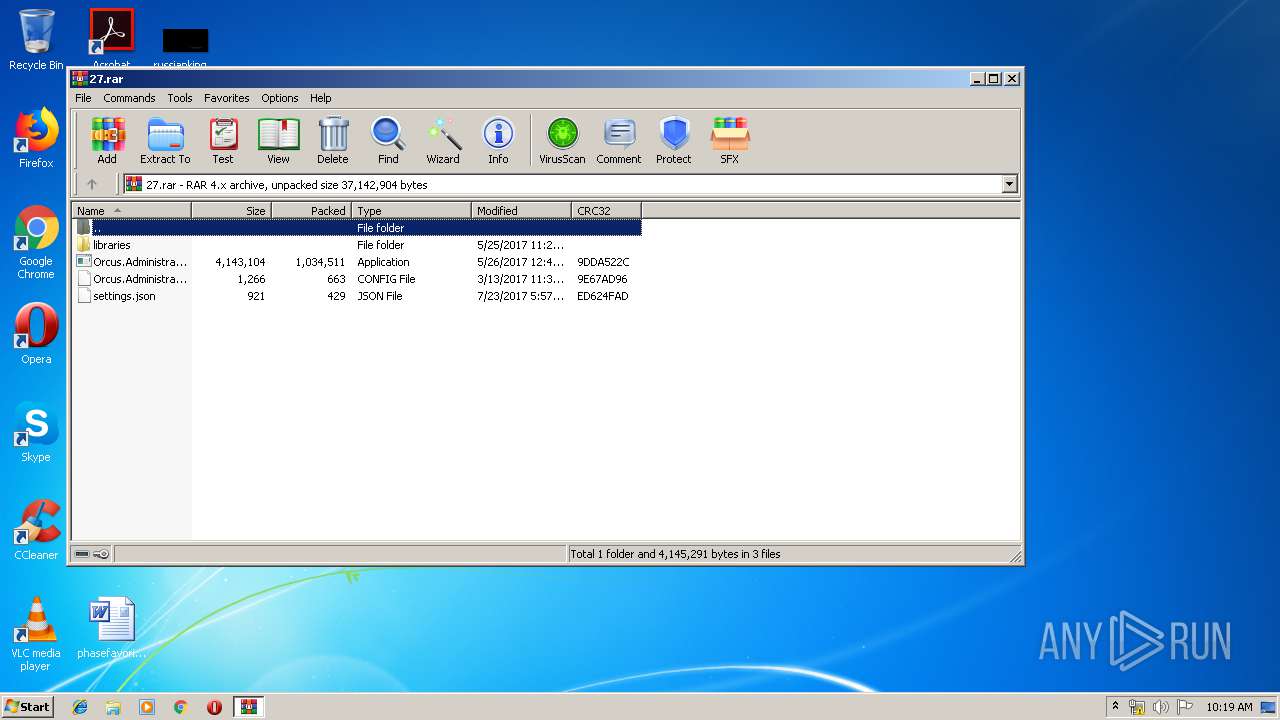
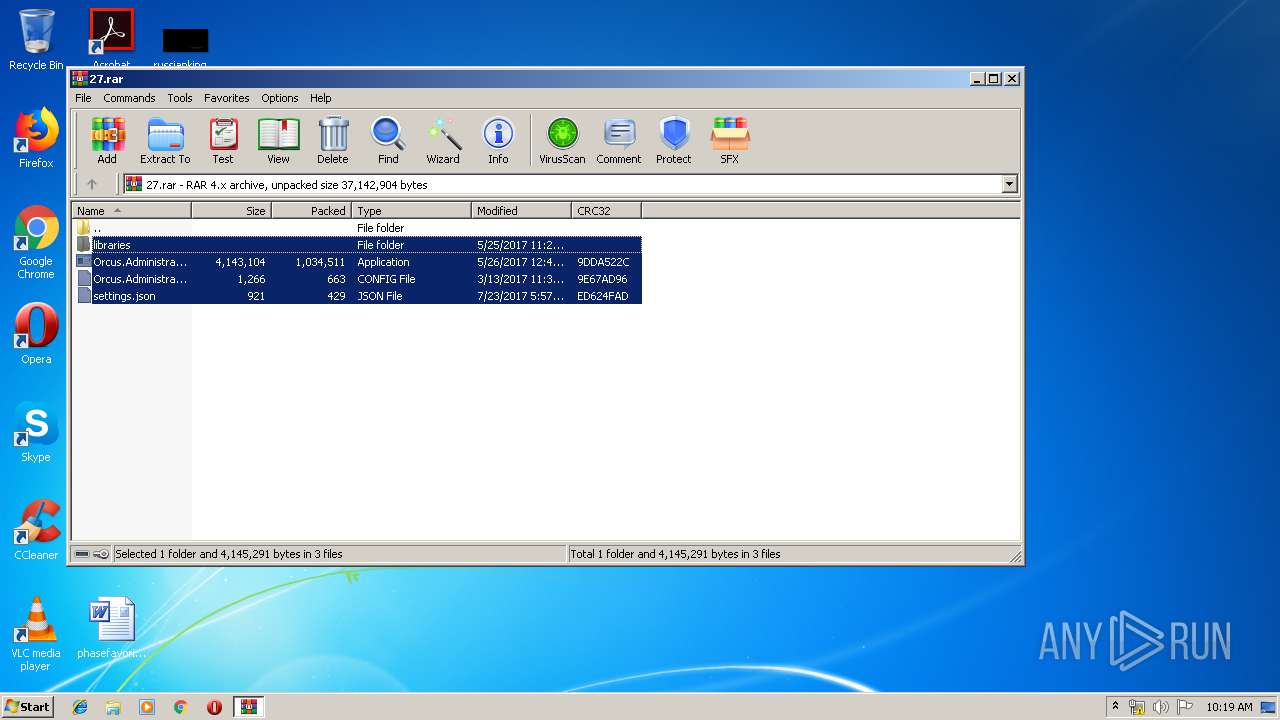
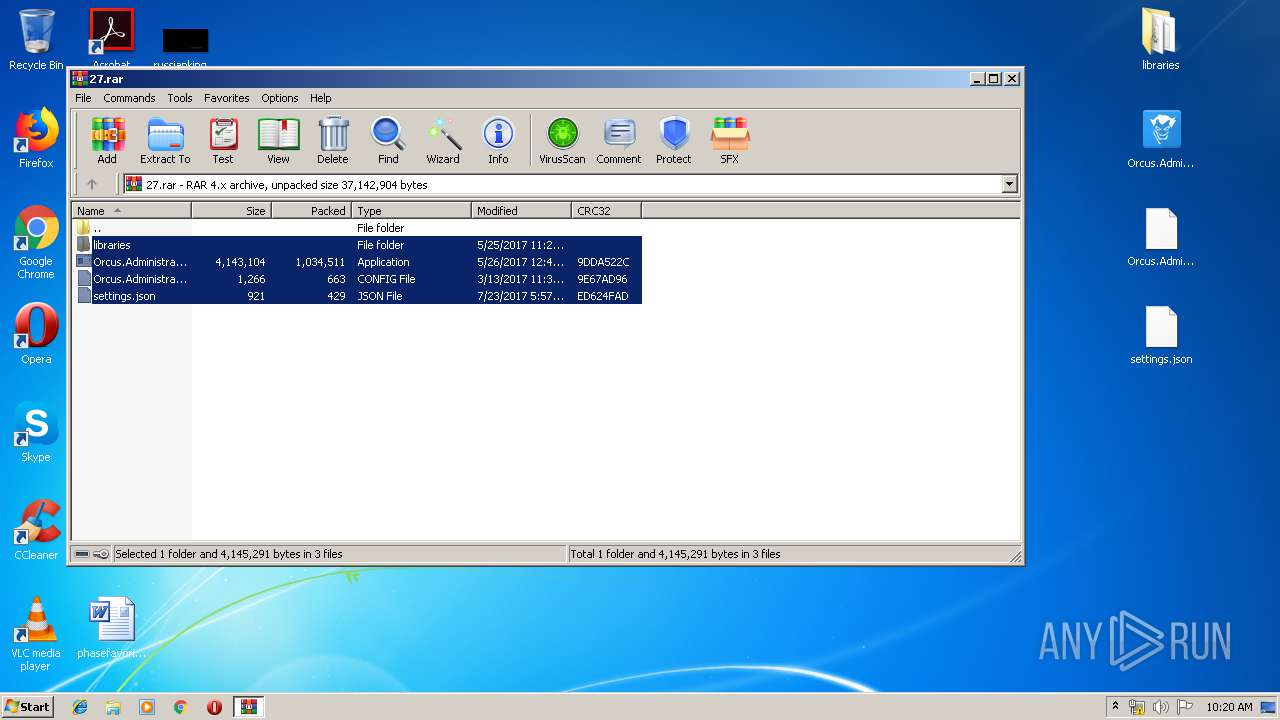
| File name: | 27.rar |
| Full analysis: | https://app.any.run/tasks/90e3798b-8880-4a1a-ab3b-8cfefd4efc94 |
| Verdict: | Malicious activity |
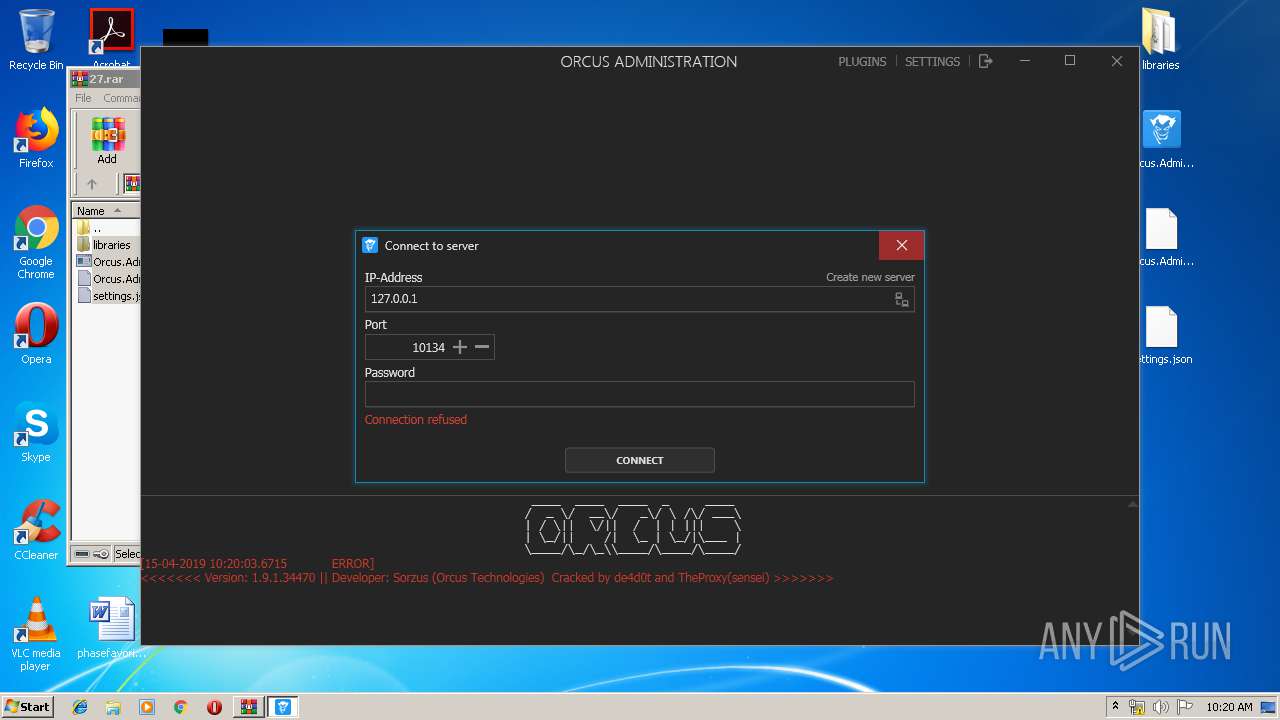
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | April 15, 2019, 09:19:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 2FF6DBB642CFA32BDDD1D516914543F7 |
| SHA1: | 80C02A3E0F007F3FD5305D86AAEFD55F35488961 |
| SHA256: | E3521204D4C41931C48E570ECEFF8C90D8E1E391C8CAEBF817DE728CD73D9BA7 |
| SSDEEP: | 98304:r13ZEnF0faxoxm5eM/u+haRQ+QwqZ9so623jL2x4Yd6Lz0O5grUyCatryXG/TTSq:r1JSoxm5z/NQRCLyo6EzY8EUwJTTSq |
MALICIOUS
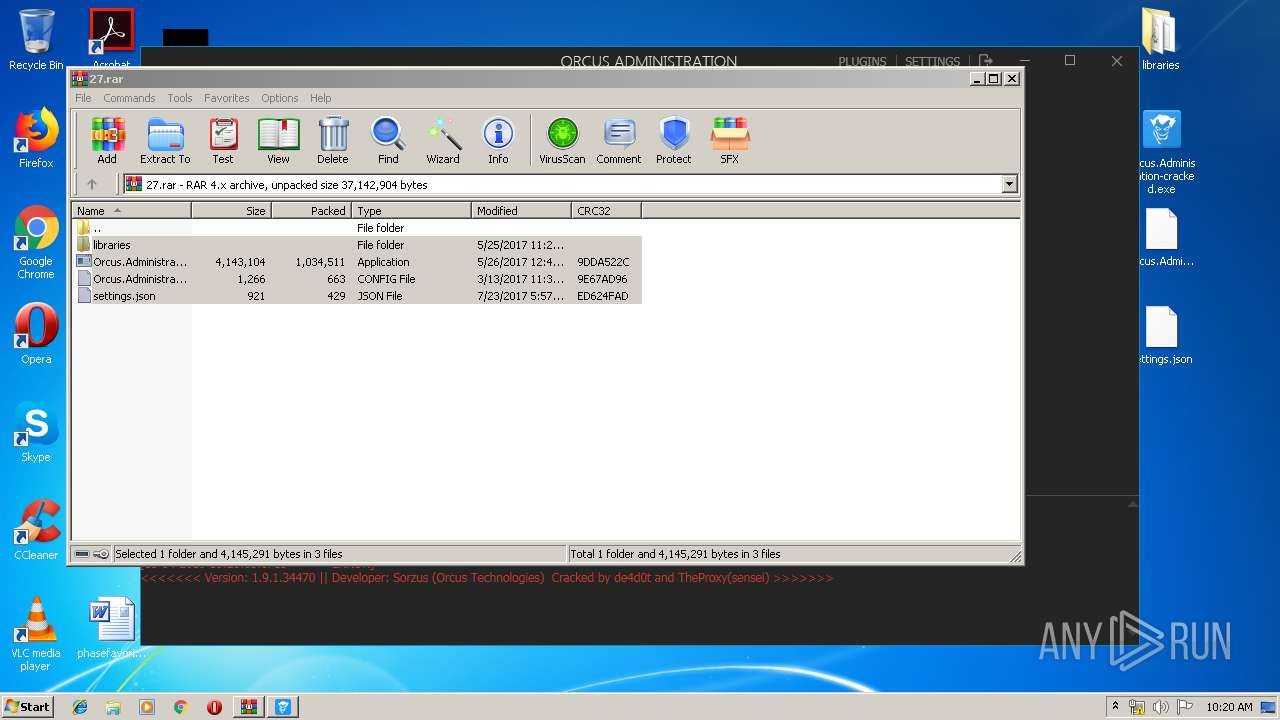
Orcus was detected
- Orcus.Administration-cracked.exe (PID: 1244)
Loads dropped or rewritten executable
- Orcus.Administration-cracked.exe (PID: 1244)
- SearchProtocolHost.exe (PID: 2944)
Application was dropped or rewritten from another process
- Orcus.Administration-cracked.exe (PID: 1244)
SUSPICIOUS
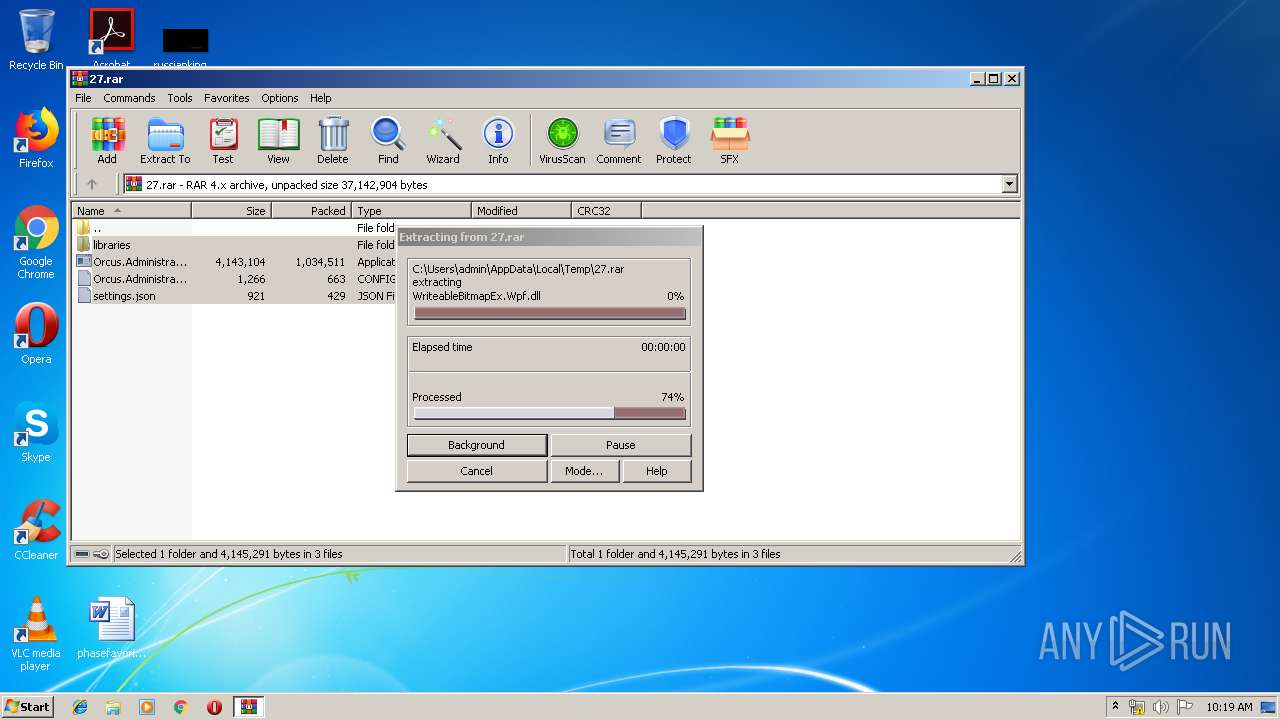
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3624)
Reads Environment values
- Orcus.Administration-cracked.exe (PID: 1244)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3624)
Reads settings of System Certificates
- Orcus.Administration-cracked.exe (PID: 1244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1034569 |
|---|---|
| UncompressedSize: | 4143104 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:05:26 12:43:14 |
| PackingMethod: | Normal |
| ArchivedFileName: | Orcus.Administration-cracked.exe |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | "C:\Users\admin\Desktop\Orcus.Administration-cracked.exe" | C:\Users\admin\Desktop\Orcus.Administration-cracked.exe | explorer.exe | ||||||||||||
User: admin Company: Orcus Technologies Integrity Level: MEDIUM Description: Orcus Administration Exit code: 0 Version: 1.9.1.0 Modules
| |||||||||||||||
| 2944 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3624 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\27.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
843
Read events
806
Write events
37
Delete events
0
Modification events
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\27.rar | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1244) Orcus.Administration-cracked.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Orcus_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1244) Orcus.Administration-cracked.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Orcus_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
48
Suspicious files
0
Text files
25
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\settings.json | text | |
MD5:98F2E3E6EE779B96279DDDC277BA6D30 | SHA256:1461AA839B4C2D0DE78BA021D1EE3210ADF69F3DD0D661ED7AE9160C7AD1BA4E | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\Orcus.Administration-cracked.exe | executable | |
MD5:CC3670F1B3E60E00B43C86D787563A44 | SHA256:9CA18641BC6B48708E4314B3F8275860AEF6B9EA16CD6230D781F0ABAA84C853 | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\de\Orcus.Plugins.resources.dll | executable | |
MD5:03258470C0C379C1EB894412FBA1F15C | SHA256:DE081D21B9D681D2E267A22CD679B215520AF8B6C7F50656915920014D1F0DE1 | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\AForge.Video.DirectShow.dll | executable | |
MD5:17ED442E8485AC3F7DC5B3C089654A61 | SHA256:666D44798D94EAFA1ED21AF79E9BC0293FFD96F863AB5D87F78BCEE9EF9FFD6B | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\Orcus.Administration-cracked.exe.config | xml | |
MD5:D689A8F25C2BE9024F4841123B3E4053 | SHA256:7383BCEFAFA33AFD801BEFED53528CF8B1F16EFF9233AC106C3297CC5D54DF1F | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\Be.Windows.Forms.HexBox.xml | xml | |
MD5:B534569D28458990C1B2F68EAFA60BC3 | SHA256:415EA2D9A22AB58E5F89ECE1CAF45FD61F2579EF0C700C990A997841F284E4E3 | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\GongSolutions.Wpf.DragDrop.dll | executable | |
MD5:21E4C0B33F44D13CDF91B4FAF828C044 | SHA256:508E1187D1A42CF9D7A2D7EAB9012FC1FD75A24B6D94D9FA636D81DC38C4FCBB | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\CSCore.xml | xml | |
MD5:8FE5E0D1F87F336FA36572F6416A112E | SHA256:DE74FF28FAC66264AB57FADC235CB6988263697EC0BF94388E6FBD7ECA4AE33F | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\GongSolutions.Wpf.DragDrop.pdb | pdb | |
MD5:4F837C9E86409823986A1ABF9C369938 | SHA256:E7317CF612E9AFB974C7C1B22502D0E10767C3A8658FFFB10D140A4876CC66BC | |||
| 3624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3624.49979\libraries\AForge.Video.dll | executable | |
MD5:0BD34AA29C7EA4181900797395A6DA78 | SHA256:BAFA6ED04CA2782270074127A0498DDE022C2A9F4096C6BB2B8E3C08BB3D404D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
3
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1244 | Orcus.Administration-cracked.exe | 198.54.117.197:443 | www.orcus.one | Namecheap, Inc. | US | malicious |
1244 | Orcus.Administration-cracked.exe | 40.85.179.199:443 | collector.exceptionless.io | Microsoft Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
orcus.pw |
| malicious |
www.orcus.one |
| malicious |
collector.exceptionless.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |