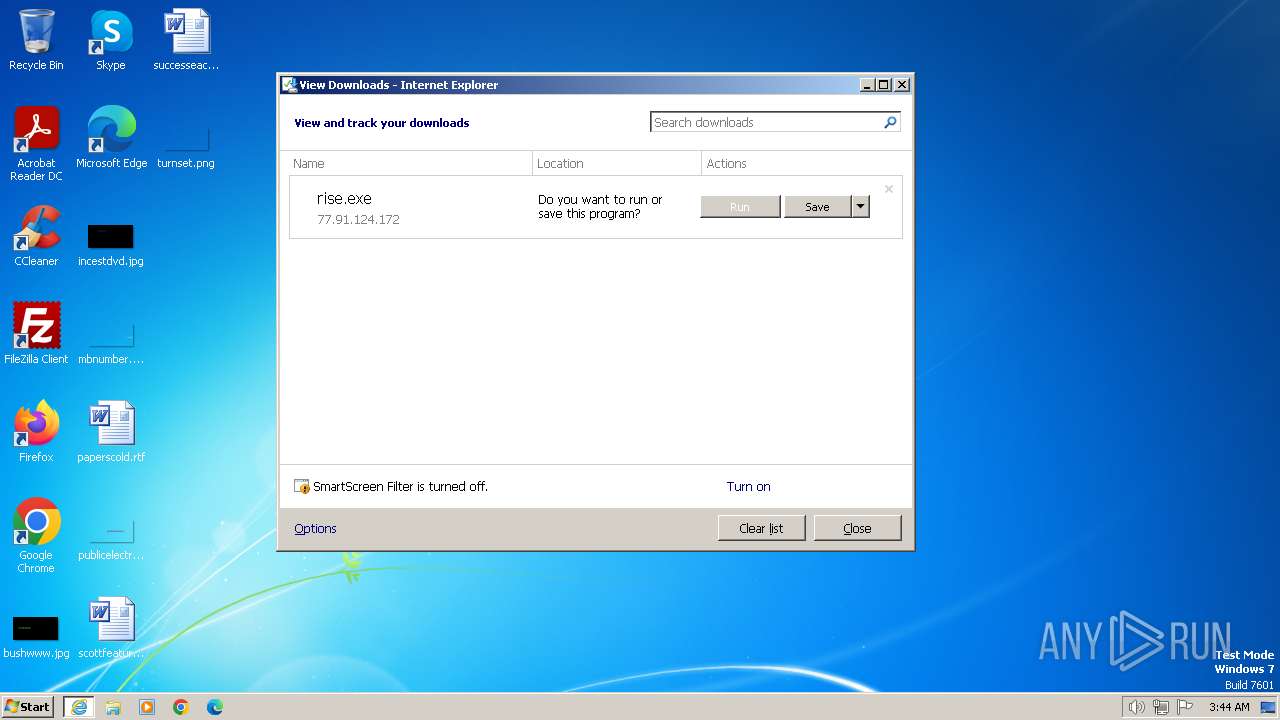
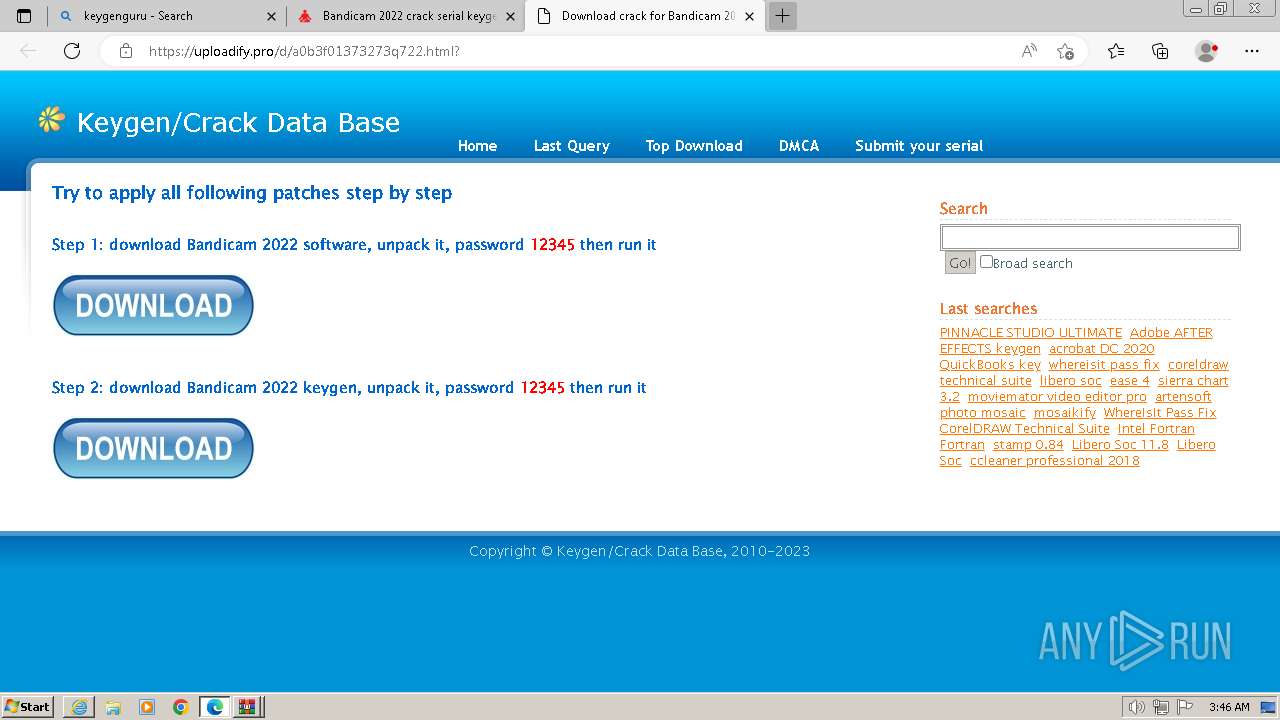
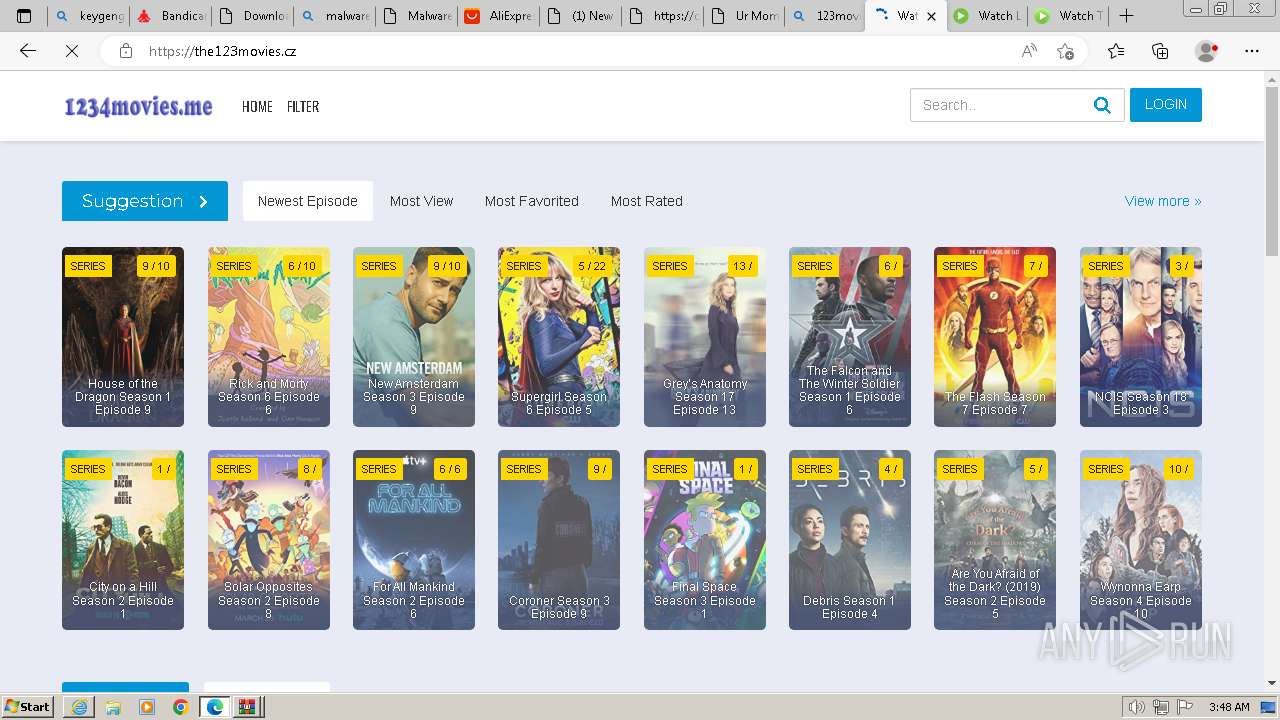
| URL: | http://77.91.124.172:3350/rise.exe |
| Full analysis: | https://app.any.run/tasks/12ec86e9-956f-4fa2-95ab-33ddeab74b46 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | December 20, 2023, 03:44:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 770B0FB483254B2BD0D3BF2123F43678 |
| SHA1: | 853436DDDDAF8AADBB50FCCE768035FF915E98F7 |
| SHA256: | E1D19AD3BDC2606CC812B5CC108C20A5CE285EA8BB09D26A0F951B13C2C86FEE |
| SSDEEP: | 3:N1KcLcU5KXMrAdAn:Ccone4A |
MALICIOUS
RISEPRO has been detected (YARA)
- rise.exe (PID: 1864)
Drops the executable file immediately after the start
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- keygen-pj.exe (PID: 2968)
Steals credentials from Web Browsers
- key.exe (PID: 3940)
AZORULT has been detected (SURICATA)
- keygen-step-1.exe (PID: 952)
Connects to the CnC server
- keygen-step-1.exe (PID: 952)
- key.exe (PID: 3940)
PONY has been detected (SURICATA)
- key.exe (PID: 3940)
Starts CMD.EXE for self-deleting
- keygen-step-3.exe (PID: 1628)
Actions looks like stealing of personal data
- key.exe (PID: 3940)
SUSPICIOUS
Connects to unusual port
- rise.exe (PID: 1864)
Reads the Internet Settings
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- cmd.exe (PID: 2824)
- control.exe (PID: 3108)
- keygen-step-3.exe (PID: 1628)
- keygen-pj.exe (PID: 2968)
- key.exe (PID: 3940)
- keygen-step-1.exe (PID: 952)
Application launched itself
- WinRAR.exe (PID: 2852)
Starts CMD.EXE for commands execution
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- key.exe (PID: 3940)
- keygen-step-3.exe (PID: 1628)
Executing commands from a ".bat" file
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- key.exe (PID: 3940)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 3108)
Checks Windows Trust Settings
- keygen-step-3.exe (PID: 1628)
Searches for installed software
- key.exe (PID: 3940)
Reads settings of System Certificates
- keygen-step-3.exe (PID: 1628)
Reads security settings of Internet Explorer
- keygen-step-3.exe (PID: 1628)
Accesses Microsoft Outlook profiles
- key.exe (PID: 3940)
INFO
Checks supported languages
- rise.exe (PID: 1864)
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- keygen-pj.exe (PID: 2968)
- keygen-step-1.exe (PID: 952)
- keygen-step-3.exe (PID: 1628)
- key.exe (PID: 3940)
The process uses the downloaded file
- iexplore.exe (PID: 124)
- msedge.exe (PID: 1592)
- WinRAR.exe (PID: 2852)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 124)
- WinRAR.exe (PID: 2496)
- msedge.exe (PID: 2128)
Application launched itself
- iexplore.exe (PID: 124)
- msedge.exe (PID: 2128)
Reads the computer name
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- keygen-pj.exe (PID: 2968)
- keygen-step-1.exe (PID: 952)
- keygen-step-3.exe (PID: 1628)
- key.exe (PID: 3940)
Create files in a temporary directory
- Bandicam.2022.software.by.ViKiNG.exe (PID: 3000)
- keygen-pj.exe (PID: 2968)
- key.exe (PID: 3940)
Manual execution by a user
- msedge.exe (PID: 2128)
The executable file from the user directory is run by the CMD process
- keygen-step-1.exe (PID: 952)
- keygen-pj.exe (PID: 2968)
- keygen-step-3.exe (PID: 1628)
Reads the machine GUID from the registry
- keygen-step-1.exe (PID: 952)
- keygen-step-3.exe (PID: 1628)
Reads product name
- keygen-step-1.exe (PID: 952)
Reads Environment values
- keygen-step-1.exe (PID: 952)
Checks proxy server information
- keygen-step-1.exe (PID: 952)
- keygen-step-3.exe (PID: 1628)
Connects to unusual port
- iexplore.exe (PID: 2204)
- msedge.exe (PID: 1844)
Creates files or folders in the user directory
- keygen-step-3.exe (PID: 1628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(1864) rise.exe
C2193.233.132.51
Total processes
139
Monitored processes
98
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://77.91.124.172:3350/rise.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 148 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2288 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=54 --mojo-platform-channel-handle=5468 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 548 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --mojo-platform-channel-handle=1188 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 712 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6c6ef598,0x6c6ef5a8,0x6c6ef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=47 --mojo-platform-channel-handle=2964 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=45 --mojo-platform-channel-handle=6832 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4176 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 952 | keygen-step-1.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-1.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=33 --mojo-platform-channel-handle=3836 --field-trial-handle=1324,i,2266744321520797610,751307095970306648,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
35 855
Read events
35 557
Write events
297
Delete events
1
Modification events
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
71
Suspicious files
1 717
Text files
349
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\rise.exe | executable | |
MD5:D5816E2B10599B51F528FB6E70D2E1B0 | SHA256:5D91DCD7EE9561C10AE772EF67696015714AAAF8B323C1C4A0E19F60ED6B68E8 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\rise.exe.5fuvru2.partial | executable | |
MD5:D5816E2B10599B51F528FB6E70D2E1B0 | SHA256:5D91DCD7EE9561C10AE772EF67696015714AAAF8B323C1C4A0E19F60ED6B68E8 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\rise[1].exe | executable | |
MD5:1DDC9F5875EE191978EC78D0F5E84AA9 | SHA256:72E833697F5112BD7822BA2DDF2ECED556E3EC74BB095048325329B73C757B89 | |||
| 2128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe93ef.TMP | — | |
MD5:— | SHA256:— | |||
| 2128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\rise.exe.5fuvru2.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 712 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:C612E96CBFAC63232FC2062E15600FB1 | SHA256:DB3C05D5EC0B6719A73E7F0BE84BCE9342772DA70567E7CE08CF6573480B38FF | |||
| 2128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:C7352A0E98449CC8AEDC1D6954C4CCD9 | SHA256:3A1591F52AD31B5B0B48F97AB5E1361D0AD0FA0F584E8FE8EFD482801DC2B9B5 | |||
| 2128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe941d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
626
DNS requests
415
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
124 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5f7e58f3f8ff9305 | unknown | compressed | 4.66 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 77.91.124.172:3350 | http://77.91.124.172:3350/rise.exe | unknown | executable | 1.61 Mb | unknown |
124 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ce98c71dc2a1b149 | unknown | compressed | 4.66 Kb | unknown |
124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3940 | key.exe | POST | — | 188.114.97.3:80 | http://top.thisispw.com/keys7369921/gate.php | unknown | — | — | unknown |
952 | keygen-step-1.exe | POST | 200 | 185.180.231.18:80 | http://gigaload.info/1210776429.php | unknown | text | 4 b | unknown |
124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
1628 | keygen-step-3.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEGxVq9vQB5LHnQcM2BGe1r8%3D | unknown | binary | 2.18 Kb | unknown |
124 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a10a16456a3ace15 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2204 | iexplore.exe | 77.91.124.172:3350 | — | Foton Telecom CJSC | RU | malicious |
1864 | rise.exe | 193.233.132.51:50500 | — | ATT-INTERNET4 | US | malicious |
124 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
124 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
124 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2128 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1844 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2204 | iexplore.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2204 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2204 | iexplore.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1844 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
952 | keygen-step-1.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/AZORult V3.3 Client Checkin M2 |
1628 | keygen-step-3.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3940 | key.exe | Malware Command and Control Activity Detected | ET MALWARE Fareit/Pony Downloader Checkin 2 |
3940 | key.exe | A Network Trojan was detected | ET MALWARE Trojan Generic - POST To gate.php with no referer |
3940 | key.exe | Potentially Bad Traffic | ET MALWARE Generic -POST To gate.php w/Extended ASCII Characters (Likely Zeus Derivative) |
1844 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PUP Domain (omnatuor .com) |
3 ETPRO signatures available at the full report