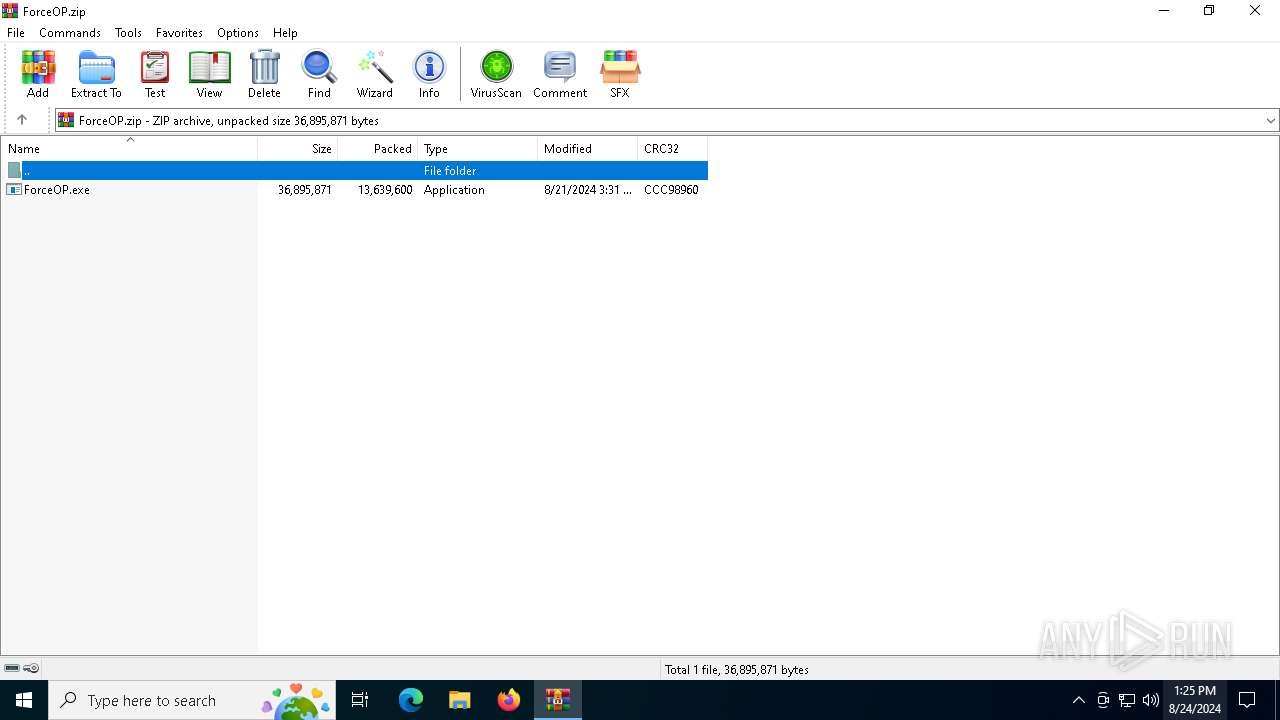
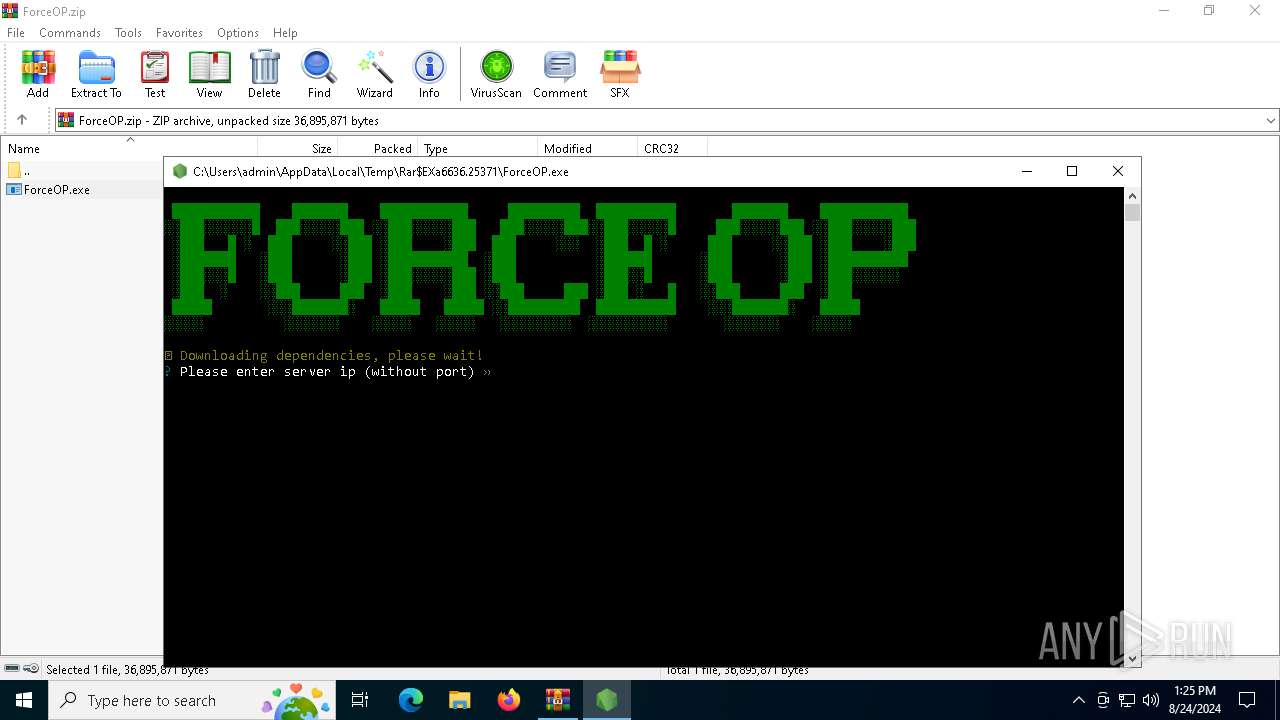
| File name: | ForceOP.zip |
| Full analysis: | https://app.any.run/tasks/16e30ff4-06c9-4daf-bd16-81e1c146d372 |
| Verdict: | Malicious activity |
| Threats: | NanoCore is a Remote Access Trojan or RAT. This malware is highly customizable with plugins which allow attackers to tailor its functionality to their needs. Nanocore is created with the .NET framework and it’s available for purchase for just $25 from its “official” website. |
| Analysis date: | August 24, 2024, 13:25:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 899AF6CB1BBBCC8116EFD2DBDBE04291 |
| SHA1: | 4FF14D716AA34148082C93BF58F58577F8F313A6 |
| SHA256: | E52C41A8A4BBADDA9866E7E1FC9E15417A2F1146FF9E2B392C48A74B78FABF74 |
| SSDEEP: | 98304:I3vfe39VtwRBly99BSWBX8QyxiUNN7p54UL8Tdsi2XYmGGVPee4reFc7sAm6r4oH:Sx+iFKvqmXai7ky8+V8z8f |
MALICIOUS
NjRAT is detected
- fiucinajestemsliczny.exe (PID: 7024)
- server.exe (PID: 7092)
Changes the autorun value in the registry
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Uses Task Scheduler to run other applications
- fiucinajestembrzydki.exe (PID: 6532)
NANOCORE has been detected (SURICATA)
- fiucinajestembrzydki.exe (PID: 6532)
Create files in the Startup directory
- server.exe (PID: 7092)
Connects to the CnC server
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
NJRAT has been detected (SURICATA)
- server.exe (PID: 7092)
NANOCORE has been detected (YARA)
- fiucinajestembrzydki.exe (PID: 6532)
NJRAT has been detected (YARA)
- server.exe (PID: 7092)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6636)
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 7144)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6636)
- ForceOP.exe (PID: 6780)
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Node.exe was dropped
- WinRAR.exe (PID: 6636)
Starts CMD.EXE for commands execution
- ForceOP.exe (PID: 6780)
The executable file from the user directory is run by the CMD process
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 7144)
Executable content was dropped or overwritten
- fiucinajestemsliczny.exe (PID: 7024)
- ForceOP.exe (PID: 6780)
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Reads the date of Windows installation
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestemsliczny.exe (PID: 7024)
Starts itself from another location
- fiucinajestemsliczny.exe (PID: 7024)
The process creates files with name similar to system file names
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 7092)
Application launched itself
- fiucinajestembrzydki.exe (PID: 7144)
Connects to unusual port
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Contacting a server suspected of hosting an CnC
- server.exe (PID: 7092)
- fiucinajestembrzydki.exe (PID: 6532)
INFO
Reads product name
- ForceOP.exe (PID: 6780)
- fiucinajestembrzydki.exe (PID: 6532)
Checks supported languages
- ForceOP.exe (PID: 6780)
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 7144)
- server.exe (PID: 7092)
- fiucinajestembrzydki.exe (PID: 6532)
Reads Environment values
- ForceOP.exe (PID: 6780)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Create files in a temporary directory
- ForceOP.exe (PID: 6780)
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 6532)
Reads the computer name
- ForceOP.exe (PID: 6780)
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Creates files or folders in the user directory
- ForceOP.exe (PID: 6780)
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Process checks computer location settings
- fiucinajestemsliczny.exe (PID: 7024)
- fiucinajestembrzydki.exe (PID: 7144)
Reads the machine GUID from the registry
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
- server.exe (PID: 7092)
Process checks whether UAC notifications are on
- fiucinajestembrzydki.exe (PID: 7144)
- fiucinajestembrzydki.exe (PID: 6532)
Creates files in the program directory
- fiucinajestembrzydki.exe (PID: 6532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(7092) server.exe
C2193.203.238.87
Ports5552
BotnetForceOP
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\bcd46e84d58aceecbf4188e8c7c796f8
Splitter|'|'|
Version0.7d
Nanocore
(PID) Process(6532) fiucinajestembrzydki.exe
KeyboardLoggingTrue
BuildTime2024-08-19 19:33:16.671608
Version1.2.2.0
Mutex58426eb7-12b3-40a8-8660-d8b12f469708
DefaultGroupDefault
PrimaryConnectionHost193.203.238.87
BackupConnectionHost127.0.0.1
ConnectionPort54984
RunOnStartupTrue
RequestElevationTrue
BypassUserAccountControlTrue
ClearZoneIdentifierTrue
ClearAccessControlTrue
SetCriticalProcessTrue
PreventSystemSleepTrue
ActivateAwayModeTrue
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8021
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:21 17:31:24 |
| ZipCRC: | 0xccc98960 |
| ZipCompressedSize: | 13639600 |
| ZipUncompressedSize: | 36895871 |
| ZipFileName: | ForceOP.exe |
Total processes
140
Monitored processes
15
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | "schtasks.exe" /create /f /tn "LAN Host" /xml "C:\Users\admin\AppData\Local\Temp\tmp213C.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | fiucinajestembrzydki.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6296 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\server.exe" "server.exe" ENABLE | C:\Windows\SysWOW64\netsh.exe | — | server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6532 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\fiucinajestembrzydki.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\fiucinajestembrzydki.exe | fiucinajestembrzydki.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
Nanocore(PID) Process(6532) fiucinajestembrzydki.exe KeyboardLoggingTrue BuildTime2024-08-19 19:33:16.671608 Version1.2.2.0 Mutex58426eb7-12b3-40a8-8660-d8b12f469708 DefaultGroupDefault PrimaryConnectionHost193.203.238.87 BackupConnectionHost127.0.0.1 ConnectionPort54984 RunOnStartupTrue RequestElevationTrue BypassUserAccountControlTrue ClearZoneIdentifierTrue ClearAccessControlTrue SetCriticalProcessTrue PreventSystemSleepTrue ActivateAwayModeTrue EnableDebugModeFalse RunDelay0 ConnectDelay4000 RestartDelay5000 TimeoutInterval5000 KeepAliveTimeout30000 MutexTimeout5000 LanTimeout2500 WanTimeout8021 BufferSize65535 MaxPacketSize10485760 GCThreshold10485760 UseCustomDnsServerTrue PrimaryDnsServer8.8.8.8 BackupDnsServer8.8.4.4 | |||||||||||||||
| 6556 | "schtasks.exe" /create /f /tn "LAN Host Task" /xml "C:\Users\admin\AppData\Local\Temp\tmp21BA.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | fiucinajestembrzydki.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6636 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\ForceOP.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6780 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6636.25371\ForceOP.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6636.25371\ForceOP.exe | WinRAR.exe | ||||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js JavaScript Runtime Version: 16.16.0 Modules
| |||||||||||||||
| 6788 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ForceOP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 260
Read events
15 117
Write events
142
Delete events
1
Modification events
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ForceOP.zip | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6636) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
7
Suspicious files
5
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6636.25371\ForceOP.exe | — | |
MD5:— | SHA256:— | |||
| 6780 | ForceOP.exe | C:\Users\admin\AppData\Local\Temp\pkg\1a0a9582c7f361685569cf47e056b1fc4deb3bfa8bdf729de8cf27a57aa06508\win-protect\test\test.js | text | |
MD5:9E083BE46CE876015F8854743F2E8CA0 | SHA256:9393F9C36F7A2CACCBBF9FFCBED74107B38202757D35BC79EAA7D2F33C314982 | |||
| 6780 | ForceOP.exe | C:\Users\admin\AppData\Local\Temp\pkg\1a0a9582c7f361685569cf47e056b1fc4deb3bfa8bdf729de8cf27a57aa06508\win-protect\package.json | binary | |
MD5:E6D0104162966F2C8F6ABAE03B70C109 | SHA256:EA2DE5C4E08B132970E2BC6B09DFC478C89348FC6D820D3DEEB6FA94F03E7D54 | |||
| 6780 | ForceOP.exe | C:\Users\admin\AppData\Local\Temp\pkg\1a0a9582c7f361685569cf47e056b1fc4deb3bfa8bdf729de8cf27a57aa06508\win-protect\src\addon.cpp | text | |
MD5:CB81295486C009B4D089602364975B2A | SHA256:901761E595A351EA9542C939C810BC9F8F6AEA41350A29C360E5997DD8C7D863 | |||
| 6780 | ForceOP.exe | C:\Users\admin\AppData\Local\Temp\pkg\1a0a9582c7f361685569cf47e056b1fc4deb3bfa8bdf729de8cf27a57aa06508\win-protect\index.js | binary | |
MD5:D292EAE897DE7CD0245F2A78830D7F31 | SHA256:BF198C4AEC01941198104A49DAEAA606CEA4A5B1A2B014BCC2AD9FD519954372 | |||
| 7024 | fiucinajestemsliczny.exe | C:\Users\admin\AppData\Local\Temp\server.exe | executable | |
MD5:F0349A2A58FFB90CED78F56799D89134 | SHA256:4F2A25CF342D307C4EA544A945049CFFDEB248A1FC230CFA538B2BE37283F5BA | |||
| 6780 | ForceOP.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\fiucinajestembrzydki.exe | executable | |
MD5:4757E3957A66009DDA083E0CEB0C1605 | SHA256:3DDF341BB96D5CB94DA122B59B38D655EBD8DEAC277FCAA9244246F7E131AB04 | |||
| 6780 | ForceOP.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\fiucinajestemsliczny.exe | executable | |
MD5:F0349A2A58FFB90CED78F56799D89134 | SHA256:4F2A25CF342D307C4EA544A945049CFFDEB248A1FC230CFA538B2BE37283F5BA | |||
| 7144 | fiucinajestembrzydki.exe | C:\Users\admin\AppData\Roaming\BB926E54-E3CA-40FD-AE90-2764341E7792\run.dat | binary | |
MD5:E9FBB016D64FB8FD2F658E27C9BD9DB5 | SHA256:1D645D8ED5E0DAAE48367E1D92F110BBB777D18A3B13888C34B6EAB45A61C2D2 | |||
| 7144 | fiucinajestembrzydki.exe | C:\Users\admin\AppData\Roaming\BB926E54-E3CA-40FD-AE90-2764341E7792\LAN Host\lanhost.exe | executable | |
MD5:4757E3957A66009DDA083E0CEB0C1605 | SHA256:3DDF341BB96D5CB94DA122B59B38D655EBD8DEAC277FCAA9244246F7E131AB04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
30
DNS requests
16
Threats
52
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7012 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3276 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5464 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2096 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5464 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6780 | ForceOP.exe | 49.12.218.71:443 | 20tz.web.svpj.pl | Hetzner Online GmbH | DE | unknown |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3276 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
20tz.web.svpj.pl |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT Keep-Alive Beacon (Inbound) |
7092 | server.exe | A Network Trojan was detected | ET MALWARE Possible Host Profile Exfiltration In Pipe Delimited Format |
7092 | server.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT Keep-Alive Beacon (Inbound) |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT Keep-Alive Beacon (Inbound) |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
6532 | fiucinajestembrzydki.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT Keep-Alive Beacon (Inbound) |
4 ETPRO signatures available at the full report