| File name: | e52a7f4ecb39233d0ed9d2f3762b8eea376c0aee63a2c2785f9428abd86bdacb |
| Full analysis: | https://app.any.run/tasks/b0d6a83d-3458-4ff1-8f01-081f4ea912b6 |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | January 22, 2019, 18:55:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 697594C989A5246E79E87F26A2B017D6 |
| SHA1: | 4E4E03D19DC83D4E6875B1D510476D691FEEC1BE |
| SHA256: | E52A7F4ECB39233D0ED9D2F3762B8EEA376C0AEE63A2C2785F9428ABD86BDACB |
| SSDEEP: | 12288:q7LKiA7Eq98OlxmQL+oVu1agnsKrTf16rLKnZO2IMB+G3OnPlrfeHOSKDY2:q7LKvl5BVuD1MIZO2IMxOntrf0JKDB |
MALICIOUS
Changes the autorun value in the registry
- wscript.exe (PID: 3844)
- reg.exe (PID: 3368)
AdWind was detected
- java.exe (PID: 3116)
- java.exe (PID: 2920)
Loads dropped or rewritten executable
- java.exe (PID: 3116)
- javaw.exe (PID: 3048)
- wscript.exe (PID: 3844)
- svchost.exe (PID: 816)
- javaw.exe (PID: 3744)
- java.exe (PID: 2920)
- javaw.exe (PID: 2260)
- explorer.exe (PID: 116)
Application was dropped or rewritten from another process
- java.exe (PID: 3116)
- javaw.exe (PID: 2260)
- javaw.exe (PID: 3744)
- javaw.exe (PID: 3048)
- java.exe (PID: 2920)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2720)
Executes JAVA applets
- explorer.exe (PID: 116)
- wscript.exe (PID: 3844)
- javaw.exe (PID: 3048)
Creates files in the user directory
- wscript.exe (PID: 3844)
- javaw.exe (PID: 3048)
- xcopy.exe (PID: 1020)
Executes scripts
- javaw.exe (PID: 2260)
- cmd.exe (PID: 3908)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 2412)
- cmd.exe (PID: 2276)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 972)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 2420)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3048)
- java.exe (PID: 3116)
- javaw.exe (PID: 3744)
- java.exe (PID: 2920)
Executable content was dropped or overwritten
- xcopy.exe (PID: 1020)
- javaw.exe (PID: 3744)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 3048)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 3048)
Starts itself from another location
- javaw.exe (PID: 3048)
Connects to unusual port
- javaw.exe (PID: 3744)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | None |
| ZipModifyDate: | 2019:01:21 10:48:19 |
| ZipCRC: | 0x3980ba4e |
| ZipCompressedSize: | 640376 |
| ZipUncompressedSize: | 640376 |
| ZipFileName: | IMG-5896.jar |
Total processes
78
Monitored processes
32
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 816 | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8857195918072811227.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | xcopy "C:\Program Files\Java\jre1.8.0_92" "C:\Users\admin\AppData\Roaming\Oracle\" /e | C:\Windows\system32\xcopy.exe | javaw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2112 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive7046335480606464315.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\IMG-5896.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2276 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive680067020343172162.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2292 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8679424248253826522.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2352 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive5577896707906818885.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2412 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive7393812441069251454.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 188
Read events
2 122
Write events
66
Delete events
0
Modification events
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\e52a7f4ecb39233d0ed9d2f3762b8eea376c0aee63a2c2785f9428abd86bdacb.zip | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
113
Suspicious files
12
Text files
75
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive8679424248253826522.vbs | — | |
MD5:— | SHA256:— | |||
| 3116 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive7393812441069251454.vbs | — | |
MD5:— | SHA256:— | |||
| 2260 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
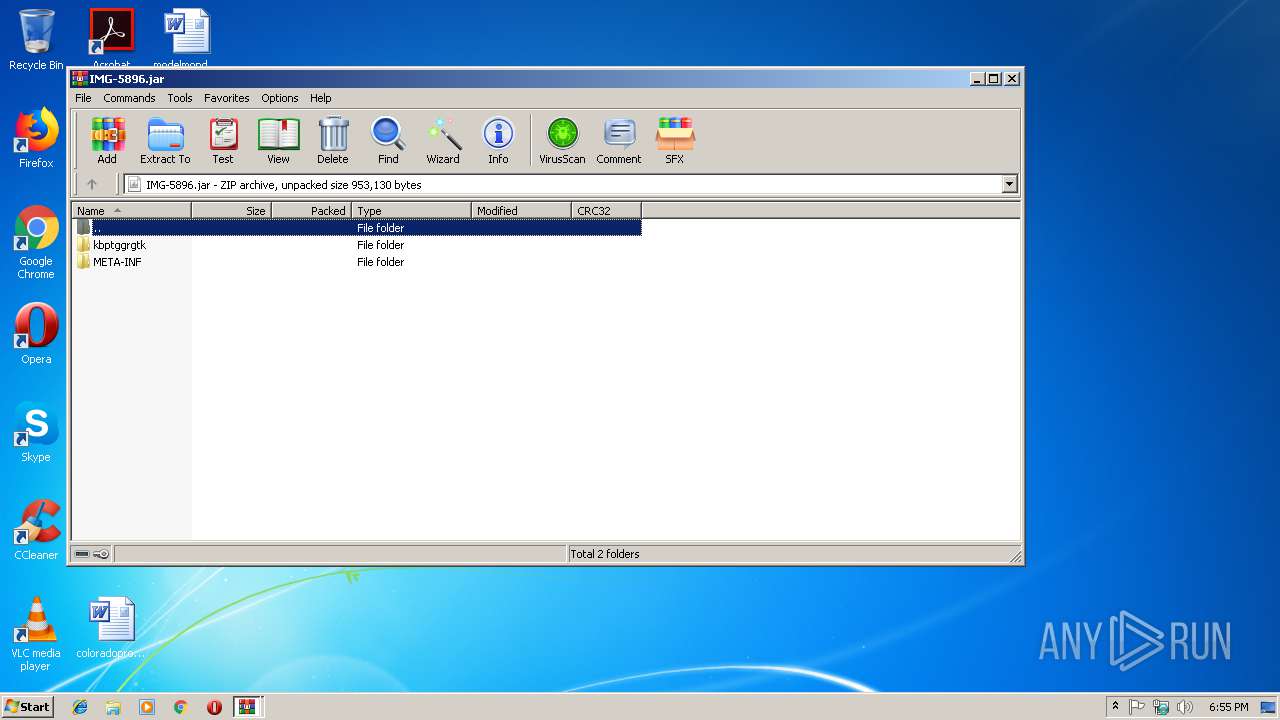
| 116 | explorer.exe | C:\Users\admin\Desktop\IMG-5896.jar | compressed | |
MD5:— | SHA256:— | |||
| 3844 | wscript.exe | C:\Users\admin\AppData\Roaming\efqbwyyun.txt | java | |
MD5:— | SHA256:— | |||
| 3116 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2260 | javaw.exe | C:\Users\admin\ccfwuebzgr.js | text | |
MD5:— | SHA256:— | |||
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2720.34519\IMG-5896.jar | compressed | |
MD5:— | SHA256:— | |||
| 3048 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive5577896707906818885.vbs | text | |
MD5:3BDFD33017806B85949B6FAA7D4B98E4 | SHA256:9DA575DD2D5B7C1E9BAB8B51A16CDE457B3371C6DCDB0537356CF1497FA868F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
40
DNS requests
4
Threats
9
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3744 | javaw.exe | 92.38.86.175:1337 | vitlop.ddns.net | ALFA TELECOM s.r.o. | CZ | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vitlop.ddns.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
3744 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |