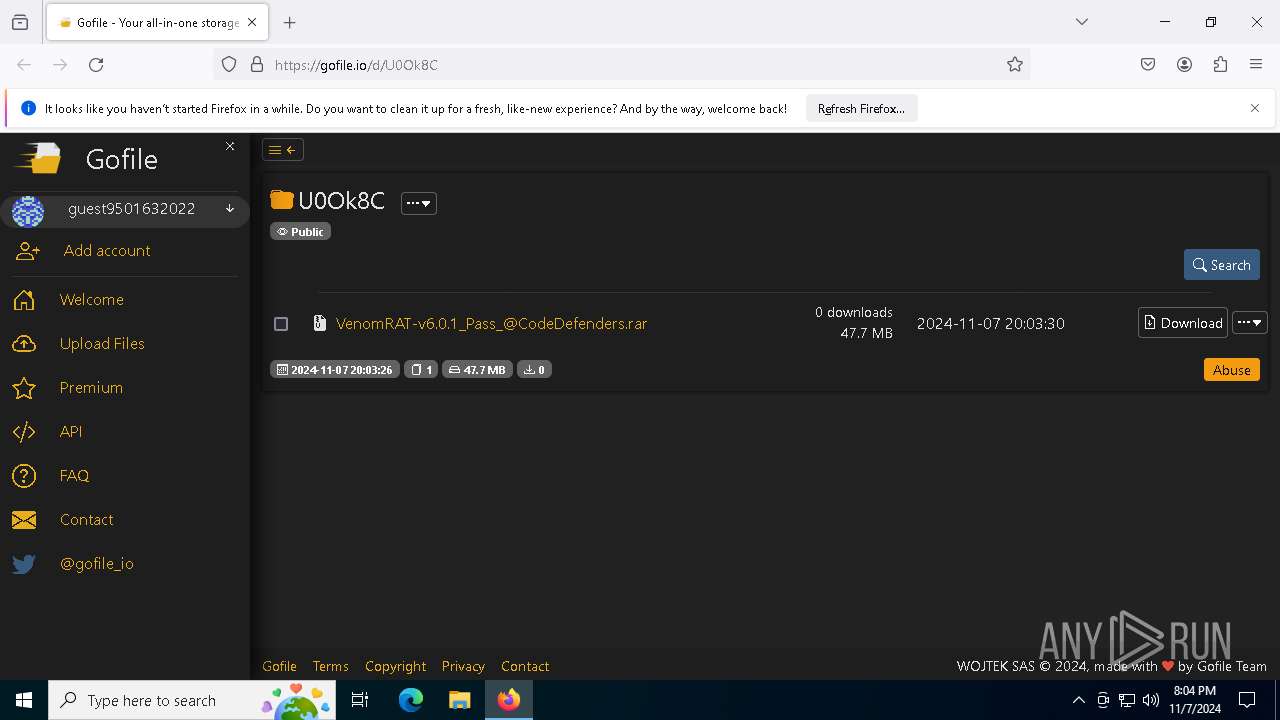
| URL: | https://gofile.io/d/U0Ok8C |
| Full analysis: | https://app.any.run/tasks/6ab61dd4-2c1a-4a6f-b302-cd7c1edd82bf |
| Verdict: | Malicious activity |
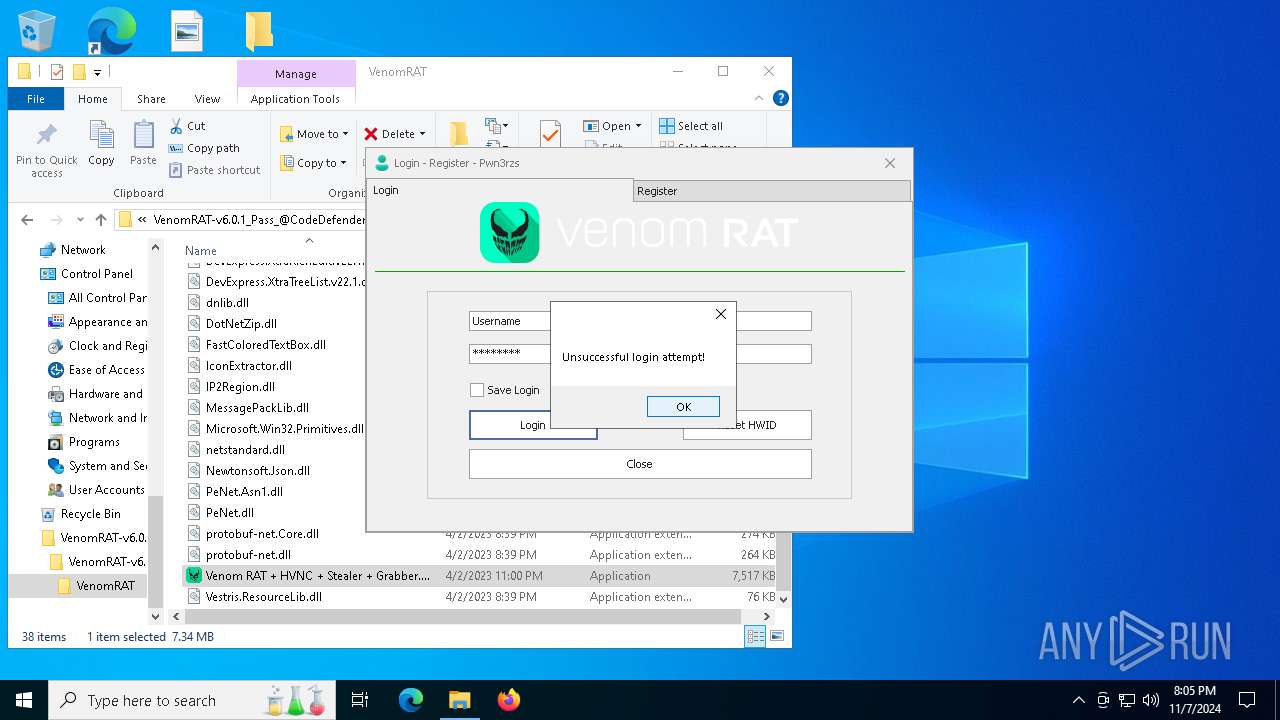
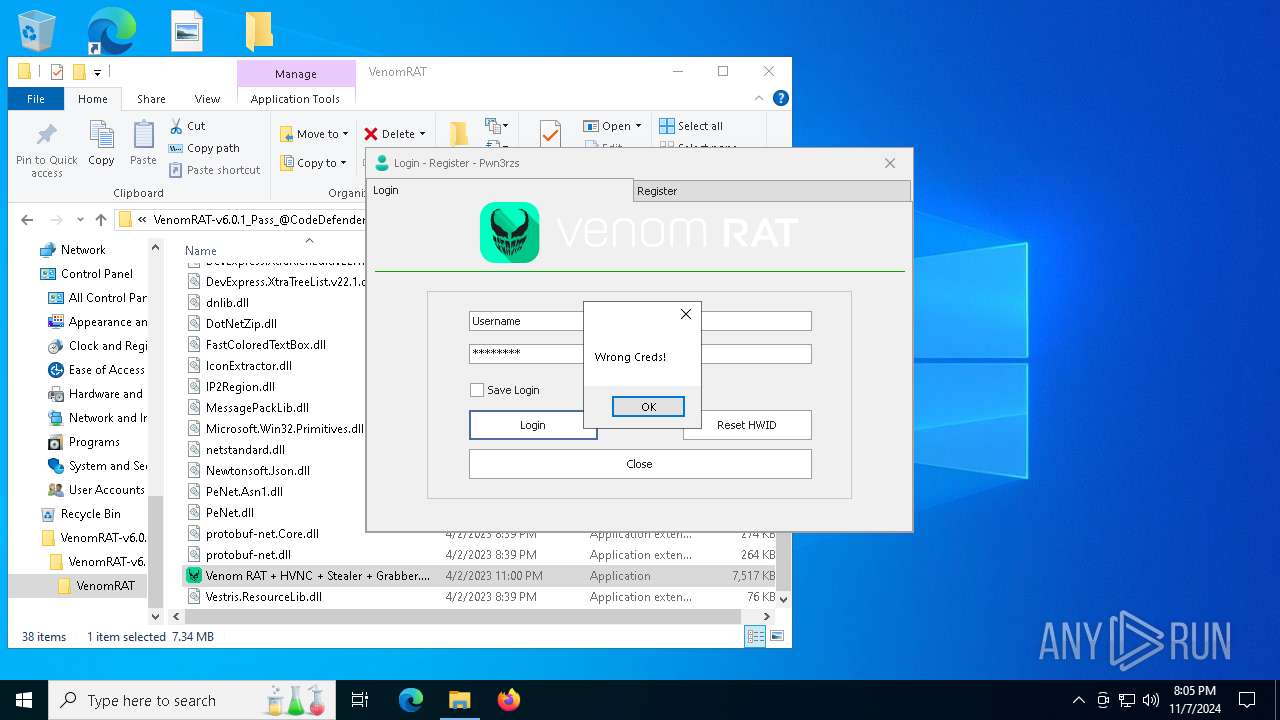
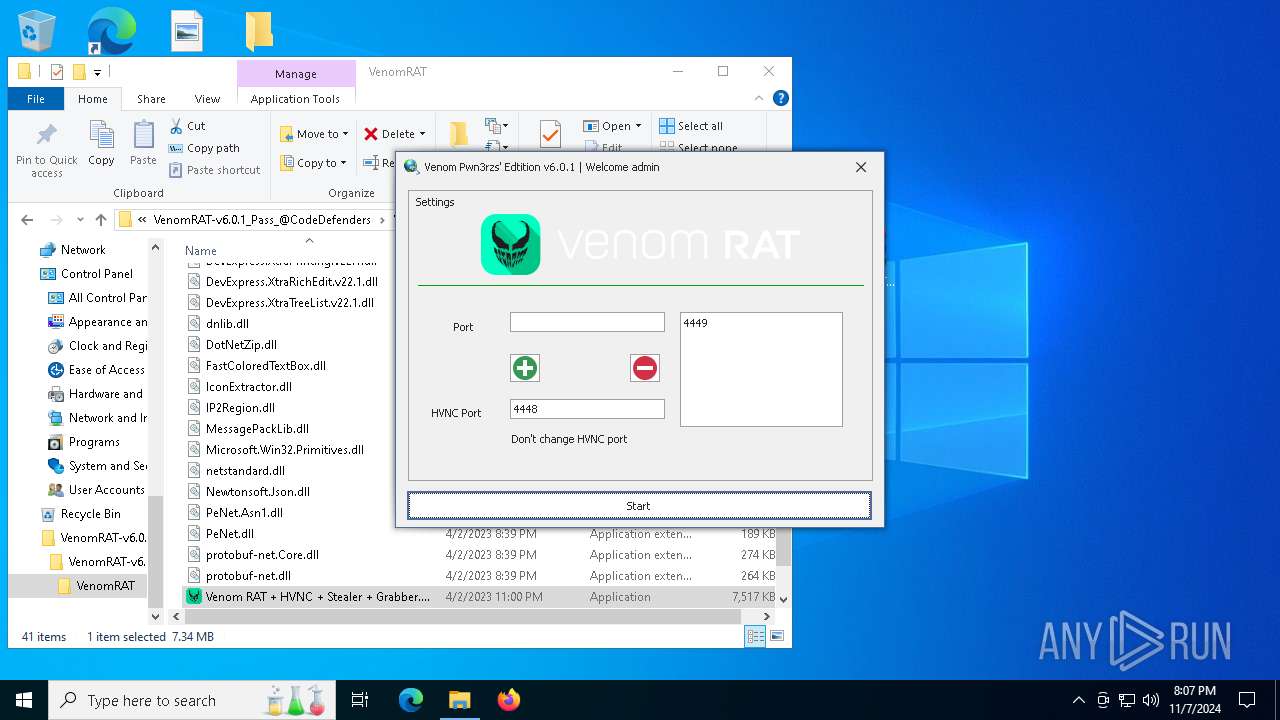
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | November 07, 2024, 20:04:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 199C66A924FC09E85B22847E3740B51F |
| SHA1: | 275518963AB8DC5B8B24CC71360F5260FE06E3DB |
| SHA256: | E475C498D18337A79E7D2992D643DA3B5001A4322C06987F5EBFF20E6E5A9E78 |
| SSDEEP: | 3:N8rxL1tn:2Z/n |
MALICIOUS
ASYNCRAT has been detected (YARA)
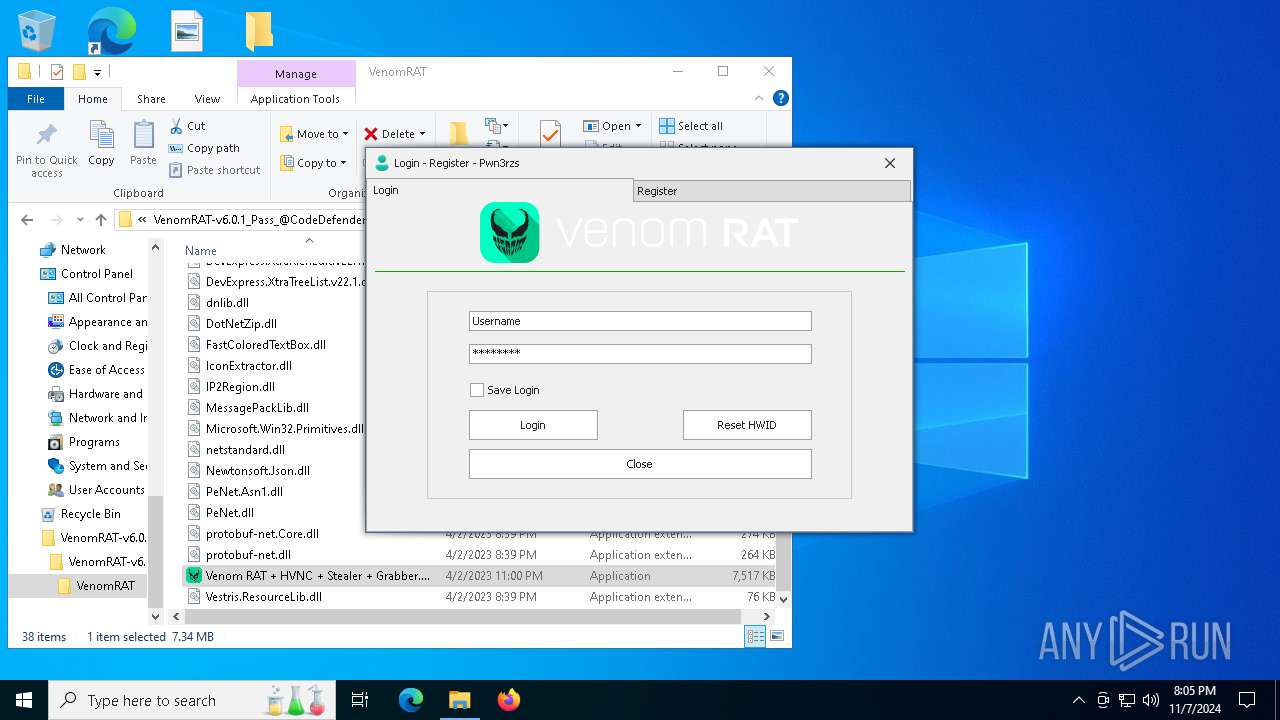
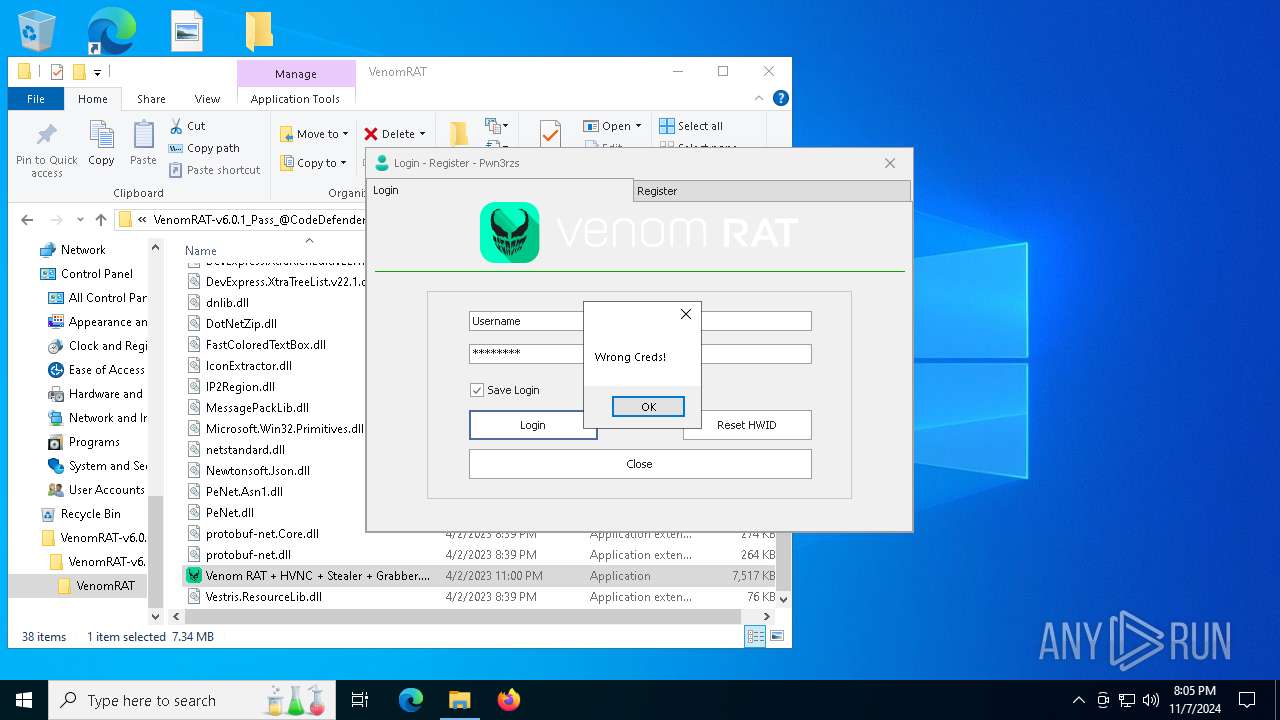
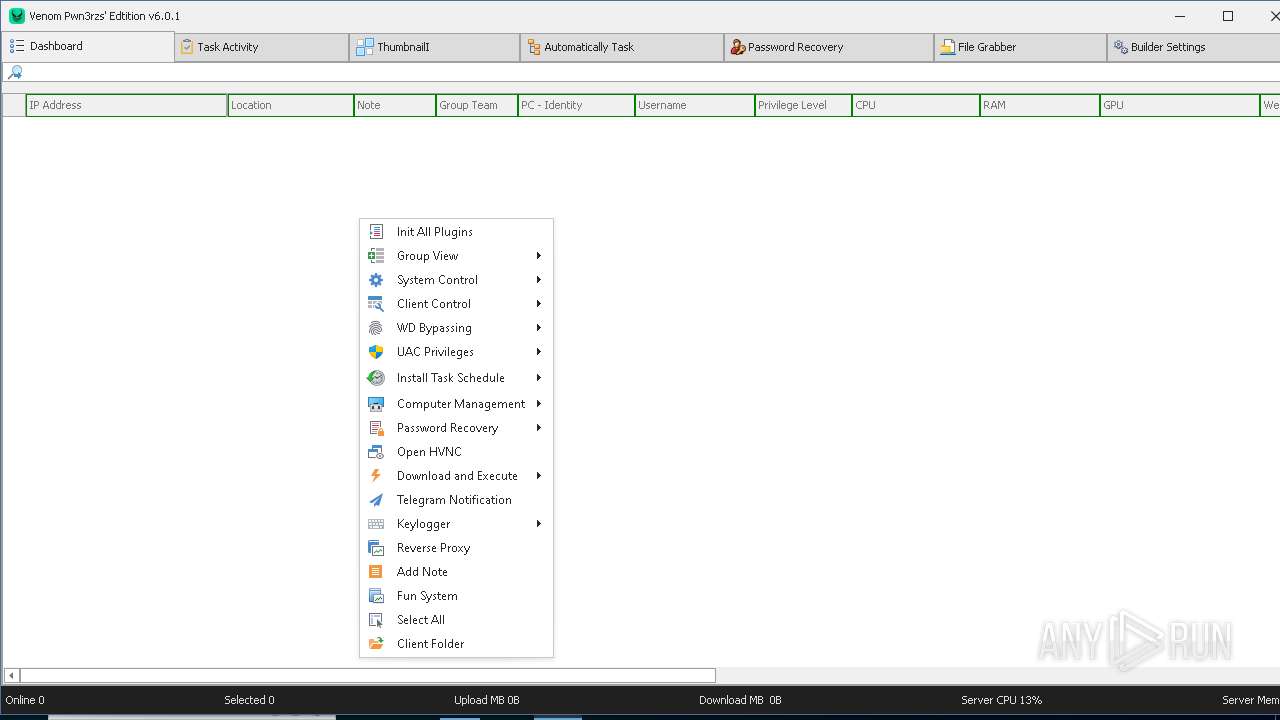
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 7344)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6192)
Possible usage of Discord/Telegram API has been detected (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 7344)
There is functionality for taking screenshot (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 7344)
INFO
Application launched itself
- firefox.exe (PID: 6684)
- firefox.exe (PID: 6708)
Manual execution by a user
- WinRAR.exe (PID: 6192)
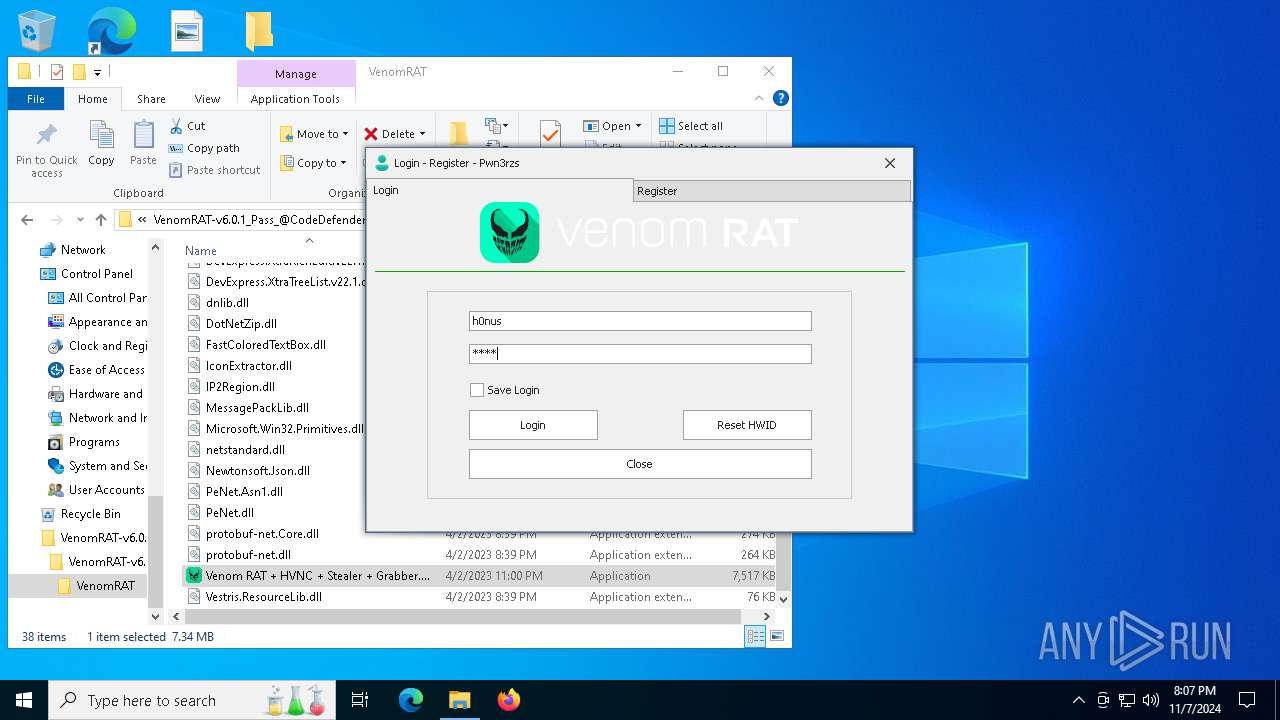
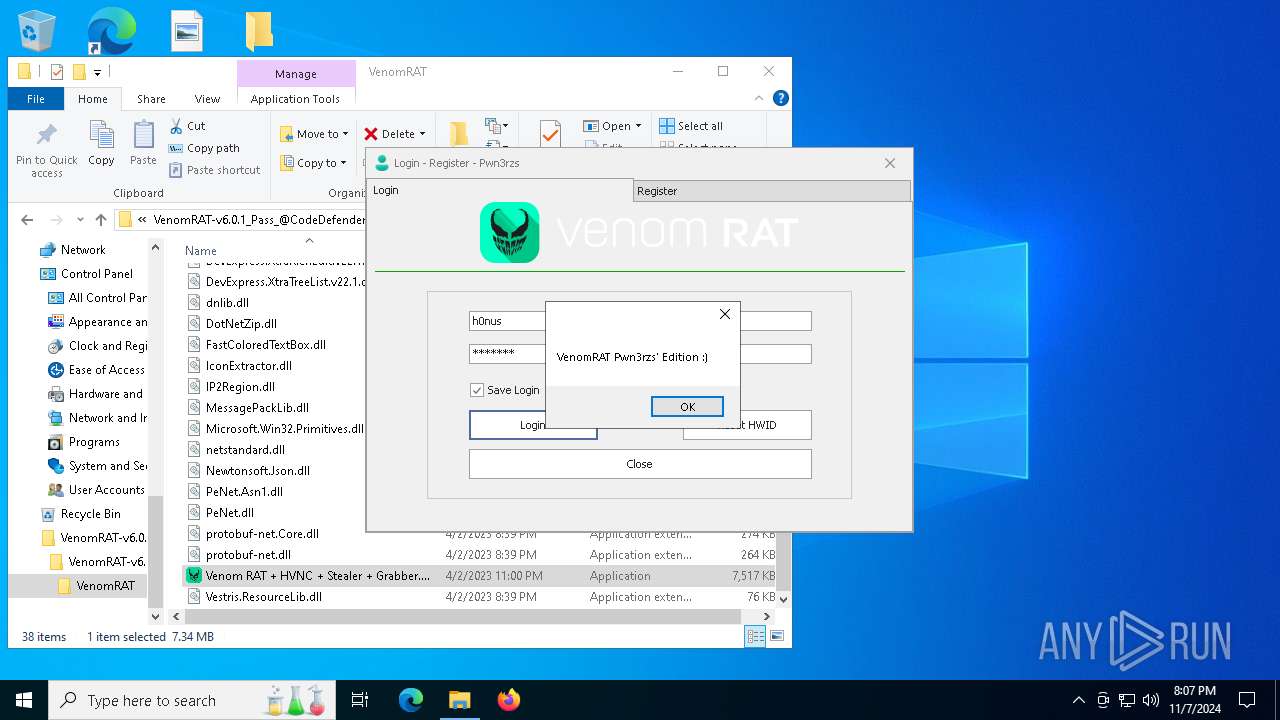
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 7344)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6192)
.NET Reactor protector has been detected
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 7344)
Themida protector has been detected
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 7344)
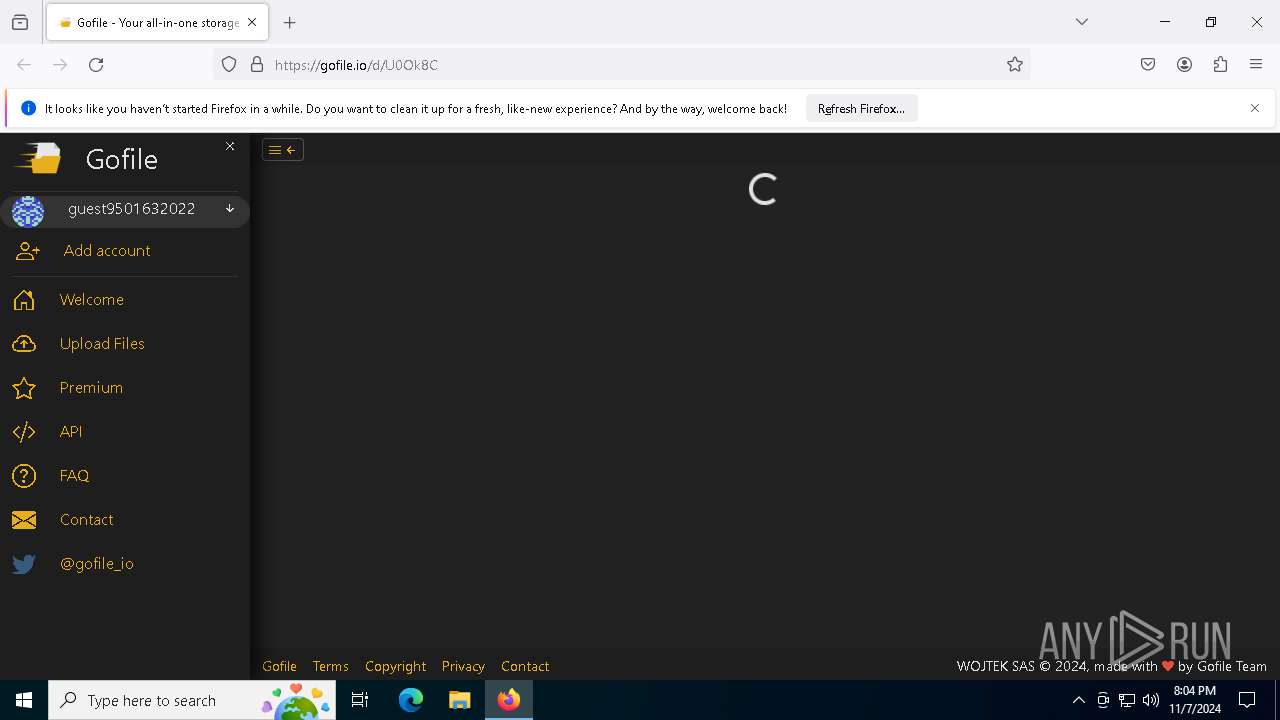
Attempting to use file storage service
- firefox.exe (PID: 6684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7344) Venom RAT + HVNC + Stealer + Grabber.exe
Telegram-Tokens (1)5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Telegram-Info-Links
5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Get info about bothttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getMe
Get incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getUpdates
Get webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Info-Links
