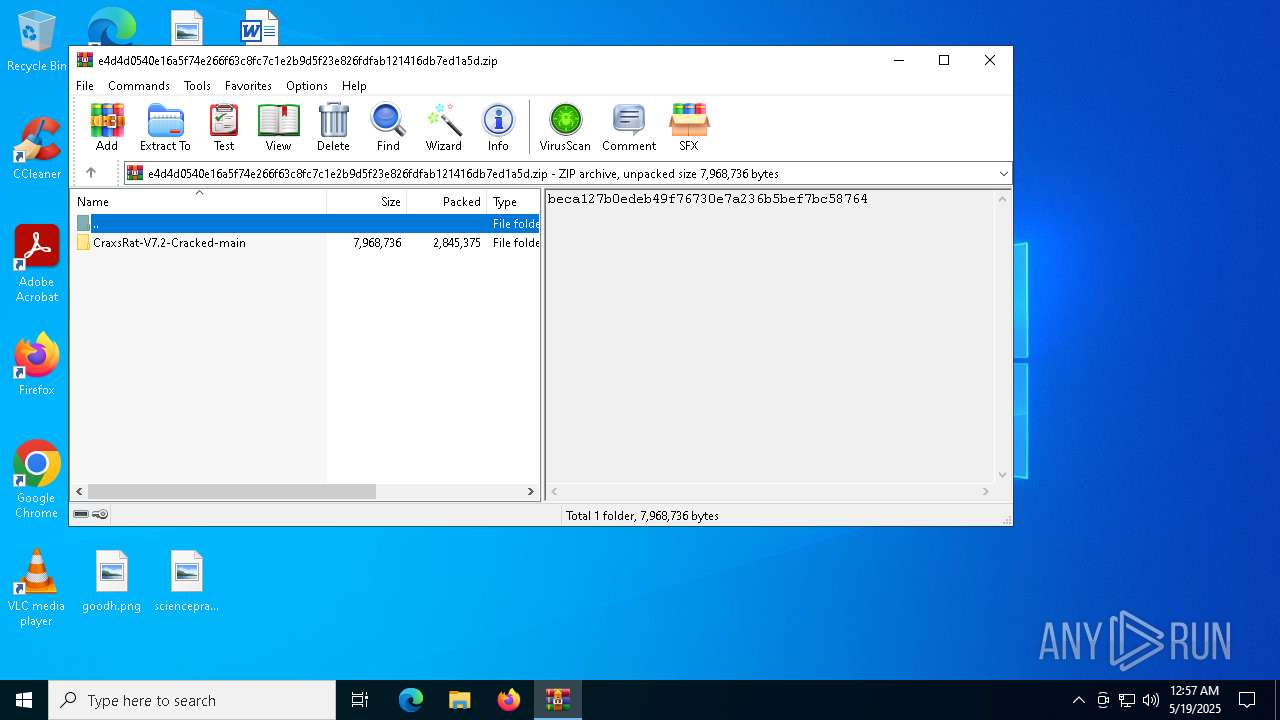
| File name: | e4d4d0540e16a5f74e266f63c8fc7c1e2b9d5f23e826fdfab121416db7ed1a5d |
| Full analysis: | https://app.any.run/tasks/6c0e3e27-027b-4b90-bb01-b42cd106b9f0 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 19, 2025, 00:57:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 7607B22FCAD9F33A7A0CB81E5B6450DF |
| SHA1: | EC17C6E2F3F8D467CFCB8DD7757B63091A151817 |
| SHA256: | E4D4D0540E16A5F74E266F63C8FC7C1E2B9D5F23E826FDFAB121416DB7ED1A5D |
| SSDEEP: | 98304:DAyiG0IaLt28T7dj/u949SaKBL3XkETykuJxsshtziCs4PIblR4EXHMuKjkeppuO:cCW22r |
MALICIOUS
Changes Windows Defender settings
- cmd.exe (PID: 2088)
- explorer.exe (PID: 5492)
Changes settings for real-time protection
- powershell.exe (PID: 5112)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 2088)
- explorer.exe (PID: 5492)
Run PowerShell with an invisible window
- powershell.exe (PID: 5112)
Uses Task Scheduler to autorun other applications
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
Uses Task Scheduler to run other applications
- chrome.exe (PID: 6136)
- explorer.exe (PID: 5492)
Changes the autorun value in the registry
- chrome.exe (PID: 6136)
Application was injected by another process
- svchost.exe (PID: 1044)
- svchost.exe (PID: 1232)
- svchost.exe (PID: 1252)
- lsass.exe (PID: 756)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 468)
- svchost.exe (PID: 1288)
- svchost.exe (PID: 1352)
- svchost.exe (PID: 1416)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 1444)
- svchost.exe (PID: 1524)
- svchost.exe (PID: 2172)
- svchost.exe (PID: 1652)
- svchost.exe (PID: 1552)
- svchost.exe (PID: 2544)
- svchost.exe (PID: 1772)
- svchost.exe (PID: 1792)
- svchost.exe (PID: 1892)
- svchost.exe (PID: 2068)
- svchost.exe (PID: 1988)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 2536)
- svchost.exe (PID: 1904)
- svchost.exe (PID: 2448)
- svchost.exe (PID: 2584)
- svchost.exe (PID: 2292)
- svchost.exe (PID: 2396)
- svchost.exe (PID: 2196)
- svchost.exe (PID: 2624)
- svchost.exe (PID: 2932)
- spoolsv.exe (PID: 2732)
- svchost.exe (PID: 2880)
- svchost.exe (PID: 3184)
- dasHost.exe (PID: 3012)
- svchost.exe (PID: 2776)
- svchost.exe (PID: 4292)
- svchost.exe (PID: 3216)
- svchost.exe (PID: 3232)
- svchost.exe (PID: 3284)
- svchost.exe (PID: 3196)
- OfficeClickToRun.exe (PID: 3112)
- svchost.exe (PID: 3104)
- svchost.exe (PID: 3564)
- svchost.exe (PID: 860)
- svchost.exe (PID: 4508)
- svchost.exe (PID: 3812)
- svchost.exe (PID: 3860)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 4312)
- svchost.exe (PID: 2112)
- svchost.exe (PID: 6024)
- svchost.exe (PID: 1572)
- MoUsoCoreWorker.exe (PID: 5496)
- sihost.exe (PID: 4984)
- uhssvc.exe (PID: 648)
- winlogon.exe (PID: 6648)
- svchost.exe (PID: 1684)
- dwm.exe (PID: 6568)
- RuntimeBroker.exe (PID: 6160)
- explorer.exe (PID: 5492)
- svchost.exe (PID: 6608)
- dllhost.exe (PID: 6896)
- UserOOBEBroker.exe (PID: 1248)
- dllhost.exe (PID: 5880)
- svchost.exe (PID: 4544)
- svchost.exe (PID: 4952)
- ctfmon.exe (PID: 956)
- dllhost.exe (PID: 6176)
- audiodg.exe (PID: 6168)
- svchost.exe (PID: 4684)
