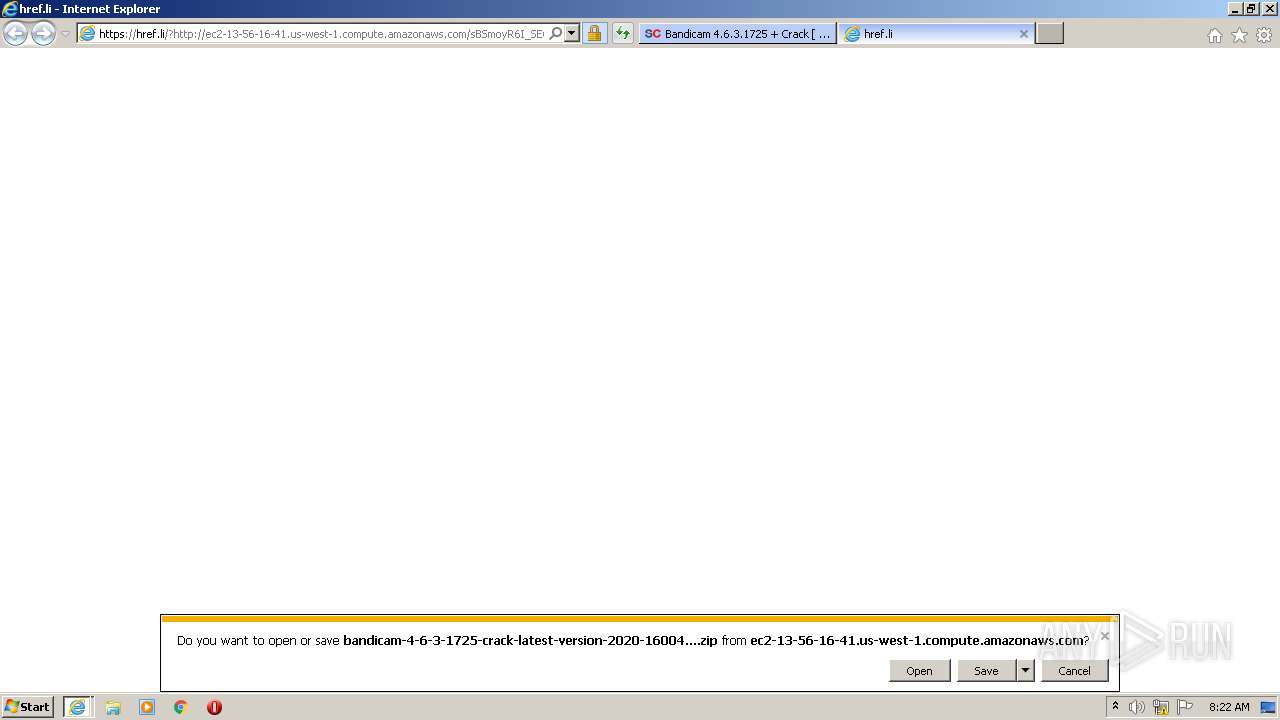
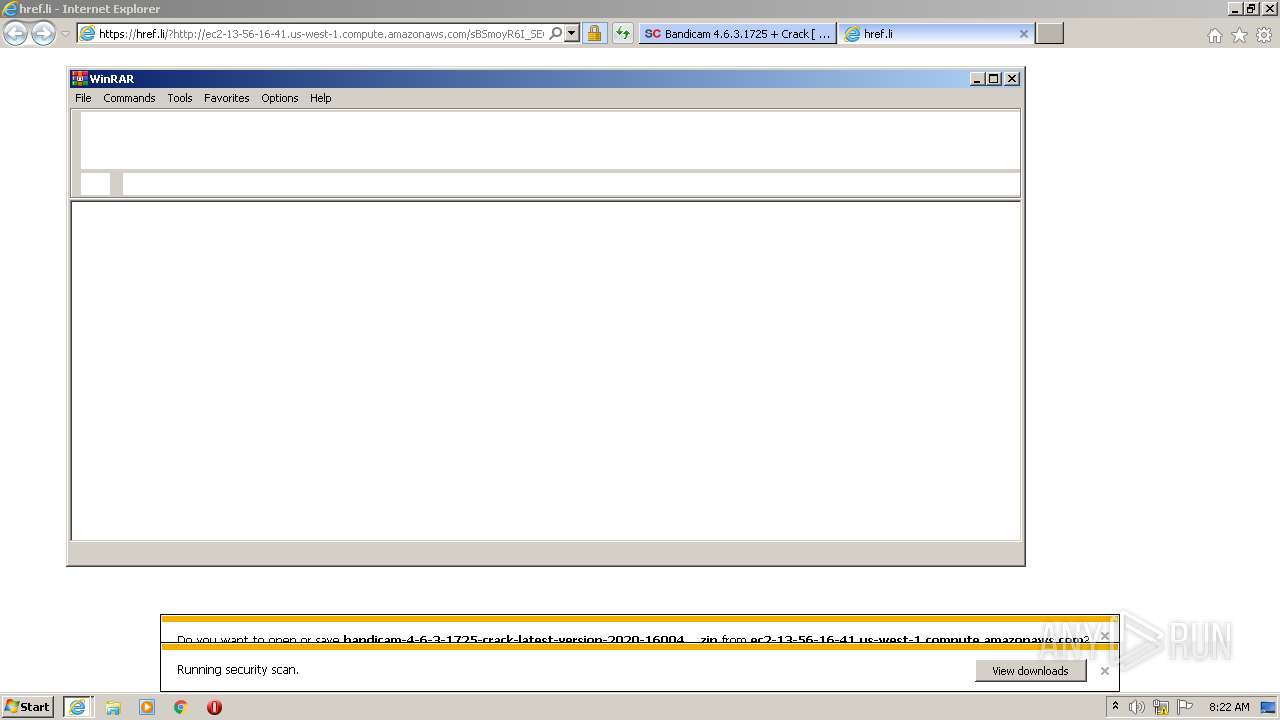
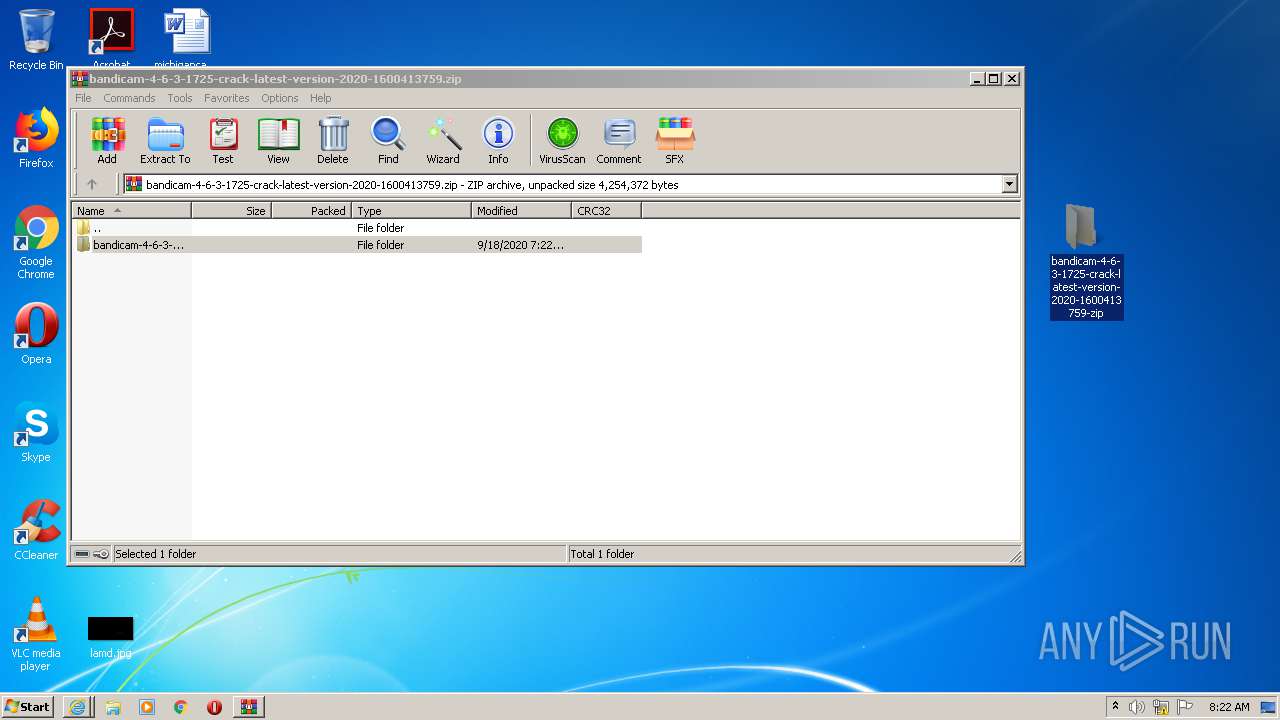
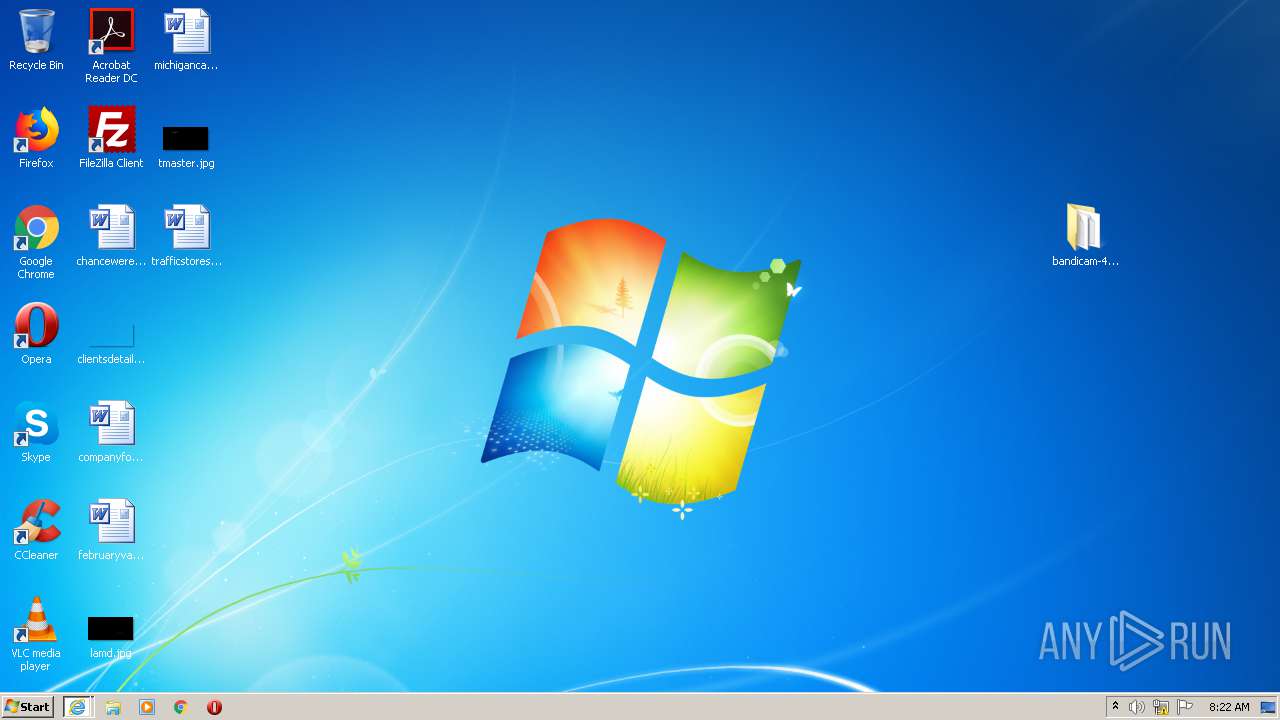
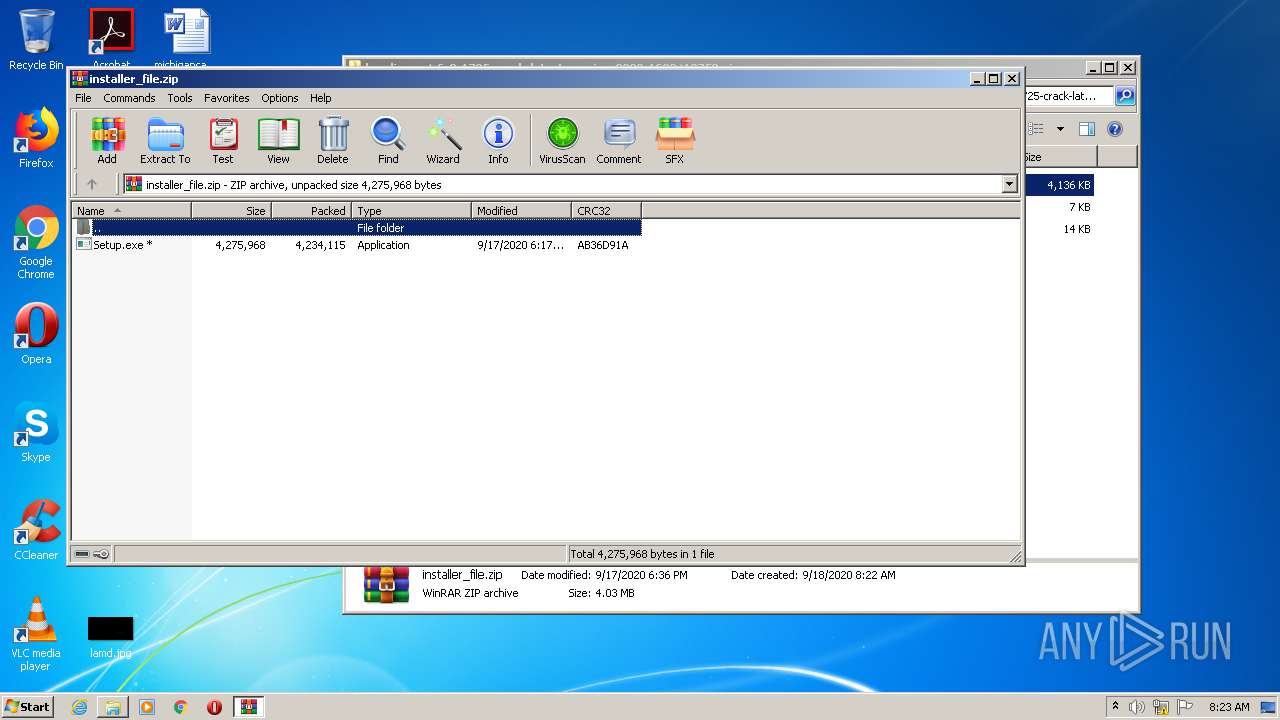
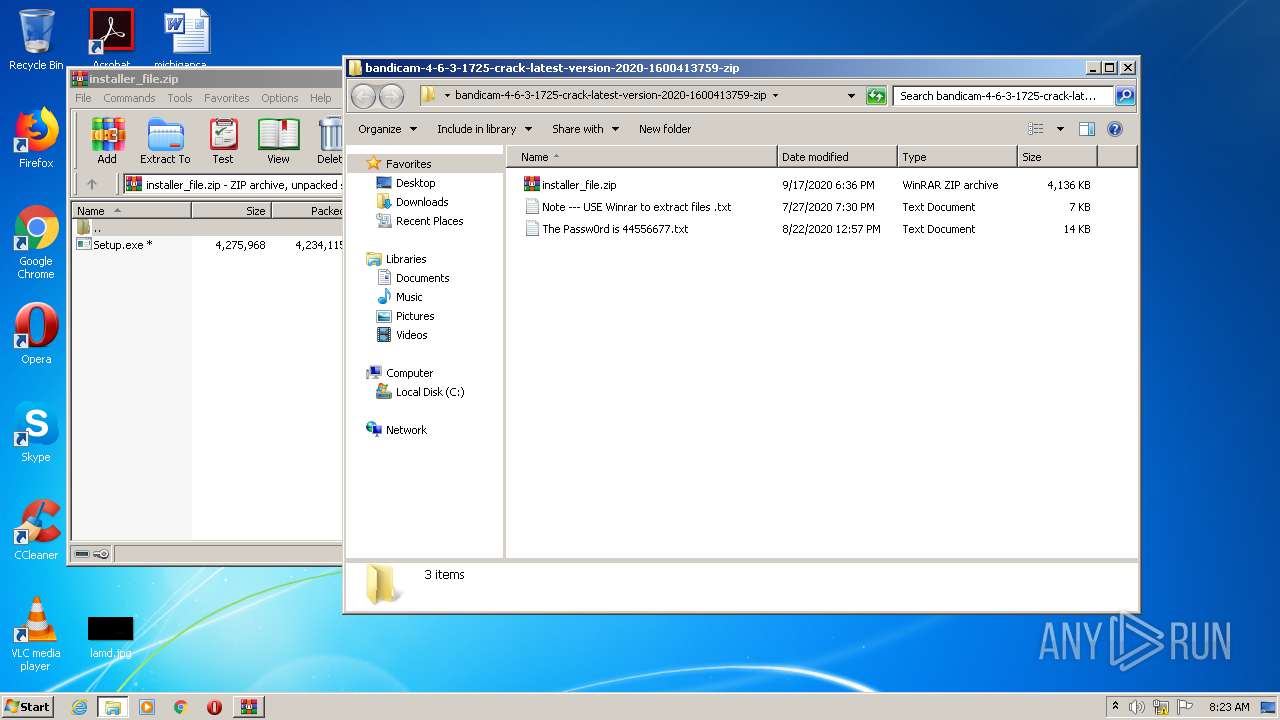
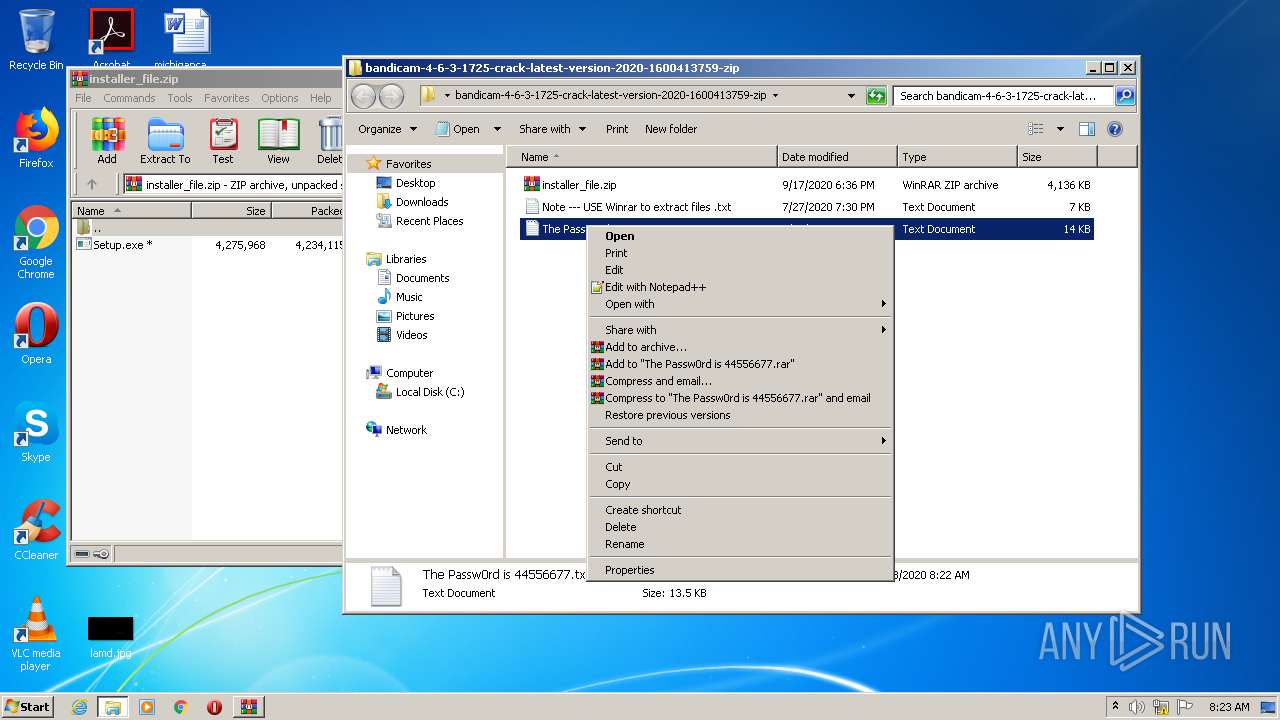
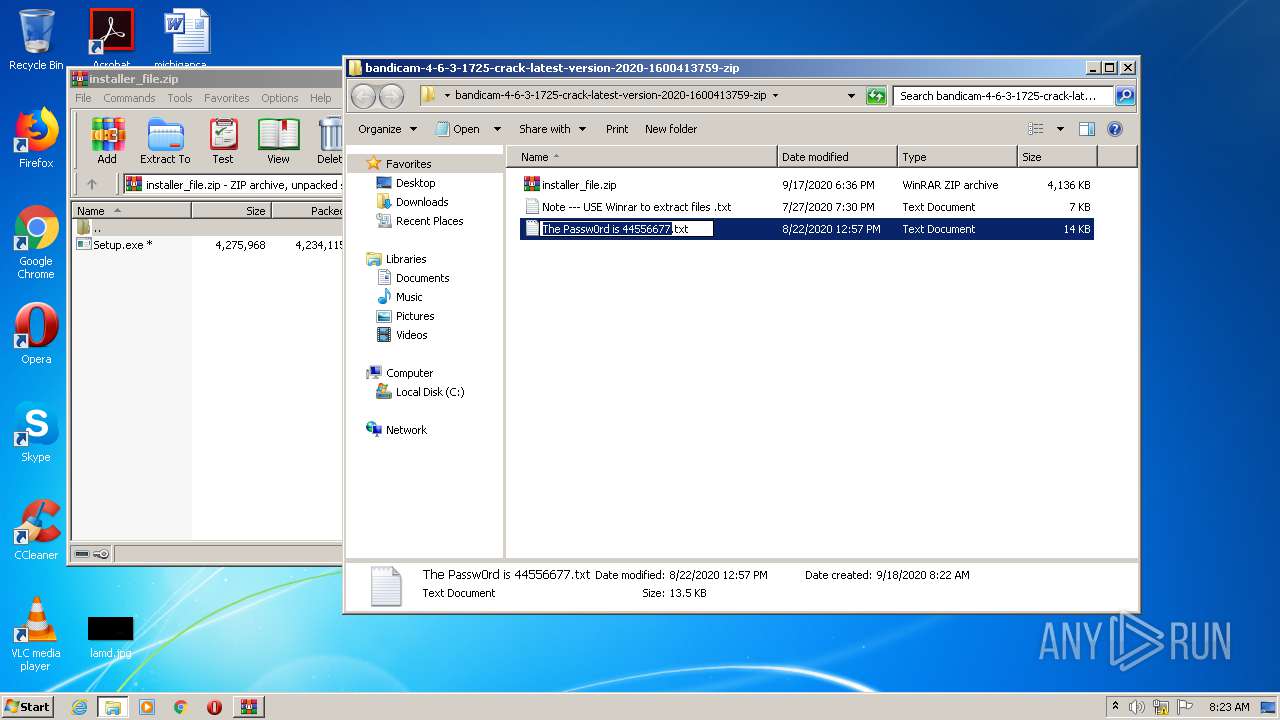
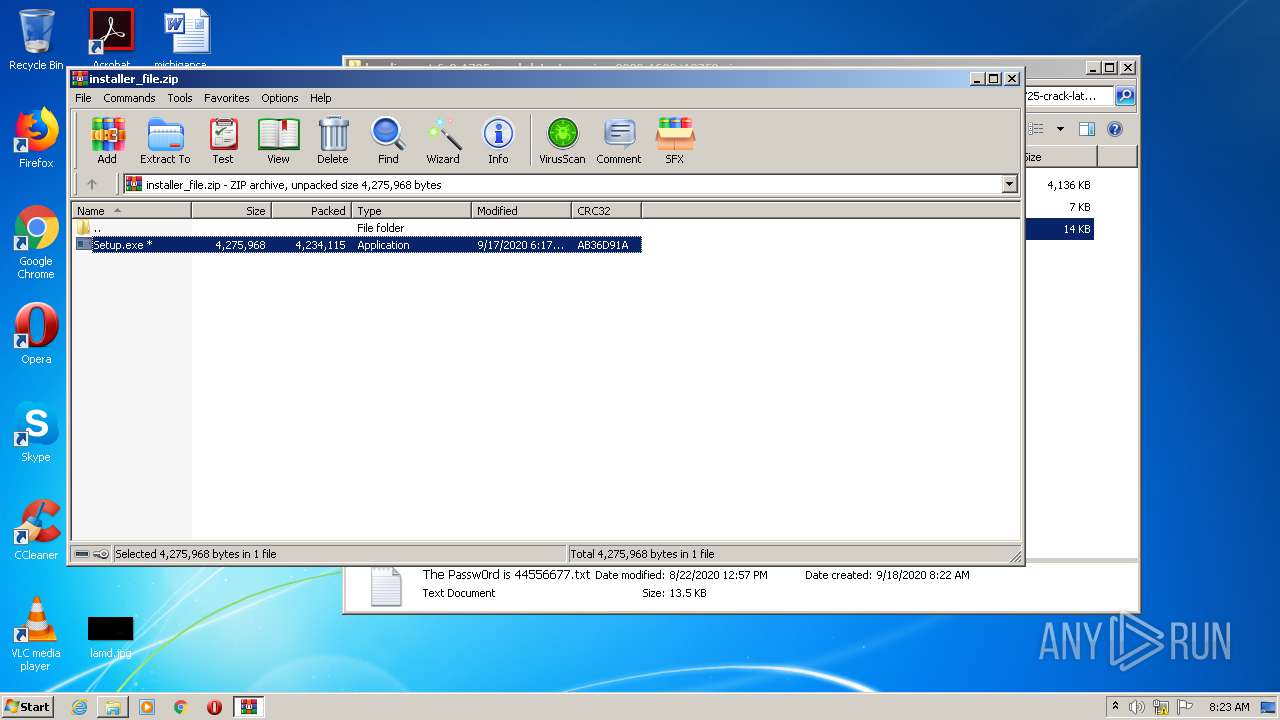
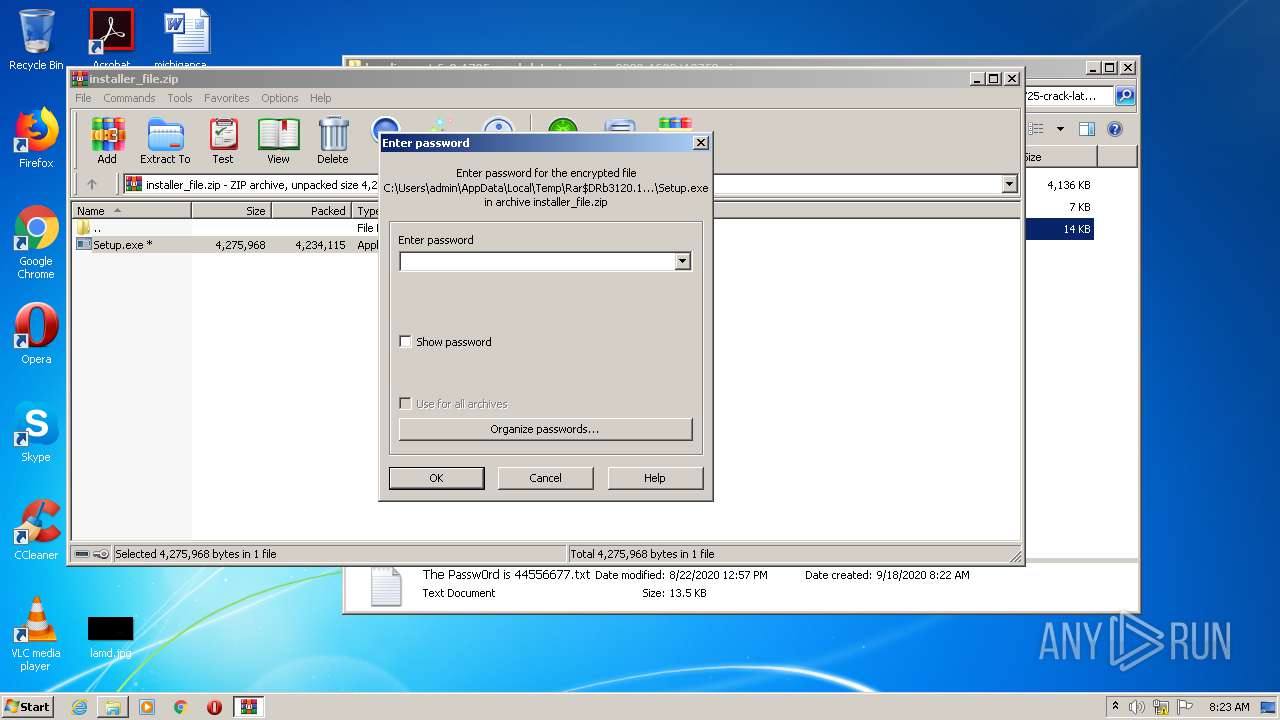
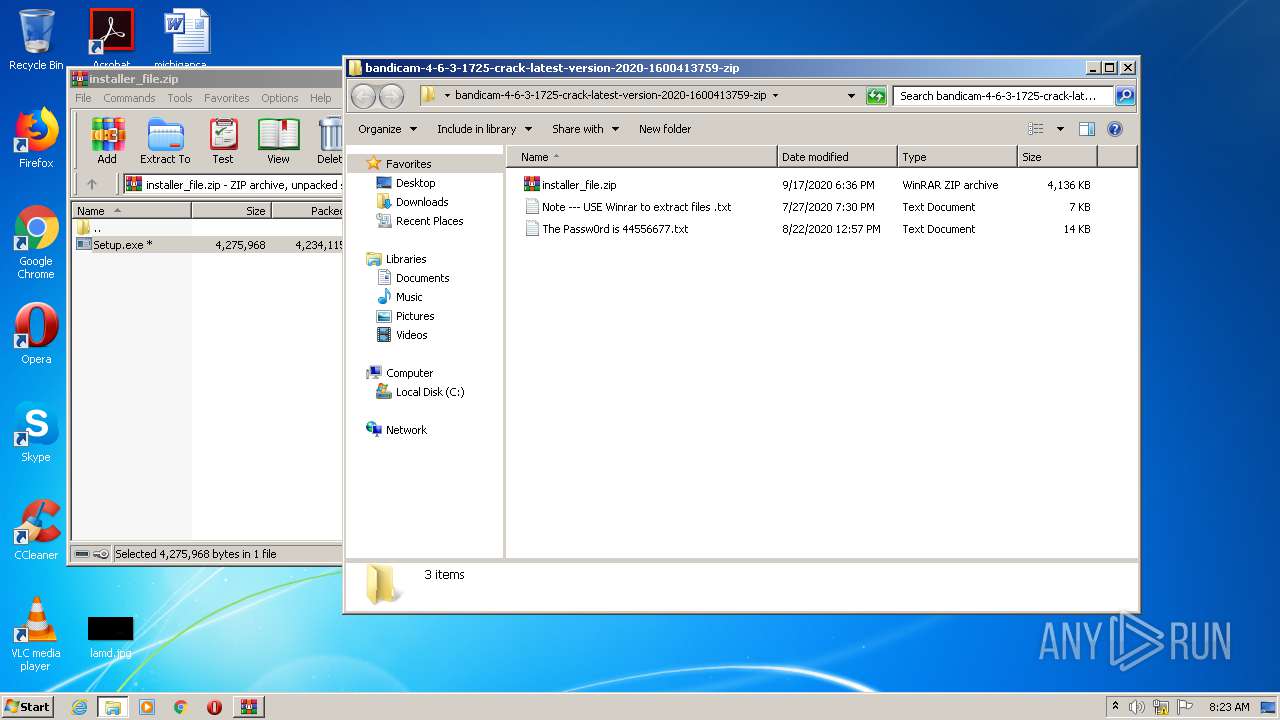
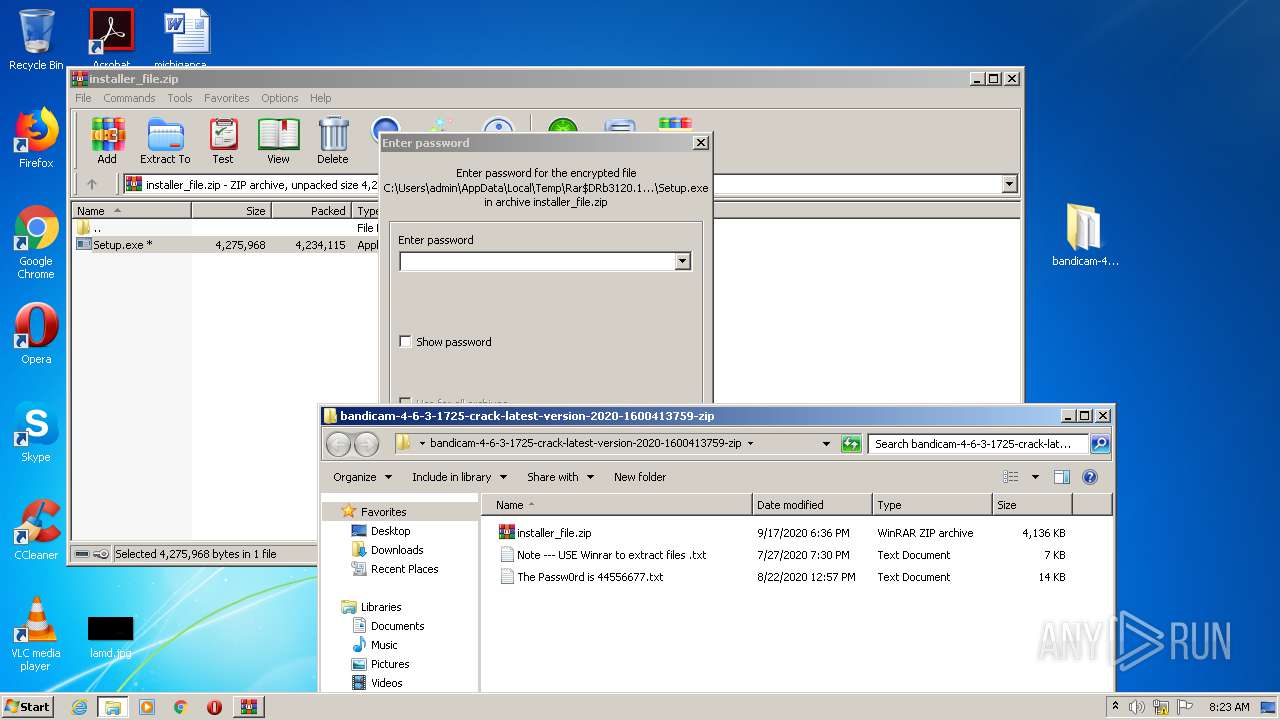
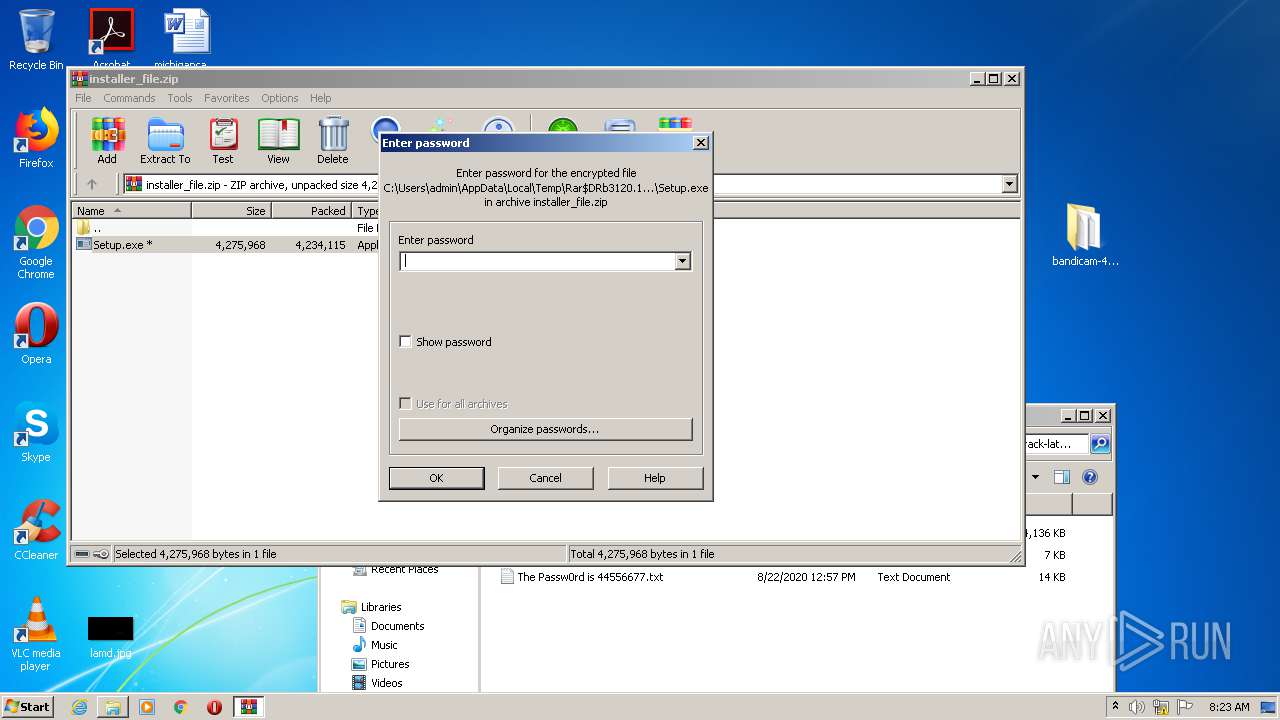
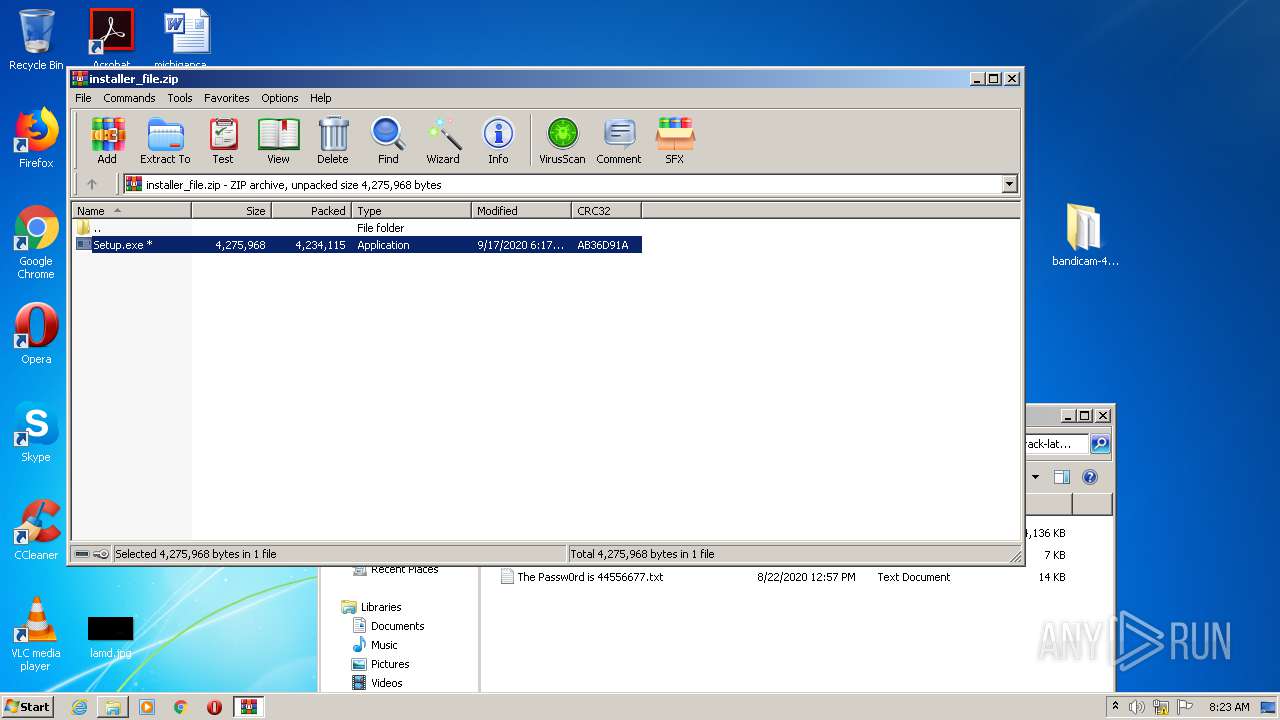
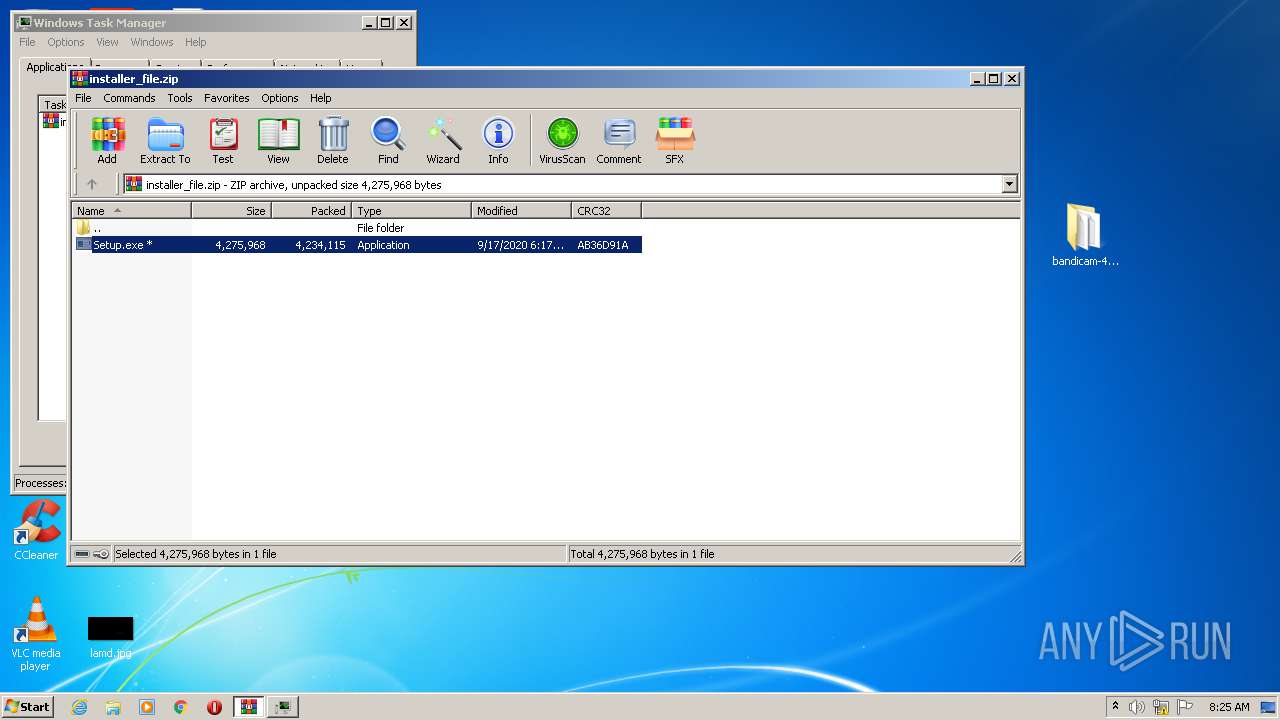
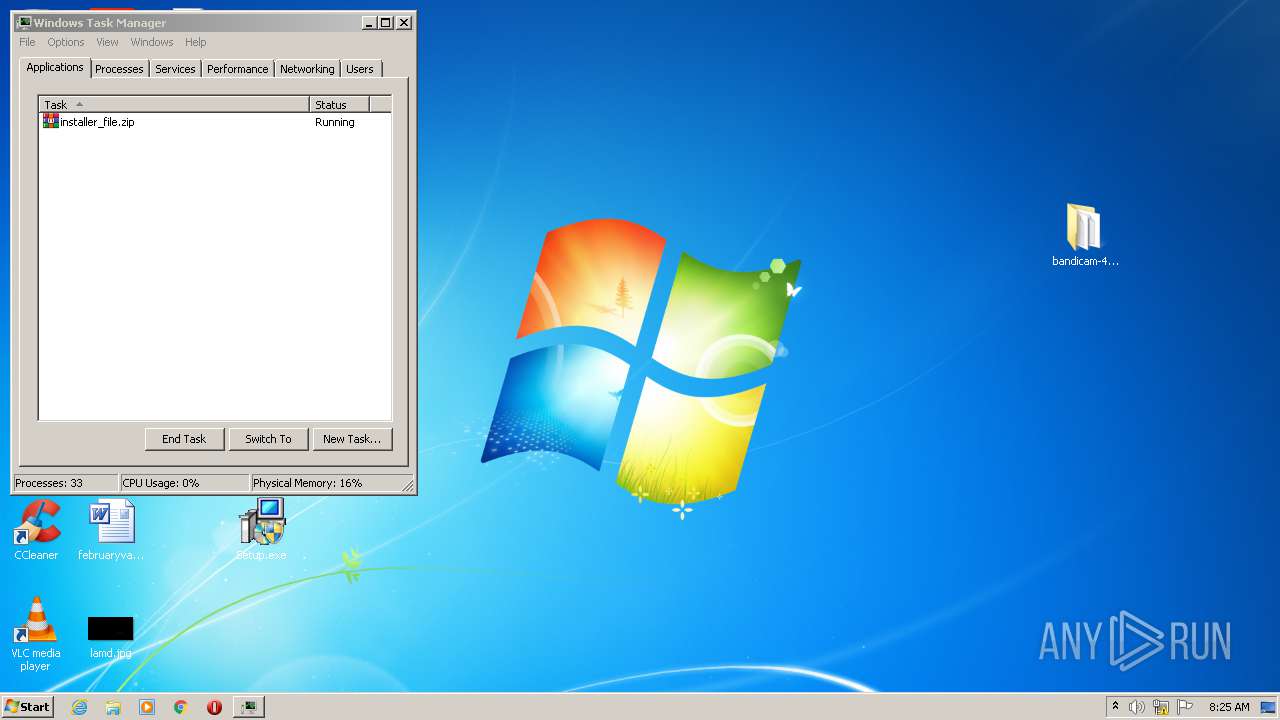
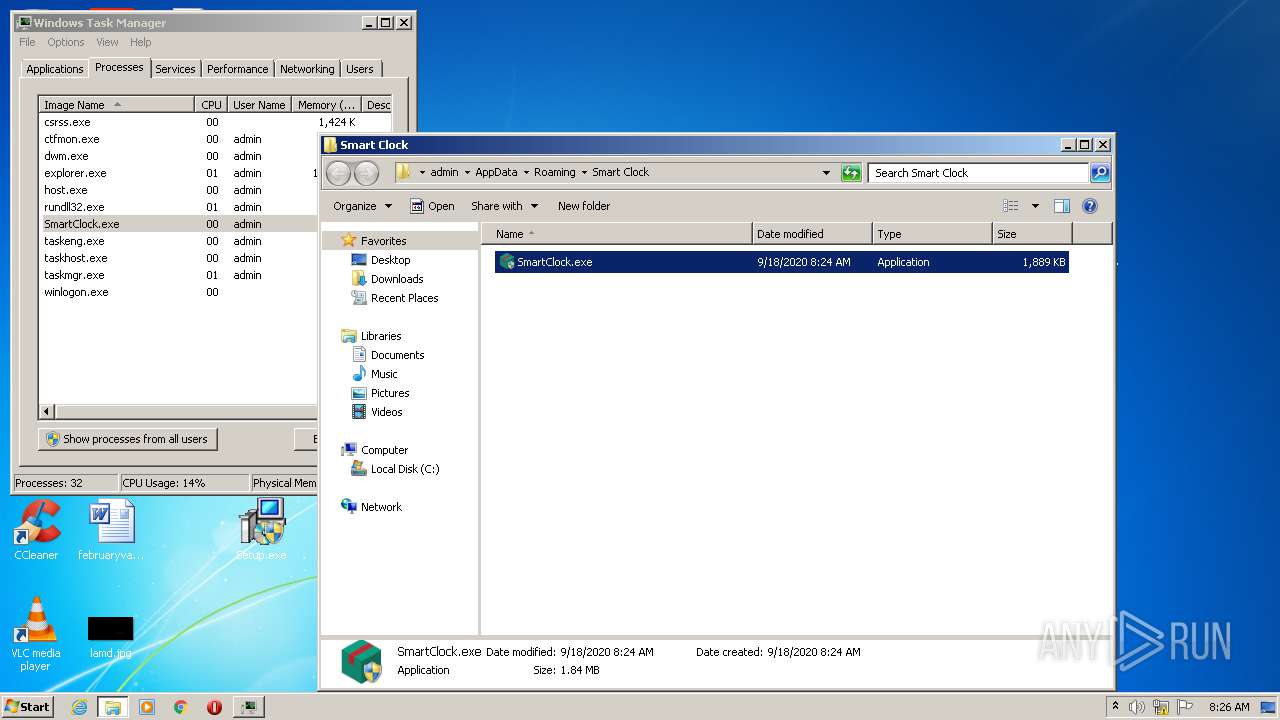
| URL: | https://startcrack.com/bandicam-crack/ |
| Full analysis: | https://app.any.run/tasks/c6538bef-7248-49b7-8f7d-959c2b3dd157 |
| Verdict: | Malicious activity |
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | September 18, 2020, 07:21:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5B029D22F6E377B5766E9598D74C7541 |
| SHA1: | D8FF3C5CD7DED7FEA102B7B4CD330C0A3F12C59A |
| SHA256: | E46CDEA86BEFF43AF2345659A8C9DE57E2215064CE8E834588672253A826B676 |
| SSDEEP: | 3:N8c8LGTBBkM9:2caKBBkw |
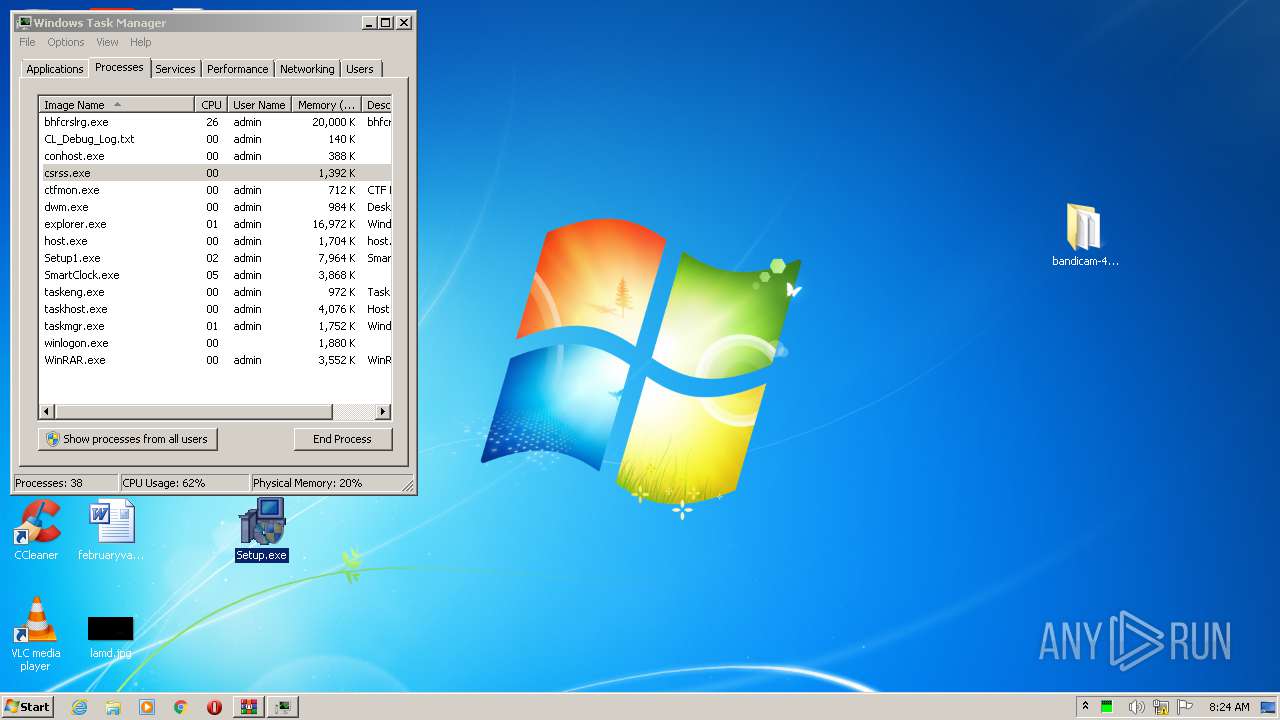
MALICIOUS
Application was dropped or rewritten from another process
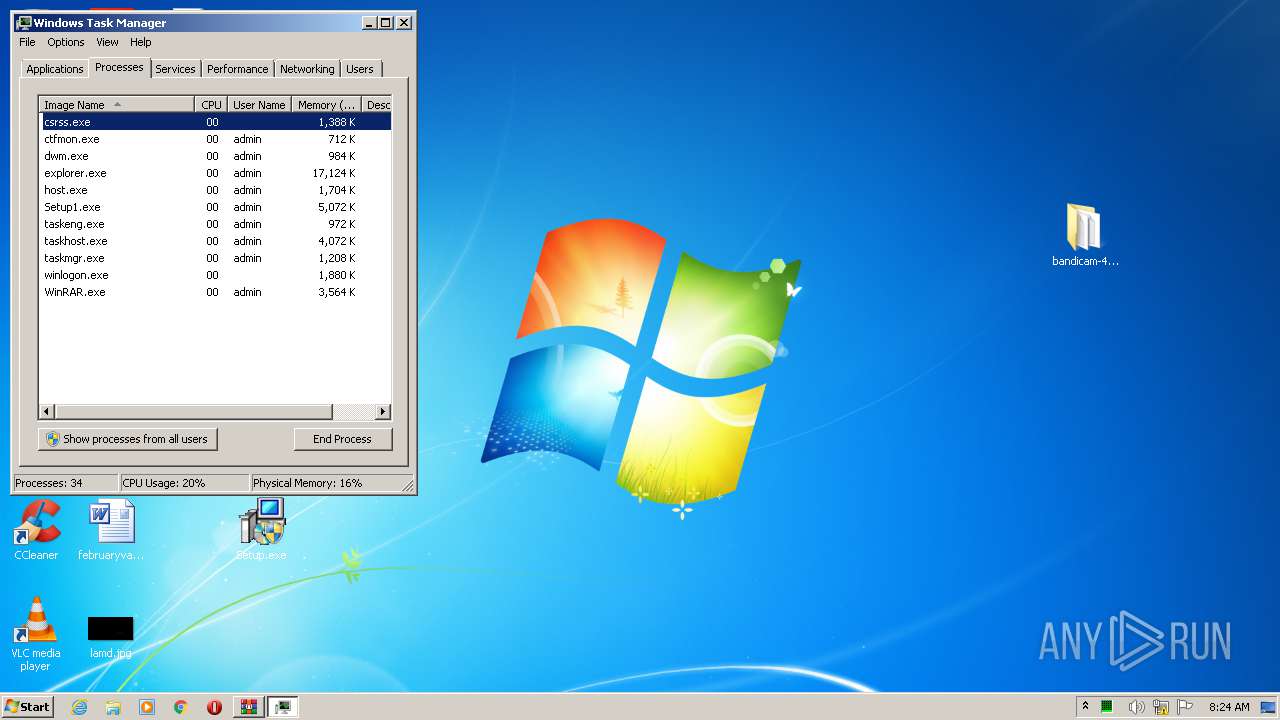
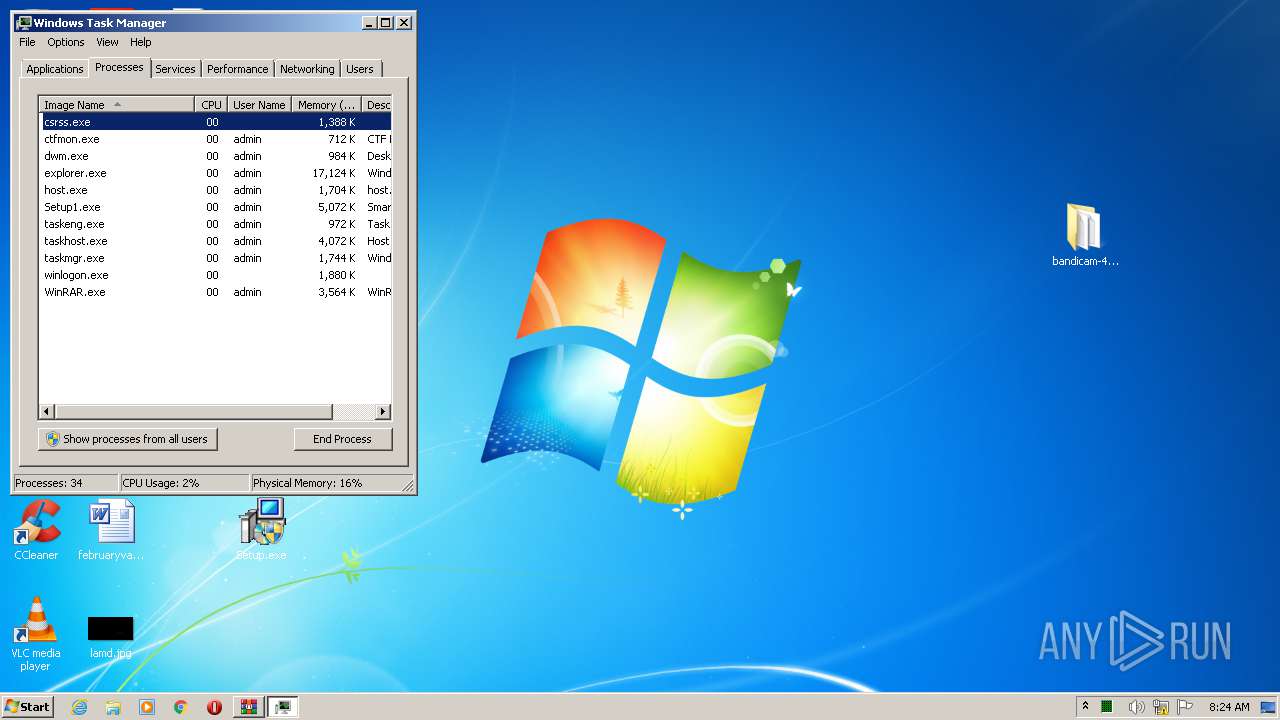
