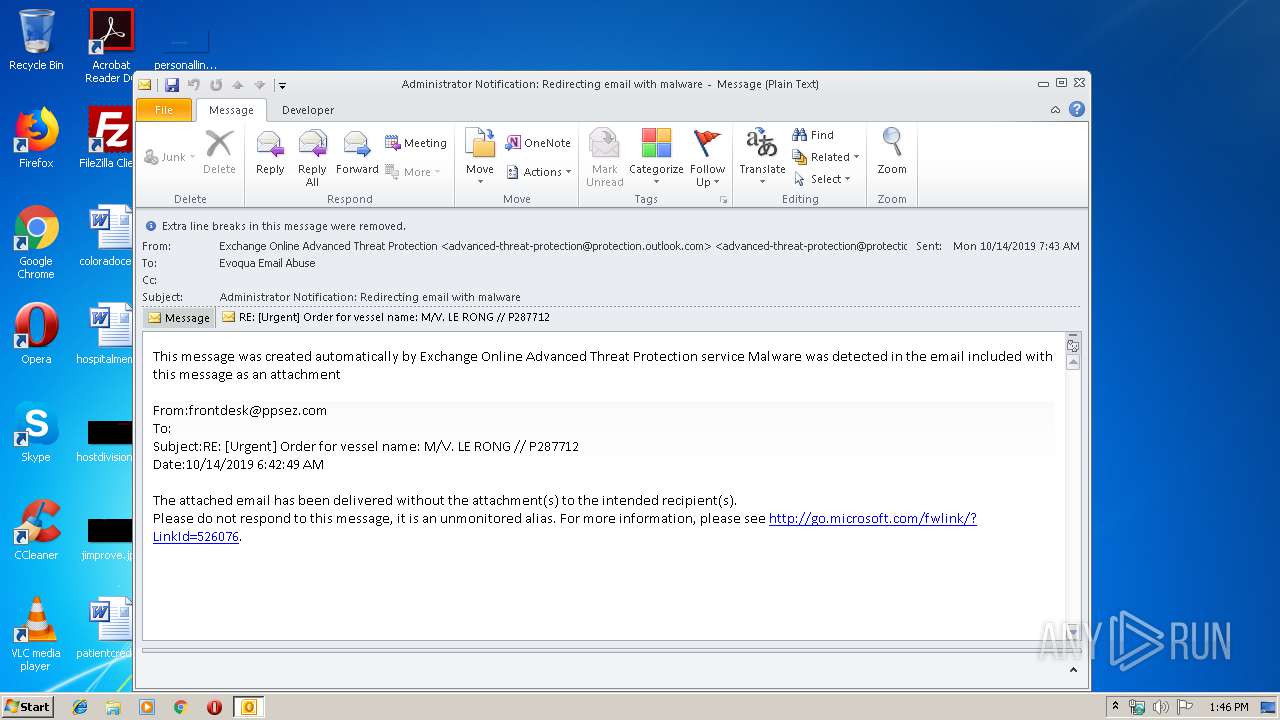
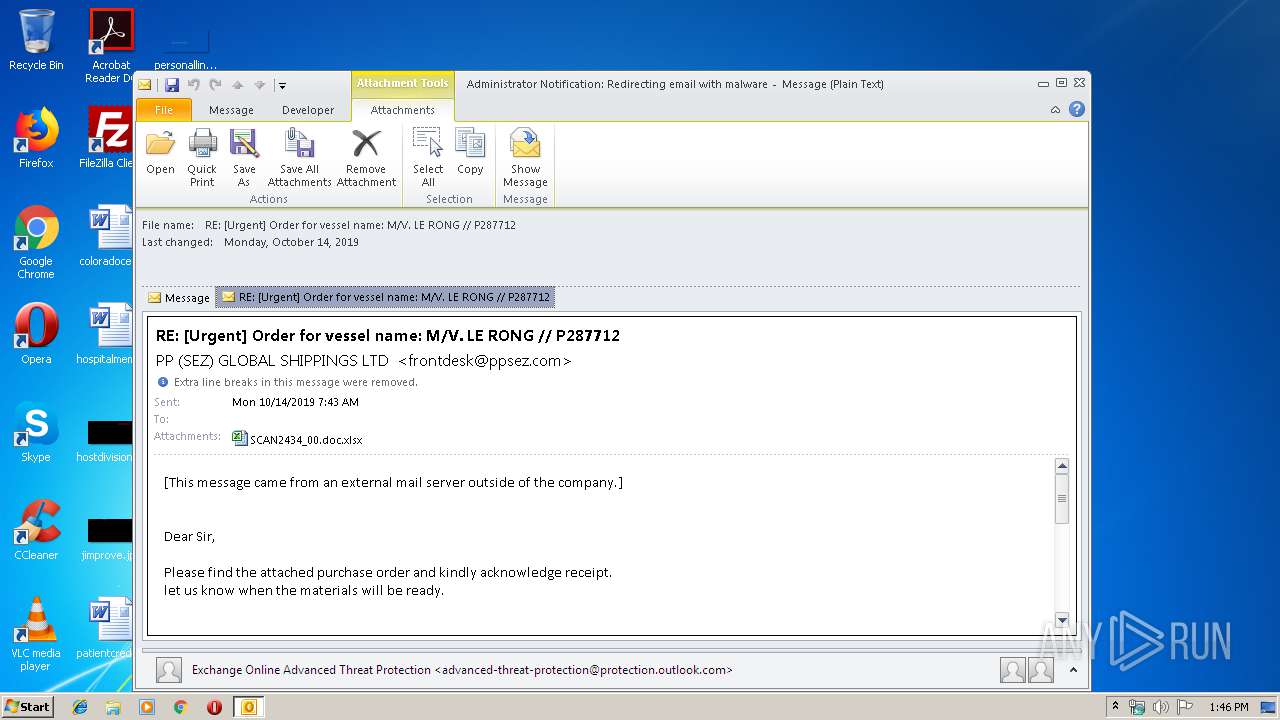
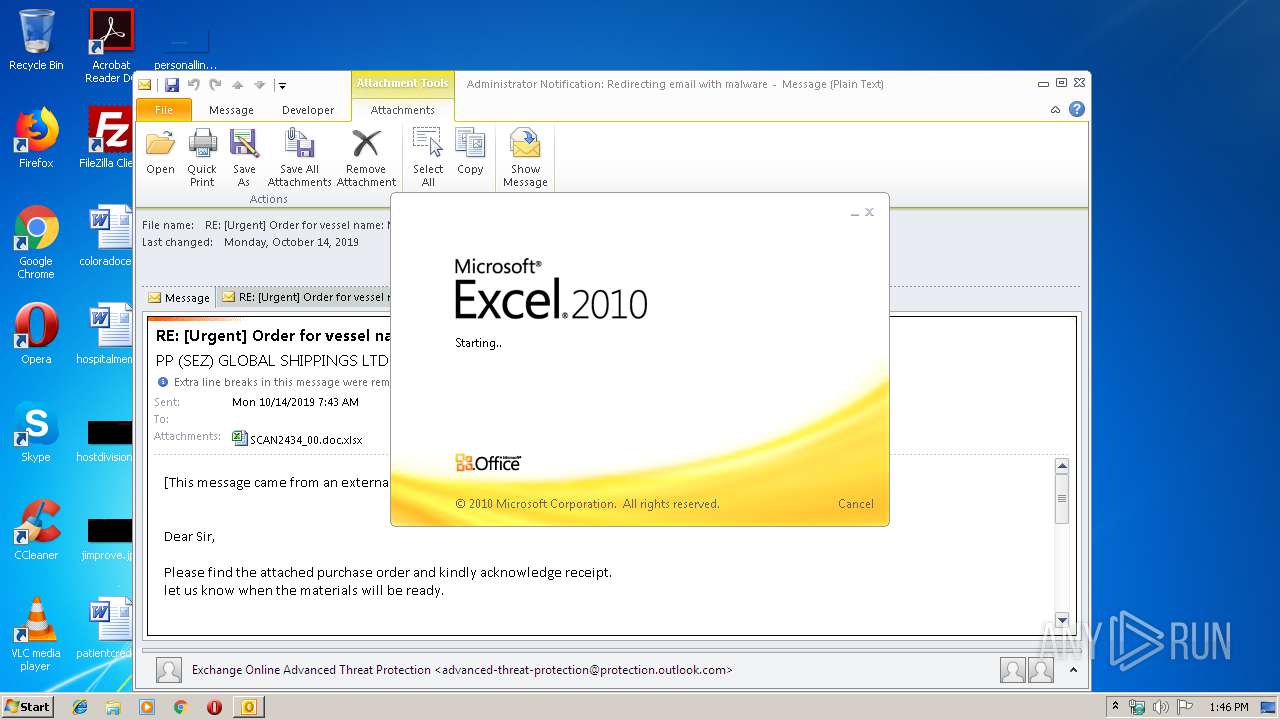
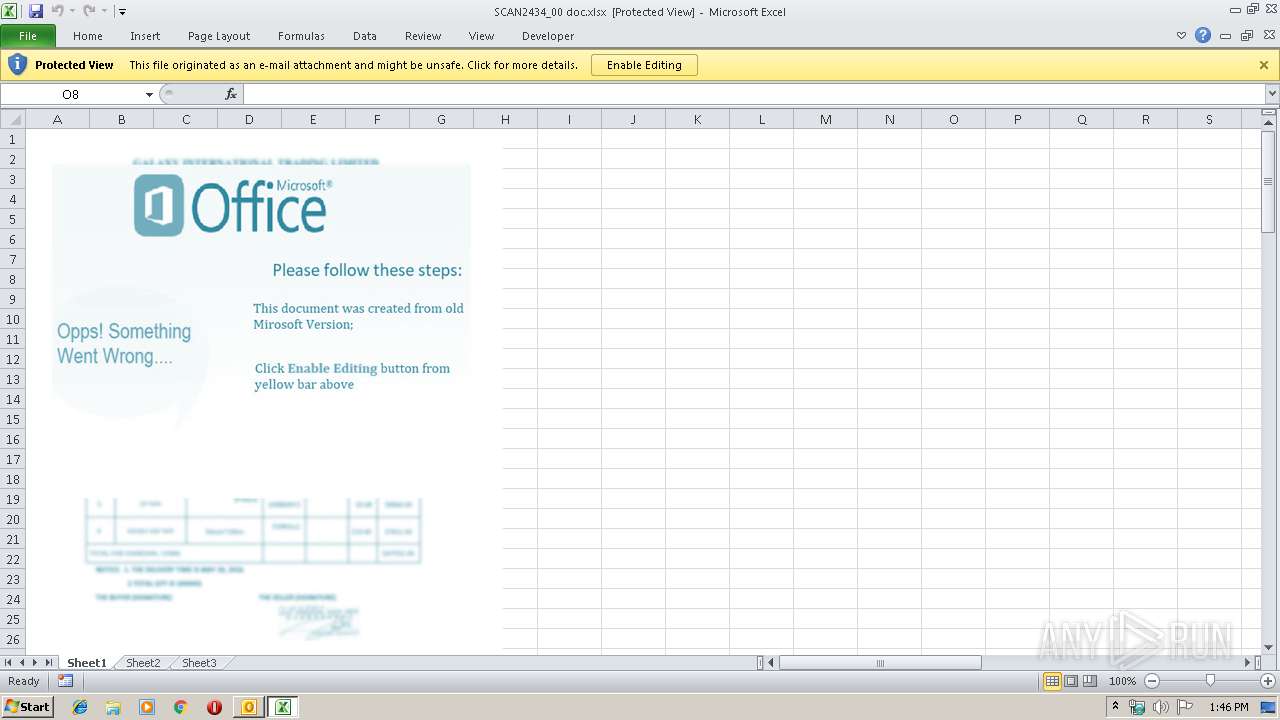
| File name: | Administrator Notification_ Redirecting email with malware.msg |
| Full analysis: | https://app.any.run/tasks/eefa6990-f85c-4b91-a809-1f4ff53a5da3 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | October 14, 2019, 12:45:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 2AB56A65DF9EFD2A7628D0D58F8B5973 |
| SHA1: | E2BDCB726BCFD7E42F9D3905A88D33FADE52D5E5 |
| SHA256: | E41B55C01C65C11617AAD5A5AC19385CFEC6284FB14AD0747C2B1C608952D0DC |
| SSDEEP: | 1536:JlWIWBVYrHfrWzgXJWnWhcfI3PVlJMJpZgdfitbTk8ECIk+qgnoyZZM6WZJUAcY:JOVWizwpoSYo8d+q6oyqP |
MALICIOUS
Application was dropped or rewritten from another process
- vbc.exe (PID: 3964)
- RegAsm.exe (PID: 3732)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 920)
Connects to CnC server
- RegAsm.exe (PID: 3732)
Writes to a start menu file
- vbc.exe (PID: 3964)
LOKIBOT was detected
- RegAsm.exe (PID: 3732)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 3732)
Detected artifacts of LokiBot
- RegAsm.exe (PID: 3732)
SUSPICIOUS
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3332)
- EXCEL.EXE (PID: 2848)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3332)
- RegAsm.exe (PID: 3732)
- vbc.exe (PID: 3964)
Executed via COM
- EQNEDT32.EXE (PID: 920)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3332)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 920)
- vbc.exe (PID: 3964)
- RegAsm.exe (PID: 3732)
Application launched itself
- EXCEL.EXE (PID: 2848)
Loads DLL from Mozilla Firefox
- RegAsm.exe (PID: 3732)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2848)
- EXCEL.EXE (PID: 3308)
- OUTLOOK.EXE (PID: 3332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3308 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3332 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Administrator Notification_ Redirecting email with malware.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3732 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | vbc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 3964 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 096
Read events
2 400
Write events
656
Delete events
40
Modification events
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330512052 | |||
| (PID) Process: | (3332) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
4
Suspicious files
5
Text files
28
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3332 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9BFC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3332 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF65E19FB3A437048F.TMP | — | |
MD5:— | SHA256:— | |||
| 3332 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\WDLBI46K\SCAN2434_00 doc (2).xlsx\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRBA42.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\WDLBI46K\~$SCAN2434_00 doc.xlsx | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFB3ABD6D85451829B.TMP | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF49720AC2FA459A70.TMP | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\OICE_08B2D100-C577-47E7-8807-06E12AF988AF.0\CC067B2C.xlsx\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\E01A.tmp\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2848 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF8378A2837494D169.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
3
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3732 | RegAsm.exe | POST | — | 161.117.39.99:80 | http://fueda.info/sky8/fre.php | SG | — | — | malicious |
3732 | RegAsm.exe | POST | — | 161.117.39.99:80 | http://fueda.info/sky8/fre.php | SG | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3332 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
920 | EQNEDT32.EXE | 103.200.4.42:443 | tps-finlogistics.com | NewMedia Express Pte Ltd | SG | suspicious |
3732 | RegAsm.exe | 161.117.39.99:80 | fueda.info | — | SG | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
tps-finlogistics.com |
| suspicious |
fueda.info |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3732 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3732 | RegAsm.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3732 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3 ETPRO signatures available at the full report