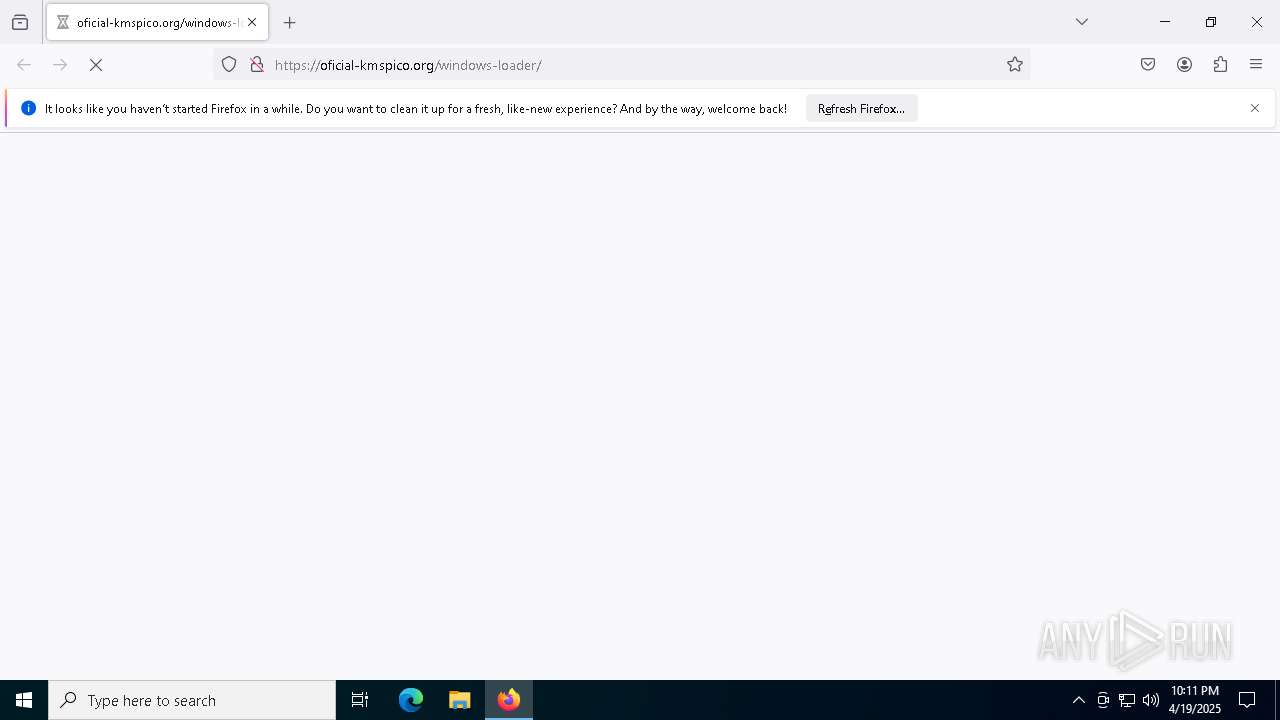
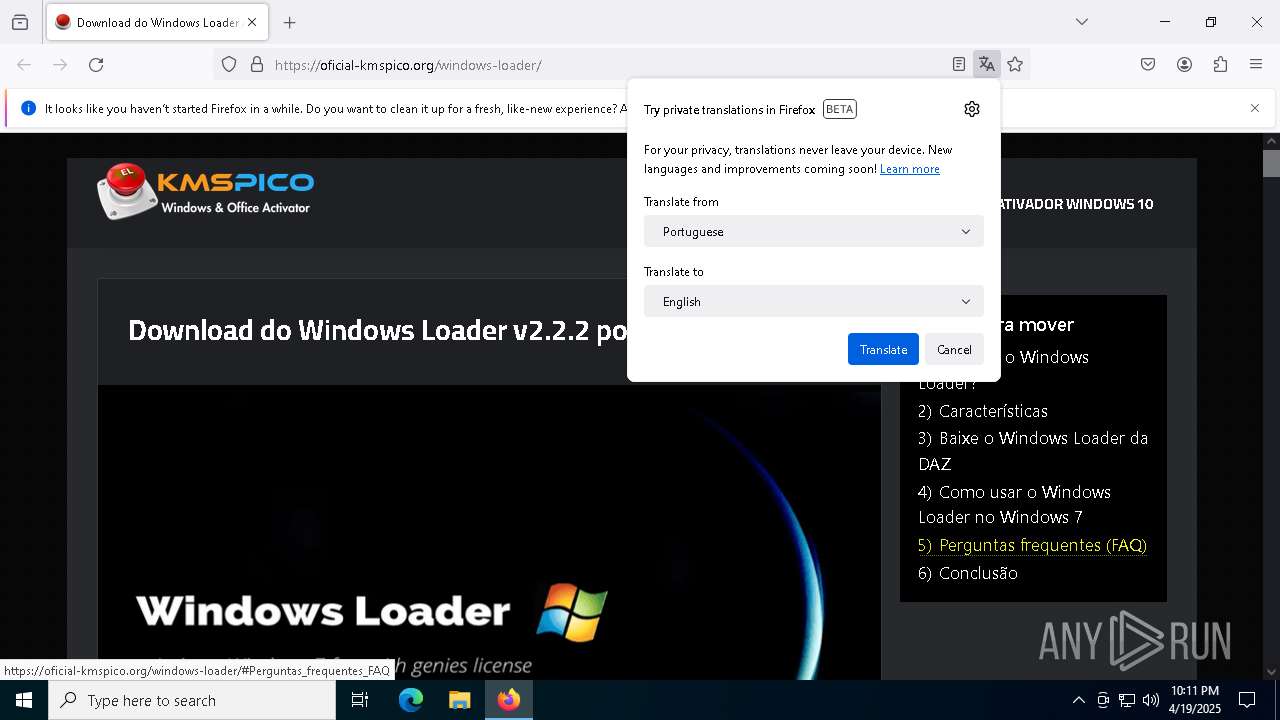
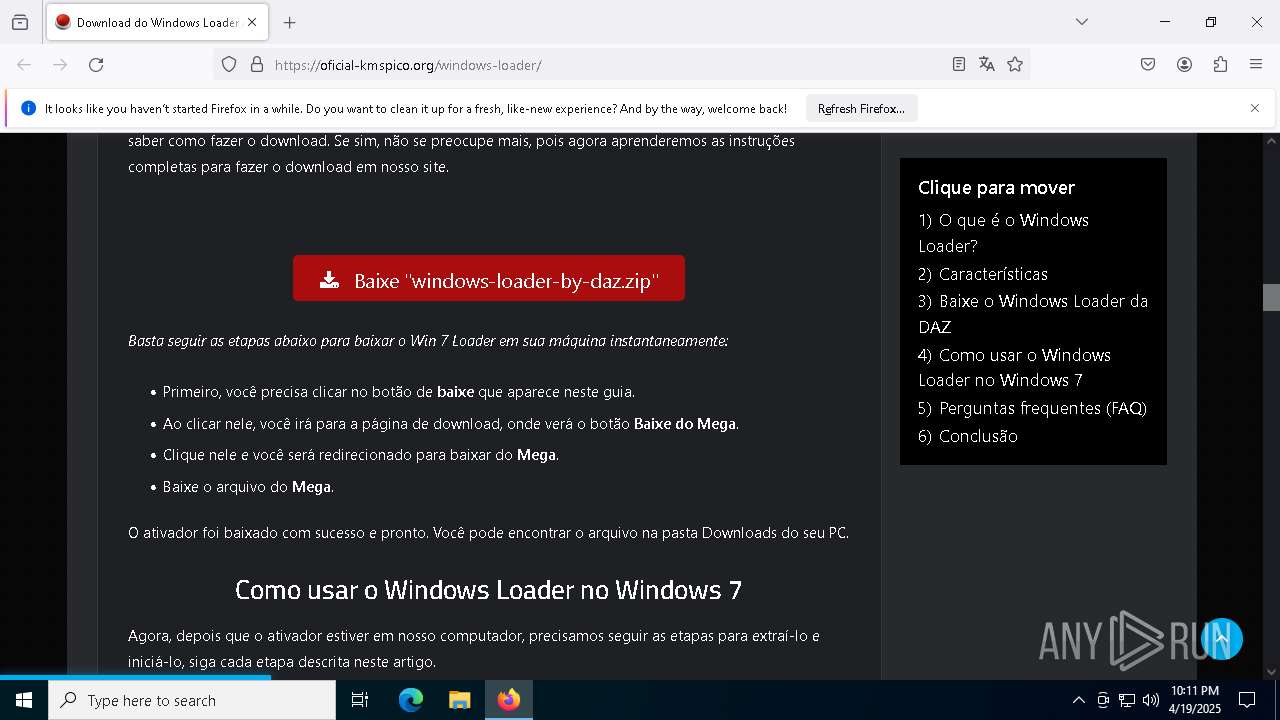
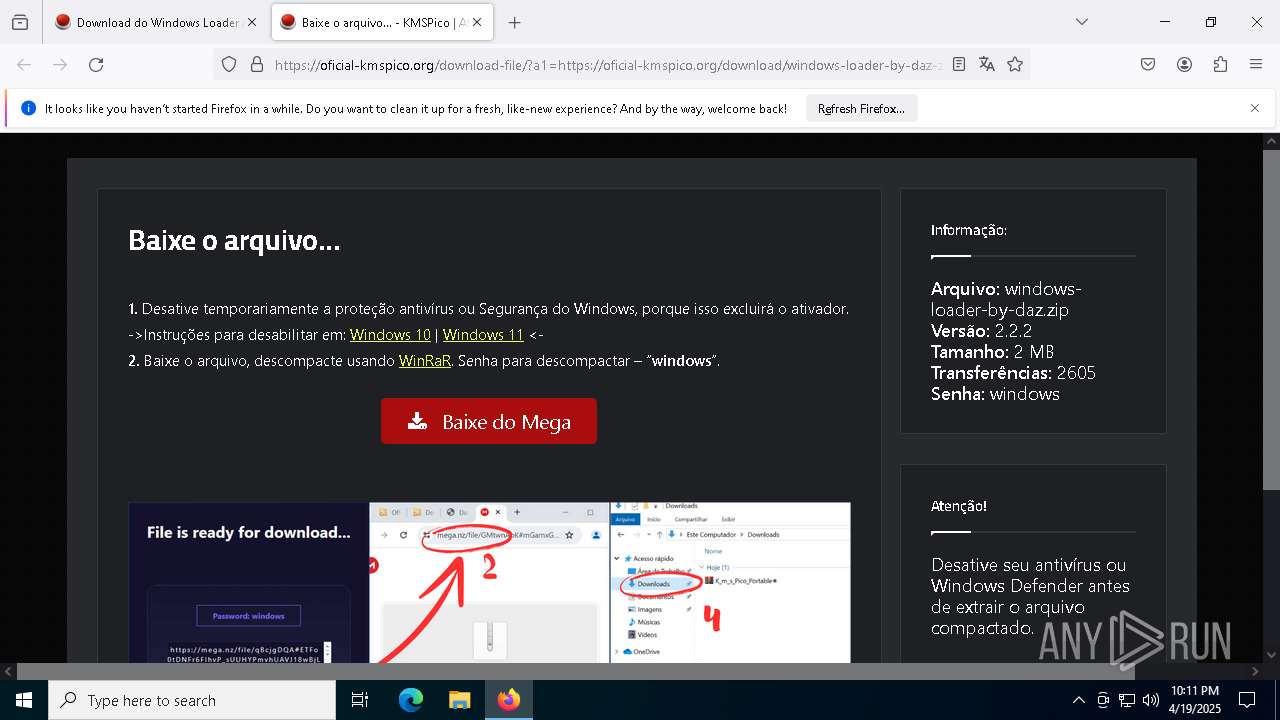
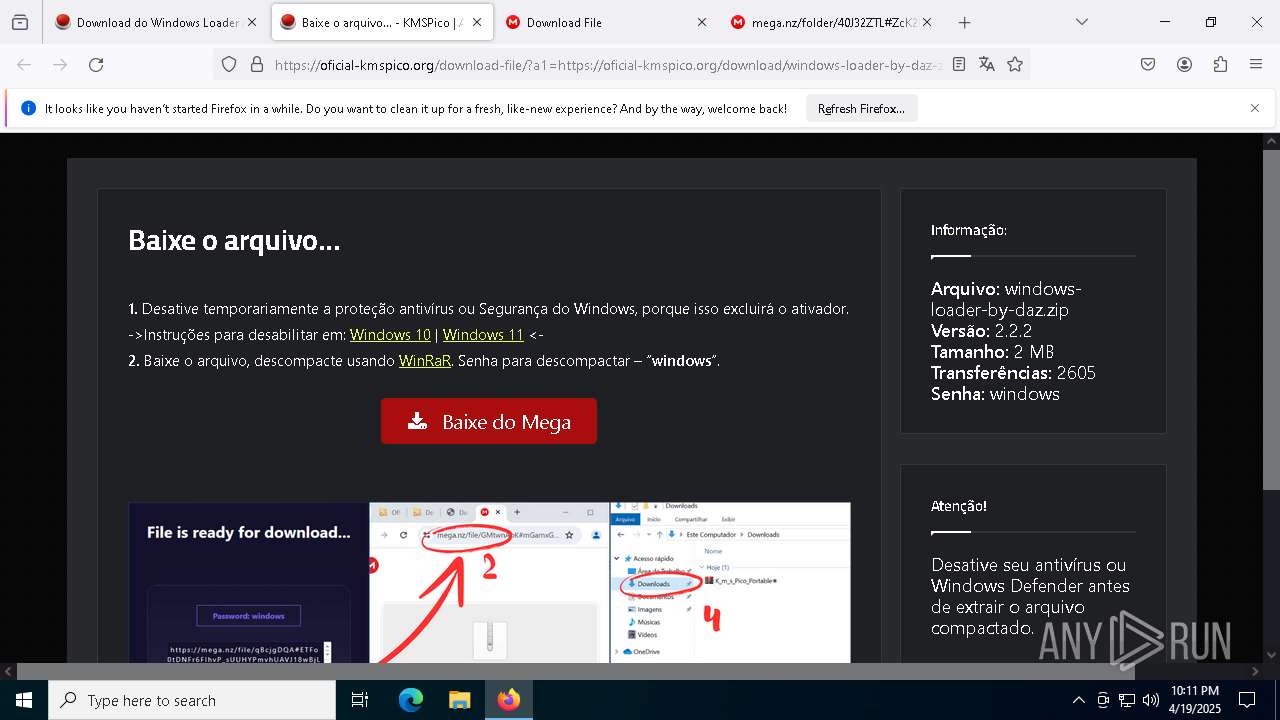
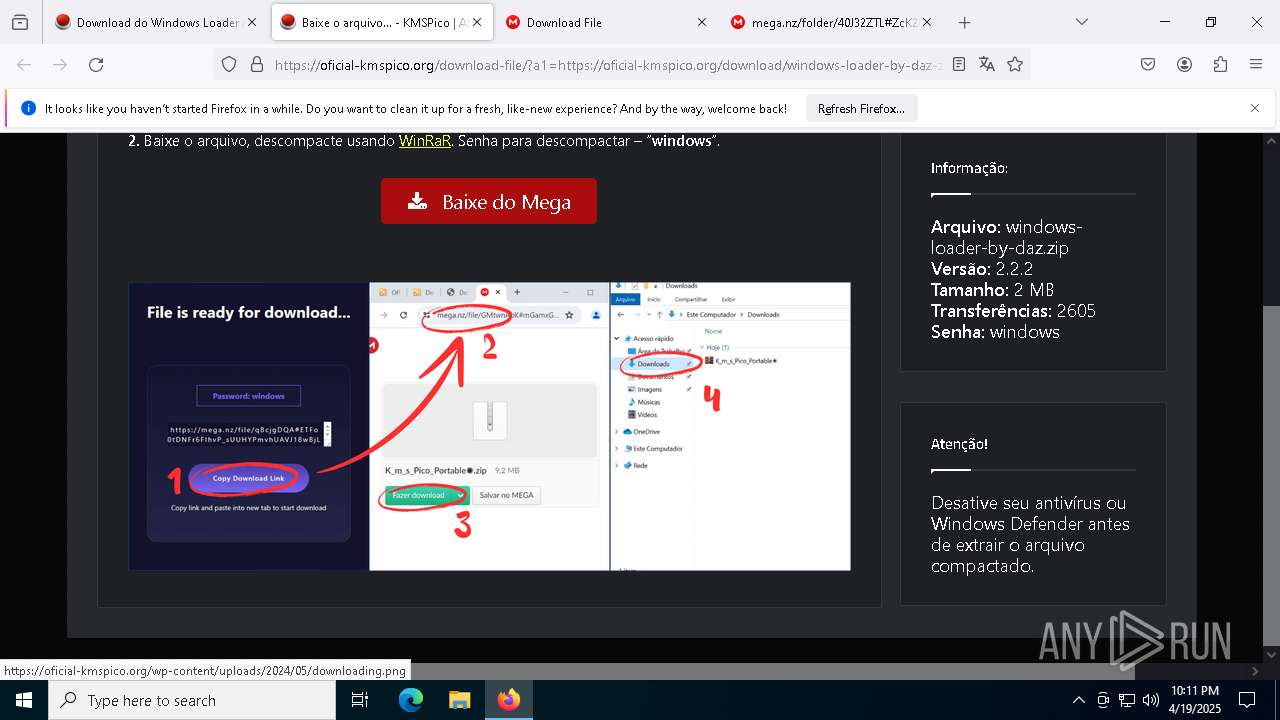
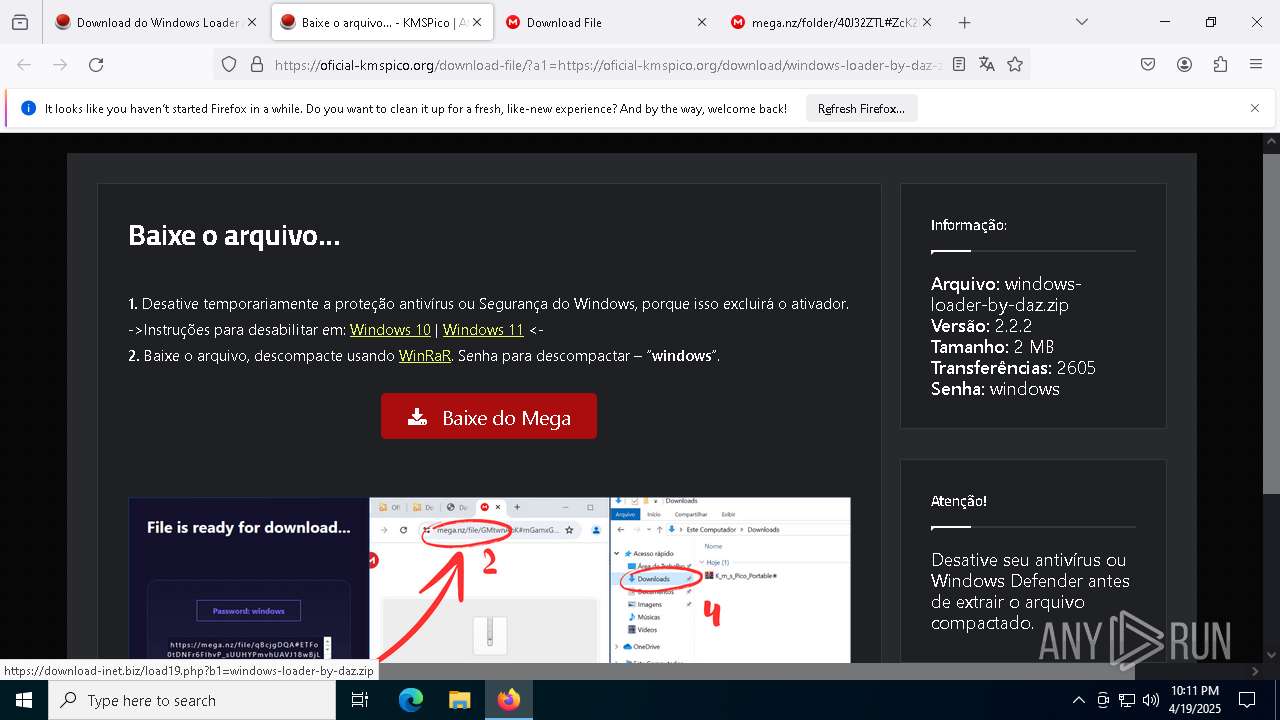
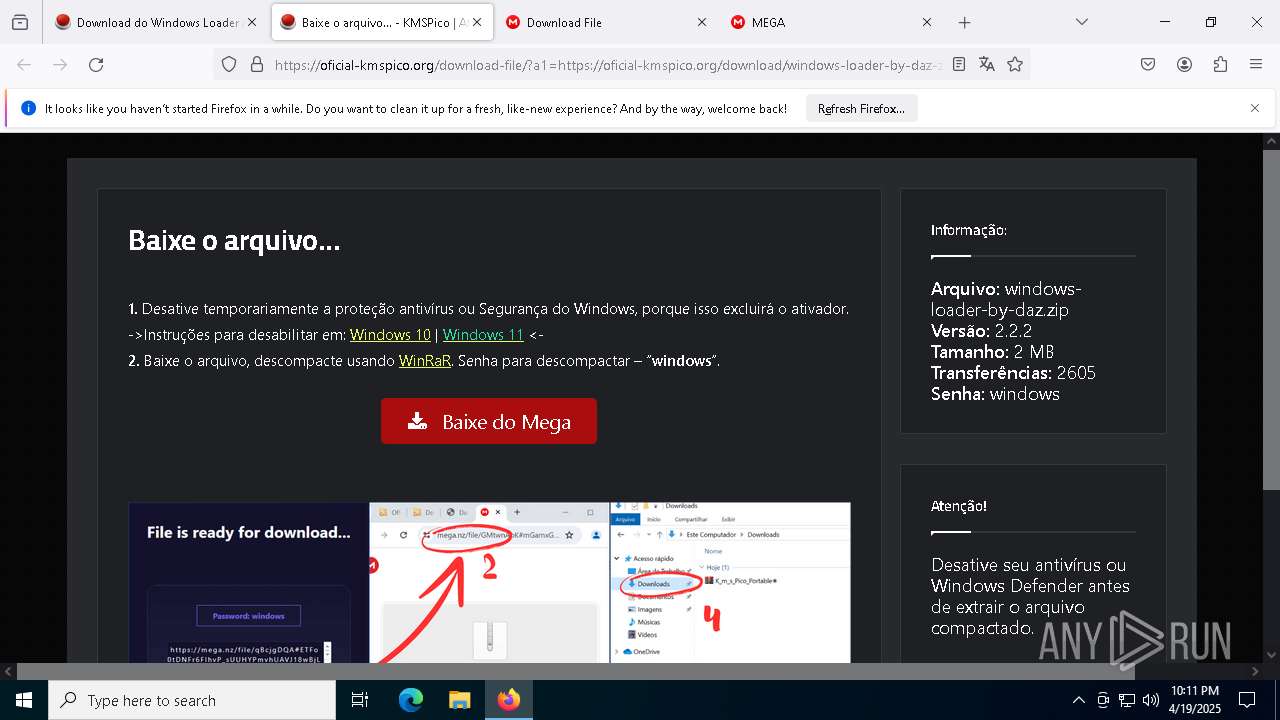
| URL: | https://oficial-kmspico.org/windows-loader/ |
| Full analysis: | https://app.any.run/tasks/aa1cd33f-35cb-494f-b2d4-e8ab5923d597 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 19, 2025, 22:11:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 990EDDD61738374B8900354408FD8F7D |
| SHA1: | D5939D497158D5828CD04652241B83EE78CA9DA2 |
| SHA256: | E4552D545DF757570ECE2CFEE24DAE57C2C8CFE88EFA06DDF1B6E0154D0313AE |
| SSDEEP: | 3:N8Ksgz4yyK:2Ks7u |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 6044)
LUMMA mutex has been found
- activate.exe (PID: 8256)
Steals credentials from Web Browsers
- activate.exe (PID: 8256)
Executing a file with an untrusted certificate
- activate.exe (PID: 8256)
LUMMA has been detected (YARA)
- activate.exe (PID: 8256)
Actions looks like stealing of personal data
- activate.exe (PID: 8256)
Changes powershell execution policy (Bypass)
- activate.exe (PID: 8256)
Bypass execution policy to execute commands
- powershell.exe (PID: 1240)
SUSPICIOUS
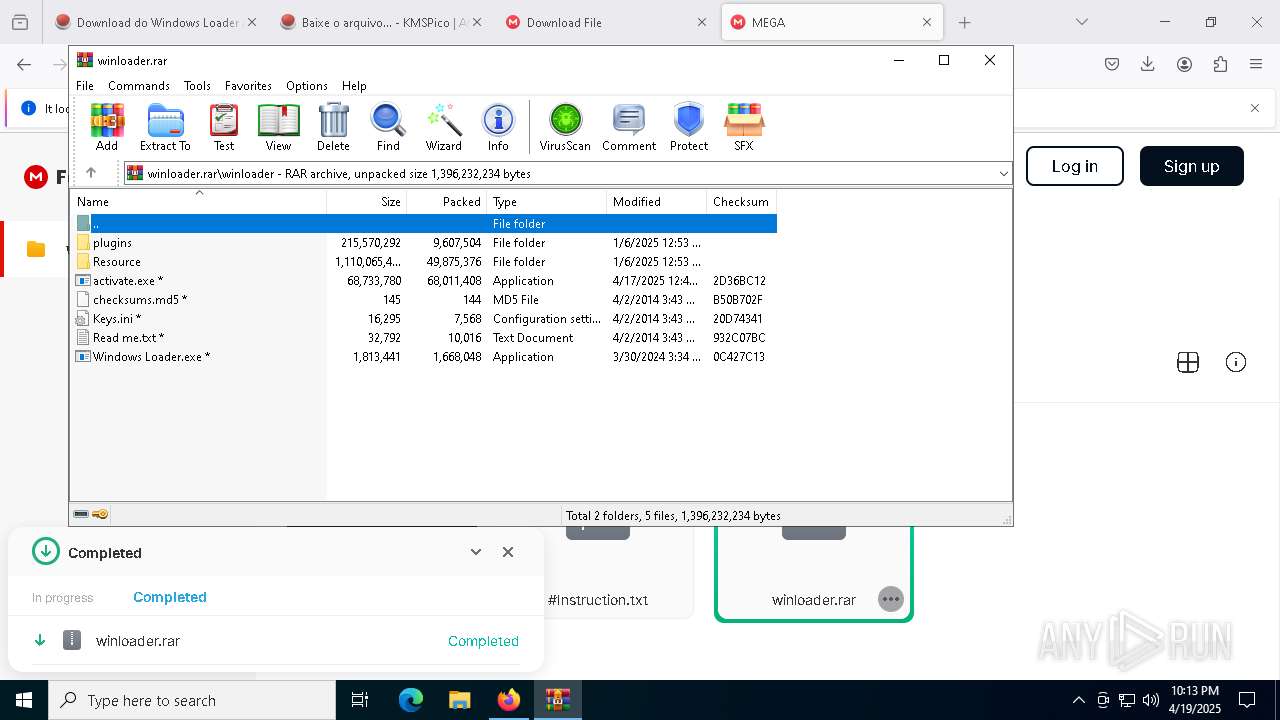
Process drops legitimate windows executable
- WinRAR.exe (PID: 6044)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6044)
There is functionality for taking screenshot (YARA)
- Windows Loader.exe (PID: 7548)
- activate.exe (PID: 8256)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6044)
- Windows Loader.exe (PID: 7548)
Starts POWERSHELL.EXE for commands execution
- activate.exe (PID: 8256)
Searches for installed software
- activate.exe (PID: 8256)
INFO
Application launched itself
- firefox.exe (PID: 6808)
- firefox.exe (PID: 2136)
Reads the software policy settings
- slui.exe (PID: 8152)
- activate.exe (PID: 8256)
- slui.exe (PID: 8556)
- powershell.exe (PID: 1240)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6044)
Manual execution by a user
- WinRAR.exe (PID: 6044)
The sample compiled with english language support
- WinRAR.exe (PID: 6044)
The sample compiled with russian language support
- WinRAR.exe (PID: 6044)
The sample compiled with chinese language support
- WinRAR.exe (PID: 6044)
Checks supported languages
- activate.exe (PID: 8256)
- Windows Loader.exe (PID: 7548)
Reads the computer name
- activate.exe (PID: 8256)
- Windows Loader.exe (PID: 7548)
Checks proxy server information
- slui.exe (PID: 8556)
Create files in a temporary directory
- Windows Loader.exe (PID: 7548)
- powershell.exe (PID: 1240)
Process checks computer location settings
- Windows Loader.exe (PID: 7548)
Reads security settings of Internet Explorer
- powershell.exe (PID: 1240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(8256) activate.exe
C2 (9)ferromny.digital/gwpd
oreheatq.live/gsopp
castmaxw.run/ganzde
steelgoy.run/pqowen
weldorae.digital/geds
advennture.top/GKsiio
smeltingt.run/giiaus
steelixr.live/aguiz
targett.top/dsANGt
Total processes
158
Monitored processes
25
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5432 -childID 7 -isForBrowser -prefsHandle 5464 -prefMapHandle 5460 -prefsLen 31285 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {61709acf-26ec-4341-86e0-f3b98546c6ec} 2136 "\\.\pipe\gecko-crash-server-pipe.2136" 27896727850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1240 | powershell -exec bypass <!DOCTYPE html> <html lang="en"> <head> <meta name="viewport" content="width=device-width, initial-scale=0.75, maximum-scale=1.0, user-scalable=yes" /> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> <title>Pastebin.com - Not Found (#404)</title> </head> <body> <h1>Not Found (#404)</h1> <p>This page is no longer available. It has either expired, been removed by its creator, or removed by one of the Pastebin staff.</p> </body> </html> | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | activate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://oficial-kmspico.org/windows-loader/ | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4200 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6744 -childID 10 -isForBrowser -prefsHandle 6976 -prefMapHandle 6972 -prefsLen 31548 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {20b38ea0-a8d4-48e2-b1c9-171a04c48fe9} 2136 "\\.\pipe\gecko-crash-server-pipe.2136" 278903c8850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4300 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4944 -childID 5 -isForBrowser -prefsHandle 4936 -prefMapHandle 4932 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {730dc82a-8f02-41ab-b7f3-018ab951e349} 2136 "\\.\pipe\gecko-crash-server-pipe.2136" 2789994b850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4756 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4924 -childID 4 -isForBrowser -prefsHandle 4916 -prefMapHandle 4212 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9da51566-19f2-4cce-866e-e485cf271115} 2136 "\\.\pipe\gecko-crash-server-pipe.2136" 2789994b690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5376 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5104 -childID 6 -isForBrowser -prefsHandle 4528 -prefMapHandle 4832 -prefsLen 38055 -prefMapSize 244583 -jsInitHandle 1296 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {4483476f-37dd-4200-a38a-cf76e31d78ab} 2136 "\\.\pipe\gecko-crash-server-pipe.2136" 27899bf7d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
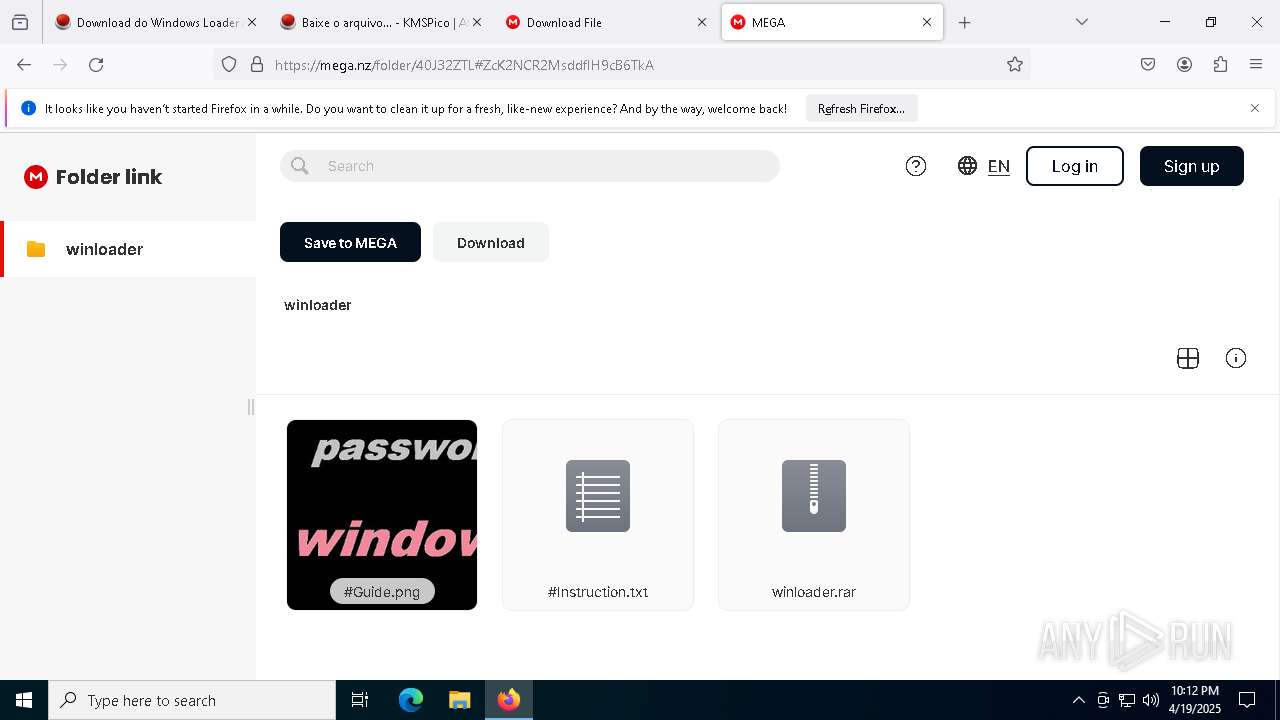
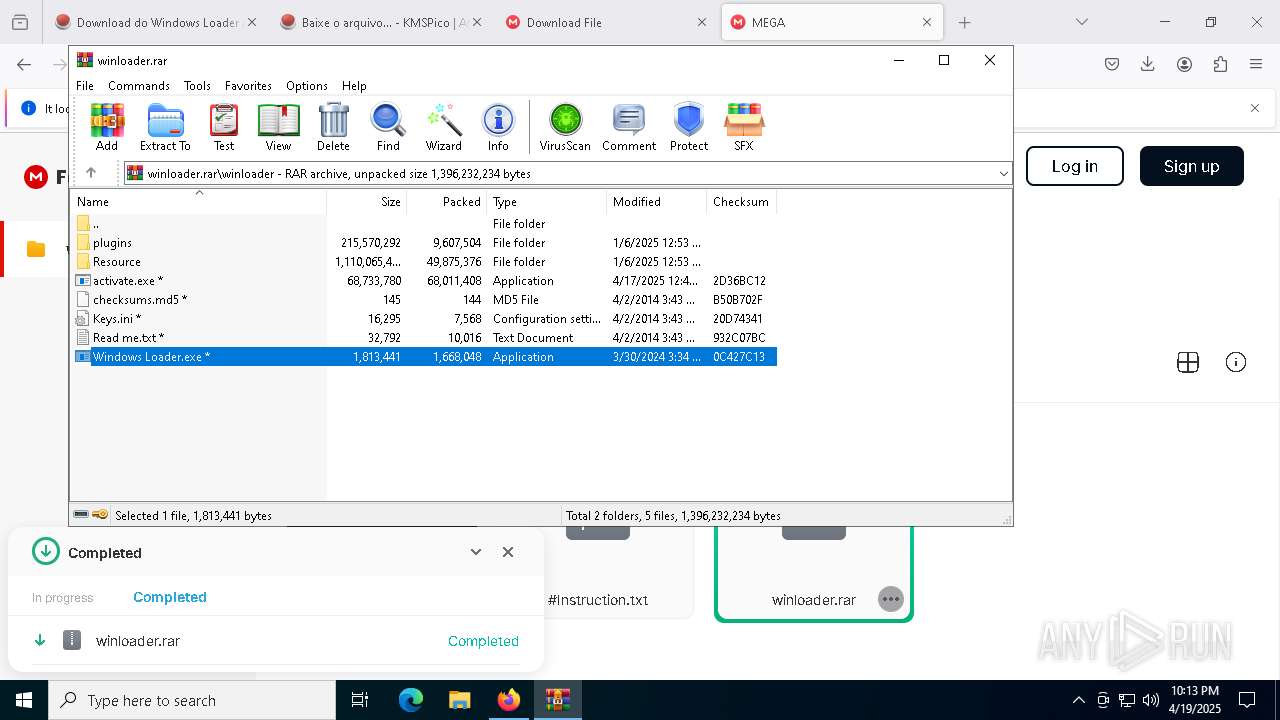
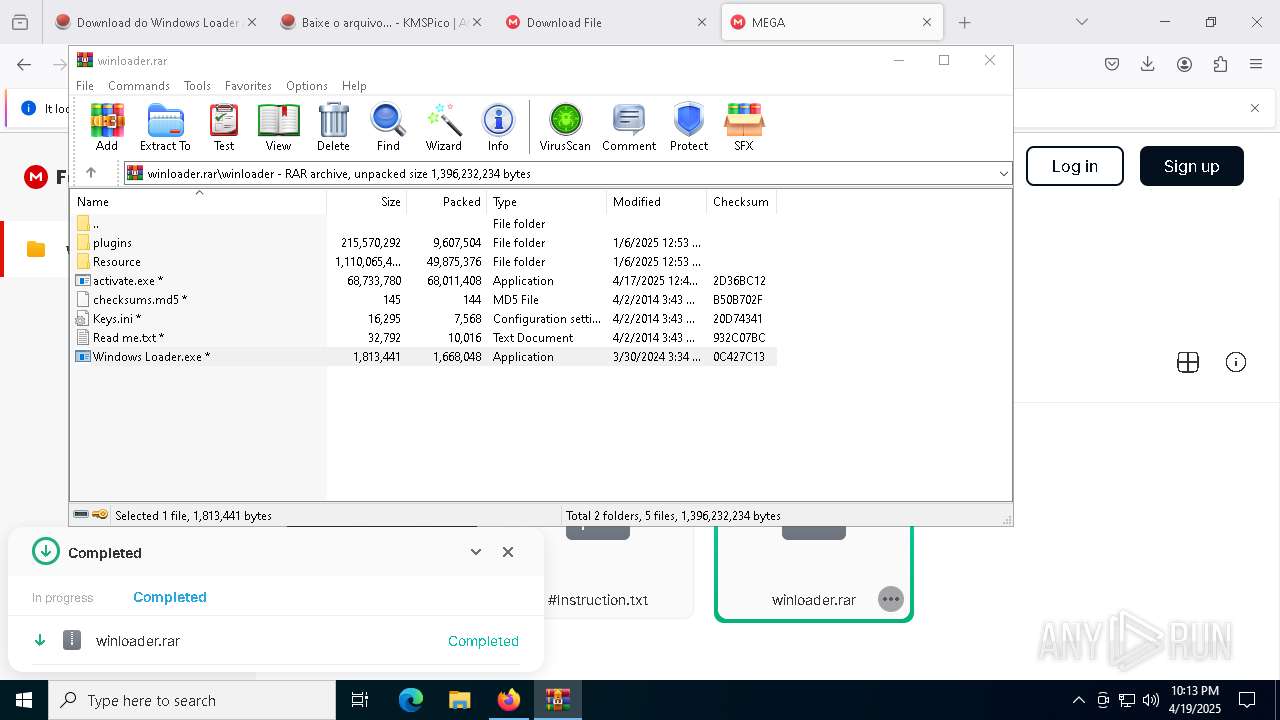
| 6044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\winloader.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
24 452
Read events
24 442
Write events
10
Delete events
0
Modification events
| (PID) Process: | (2136) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\winloader.rar | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
54
Suspicious files
408
Text files
535
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:3462294949FCE0DDBDC5EB19DD2B3B55 | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 2136 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
132
DNS requests
163
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 184.24.77.179:80 | http://e5.o.lencr.org/ | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 184.24.77.179:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 184.24.77.179:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2136 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 184.24.77.179:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2136 | firefox.exe | POST | 200 | 184.24.77.179:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6700 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2136 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2136 | firefox.exe | 104.21.96.1:443 | oficial-kmspico.org | CLOUDFLARENET | — | unknown |
2136 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
2136 | firefox.exe | 216.58.206.74:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
oficial-kmspico.org |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
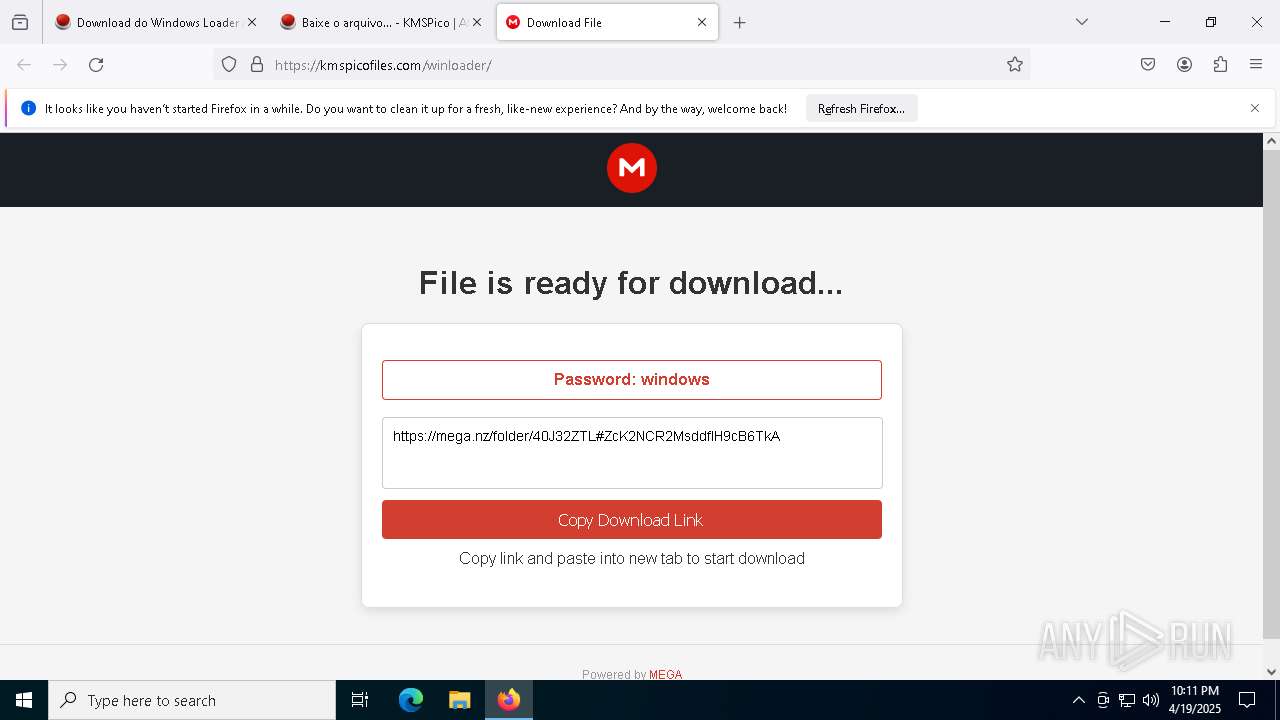
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
2136 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
2136 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
2136 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |