| download: | /Pyran1/MalwareDatabase/raw/master/Backdoor/DarkCometRAT/967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.zip |
| Full analysis: | https://app.any.run/tasks/f5e3719a-fa03-47ec-9bf4-bc74d354f8e7 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | July 05, 2024, 18:12:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
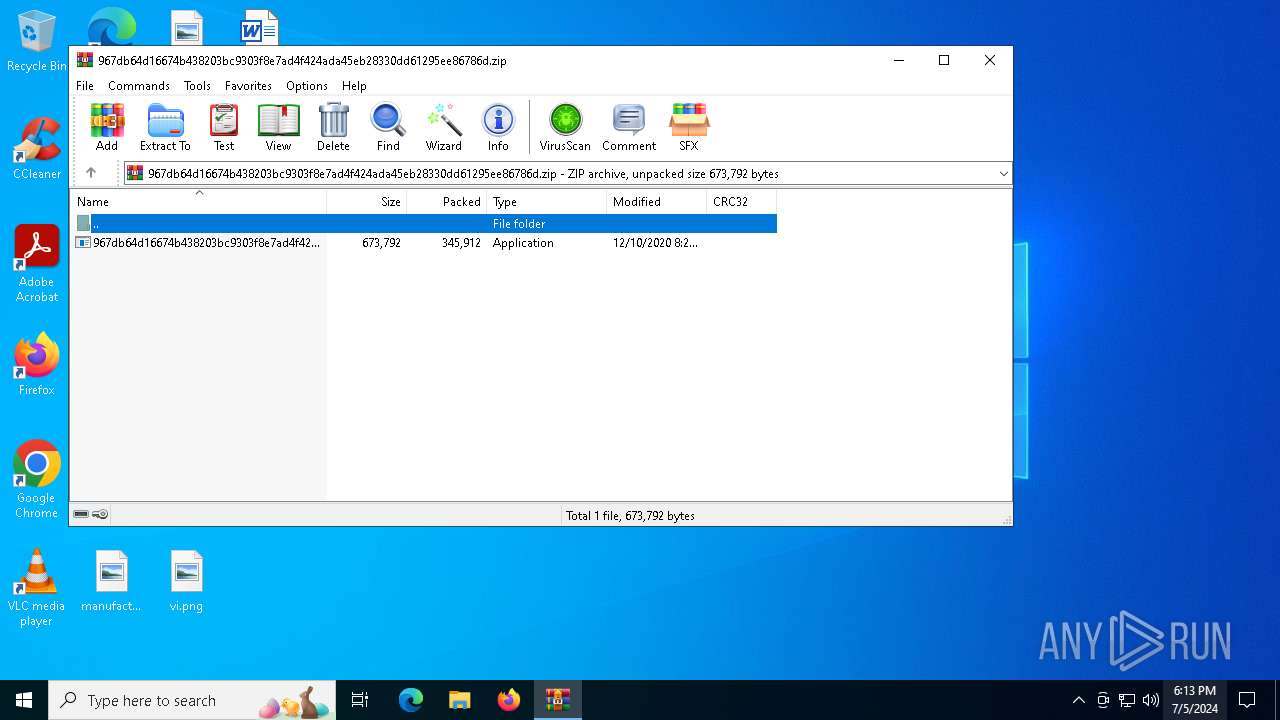
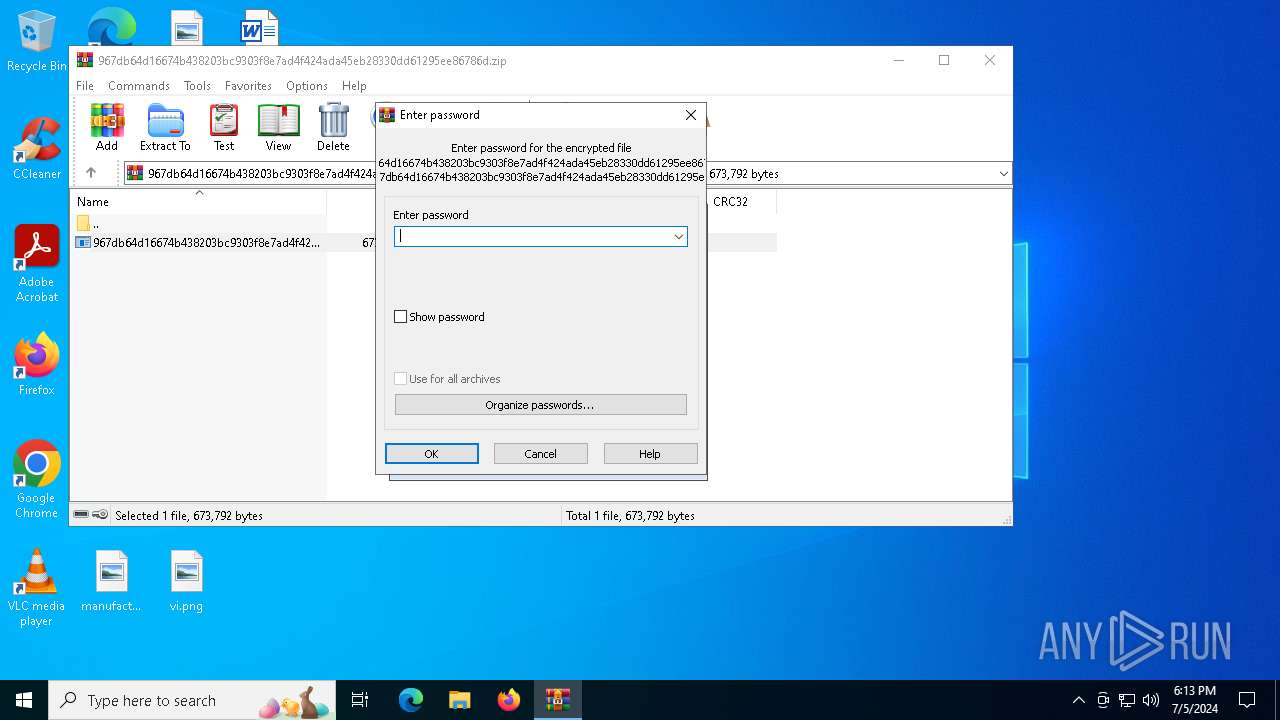
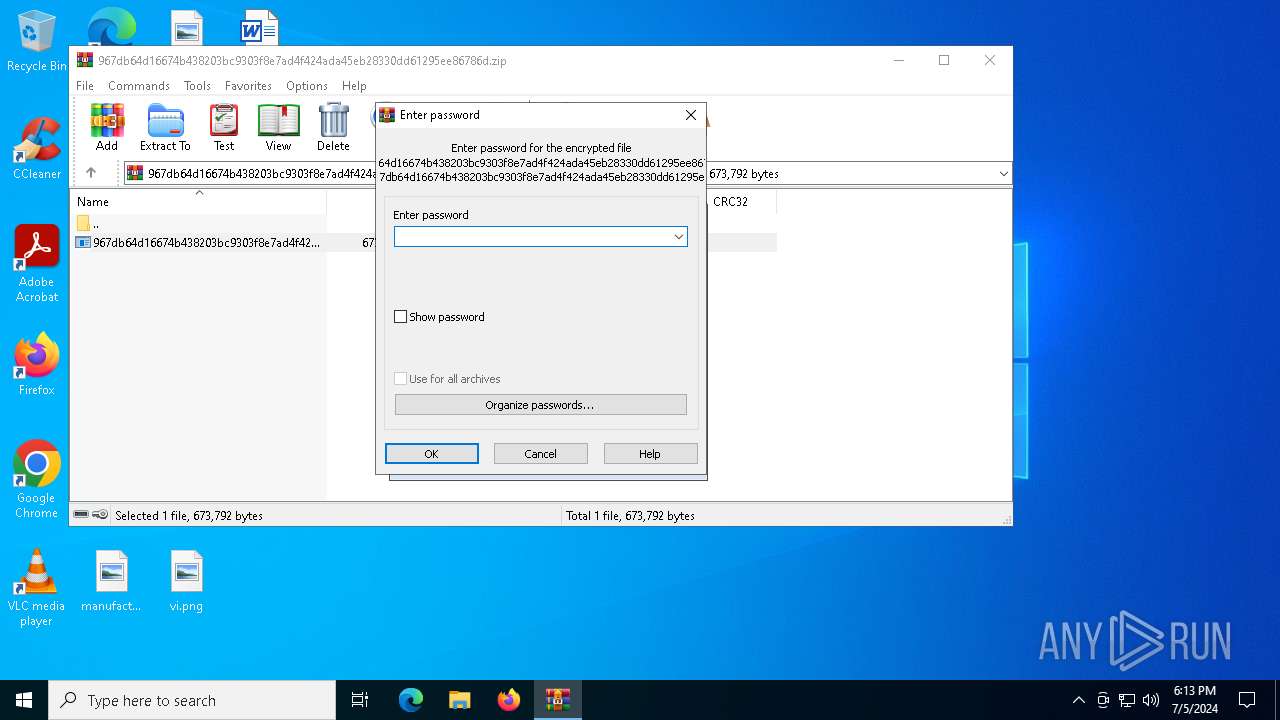
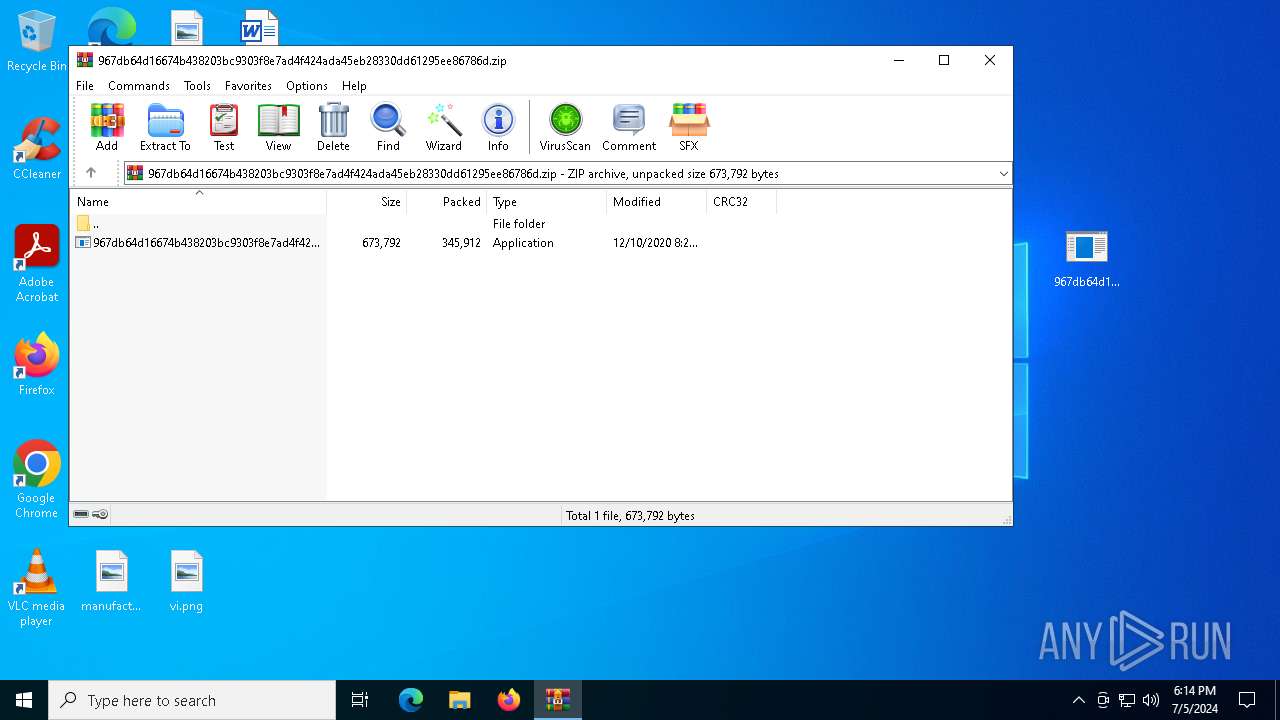
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 5AD9B600ED0ADDC5E132F2E40459203C |
| SHA1: | 168194CF94B30A0DD17C11216E610D50946054A0 |
| SHA256: | E526D7E14BF4D6242841EEE0F5687CB83D4E051F5F4686E7F399B9238ABC8BBF |
| SSDEEP: | 12288:Qco/uTMPAvuL3dAyN+AIvmpMBU1bRVABtoWNNnaf5i2O9t6:Qco2TbA36o+AympMB0bRVABto4NAgR94 |
MALICIOUS
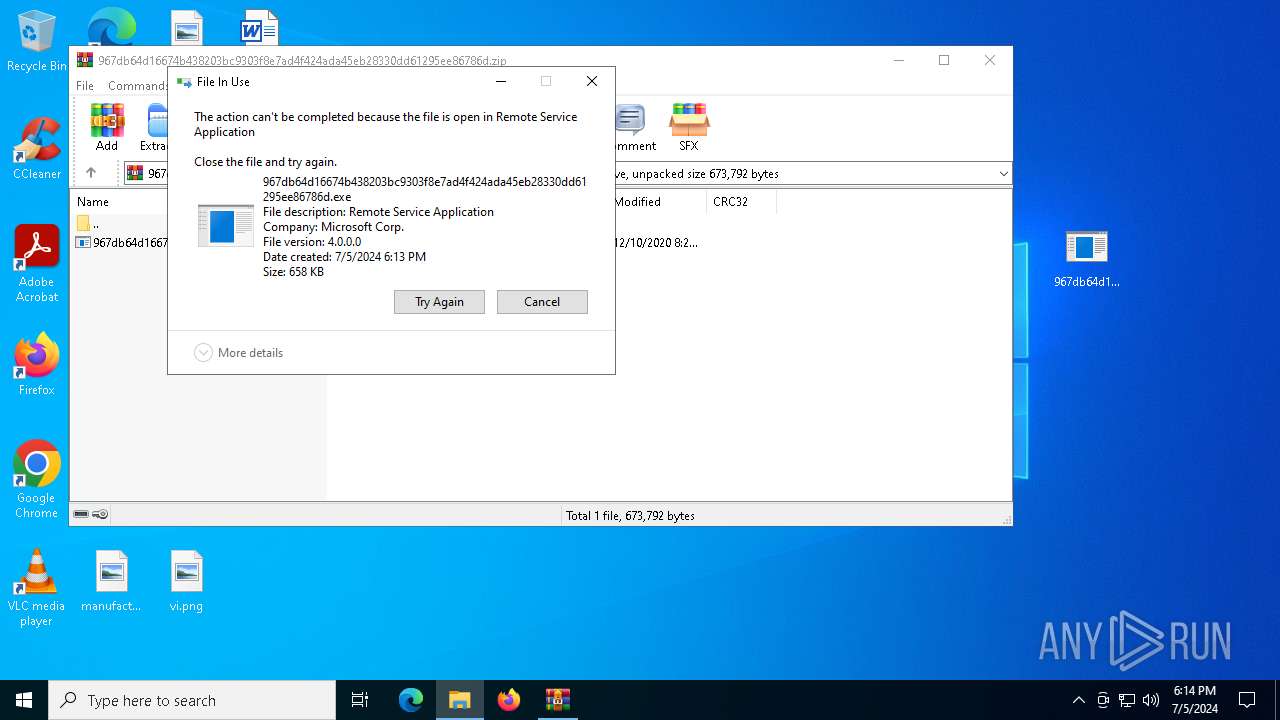