- Setup.exe (PID: 4052)
- Setup.exe (PID: 3096)
- ns9DB6.tmp (PID: 3460)
- Setup1.exe (PID: 1972)
- 1.exe (PID: 3376)
- bhfcrslrg.exe (PID: 3432)
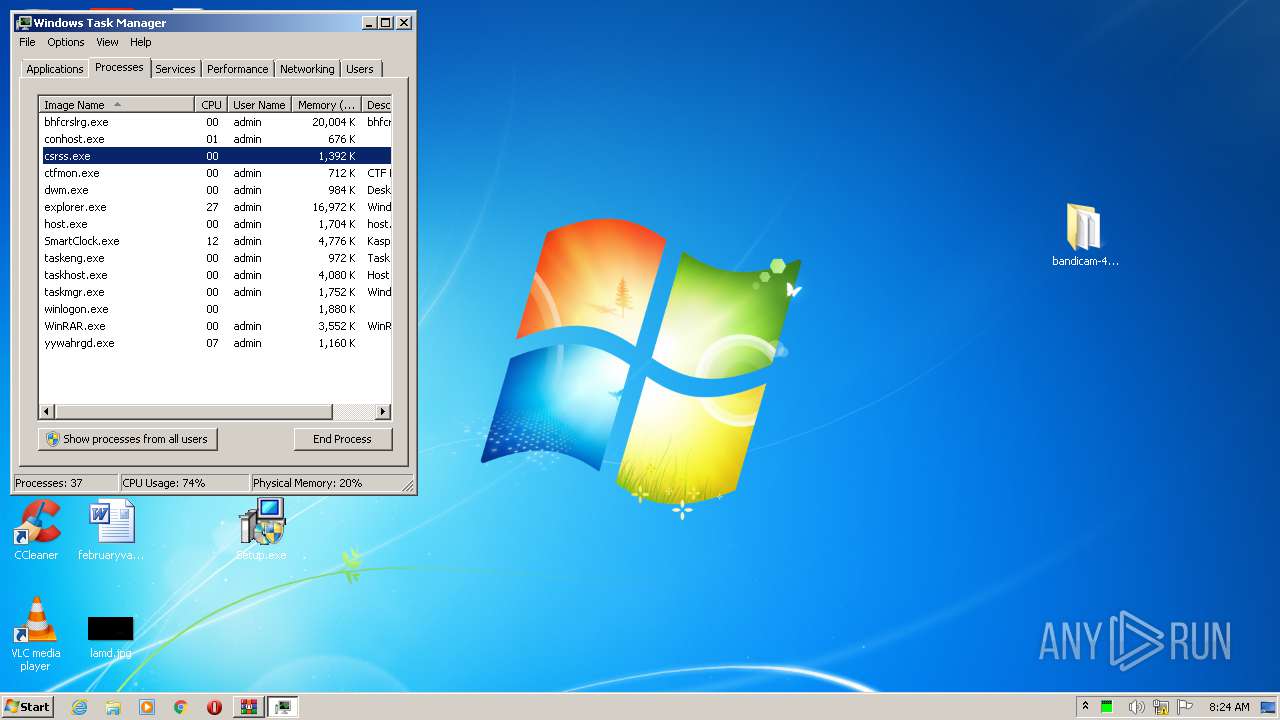
- yywahrgd.exe (PID: 2184)
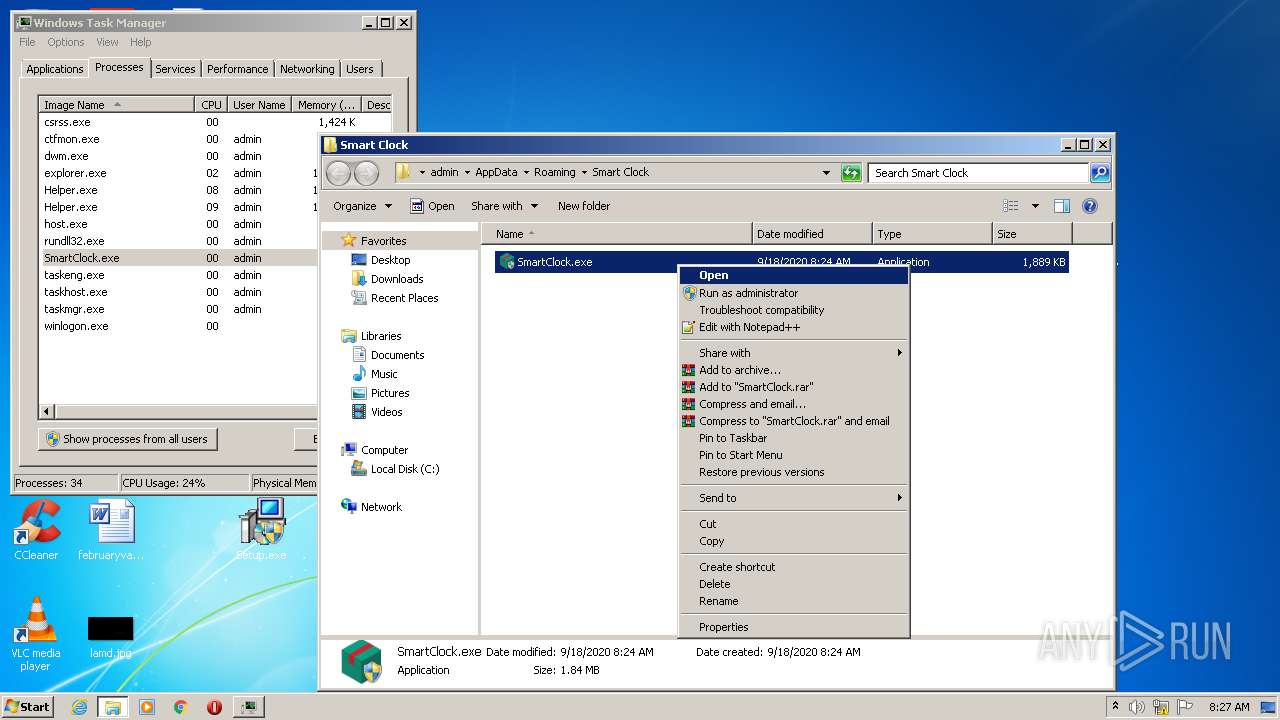
- Helper.exe (PID: 4008)
- tuyijamvvex.exe (PID: 2336)
- Helper.exe (PID: 1448)
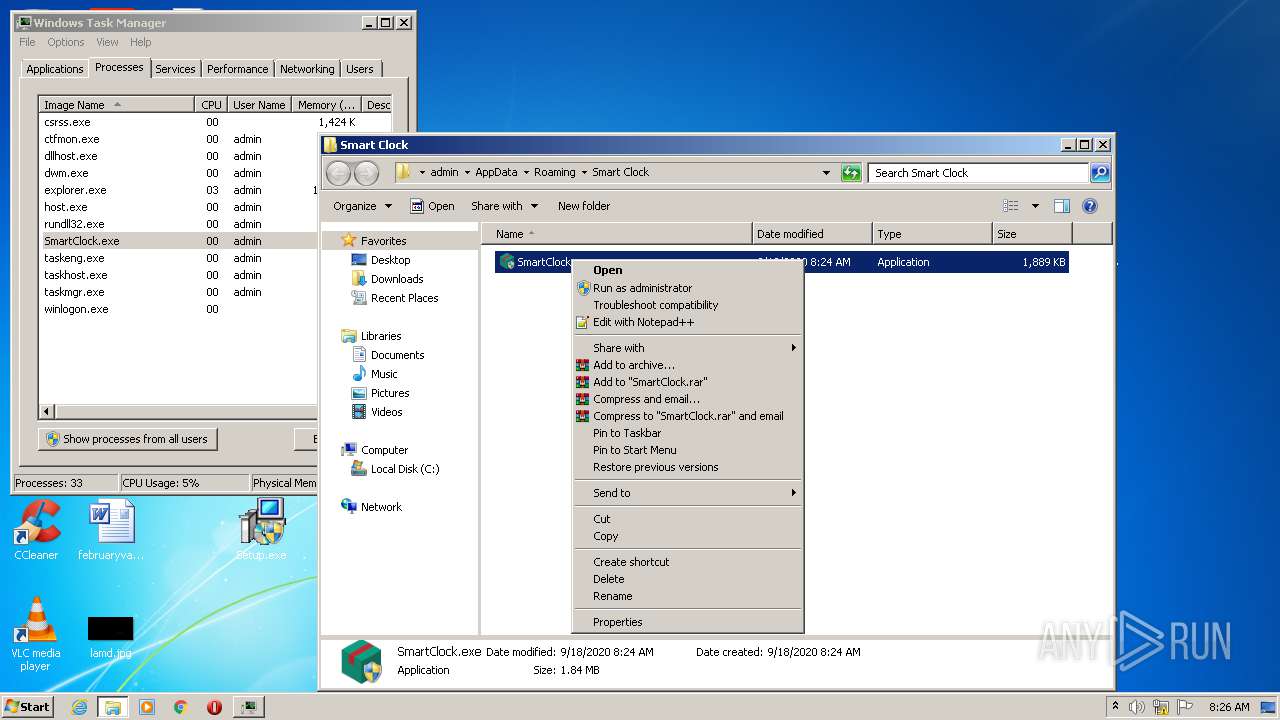
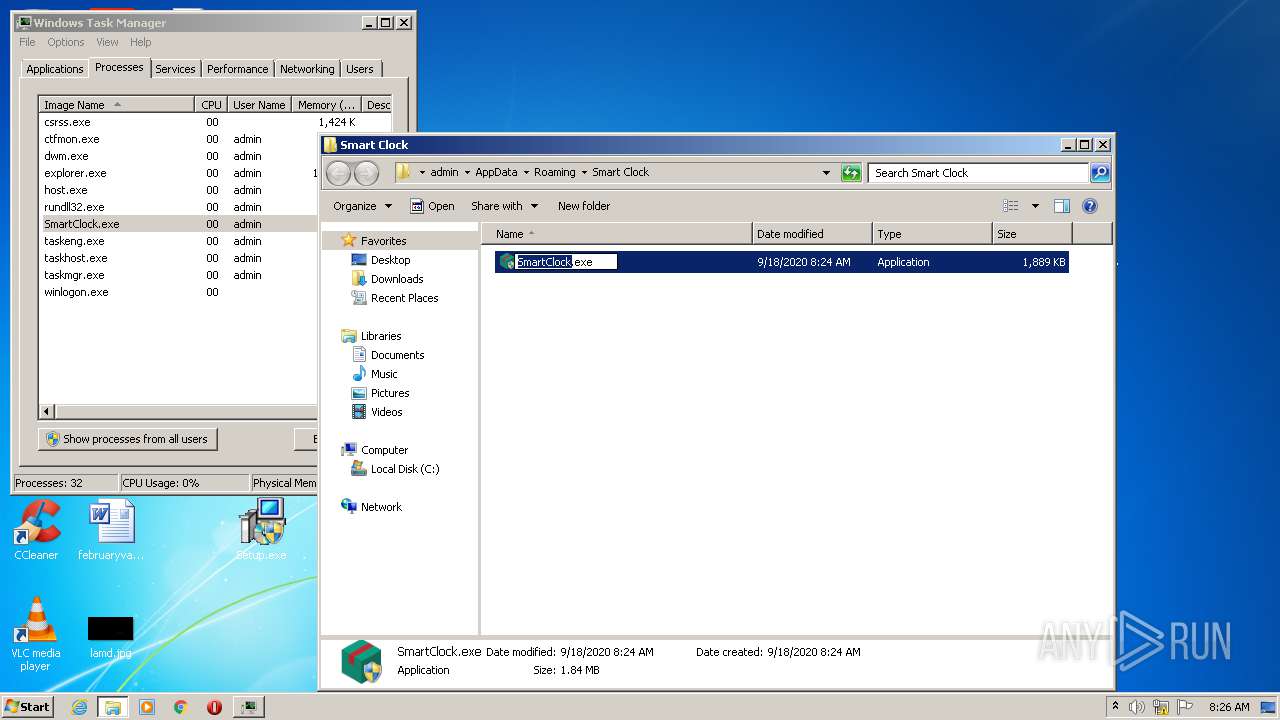
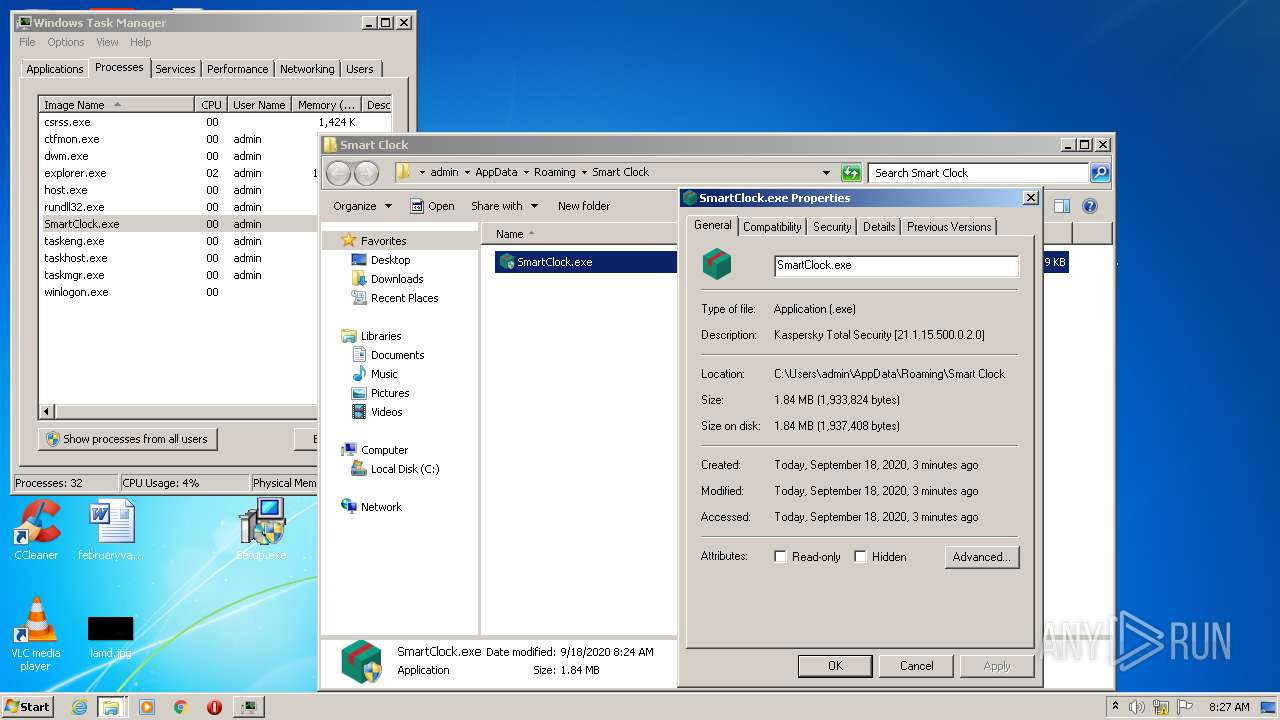
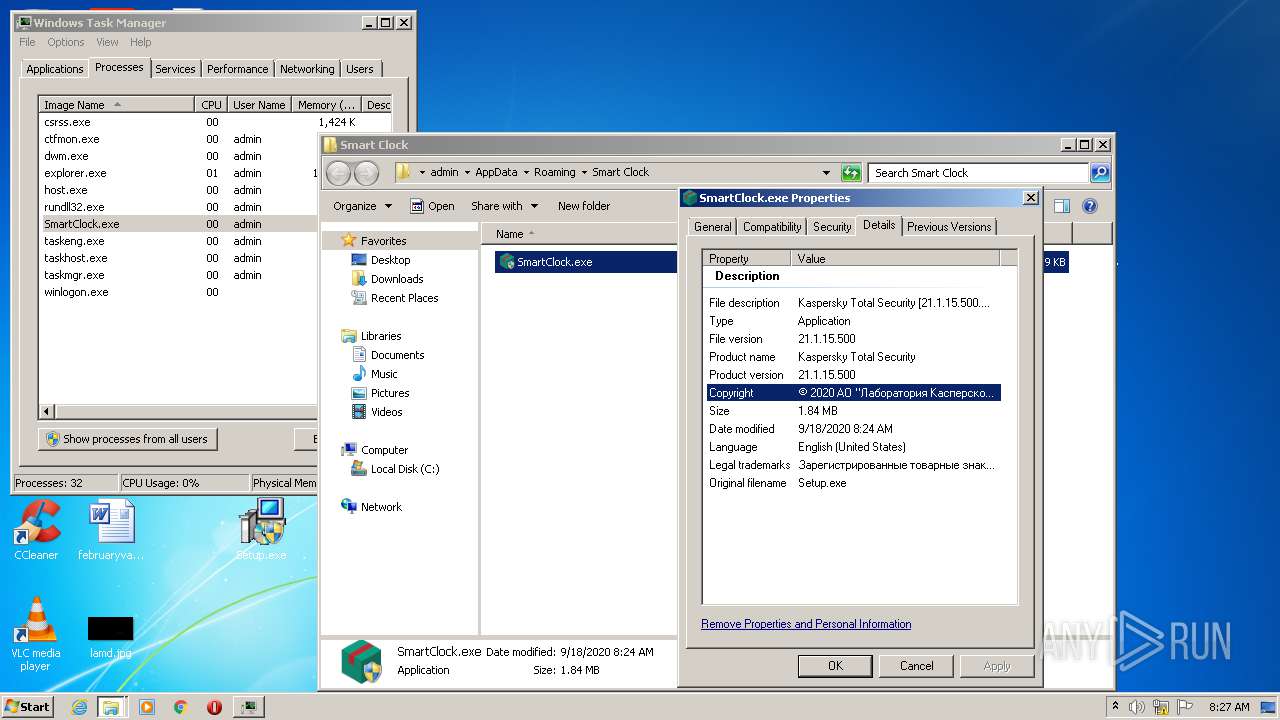
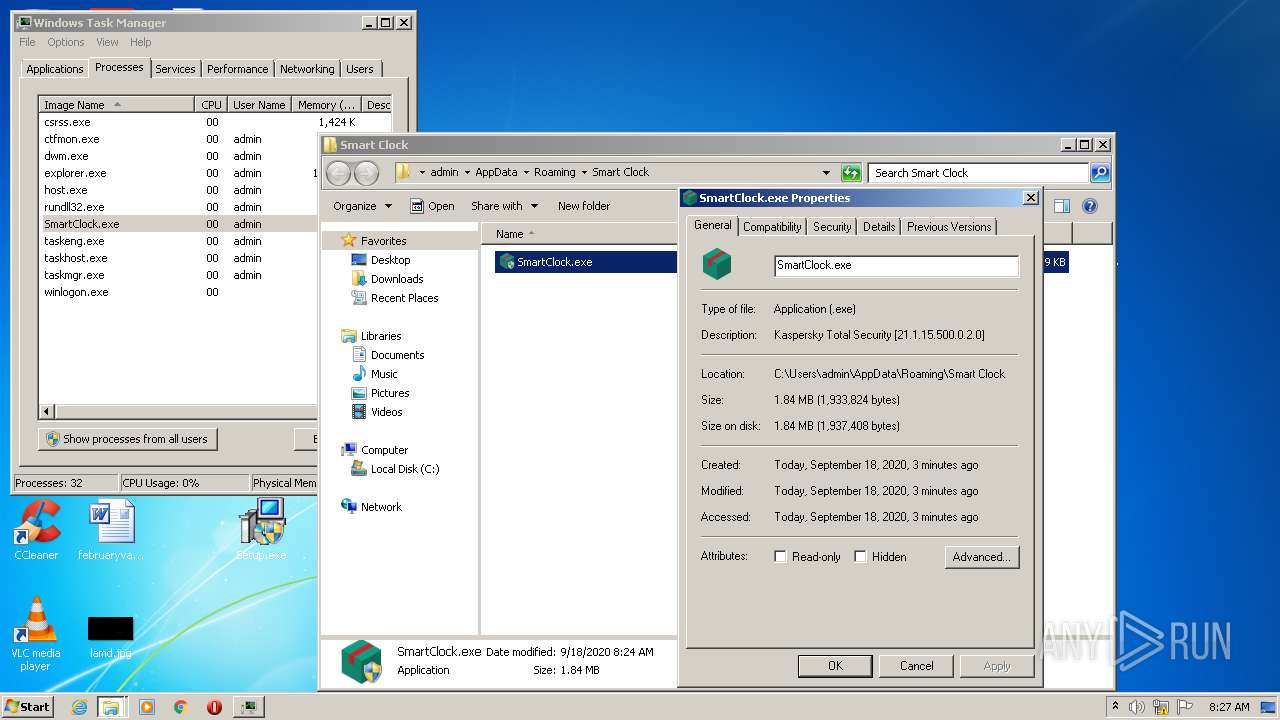
- SmartClock.exe (PID: 2796)
- CL_Debug_Log.txt (PID: 2424)
- Helper.exe (PID: 4032)
- Helper.exe (PID: 1948)
- Helper.exe (PID: 3780)
- Helper.exe (PID: 2572)
Loads dropped or rewritten executable
- Setup.exe (PID: 3096)
- rundll32.exe (PID: 2076)
- regsvr32.exe (PID: 1848)
Changes settings of System certificates
- CScript.exe (PID: 2884)
Actions looks like stealing of personal data
- 1.exe (PID: 3376)
Stealing of credential data
- 1.exe (PID: 3376)
Loads the Task Scheduler COM API
- tuyijamvvex.exe (PID: 2336)
- schtasks.exe (PID: 3896)
Writes to a start menu file
- tuyijamvvex.exe (PID: 2336)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2532)
Downloads executable files from the Internet
- Setup1.exe (PID: 1972)
Downloads executable files from IP
- Setup1.exe (PID: 1972)
Registers / Runs the DLL via REGSVR32.EXE
- yywahrgd.exe (PID: 2184)
Connects to CnC server
- rundll32.exe (PID: 2076)
DANABOT was detected
- rundll32.exe (PID: 2076)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3120)
- Setup.exe (PID: 3096)
- tuyijamvvex.exe (PID: 2336)
- bhfcrslrg.exe (PID: 3432)
- Setup1.exe (PID: 1972)
- CL_Debug_Log.txt (PID: 2424)
- yywahrgd.exe (PID: 2184)
Creates files in the program directory
- Setup.exe (PID: 3096)
Executes scripts
- ns9DB6.tmp (PID: 3460)
Adds / modifies Windows certificates
- CScript.exe (PID: 2884)
Starts application with an unusual extension
- Setup.exe (PID: 3096)
- bhfcrslrg.exe (PID: 3432)
Reads Internet Cache Settings
- CScript.exe (PID: 2884)
- 1.exe (PID: 3376)
- Setup1.exe (PID: 1972)
Reads the cookies of Google Chrome
- 1.exe (PID: 3376)
Reads the cookies of Mozilla Firefox
- 1.exe (PID: 3376)
Starts CMD.EXE for commands execution
- 1.exe (PID: 3376)
- Setup1.exe (PID: 1972)
- bhfcrslrg.exe (PID: 3432)
Starts CMD.EXE for self-deleting
- 1.exe (PID: 3376)
Checks for external IP
- Setup1.exe (PID: 1972)
Creates files in the user directory
- tuyijamvvex.exe (PID: 2336)
- Setup1.exe (PID: 1972)
- bhfcrslrg.exe (PID: 3432)
Starts itself from another location
- tuyijamvvex.exe (PID: 2336)
Searches for installed software
- 1.exe (PID: 3376)
Executed via Task Scheduler
- Helper.exe (PID: 4008)
- Helper.exe (PID: 1448)
- Helper.exe (PID: 4032)
- Helper.exe (PID: 1948)
- Helper.exe (PID: 2572)
- Helper.exe (PID: 3780)
Uses RUNDLL32.EXE to load library
- regsvr32.exe (PID: 1848)
INFO
Application launched itself
- iexplore.exe (PID: 2632)
Reads Internet Cache Settings
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 2632)
- iexplore.exe (PID: 2736)
Reads settings of System Certificates
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 2632)
- iexplore.exe (PID: 2736)
Changes internet zones settings
- iexplore.exe (PID: 2632)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2632)
Creates files in the user directory
- iexplore.exe (PID: 2632)
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 2736)
Reads internet explorer settings
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 2736)
Changes settings of System certificates
- iexplore.exe (PID: 2632)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2632)
Manual execution by user
- WinRAR.exe (PID: 3120)
- Setup.exe (PID: 4052)
- Setup.exe (PID: 3096)
- taskmgr.exe (PID: 3988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
83
Monitored processes
32
Malicious processes
8
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | "C:\Windows\system32\cmd.exe" /c start "" "C:\Users\admin\AppData\Local\Temp\tuyijamvvex.exe" | C:\Windows\system32\cmd.exe | — | Setup1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1448 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1848 | C:\Windows\system32\regsvr32.exe -s C:\Users\admin\AppData\Local\Temp\yywahrgd.dll f1 C:\Users\admin\AppData\Local\Temp\yywahrgd.exe@2184 | C:\Windows\system32\regsvr32.exe | — | yywahrgd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1868 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2632 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1948 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Mader\lase\Setup1.exe" | C:\Program Files\Mader\lase\Setup1.exe | Setup.exe | ||||||||||||
User: admin Company: simplix Integrity Level: HIGH Description: Smart troubleshooting Exit code: 0 Version: 2.3.4.0 Modules
| |||||||||||||||
| 2076 | C:\Windows\system32\\rundll32.exe C:\Users\admin\AppData\Local\Temp\yywahrgd.dll,f0 | C:\Windows\system32\rundll32.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
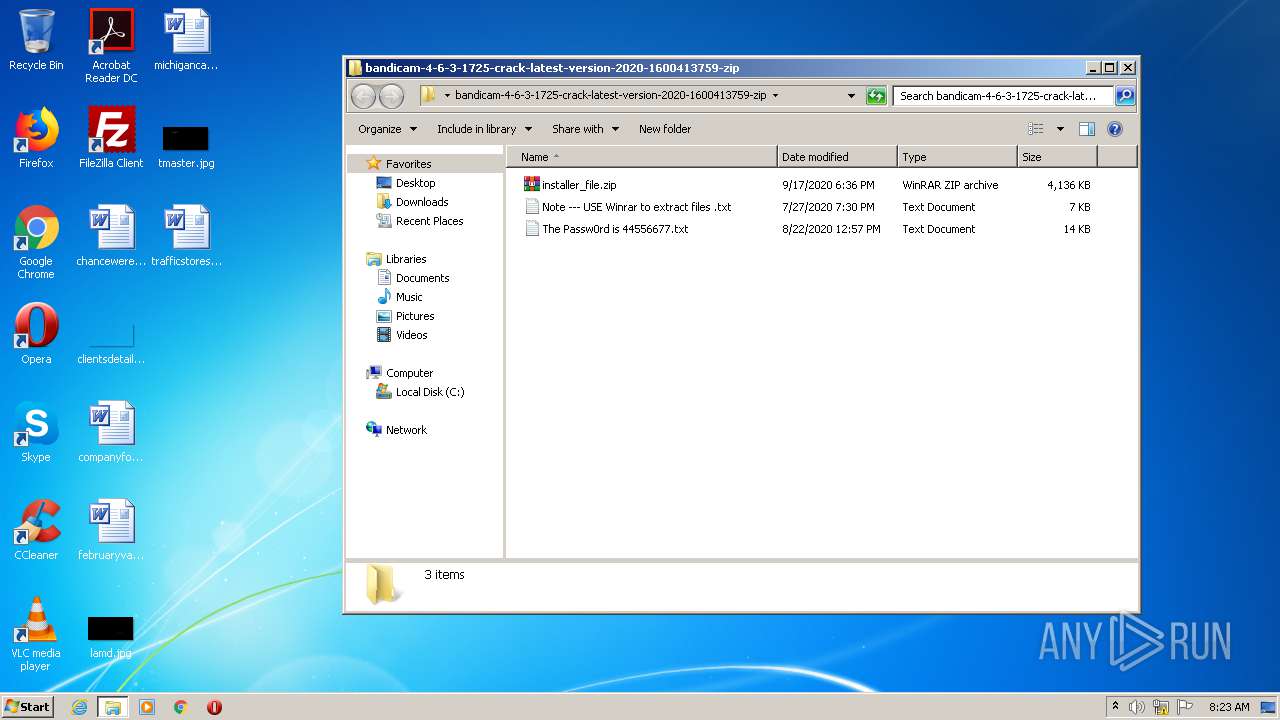
| 2144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\bandicam-4-6-3-1725-crack-latest-version-2020-1600413759.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\AppData\Local\Temp\yywahrgd.exe" | C:\Users\admin\AppData\Local\Temp\yywahrgd.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2336 | "C:\Users\admin\AppData\Local\Temp\tuyijamvvex.exe" | C:\Users\admin\AppData\Local\Temp\tuyijamvvex.exe | cmd.exe | ||||||||||||
User: admin Company: Лаборатория Касперского Integrity Level: HIGH Description: Kaspersky Total Security [21.1.15.500.0.2.0] Exit code: 0 Version: 21.1.15.500 Modules
| |||||||||||||||
Total events
3 760
Read events
3 544
Write events
210
Delete events
6
Modification events
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2142663824 | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30838156 | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2632) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
18
Suspicious files
83
Text files
353
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabE68E.tmp | — | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarE68F.tmp | — | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\W1AMYTC7.txt | text | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_637E13846EBA0E514706B3E4EFEC0CA1 | der | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9FF67FB3141440EED32363089565AE60_637E13846EBA0E514706B3E4EFEC0CA1 | binary | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\style[1].css | text | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bandicam-crack[1].htm | html | |
MD5:— | SHA256:— | |||
| 1868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\button_download[1].png | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
90
DNS requests
40
Threats
62
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1868 | iexplore.exe | GET | 304 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | — | — | whitelisted |
1868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAaJQ9pyIyeUDQGGyCnUt%2BI%3D | US | der | 279 b | whitelisted |
1868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAaJQ9pyIyeUDQGGyCnUt%2BI%3D | US | der | 279 b | whitelisted |
1868 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
1868 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1868 | iexplore.exe | GET | 304 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1868 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1868 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAQSqG2Vcy5VgVdz4Q5GOwg%3D | US | der | 279 b | whitelisted |
1868 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1868 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1868 | iexplore.exe | 172.67.155.69:443 | startcrack.com | — | US | suspicious |
1868 | iexplore.exe | 142.250.74.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1868 | iexplore.exe | 151.101.2.109:443 | cdn.jsdelivr.net | Fastly | US | suspicious |
1868 | iexplore.exe | 192.0.73.2:443 | secure.gravatar.com | Automattic, Inc | US | whitelisted |
1868 | iexplore.exe | 172.217.21.206:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
1868 | iexplore.exe | 104.18.226.52:443 | cdn.onesignal.com | Cloudflare Inc | US | malicious |
1868 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
1868 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
1868 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
startcrack.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
secure.gravatar.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
cdn.onesignal.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .cf Domain |
2736 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.cf) in TLS SNI |
2884 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2884 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3376 | 1.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3376 | 1.exe | A Network Trojan was detected | ET TROJAN Suspicious Zipped Filename in Outbound POST Request (Passwords.txt) |
1972 | Setup1.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
1972 | Setup1.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
1972 | Setup1.exe | A Network Trojan was detected | ET TROJAN Possible Malicious Macro DL EXE Feb 2016 |
23 ETPRO signatures available at the full report
Process | Message |
|---|---|
1.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
Setup1.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
bhfcrslrg.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
tuyijamvvex.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
SmartClock.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|