- ApplicationFrameHost.exe (PID: 6952)
- svchost.exe (PID: 6180)
- svchost.exe (PID: 6544)
- svchost.exe (PID: 4916)
- svchost.exe (PID: 4348)
- SppExtComObj.Exe (PID: 2140)
- svchost.exe (PID: 3364)
- slui.exe (PID: 5576)
- svchost.exe (PID: 4844)
- svchost.exe (PID: 6240)
- svchost.exe (PID: 2560)
- WmiPrvSE.exe (PID: 7804)
- RuntimeBroker.exe (PID: 7680)
- WmiPrvSE.exe (PID: 8004)
- RuntimeBroker.exe (PID: 5368)
- RuntimeBroker.exe (PID: 1036)
- WerFault.exe (PID: 7756)
- svchost.exe (PID: 5196)
- svchost.exe (PID: 3396)
- WerFault.exe (PID: 1004)
Runs injected code in another process
- dialer.exe (PID: 1040)
- dialer.exe (PID: 2384)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
Vulnerable driver has been detected
- updater.exe (PID: 7952)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5364)
Reads security settings of Internet Explorer
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- chrome.exe (PID: 6136)
Reads the date of Windows installation
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- chrome.exe (PID: 6136)
Executing commands from a ".bat" file
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
Starts CMD.EXE for commands execution
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- explorer.exe (PID: 5492)
The process hide an interactive prompt from the user
- cmd.exe (PID: 2088)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2088)
- explorer.exe (PID: 5492)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 2088)
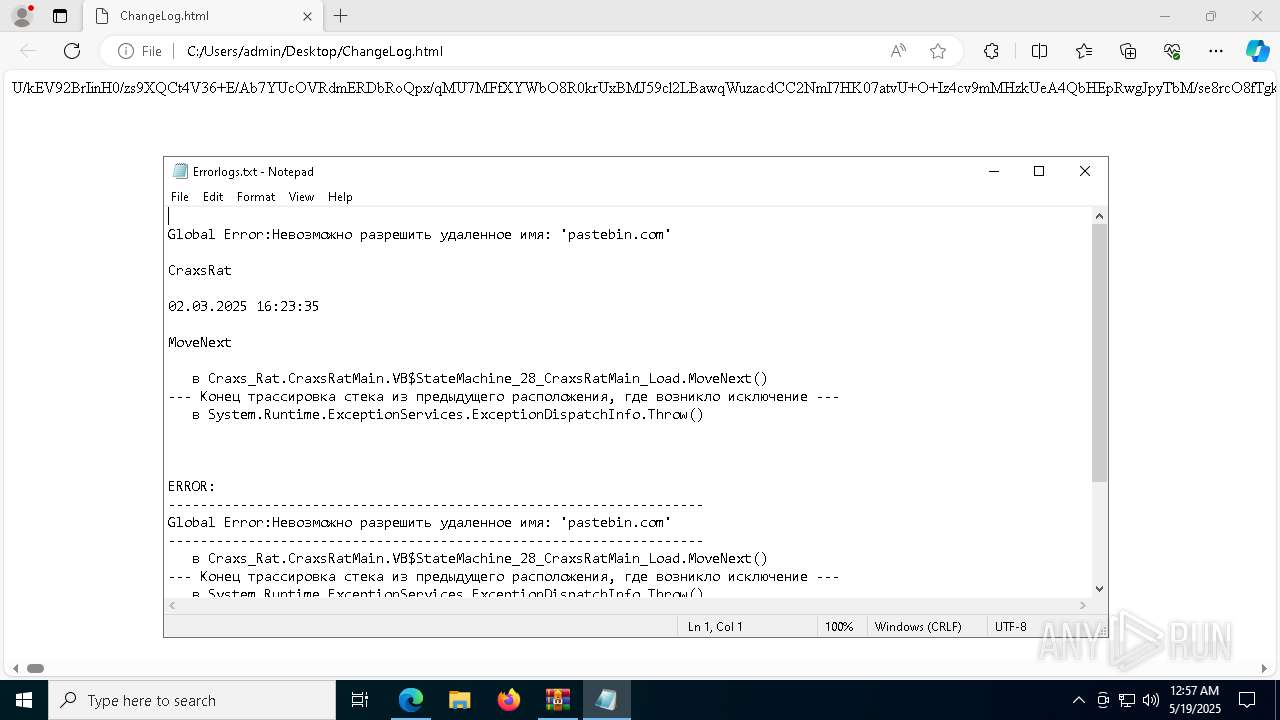
Downloads file from URI via Powershell
- powershell.exe (PID: 5112)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2088)
Starts process via Powershell
- powershell.exe (PID: 5112)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 2088)
- explorer.exe (PID: 5492)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 2088)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 5492)
Executable content was dropped or overwritten
- powershell.exe (PID: 5112)
- chrome.exe (PID: 5772)
- x2.exe (PID: 5436)
- updater.exe (PID: 7952)
Starts itself from another location
- chrome.exe (PID: 5772)
Creates file in the systems drive root
- chrome.exe (PID: 6136)
Checks for external IP
- svchost.exe (PID: 2196)
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
Connects to unusual port
- chrome.exe (PID: 6136)
Manipulates environment variables
- powershell.exe (PID: 7508)
- powershell.exe (PID: 7652)
Starts SC.EXE for service management
- cmd.exe (PID: 1348)
- cmd.exe (PID: 7824)
Stops a currently running service
- sc.exe (PID: 4620)
- sc.exe (PID: 7928)
- sc.exe (PID: 1228)
- sc.exe (PID: 4784)
- sc.exe (PID: 1164)
- sc.exe (PID: 6476)
- sc.exe (PID: 1600)
- sc.exe (PID: 924)
- sc.exe (PID: 2332)
- sc.exe (PID: 6208)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7552)
The process executes via Task Scheduler
- updater.exe (PID: 7952)
- chrome.exe (PID: 5412)
- chrome.exe (PID: 1128)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 7952)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Executes application which crashes
- chrome.exe (PID: 5412)
- chrome.exe (PID: 1128)
INFO
Manual execution by a user
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 5392)
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- msedge.exe (PID: 2908)
- OpenWith.exe (PID: 8168)
- rundll32.exe (PID: 7220)
- OpenWith.exe (PID: 7524)
- msedge.exe (PID: 6080)
- notepad.exe (PID: 7568)
- notepad.exe (PID: 7856)
- chrome.exe (PID: 812)
- powershell.exe (PID: 7508)
- cmd.exe (PID: 1348)
- chrome.exe (PID: 1240)
- dialer.exe (PID: 1040)
- schtasks.exe (PID: 7552)
- schtasks.exe (PID: 6476)
- schtasks.exe (PID: 5020)
- powershell.exe (PID: 7652)
- cmd.exe (PID: 7824)
- dialer.exe (PID: 2384)
- dialer.exe (PID: 7968)
- schtasks.exe (PID: 4932)
Reads the software policy settings
- lsass.exe (PID: 756)
- slui.exe (PID: 5576)
- slui.exe (PID: 4376)
Create files in a temporary directory
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- x2.exe (PID: 5436)
Checks supported languages
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- identity_helper.exe (PID: 8068)
- x2.exe (PID: 5436)
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
- chrome.exe (PID: 1240)
- chrome.exe (PID: 812)
- updater.exe (PID: 7952)
- uhssvc.exe (PID: 648)
- chrome.exe (PID: 5412)
- chrome.exe (PID: 1128)
Reads the computer name
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- identity_helper.exe (PID: 8068)
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
- chrome.exe (PID: 812)
- chrome.exe (PID: 1240)
Process checks computer location settings
- CraxsRatV7.2CrackedByWantHacks.exe (PID: 1056)
- chrome.exe (PID: 6136)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- svchost.exe (PID: 2536)
- notepad.exe (PID: 7568)
- notepad.exe (PID: 7856)
Application launched itself
- msedge.exe (PID: 2908)
Creates files or folders in the user directory
- lsass.exe (PID: 756)
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
- WerFault.exe (PID: 840)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 8168)
- OpenWith.exe (PID: 7524)
- OfficeClickToRun.exe (PID: 3112)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5112)
- powershell.exe (PID: 7508)
- powershell.exe (PID: 7652)
Reads Environment values
- identity_helper.exe (PID: 8068)
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5112)
- powershell.exe (PID: 7508)
- powershell.exe (PID: 7652)
Reads the machine GUID from the registry
- chrome.exe (PID: 5772)
- chrome.exe (PID: 6136)
- chrome.exe (PID: 812)
- chrome.exe (PID: 1240)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 7804)
Disables trace logs
- chrome.exe (PID: 5772)
- powershell.exe (PID: 5112)
- chrome.exe (PID: 6136)
Checks proxy server information
- chrome.exe (PID: 5772)
- powershell.exe (PID: 5112)
- chrome.exe (PID: 6136)
- slui.exe (PID: 4376)
The sample compiled with english language support
- powershell.exe (PID: 5112)
- x2.exe (PID: 5436)
- msedge.exe (PID: 5084)
Auto-launch of the file from Registry key
- chrome.exe (PID: 6136)
Creates files in the program directory
- x2.exe (PID: 5436)
- MoUsoCoreWorker.exe (PID: 5496)
- svchost.exe (PID: 5196)
- svchost.exe (PID: 3284)
Executable content was dropped or overwritten
- msedge.exe (PID: 5084)
The sample compiled with japanese language support
- updater.exe (PID: 7952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:13 22:07:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | CraxsRat-V7.2-Cracked-main/ |
Total processes
235
Monitored processes
200
Malicious processes
98
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 468 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7040 --field-trial-handle=2244,i,6156262879132228544,13401182821237125699,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 648 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2528 --field-trial-handle=2244,i,6156262879132228544,13401182821237125699,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 756 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\Users\admin\AppData\Roaming\chrome\chrome.exe | C:\Users\admin\AppData\Roaming\chrome\chrome.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 840 | C:\WINDOWS\system32\WerFault.exe -u -p 5412 -s 244 | C:\Windows\System32\WerFault.exe | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 860 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -s RmSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | sc stop bits | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
63 965
Read events
63 719
Write events
196
Delete events
50
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000010000000000000006100660072006900630061006E006C002E006A00700067003E002000200000001300000000000000630065006C006C0073006100630074006900760065002E007200740066003E002000200000001500000000000000660065006D0061006C006500660069006E0061006C006C0079002E007200740066003E002000200000000D0000000000000067006F006F00640068002E0070006E0067003E0020002000000010000000000000006D0061007000730079006500610072002E006A00700067003E0020002000000013000000000000006D00750073007400630075006C0074007500720065002E007200740066003E0020002000000015000000000000006F007400680065007200730064006500760069006300650073002E007200740066003E0020002000000011000000000000006F00750072007300650061007200630068002E006A00700067003E002000200000001400000000000000730061006600650074007900730065006C006500630074002E007200740066003E00200020000000170000000000000073006300690065006E0063006500700072006100630074006900630065002E006A00700067003E00200020000000130000000000000073006500610073006F006E006100640075006C0074002E007200740066003E002000200000001500000000000000750072006C0065006E00740065007200700072006900730065002E006A00700067003E00200020000000480000000000000065003400640034006400300035003400300065003100360061003500660037003400650032003600360066003600330063003800660063003700630031006500320062003900640035006600320033006500380032003600660064006600610062003100320031003400310036006400620037006500640031006100350064002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000040400000803F1300000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000004040000000401400 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 0F822A6800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000B02D4 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\e4d4d0540e16a5f74e266f63c8fc7c1e2b9d5f23e826fdfab121416db7ed1a5d.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
24
Suspicious files
447
Text files
103
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1772 | svchost.exe | C:\Windows\Prefetch\CRAXSRATV7.2CRACKEDBYWANTHACK-5C959D09.pf | binary | |
MD5:9CDEB31EB5068B8E4BAFA7AE21BCBE6D | SHA256:B6FB66035F31756DBE2B0AA84DDB26CE8E129BC9F6A8883260902F946B9E269E | |||
| 1772 | svchost.exe | C:\Windows\Prefetch\CONSENT.EXE-531BD9EA.pf | binary | |
MD5:CD9813D7BDC219A63A0098491349444B | SHA256:079F247DD77B8F81FC838705521689DDDD4B96481A20B3EB153B99C94472435E | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10cc2b.TMP | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10cc2b.TMP | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10cc2b.TMP | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10cc2b.TMP | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2908 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
79
DNS requests
47
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1747939494&P2=404&P3=2&P4=m0RTUnDEzthtXoy%2b%2bdwf7Cx4mCgqQEqD%2fZwLQKjzBAYS%2bHZSsGCEEfLgtnTpoRKnl55ZCfFVvorMMym5Ar6hcg%3d%3d | unknown | — | — | whitelisted |
6136 | chrome.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
5772 | chrome.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747695345&P2=404&P3=2&P4=V%2f82Zh7H4v%2bAvjTk3c%2bsR4Jr%2fXEC93HbD3As9I7GZf2mIsBRtB02CIXSURaBfOkNWyHB0CyuXs9XQ9wwu2ud2A%3d%3d | unknown | — | — | whitelisted |
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1747695346&P2=404&P3=2&P4=B5s9aPqbhkiUdthY1Zwar32I8UxiF0uwgUL6cXWw9csw1TBGGConyA2L%2bg7IZbkvPYCNDCDppw9rhcTpxoIkHg%3d%3d | unknown | — | — | whitelisted |
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747695345&P2=404&P3=2&P4=X0xC3jC701IXRpa4ZTISTB5BFf2bxGsgCk2xVjzTphUsJkqWVI%2fOoPuLNBZPFJ46W%2fVMXyHqzd5%2b%2fxW321ObVw%3d%3d | unknown | — | — | whitelisted |
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4b01f7e3-1016-48fe-9466-15e9587c9c82?P1=1747695347&P2=404&P3=2&P4=LwuTa3XmD8WnROBg0iFuG%2bCKWO2FZMdxEX43zARROlVBMdpvTuzsubNC0n54mp7h7lPGO%2b7d2DWlTMWE5CN2vQ%3d%3d | unknown | — | — | whitelisted |
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1747695346&P2=404&P3=2&P4=fE4NGSullywZ63LzjoWDvScxN%2f6llE4jJ8Ooo477Kc1CXsWHU3UM9sW39U6XTVxUK1gtvPIkZajQ1vYLwCCfOg%3d%3d | unknown | — | — | whitelisted |
680 | msedge.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1747695345&P2=404&P3=2&P4=Dvz9P500UgWt93epRm7TiWH2mnxIV6UoO8LbT3gFNAotuP3ghOH5%2b%2f6K96QDmyjsZvHHyHsym6jX6k2e3kgLjQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2908 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
680 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
680 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
680 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
— | — | Misc activity | ET INFO Request for EXE via Powershell |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | ET INFO Request for EXE via Powershell |
— | — | Misc activity | ET INFO Packed Executable Download |
— | — | Misc activity | ET HUNTING EXE Downloaded from Github |