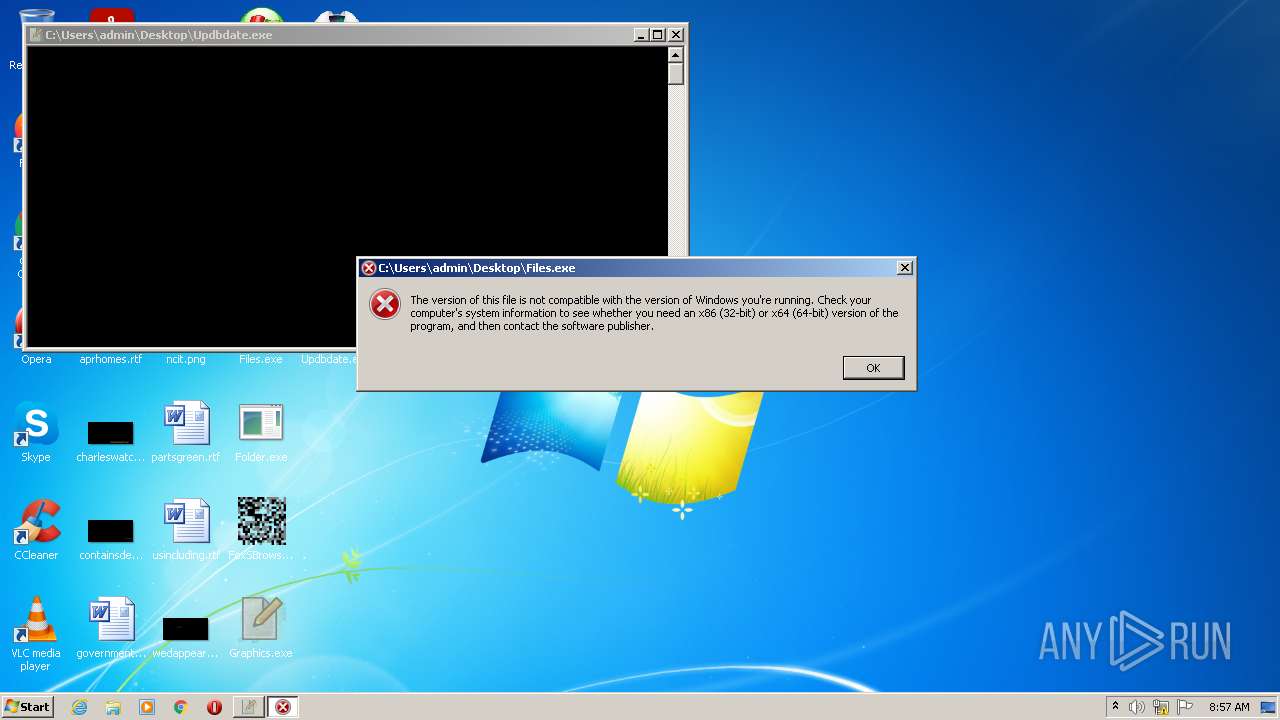
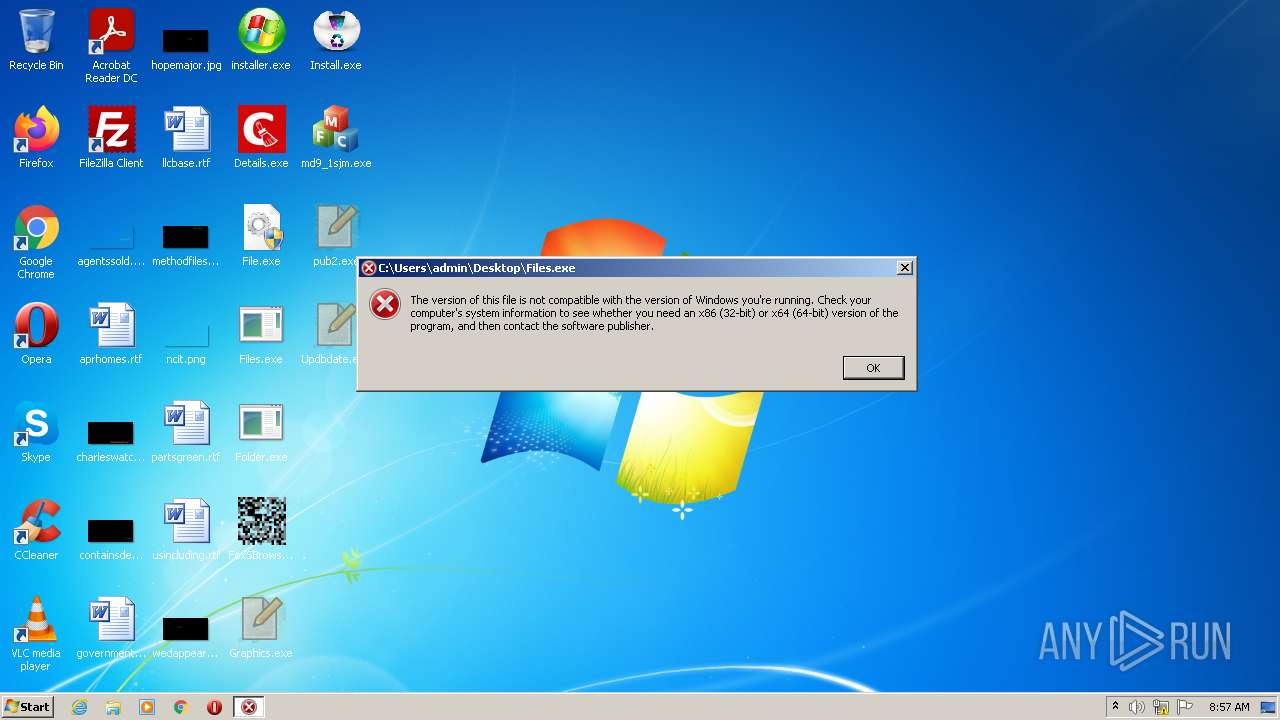
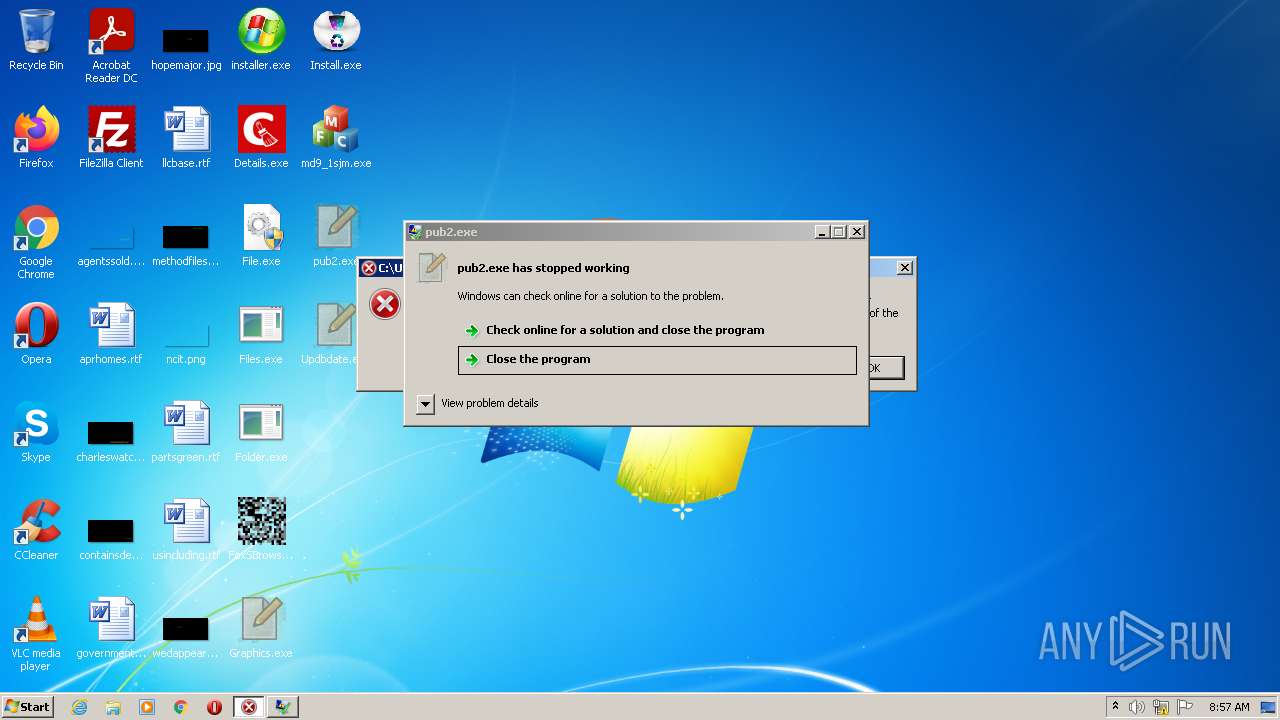
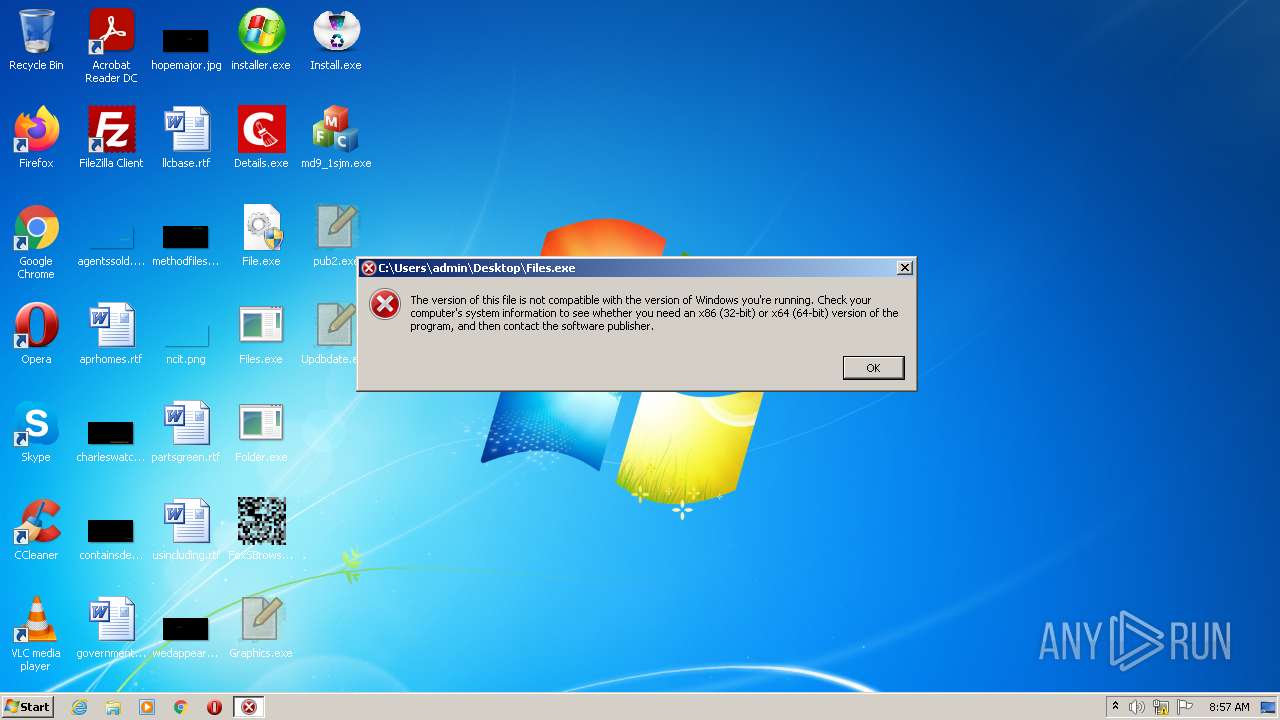
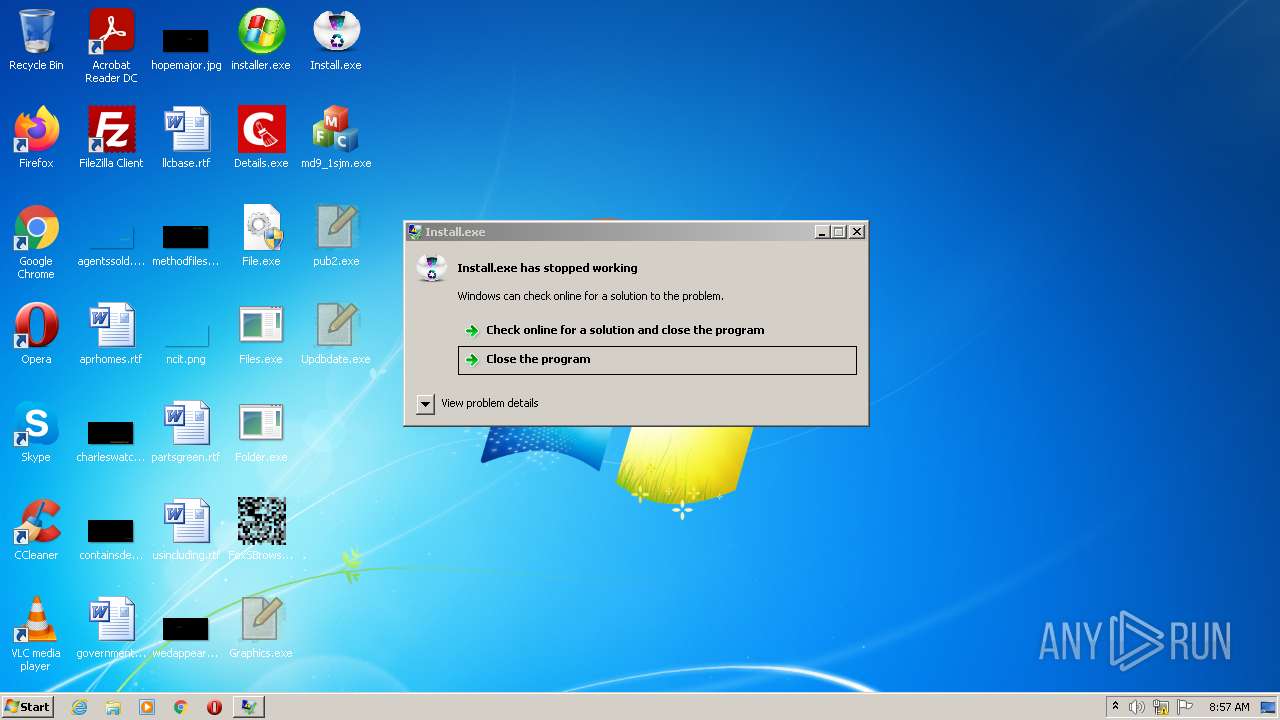
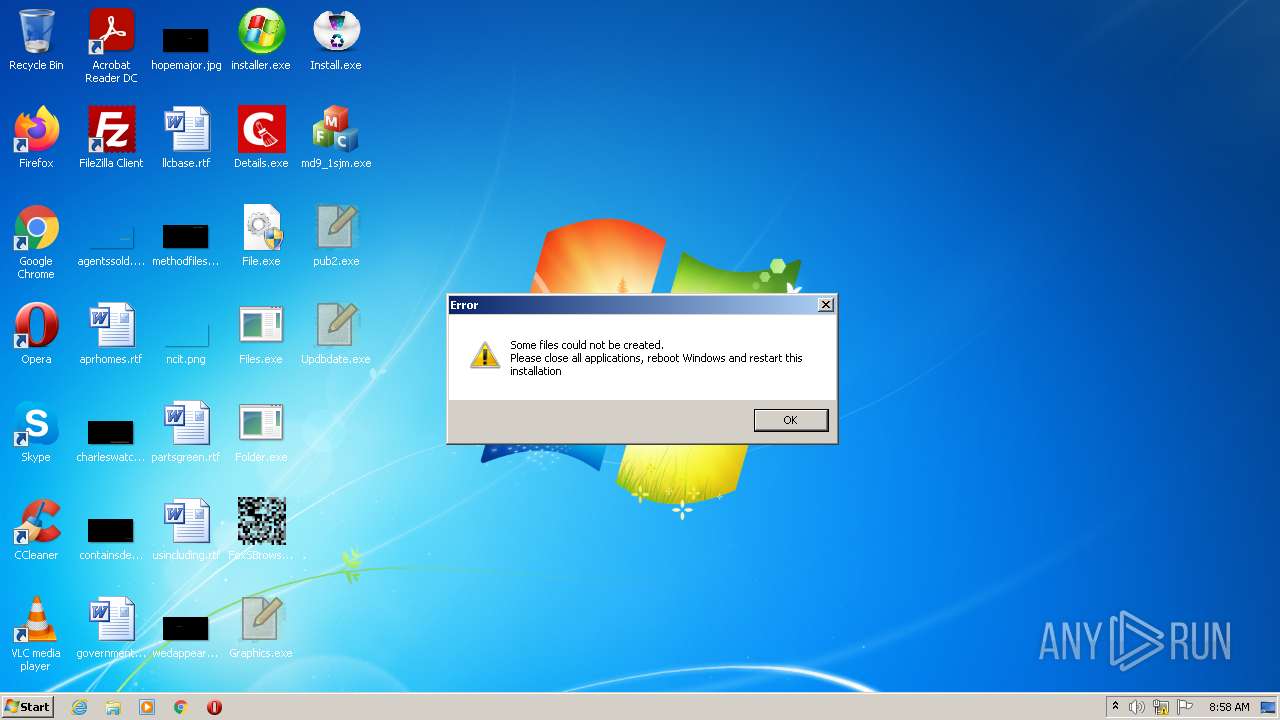
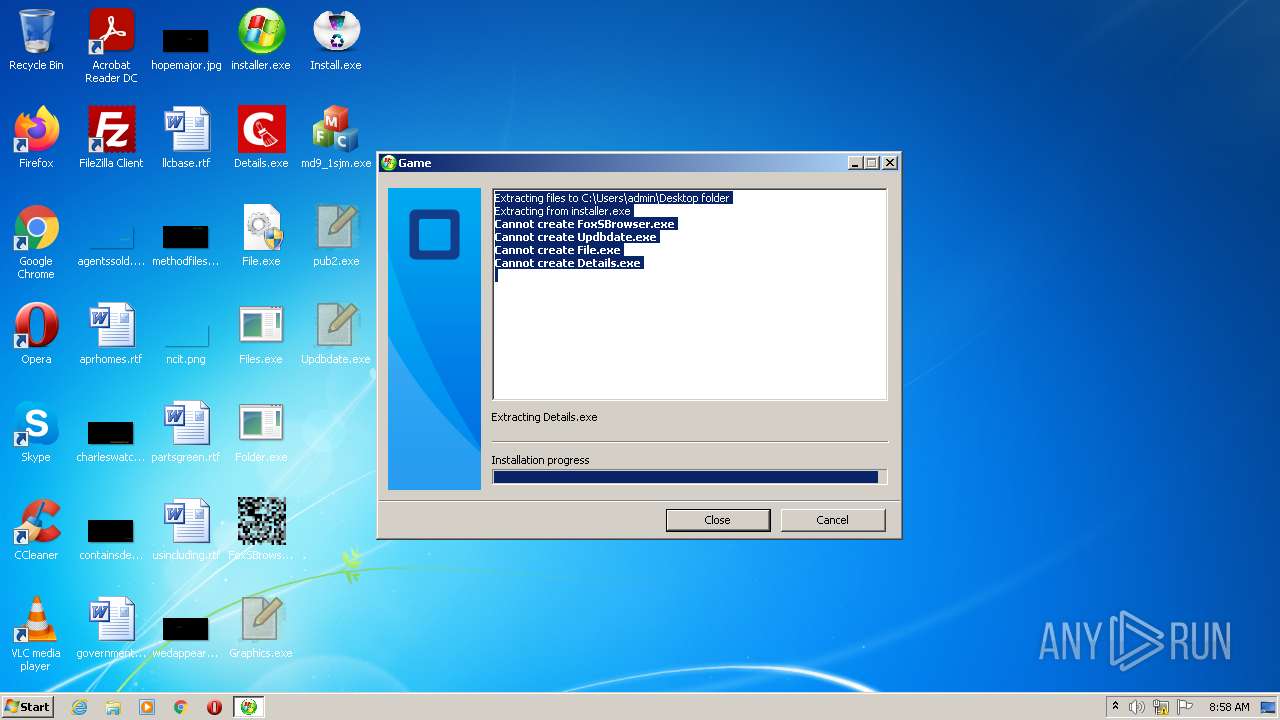
| File name: | installer.exe |
| Full analysis: | https://app.any.run/tasks/1f606d84-5536-4258-8f51-3cd5fc1d4a95 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | June 27, 2022, 07:56:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 93E23E5BED552C0500856641D19729A8 |
| SHA1: | 7E14CDF808DCD21D766A4054935C87C89C037445 |
| SHA256: | E4B23EBEB82594979325357CE20F14F70143D98FF49A9D5A2E6258FBFB33E555 |
| SSDEEP: | 196608:PBXWySxHnUIYfGp0N6k7jn3R655p0aRnk6bAEzV1d:pXc6rf6Q3ipdnkqAEzVf |
MALICIOUS
Drops executable file immediately after starts
- installer.exe (PID: 1952)
- Folder.exe (PID: 3192)
- md9_1sjm.exe (PID: 4020)
Runs injected code in another process
- rUNdlL32.eXe (PID: 1464)
- rUNdlL32.eXe (PID: 3036)
Application was dropped or rewritten from another process
- File.exe (PID: 2264)
- Install.exe (PID: 3472)
- FoxSBrowser.exe (PID: 2672)
- Install.exe (PID: 1988)
- md9_1sjm.exe (PID: 4020)
- File.exe (PID: 3652)
- Folder.exe (PID: 3192)
- Graphics.exe (PID: 3016)
- pub2.exe (PID: 3948)
- Updbdate.exe (PID: 1856)
- Folder.exe (PID: 532)
- Details.exe (PID: 2424)
- File.exe (PID: 2352)
- Graphics.exe (PID: 2228)
- pub2.exe (PID: 2536)
- File.exe (PID: 1008)
- Updbdate.exe (PID: 3684)
- Install.exe (PID: 2968)
- Install.exe (PID: 3828)
- md9_1sjm.exe (PID: 3344)
- Folder.exe (PID: 3720)
- Folder.exe (PID: 2080)
Application was injected by another process
- svchost.exe (PID: 868)
Known privilege escalation attack
- DllHost.exe (PID: 1832)
- DllHost.exe (PID: 1956)
Changes settings of System certificates
- Install.exe (PID: 1988)
- File.exe (PID: 2264)
REDLINE detected by memory dumps
- Updbdate.exe (PID: 1856)
- Updbdate.exe (PID: 3684)
Connects to CnC server
- md9_1sjm.exe (PID: 4020)
- md9_1sjm.exe (PID: 3344)
- File.exe (PID: 2264)
Actions looks like stealing of personal data
- md9_1sjm.exe (PID: 4020)
- md9_1sjm.exe (PID: 3344)
Loads dropped or rewritten executable
- rUNdlL32.eXe (PID: 1464)
- rUNdlL32.eXe (PID: 3036)
Steals credentials from Web Browsers
- md9_1sjm.exe (PID: 4020)
- md9_1sjm.exe (PID: 3344)
Disables Windows Defender
- File.exe (PID: 2264)
SOCELARS was detected
- File.exe (PID: 2264)
SUSPICIOUS
Reads the computer name
- installer.exe (PID: 1952)
- FoxSBrowser.exe (PID: 2672)
- md9_1sjm.exe (PID: 4020)
- Install.exe (PID: 3472)
- Folder.exe (PID: 3192)
- File.exe (PID: 2264)
- Folder.exe (PID: 532)
- Install.exe (PID: 1988)
- Updbdate.exe (PID: 1856)
- IELowutil.exe (PID: 3500)
- Graphics.exe (PID: 3016)
- Updbdate.exe (PID: 3684)
- Graphics.exe (PID: 2228)
- File.exe (PID: 1008)
- Install.exe (PID: 2968)
- Install.exe (PID: 3828)
- md9_1sjm.exe (PID: 3344)
- Folder.exe (PID: 3720)
- IELowutil.exe (PID: 2072)
- Folder.exe (PID: 2080)
- installer.exe (PID: 1132)
Checks supported languages
- installer.exe (PID: 1952)
- md9_1sjm.exe (PID: 4020)
- Folder.exe (PID: 532)
- Graphics.exe (PID: 3016)
- Updbdate.exe (PID: 1856)
- Install.exe (PID: 3472)
- FoxSBrowser.exe (PID: 2672)
- Folder.exe (PID: 3192)
- File.exe (PID: 2264)
- pub2.exe (PID: 3948)
- Install.exe (PID: 1988)
- Details.exe (PID: 2424)
- IELowutil.exe (PID: 3500)
- Updbdate.exe (PID: 3684)
- Graphics.exe (PID: 2228)
- pub2.exe (PID: 2536)
- File.exe (PID: 1008)
- Install.exe (PID: 2968)
- Install.exe (PID: 3828)
- md9_1sjm.exe (PID: 3344)
- IELowutil.exe (PID: 2072)
- Folder.exe (PID: 2080)
- Folder.exe (PID: 3720)
- installer.exe (PID: 1132)
Drops a file with a compile date too recent
- installer.exe (PID: 1952)
- md9_1sjm.exe (PID: 4020)
- Folder.exe (PID: 3192)
Executable content was dropped or overwritten
- installer.exe (PID: 1952)
- md9_1sjm.exe (PID: 4020)
- Folder.exe (PID: 3192)
Reads Environment values
- FoxSBrowser.exe (PID: 2672)
Application launched itself
- Folder.exe (PID: 532)
- Folder.exe (PID: 2080)
Executed via COM
- DllHost.exe (PID: 1832)
- DllHost.exe (PID: 1956)
Executed via WMI
- rUNdlL32.eXe (PID: 1464)
- rUNdlL32.eXe (PID: 3036)
Reads the cookies of Mozilla Firefox
- md9_1sjm.exe (PID: 4020)
- md9_1sjm.exe (PID: 3344)
Checks for external IP
- Install.exe (PID: 1988)
- Install.exe (PID: 3828)
- File.exe (PID: 2264)
Adds / modifies Windows certificates
- Install.exe (PID: 1988)
- File.exe (PID: 2264)
Reads the cookies of Google Chrome
- md9_1sjm.exe (PID: 4020)
- md9_1sjm.exe (PID: 3344)
INFO
Checks supported languages
- DllHost.exe (PID: 1832)
- rUNdlL32.eXe (PID: 1464)
- DllHost.exe (PID: 1956)
- rUNdlL32.eXe (PID: 3036)
Reads the computer name
- rUNdlL32.eXe (PID: 1464)
- DllHost.exe (PID: 1832)
- DllHost.exe (PID: 1956)
- rUNdlL32.eXe (PID: 3036)
Reads settings of System Certificates
- md9_1sjm.exe (PID: 4020)
- Install.exe (PID: 1988)
- File.exe (PID: 2264)
- md9_1sjm.exe (PID: 3344)
Checks Windows Trust Settings
- Install.exe (PID: 1988)
- File.exe (PID: 2264)
Manual execution by user
- File.exe (PID: 1008)
- Graphics.exe (PID: 2228)
- pub2.exe (PID: 2536)
- File.exe (PID: 2352)
- Updbdate.exe (PID: 3684)
- Install.exe (PID: 2968)
- md9_1sjm.exe (PID: 3344)
- Folder.exe (PID: 2080)
- installer.exe (PID: 1132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(1856) Updbdate.exe
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
(PID) Process(3684) Updbdate.exe
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x1ec40 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 143360 |
| CodeSize: | 201216 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| TimeStamp: | 2020:12:01 19:00:55+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Dec-2020 18:00:55 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 01-Dec-2020 18:00:55 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000310EA | 0x00031200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70808 |
.rdata | 0x00033000 | 0x0000A612 | 0x0000A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.22174 |
.data | 0x0003E000 | 0x00023728 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.70882 |
.didat | 0x00062000 | 0x00000188 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.29825 |
.rsrc | 0x00063000 | 0x00015168 | 0x00015200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.24093 |
.reloc | 0x00079000 | 0x00002268 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.55486 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | Latin 1 / Western European | English - United States | RT_MANIFEST |
7 | 3.1586 | 482 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 3.11685 | 460 | Latin 1 / Western European | English - United States | RT_STRING |
9 | 3.11236 | 440 | Latin 1 / Western European | English - United States | RT_STRING |
10 | 2.99727 | 326 | Latin 1 / Western European | English - United States | RT_STRING |
11 | 3.2036 | 1094 | Latin 1 / Western European | English - United States | RT_STRING |
12 | 3.12889 | 358 | Latin 1 / Western European | English - United States | RT_STRING |
13 | 3.01704 | 338 | Latin 1 / Western European | English - United States | RT_STRING |
14 | 2.94627 | 266 | Latin 1 / Western European | English - United States | RT_STRING |
15 | 2.83619 | 188 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
98
Monitored processes
31
Malicious processes
18
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Users\admin\Desktop\Folder.exe" | C:\Users\admin\Desktop\Folder.exe | — | installer.exe | |||||||||||
User: admin Company: RealVNC Ltd Integrity Level: MEDIUM Description: VNC® Viewer Exit code: 0 Version: 6.21.406 (r44671) Modules
| |||||||||||||||
| 868 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | Explorer.EXE | ||||||||||||
User: admin Company: Yoko Integrity Level: HIGH Description: Yoko Exit code: 0 Version: 35.205.10001.50000 Modules
| |||||||||||||||
| 1132 | "C:\Users\admin\Desktop\installer.exe" | C:\Users\admin\Desktop\installer.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1464 | rUNdlL32.eXe "C:\Users\admin\AppData\Local\Temp\axhub.dll",main | C:\Windows\system32\rUNdlL32.eXe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1856 | "C:\Users\admin\Desktop\Updbdate.exe" | C:\Users\admin\Desktop\Updbdate.exe | installer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
RedLine(PID) Process(1856) Updbdate.exe C2 (1)45.9.20.20:13441 BotnetUDP Err_msg Auth_value US (117) UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Host Port : User Pass MANGO Environment %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - net.tcp:// / localhost | Yandex\YaAddon HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP BTQgIw== Sarring ToString asf *wallet* Atomic \atomic * Binance \Binance *app-store* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ Collection String Replace Message BPOTE6AJI System.UI File.IO Warning Exception string.Replace Guarda \Guarda File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo File.Write StringBuilder \MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts MemoryStream %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ( UNIQUE " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' FileSystem ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ (PID) Process(1856) Updbdate.exe C2 (1)45.9.20.20:13441 BotnetUDP Err_msg Auth_value US (117) UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Host Port : User Pass MANGO Environment %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - net.tcp:// / localhost | Yandex\YaAddon HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP BTQgIw== Sarring ToString asf *wallet* Atomic \atomic * Binance \Binance *app-store* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ Collection String Replace Message BPOTE6AJI System.UI File.IO Warning Exception string.Replace Guarda \Guarda File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo File.Write StringBuilder \MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts MemoryStream %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ( UNIQUE " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' FileSystem ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ (PID) Process(1856) Updbdate.exe C2 (1)45.9.20.20:13441 BotnetUDP Err_msg Auth_value US (117) UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Host Port : User Pass MANGO Environment %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - net.tcp:// / localhost | Yandex\YaAddon HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP BTQgIw== Sarring ToString asf *wallet* Atomic \atomic * Binance \Binance *app-store* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ Collection String Replace Message BPOTE6AJI System.UI File.IO Warning Exception string.Replace Guarda \Guarda File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo File.Write StringBuilder \MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts MemoryStream %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ( UNIQUE " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' FileSystem ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ (PID) Process(1856) Updbdate.exe C2 (1)45.9.20.20:13441 BotnetUDP Err_msg Auth_value US (117) UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Host Port : User Pass MANGO Environment %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - net.tcp:// / localhost | Yandex\YaAddon HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP BTQgIw== Sarring ToString asf *wallet* Atomic \atomic * Binance \Binance *app-store* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ Collection String Replace Message BPOTE6AJI System.UI File.IO Warning Exception string.Replace Guarda \Guarda File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo File.Write StringBuilder \MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts MemoryStream %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ( UNIQUE " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' FileSystem ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ (PID) Process(1856) Updbdate.exe C2 (1)45.9.20.20:13441 BotnetUDP Err_msg Auth_value US (117) UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Host Port : User Pass MANGO Environment %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - net.tcp:// / localhost | Yandex\YaAddon HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP BTQgIw== Sarring ToString asf *wallet* Atomic \atomic * Binance \Binance *app-store* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ Collection String Replace Message BPOTE6AJI System.UI File.IO Warning Exception string.Replace Guarda \Guarda File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo File.Write StringBuilder \MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts MemoryStream %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ( UNIQUE " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' FileSystem ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ | |||||||||||||||
| 1952 | "C:\Users\admin\Desktop\installer.exe" | C:\Users\admin\Desktop\installer.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1956 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1988 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | DllHost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
18 950
Read events
18 637
Write events
309
Delete events
4
Modification events
| (PID) Process: | (1952) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1952) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1952) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1952) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (532) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (532) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (532) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (532) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2672) FoxSBrowser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FoxSBrowser_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2672) FoxSBrowser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FoxSBrowser_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
14
Suspicious files
14
Text files
0
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 868 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 1952 | installer.exe | C:\Users\admin\Desktop\md9_1sjm.exe | executable | |
MD5:3B3D48102A0D45A941F98D8AABE2DC43 | SHA256:F4FDF9842D2221EB8910E6829B8467D867E346B7F73E2C3040F16EB77630B8F0 | |||
| 1988 | Install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 1988 | Install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 1988 | Install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1952 | installer.exe | C:\Users\admin\Desktop\FoxSBrowser.exe | executable | |
MD5:849B899ACDC4478C116340B86683A493 | SHA256:5F5EED76DA09DC92090A6501DE1F2A6CC7FB0C92E32053163B28F380F3B06631 | |||
| 1952 | installer.exe | C:\Users\admin\Desktop\Updbdate.exe | executable | |
MD5:3D09B651BAA310515BB5DF3C04506961 | SHA256:2599FED90469C6C2250883F90D1C9D20FE41755B9DA670A306A884797DBD7DF6 | |||
| 1952 | installer.exe | C:\Users\admin\Desktop\Install.exe | executable | |
MD5:DEEB8730435A83CB41CA5679429CB235 | SHA256:002F4696F089281A8C82F3156063CEE84249D1715055E721A47618F2EFECF150 | |||
| 4020 | md9_1sjm.exe | C:\Users\admin\Documents\VlcpVideoV1.0.1\md9_1sjm.exe | executable | |
MD5:3B3D48102A0D45A941F98D8AABE2DC43 | SHA256:F4FDF9842D2221EB8910E6829B8467D867E346B7F73E2C3040F16EB77630B8F0 | |||
| 1952 | installer.exe | C:\Users\admin\Desktop\Graphics.exe | executable | |
MD5:7C20B40B1ABCA9C0C50111529F4A06FA | SHA256:5CAAE6F11ABC0A10481F56F9E598F98332B6144E24BF6EFA67B63BECC7DEBD36 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
38
DNS requests
13
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2264 | File.exe | GET | — | 45.133.1.182:80 | http://45.133.1.182/proxies.txt | unknown | — | — | suspicious |
2264 | File.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
1008 | File.exe | GET | — | 45.133.1.182:80 | http://45.133.1.182/proxies.txt | unknown | — | — | suspicious |
1008 | File.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
2264 | File.exe | GET | — | 193.233.185.125:80 | http://193.233.185.125/download/NiceProcessX32.bmp | RU | — | — | malicious |
2264 | File.exe | HEAD | — | 193.233.185.125:80 | http://193.233.185.125/download/NiceProcessX32.bmp | RU | — | — | malicious |
2264 | File.exe | GET | 200 | 85.202.169.116:80 | http://85.202.169.116/base/api/statistics.php | unknown | binary | 94 b | malicious |
2264 | File.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2264 | File.exe | POST | 200 | 85.202.169.116:80 | http://85.202.169.116/base/api/getData.php | unknown | text | 108 b | malicious |
2264 | File.exe | POST | 200 | 85.202.169.116:80 | http://85.202.169.116/base/api/getData.php | unknown | text | 108 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1988 | Install.exe | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
4020 | md9_1sjm.exe | 186.2.171.3:80 | — | DANCOM LTD | RU | malicious |
2672 | FoxSBrowser.exe | 35.205.61.67:443 | premium-s0ftwar3875.bar | Google Inc. | US | malicious |
2264 | File.exe | 45.133.1.182:80 | — | — | — | suspicious |
1856 | Updbdate.exe | 45.9.20.20:13441 | — | — | — | malicious |
1988 | Install.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
1988 | Install.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
2264 | File.exe | 45.133.1.107:80 | — | — | — | malicious |
1008 | File.exe | 45.133.1.182:80 | — | — | — | suspicious |
3828 | Install.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
guidereviews.bar |
| malicious |
auto-repair-solutions.bar |
| whitelisted |
onepremiumstore.bar |
| malicious |
premium-s0ftwar3875.bar |
| malicious |
google.vrthcobj.com |
| whitelisted |
www.listincode.com |
| whitelisted |
iplogger.org |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
pastebin.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in DNS Lookup) |
1988 | Install.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
4020 | md9_1sjm.exe | A Network Trojan was detected | ET TROJAN Win32/FFDroider CnC Activity M2 |
4020 | md9_1sjm.exe | A Network Trojan was detected | AV TROJAN Win32/Masson CnC Activity |
2264 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2264 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3828 | Install.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
3344 | md9_1sjm.exe | A Network Trojan was detected | ET TROJAN Win32/FFDroider CnC Activity M2 |
3344 | md9_1sjm.exe | A Network Trojan was detected | AV TROJAN Win32/Masson CnC Activity |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |