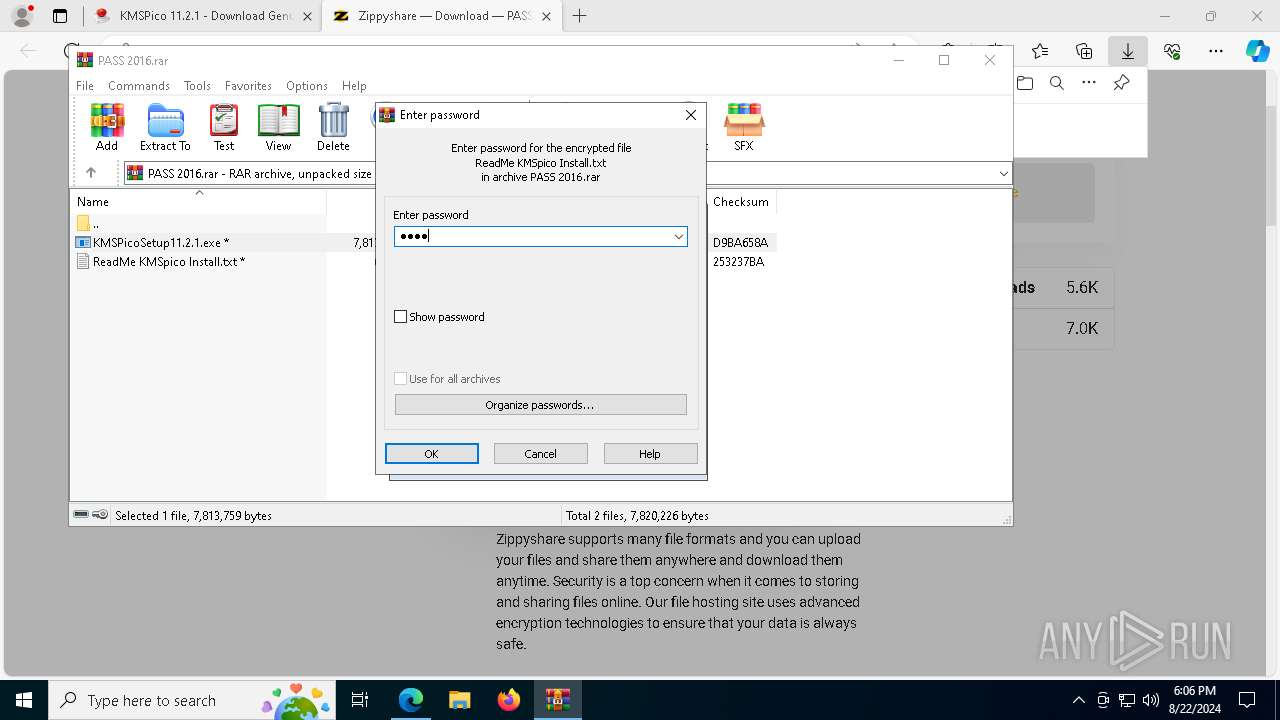
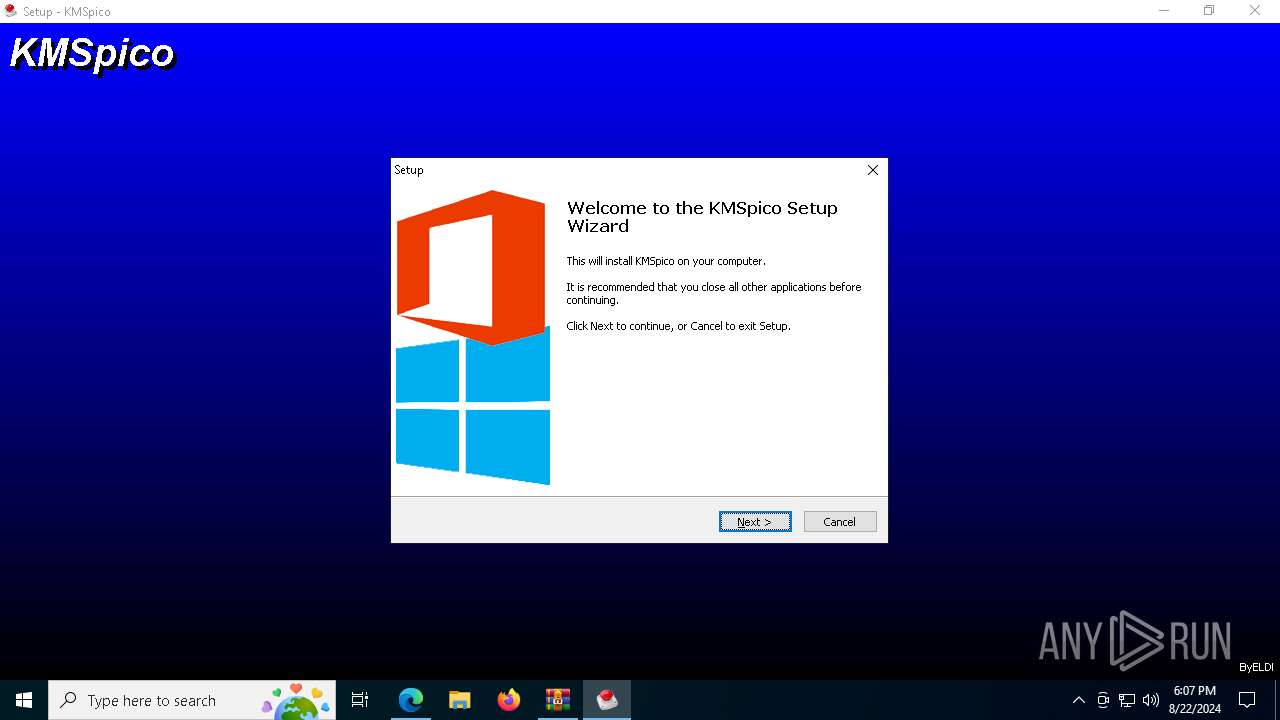
| URL: | https://kmspi.co/kmspico-11/ |
| Full analysis: | https://app.any.run/tasks/1cf7b040-044c-4fc5-aea4-936902d19075 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 22, 2024, 18:05:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A61428445AAA2C4AD8FEA9DF88CD5E41 |
| SHA1: | 60B8CD4730CDAC1BD13A10498CED6FBC7E56F030 |
| SHA256: | E180703B26D72E1E79DA4B5024351878D05452EFFE8D0919F2DFBB7DB7883643 |
| SSDEEP: | 3:N8N/eT:2deT |
MALICIOUS
Adds extension to the Windows Defender exclusion list
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
MINER has been detected (SURICATA)
- explorer.exe (PID: 7724)
- svchost.exe (PID: 2256)
Connects to the CnC server
- explorer.exe (PID: 7724)
XORed URL has been found (YARA)
- explorer.exe (PID: 7724)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 7724)
SILENTCRYPTOMINER has been detected (SURICATA)
- explorer.exe (PID: 7724)
Changes image file execution options
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7588)
SUSPICIOUS
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 7368)
- WinRAR.exe (PID: 7300)
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.tmp (PID: 3672)
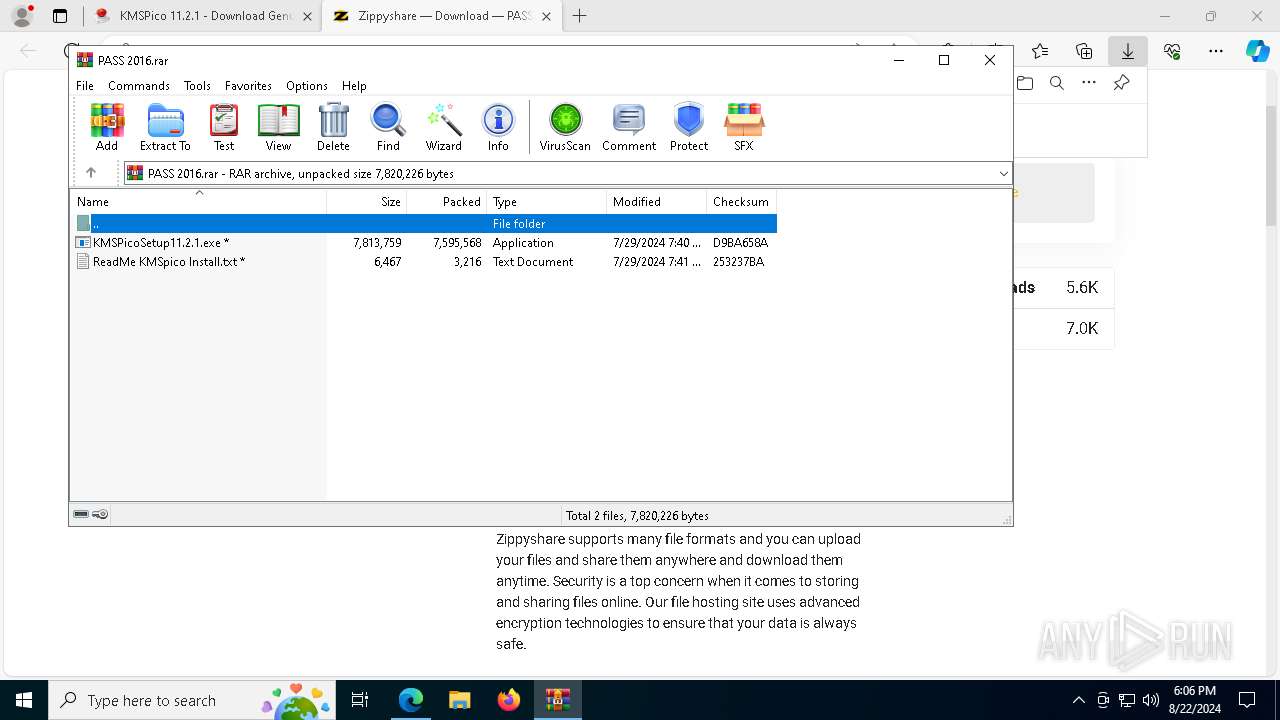
Executable content was dropped or overwritten
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.exe (PID: 2816)
- KMSpicosetup.tmp (PID: 5700)
- KMSpicosetup.exe (PID: 4880)
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
- KMSELDI.exe (PID: 4524)
The process creates files with name similar to system file names
- KMSPicoSetup11.2.1.exe (PID: 1440)
Drops the executable file immediately after the start
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.exe (PID: 2816)
- KMSpicosetup.tmp (PID: 5700)
- KMSpicosetup.exe (PID: 4880)
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
- KMSELDI.exe (PID: 4524)
Reads the date of Windows installation
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.tmp (PID: 3672)
Starts POWERSHELL.EXE for commands execution
- RegistryHost.exe (PID: 2396)
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
Powershell scripting: start process
- RegistryHost.exe (PID: 2396)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 4076)
Process drops legitimate windows executable
- KMSpicosetup.tmp (PID: 5700)
Reads the Windows owner or organization settings
- KMSpicosetup.tmp (PID: 5700)
Script adds exclusion extension to Windows Defender
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
Script adds exclusion path to Windows Defender
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
Starts CMD.EXE for commands execution
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
- KMSpicosetup.tmp (PID: 5700)
Starts SC.EXE for service management
- RegistryHost.exe (PID: 6380)
- cmd.exe (PID: 7576)
Process uninstalls Windows update
- wusa.exe (PID: 8156)
- wusa.exe (PID: 7896)
Executes as Windows Service
- rkduajedzcrd.exe (PID: 7540)
Drops a system driver (possible attempt to evade defenses)
- rkduajedzcrd.exe (PID: 7540)
Potential Corporate Privacy Violation
- explorer.exe (PID: 7724)
- svchost.exe (PID: 2256)
Executing commands from ".cmd" file
- KMSpicosetup.tmp (PID: 5700)
Modifies the phishing filter of IE
- KMSpicosetup.tmp (PID: 5700)
Connects to unusual port
- explorer.exe (PID: 7724)
Crypto Currency Mining Activity Detected
- explorer.exe (PID: 7724)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 6696)
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
Checks supported languages
- identity_helper.exe (PID: 7664)
- cookie_exporter.exe (PID: 7368)
- KMSPicoSetup11.2.1.exe (PID: 1440)
- RegistryHost.exe (PID: 2396)
- KMSpicosetup.tmp (PID: 3672)
- KMSpicosetup.exe (PID: 4880)
- KMSpicosetup.exe (PID: 2816)
- KMSpicosetup.tmp (PID: 5700)
- RegistryHost.exe (PID: 6380)
- rkduajedzcrd.exe (PID: 7540)
- UninsHs.exe (PID: 5400)
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
- SECOH-QAD.exe (PID: 6108)
Reads Environment values
- identity_helper.exe (PID: 7664)
- cookie_exporter.exe (PID: 7368)
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
Reads the computer name
- identity_helper.exe (PID: 7664)
- cookie_exporter.exe (PID: 7368)
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.tmp (PID: 3672)
- KMSpicosetup.tmp (PID: 5700)
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
Checks proxy server information
- cookie_exporter.exe (PID: 7368)
The process uses the downloaded file
- msedge.exe (PID: 4316)
- msedge.exe (PID: 6696)
- WinRAR.exe (PID: 7300)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7300)
Create files in a temporary directory
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.exe (PID: 2816)
- KMSpicosetup.exe (PID: 4880)
- KMSpicosetup.tmp (PID: 5700)
Process checks computer location settings
- KMSPicoSetup11.2.1.exe (PID: 1440)
- KMSpicosetup.tmp (PID: 3672)
Application launched itself
- msedge.exe (PID: 6696)
The executable file from the user directory is run by the Powershell process
- RegistryHost.exe (PID: 6380)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 6356)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 6356)
Creates files in the program directory
- KMSpicosetup.tmp (PID: 5700)
- RegistryHost.exe (PID: 6380)
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
UPX packer has been detected
- explorer.exe (PID: 7724)
Creates a software uninstall entry
- KMSpicosetup.tmp (PID: 5700)
Reads product name
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 4524)
- AutoPico.exe (PID: 7200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(7724) explorer.exe
Decrypted-URLs (1)https://206.12
Total processes
246
Monitored processes
102
Malicious processes
12
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 508 | C:\WINDOWS\system32\sc.exe stop eventlog | C:\Windows\System32\sc.exe | — | RegistryHost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1051 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5672 --field-trial-handle=2452,i,13576902805915908532,17816386157089299394,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6368 --field-trial-handle=2452,i,13576902805915908532,17816386157089299394,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1440 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb7300.32522\KMSPicoSetup11.2.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb7300.32522\KMSPicoSetup11.2.1.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=51 --mojo-platform-channel-handle=7120 --field-trial-handle=2452,i,13576902805915908532,17816386157089299394,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=792 --field-trial-handle=2452,i,13576902805915908532,17816386157089299394,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\RegistryHost.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\RegistryHost.exe | — | KMSPicoSetup11.2.1.exe | |||||||||||
User: admin Company: MS Inc. Integrity Level: MEDIUM Description: Registry Host Exit code: 0 Version: 70,0,3538,110 Modules
| |||||||||||||||
Total events
55 448
Read events
55 119
Write events
309
Delete events
20
Modification events
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 6789277 | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31126718 | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6532) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
34
Suspicious files
345
Text files
860
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11dbe6.TMP | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11dbe6.TMP | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11dbe6.TMP | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11dbe6.TMP | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF11dc34.TMP | — | |
MD5:— | SHA256:— | |||
| 6696 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
143
DNS requests
138
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5116 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7992 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7944 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
6192 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7944 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
7944 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
7944 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
7944 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
7944 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
7944 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/47f9eec4-45e7-4567-b813-2cac77a54a3d?P1=1724900017&P2=404&P3=2&P4=eIZKxX7JpWo%2beXaVYJvglzDWsBvwvpGq5ajOhNoek8MkV6H1GeHKEhcowd5x9fVccp2MBC8SnF6MfrnzIxykMA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5144 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1488 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6968 | msedge.exe | 169.150.247.36:443 | kmspico.b-cdn.net | — | — | unknown |
6968 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6696 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6968 | msedge.exe | 188.114.96.3:443 | kmspi.co | CLOUDFLARENET | NL | unknown |
6968 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6968 | msedge.exe | 2.23.209.176:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
kmspi.co |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
kmspico.b-cdn.net |
| whitelisted |
www.bing.com |
| whitelisted |
www.statcounter.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6968 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Domain (wasabisys .com) in DNS Lookup |
6968 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Domain (wasabisys .com) in DNS Lookup |
6968 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Domain (wasabisys .com) in DNS Lookup |
6968 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Domain (wasabisys .com) in TLS SNI |
6968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2256 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY Observed DNS Query to Coin Mining Domain (nanopool .org) |
7724 | explorer.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M3 |
7724 | explorer.exe | A Network Trojan was detected | ET MALWARE SilentCryptoMiner Agent Config Inbound |
7724 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1 ETPRO signatures available at the full report