1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Total processes
152
Monitored processes
18
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3276 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2884 -childID 1 -isForBrowser -prefsHandle 2876 -prefMapHandle 2872 -prefsLen 26798 -prefMapSize 244343 -jsInitHandle 1324 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ddb3674a-4c74-400c-915e-1ddb96127a25} 6684 "\\.\pipe\gecko-crash-server-pipe.6684" 2182df5e150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 3912 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1716 -parentBuildID 20240213221259 -prefsHandle 1748 -prefMapHandle 1740 -prefsLen 30705 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {3e7e0c02-2fe7-4353-bccb-edbe90f4d236} 6684 "\\.\pipe\gecko-crash-server-pipe.6684" 218280c2710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 3952 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2192 -parentBuildID 20240213221259 -prefsHandle 2188 -prefMapHandle 2184 -prefsLen 30705 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {08d87228-e85c-49c1-a7b4-caaa640c807f} 6684 "\\.\pipe\gecko-crash-server-pipe.6684" 2181c27f310 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5756 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
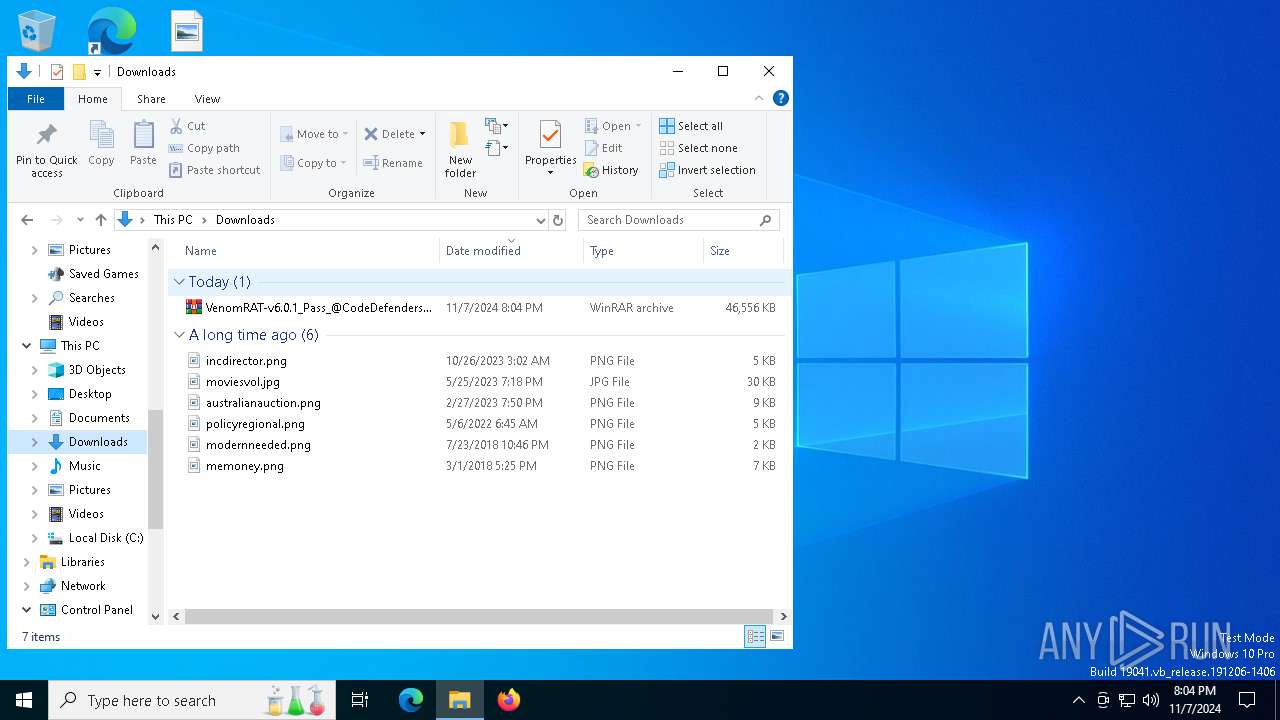
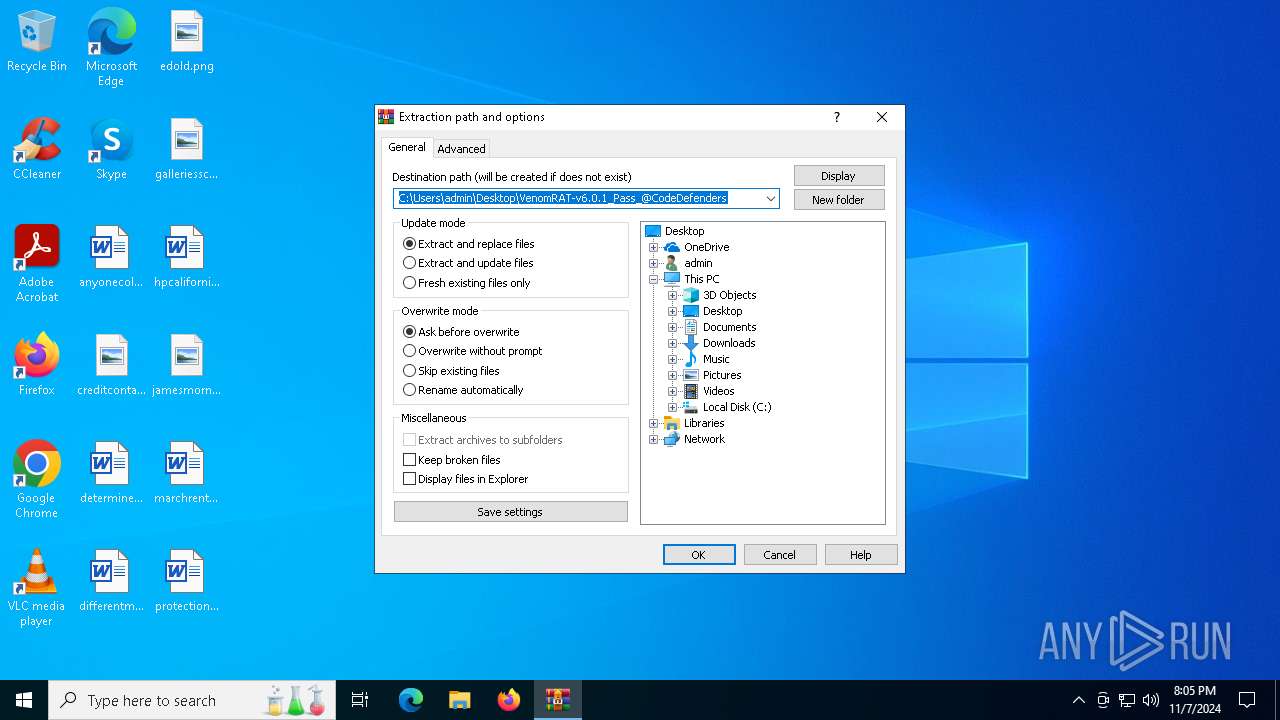
| 6192 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\VenomRAT-v6.0.1_Pass_@CodeDefenders.rar" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6684 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://gofile.io/d/U0Ok8C | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6708 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://gofile.io/d/U0Ok8C" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
17 201
Read events
17 180
Write events
8
Delete events
13
Modification events
| (PID) Process: | (6684) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (6192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
Executable files
63
Suspicious files
170
Text files
23
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:C09FF302D57C404B61E6A89B0B9F36E7 | SHA256:6A5B4F82595799346D0E501FE6CC8629E0FD6ED27B74D0E6CB5073DDB2E3C40B | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:F90C8D7DA668AF2EA545F60BC38BB10B | SHA256:00133EFC3AADA7ECCF82AE5D84B46DBF6C5D30AF0C50AF625D18444C936E6FBC | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6684 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
80
DNS requests
101
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7516 | SIHClient.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6684 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6684 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6684 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6684 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6684 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6684 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/yvU | unknown | — | — | whitelisted |
6684 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
6684 | firefox.exe | POST | 200 | 184.24.77.45:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1752 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 92.123.104.51:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
— | — | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
6684 | firefox.exe | 142.250.185.106:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
gofile.io |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6684 | firefox.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6684 | firefox.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2172 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |