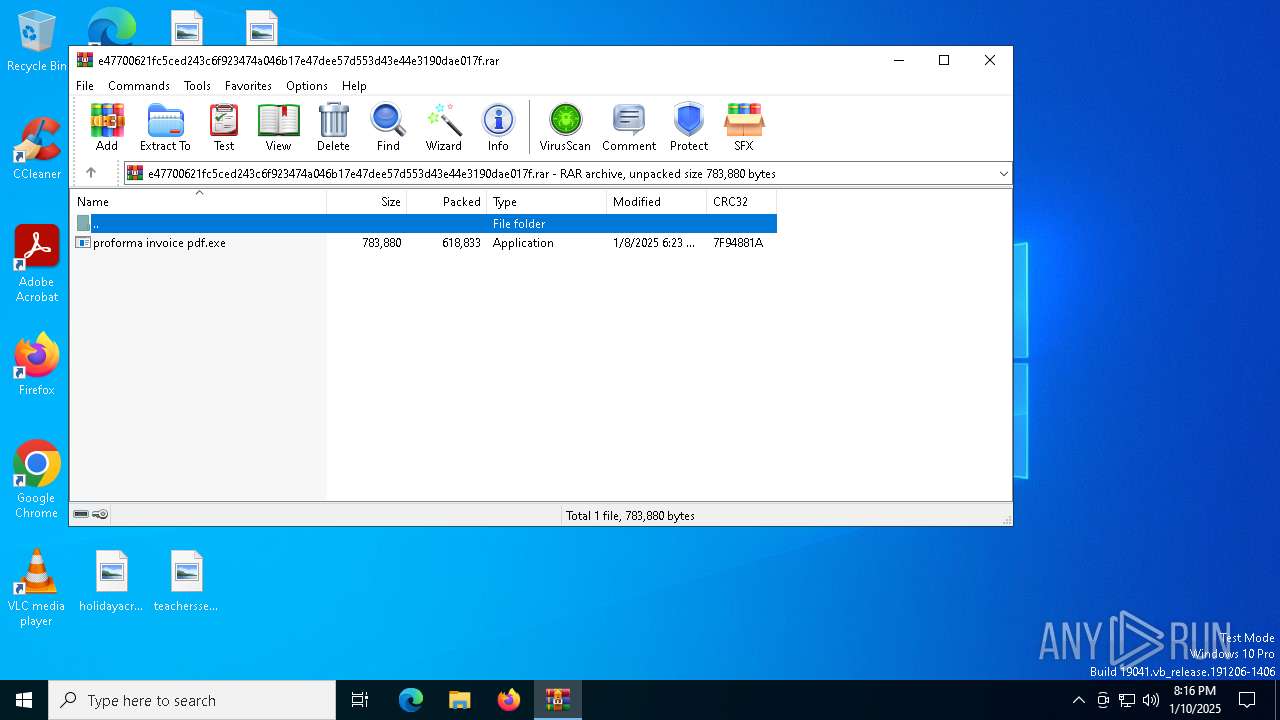
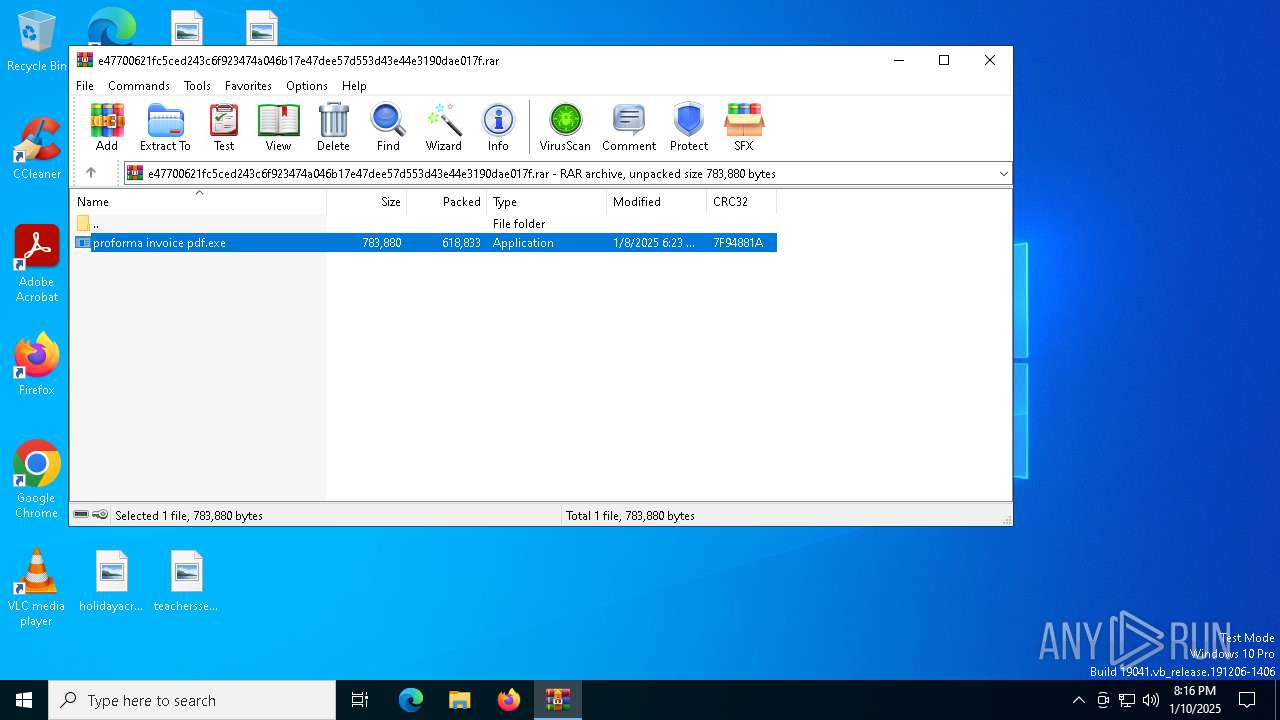
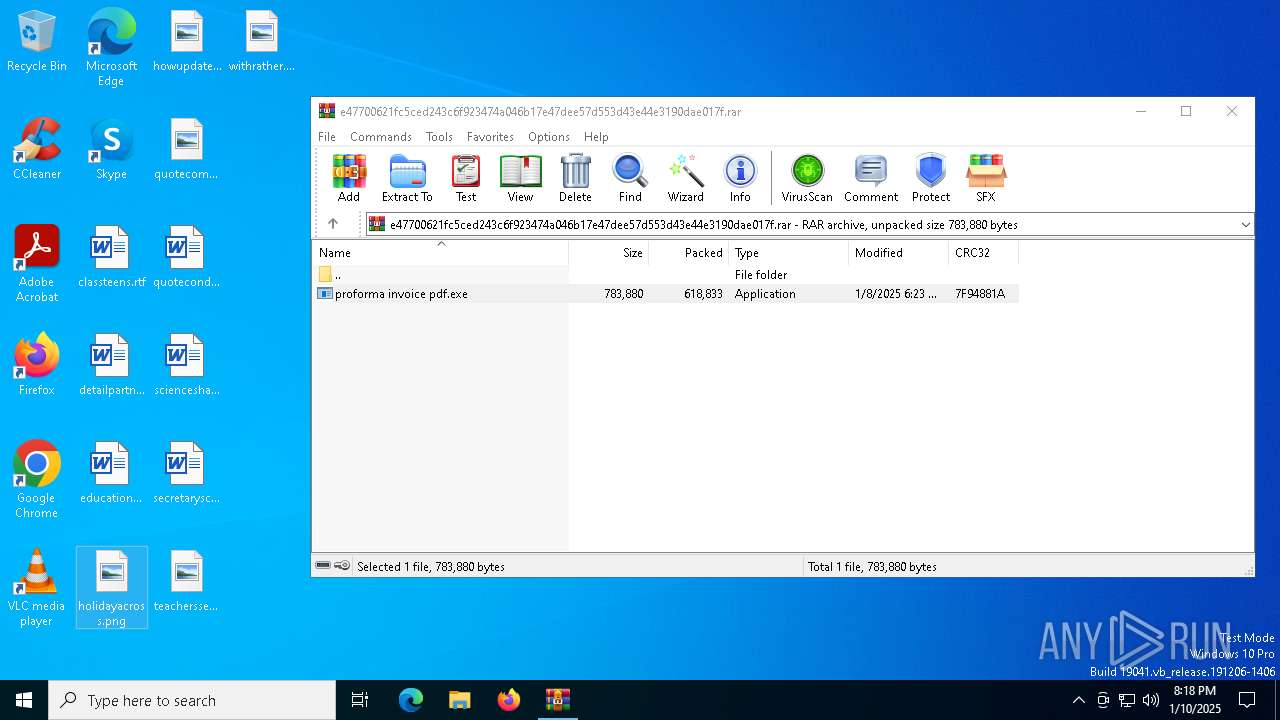
| download: | /1e0d79e1-635c-41f5-941a-d22021802032/2025-01-08/bnajdk9b0q1mkdimuok0k3lfntffcd91v50d5r01/e47700621fc5ced243c6f923474a046b17e47dee57d553d43e44e3190dae017f |
| Full analysis: | https://app.any.run/tasks/b9dd0309-781b-4752-8f74-df82381e3419 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | January 10, 2025, 20:16:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1A99740D66EAD67349E23847B42A4A57 |
| SHA1: | 4D695766214270C7300BACCAD8A899C8DC7A658A |
| SHA256: | E47700621FC5CED243C6F923474A046B17E47DEE57D553D43E44E3190DAE017F |
| SSDEEP: | 24576:NRusAq+//cl0nFyrL7sud+UfHNpHlHEwDTs0YQAO1py6iRP:NRusAq+//cinFyrL7sud+UfHNpHlHEcG |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5432)
Executing a file with an untrusted certificate
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Uses Task Scheduler to run other applications
- proforma invoice pdf.exe (PID: 6772)
Steals credentials from Web Browsers
- proforma invoice pdf.exe (PID: 6984)
Changes the autorun value in the registry
- proforma invoice pdf.exe (PID: 6984)
Actions looks like stealing of personal data
- proforma invoice pdf.exe (PID: 6984)
AGENTTESLA has been detected (YARA)
- proforma invoice pdf.exe (PID: 6984)
SUSPICIOUS
Starts a Microsoft application from unusual location
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5432)
