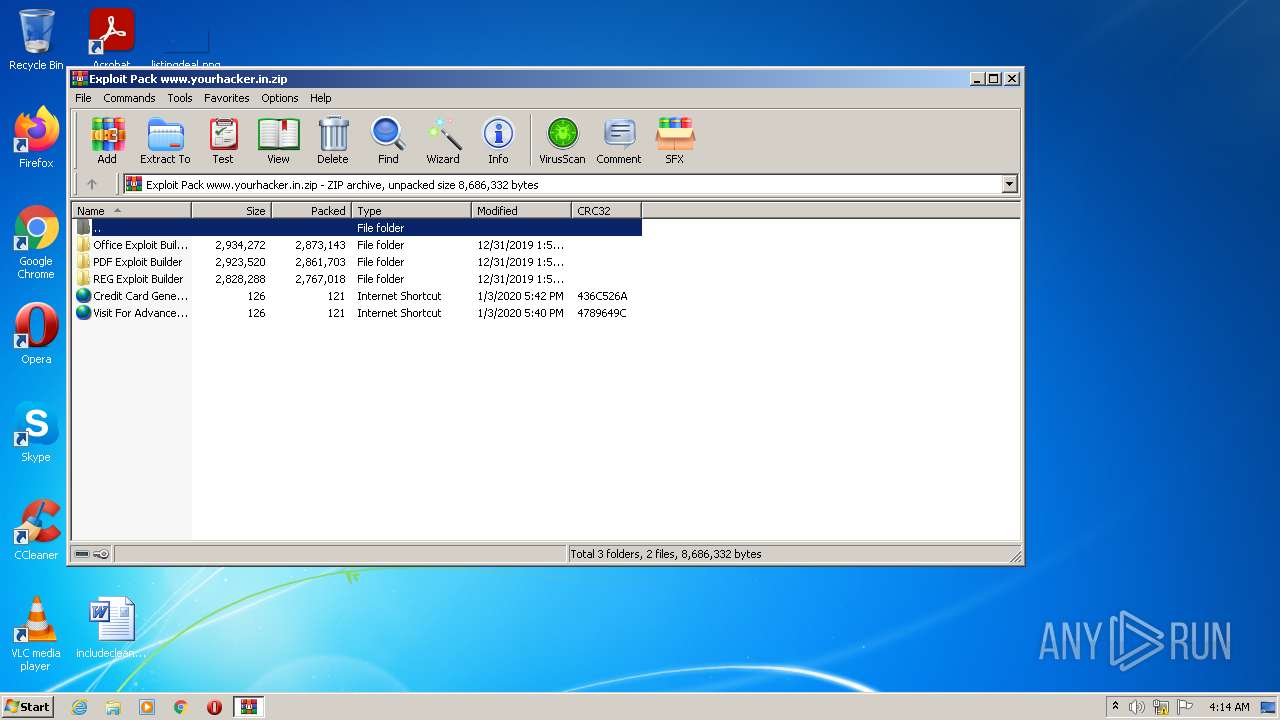
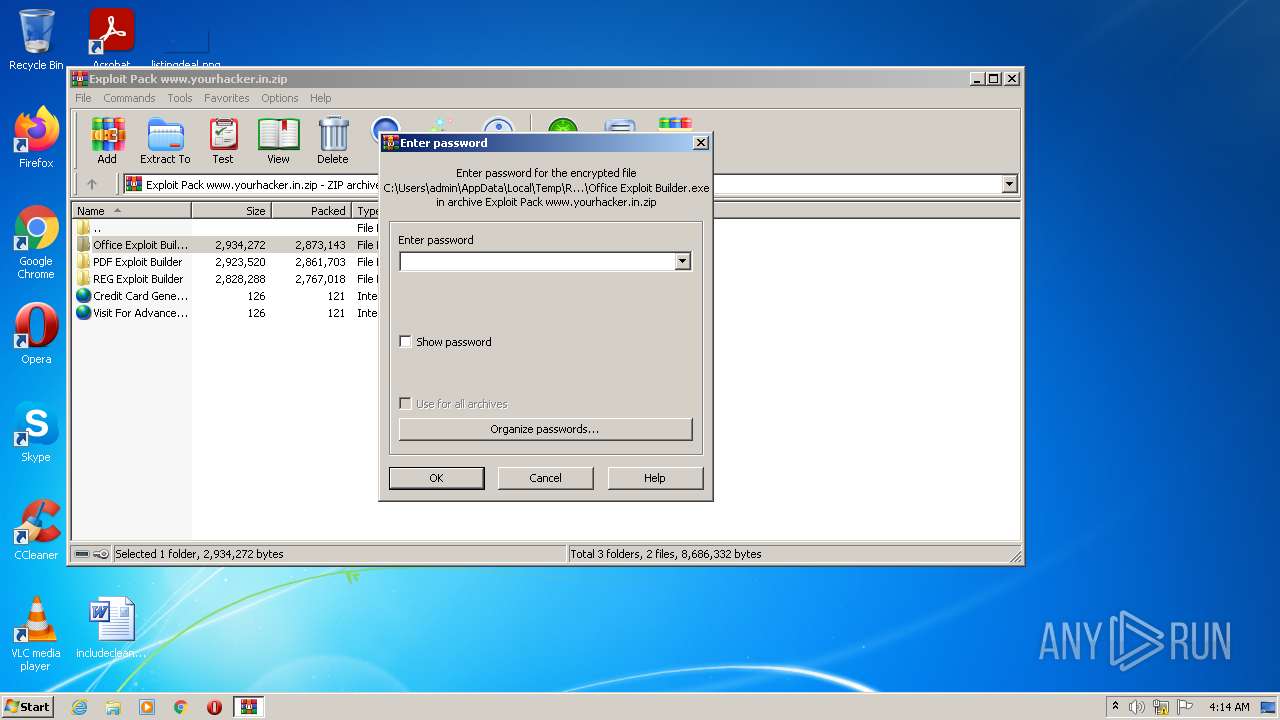
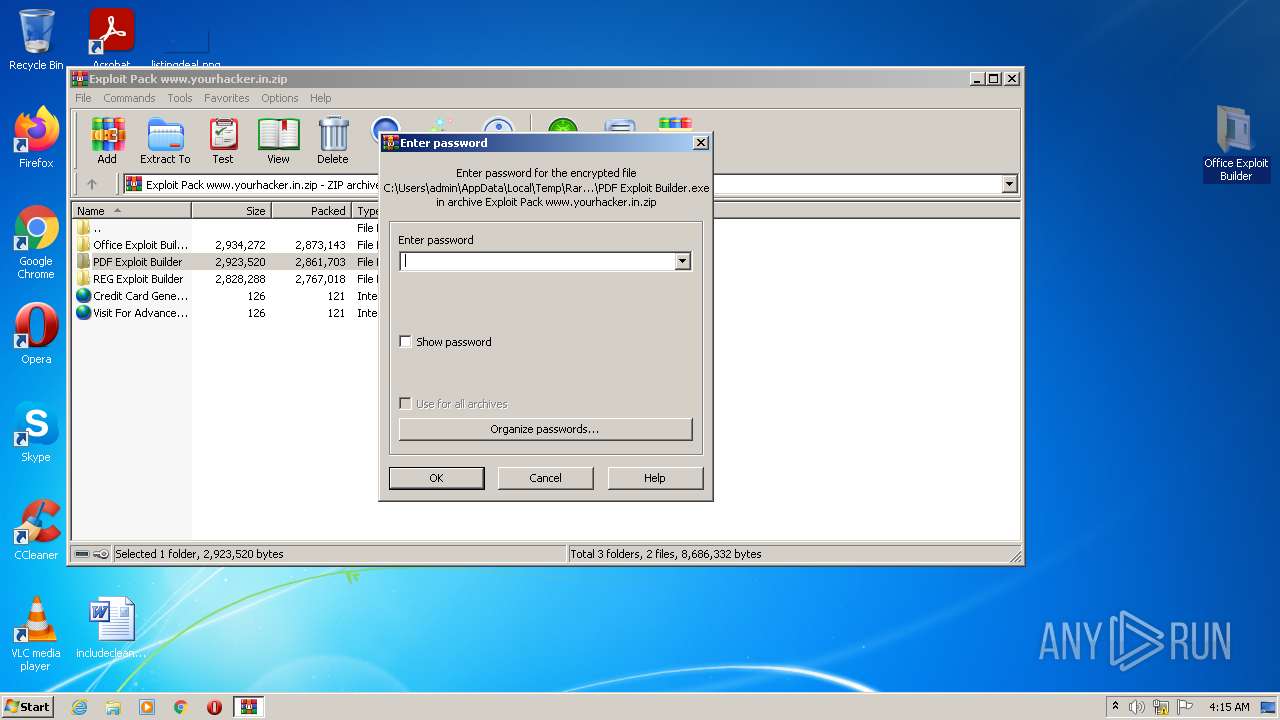
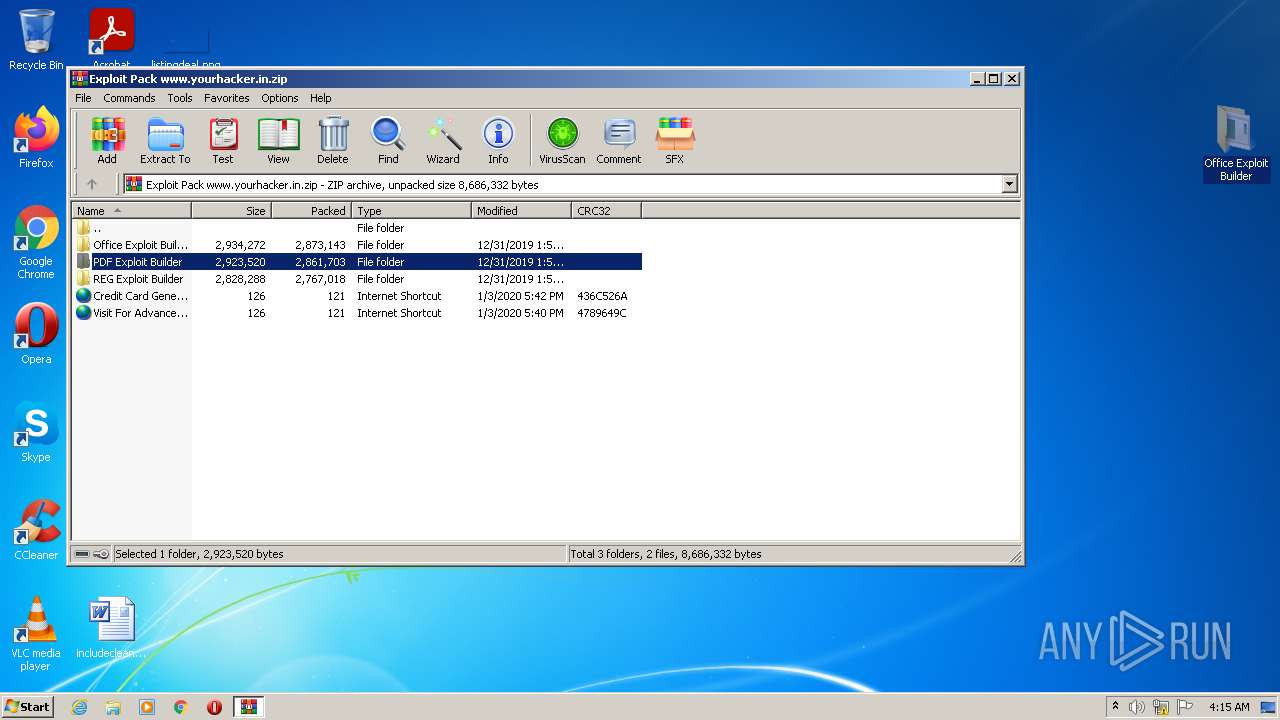
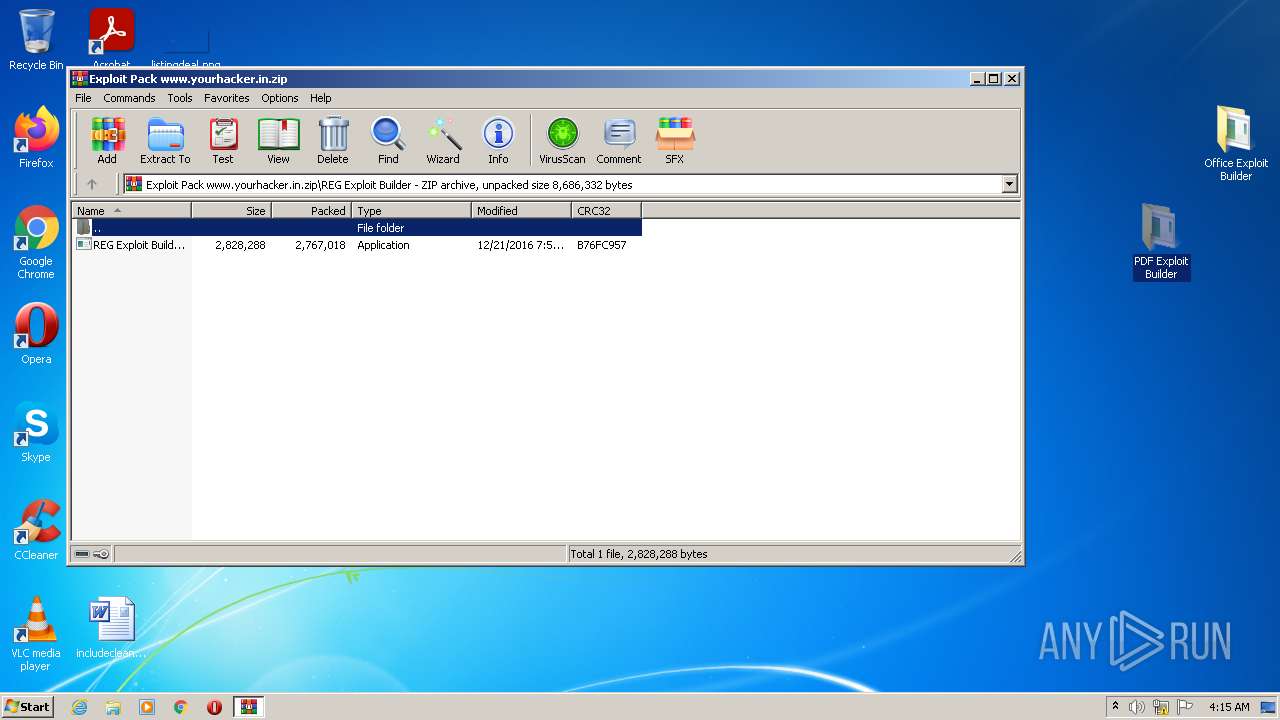
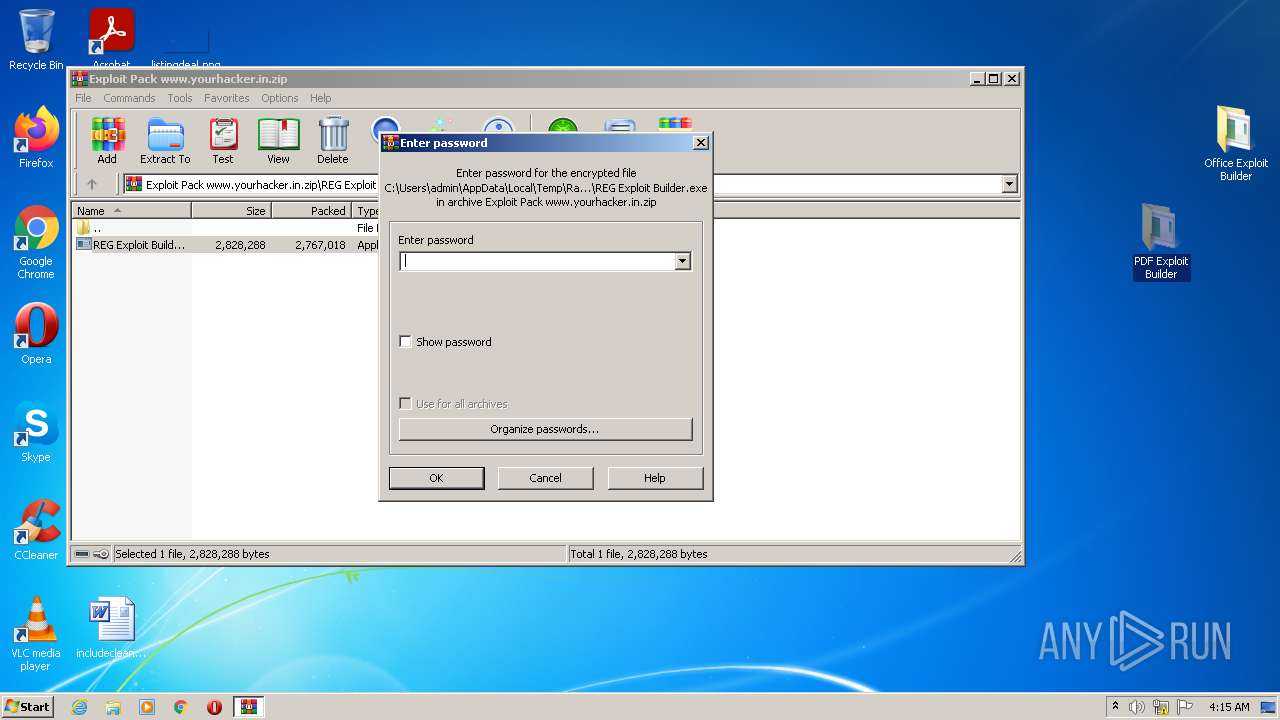
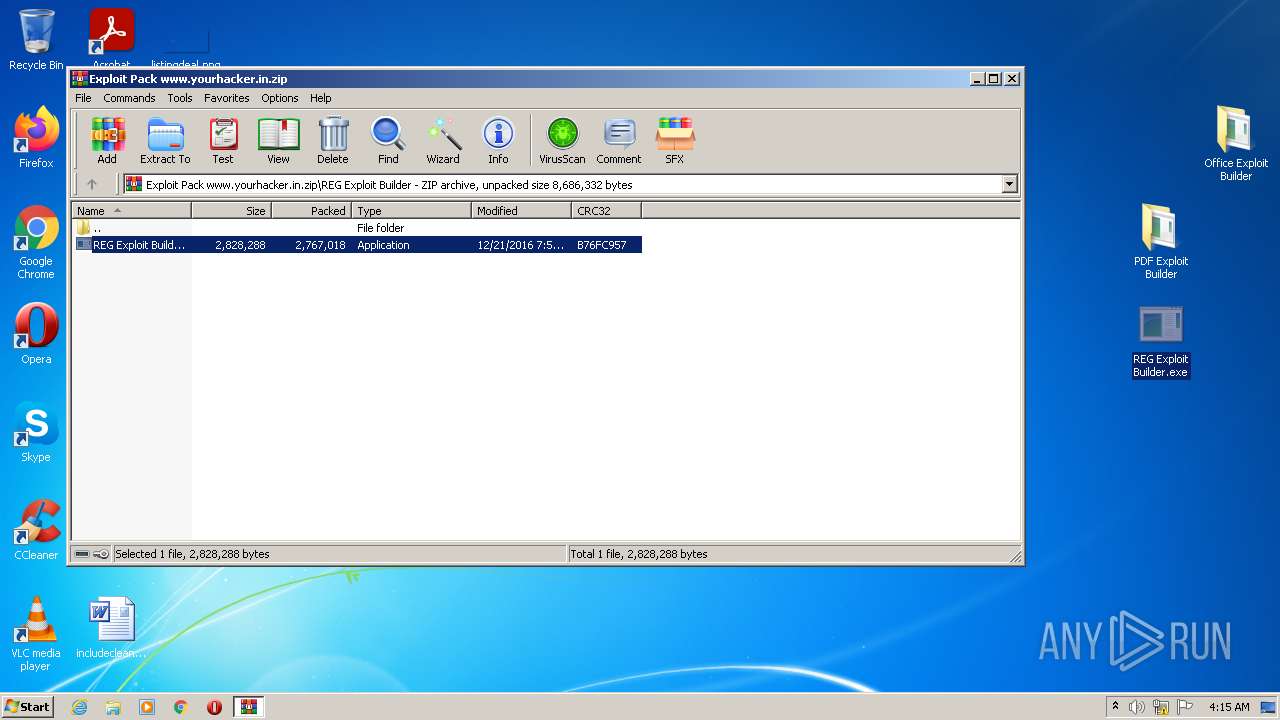
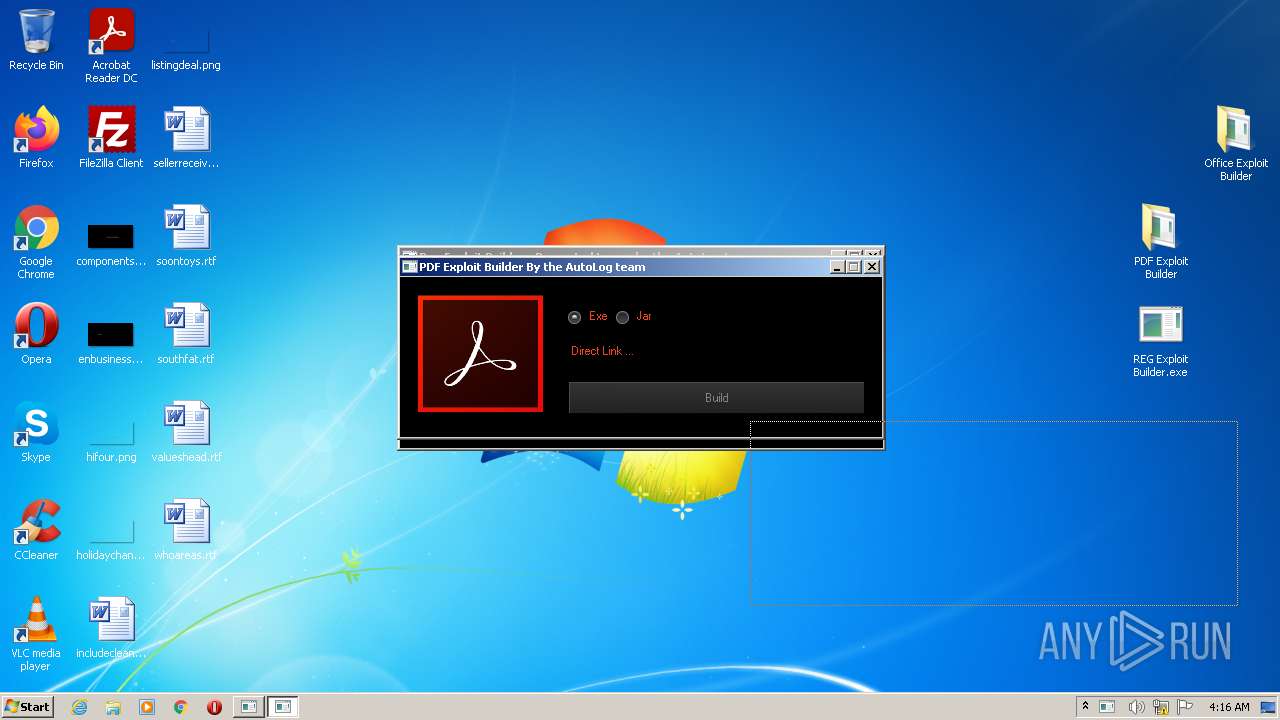
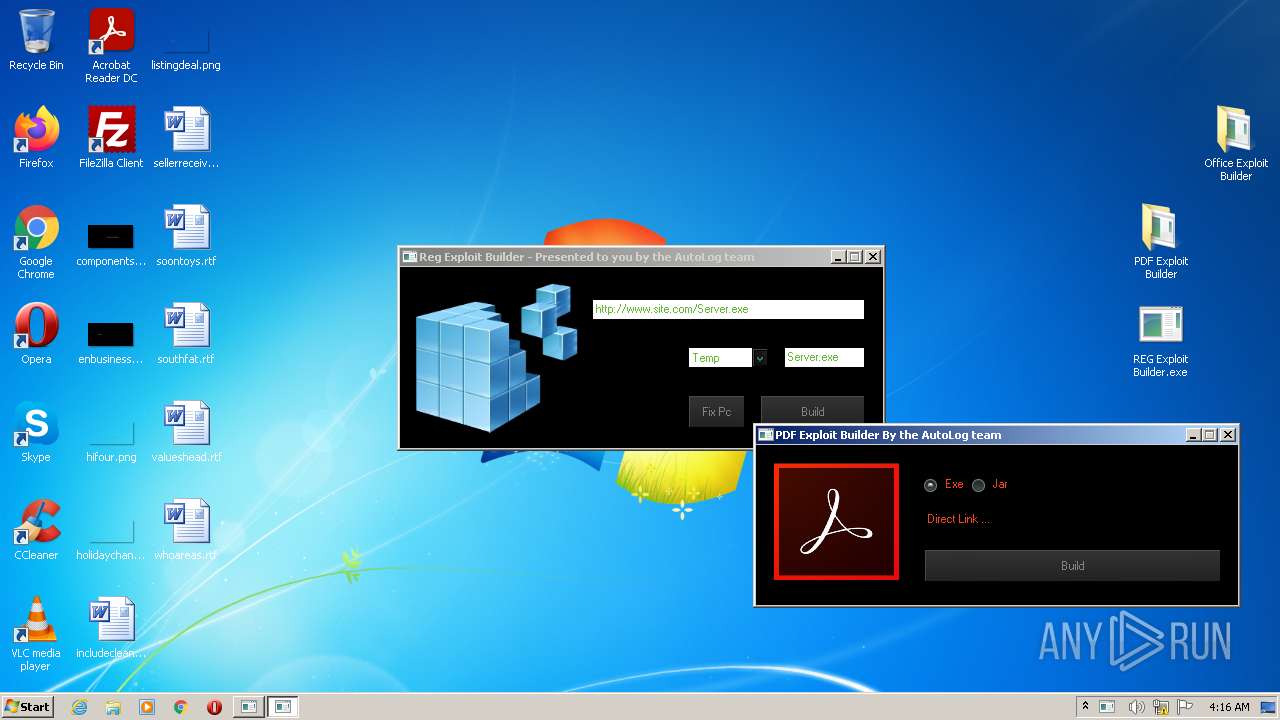
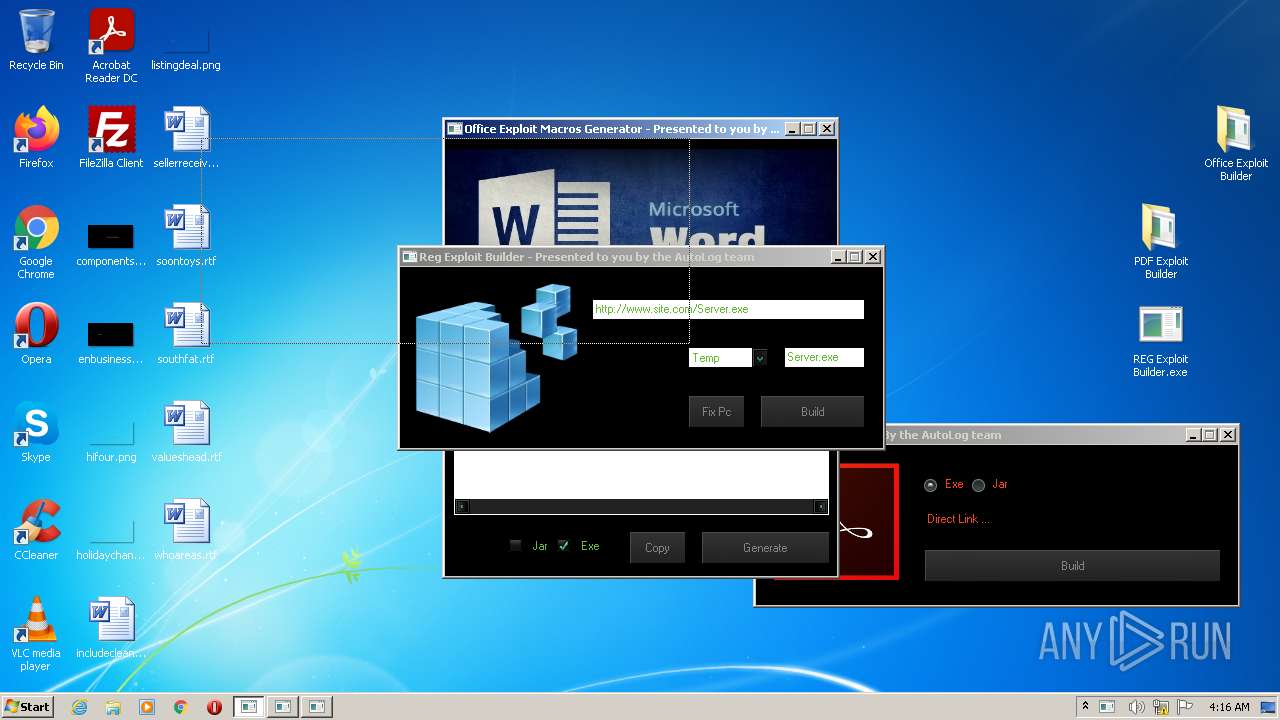
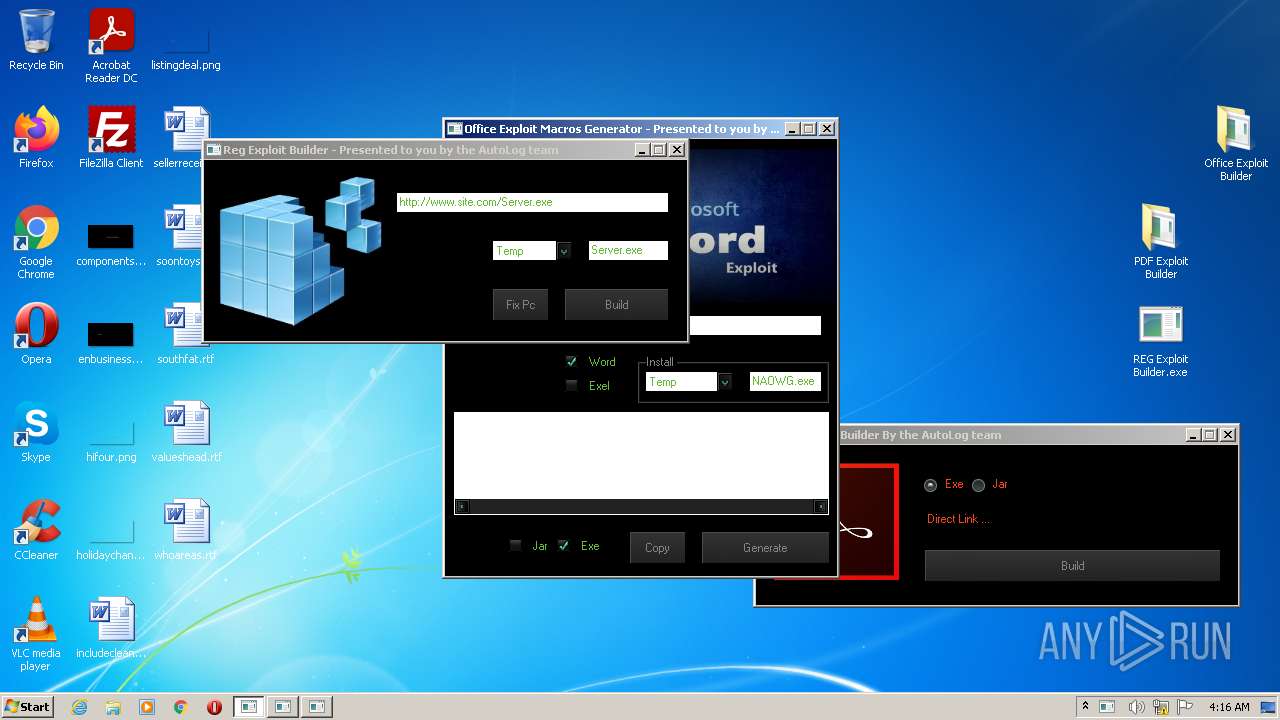
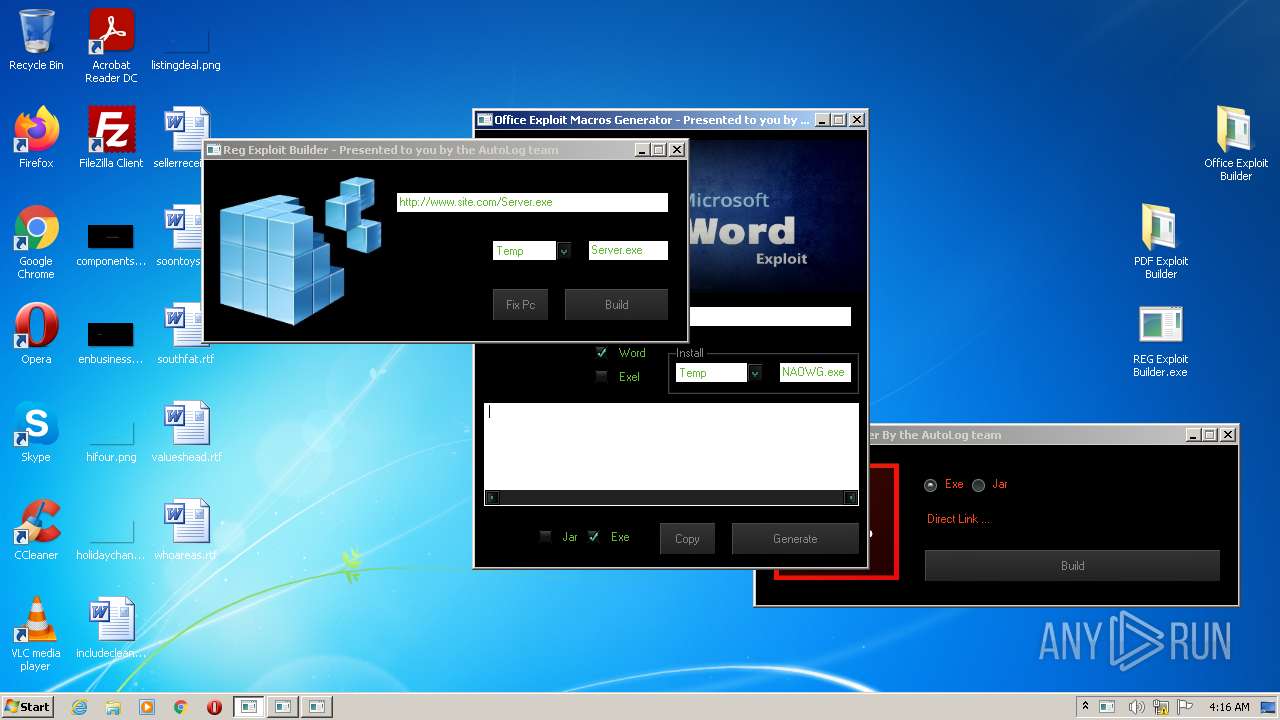
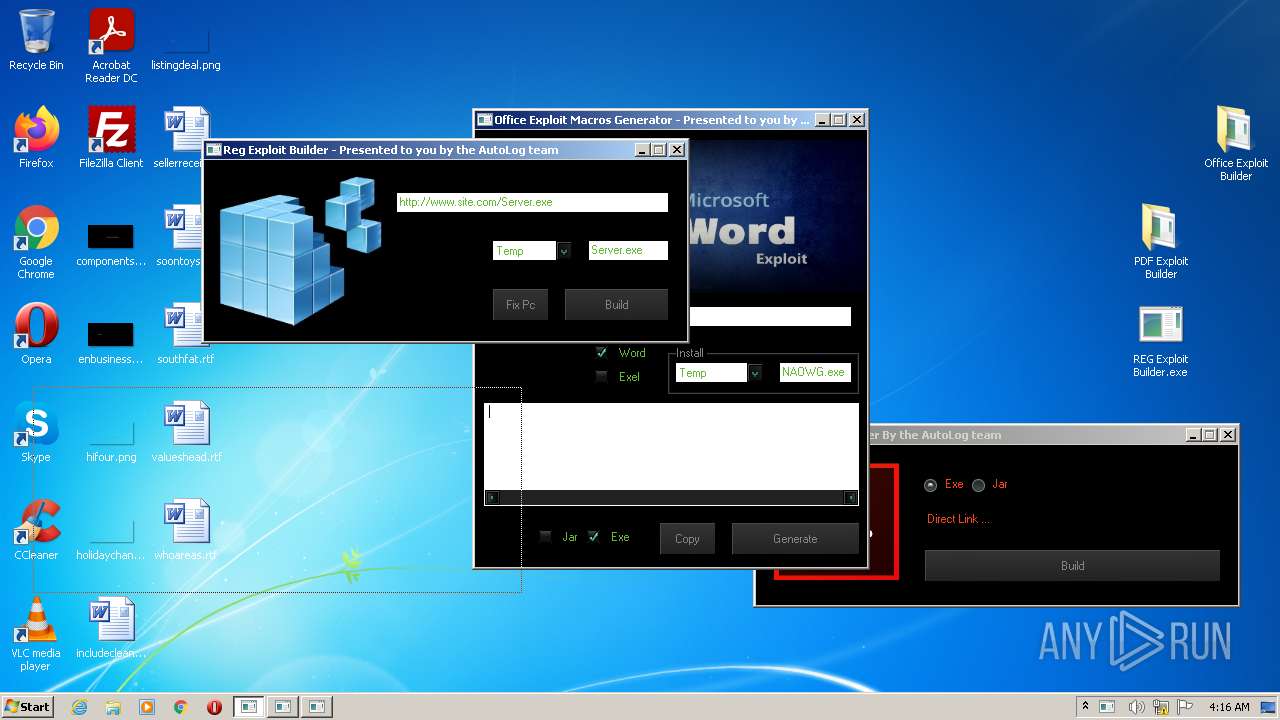
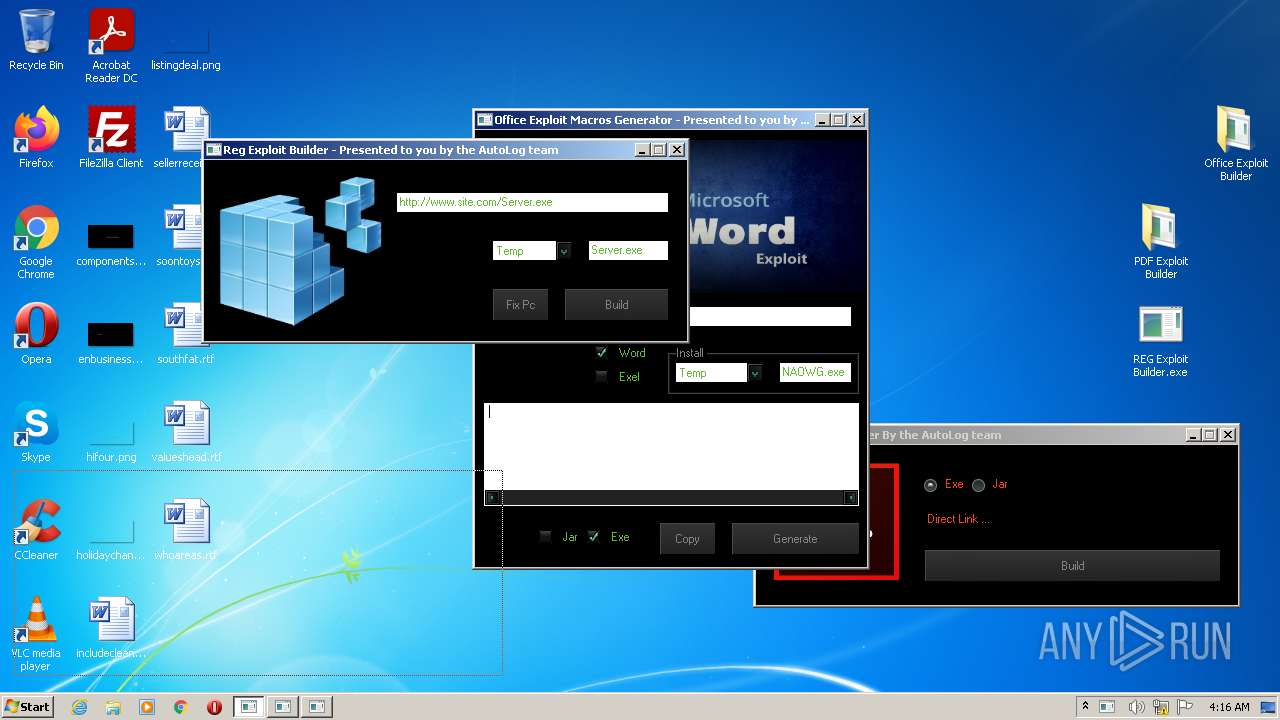
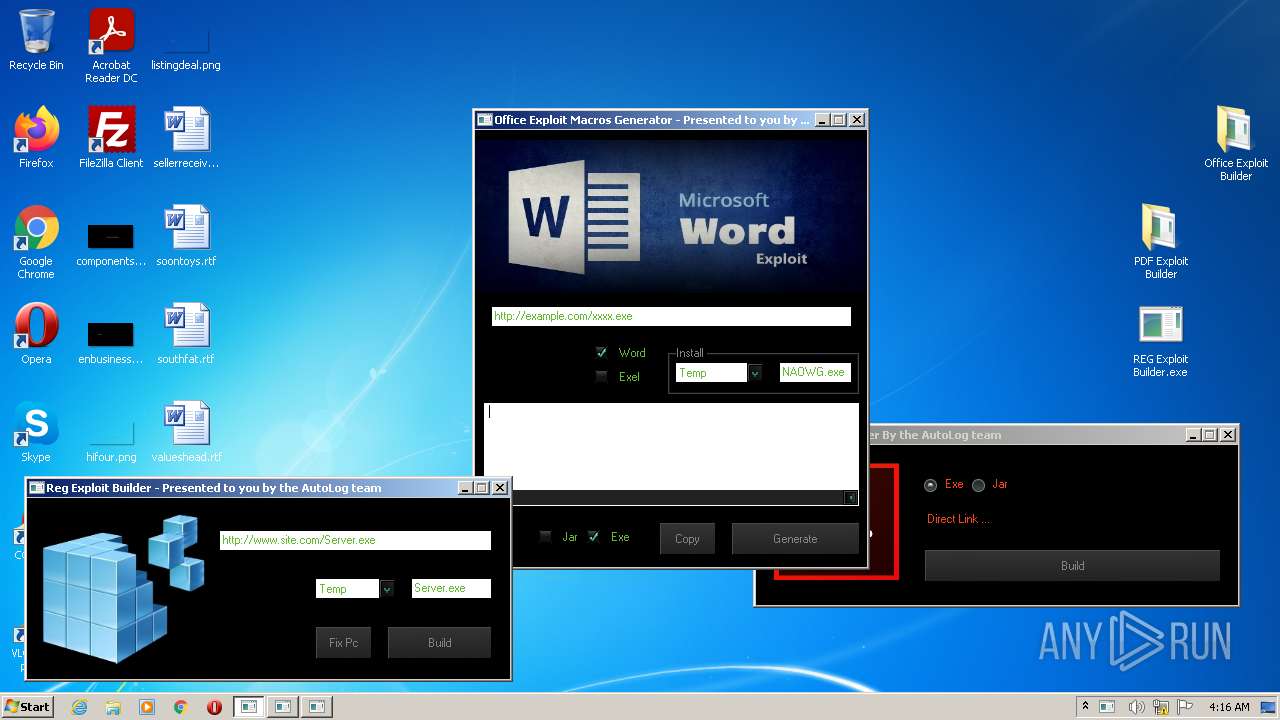
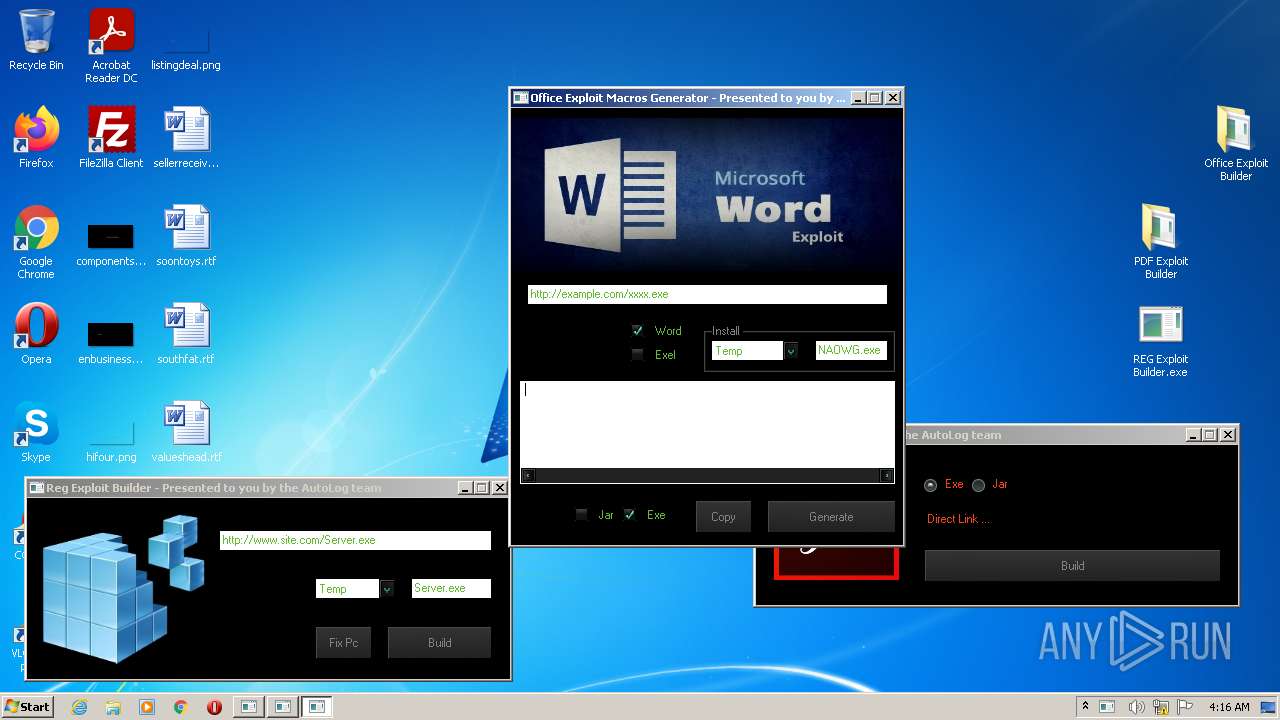
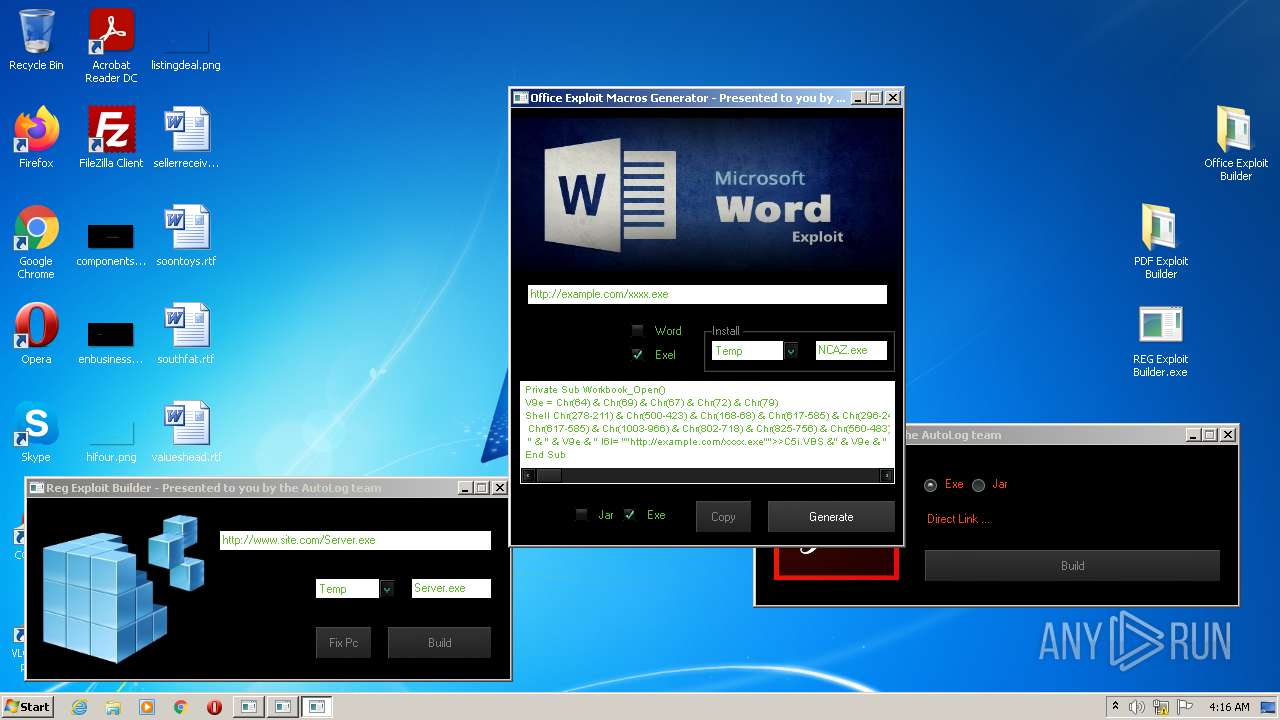
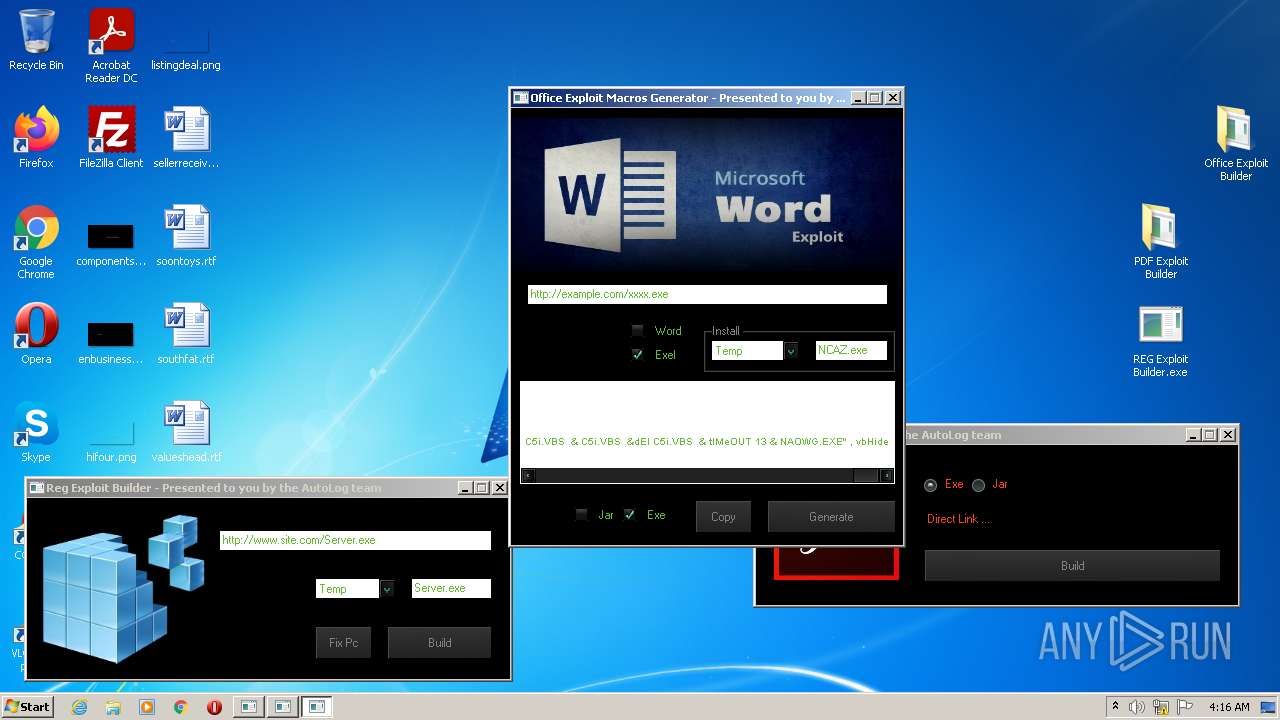
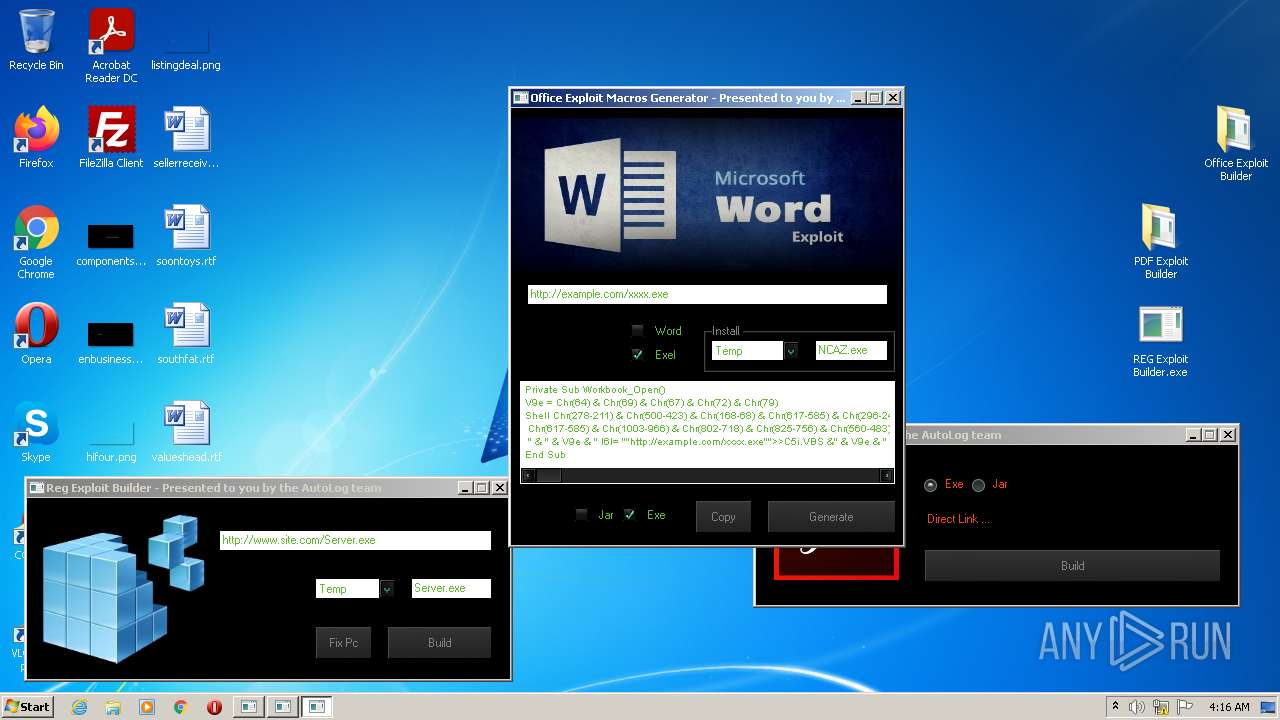
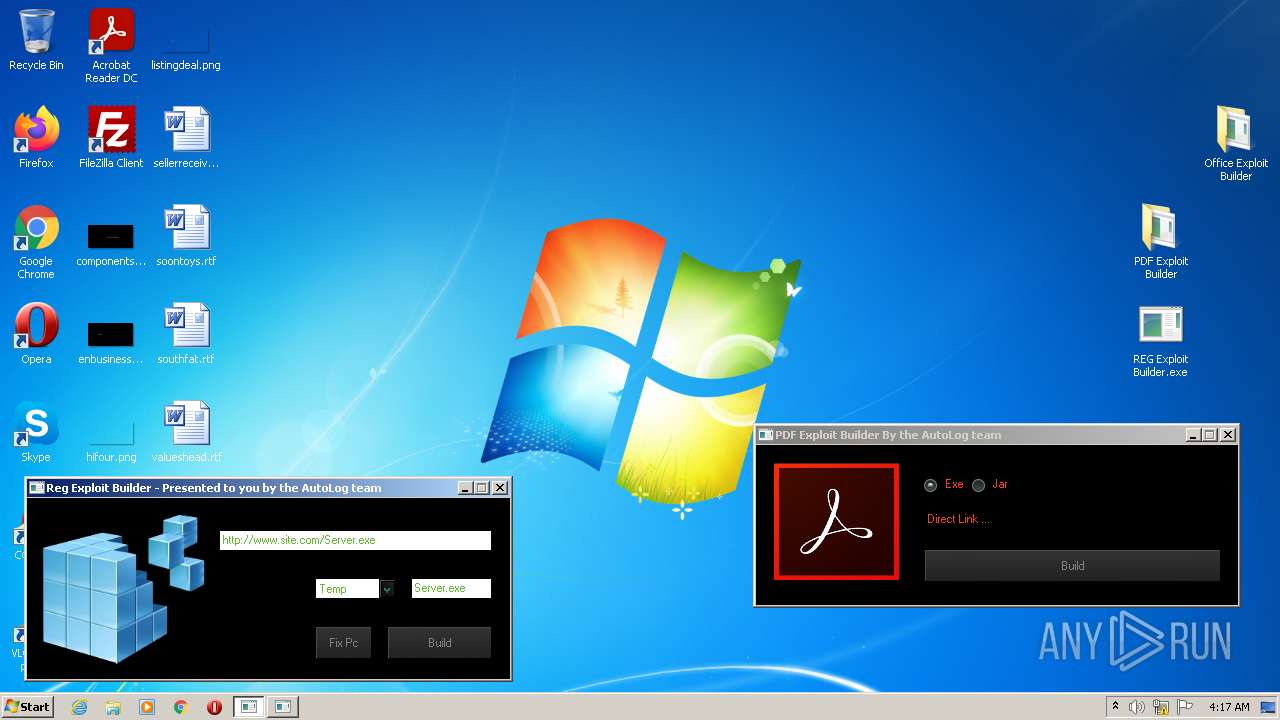
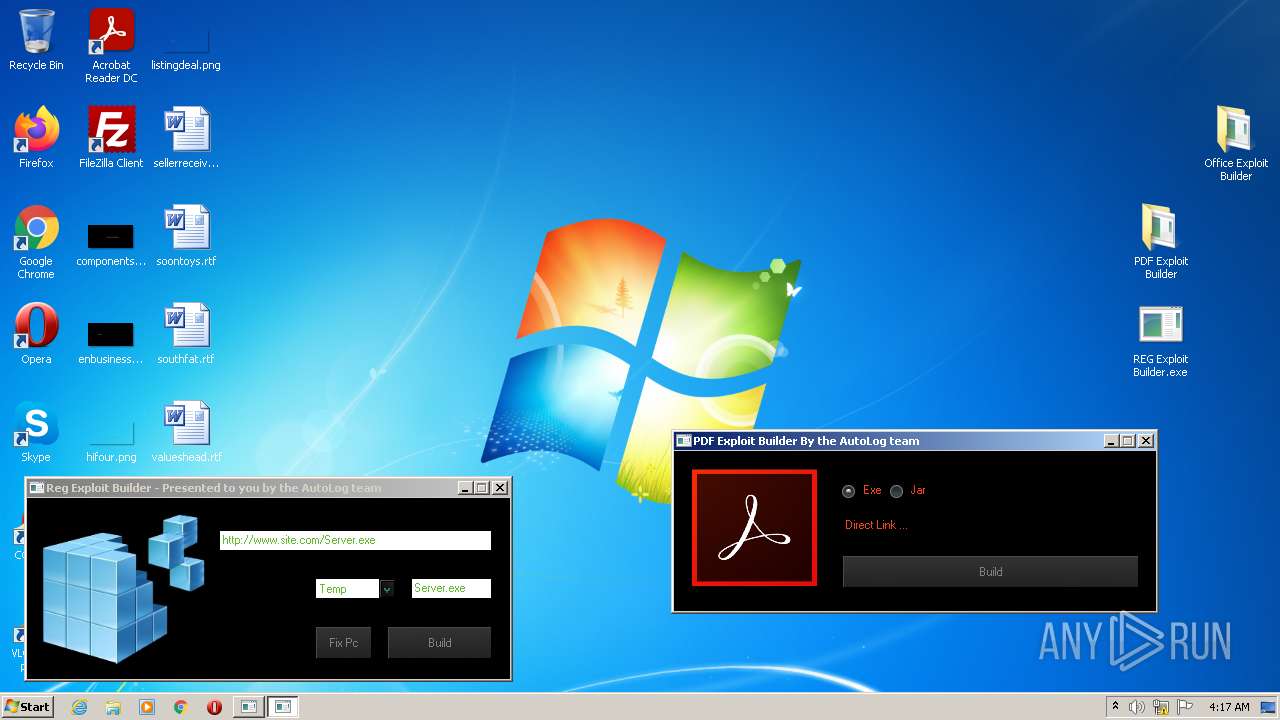
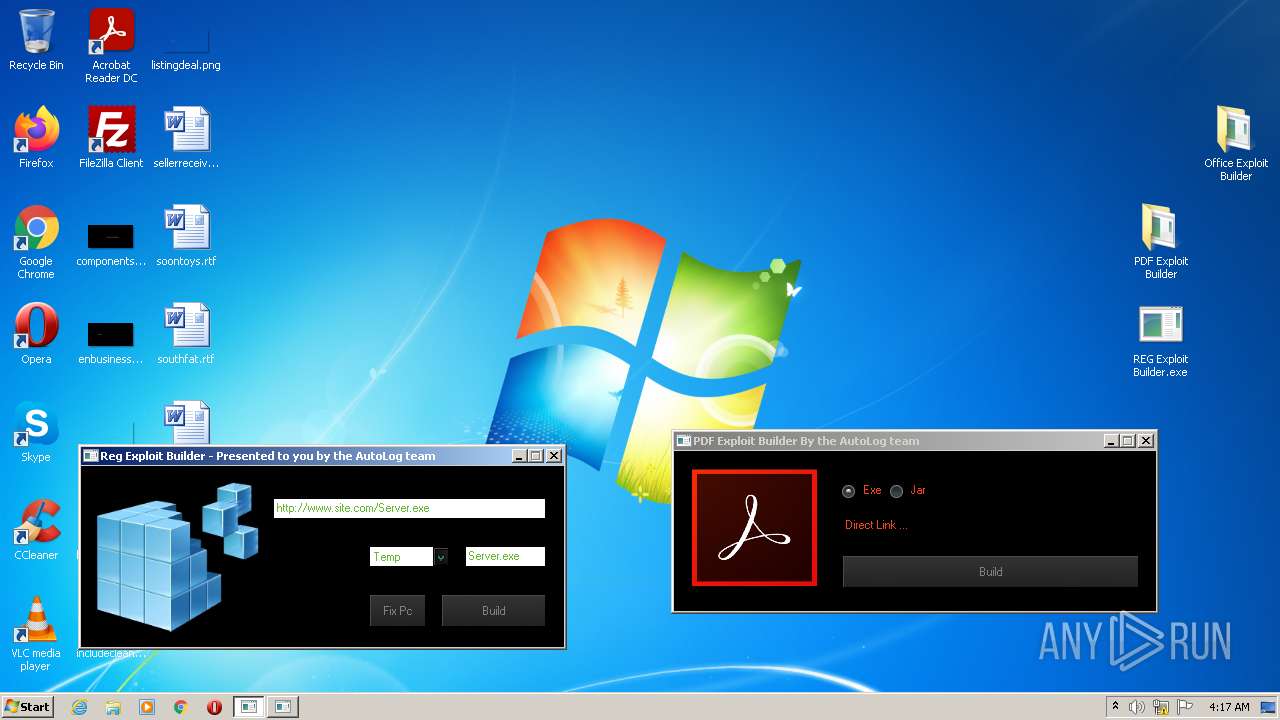
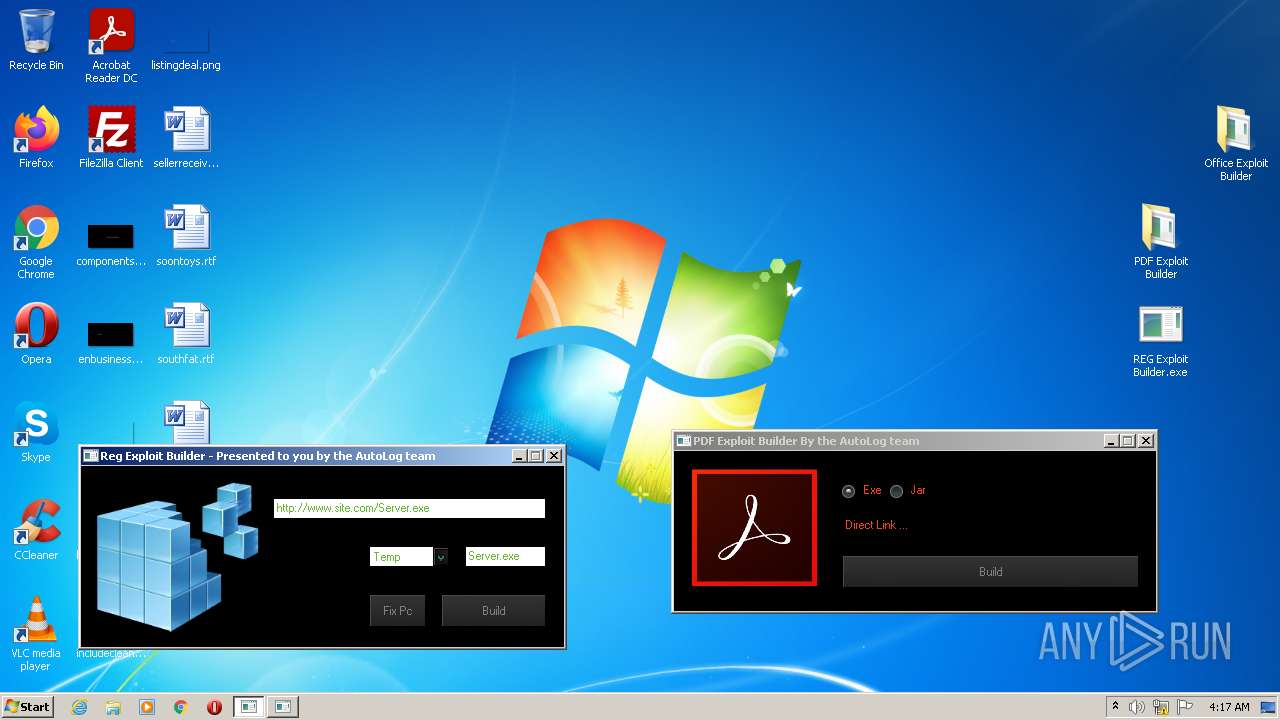
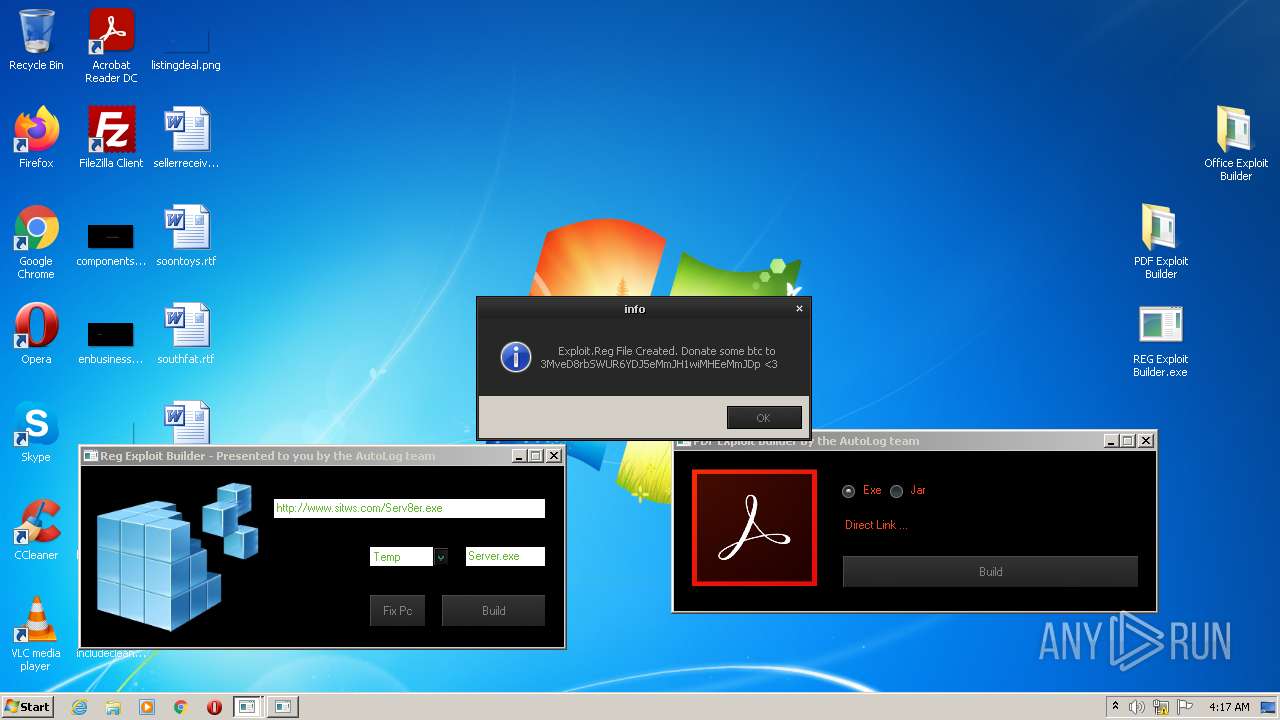
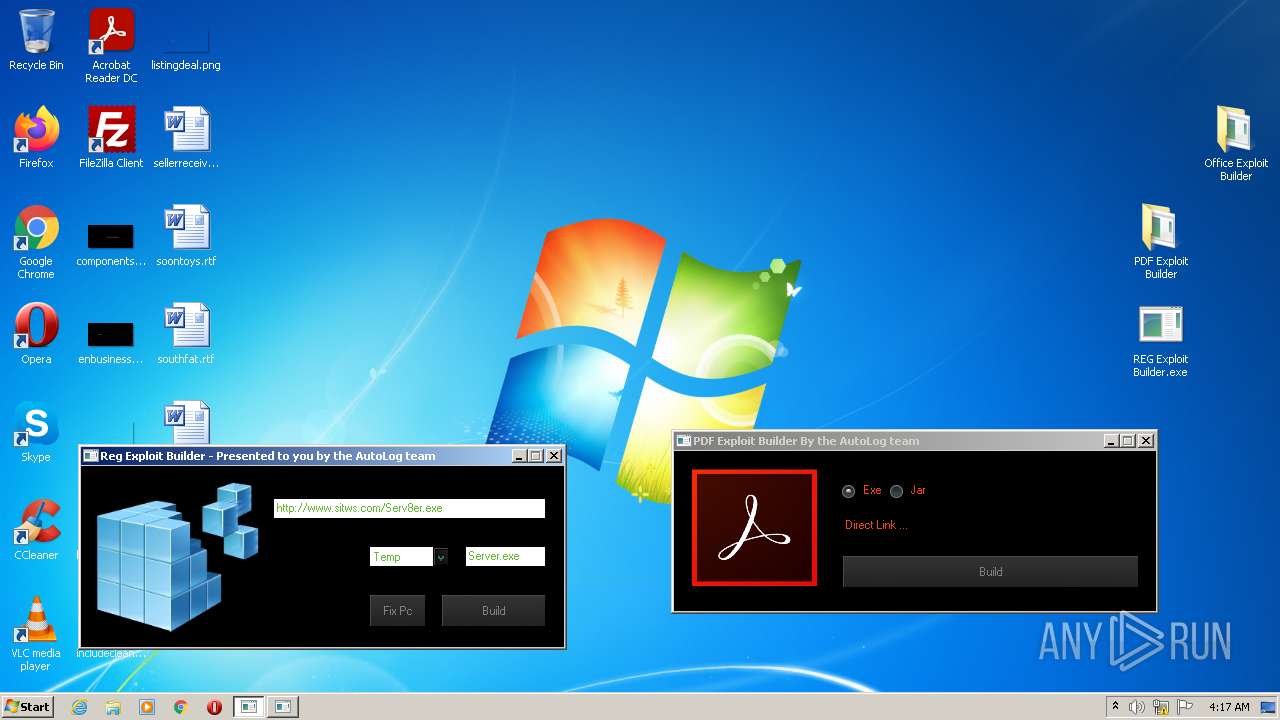
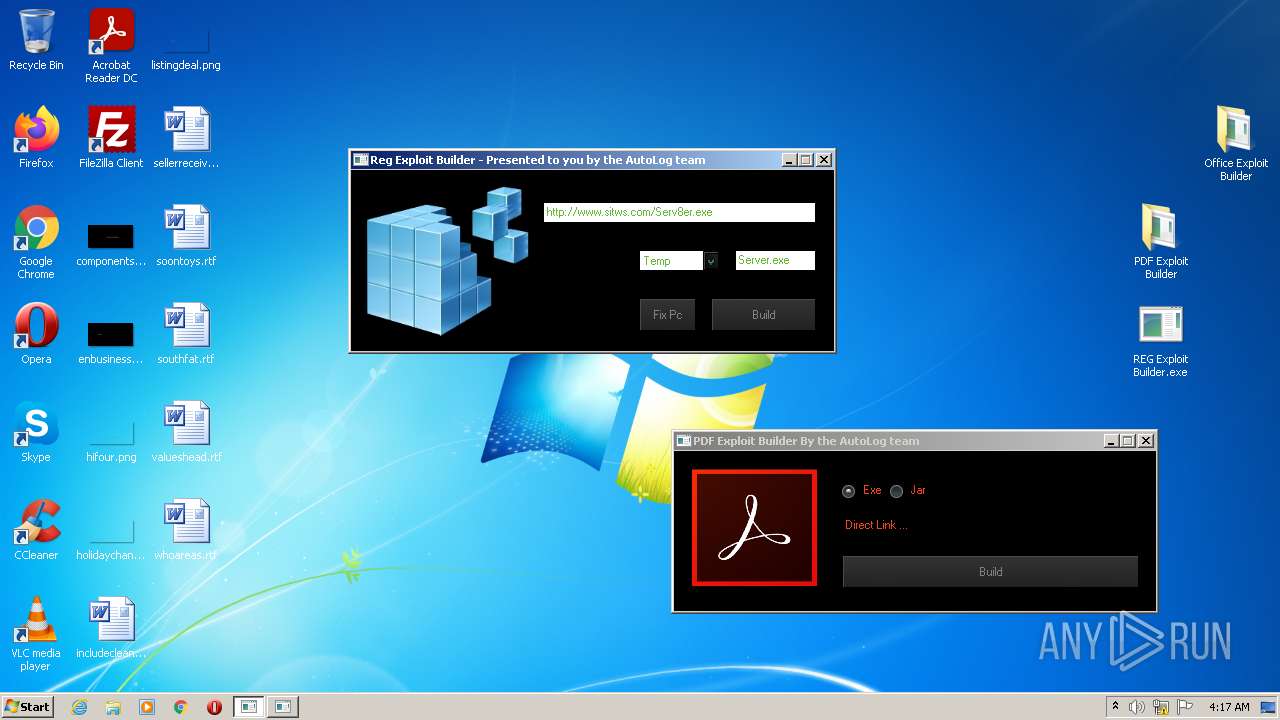
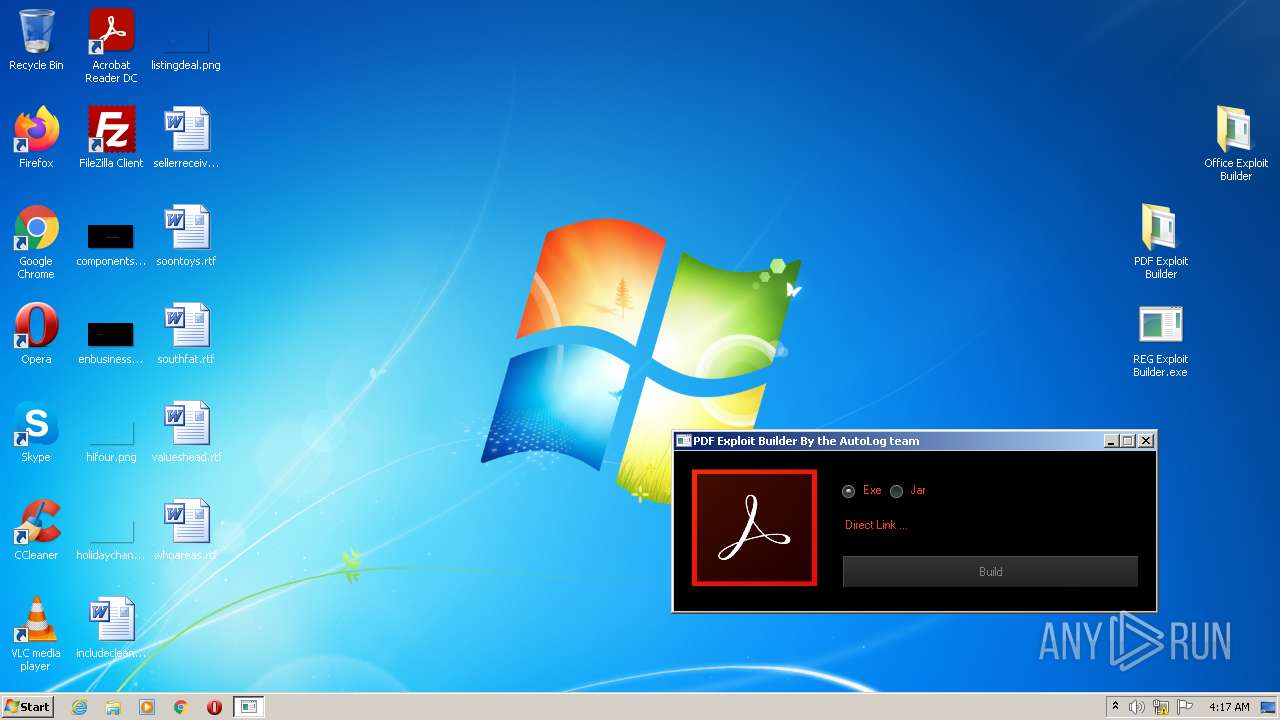
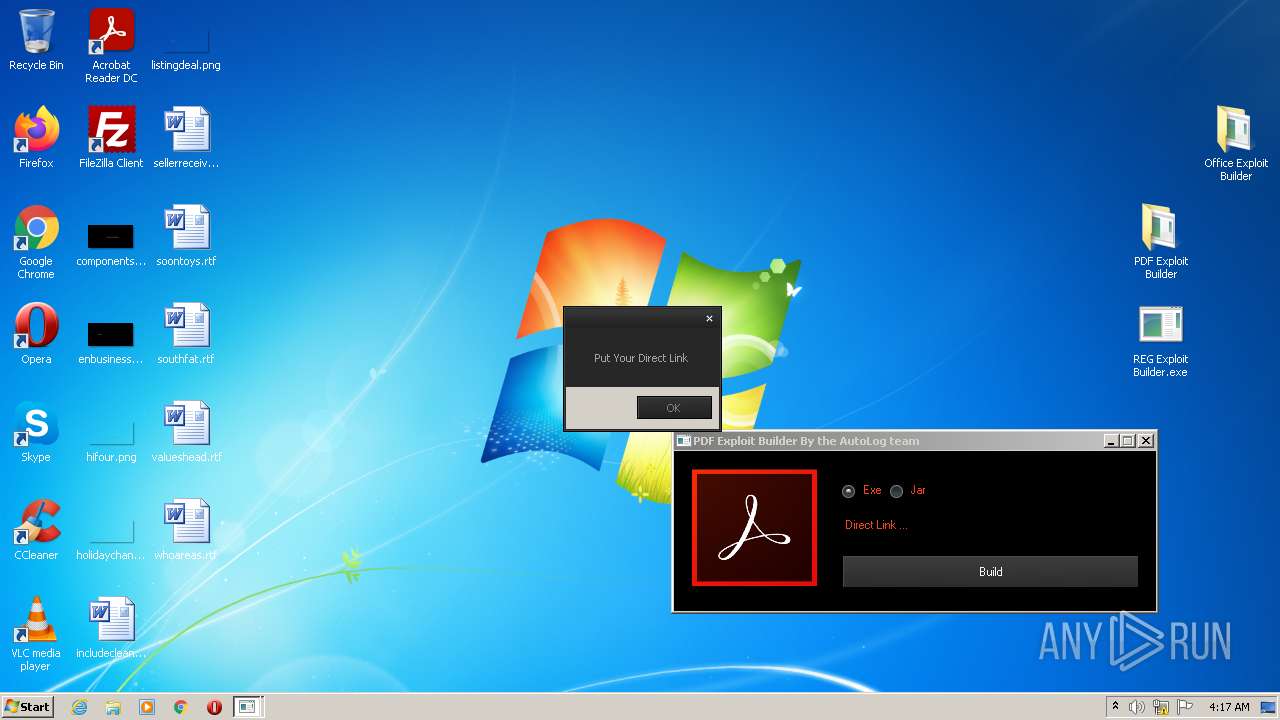
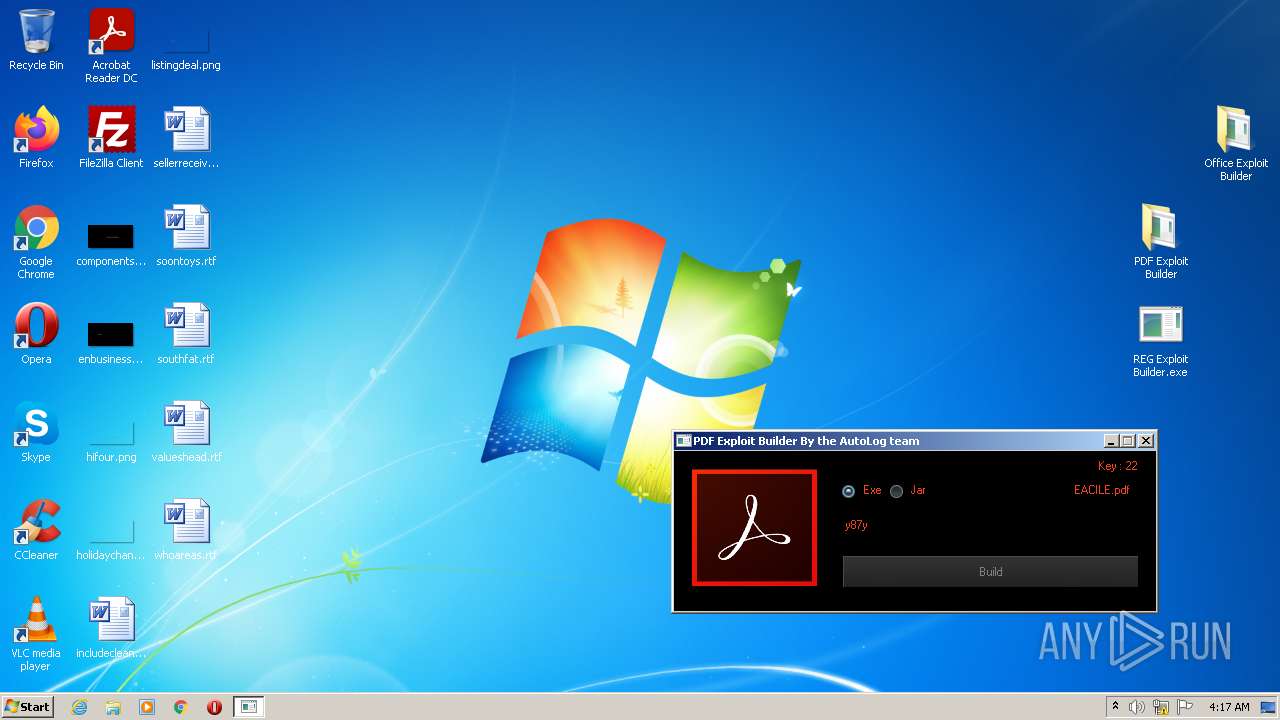
| File name: | Exploit Pack www.yourhacker.in.zip |
| Full analysis: | https://app.any.run/tasks/6aeba81f-5c4f-4639-b405-9763a39b9b54 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | May 21, 2022, 03:14:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 1556E689004D8F31DBD7D06EF5E05695 |
| SHA1: | 8C16FF871B70F74068F7D35A74FE27B444F9108E |
| SHA256: | E4A182083C97B29550D76D1496910A0EDA566C80BC03612BFAFCB48F8F79C50B |
| SSDEEP: | 196608:QXK9KW9x6BqzgXDML/XRqUJjqIgZRvvx55BKBQIPzZ8J1I1fBMTiC64:kGCB0cDML/bJuhZRHn5BKPqJ1WSWCl |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3064)
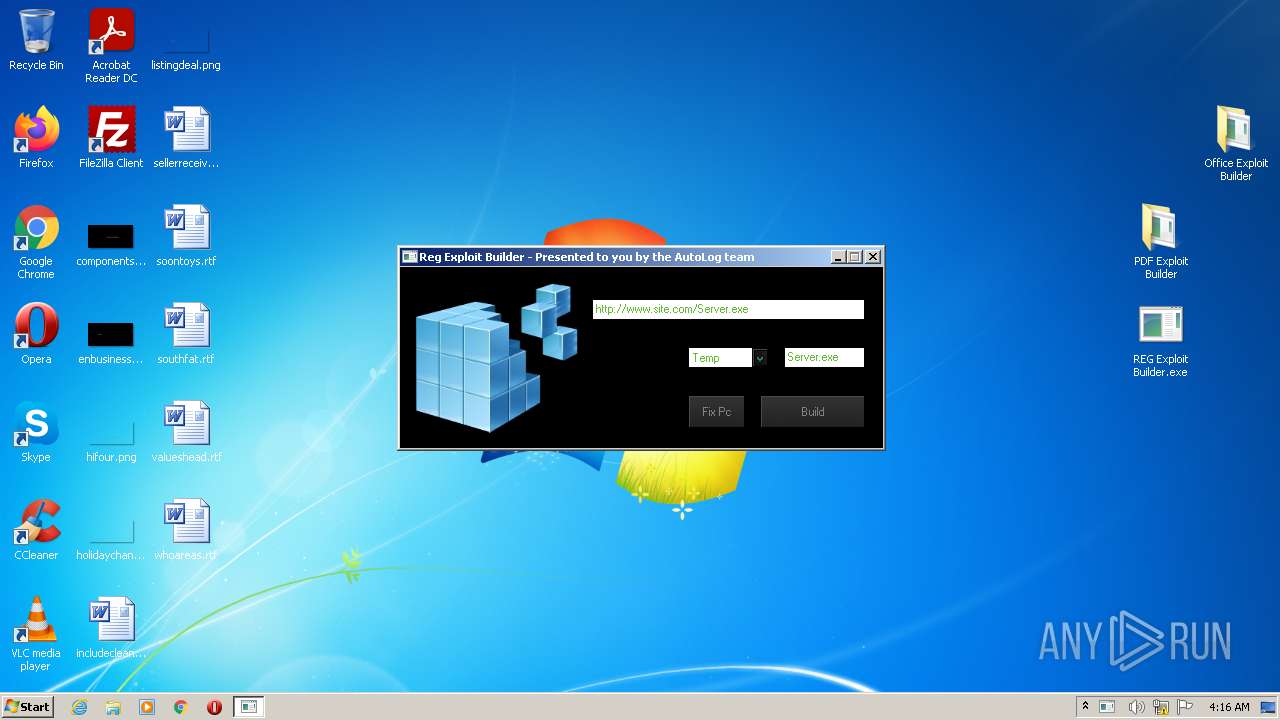
- REG Exploit Builder.exe (PID: 2676)
- cmd.exe (PID: 3360)
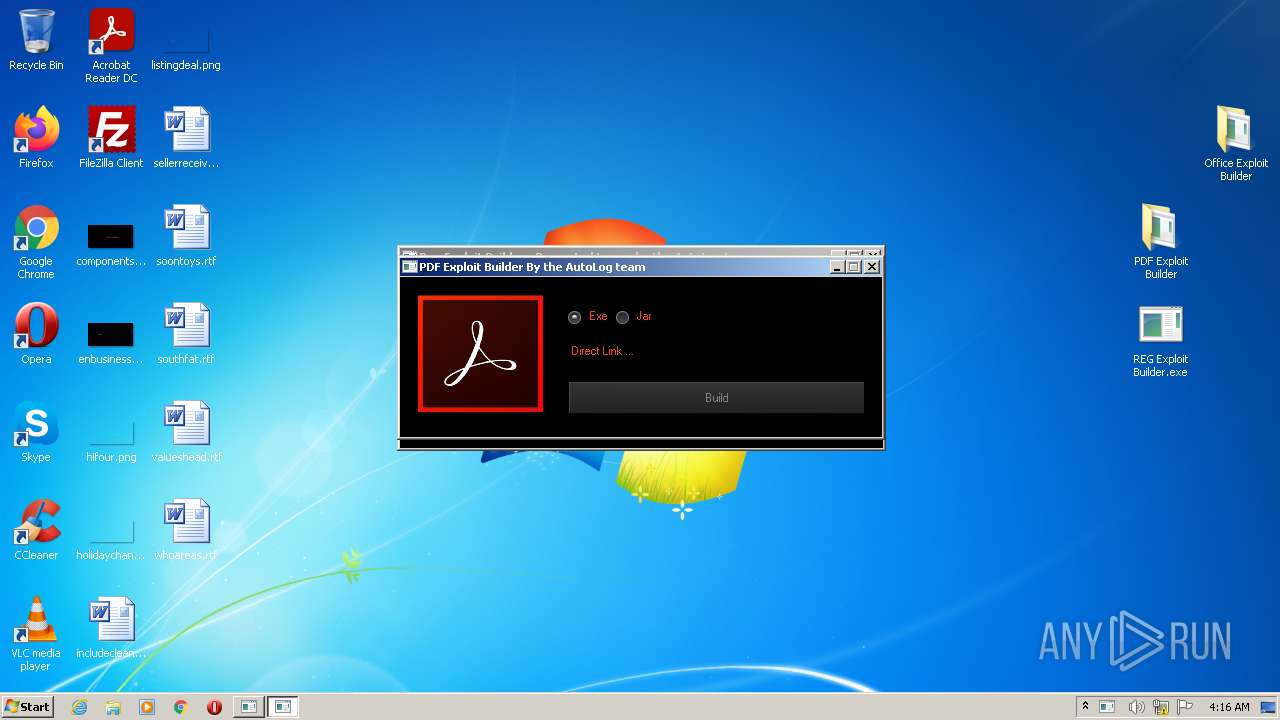
- PDF Exploit Builder.exe (PID: 624)
- REG Exploit Builder.exe (PID: 3564)
- PDF Exploit Builder.exe (PID: 3388)
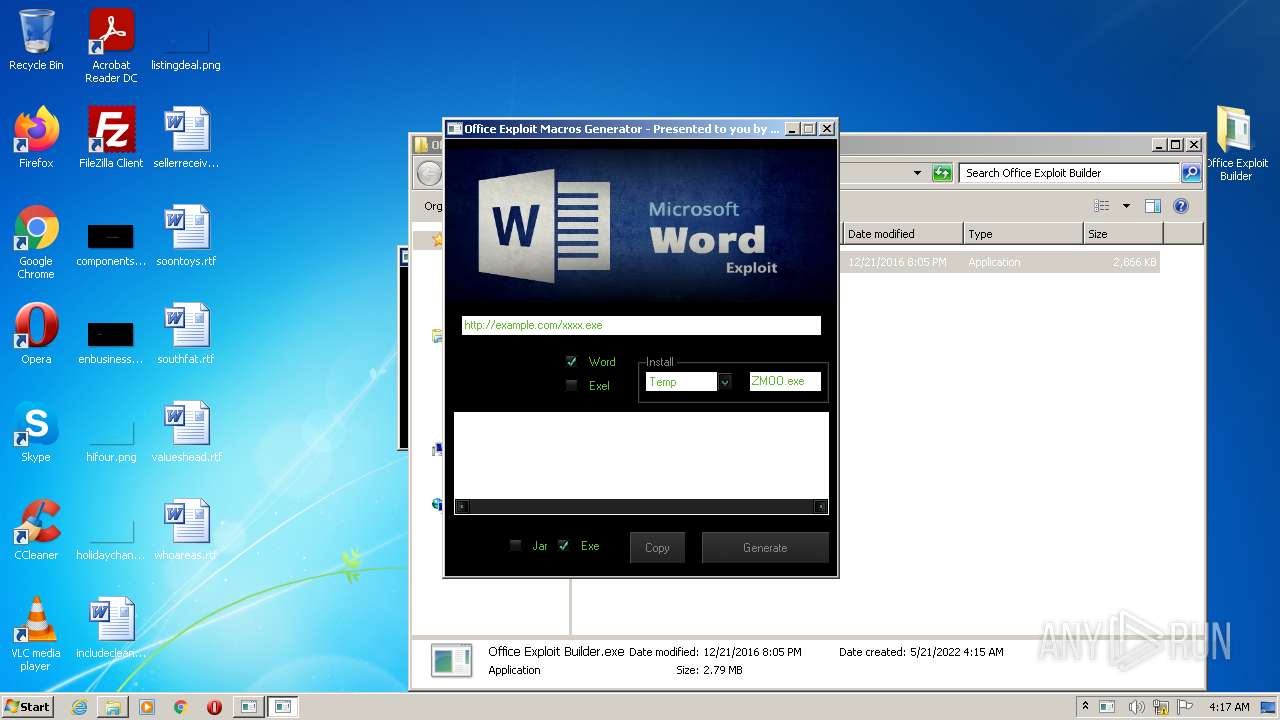
- Office Exploit Builder.exe (PID: 3728)
Application was dropped or rewritten from another process
- REG Exploit Builder.exe (PID: 2676)
- PDF Exploit Builder.exe (PID: 624)
- REG Exploit Builder.exe (PID: 3564)
- svchost.exe (PID: 3968)
- svchost.exe (PID: 1132)
- Office Exploit Builder.exe (PID: 3728)
- PDF Exploit Builder.exe (PID: 3388)
- svchost.exe (PID: 1768)
- Office Exploit Builder.exe (PID: 3148)
- REG Exploit Builder.exe (PID: 2600)
- REG Exploit Builder.exe (PID: 276)
- svchost.exe (PID: 3596)
- Office Exploit Builder.exe (PID: 3652)
- Office Exploit Builder.exe (PID: 2952)
- svchost.exe (PID: 3732)
Changes the autorun value in the registry
- reg.exe (PID: 2984)
- reg.exe (PID: 2868)
- reg.exe (PID: 3680)
- reg.exe (PID: 2860)
- reg.exe (PID: 3656)
Loads dropped or rewritten executable
- REG Exploit Builder.exe (PID: 3564)
- PDF Exploit Builder.exe (PID: 3388)
- Office Exploit Builder.exe (PID: 3148)
- REG Exploit Builder.exe (PID: 276)
- Office Exploit Builder.exe (PID: 2952)
Runs app for hidden code execution
- PDF Exploit Builder.exe (PID: 624)
- Office Exploit Builder.exe (PID: 3728)
- REG Exploit Builder.exe (PID: 2600)
- REG Exploit Builder.exe (PID: 2676)
- Office Exploit Builder.exe (PID: 3652)
DARKCOMET detected by memory dumps
- svchost.exe (PID: 3968)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3064)
- REG Exploit Builder.exe (PID: 2676)
- PDF Exploit Builder.exe (PID: 624)
- svchost.exe (PID: 3968)
- REG Exploit Builder.exe (PID: 3564)
- svchost.exe (PID: 1132)
- PDF Exploit Builder.exe (PID: 3388)
- Office Exploit Builder.exe (PID: 3728)
- svchost.exe (PID: 1768)
- Office Exploit Builder.exe (PID: 3148)
- REG Exploit Builder.exe (PID: 2600)
- Office Exploit Builder.exe (PID: 3652)
- REG Exploit Builder.exe (PID: 276)
- svchost.exe (PID: 3596)
- svchost.exe (PID: 3732)
- Office Exploit Builder.exe (PID: 2952)
Starts CMD.EXE for commands execution
- REG Exploit Builder.exe (PID: 2676)
- PDF Exploit Builder.exe (PID: 624)
- Office Exploit Builder.exe (PID: 3728)
- REG Exploit Builder.exe (PID: 2600)
- Office Exploit Builder.exe (PID: 3652)
Checks supported languages
- WinRAR.exe (PID: 3064)
- REG Exploit Builder.exe (PID: 2676)
- PDF Exploit Builder.exe (PID: 624)
- cmd.exe (PID: 240)
- svchost.exe (PID: 3968)
- PDF Exploit Builder.exe (PID: 3388)
- svchost.exe (PID: 1132)
- cmd.exe (PID: 3616)
- Office Exploit Builder.exe (PID: 3728)
- Office Exploit Builder.exe (PID: 3148)
- cmd.exe (PID: 4008)
- REG Exploit Builder.exe (PID: 2600)
- Office Exploit Builder.exe (PID: 3652)
- svchost.exe (PID: 1768)
- REG Exploit Builder.exe (PID: 276)
- cmd.exe (PID: 3236)
- REG Exploit Builder.exe (PID: 3564)
- cmd.exe (PID: 3360)
- cmd.exe (PID: 3144)
- Office Exploit Builder.exe (PID: 2952)
- svchost.exe (PID: 3596)
- svchost.exe (PID: 3732)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3064)
- cmd.exe (PID: 3360)
- PDF Exploit Builder.exe (PID: 624)
- REG Exploit Builder.exe (PID: 3564)
- PDF Exploit Builder.exe (PID: 3388)
- Office Exploit Builder.exe (PID: 3728)
- REG Exploit Builder.exe (PID: 2676)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3064)
- cmd.exe (PID: 3360)
- REG Exploit Builder.exe (PID: 3564)
- PDF Exploit Builder.exe (PID: 624)
- PDF Exploit Builder.exe (PID: 3388)
- Office Exploit Builder.exe (PID: 3728)
- REG Exploit Builder.exe (PID: 2676)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3360)
- cmd.exe (PID: 3616)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 3236)
- cmd.exe (PID: 3144)
Reads mouse settings
- REG Exploit Builder.exe (PID: 3564)
- PDF Exploit Builder.exe (PID: 3388)
- Office Exploit Builder.exe (PID: 3148)
- REG Exploit Builder.exe (PID: 276)
- Office Exploit Builder.exe (PID: 2952)
Creates executable files which already exist in Windows
- REG Exploit Builder.exe (PID: 2676)
Creates files in the user directory
- svchost.exe (PID: 3968)
INFO
Manual execution by user
- REG Exploit Builder.exe (PID: 2676)
- PDF Exploit Builder.exe (PID: 624)
- Office Exploit Builder.exe (PID: 3728)
- Office Exploit Builder.exe (PID: 3652)
- REG Exploit Builder.exe (PID: 2600)
Checks supported languages
- reg.exe (PID: 2984)
- timeout.exe (PID: 2320)
- reg.exe (PID: 2868)
- reg.exe (PID: 3680)
- reg.exe (PID: 2860)
- reg.exe (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DarkComet
(PID) Process(3968) svchost.exe
C2 (1)subdomain-dns.duckdns.org:3725
Version#KCMDDC51#
MutexDC_MUTEX-ULRUWYX
sid3XPL01T
FWB0
gencodegRoaiSdA59FN
Offline keyloggerTrue
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | PDF Exploit Builder/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2019:12:31 07:20:16 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
71
Monitored processes
28
Malicious processes
10
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\Macromed\FlashPlayerUpdateService.exe.bat | C:\Windows\system32\cmd.exe | — | REG Exploit Builder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 276 | "C:\Users\admin\AppData\Local\Temp\REG Exploit Builder.exe" | C:\Users\admin\AppData\Local\Temp\REG Exploit Builder.exe | — | REG Exploit Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 624 | "C:\Users\admin\Desktop\PDF Exploit Builder\PDF Exploit Builder.exe" | C:\Users\admin\Desktop\PDF Exploit Builder\PDF Exploit Builder.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1132 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | — | PDF Exploit Builder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1768 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | — | Office Exploit Builder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2320 | timeout /t 300 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2600 | "C:\Users\admin\Desktop\REG Exploit Builder.exe" | C:\Users\admin\Desktop\REG Exploit Builder.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader 9.0 Exit code: 0 Version: 9.0.0.2008061200 Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\Desktop\REG Exploit Builder.exe" | C:\Users\admin\Desktop\REG Exploit Builder.exe | Explorer.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader 9.0 Exit code: 0 Version: 9.0.0.2008061200 Modules
| |||||||||||||||
| 2860 | reg add "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows" /v Load /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\Macromed\FlashPlayerUpdateService.exe.lnk " /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2868 | reg add "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows" /v Load /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\Macromed\FlashPlayerUpdateService.exe.lnk " /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 763
Read events
8 688
Write events
75
Delete events
0
Modification events
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Exploit Pack www.yourhacker.in.zip | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3064) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
12
Suspicious files
9
Text files
10
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2676 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\REG Exploit Builder.exe | executable | |
MD5:— | SHA256:— | |||
| 2676 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\Macromed\FlashPlayerUpdateService.exe.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3564 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\imdf.jpg | image | |
MD5:— | SHA256:— | |||
| 3564 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\aut25C5.tmp | image | |
MD5:— | SHA256:— | |||
| 3064 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3064.11175\REG Exploit Builder\REG Exploit Builder.exe | executable | |
MD5:473FE6918F601D2B47114D0665AA8B86 | SHA256:379AB075E2240BCC4B1052380E004B54D0D8D28FF769F7BDD5C8B72B9F2425FB | |||
| 3564 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\aut25D5.tmp | binary | |
MD5:CB68E4CE4BAC8B40E64064A76F765F76 | SHA256:45E7A6813B60E5F2F3E1F3B6E40AAC0380B61CC8C867DC3C975D7A946BA95431 | |||
| 2676 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\Macromed\FlashPlayerUpdateService.exe.bat | text | |
MD5:— | SHA256:— | |||
| 3064 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3064.10670\PDF Exploit Builder\PDF Exploit Builder.exe | executable | |
MD5:9BE355706F21BA8F5DBD06224B7E5FED | SHA256:F37AC82BE444ADFEBCDDC1A2A0E1A5BA1EF90394067265F51A771A3896690C17 | |||
| 2676 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\svchost.exe | executable | |
MD5:30426476DE94A57F7807277BE471E32E | SHA256:DA5C2D3E6B5E937DB77E725E1C4BE5D1A7C32B9DA24D2A93CB86736087C466D0 | |||
| 3564 | REG Exploit Builder.exe | C:\Users\admin\AppData\Local\Temp\aut25F7.tmp | executable | |
MD5:29E1D5770184BF45139084BCED50D306 | SHA256:794987C4069286F797631F936C73B925C663C42D552AECA821106DFC7C7BA307 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
3
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 84.220.40.120:3725 | subdomain-dns.duckdns.org | Tiscali SpA | IT | unknown |
3968 | svchost.exe | 84.220.40.120:3725 | subdomain-dns.duckdns.org | Tiscali SpA | IT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
subdomain-dns.duckdns.org |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |