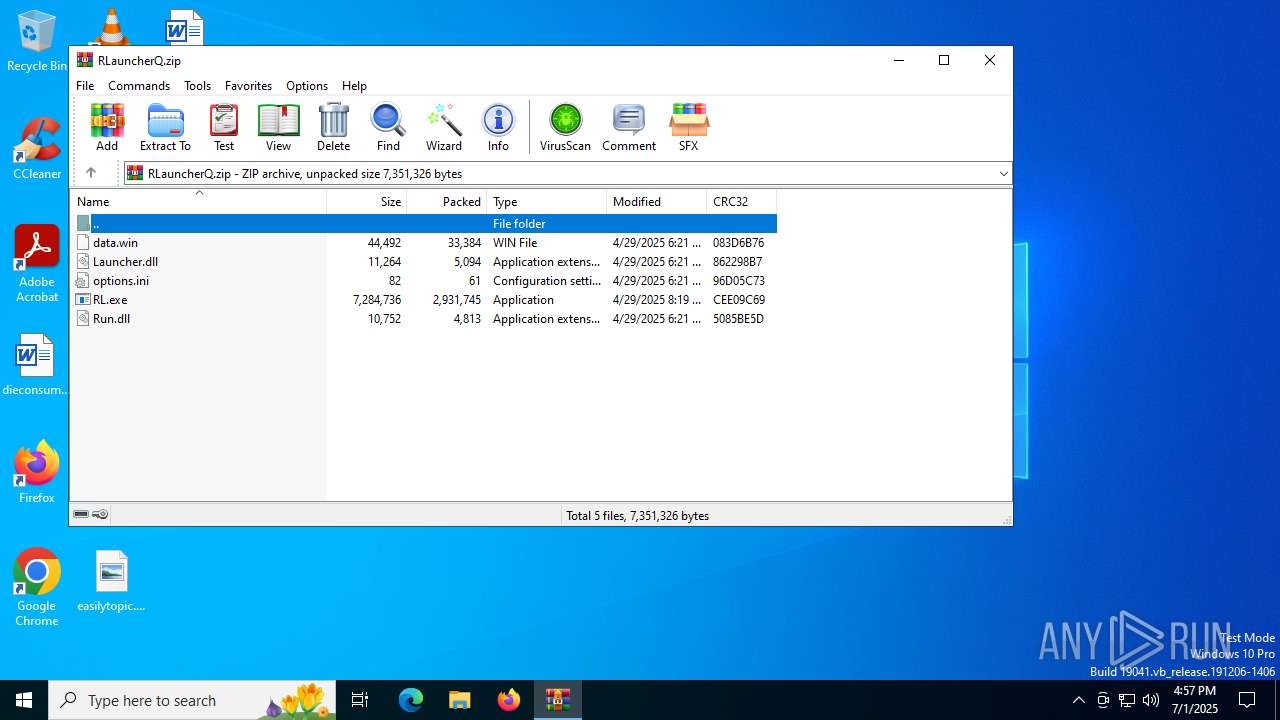
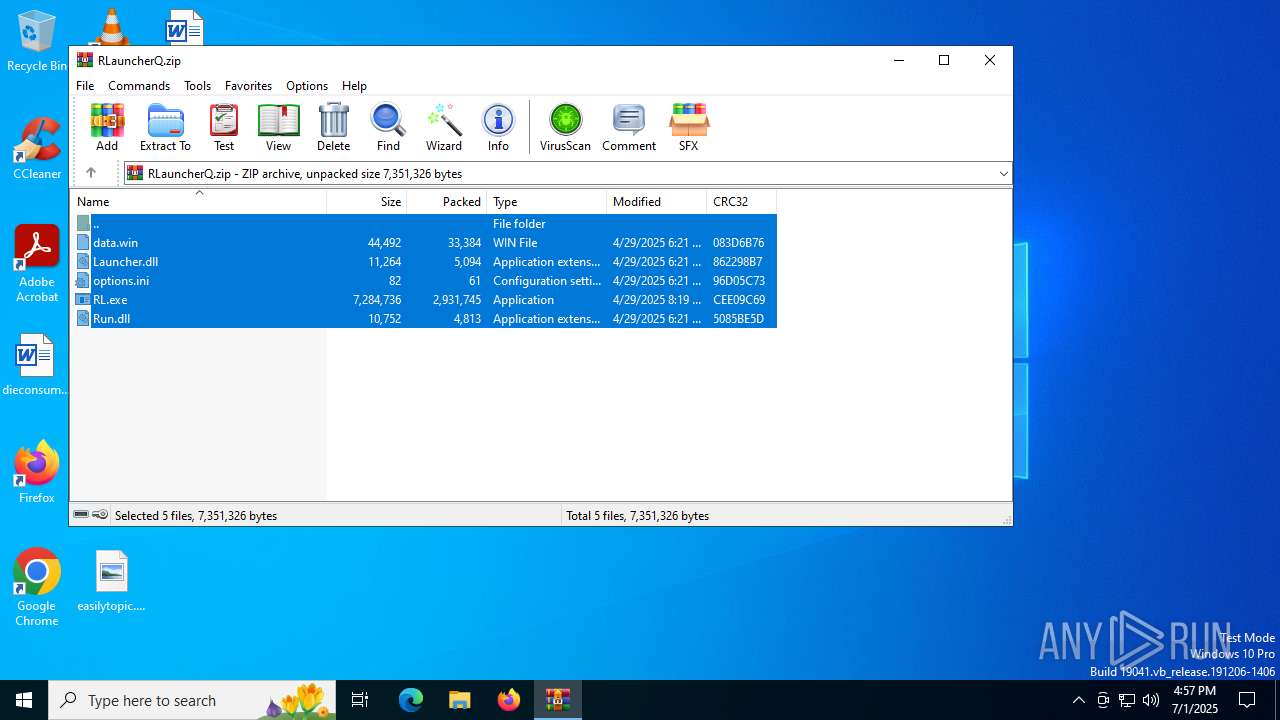
| File name: | RLauncherQ.zip |
| Full analysis: | https://app.any.run/tasks/5a02e16b-42b0-4e76-b311-d40633d75cad |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 01, 2025, 16:57:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A82633D6C3FAB3A08070480F06D1997C |
| SHA1: | 810FA9EC126FA4E6DBB075B778F5B8E12BD0D85C |
| SHA256: | E4D43A92EB1067D19856BAC6E2CA35ADACB73FA6B0DD67BF85B7D77AD0D2F854 |
| SSDEEP: | 98304:jK5pXjEyMxnSW1YNd8PDKcp14wj68jq0kvfNeG15/qLMOR0/Xh1agjsOwAw7Uw+u:am7 |
MALICIOUS
LUMMA has been found (auto)
- WinRAR.exe (PID: 2972)
Generic archive extractor
- WinRAR.exe (PID: 2972)
Adds path to the Windows Defender exclusion list
- RL.exe (PID: 5552)
- cmd.exe (PID: 5264)
Changes Windows Defender settings
- cmd.exe (PID: 5264)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
Connects to the CnC server
- svchost.exe (PID: 2200)
SUSPICIOUS
Reads security settings of Internet Explorer
- RL.exe (PID: 5552)
There is functionality for taking screenshot (YARA)
- RL.exe (PID: 5552)
Reads the date of Windows installation
- RL.exe (PID: 5552)
Starts CMD.EXE for commands execution
- RL.exe (PID: 5552)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5264)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 5264)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2200)
Executable content was dropped or overwritten
- RL.exe (PID: 5552)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2972)
Manual execution by a user
- RL.exe (PID: 5552)
- RL.exe (PID: 5576)
Reads the computer name
- RL.exe (PID: 5552)
- MSBuild.exe (PID: 1512)
The sample compiled with english language support
- WinRAR.exe (PID: 2972)
Checks supported languages
- RL.exe (PID: 5552)
- MSBuild.exe (PID: 1512)
- kosdko0.exe (PID: 5400)
Process checks computer location settings
- RL.exe (PID: 5552)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4820)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4820)
Checks proxy server information
- RL.exe (PID: 5552)
Reads the software policy settings
- RL.exe (PID: 5552)
- MSBuild.exe (PID: 1512)
Creates files or folders in the user directory
- RL.exe (PID: 5552)
Reads the machine GUID from the registry
- RL.exe (PID: 5552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:29 10:21:58 |
| ZipCRC: | 0x862298b7 |
| ZipCompressedSize: | 5094 |
| ZipUncompressedSize: | 11264 |
| ZipFileName: | Launcher.dll |
Total processes
144
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | kosdko0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | kosdko0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2348 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\RLauncherQ.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | powershell Add-MpPreference -ExclusionPath 'C:\' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5264 | "C:\Windows\System32\cmd.exe" /c powershell Add-MpPreference -ExclusionPath 'C:\' | C:\Windows\System32\cmd.exe | — | RL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "C:\Users\admin\Documents\update\kosdko0.exe" | C:\Users\admin\Documents\update\kosdko0.exe | — | RL.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5552 | "C:\Users\admin\Desktop\RL.exe" | C:\Users\admin\Desktop\RL.exe | explorer.exe | ||||||||||||
User: admin Company: YoYo Games Ltd Integrity Level: HIGH Description: A GameMaker Game Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
9 065
Read events
9 040
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RLauncherQ.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
4
Suspicious files
7
Text files
3
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2972.34384\options.ini | ini | |
MD5:41616038DE3B5861FEF6BBA57C874720 | SHA256:DAB8470F9999E4E41088D5A678522E9A4993D1F2DBF184EFC5814D5590642272 | |||
| 2972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2972.34384\Run.dll | executable | |
MD5:59061112AD98C09A19D915436F4730F8 | SHA256:B30F60EB792AE388D3CEAE6DE6CEB693C8EE2A9C1F6F342093A2C8FD1646B50A | |||
| 2972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2972.34384\data.win | binary | |
MD5:9E0E540653A377725839E07A7FF22539 | SHA256:AA615042DDC5CDC5F4EDC3C17F539641B9B231A2C89758E28246BC332608748E | |||
| 4820 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lqnhvp0f.wgp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5552 | RL.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:968B0DCCDCFE0CB3B743BADE61B58EA7 | SHA256:38ACC7AC1975D707F3537E0970A023E07C3474DCCA21F67756A90DDC810989CA | |||
| 4820 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:603FB45AB30889F1F01CE953F4C4F548 | SHA256:7F620377739396CA5F540742B7C6EAA6859C1BCC0F69C8FC6006A19EB301D5C1 | |||
| 4820 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_eotsiiab.t32.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5552 | RL.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:8CDA41C7449DDE7820AF21537766EBA2 | SHA256:C2FC0333B6897223CD8CB59722F0CA1211198F6C1D4226F5E88EB455FA0C7FB0 | |||
| 5552 | RL.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D9CA54E0FA212456E1DB00704A97658E | der | |
MD5:1679ABA16F40BC7A484748ABA258D307 | SHA256:9F3EDF4424C0C08B9F6D102F0626F1FDBBB15C97A09B3073BEA72D266D9B8B7A | |||
| 2972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2972.34384\Launcher.dll | executable | |
MD5:4C4EB82B11CC4B2BA721DF86EB02265C | SHA256:0FDD35F2B0D3356A3BB9C4CDDD8831432509E29F1681DAF1F76588B6A18BBCA2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
26
DNS requests
30
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2648 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2288 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5552 | RL.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
5552 | RL.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
5552 | RL.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
5552 | RL.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
5552 | RL.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
2648 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3980 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2288 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2288 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (battlefled .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (harumseeiw .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (escczlv .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (korxddl .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (localixbiw .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (narrathfpt .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (diecam .top) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (citellcagt .top) |