| File name: | random.exe |
| Full analysis: | https://app.any.run/tasks/d81604be-d942-4e7e-b4bc-48b29f8c809f |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 18, 2024, 02:39:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 77DDB7264BCCD00910D07ADE2F33A90D |
| SHA1: | 26E5256854040A0DCADA7746CE9479B9755B12DD |
| SHA256: | E2A01FD1E2DC81C6EBFBF79BFB243932CBA16C163DBF48A14DBBEAAA0F151CBD |
| SSDEEP: | 98304:M2KeDTqVgey8C+mwa4JHSNRa3x+ATxIC4Esu3A5sWKRimBTNFQofxKuxHJi4befJ:VQu |
MALICIOUS
Drops the executable file immediately after the start
- random.exe (PID: 3968)
- axplong.exe (PID: 2104)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- b2c2c1.exe (PID: 1888)
Connects to the CnC server
- axplong.exe (PID: 2104)
- redline123123.exe (PID: 588)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
AMADEY has been detected (SURICATA)
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
- Dctooux.exe (PID: 2876)
AMADEY has been detected (YARA)
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 2504)
- Hkbsse.exe (PID: 992)
REDLINE has been detected (SURICATA)
- redline123123.exe (PID: 588)
METASTEALER has been detected (SURICATA)
- redline123123.exe (PID: 588)
Amadey has been detected
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
Actions looks like stealing of personal data
- redline123123.exe (PID: 588)
REDLINE has been detected (YARA)
- redline123123.exe (PID: 588)
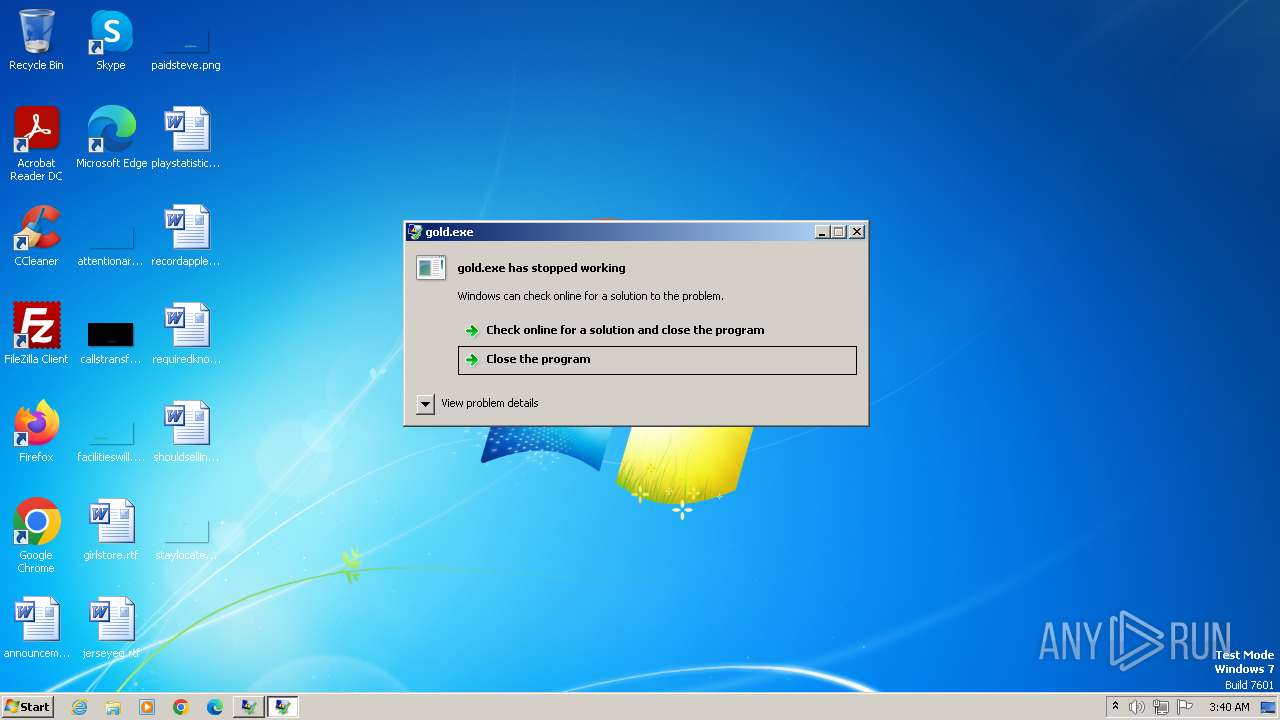
- gold.exe (PID: 284)
- upd.exe (PID: 1604)
Steals credentials from Web Browsers
- redline123123.exe (PID: 588)
SUSPICIOUS
Reads security settings of Internet Explorer
- random.exe (PID: 3968)
- axplong.exe (PID: 2104)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- b2c2c1.exe (PID: 1888)
- Dctooux.exe (PID: 2876)
Starts itself from another location
- random.exe (PID: 3968)
- NewLatest.exe (PID: 2020)
- bin.exe (PID: 2612)
- b2c2c1.exe (PID: 1888)
Reads the BIOS version
- axplong.exe (PID: 2104)
- random.exe (PID: 3968)
Reads the Internet Settings
- axplong.exe (PID: 2104)
- random.exe (PID: 3968)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- redline123123.exe (PID: 588)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- Dctooux.exe (PID: 2876)
- b2c2c1.exe (PID: 1888)
Potential Corporate Privacy Violation
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
Contacting a server suspected of hosting an CnC
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
- Dctooux.exe (PID: 2876)
Connects to the server without a host name
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
Executable content was dropped or overwritten
- axplong.exe (PID: 2104)
- random.exe (PID: 3968)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- b2c2c1.exe (PID: 1888)
Process requests binary or script from the Internet
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
Connects to unusual port
- redline123123.exe (PID: 588)
Process drops legitimate windows executable
- axplong.exe (PID: 2104)
Reads browser cookies
- redline123123.exe (PID: 588)
The process connected to a server suspected of theft
- redline123123.exe (PID: 588)
Searches for installed software
- redline123123.exe (PID: 588)
INFO
Checks supported languages
- random.exe (PID: 3968)
- axplong.exe (PID: 2104)
- wmpnscfg.exe (PID: 1056)
- redline123123.exe (PID: 588)
- drivermanager.exe (PID: 1928)
- upd.exe (PID: 1604)
- MSBuild.exe (PID: 1940)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- b2c2c1.exe (PID: 1888)
- bin.exe (PID: 2612)
- legs.exe (PID: 2764)
- Hkbsse.exe (PID: 2504)