- proforma invoice pdf.exe (PID: 6772)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5432)
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Executable content was dropped or overwritten
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Application launched itself
- proforma invoice pdf.exe (PID: 6772)
Checks for external IP
- proforma invoice pdf.exe (PID: 6984)
The process connected to a server suspected of theft
- proforma invoice pdf.exe (PID: 6984)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- proforma invoice pdf.exe (PID: 6984)
Possible usage of Discord/Telegram API has been detected (YARA)
- proforma invoice pdf.exe (PID: 6984)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5432)
The process uses the downloaded file
- WinRAR.exe (PID: 5432)
- proforma invoice pdf.exe (PID: 6772)
Reads the computer name
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Checks supported languages
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Reads the machine GUID from the registry
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Creates files or folders in the user directory
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Create files in a temporary directory
- proforma invoice pdf.exe (PID: 6772)
- proforma invoice pdf.exe (PID: 6984)
Process checks computer location settings
- proforma invoice pdf.exe (PID: 6772)
Checks proxy server information
- proforma invoice pdf.exe (PID: 6984)
Disables trace logs
- proforma invoice pdf.exe (PID: 6984)
Reads the software policy settings
- proforma invoice pdf.exe (PID: 6984)
Attempting to use instant messaging service
- proforma invoice pdf.exe (PID: 6984)
Manual execution by a user
- Taskmgr.exe (PID: 3260)
- Taskmgr.exe (PID: 2216)
- mspaint.exe (PID: 6608)
- mspaint.exe (PID: 6924)
- mspaint.exe (PID: 6744)
- mspaint.exe (PID: 6448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(6984) proforma invoice pdf.exe
C2https://api.telegram.org/bot5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c/
ims-api
(PID) Process(6984) proforma invoice pdf.exe
Telegram-Tokens (1)5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c
Telegram-Info-Links
5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c
Get info about bothttps://api.telegram.org/bot5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c/getMe
Get incoming updateshttps://api.telegram.org/bot5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c/getUpdates
Get webhookhttps://api.telegram.org/bot5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token5145135161:AAFnBnjYGtIUE_EwGqQ3-YIV1FOEItrzy8c
End-PointsendDocument
Args
Telegram-Responses
oktrue
result
message_id140621
from
id5145135161
is_bottrue
first_nameU2origin
usernameU2originbot
chat
id1279485009
first_nameMax
usernamezacsees
typeprivate
date1736540232
document
file_nameadmin-DESKTOP-JGLLJLD 2025-01-10 20-17-11.zip
mime_typeapplication/zip
file_idBQACAgQAAxkDAAECJU1ngYBIyf829Hidbho_WpFMLYNcBAACwRcAAh3sEFD-mrzO3AmvTDYE
file_unique_idAgADwRcAAh3sEFA
file_size10733
captionNew CO Recovered!
Time: 01/10/2025 20:17:10
User Name: admin/DESKTOP-JGLLJLD
OSFullName: Microsoft Windows 10 Pro
CPU: Intel(R) Core(TM) i5-6400 CPU @ 2.70GHz
RAM: 4090.45 MB
IP Address: 216.24.216.129
caption_entities
offset188
length14
typeurl
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 618833 |
| UncompressedSize: | 783880 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | proforma invoice pdf.exe |
Total processes
139
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2216 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5432 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\e47700621fc5ced243c6f923474a046b17e47dee57d553d43e44e3190dae017f.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6448 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\teacherssent.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6608 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\holidayacross.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6744 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\withrather.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6772 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5432.2180\proforma invoice pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5432.2180\proforma invoice pdf.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RDP Session Agent Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 6912 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\KbbpmaNYvNyuv" /XML "C:\Users\admin\AppData\Local\Temp\tmp99E2.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | proforma invoice pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6924 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\howupdates.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 179
Read events
7 062
Write events
113
Delete events
4
Modification events
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\e47700621fc5ced243c6f923474a046b17e47dee57d553d43e44e3190dae017f.rar | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6984) proforma invoice pdf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\proforma invoice pdf_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6984) proforma invoice pdf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\proforma invoice pdf_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
3
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6984 | proforma invoice pdf.exe | C:\Users\admin\AppData\Roaming\4jj4f3xs.5r5\Chrome\Default\Network\Cookies | binary | |
MD5:06AD9E737639FDC745B3B65312857109 | SHA256:C8925892CA8E213746633033AE95ACFB8DD9531BC376B82066E686AC6F40A404 | |||
| 6772 | proforma invoice pdf.exe | C:\Users\admin\AppData\Roaming\KbbpmaNYvNyuv.exe | executable | |
MD5:CFF00EA297618407A3FF1A4800066029 | SHA256:7488790C53F9CE42EE7B8138D93B6952693F3847D4A94F3AED0A535F15A3997F | |||
| 6772 | proforma invoice pdf.exe | C:\Users\admin\AppData\Local\Temp\tmp99E2.tmp | xml | |
MD5:853D960D92EE6F3C732322C72FCBBCB0 | SHA256:5946B1D0CFF583BEE48D18158D42E54FA8729F9CB143194A23EC7A902A670F26 | |||
| 6984 | proforma invoice pdf.exe | C:\Users\admin\AppData\Roaming\4jj4f3xs.5r5\Edge Chromium\Default\Network\Cookies | binary | |
MD5:46D9FCA6032297F8AEE08D73418312BA | SHA256:865856FA4C33C4AEE52E15FBB370B6611468FE947E76E197F0E50D0AD62CB1B4 | |||
| 6984 | proforma invoice pdf.exe | C:\Users\admin\AppData\Local\Temp\bmBOz\bmBOz.exe | executable | |
MD5:CFF00EA297618407A3FF1A4800066029 | SHA256:7488790C53F9CE42EE7B8138D93B6952693F3847D4A94F3AED0A535F15A3997F | |||
| 6984 | proforma invoice pdf.exe | C:\Users\admin\AppData\Roaming\4jj4f3xs.5r5\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite | binary | |
MD5:19BA68C3ECBCA72C2B90AFADDE745DC6 | SHA256:8B3758EE2D2C0A07EE7003F902F0667ABE5D9667941F8617EDA3CDF94C78E7B8 | |||
| 2216 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 5432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5432.2180\proforma invoice pdf.exe | executable | |
MD5:CFF00EA297618407A3FF1A4800066029 | SHA256:7488790C53F9CE42EE7B8138D93B6952693F3847D4A94F3AED0A535F15A3997F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
19
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6056 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5308 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5308 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4652 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
api.telegram.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6984 | proforma invoice pdf.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2192 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
6984 | proforma invoice pdf.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6984 | proforma invoice pdf.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6984 | proforma invoice pdf.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |