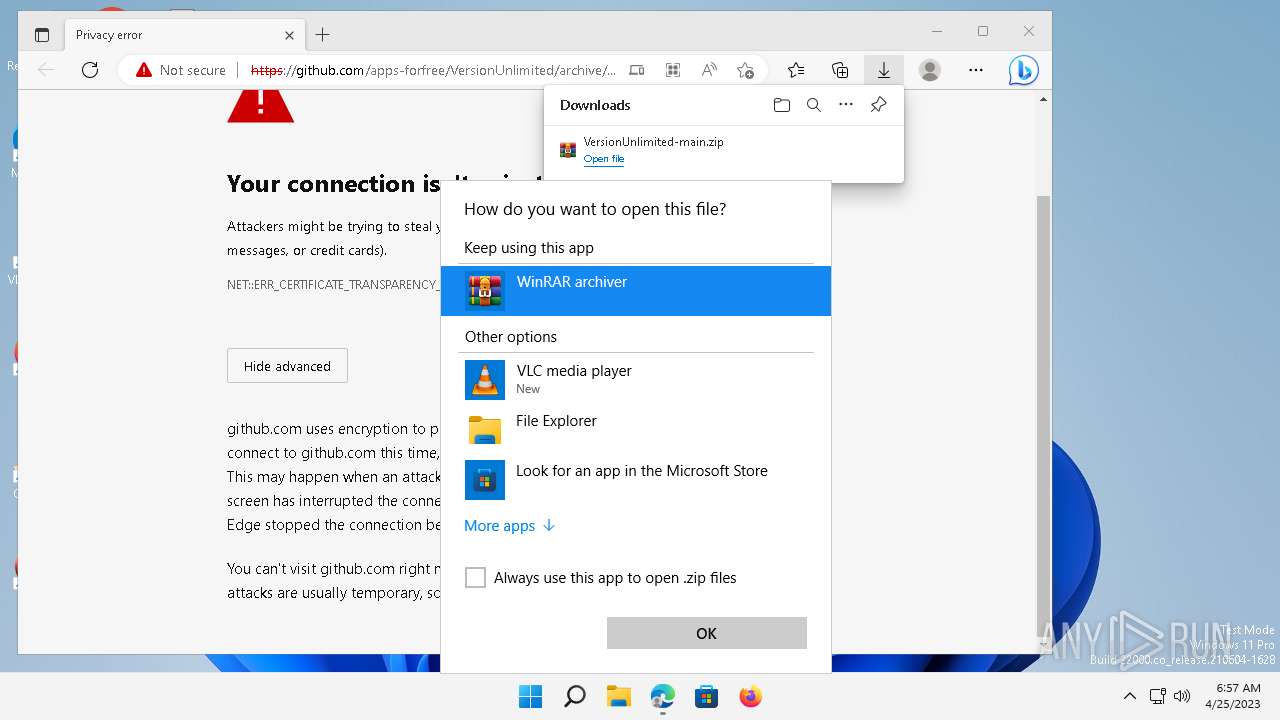
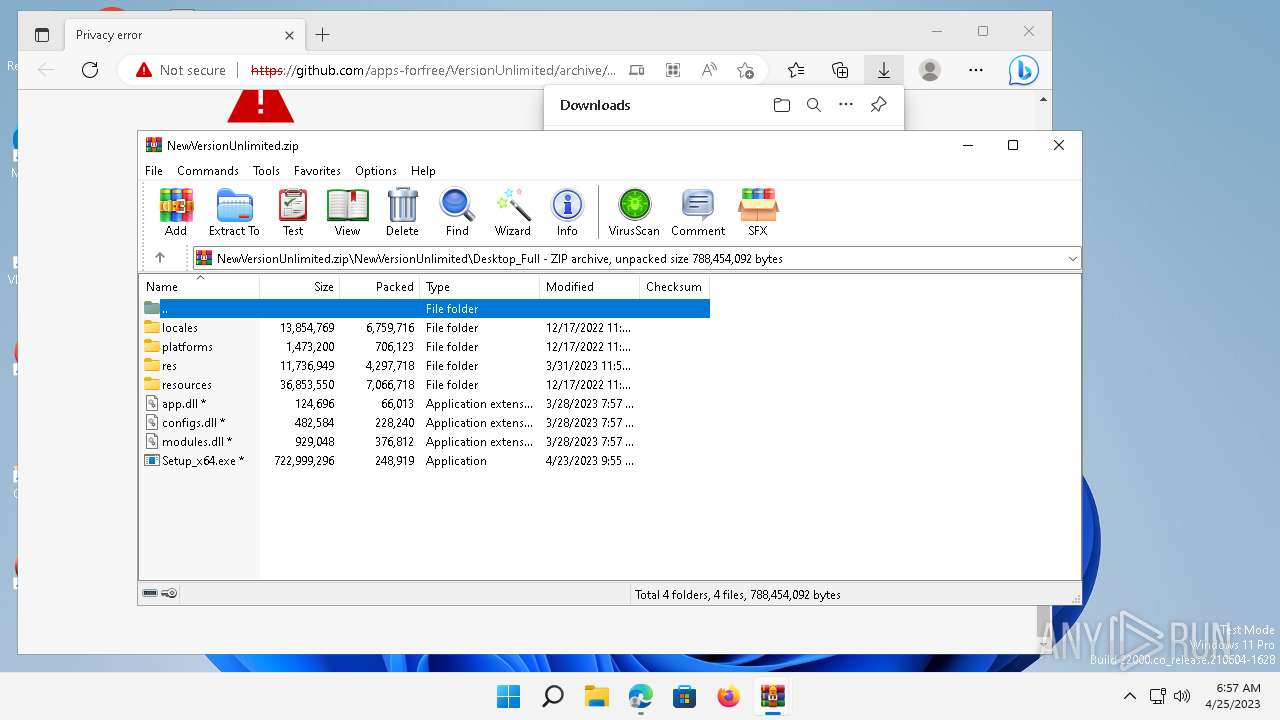
| URL: | https://github.com/apps-forfree/VersionUnlimited/archive/refs/heads/main.zip |
| Full analysis: | https://app.any.run/tasks/0e3de903-3cc9-410b-a504-622dc395aea6 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 25, 2023, 13:56:35 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3BC93975CCCE5A29428A0207C3FC90F1 |
| SHA1: | 47257E57246A67EE98ED862D6365BAC69E974DD1 |
| SHA256: | E2ADDEBE1811F1BBDF447DC53F76F67CBF9084AE42AC665ED01E21F9495756AE |
| SSDEEP: | 3:N8tEd0A5dKkONS4RSLNLc:2ui6bOM4ULN4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- explorer.exe (PID: 4036)
Reads the Internet Settings
- OpenWith.exe (PID: 7568)
- explorer.exe (PID: 4036)
Reads settings of System Certificates
- explorer.exe (PID: 4036)
Application launched itself
- WinRAR.exe (PID: 5348)
INFO
Checks proxy server information
- explorer.exe (PID: 4036)
The process checks LSA protection
- OpenWith.exe (PID: 7568)
- explorer.exe (PID: 4036)
Application launched itself
- msedge.exe (PID: 2180)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7712)
The process uses the downloaded file
- OpenWith.exe (PID: 7568)
- WinRAR.exe (PID: 5348)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7712)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 7712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
145
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://github.com/apps-forfree/VersionUnlimited/archive/refs/heads/main.zip" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 4036 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.22000.184 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5348 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\VersionUnlimited-main.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=111.0.5563.149 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=111.0.1661.62 --initial-client-data=0x11c,0x120,0x124,0xf8,0x130,0x7ff8fc98b5f8,0x7ff8fc98b608,0x7ff8fc98b618 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 7568 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7712 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa5348.2835\NewVersionUnlimited.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
11 586
Read events
11 468
Write events
116
Delete events
2
Modification events
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000B0000001C000000ED281000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF809BEF9EA60BD90100000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000710100000A030000DCAE6901540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000160260 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000B0000001D000000ED281000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF809BEF9EA60BD90100000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000710100000B030000DCAE6901540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7568) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
8
Suspicious files
16
Text files
148
Unknown types
112
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:CA31928FE184CD410D247D4F47FBC147 | SHA256:342C97A68EF8B7C9A449F67F7C60CC313FBCC02D12FB150DBEA166754F9D52AE | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:84418143D4EA6C829486C2E0B588D9BB | SHA256:94941FD0417BF809EADC4CDA6234B1C07E8AA8403D2E264858A2747CFBFF02E3 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\5f7b5f1e01b83767.automaticDestinations-ms | binary | |
MD5:9D7DEB8AE92EA0259085BBEC44671E2A | SHA256:183BB1B453A0FDDFEBAB8CCC0F7F1ED9BB97AF5B42D29A55911C4C6E16790BE2 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Downloads.lnk | lnk | |
MD5:5983E6586731A4CD86FDB5D4C7E75859 | SHA256:808B2FA90890129DC4B9133174E706B0C9AE0A120AFF1DD47EDD343D69A9AE37 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\VersionUnlimited-main.zip.lnk | lnk | |
MD5:6BD15268DF74C55BF60A41DB8F160B5C | SHA256:34CFE0A76226266F1B57D18FF476AEC0B4CDB4208F065C54711D93E8D47B0CF5 | |||
| 2180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:F08531363BD004D9DA5B6B776D25F336 | SHA256:AC046D56F0CAF974B8A21DB0D7EA48D803A7B31992ECC58397F6C4FDBF869396 | |||
| 7712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7712.3201\NewVersionUnlimited\Desktop_Full\locales\da.pak | mmw | |
MD5:FE10A4CE457F1EA61D532AED7536D168 | SHA256:08A1FD0B3A965971AF996E357409416EF2AA5BB15B62EC4A89A597BA7B519DB9 | |||
| 7712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7712.3201\NewVersionUnlimited\Desktop_Full\app.dll | executable | |
MD5:768A1C4E4FC28A2C8ADDD11E70F824A4 | SHA256:F1D56CDFC9C7761B3FD1CD7DC9DD98C6C0494FC525D970C4D8DF1E1B32CCC9BE | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\46f433176bc0b3d2.automaticDestinations-ms | automaticdestinations-ms | |
MD5:461F462AB229084F0A8A1B836A698D5C | SHA256:B5EFBD396B2334767A3FC5F80018559070379B6D04AE2C92610A4178282437B2 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
52
DNS requests
44
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ace3142296cb0c59 | US | — | — | whitelisted |
4536 | msedge.exe | GET | 204 | 13.107.6.158:80 | http://edge-http.microsoft.com/captiveportal/generate_204 | US | — | — | whitelisted |
4536 | msedge.exe | GET | 204 | 13.107.6.158:80 | http://edge-http.microsoft.com/captiveportal/generate_204 | US | — | — | whitelisted |
4000 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
— | — | POST | 200 | 185.99.132.51:80 | http://185.99.132.51/c2sock | NZ | text | 5 b | malicious |
— | — | POST | 200 | 185.99.132.51:80 | http://185.99.132.51/c2sock | NZ | text | 5 b | malicious |
— | — | POST | 200 | 185.99.132.51:80 | http://185.99.132.51/c2sock | NZ | text | 5 b | malicious |
— | — | POST | 200 | 185.99.132.51:80 | http://185.99.132.51/c2sock | NZ | text | 5 b | malicious |
1480 | svchost.exe | GET | 200 | 13.107.4.52:80 | http://www.msftconnecttest.com/connecttest.txt | US | text | 22 b | whitelisted |
4036 | explorer.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7df80a6f126af89c | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4536 | msedge.exe | 140.82.121.3:443 | — | GITHUB | US | suspicious |
4000 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | suspicious |
4000 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
4536 | msedge.exe | 20.8.16.139:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4536 | msedge.exe | 13.107.22.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4536 | msedge.exe | 13.107.6.158:80 | edge-http.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6224 | svchost.exe | 23.35.236.109:443 | fs.microsoft.com | AKAMAI-AS | DE | malicious |
4036 | explorer.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1480 | svchost.exe | 13.107.4.52:80 | www.msftconnecttest.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-http.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
www.msftconnecttest.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
2 ETPRO signatures available at the full report