- Dctooux.exe (PID: 2876)
- lummac2.exe (PID: 2008)
- gold.exe (PID: 284)
Reads the machine GUID from the registry
- random.exe (PID: 3968)
- axplong.exe (PID: 2104)
- redline123123.exe (PID: 588)
- drivermanager.exe (PID: 1928)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- b2c2c1.exe (PID: 1888)
- Dctooux.exe (PID: 2876)
Reads the computer name
- axplong.exe (PID: 2104)
- wmpnscfg.exe (PID: 1056)
- redline123123.exe (PID: 588)
- drivermanager.exe (PID: 1928)
- random.exe (PID: 3968)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- b2c2c1.exe (PID: 1888)
- Dctooux.exe (PID: 2876)
Create files in a temporary directory
- axplong.exe (PID: 2104)
- random.exe (PID: 3968)
- NewLatest.exe (PID: 2020)
- Hkbsse.exe (PID: 992)
- redline123123.exe (PID: 588)
- bin.exe (PID: 2612)
- Hkbsse.exe (PID: 2504)
- b2c2c1.exe (PID: 1888)
- Dctooux.exe (PID: 2876)
Checks proxy server information
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
- Dctooux.exe (PID: 2876)
Creates files or folders in the user directory
- axplong.exe (PID: 2104)
- Hkbsse.exe (PID: 992)
- Hkbsse.exe (PID: 2504)
Manual execution by a user
- wmpnscfg.exe (PID: 1056)
Reads Environment values
- redline123123.exe (PID: 588)
Disables trace logs
- redline123123.exe (PID: 588)
Reads product name
- redline123123.exe (PID: 588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(2104) axplong.exe
C277.91.77.81
URLhttp://77.91.77.81/Kiru9gu/index.php
Version4.30
Options
Drop directory8254624243
Drop nameaxplong.exe
Strings (113)Main
cmd /C RMDIR /s/q
/Plugins/
ESET
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
ProductName
/k
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
vs:
4.30
<d>
exe
8254624243
ComputerName
2019
id:
" && ren
ar:
:::
Sophos
77.91.77.81
sd:
#
Bitdefender
Panda Security
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
Content-Disposition: form-data; name="data"; filename="
rb
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
=
Avira
%USERPROFILE%
og:
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e0
axplong.exe
random
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
/Kiru9gu/index.php
Comodo
AVAST Software
wb
\
AVG
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
ProgramData\
CurrentBuild
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
<c>
dm:
e1
http://
--
%-lu
.jpg
Kaspersky Lab
2022
DefaultSettings.XResolution
(PID) Process(2504) Hkbsse.exe
C2o7labs.top
URLhttp://o7labs.top/visual/skins/index.php
Version4.30
Options
Drop directory5641a448ac
Drop nameHkbsse.exe
Strings (113)Main
cmd /C RMDIR /s/q
/Plugins/
ESET
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
ProductName
/k
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
vs:
4.30
<d>
exe
ComputerName
2019
id:
" && ren
ar:
:::
Sophos
sd:
#
Bitdefender
Panda Security
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
Content-Disposition: form-data; name="data"; filename="
rb
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
=
Avira
%USERPROFILE%
og:
o7labs.top
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e0
random
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
5641a448ac
Comodo
AVAST Software
wb
\
AVG
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
/visual/skins/index.php
ProgramData\
CurrentBuild
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
<c>
dm:
e1
Hkbsse.exe
http://
--
%-lu
.jpg
Kaspersky Lab
2022
DefaultSettings.XResolution
(PID) Process(992) Hkbsse.exe
C2185.172.128.116
URLhttp://185.172.128.116/Mb3GvQs8/index.php
Version4.30
Options
Drop directoryb66a8ae076
Drop nameHkbsse.exe
Strings (113)Main
cmd /C RMDIR /s/q
/Plugins/
ESET
185.172.128.116
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
ProductName
/k
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
vs:
4.30
<d>
exe
ComputerName
2019
id:
" && ren
ar:
:::
Sophos
sd:
#
Bitdefender
Panda Security
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
Content-Disposition: form-data; name="data"; filename="
rb
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
=
Avira
%USERPROFILE%
og:
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/Mb3GvQs8/index.php
e0
random
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
Comodo
AVAST Software
wb
\
AVG
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
ProgramData\
CurrentBuild
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
<c>
dm:
b66a8ae076
e1
Hkbsse.exe
http://
--
%-lu
.jpg
Kaspersky Lab
2022
DefaultSettings.XResolution
RedLine
(PID) Process(588) redline123123.exe
C2 (1)185.215.113.67:40960
Botnetnewbild
Options
ErrorMessage
Keys
XorOsteogeny
(PID) Process(1604) upd.exe
C2 (1)185.172.128.33:8970
Botnet@LOGSCLOUDYT_BOT
Options
ErrorMessage
Keys
XorLevins
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:04 08:24:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 320512 |
| InitializedDataSize: | 116224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4c2000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
56
Monitored processes
16
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Users\admin\AppData\Local\Temp\1000035001\gold.exe" | C:\Users\admin\AppData\Local\Temp\1000035001\gold.exe | axplong.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 588 | "C:\Users\admin\AppData\Local\Temp\1000007001\redline123123.exe" | C:\Users\admin\AppData\Local\Temp\1000007001\redline123123.exe | axplong.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XHP Exit code: 0 Version: 12.9.1.22 Modules
RedLine(PID) Process(588) redline123123.exe C2 (1)185.215.113.67:40960 Botnetnewbild Options ErrorMessage Keys XorOsteogeny | |||||||||||||||
| 992 | "C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe" | C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe | NewLatest.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
Amadey(PID) Process(992) Hkbsse.exe C2185.172.128.116 URLhttp://185.172.128.116/Mb3GvQs8/index.php Version4.30 Options Drop directoryb66a8ae076 Drop nameHkbsse.exe Strings (113)Main cmd /C RMDIR /s/q /Plugins/ ESET 185.172.128.116 " && timeout 1 && del && Exit" lv: av: SOFTWARE\Microsoft\Windows NT\CurrentVersion st=s Doctor Web https:// Norton Content-Type: application/x-www-form-urlencoded ProductName /k Content-Type: multipart/form-data; boundary=---- ?scr=1 cred.dll|clip.dll| vs: 4.30 <d> exe ComputerName 2019 id: " && ren ar: ::: Sophos sd: # Bitdefender Panda Security 2016 abcdefghijklmnopqrstuvwxyz0123456789-_ -unicode- Programs Startup d1 VideoID bi: && S-%lu- Content-Disposition: form-data; name="data"; filename=" rb Rem \App rundll32.exe SYSTEM\ControlSet001\Services\BasicDisplay\Video ------ \0000 SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ = Avira %USERPROFILE% og: un: pc: WinDefender r= +++ SOFTWARE\Microsoft\Windows\CurrentVersion\Run /Mb3GvQs8/index.php e0 random | &unit= DefaultSettings.YResolution GetNativeSystemInfo 360TotalSecurity -%lu SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce ps1 ------ Comodo AVAST Software wb \ AVG GET -executionpolicy remotesigned -File " Powershell.exe "
Content-Type: application/octet-stream shutdown -s -t 0 kernel32.dll shell32.dll dll "taskkill /f /im " ProgramData\ CurrentBuild cmd SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders POST 0123456789 os: SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders " rundll32 SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName <c> dm: b66a8ae076 e1 Hkbsse.exe http:// -- %-lu .jpg Kaspersky Lab 2022 DefaultSettings.XResolution | |||||||||||||||
| 1056 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | "C:\Users\admin\AppData\Local\Temp\1000008001\upd.exe" | C:\Users\admin\AppData\Local\Temp\1000008001\upd.exe | axplong.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
RedLine(PID) Process(1604) upd.exe C2 (1)185.172.128.33:8970 Botnet@LOGSCLOUDYT_BOT Options ErrorMessage Keys XorLevins | |||||||||||||||
| 1888 | "C:\Users\admin\AppData\Local\Temp\1000003001\b2c2c1.exe" | C:\Users\admin\AppData\Local\Temp\1000003001\b2c2c1.exe | Hkbsse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\AppData\Local\Temp\1000063001\drivermanager.exe" | C:\Users\admin\AppData\Local\Temp\1000063001\drivermanager.exe | — | axplong.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WTTLogger_COM_GitEnlistment(sscpbld01) Exit code: 0 Version: 2.7.3483.0 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1940 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | drivermanager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 2008 | "C:\Users\admin\AppData\Local\Temp\1000047001\lummac2.exe" | C:\Users\admin\AppData\Local\Temp\1000047001\lummac2.exe | — | axplong.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\AppData\Local\Temp\1000064001\NewLatest.exe" | C:\Users\admin\AppData\Local\Temp\1000064001\NewLatest.exe | axplong.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
21 680
Read events
21 463
Write events
178
Delete events
39
Modification events
| (PID) Process: | (3968) random.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3968) random.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3968) random.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3968) random.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2104) axplong.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2104) axplong.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2104) axplong.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2104) axplong.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2104) axplong.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (2104) axplong.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
Executable files
32
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | random.exe | C:\Users\admin\AppData\Local\Temp\8254624243\axplong.exe | executable | |
MD5:77DDB7264BCCD00910D07ADE2F33A90D | SHA256:E2A01FD1E2DC81C6EBFBF79BFB243932CBA16C163DBF48A14DBBEAAA0F151CBD | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\judit[1].exe | executable | |
MD5:C09FF1273B09CB1F9C7698ED147BF22E | SHA256:BF8CE6BB537881386FACFE6C1F9003812B985CBC4B9E9ADDD39E102449868D92 | |||
| 3968 | random.exe | C:\Windows\Tasks\axplong.job | binary | |
MD5:AA2E05A705CED4F59452DC83F4C21C6B | SHA256:29741D671B274F7189B31B53CDCE348056284C48C3FDE5506929C6E1D2CD77AD | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\setup222[1].exe | executable | |
MD5:8677376C509F0C66D1F02C6B66D7EF90 | SHA256:F7AFAC39D2754AC953BF129EE094C8B092E349CDF35F1BA23C2C76A0229F9E96 | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Temp\1000007001\redline123123.exe | executable | |
MD5:0EFD5136528869A8EA1A37C5059D706E | SHA256:7C21C1F3063BA963818542036A50F62AC7494AD422E7088897B55C61306EC74E | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\upd[1].exe | executable | |
MD5:E8A7D0C6DEDCE0D4A403908A29273D43 | SHA256:672F24842AEB72D7BD8D64E78AABA5F3A953409CE21CFE97D3A80E7EF67F232A | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Temp\1000025001\setup222.exe | executable | |
MD5:8677376C509F0C66D1F02C6B66D7EF90 | SHA256:F7AFAC39D2754AC953BF129EE094C8B092E349CDF35F1BA23C2C76A0229F9E96 | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Temp\1000047001\lummac2.exe | executable | |
MD5:6E3D83935C7A0810F75DFA9BADC3F199 | SHA256:DC4F0A8E3D12C98EAC09A42BD976579CCC1851056D9DE447495E8BE7519760ED | |||
| 2020 | NewLatest.exe | C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe | executable | |
MD5:07101CAC5B9477BA636CD8CA7B9932CB | SHA256:488385CD54D14790B03FA7C7DC997EBEA3F7B2A8499E5927EB437A3791102A77 | |||
| 2104 | axplong.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\lummac2[1].exe | executable | |
MD5:6E3D83935C7A0810F75DFA9BADC3F199 | SHA256:DC4F0A8E3D12C98EAC09A42BD976579CCC1851056D9DE447495E8BE7519760ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
24
DNS requests
21
Threats
102
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
2104 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
2104 | axplong.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/judit.exe | unknown | — | — | unknown |
2104 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
2104 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
2104 | axplong.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/upd.exe | unknown | — | — | unknown |
2104 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
2104 | axplong.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/gold.exe | unknown | — | — | unknown |
2104 | axplong.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/setup222.exe | unknown | — | — | unknown |
2104 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | axplong.exe | 77.91.77.81:80 | — | Foton Telecom CJSC | RU | malicious |
588 | redline123123.exe | 185.215.113.67:40960 | — | 1337team Limited | SC | malicious |
2104 | axplong.exe | 185.172.128.116:80 | — | OOO Nadym Svyaz Service | RU | malicious |
992 | Hkbsse.exe | 185.172.128.116:80 | — | OOO Nadym Svyaz Service | RU | malicious |
992 | Hkbsse.exe | 185.172.128.19:80 | — | OOO Nadym Svyaz Service | RU | malicious |
588 | redline123123.exe | 49.13.77.253:443 | kmsandallapp.ru | Hetzner Online GmbH | DE | unknown |
2104 | axplong.exe | 91.92.240.234:80 | o7labs.top | Natskovi & Sie Ltd. | BG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kmsandallapp.ru |
| malicious |
o7labs.top |
| unknown |
osdhs.in.ne |
| unknown |
jkshb.su |
| malicious |
greendag.ru |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2104 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2104 | axplong.exe | Misc activity | ET INFO Packed Executable Download |
2104 | axplong.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2104 | axplong.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
2104 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2104 | axplong.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2104 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2104 | axplong.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M2 |
2104 | axplong.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2104 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5 ETPRO signatures available at the full report
Process | Message |
|---|---|
random.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|