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1452)
DARKCOMET has been detected (YARA)
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
SUSPICIOUS
Connects to unusual port
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
There is functionality for taking screenshot (YARA)
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
There is functionality for communication over UDP network (YARA)
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
INFO
Checks supported languages
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
Reads the computer name
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1452)
Manual execution by a user
- 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe (PID: 3832)
Reads the software policy settings
- slui.exe (PID: 6224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:12:10 20:24:12 |
| ZipCRC: | 0x5428caec |
| ZipCompressedSize: | 345912 |
| ZipUncompressedSize: | 673792 |
| ZipFileName: | 967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe |
Total processes
143
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3832 | "C:\Users\admin\Desktop\967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe" | C:\Users\admin\Desktop\967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 6224 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6304 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 814
Read events
4 792
Write events
22
Delete events
0
Modification events
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.zip | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1452.49877\967db64d16674b438203bc9303f8e7ad4f424ada45eb28330dd61295ee86786d.exe | executable | |
MD5:0344D9439A0ABEFC67C14A8DF8C5CC98 | SHA256:967DB64D16674B438203BC9303F8E7AD4F424ADA45EB28330DD61295EE86786D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
67
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5680 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5680 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4180 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6420 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5824 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6500 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5824 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5680 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2196 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4180 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5680 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5680 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
5680 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |