| download: | index.html |
| Full analysis: | https://app.any.run/tasks/8aa541e9-7a0f-4570-9d43-53d22bb81726 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | October 20, 2020, 06:50:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | D3BAFC03BF6529D04E7F9AC0DD3AED49 |
| SHA1: | 83DF1527B8EF69CC0EE9D1A4F4F9CEFA2FBCC68D |
| SHA256: | E27E5FD4EBD54568F636C69891546DCC59A3F4136FDFCCACA3009533389B682B |
| SSDEEP: | 1536:kdgOiAEFgfRMIEIIUIwISXj9xWn0K6DmQWNwO8ZGqJtlBDwhard:AHHZVrd |
MALICIOUS
MINER was detected
- chrome.exe (PID: 2248)
SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 964)
Manual execution by user
- chrome.exe (PID: 2396)
Reads the hosts file
- chrome.exe (PID: 2396)
- chrome.exe (PID: 2248)
Application launched itself
- iexplore.exe (PID: 964)
- chrome.exe (PID: 2396)
Reads internet explorer settings
- iexplore.exe (PID: 2460)
Reads settings of System Certificates
- chrome.exe (PID: 2248)
Changes settings of System certificates
- chrome.exe (PID: 2248)
Reads Internet Cache Settings
- iexplore.exe (PID: 964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| ContentType: | text/html; charset=utf-8 |
|---|---|
| HTTPEquivXUACompatible: | IE=edge,chrome=1 |
| CacheControl: | no-cache |
| viewport: | width=device-width, initial-scale=1.0, user-scalable=no, minimum-scale=1.0, maximum-scale=1.0 |
| HandheldFriendly: | |
| formatDetection: | address=no |
| csrfToken: | 97bc592b27a9ada2d9a4bb418ed0ebed |
| csrfParam: | csrf_token |
| Title: | Новости дня в России и мире — РБК |
| Description: | Последние новости России и мира на РБК. «РосБизнесКонсалтинг» — ведущая российская компания, работающая в сферах масс-медиа и информационных технологий. Самые свежие новости, главные темы дня в политике, экономике, бизнесе и жизни. |
| Copyright: | «РосБизнесКонсалтинг» |
| twitterSite: | @ru_rbc |
| twitterCreator: | @ru_rbc |
| twitterTitle: | РБК – новости в реальном времени |
| twitterDescription: | Главные новости политики, экономики и бизнеса, комментарии аналитиков, финансовые данные с российских и мировых биржевых систем на сайте rbc.ru. |
| twitterImage: | РБК – новости в реальном времени |
| Keywords: | новости, доллар, политика, курс, акции, облигации, нефть, рубль, евро, финансы, экономика, банк, кредит, вексель, информация, фондовый, инвестиционный, рынок, недвижимость, валюта, эмитент, комментарии, аналитика, продаж/продажа, цена, компания, товары, исследование, прогноз, индекс, рейтинг, биржа, семинар, фондовый, ПИФ, доходность, IPO, паевой |
| ReplyTo: | webmaster@rbc.ru |
| twitterCard: | summary |
| msapplicationTileColor: | #ffffff |
| msapplicationTileImage: | //s.rbk.ru/v10_rbcnews_static/common/common-10.4.19/images/mstile-144x144.png |
| msapplicationSquare70x70logo: | //s.rbk.ru/v10_rbcnews_static/common/common-10.4.19/images/mstile-70x70.png |
| msapplicationSquare150x150logo: | //s.rbk.ru/v10_rbcnews_static/common/common-10.4.19/images/mstile-150x150.png |
| msapplicationSquare310x310logo: | //s.rbk.ru/v10_rbcnews_static/common/common-10.4.19/images/mstile-310x310.png |
| msapplicationWide310x150logo: | //s.rbk.ru/v10_rbcnews_static/common/common-10.4.19/images/mstile-310x150.png |
| appleItunesApp: | app-id=483524731 |
| themeColor: | #11BB88 |
Total processes
56
Monitored processes
20
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11597373328986949396 --mojo-platform-channel-handle=3468 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 964 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11884394910118704899 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=11125041211027498886 --mojo-platform-channel-handle=2628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=294968050663028686 --mojo-platform-channel-handle=500 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4583677687680254058 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2520 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1940 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=7954858671046769657 --mojo-platform-channel-handle=1632 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,16547744353758978579,976638741725569956,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=7085176789281765248 --mojo-platform-channel-handle=1052 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 041
Read events
889
Write events
147
Delete events
5
Modification events
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1827401156 | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30844589 | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
46
Text files
109
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC71DA450A6113E34.TMP | — | |
MD5:— | SHA256:— | |||
| 964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF34D7377D98013E16.TMP | — | |
MD5:— | SHA256:— | |||
| 964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1DFDA1C6303E4478.TMP | — | |
MD5:— | SHA256:— | |||
| 964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA2100FA3A0B26965.TMP | — | |
MD5:— | SHA256:— | |||
| 964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{98A62629-12A0-11EB-B41E-12A9866C77DE}.dat | — | |
MD5:— | SHA256:— | |||
| 964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCB6AEBB62B9B27EA.TMP | — | |
MD5:— | SHA256:— | |||
| 2396 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F8E88E1-95C.pma | — | |
MD5:— | SHA256:— | |||
| 2396 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\819f70a2-328a-4ae2-bac4-44957f8a4884.tmp | — | |
MD5:— | SHA256:— | |||
| 2396 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
49
DNS requests
33
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
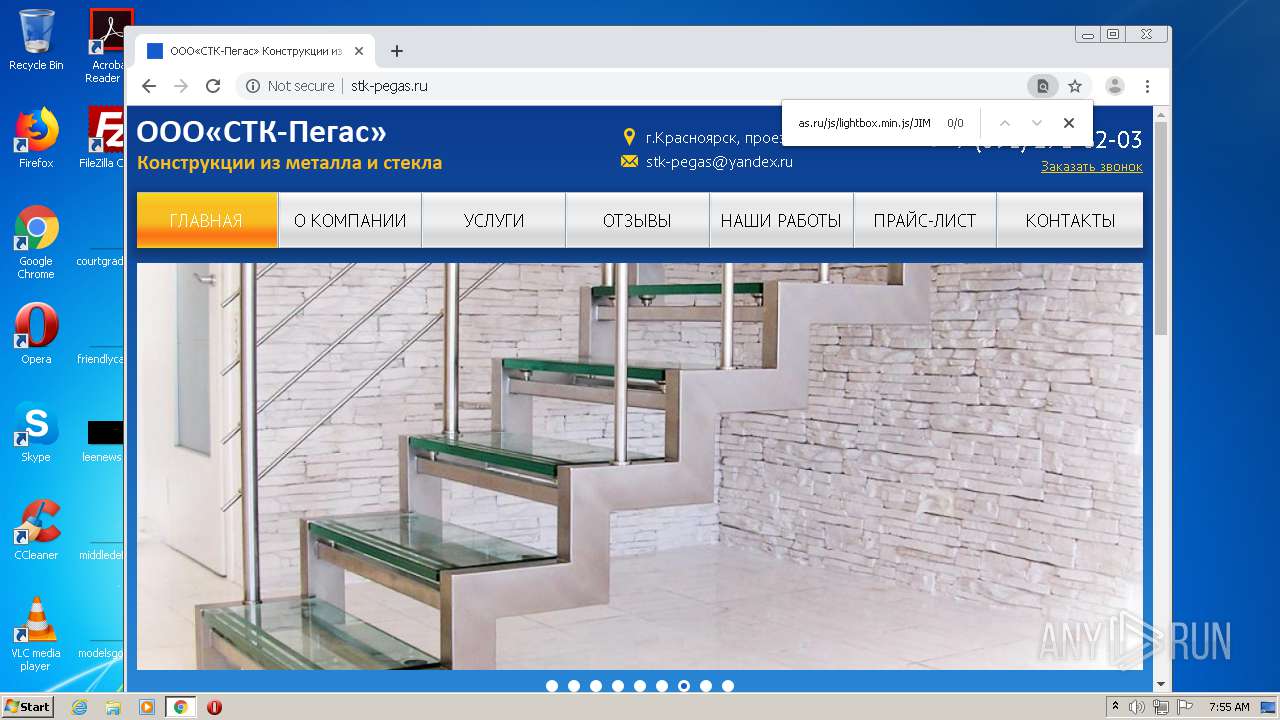
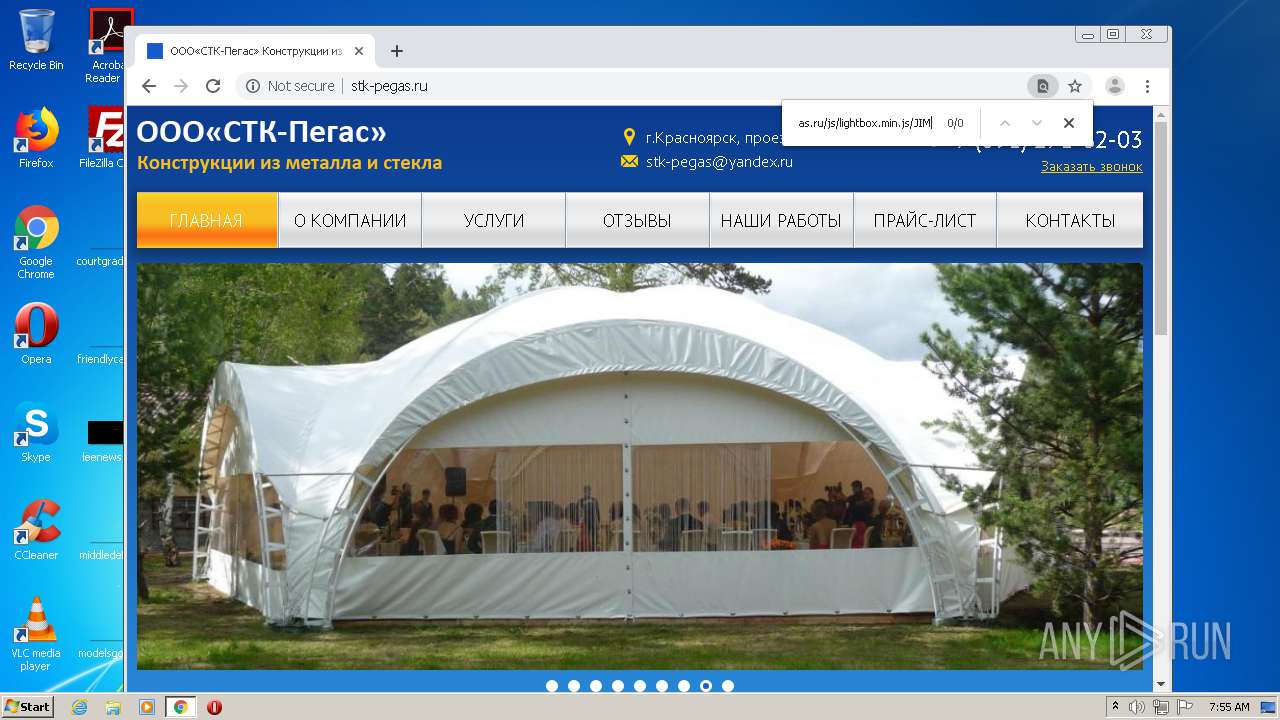
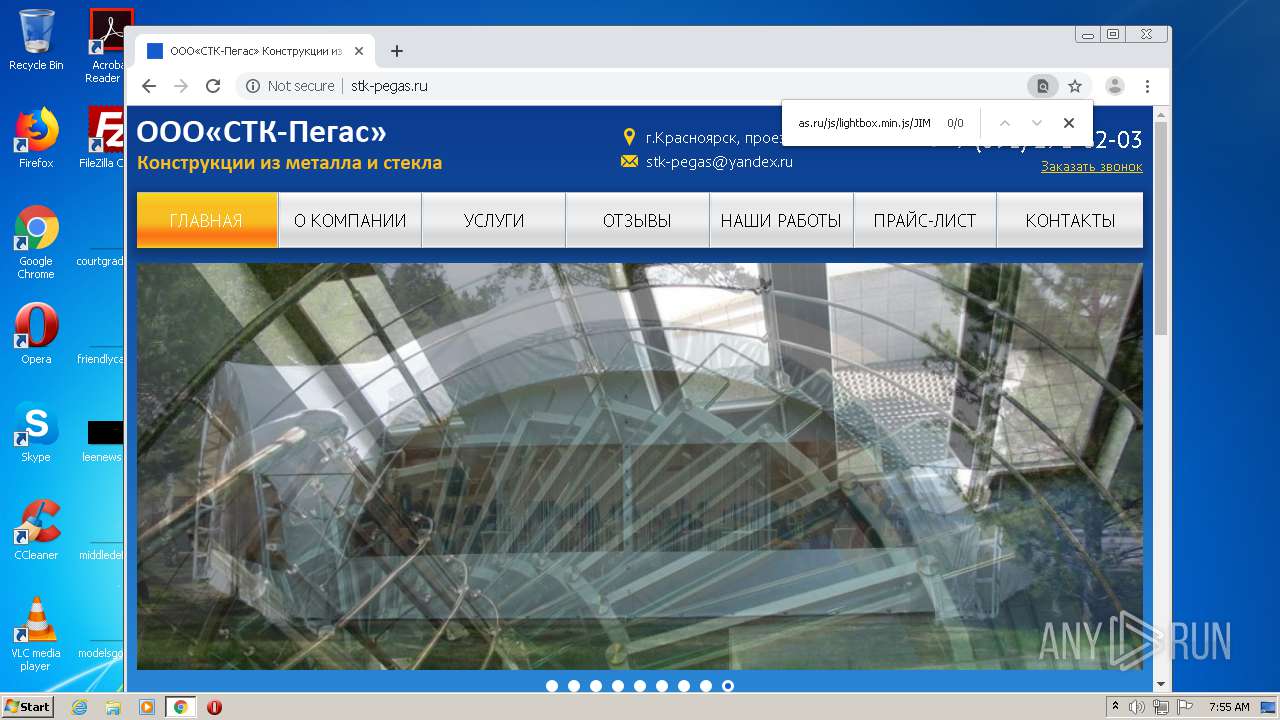
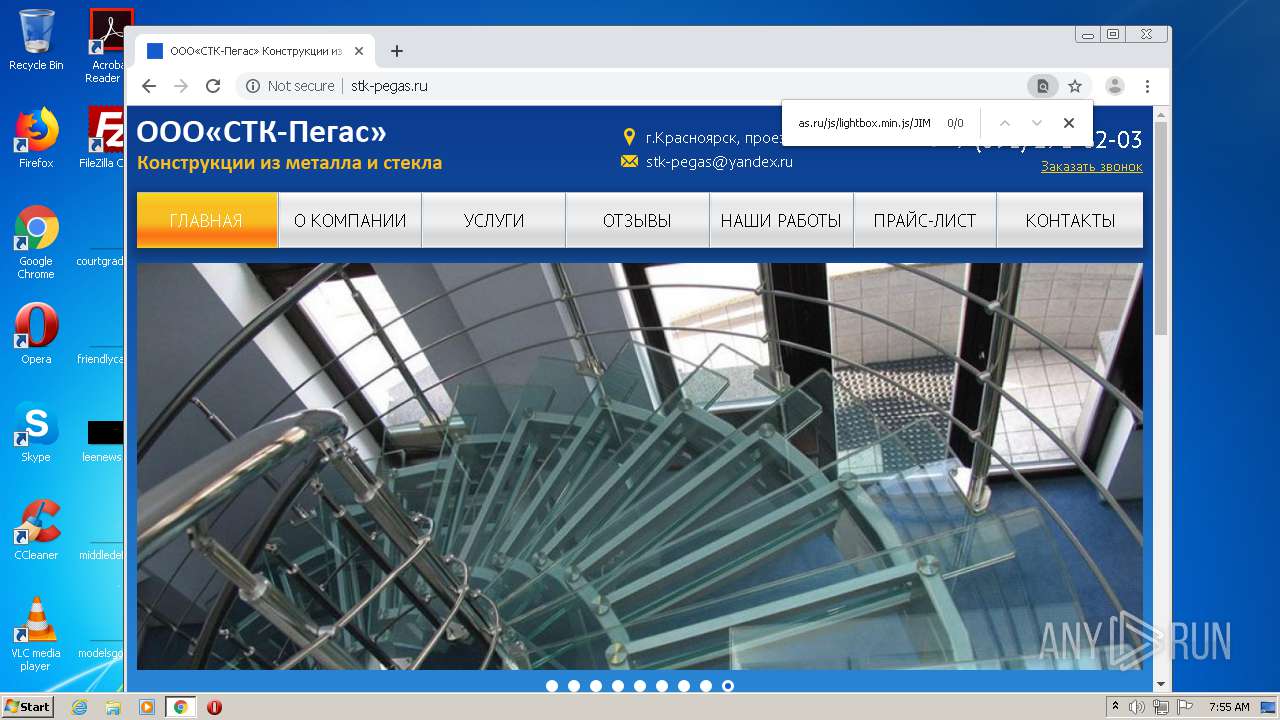
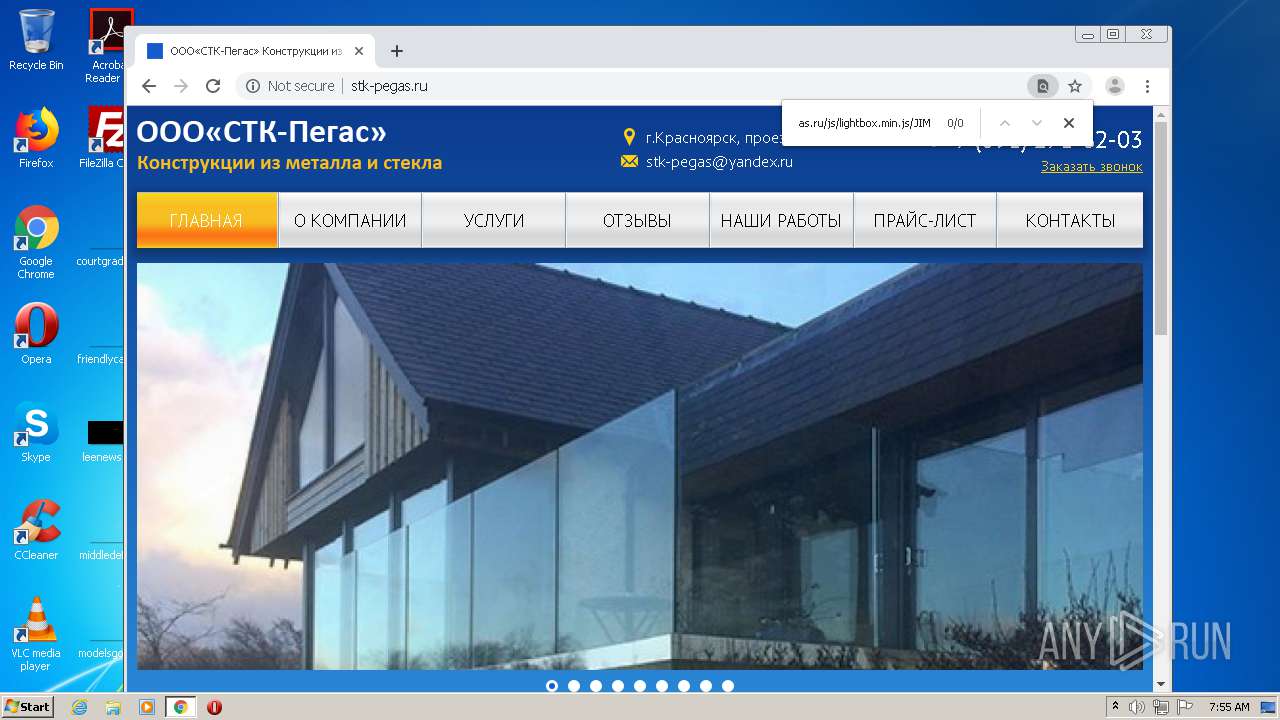
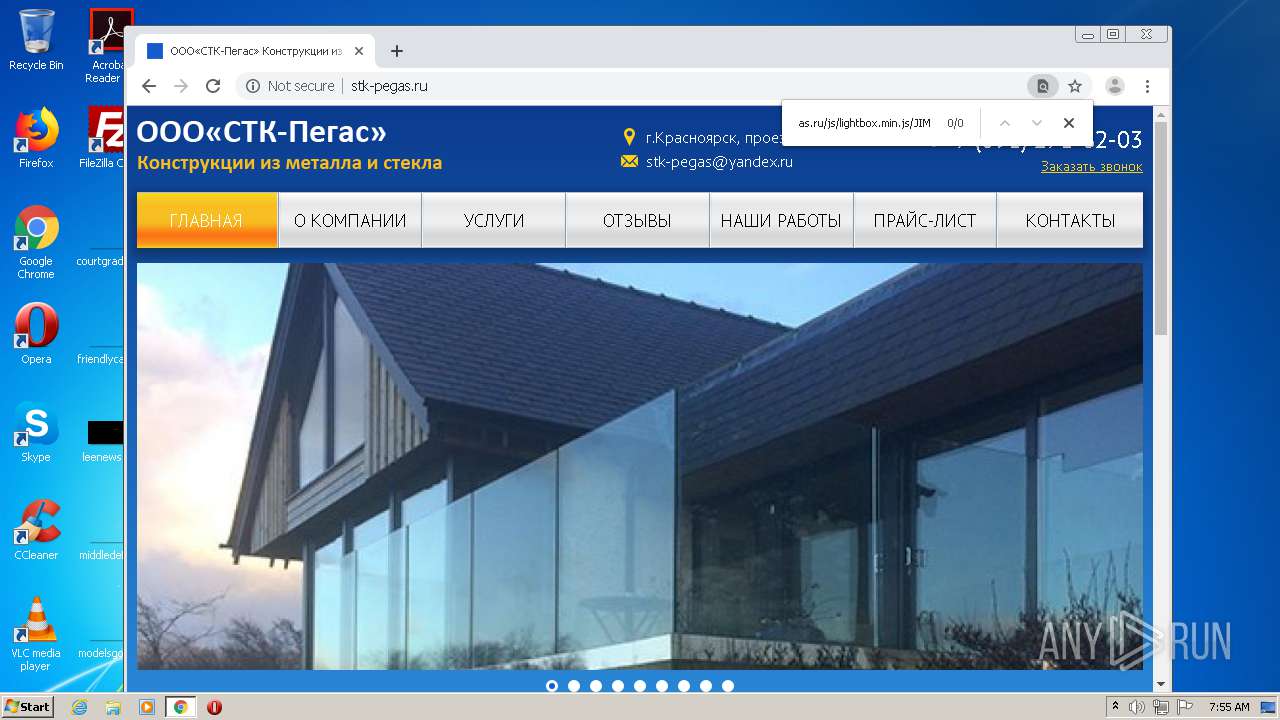
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/css/swiper.css?132 | RU | text | 3.21 Kb | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/css/lightbox.css | RU | text | 1.00 Kb | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/ | RU | html | 5.41 Kb | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/img/x.png | RU | image | 1.66 Kb | malicious |
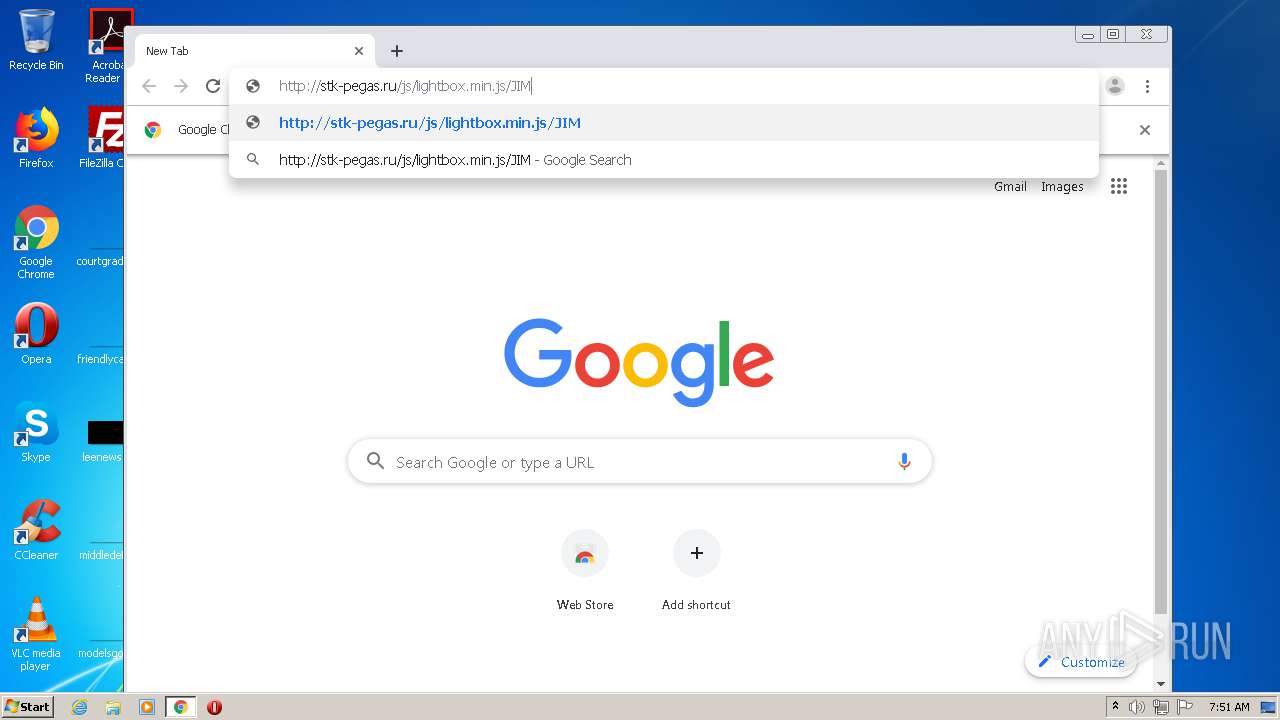
2248 | chrome.exe | GET | 404 | 92.53.118.140:80 | http://stk-pegas.ru/js/lightbox.min.js/JIM/ | RU | html | 559 b | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/css/style.css?132 | RU | text | 5.38 Kb | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/img/phone.png | RU | image | 1.16 Kb | malicious |
2248 | chrome.exe | GET | 301 | 92.53.118.140:80 | http://stk-pegas.ru/js/lightbox.min.js/JIM | RU | html | 251 b | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/js/lightbox.min.js | RU | s | 145 Kb | malicious |
2248 | chrome.exe | GET | 200 | 92.53.118.140:80 | http://stk-pegas.ru/favicon.ico | RU | image | 96 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2248 | chrome.exe | 172.217.21.196:443 | www.google.com | Google Inc. | US | whitelisted |
4 | System | 80.68.253.2:445 | s.rbk.ru | Rosbusinessconsulting Cjsc | RU | unknown |
4 | System | 185.72.229.2:445 | s.rbk.ru | Rosbusinessconsulting Cjsc | RU | unknown |
2248 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
964 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2248 | chrome.exe | 216.58.212.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
— | — | 185.72.229.2:137 | s.rbk.ru | Rosbusinessconsulting Cjsc | RU | unknown |
2248 | chrome.exe | 216.58.212.142:443 | apis.google.com | Google Inc. | US | whitelisted |
2248 | chrome.exe | 142.250.74.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2248 | chrome.exe | 172.217.16.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s.rbk.ru |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report