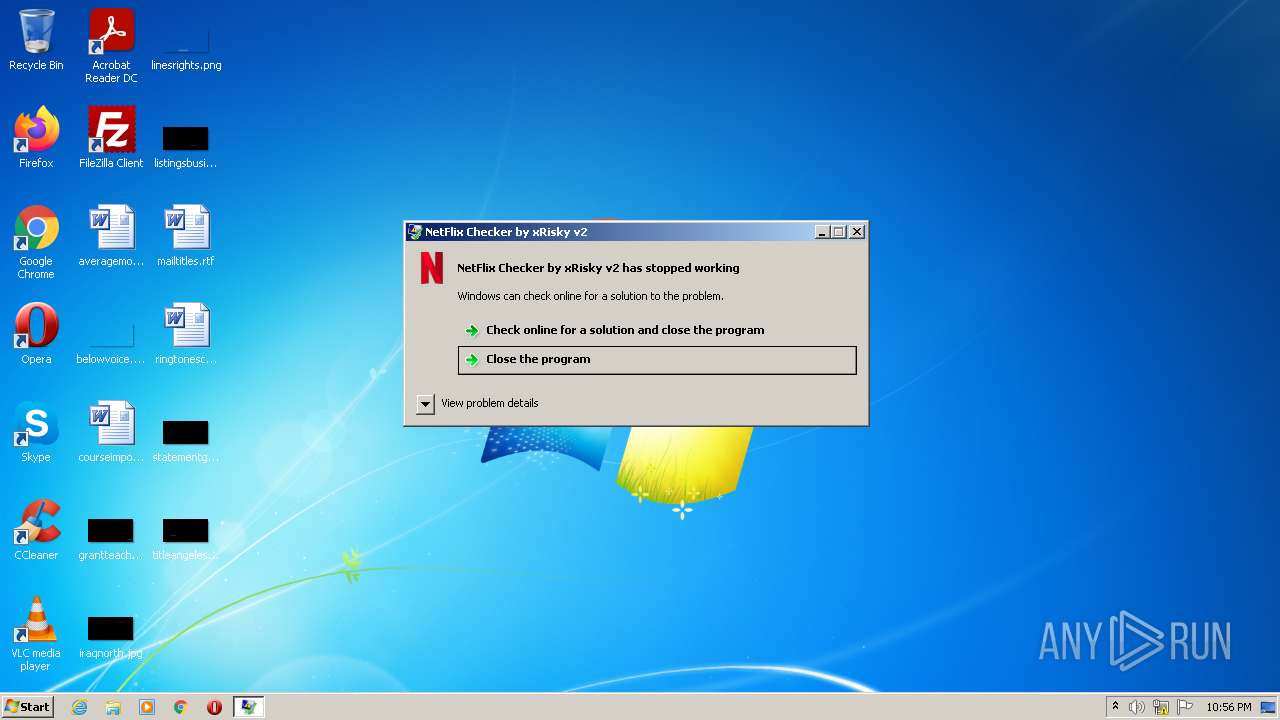
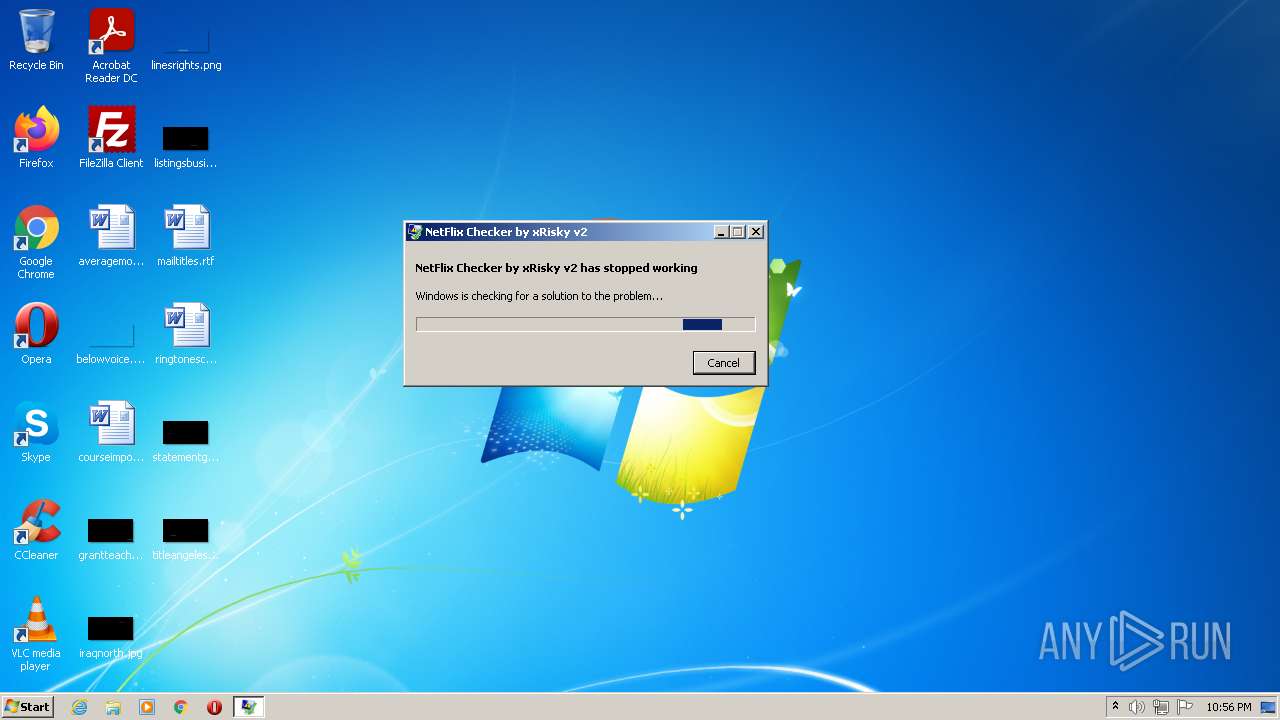
| File name: | NetFlix Checker by xRisky v2.exe |
| Full analysis: | https://app.any.run/tasks/42a8ca35-9d1e-47b3-bba3-43d5eb19234f |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | July 09, 2022, 21:56:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 8556792F20126E1ED89F93E1E26030E5 |
| SHA1: | E733716554CF9EDF2A5343AEF0E93C95B7FA7CD4 |
| SHA256: | E3544F1A9707EC1CE083AFE0AE64F2EDE38A7D53FC6F98AAB917CA049BC63E69 |
| SSDEEP: | 196608:/GGbxwsjQ9VQ5MTZyFJ0NqRJa+Go7zJPF3v/:hbFqyFCNqSuR5v |
MALICIOUS
Application was dropped or rewritten from another process
- winlogon.exe (PID: 3464)
REDLINE detected by memory dumps
- winlogon.exe (PID: 3464)
- NetFlix Checker by xRisky v2.exe (PID: 3036)
Drops executable file immediately after starts
- NetFlix Checker by xRisky v2.exe (PID: 3036)
REDLINE was detected
- winlogon.exe (PID: 3464)
Stealing of credential data
- winlogon.exe (PID: 3464)
Steals credentials from Web Browsers
- winlogon.exe (PID: 3464)
Actions looks like stealing of personal data
- winlogon.exe (PID: 3464)
SUSPICIOUS
Checks supported languages
- NetFlix Checker by xRisky v2.exe (PID: 3036)
- winlogon.exe (PID: 3464)
Creates files in the user directory
- NetFlix Checker by xRisky v2.exe (PID: 3036)
Reads the computer name
- winlogon.exe (PID: 3464)
- NetFlix Checker by xRisky v2.exe (PID: 3036)
Executable content was dropped or overwritten
- NetFlix Checker by xRisky v2.exe (PID: 3036)
Drops a file with a compile date too recent
- NetFlix Checker by xRisky v2.exe (PID: 3036)
Reads Environment values
- winlogon.exe (PID: 3464)
Reads the cookies of Mozilla Firefox
- winlogon.exe (PID: 3464)
Reads the cookies of Google Chrome
- winlogon.exe (PID: 3464)
Searches for installed software
- winlogon.exe (PID: 3464)
INFO
Reads settings of System Certificates
- winlogon.exe (PID: 3464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3036) NetFlix Checker by xRisky v2.exe
C2 (1)siyatermi.duckdns.org:17044
Botnet,
US (157)
Environment
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Local State
LocalPrefs.json
Port
Pass
User
:
Host
MANGO
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
KeyDataBlob
ObjectLength
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
http://
/
|
Yandex\YaAddon
AwsR
siyatermi.duckdns.org:17044
,
asf
*wallet*
Armory
\Armory
*.wallet
Atomic
\atomic
*
ibnejdfjmmkpcnlpebklmnkoeoihofec
Tronlink
jbdaocneiiinmjbjlgalhcelgbejmnid
NiftyWallet
nkbihfbeogaeaoehlefnkodbefgpgknn
Metamask
afbcbjpbpfadlkmhmclhkeeodmamcflc
MathWallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Coinbase
fhbohimaelbohpjbbldcngcnapndodjp
BinanceChain
odbfpeeihdkbihmopkbjmoonfanlbfcl
BraveWallet
hpglfhgfnhbgpjdenjgmdgoeiappafln
GuardaWallet
blnieiiffboillknjnepogjhkgnoapac
EqualWallet
cjelfplplebdjjenllpjcblmjkfcffne
JaxxxLiberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi
BitAppWallet
kncchdigobghenbbaddojjnnaogfppfj
iWallet
amkmjjmmflddogmhpjloimipbofnfjih
Wombat
UnknownExtension
_
Local Extension Settings
Coinomi
\Coinomi
Profile_
Tel
egram.exe
\Telegram Desktop\tdata
-*.lo--g
1*.1l1d1b
String
Replace
.csv
.exe
.docx
.doc
.dll
.txt
System.UI
File.IO
*.json
string.Replace
Guarda
\Guarda
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
ToString
UNIQUE
(
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
ROWindowsServiceOT\SecurityCenteWindowsServicer2
ROWindowsServiceOT\SecurWindowsServiceityCenter
AntqueiresivirusProdqueiresuct
AntqueiresiSpyqueiresWareProdqueiresuct
FiqueiresrewallProqueiresduct
WindowsService
SELECT * FROM
queires
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
TotalVisibleMemorySize
{0} MB or {1}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
(PID) Process(3464) winlogon.exe
C2 (1)siyatermi.duckdns.org:17044
Botnet,
US (157)
Environment
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Local State
LocalPrefs.json
Port
Pass
User
:
Host
MANGO
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
KeyDataBlob
ObjectLength
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
http://
/
|
Yandex\YaAddon
AwsR
siyatermi.duckdns.org:17044
,
asf
*wallet*
Armory
\Armory
*.wallet
Atomic
\atomic
*
ibnejdfjmmkpcnlpebklmnkoeoihofec
Tronlink
jbdaocneiiinmjbjlgalhcelgbejmnid
NiftyWallet
nkbihfbeogaeaoehlefnkodbefgpgknn
Metamask
afbcbjpbpfadlkmhmclhkeeodmamcflc
MathWallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Coinbase
fhbohimaelbohpjbbldcngcnapndodjp
BinanceChain
odbfpeeihdkbihmopkbjmoonfanlbfcl
BraveWallet
hpglfhgfnhbgpjdenjgmdgoeiappafln
GuardaWallet
blnieiiffboillknjnepogjhkgnoapac
EqualWallet
cjelfplplebdjjenllpjcblmjkfcffne
JaxxxLiberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi
BitAppWallet
kncchdigobghenbbaddojjnnaogfppfj
iWallet
amkmjjmmflddogmhpjloimipbofnfjih
Wombat
UnknownExtension
_
Local Extension Settings
Coinomi
\Coinomi
Profile_
Tel
egram.exe
\Telegram Desktop\tdata
-*.lo--g
1*.1l1d1b
String
Replace
.csv
.exe
.docx
.doc
.dll
.txt
System.UI
File.IO
*.json
string.Replace
Guarda
\Guarda
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
ToString
UNIQUE
(
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
ROWindowsServiceOT\SecurityCenteWindowsServicer2
ROWindowsServiceOT\SecurWindowsServiceityCenter
AntqueiresivirusProdqueiresuct
AntqueiresiSpyqueiresWareProdqueiresuct
FiqueiresrewallProqueiresduct
WindowsService
SELECT * FROM
queires
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
TotalVisibleMemorySize
{0} MB or {1}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| AssemblyVersion: | 0.0.0.0 |
|---|---|
| ProductVersion: | 2,0,0,0 |
| ProductName: | NetFlix Checker by xRisky v2 |
| OriginalFileName: | NetFlix Checker by xRisky v22.exe |
| LegalTrademarks: | NetFlix Checker by xRisky v2 |
| LegalCopyright: | NetFlix Checker by xRisky v2 |
| InternalName: | NetFlix Checker by xRisky v22.exe |
| FileVersion: | 2,0,0,0 |
| FileDescription: | NetFlix Checker by xRisky v2 |
| CompanyName: | NetFlix Checker by xRisky v2 |
| Comments: | NetFlix Checker by xRisky v2 |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 2.0.0.0 |
| FileVersionNumber: | 2.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x675eae |
| UninitializedDataSize: | - |
| InitializedDataSize: | 25088 |
| CodeSize: | 6766592 |
| LinkerVersion: | 11 |
| PEType: | PE32 |
| TimeStamp: | 2022:07:03 09:45:37+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Jul-2022 07:45:37 |
| Comments: | NetFlix Checker by xRisky v2 |
| CompanyName: | NetFlix Checker by xRisky v2 |
| FileDescription: | NetFlix Checker by xRisky v2 |
| FileVersion: | 2,0,0,0 |
| InternalName: | NetFlix Checker by xRisky v22.exe |
| LegalCopyright: | NetFlix Checker by xRisky v2 |
| LegalTrademarks: | NetFlix Checker by xRisky v2 |
| OriginalFilename: | NetFlix Checker by xRisky v22.exe |
| ProductName: | NetFlix Checker by xRisky v2 |
| ProductVersion: | 2,0,0,0 |
| Assembly Version: | 0.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 03-Jul-2022 07:45:37 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00673EB4 | 0x00674000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.99996 |
.rsrc | 0x00676000 | 0x00005F50 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.27639 |
.reloc | 0x0067C000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89886 | 669 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 3.94232 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 3.49824 | 4392 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 3.27986 | 9832 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 7.70588 | 6709 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.55342 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
38
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3036 | "C:\Users\admin\AppData\Local\Temp\NetFlix Checker by xRisky v2.exe" | C:\Users\admin\AppData\Local\Temp\NetFlix Checker by xRisky v2.exe | Explorer.EXE | ||||||||||||
User: admin Company: NetFlix Checker by xRisky v2 Integrity Level: MEDIUM Description: NetFlix Checker by xRisky v2 Exit code: 3762504530 Version: 2,0,0,0 Modules
RedLine(PID) Process(3036) NetFlix Checker by xRisky v2.exe C2 (1)siyatermi.duckdns.org:17044 Botnet, US (157) Environment UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Local State LocalPrefs.json Port Pass User : Host MANGO %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode KeyDataBlob ObjectLength BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - http:// / | Yandex\YaAddon AwsR siyatermi.duckdns.org:17044 , asf *wallet* Armory \Armory *.wallet Atomic \atomic * ibnejdfjmmkpcnlpebklmnkoeoihofec Tronlink jbdaocneiiinmjbjlgalhcelgbejmnid NiftyWallet nkbihfbeogaeaoehlefnkodbefgpgknn Metamask afbcbjpbpfadlkmhmclhkeeodmamcflc MathWallet hnfanknocfeofbddgcijnmhnfnkdnaad Coinbase fhbohimaelbohpjbbldcngcnapndodjp BinanceChain odbfpeeihdkbihmopkbjmoonfanlbfcl BraveWallet hpglfhgfnhbgpjdenjgmdgoeiappafln GuardaWallet blnieiiffboillknjnepogjhkgnoapac EqualWallet cjelfplplebdjjenllpjcblmjkfcffne JaxxxLiberty fihkakfobkmkjojpchpfgcmhfjnmnfpi BitAppWallet kncchdigobghenbbaddojjnnaogfppfj iWallet amkmjjmmflddogmhpjloimipbofnfjih Wombat UnknownExtension _ Local Extension Settings Coinomi \Coinomi Profile_ Tel egram.exe \Telegram Desktop\tdata -*.lo--g 1*.1l1d1b String Replace .csv .exe .docx .doc .dll .txt System.UI File.IO *.json string.Replace Guarda \Guarda %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ToString UNIQUE ( " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM ROWindowsServiceOT\SecurityCenteWindowsServicer2 ROWindowsServiceOT\SecurWindowsServiceityCenter AntqueiresivirusProdqueiresuct AntqueiresiSpyqueiresWareProdqueiresuct FiqueiresrewallProqueiresduct WindowsService SELECT * FROM queires SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem TotalVisibleMemorySize {0} MB or {1} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ | |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Roaming\winlogon.exe" | C:\Users\admin\AppData\Roaming\winlogon.exe | NetFlix Checker by xRisky v2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
RedLine(PID) Process(3464) winlogon.exe C2 (1)siyatermi.duckdns.org:17044 Botnet, US (157) Environment UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Local State LocalPrefs.json Port Pass User : Host MANGO %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode KeyDataBlob ObjectLength BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - http:// / | Yandex\YaAddon AwsR siyatermi.duckdns.org:17044 , asf *wallet* Armory \Armory *.wallet Atomic \atomic * ibnejdfjmmkpcnlpebklmnkoeoihofec Tronlink jbdaocneiiinmjbjlgalhcelgbejmnid NiftyWallet nkbihfbeogaeaoehlefnkodbefgpgknn Metamask afbcbjpbpfadlkmhmclhkeeodmamcflc MathWallet hnfanknocfeofbddgcijnmhnfnkdnaad Coinbase fhbohimaelbohpjbbldcngcnapndodjp BinanceChain odbfpeeihdkbihmopkbjmoonfanlbfcl BraveWallet hpglfhgfnhbgpjdenjgmdgoeiappafln GuardaWallet blnieiiffboillknjnepogjhkgnoapac EqualWallet cjelfplplebdjjenllpjcblmjkfcffne JaxxxLiberty fihkakfobkmkjojpchpfgcmhfjnmnfpi BitAppWallet kncchdigobghenbbaddojjnnaogfppfj iWallet amkmjjmmflddogmhpjloimipbofnfjih Wombat UnknownExtension _ Local Extension Settings Coinomi \Coinomi Profile_ Tel egram.exe \Telegram Desktop\tdata -*.lo--g 1*.1l1d1b String Replace .csv .exe .docx .doc .dll .txt System.UI File.IO *.json string.Replace Guarda \Guarda %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ToString UNIQUE ( " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM ROWindowsServiceOT\SecurityCenteWindowsServicer2 ROWindowsServiceOT\SecurWindowsServiceityCenter AntqueiresivirusProdqueiresuct AntqueiresiSpyqueiresWareProdqueiresuct FiqueiresrewallProqueiresduct WindowsService SELECT * FROM queires SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem TotalVisibleMemorySize {0} MB or {1} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ | |||||||||||||||
Total events
4 896
Read events
4 862
Write events
34
Delete events
0
Modification events
| (PID) Process: | (3036) NetFlix Checker by xRisky v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3036) NetFlix Checker by xRisky v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3036) NetFlix Checker by xRisky v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3036) NetFlix Checker by xRisky v2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3464) winlogon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\winlogon_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3464) winlogon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\winlogon_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3464) winlogon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\winlogon_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3464) winlogon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\winlogon_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3464) winlogon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\winlogon_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3464) winlogon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\winlogon_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BDC.tmp | sqlite | |
MD5:D02907BE1C995E1E51571EEDB82FA281 | SHA256:2189977F6EA58BDAD5883720B099E12B869F223FB9B18AC40E7D37C5954A55DD | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BED.tmp | sqlite | |
MD5:D02907BE1C995E1E51571EEDB82FA281 | SHA256:2189977F6EA58BDAD5883720B099E12B869F223FB9B18AC40E7D37C5954A55DD | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BEE.tmp | sqlite | |
MD5:D02907BE1C995E1E51571EEDB82FA281 | SHA256:2189977F6EA58BDAD5883720B099E12B869F223FB9B18AC40E7D37C5954A55DD | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BCA.tmp | sqlite | |
MD5:B8E63E7225C9F4E0A81371F29D6456D8 | SHA256:35A6919CE60EA8E0A44934F8B267BDE2C5A063C2E32F22D34724F168C43150C8 | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8C02.tmp | sqlite | |
MD5:D02907BE1C995E1E51571EEDB82FA281 | SHA256:2189977F6EA58BDAD5883720B099E12B869F223FB9B18AC40E7D37C5954A55DD | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BA8.tmp | sqlite | |
MD5:CC104C4E4E904C3AD7AD5C45FBFA7087 | SHA256:321BE844CECC903EF1E7F875B729C96BB3ED0D4986314384CD5944A29A670C9B | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BC9.tmp | sqlite | |
MD5:B8E63E7225C9F4E0A81371F29D6456D8 | SHA256:35A6919CE60EA8E0A44934F8B267BDE2C5A063C2E32F22D34724F168C43150C8 | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BA9.tmp | sqlite | |
MD5:CC104C4E4E904C3AD7AD5C45FBFA7087 | SHA256:321BE844CECC903EF1E7F875B729C96BB3ED0D4986314384CD5944A29A670C9B | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8C13.tmp | sqlite | |
MD5:D02907BE1C995E1E51571EEDB82FA281 | SHA256:2189977F6EA58BDAD5883720B099E12B869F223FB9B18AC40E7D37C5954A55DD | |||
| 3464 | winlogon.exe | C:\Users\admin\AppData\Local\Temp\tmp8BEF.tmp | sqlite | |
MD5:D02907BE1C995E1E51571EEDB82FA281 | SHA256:2189977F6EA58BDAD5883720B099E12B869F223FB9B18AC40E7D37C5954A55DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
3
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3464 | winlogon.exe | POST | 200 | 18.196.41.122:17044 | http://siyatermi.duckdns.org:17044/ | DE | text | 212 b | malicious |
3464 | winlogon.exe | POST | 200 | 18.196.41.122:17044 | http://siyatermi.duckdns.org:17044/ | DE | text | 10.0 Kb | malicious |
3464 | winlogon.exe | POST | 200 | 18.196.41.122:17044 | http://siyatermi.duckdns.org:17044/ | DE | text | 147 b | malicious |
3464 | winlogon.exe | POST | 200 | 18.196.41.122:17044 | http://siyatermi.duckdns.org:17044/ | DE | text | 261 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3464 | winlogon.exe | 18.196.41.122:17044 | siyatermi.duckdns.org | Amazon.com, Inc. | DE | malicious |
3464 | winlogon.exe | 104.26.12.31:443 | api.ip.sb | Cloudflare Inc | US | suspicious |
3884 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
siyatermi.duckdns.org |
| malicious |
api.ip.sb |
| whitelisted |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
3464 | winlogon.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to DuckDNS Domain |
3464 | winlogon.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to DuckDNS Domain |
3464 | winlogon.exe | A Network Trojan was detected | AV TROJAN RedLine Stealer Config Download |
3464 | winlogon.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to DuckDNS Domain |
3464 | winlogon.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
5 ETPRO signatures available at the full report