00627CB8F354D571D4E9C6DE0CC | |||
| 5904 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Contemporary | binary | |
MD5:65E7DDD7AD535913864F7E4F04FA4AAE | SHA256:8AE30F48C869562C196BC13F0C8C135A1FE6AB3A839426B09D0056C2521C6F34 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
43
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7164 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4804 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4804 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2468 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7164 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7164 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
VNrIvKwkcUq.VNrIvKwkcUq |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4920 | Dam.com | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 42 |